b13078725865d8ebc9b32ea5f7056bc3.ppt
- Количество слайдов: 21
 The 38 th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Convicting Exploitable Software Vulnerabilities: An Efficient Input Provenance Based Approach Zhiqiang Lin Xiangyu Zhang, Dongyan Xu Purdue University June 27 th, 2008
The 38 th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Convicting Exploitable Software Vulnerabilities: An Efficient Input Provenance Based Approach Zhiqiang Lin Xiangyu Zhang, Dongyan Xu Purdue University June 27 th, 2008
 Motivation Internet Worms (Code. Red, Slammer) Vulnerability In Software FC Accidental Breaches in Security Do. S Viruses, Trojan Horses, User Bots (Botnet) Do. S Denial of Service (Do. S)
Motivation Internet Worms (Code. Red, Slammer) Vulnerability In Software FC Accidental Breaches in Security Do. S Viruses, Trojan Horses, User Bots (Botnet) Do. S Denial of Service (Do. S)
 Related Work q Dynamic analysis Q Program shepherding (V. Kiriansky et al. ) Taint. Check (J. Newsome et al. ) Control Flow Integrity (M. Abadi et al. ) Data Flow Integrity (M. Castro et al. )… Q Run-time overhead, and waiting for attack q Static analysis Q BOON (D. Wagner et al. ), Splint (D. Larochelle et al. ), Archer (Y. Xie et al. ), RATS, Flawfinder Q False positive q Recent automated multi-path exploration Q DART (P. Godefroid et al. ), Cute (K. Sen et al. ), EXE (C. Cadar et al. ), SAGE (P. Godefroid et al. ) Q Low Efficiency
Related Work q Dynamic analysis Q Program shepherding (V. Kiriansky et al. ) Taint. Check (J. Newsome et al. ) Control Flow Integrity (M. Abadi et al. ) Data Flow Integrity (M. Castro et al. )… Q Run-time overhead, and waiting for attack q Static analysis Q BOON (D. Wagner et al. ), Splint (D. Larochelle et al. ), Archer (Y. Xie et al. ), RATS, Flawfinder Q False positive q Recent automated multi-path exploration Q DART (P. Godefroid et al. ), Cute (K. Sen et al. ), EXE (C. Cadar et al. ), SAGE (P. Godefroid et al. ) Q Low Efficiency
 Problem Statement and Our Technique q How to more efficiently discover/convict software vulnerability q An Efficient Input Provenance Based Approach Q Conservative static analysis => Suspect Q Dynamic analysis => Convicting the suspect and pruning false positives v Randomly mutation is avoided v No symbolic execution (can handle long execution) q Key idea Q Data lineage tracing (Input Provenance)
Problem Statement and Our Technique q How to more efficiently discover/convict software vulnerability q An Efficient Input Provenance Based Approach Q Conservative static analysis => Suspect Q Dynamic analysis => Convicting the suspect and pruning false positives v Randomly mutation is avoided v No symbolic execution (can handle long execution) q Key idea Q Data lineage tracing (Input Provenance)
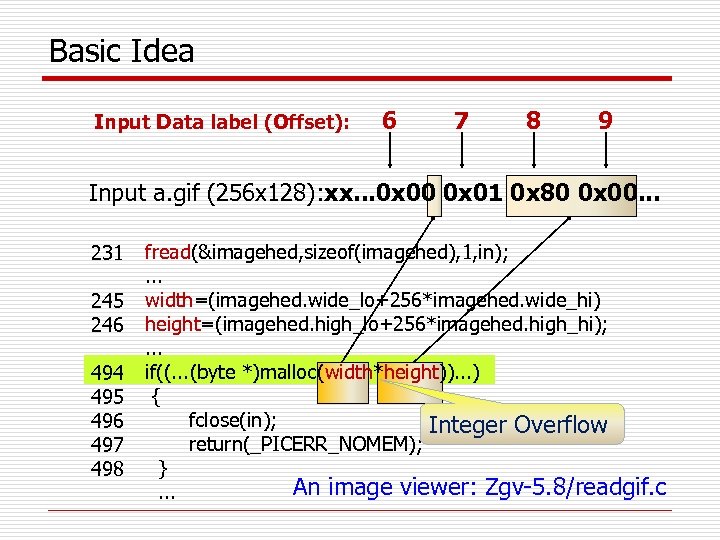 Basic Idea Input Data label (Offset): 6 7 8 9 Input a. gif (256 x 128): xx. . . 0 x 00 0 x 01 0 x 80 0 x 00. . . 231 245 246 494 495 496 497 498 fread(&imagehed, sizeof(imagehed), 1, in); . . . width=(imagehed. wide_lo+256*imagehed. wide_hi) height=(imagehed. high_lo+256*imagehed. high_hi); . . . if((. . . (byte *)malloc(width*height)). . . ) { fclose(in); Integer Overflow return(_PICERR_NOMEM); } An image viewer: Zgv-5. 8/readgif. c. . .
