0bf44a9e04a3b913dee6e3c93d3ed29f.ppt
- Количество слайдов: 17

The Cyber. Science Laboratory: A Cyber. Security and Incident Response Enabler 8 November 2007 Salvatore C. Paladino, CISSP

Overview • • • Mission/Objectives Staff Cyber. Security Network of Partners Delivery System Rapid Technology Deployments Technology Development and Analysis – Rapid Forensic Analyst • Dynamic Training Capabilities • Virtual Training Portal and Resources – Cyber. Security Technical Assistance Package • Embedded Intern Program • Future Plans

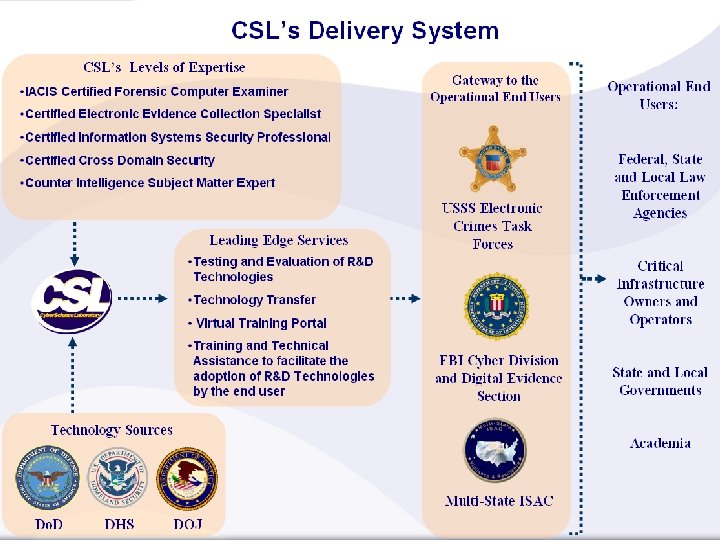
Cyber. Science Laboratory • Established March 2000 • Mission/Objectives – Develop a national and international government, industry & academia network to address cybersecurity technical issues – Evaluate DOD, DHS and DOJ R&D technologies and provide technology assistance for transition to federal, state and local law enforcement agencies and critical infrastructure owners and operators across the U. S. – Facilitate cybersecurity training, technical assistance and technology transfer to the cybersecurity community Rapid Technology Deployment Tool Demonstrations Cyber. Security Training

CSL Staff • Members of the CSL staff include: – – Cyber Security Specialists Electronic Crime Specialists Information Analysts Software Engineers • Certifications include: – Certified Forensic Computer Examiner (CFCE) – Certified Electronic Evidence Collection Specialist (CEECS) – Certified Information Systems Security Professional (CISSP) – Network+ Certified Professional – Certified Ethical Hacker (CE/H)

CSL’s Public, Private and Academia Network • Public Sector – National Institute of Justice – Office of Science & Technology – Air Force Research Laboratory/Information Directorate – Department of Homeland Security - Science and Technology –– National. Electronic Crimes Task Forces (ECTFs) DHS/USSS Institute of Justice – Office of Science & Technology • – Air Atlanta, Charlotte, Chicago, Dallas, Houston, Kentucky, Los Angeles, Miami, New England, New York, San Francisco, Force Research Laboratory/Information Directorate Washington D. C. Federal Bureau of Investigation (FBI) Cyber Division - Digital Evidence Section (DES) –– Department of Homeland Securityand. Science and Technology – Inter-American Committee Against Terrorism (CICTE) –– DHS/USSS Electronic Crimes Task Forces (ECTFs) International Association of Computer Investigative Specialists (IACIS) – Multi-State Information Sharing and Analysis Center Houston, Kentucky, Los Angeles, Miami, New • Atlanta, Charlotte, Chicago, Dallas, (MS-ISAC) – New York City Criminal Justice. San Francisco, Washington D. C. England, New York, Coordinator’s Office – New York State Police (NYSP) –– Federal Bureau of Investigation (FBI) Cyber Division and Digital Evidence Organization of American States (OAS) – Section (DES) Upstate New York Electronic Crimes Coalition (UNYECC) – Western NY Regional Computer Forensic Lab –– Inter-American Committee Against Terrorism (CICTE) Infragard – International Association of Computer Investigative Specialists (IACIS) – Central New York Computer Crime Coalition (CNY 3 C) • Private Sector –– Multi-State Information Sharing and Analysis Center. Paraben Corporation – (MS-ISAC) Access. Data Corporation – – Digital Intelligence, Inc. –– New York City. Inc. Criminal Justice Coordinator’s Office Partners Trust Bank – The Training. Co. LLC. Dolphin Technology, – Wet. Stone Technologies, Inc. Guidance Software –– New York State Police (NYSP) – International High Technology Crime Investigation Association (HTCIA) –– Organization of American States (OAS) Intelligent Computer Solutions, Inc. – Upstate. Chase York Electronic Crimes Coalition (UNYECC) – JPMorgan New – Master. Card –– Western NY Regional Computer Forensic Lab National Grid • Academia –– Infragard Economic Crime Investigation Institute – Eastern Kentucky University Utica College: – Florida Atlantic University John Jay New York Computer Crime Coalition University – Stanford (CNY 3 C) –– Central. College of Criminal Justice – George Mason University – Syracuse University – James Madison University – George Washington University – Columbia University – Champlain College – Carnegie Mellon University – Dartmouth College – Cornell University – University of Dayton: Institute on Law, Technology & Security • Public Sector Academia Private Sector – Access. Data Corporation Crime Investigation Institute Utica College: Economic – Digital Intelligence, Inc. John Jay College of Criminal Justice – Guidance University Syracuse Software – International High Technology Crime Investigation Association (HTCIA) Columbia University – ITT Dolphin Technology, LLC Carnegie Mellon University – Intelligent Computer Solutions, Inc. Cornell University – JPMorgan Chase University Eastern Kentucky – Master. Card Stanford University – National Grid University James Madison – Paraben Corporation Champlain College – Partners Trust Bank Dartmouth College – The Training. Co. LLC. Institute on Law, Technology & Security University of Dayton: – Wet. Stone Technologies, Inc. Florida Atlantic University – George Mason University – George Washington University

