a7083a8c24ebd3492ed7b6d9be6593bb.ppt
- Количество слайдов: 11
 The 8 th ICCC in Rome, Italy Updates on Korean Scheme IT Security Certification Center, National Intelligence Service
The 8 th ICCC in Rome, Italy Updates on Korean Scheme IT Security Certification Center, National Intelligence Service
 Introduction to ITSCC v ITSCC(IT Security Certification Center) is… § Aiming at enhancing the IT security in government organizations by evaluating and certifying commercial IT security products that government organizations plan to procure § The certification body of Korea for security certification, responsible for properation of the Korean Evaluation and Certification Scheme(KECS) v Our Six Main Roles § Issue Common Criteria certificates for IT security products § Regulate the procurement of products within government § Plan and develop Protection Profiles for IT security products § Approve IT security evaluation facilities § Operate the training and education program for evaluators § Participate in CC related international cooperation IT Security Certification Center
Introduction to ITSCC v ITSCC(IT Security Certification Center) is… § Aiming at enhancing the IT security in government organizations by evaluating and certifying commercial IT security products that government organizations plan to procure § The certification body of Korea for security certification, responsible for properation of the Korean Evaluation and Certification Scheme(KECS) v Our Six Main Roles § Issue Common Criteria certificates for IT security products § Regulate the procurement of products within government § Plan and develop Protection Profiles for IT security products § Approve IT security evaluation facilities § Operate the training and education program for evaluators § Participate in CC related international cooperation IT Security Certification Center
 Korean Procurement Policy v Government organizations must procure certified IT security products since 1 Jan. 2006 § To promote the use of Common Criteria in Korea § To encourage Korean developers to produce sound security products that meet the international standards v Although this policy certainly contributed to the provision of improved confidence in commercial IT security products… v Encountered a problem § The number of products applying for CC certificates farexceeded the evaluation capacity we can afford § This means products have to wait for a long time in the queue before actual evaluation work begins IT Security Certification Center
Korean Procurement Policy v Government organizations must procure certified IT security products since 1 Jan. 2006 § To promote the use of Common Criteria in Korea § To encourage Korean developers to produce sound security products that meet the international standards v Although this policy certainly contributed to the provision of improved confidence in commercial IT security products… v Encountered a problem § The number of products applying for CC certificates farexceeded the evaluation capacity we can afford § This means products have to wait for a long time in the queue before actual evaluation work begins IT Security Certification Center
 New Evaluation Facilities(1) v Most obvious and effective solution was to expand evaluation capacity of the country § There was only one evaluation facility, KISA(Korea Information Security Agency), which had been established by law § In Dec. 2006, introduced a new procedure to approve evaluation facilities by amending the Korean Standard Lab. Accreditation Program v As a result, we have two more evaluation facilities § Early this year, KTL(Korea Testing Laboratory) and KOSYAS(Korea System Assurance) applied for approval § After accredited against ISO 17025, KTL and KOSYAS were finally approved as an evaluation facility on 29 June and 9 August, respectively IT Security Certification Center
New Evaluation Facilities(1) v Most obvious and effective solution was to expand evaluation capacity of the country § There was only one evaluation facility, KISA(Korea Information Security Agency), which had been established by law § In Dec. 2006, introduced a new procedure to approve evaluation facilities by amending the Korean Standard Lab. Accreditation Program v As a result, we have two more evaluation facilities § Early this year, KTL(Korea Testing Laboratory) and KOSYAS(Korea System Assurance) applied for approval § After accredited against ISO 17025, KTL and KOSYAS were finally approved as an evaluation facility on 29 June and 9 August, respectively IT Security Certification Center