Basic Idea Input Data label (Offset): 6 7 8 9 Input a. gif (256 x 128): xx. . . 0 x 00 0 x 01 0 x 80 0 x 00. . . 231 245 246 494 495 496 497 498 fread(&imagehed, sizeof(imagehed), 1, in); . . . width=(imagehed. wide_lo+256*imagehed. wide_hi) height=(imagehed. high_lo+256*imagehed. high_hi); . . . if((. . . (byte *)malloc(width*height)). . . ) { fclose(in); Integer Overflow return(_PICERR_NOMEM); } An image viewer: Zgv-5. 8/readgif. c. . .
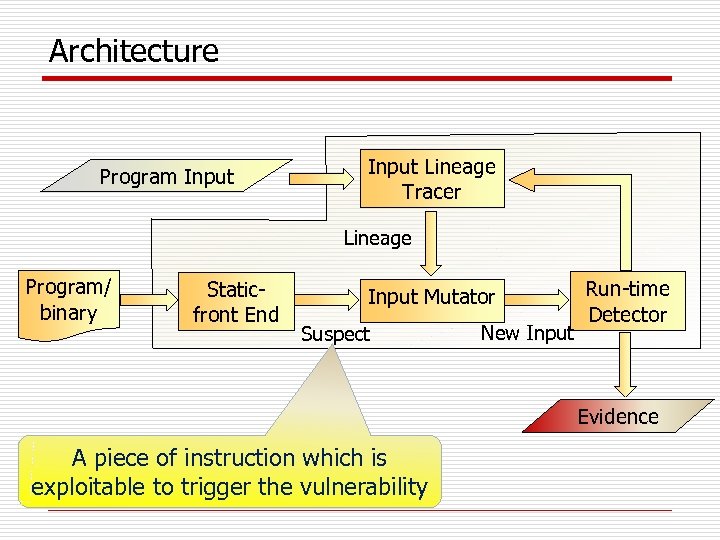 Architecture Program Input Lineage Tracer Lineage Program/ binary Staticfront End Input Mutator Suspect New Input Run-time Detector Evidence A piece of instruction which is exploitable to trigger the vulnerability
Architecture Program Input Lineage Tracer Lineage Program/ binary Staticfront End Input Mutator Suspect New Input Run-time Detector Evidence A piece of instruction which is exploitable to trigger the vulnerability
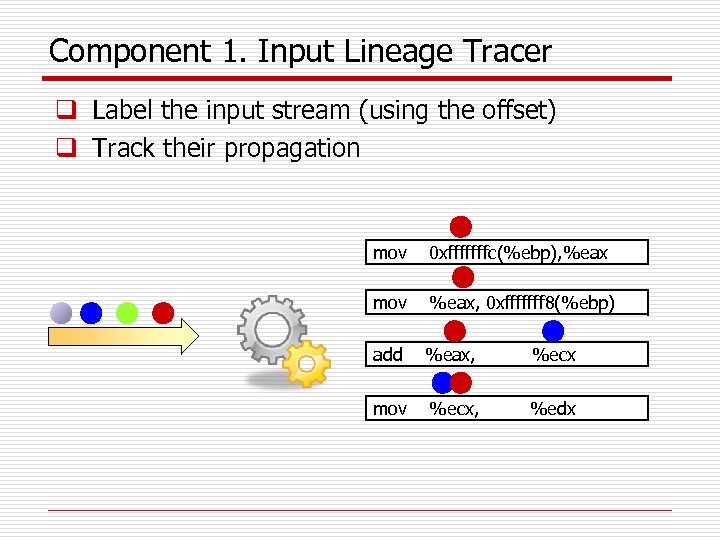 Component 1. Input Lineage Tracer q Label the input stream (using the offset) q Track their propagation mov 0 xfffffffc(%ebp), %eax mov %eax, 0 xfffffff 8(%ebp) add %eax, %ecx mov %ecx, %edx
Component 1. Input Lineage Tracer q Label the input stream (using the offset) q Track their propagation mov 0 xfffffffc(%ebp), %eax mov %eax, 0 xfffffff 8(%ebp) add %eax, %ecx mov %ecx, %edx
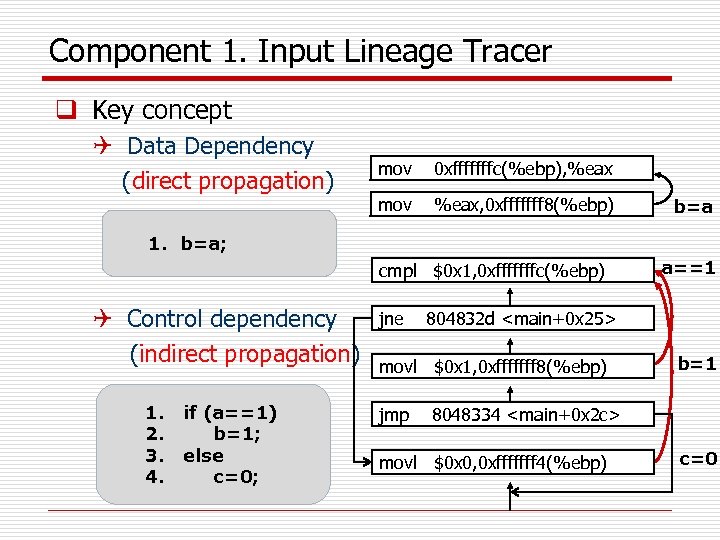 Component 1. Input Lineage Tracer q Key concept Q Data Dependency (direct propagation) mov 0 xfffffffc(%ebp), %eax mov %eax, 0 xfffffff 8(%ebp) b=a 1. b=a; cmpl $0 x 1, 0 xfffffffc(%ebp) Q Control dependency (indirect propagation) 1. 2. 3. 4. if (a==1) b=1; else c=0; jne 804832 d
