2c44ad8d2bb7630c7817be4748c1a5c5.ppt
- Количество слайдов: 28
 TERENA 12 th TF-EMC 2 meeting Japanese University PKI (UPKI) Update and Single Sign-On Trial Yasuo Okabe Kyoto University/ National Institute of Informatics Dec 4, 2008
TERENA 12 th TF-EMC 2 meeting Japanese University PKI (UPKI) Update and Single Sign-On Trial Yasuo Okabe Kyoto University/ National Institute of Informatics Dec 4, 2008
 OUTLINE 1. Overview of UPKI 2. Server Certificate Pilot Project 3. Single Sing-On Trial 4. Shibboleth using PKI Authentication 2
OUTLINE 1. Overview of UPKI 2. Server Certificate Pilot Project 3. Single Sing-On Trial 4. Shibboleth using PKI Authentication 2
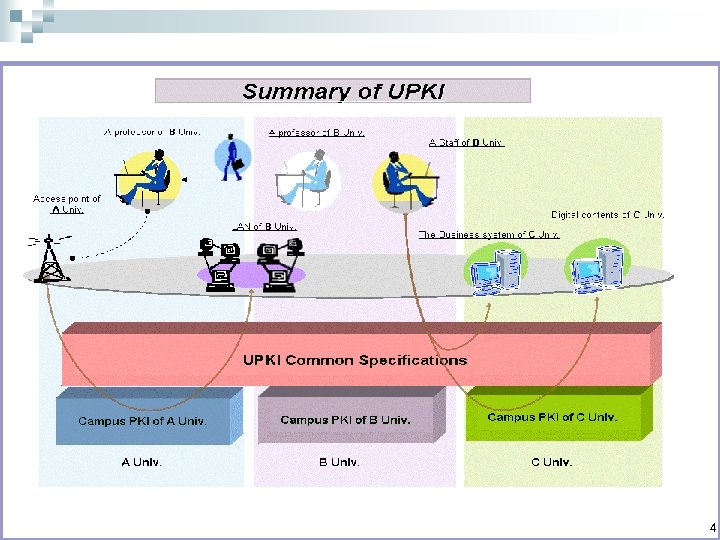
 What is UPKI? n n We are undertaking the construction of University Public Key Infrastructure (UPKI), which is intended to achieve an inter-university cooperation that makes use of educational and research computing systems, digital contents, networks, and business systems at almost 800 universities and other institutions in Japan, in safe, convenient, and effective ways. We are promoting an Inter-university authentication federation by developing UPKI common specifications, and by developing applications using the PKI. 3
What is UPKI? n n We are undertaking the construction of University Public Key Infrastructure (UPKI), which is intended to achieve an inter-university cooperation that makes use of educational and research computing systems, digital contents, networks, and business systems at almost 800 universities and other institutions in Japan, in safe, convenient, and effective ways. We are promoting an Inter-university authentication federation by developing UPKI common specifications, and by developing applications using the PKI. 3
 1. Overview of UPKI 4
1. Overview of UPKI 4
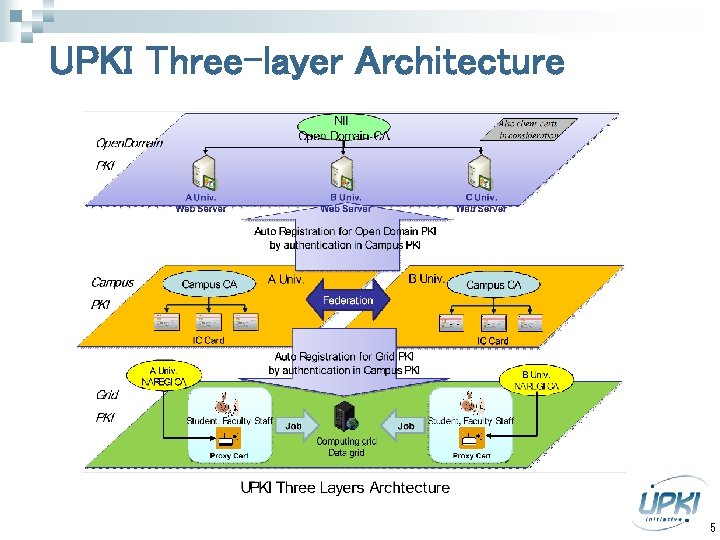 UPKI Three-layer Architecture 5
UPKI Three-layer Architecture 5