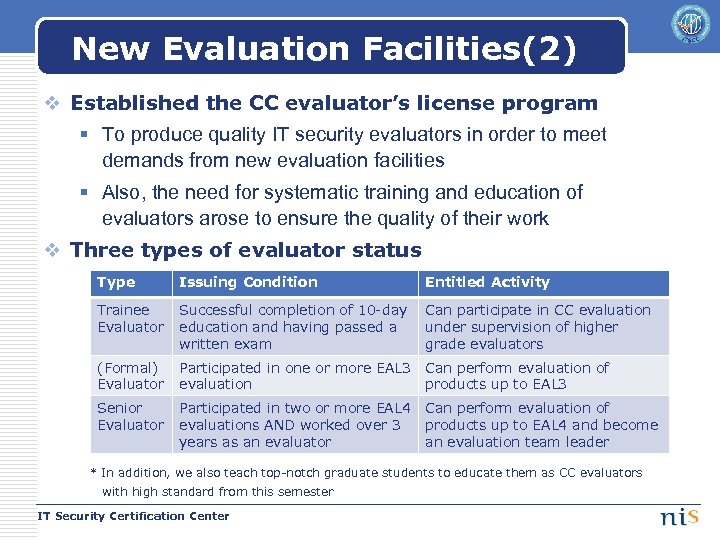 New Evaluation Facilities(2) v Established the CC evaluator’s license program § To produce quality IT security evaluators in order to meet demands from new evaluation facilities § Also, the need for systematic training and education of evaluators arose to ensure the quality of their work v Three types of evaluator status Type Issuing Condition Entitled Activity Trainee Evaluator Successful completion of 10 -day education and having passed a written exam Can participate in CC evaluation under supervision of higher grade evaluators (Formal) Evaluator Participated in one or more EAL 3 evaluation Can perform evaluation of products up to EAL 3 Senior Evaluator Participated in two or more EAL 4 evaluations AND worked over 3 years as an evaluator Can perform evaluation of products up to EAL 4 and become an evaluation team leader * In addition, we also teach top-notch graduate students to educate them as CC evaluators with high standard from this semester IT Security Certification Center
New Evaluation Facilities(2) v Established the CC evaluator’s license program § To produce quality IT security evaluators in order to meet demands from new evaluation facilities § Also, the need for systematic training and education of evaluators arose to ensure the quality of their work v Three types of evaluator status Type Issuing Condition Entitled Activity Trainee Evaluator Successful completion of 10 -day education and having passed a written exam Can participate in CC evaluation under supervision of higher grade evaluators (Formal) Evaluator Participated in one or more EAL 3 evaluation Can perform evaluation of products up to EAL 3 Senior Evaluator Participated in two or more EAL 4 evaluations AND worked over 3 years as an evaluator Can perform evaluation of products up to EAL 4 and become an evaluation team leader * In addition, we also teach top-notch graduate students to educate them as CC evaluators with high standard from this semester IT Security Certification Center
 Domestic Certification v Introduced a domestic certification scheme to shorten the evaluation time itself § Intended to deal with the products having waited or being expected to wait in the evaluation queue for quite a long time, say, more than a year § Identical to CC except that sampling-based evaluation is used for some components rather than full examination, being able to save evaluation time up to four weeks v The domestic scheme can only be regarded as a temporary solution because… § It still requires the same developer’s evidence as CC § And there is no significant reduction in evaluation time at the expense of internationally recognized CC certification * Note : This domestic scheme is outside the scope of the conference IT Security Certification Center
Domestic Certification v Introduced a domestic certification scheme to shorten the evaluation time itself § Intended to deal with the products having waited or being expected to wait in the evaluation queue for quite a long time, say, more than a year § Identical to CC except that sampling-based evaluation is used for some components rather than full examination, being able to save evaluation time up to four weeks v The domestic scheme can only be regarded as a temporary solution because… § It still requires the same developer’s evidence as CC § And there is no significant reduction in evaluation time at the expense of internationally recognized CC certification * Note : This domestic scheme is outside the scope of the conference IT Security Certification Center
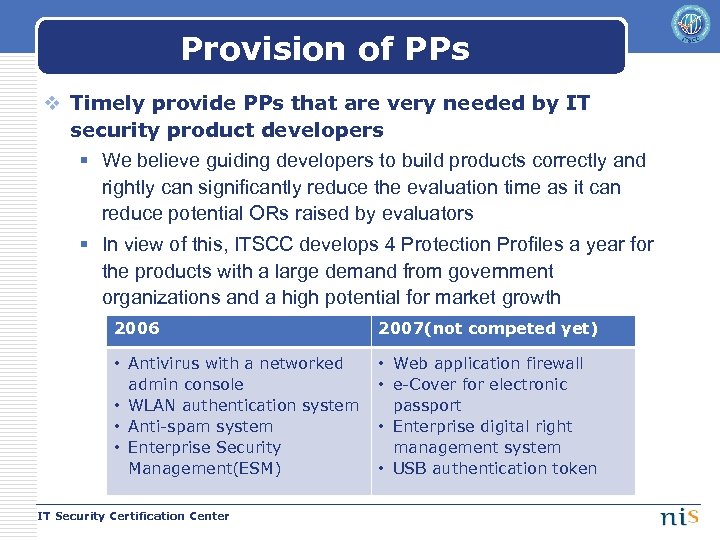 Provision of PPs v Timely provide PPs that are very needed by IT security product developers § We believe guiding developers to build products correctly and rightly can significantly reduce the evaluation time as it can reduce potential ORs raised by evaluators § In view of this, ITSCC develops 4 Protection Profiles a year for the products with a large demand from government organizations and a high potential for market growth 2006 • AND 2007(not competed yet) a high potential for market growth • Antivirus with a networked admin console • WLAN authentication system • Anti-spam system • Enterprise Security Management(ESM) IT Security Certification Center • Web application firewall • e-Cover for electronic passport • Enterprise digital right management system • USB authentication token