Component 1. Input Lineage Tracer q Key concept Q Data Dependency (direct propagation) mov 0 xfffffffc(%ebp), %eax mov %eax, 0 xfffffff 8(%ebp) b=a 1. b=a; cmpl $0 x 1, 0 xfffffffc(%ebp) Q Control dependency (indirect propagation) 1. 2. 3. 4. if (a==1) b=1; else c=0; jne 804832 d
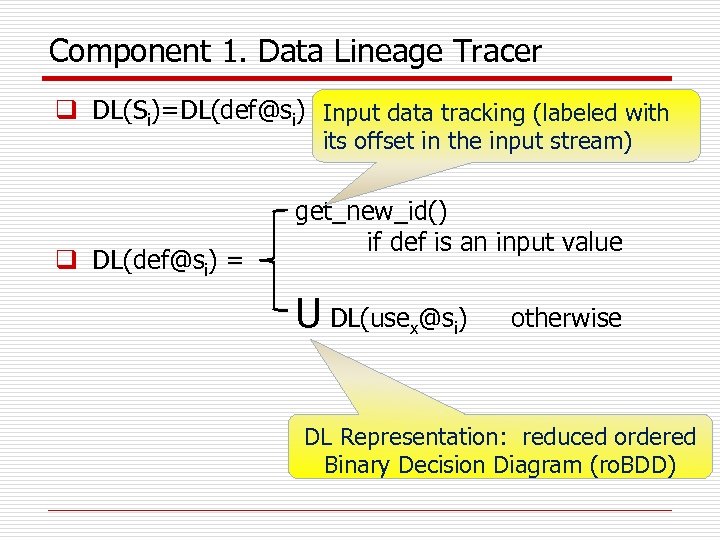 Component 1. Data Lineage Tracer q DL(Si)=DL(def@si) Input data tracking (labeled with its offset in the input stream) q DL(def@si) = get_new_id() if def is an input value U DL(usex@si) otherwise DL Representation: reduced ordered Binary Decision Diagram (ro. BDD)
Component 1. Data Lineage Tracer q DL(Si)=DL(def@si) Input data tracking (labeled with its offset in the input stream) q DL(def@si) = get_new_id() if def is an input value U DL(usex@si) otherwise DL Representation: reduced ordered Binary Decision Diagram (ro. BDD)
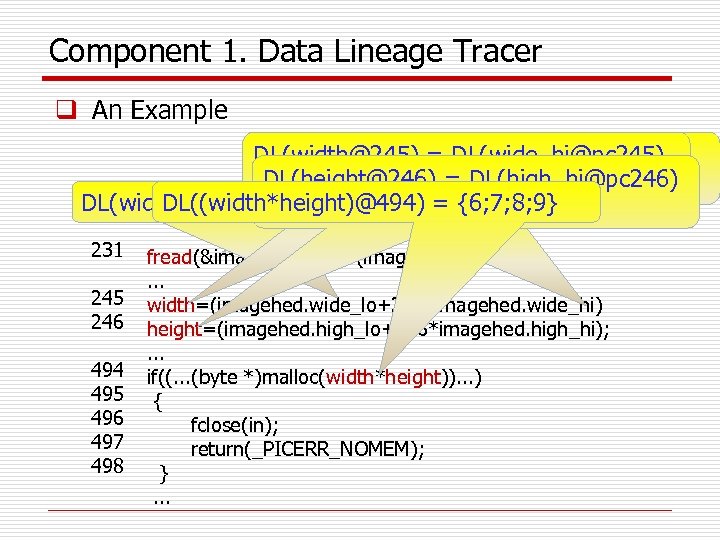 Component 1. Data Lineage Tracer q An Example DL(width@245) = DL(wide_hi@pc 245) READ (buf, size, . . . ), 0<= i < size , buf[i], DL(height@246) = get_new_id() U DL(wide_lo@pc 245) = {6; 7} DL(buf[i]@pc 231)= DL(high_hi@pc 246) DL(wide_hi@pc 245)=DL(buf[7]@pc 231) = {6} DL(wide_lo@pc 245)= DL(buf[6]@pc 231)= {7} DL((width*height)@494) = {6; 7; 8; 9} 9} U DL(high_lo@pc 246) = {8; 231 245 246 494 495 496 497 498 fread(&imagehed, sizeof(imagehed), 1, in); . . . width=(imagehed. wide_lo+256*imagehed. wide_hi) height=(imagehed. high_lo+256*imagehed. high_hi); . . . if((. . . (byte *)malloc(width*height)). . . ) { fclose(in); return(_PICERR_NOMEM); }. . .