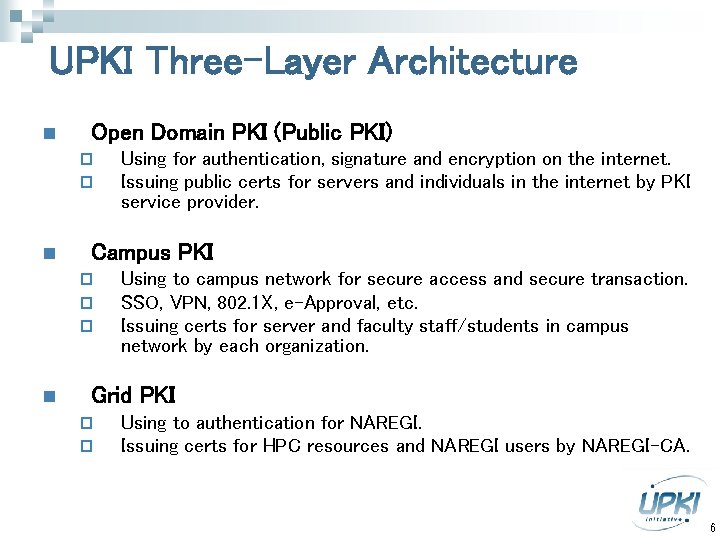 UPKI Three-Layer Architecture n Open Domain PKI (Public PKI) p p n Campus PKI p p p n Using for authentication, signature and encryption on the internet. Issuing public certs for servers and individuals in the internet by PKI service provider. Using to campus network for secure access and secure transaction. SSO, VPN, 802. 1 X, e-Approval, etc. Issuing certs for server and faculty staff/students in campus network by each organization. Grid PKI p p Using to authentication for NAREGI. Issuing certs for HPC resources and NAREGI users by NAREGI-CA. 6
UPKI Three-Layer Architecture n Open Domain PKI (Public PKI) p p n Campus PKI p p p n Using for authentication, signature and encryption on the internet. Issuing public certs for servers and individuals in the internet by PKI service provider. Using to campus network for secure access and secure transaction. SSO, VPN, 802. 1 X, e-Approval, etc. Issuing certs for server and faculty staff/students in campus network by each organization. Grid PKI p p Using to authentication for NAREGI. Issuing certs for HPC resources and NAREGI users by NAREGI-CA. 6
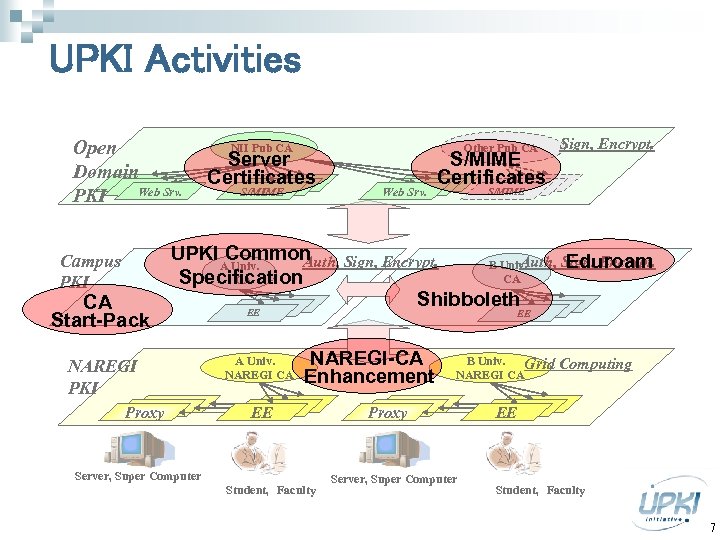 UPKI Activities Open Domainサーバ Web Web Srv. PKI Campus PKI CA Start-Pack NII Pub CA Server Certificates S/MIME Other Pub CA S/MIME Certificates Webサーバ S/MIME Web Srv. Sign, Encrypt. S/MIME UPKI Common Auth, Sign, Encrypt. Eduroam B Univ. A Univ. CA Specification CA Shibboleth 学内用 学内用 EE EE A Univ. NAREGI CA NAREGI PKI Proxy EEEE NAREGI-CA Enhancement EE Server, Super Computer Student, Faculty B Univ. Grid NAREGI CA Proxy Server, Super Computer EEEE Computing EE Student, Faculty 7
UPKI Activities Open Domainサーバ Web Web Srv. PKI Campus PKI CA Start-Pack NII Pub CA Server Certificates S/MIME Other Pub CA S/MIME Certificates Webサーバ S/MIME Web Srv. Sign, Encrypt. S/MIME UPKI Common Auth, Sign, Encrypt. Eduroam B Univ. A Univ. CA Specification CA Shibboleth 学内用 学内用 EE EE A Univ. NAREGI CA NAREGI PKI Proxy EEEE NAREGI-CA Enhancement EE Server, Super Computer Student, Faculty B Univ. Grid NAREGI CA Proxy Server, Super Computer EEEE Computing EE Student, Faculty 7