Rapid Technology Deployments Wireless Intrusion Detection System (WIDS) MOZART Impact of deployments on the practitioner community • Demonstrated a need for wireless security and identified wireless gaps in networks Future Deployments • Saved a tremendous amount of manual work that is now automated Future Test Sites • Immigrations and Customs Enforcement • CAULDRON • Office of Emergency & Public Health • Iron. Key üDeployed • Zippy Reporting Tool üDeployed Preparedness • USSS ECTFs • Phish. Bouncer • Utica Police Department • Rapid Forensic Analyst Presidential Debate (2004) Utica PD (2004) Gaston County, NC and Gastonia PD (2005 - 2006) Miami ECTF (2007)

Rapid Forensic Analyst • First responder’s triage tool forensic analysis – Quickly and easily assess field situations – Focus on pertinent, relevant, and useful data while filtering out extraneous information – Gather potentially volatile (perishable) information in a secure manner • Use indications & warnings to focus first responders: – Where to look – What evidence gathering tools to use and in what order • Turnkey solution – Ideal for border, parole, or other incident response – Ready for beta testing

Technology Analysis • An unbiased “honest broker” approach for the functional testing and evaluation of the following technologies: – – Government Commercial Open-source Freeware • Demonstrate technologies to the cybersecurity community to raise awareness • Provide on-site technology assistance to help facilitate the adoption of appropriate cybersecurity technology solutions

CSL’s Dynamic Training Capabilities Judicial and Prosecutor’s Perspectives on Electronic Crime Cyber. Crimes Investigations Training Course Intrusion Forensic Experiment (IFX) Forensic Tool Workshop Senior Official's Cyber. Security Seminar The CSL has trained over 2, 000 International, Federal, State, Local, and Private Sector Cyber. Security Agencies OAS Cyber. Security and Cyber. Crime Seminar

Cybersecurity/Cybercrime Training Topics
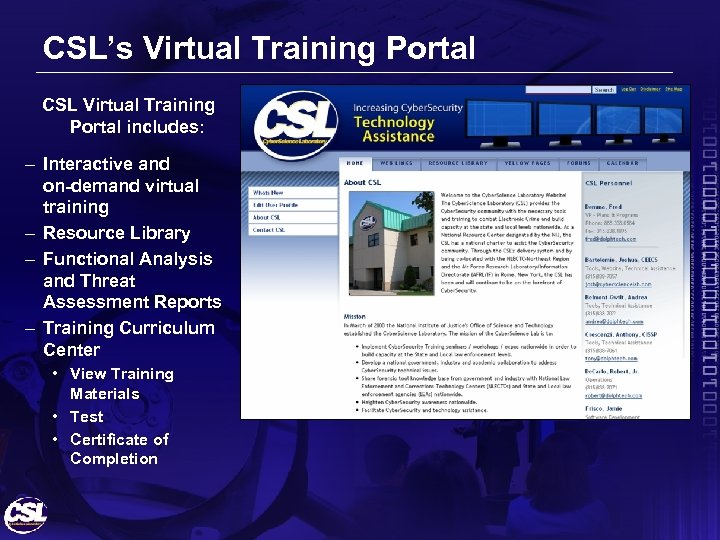
CSL’s Virtual Training Portal CSL Virtual Training Portal includes: – Interactive and on-demand virtual training – Resource Library – Functional Analysis and Threat Assessment Reports – Training Curriculum Center • View Training Materials • Test • Certificate of Completion

Training Resources Cyber. Security Cyberthreat Technical Resource Kit (C-Kit) Assistance CSL Desktop and Pocket Reference Cards Package CSL Cybersecurity and Cybercrime Training DVDs USSS Forward Edge II Training DVD


CSL Future Plans • Technology/Tool Transfer – 23 rd Annual Computer Security Applications Conference, FL – 12/07 – Develop of C-Kit v 3. 0 • Technical Assistance – Embedded intern program – NY/NJ ECTF and FBI’s RCFL • Capacity Building – OAS Cyber. Security and Cyber. Crime Seminar: The Way Forward, FL – 11/07 – Do. D 2008 Cyber. Crime Conference, MO – 1/08
Website Registration www. cybersciencelab. com

Thank You Salvatore C. Paladino, CISSP Cyber Security Specialist ITT Advanced Engineering & Sciences Cyber. Science Laboratory www. cybersciencelab. com sal. paladino@itt. com 315 -838 -7066
0bf44a9e04a3b913dee6e3c93d3ed29f.ppt