Component 1. Data Lineage Tracer q An Example DL(width@245) = DL(wide_hi@pc 245) READ (buf, size, . . . ), 0<= i < size , buf[i], DL(height@246) = get_new_id() U DL(wide_lo@pc 245) = {6; 7} DL(buf[i]@pc 231)= DL(high_hi@pc 246) DL(wide_hi@pc 245)=DL(buf[7]@pc 231) = {6} DL(wide_lo@pc 245)= DL(buf[6]@pc 231)= {7} DL((width*height)@494) = {6; 7; 8; 9} 9} U DL(high_lo@pc 246) = {8; 231 245 246 494 495 496 497 498 fread(&imagehed, sizeof(imagehed), 1, in); . . . width=(imagehed. wide_lo+256*imagehed. wide_hi) height=(imagehed. high_lo+256*imagehed. high_hi); . . . if((. . . (byte *)malloc(width*height)). . . ) { fclose(in); return(_PICERR_NOMEM); }. . .
 Component 2. Input Mutator Program Input Data Lineage Suspect Evidence Heuristics#1: Buffer overflow mutation (double buffer size …) Heuristics#2: Format string mutation (replace %s in format string argument) Heuristics#3: Integer overflow mutation (Boundary integer value: 0 xffff, 0, 0 x 0 fffffff) …
Component 2. Input Mutator Program Input Data Lineage Suspect Evidence Heuristics#1: Buffer overflow mutation (double buffer size …) Heuristics#2: Format string mutation (replace %s in format string argument) Heuristics#3: Integer overflow mutation (Boundary integer value: 0 xffff, 0, 0 x 0 fffffff) …
 Implementation q Diablo: Q Control flow graph Q Statically generate Control dependency to facilitate Valgrind instrumentation Q http: //diablo. elis. ugent. be/ q Valgrind: Q Lineage tracing Q http: //valgrind. org/ Q Ro. BDD (Reduced ordered Binary Decision Diagram) to represent the data lineage.
Implementation q Diablo: Q Control flow graph Q Statically generate Control dependency to facilitate Valgrind instrumentation Q http: //diablo. elis. ugent. be/ q Valgrind: Q Lineage tracing Q http: //valgrind. org/ Q Ro. BDD (Reduced ordered Binary Decision Diagram) to represent the data lineage.