 Server Certificate Pilot project n n NII is addressing the operation of "Server Certificate Pilot Project" for the promotion of public server certificates and the evaluation of registration scheme in Higher-Education institutions since May 2007. At this project, NII is operating "NII Open Domain CA" subordinated by Public Root CA, for issuing public server certificates to High. Ed institutions. 8
Server Certificate Pilot project n n NII is addressing the operation of "Server Certificate Pilot Project" for the promotion of public server certificates and the evaluation of registration scheme in Higher-Education institutions since May 2007. At this project, NII is operating "NII Open Domain CA" subordinated by Public Root CA, for issuing public server certificates to High. Ed institutions. 8
 Quick view of Pilot project (cont’d) n Challenges p p p n Optimization of RA operation for High-Ed Customization of local operation in each institution Automization of RA operation by using Campus PKI certs as a credential (planning stage) Expected outcomes p p Best practice of local operation optimized for High-Ed Tips for server certificate installation (for niche implementation) Tips for local operations improvement in institutions Demand of stimulation for S/MIME (using for Local Operators) 9
Quick view of Pilot project (cont’d) n Challenges p p p n Optimization of RA operation for High-Ed Customization of local operation in each institution Automization of RA operation by using Campus PKI certs as a credential (planning stage) Expected outcomes p p Best practice of local operation optimized for High-Ed Tips for server certificate installation (for niche implementation) Tips for local operations improvement in institutions Demand of stimulation for S/MIME (using for Local Operators) 9