Provision of PPs v Timely provide PPs that are very needed by IT security product developers § We believe guiding developers to build products correctly and rightly can significantly reduce the evaluation time as it can reduce potential ORs raised by evaluators § In view of this, ITSCC develops 4 Protection Profiles a year for the products with a large demand from government organizations and a high potential for market growth 2006 • AND 2007(not competed yet) a high potential for market growth • Antivirus with a networked admin console • WLAN authentication system • Anti-spam system • Enterprise Security Management(ESM) IT Security Certification Center • Web application firewall • e-Cover for electronic passport • Enterprise digital right management system • USB authentication token
 CEMS (1) v Improve the management process of evaluation and certification by employing an automated document management system called CEMS § Handled documents manually because EF and CB are located very closely and therefore preferred in-person contact § However, manual handling of deliverables between CB and EF was partly responsible for inevitable delays in evaluation § Moreover, location of new EFs are widely separated across the city and therefore electronic communication becomes necessary v Therefore, started to build the CEMS system § Supports electronic management of documents § And also some essential functions of project management such as real time monitoring of progress * CEMS : Certification and Evaluation Management System IT Security Certification Center
CEMS (1) v Improve the management process of evaluation and certification by employing an automated document management system called CEMS § Handled documents manually because EF and CB are located very closely and therefore preferred in-person contact § However, manual handling of deliverables between CB and EF was partly responsible for inevitable delays in evaluation § Moreover, location of new EFs are widely separated across the city and therefore electronic communication becomes necessary v Therefore, started to build the CEMS system § Supports electronic management of documents § And also some essential functions of project management such as real time monitoring of progress * CEMS : Certification and Evaluation Management System IT Security Certification Center
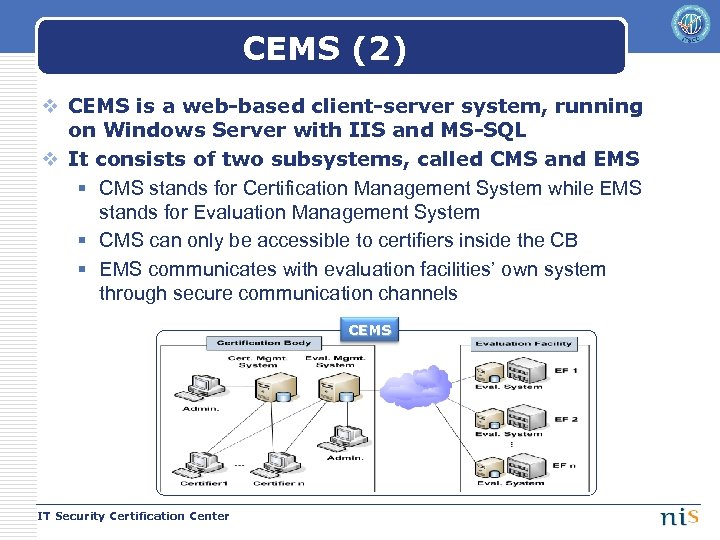 CEMS (2) v CEMS is a web-based client-server system, running on Windows Server with IIS and MS-SQL v It consists of two subsystems, called CMS and EMS § CMS stands for Certification Management System while EMS stands for Evaluation Management System § CMS can only be accessible to certifiers inside the CB § EMS communicates with evaluation facilities’ own system through secure communication channels CEMS IT Security Certification Center
CEMS (2) v CEMS is a web-based client-server system, running on Windows Server with IIS and MS-SQL v It consists of two subsystems, called CMS and EMS § CMS stands for Certification Management System while EMS stands for Evaluation Management System § CMS can only be accessible to certifiers inside the CB § EMS communicates with evaluation facilities’ own system through secure communication channels CEMS IT Security Certification Center
 CEMS (3) v Main Features of CEMS developed so far: § Online document management and storage § Real-time monitoring of work progress § Management of document templates § CEMS user management and audit functions § Backup and other system maintenance v With the help of CEMS, we expect to achieve the improved efficiency in evaluation and certification and reduction in evaluation and certification time v For anyone interested in CEMS, demonstration is available at out booth outside IT Security Certification Center
CEMS (3) v Main Features of CEMS developed so far: § Online document management and storage § Real-time monitoring of work progress § Management of document templates § CEMS user management and audit functions § Backup and other system maintenance v With the help of CEMS, we expect to achieve the improved efficiency in evaluation and certification and reduction in evaluation and certification time v For anyone interested in CEMS, demonstration is available at out booth outside IT Security Certification Center
 Conclusion Q&A IT Security Certification Center www. kecs. go. kr IT Security Certification Center
Conclusion Q&A IT Security Certification Center www. kecs. go. kr IT Security Certification Center