 Evaluation - Effectiveness q Static Detector Q Known vulnerability v v v v v CVE-2001 -1413 CVE-2001 -1228 CVE-2002 -1496 CVE-2002 -1549 CVE-2000 -0573 CVE-2001 -0609 CVE-2005 -0226 CVE-2004 -0904 CVE-2006 -3082 (ncompress 4. 2. 4, SO) (gzip 1. 2. 4, SO) (Nullhttpd 0. 50, HO) (lhttpd 0. 1, SO) (wu-ftpd-2. 6. 0, Format String) (cfingerd-1. 4. 3, Format String) (ngircd-0. 8. 2, Format String) (xzgv-0. 8, IO & HO) (Gnu. PG 1. 4. 3, IO & HO) q RATS (Unknown) Q Make extension to catch: buffer overflow, integer overflow (ipgrab-0. 99, epstool-3. 3, dcraw-7. 94)
Evaluation - Effectiveness q Static Detector Q Known vulnerability v v v v v CVE-2001 -1413 CVE-2001 -1228 CVE-2002 -1496 CVE-2002 -1549 CVE-2000 -0573 CVE-2001 -0609 CVE-2005 -0226 CVE-2004 -0904 CVE-2006 -3082 (ncompress 4. 2. 4, SO) (gzip 1. 2. 4, SO) (Nullhttpd 0. 50, HO) (lhttpd 0. 1, SO) (wu-ftpd-2. 6. 0, Format String) (cfingerd-1. 4. 3, Format String) (ngircd-0. 8. 2, Format String) (xzgv-0. 8, IO & HO) (Gnu. PG 1. 4. 3, IO & HO) q RATS (Unknown) Q Make extension to catch: buffer overflow, integer overflow (ipgrab-0. 99, epstool-3. 3, dcraw-7. 94)
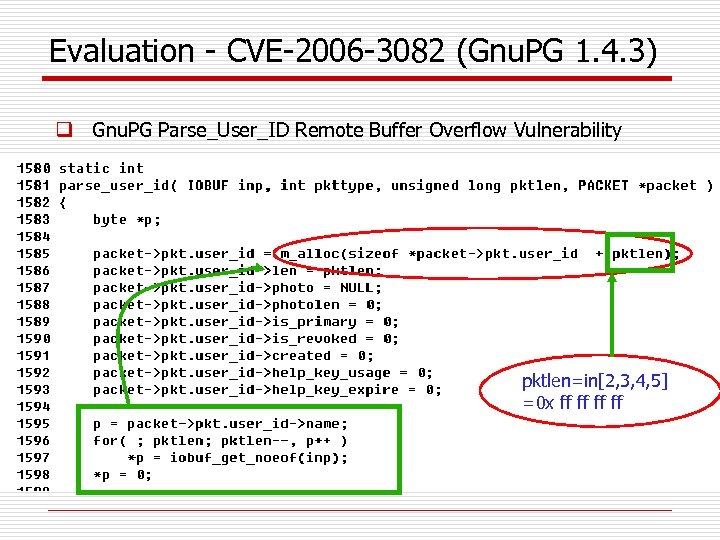 Evaluation - CVE-2006 -3082 (Gnu. PG 1. 4. 3) q Gnu. PG Parse_User_ID Remote Buffer Overflow Vulnerability pktlen=in[2, 3, 4, 5] =0 x ff ff
Evaluation - CVE-2006 -3082 (Gnu. PG 1. 4. 3) q Gnu. PG Parse_User_ID Remote Buffer Overflow Vulnerability pktlen=in[2, 3, 4, 5] =0 x ff ff
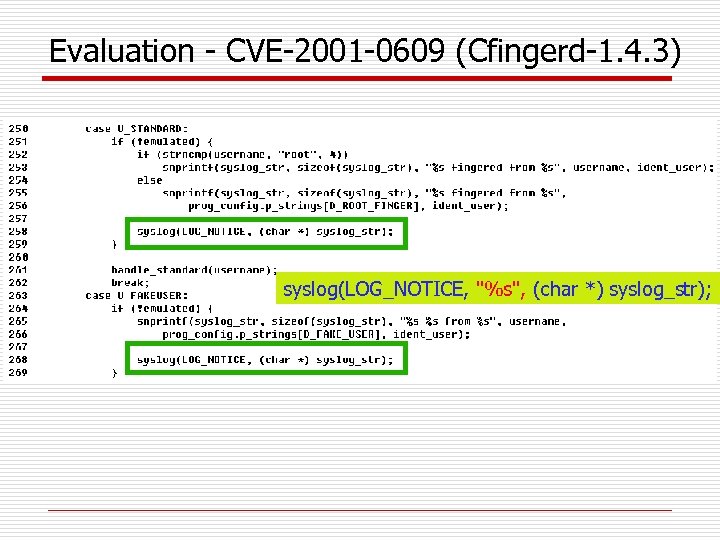 Evaluation - CVE-2001 -0609 (Cfingerd-1. 4. 3) syslog(LOG_NOTICE, "%s", (char *) syslog_str);
Evaluation - CVE-2001 -0609 (Cfingerd-1. 4. 3) syslog(LOG_NOTICE, "%s", (char *) syslog_str);
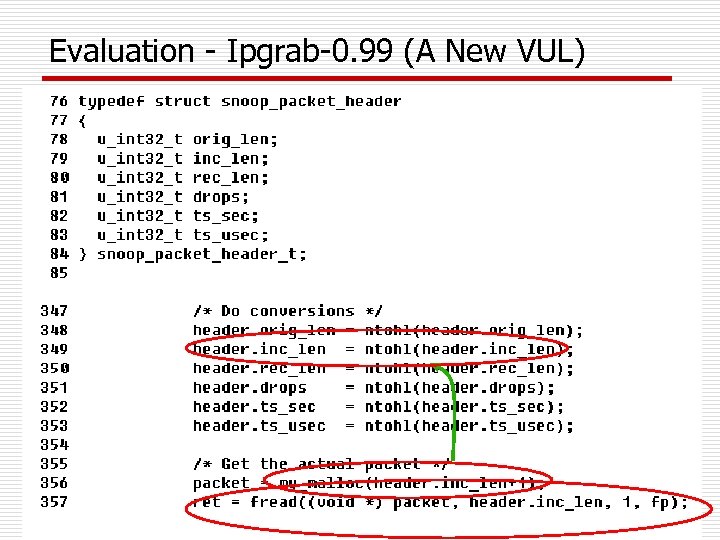 Evaluation - Ipgrab-0. 99 (A New VUL)
Evaluation - Ipgrab-0. 99 (A New VUL)
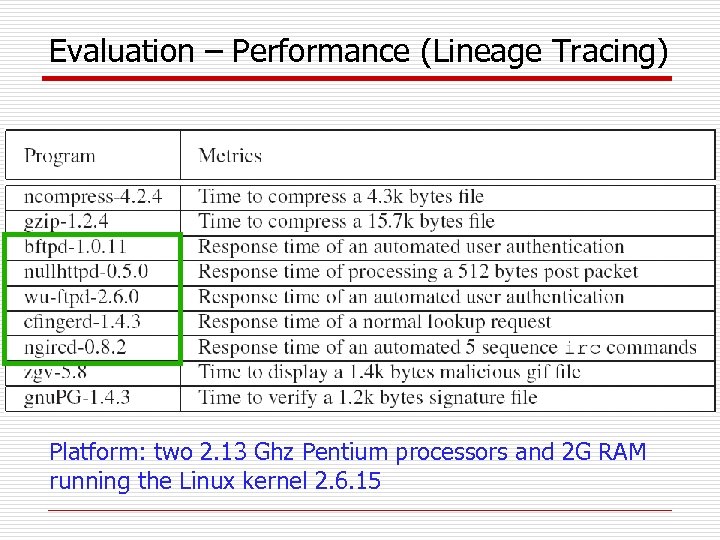 Evaluation – Performance (Lineage Tracing) Platform: two 2. 13 Ghz Pentium processors and 2 G RAM running the Linux kernel 2. 6. 15
Evaluation – Performance (Lineage Tracing) Platform: two 2. 13 Ghz Pentium processors and 2 G RAM running the Linux kernel 2. 6. 15
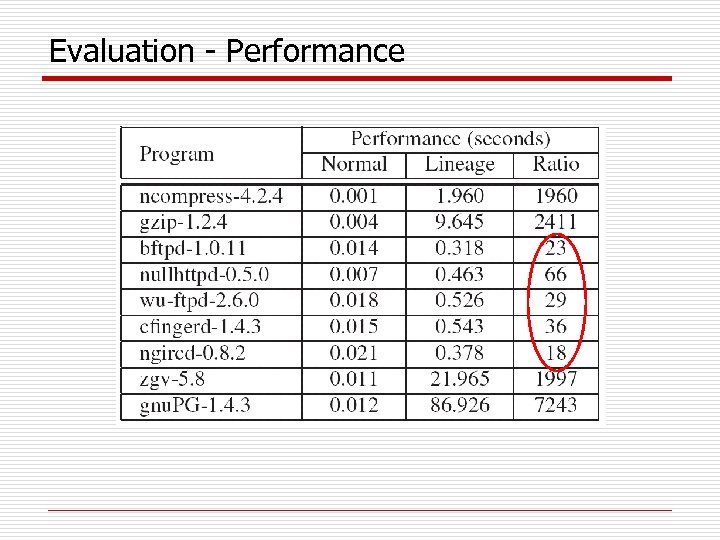 Evaluation - Performance
Evaluation - Performance
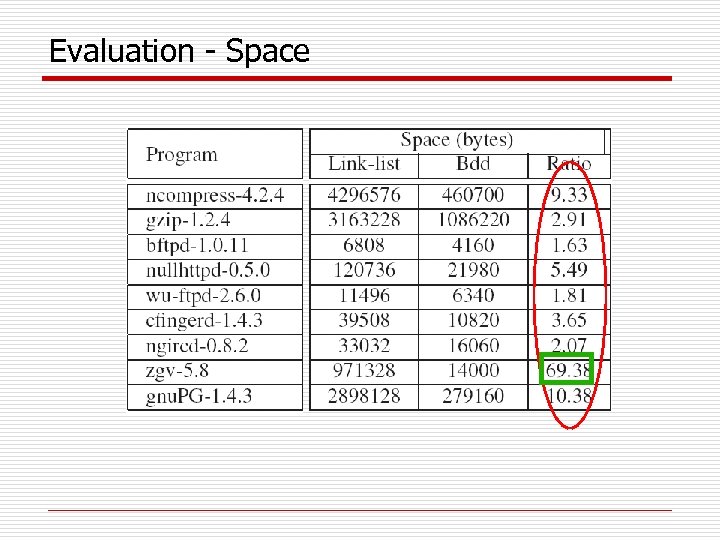 Evaluation - Space
Evaluation - Space
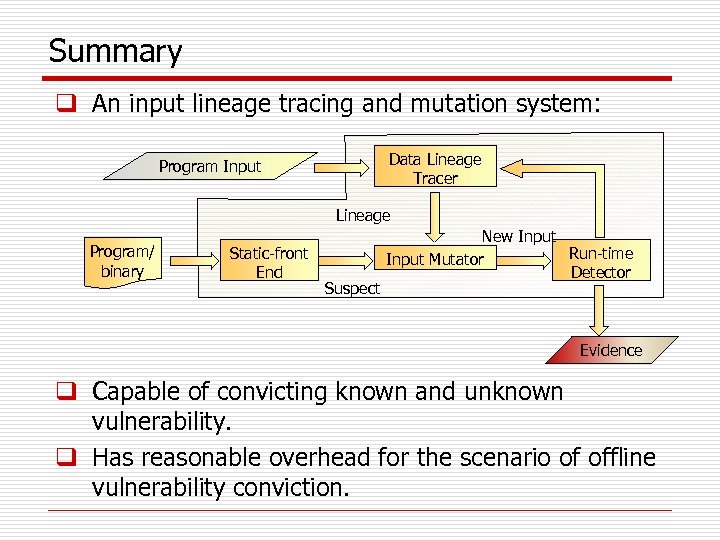 Summary q An input lineage tracing and mutation system: Data Lineage Tracer Program Input Lineage Program/ binary Static-front End Suspect New Input Run-time Input Mutator Detector Evidence q Capable of convicting known and unknown vulnerability. q Has reasonable overhead for the scenario of offline vulnerability conviction.
Summary q An input lineage tracing and mutation system: Data Lineage Tracer Program Input Lineage Program/ binary Static-front End Suspect New Input Run-time Input Mutator Detector Evidence q Capable of convicting known and unknown vulnerability. q Has reasonable overhead for the scenario of offline vulnerability conviction.
 Q&A Thank you For more information: {zlin, xyzhang, dxu}@cs. purdue. edu
Q&A Thank you For more information: {zlin, xyzhang, dxu}@cs. purdue. edu