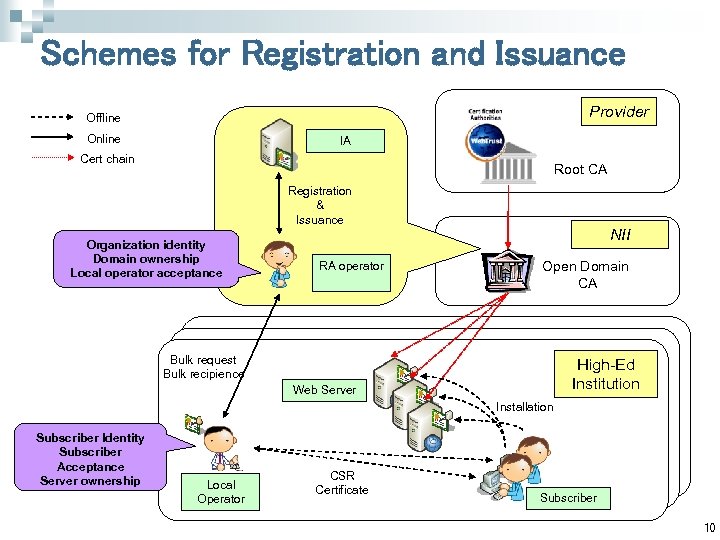 Schemes for Registration and Issuance Provider Offline Online IA Cert chain Root CA Registration & Issuance Organization identity Domain ownership Local operator acceptance RA operator NII Open Domain CA Bulk request Bulk recipience High-Ed Institution Web Server Installation Subscriber Identity Subscriber Acceptance Server ownership Local Operator CSR Certificate Subscriber 10
Schemes for Registration and Issuance Provider Offline Online IA Cert chain Root CA Registration & Issuance Organization identity Domain ownership Local operator acceptance RA operator NII Open Domain CA Bulk request Bulk recipience High-Ed Institution Web Server Installation Subscriber Identity Subscriber Acceptance Server ownership Local Operator CSR Certificate Subscriber 10
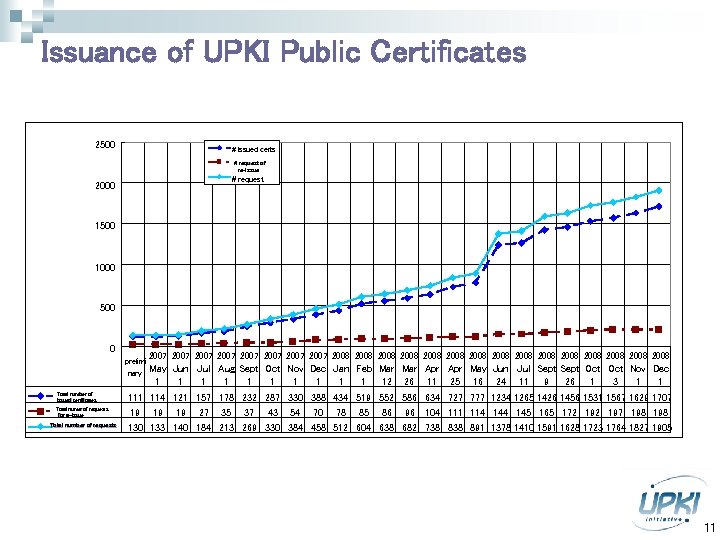 Issuance of UPKI Public Certificates 2500 # issued certs # request of re-issue # request 2000 1500 1000 500 0 prelimi nary Total number of issued certificates Total numer of requests for re-issue Total number of requests 2007 2007 2008 2008 2008 2008 May Jun Jul Aug Sept Oct Nov Dec Jan Feb Mar Apr May Jun Jul Sept Oct Nov Dec 1 1 12 26 11 25 16 24 11 9 26 1 3 1 1 114 121 157 178 232 287 330 388 434 519 552 586 634 727 777 1234 1265 1426 1456 1531 1567 1629 1707 19 19 19 27 35 37 43 54 70 78 85 86 96 104 111 114 145 165 172 197 198 130 133 140 184 213 269 330 384 458 512 604 638 682 738 891 1378 1410 1591 1628 1723 1764 1827 1905 11
Issuance of UPKI Public Certificates 2500 # issued certs # request of re-issue # request 2000 1500 1000 500 0 prelimi nary Total number of issued certificates Total numer of requests for re-issue Total number of requests 2007 2007 2008 2008 2008 2008 May Jun Jul Aug Sept Oct Nov Dec Jan Feb Mar Apr May Jun Jul Sept Oct Nov Dec 1 1 12 26 11 25 16 24 11 9 26 1 3 1 1 114 121 157 178 232 287 330 388 434 519 552 586 634 727 777 1234 1265 1426 1456 1531 1567 1629 1707 19 19 19 27 35 37 43 54 70 78 85 86 96 104 111 114 145 165 172 197 198 130 133 140 184 213 269 330 384 458 512 604 638 682 738 891 1378 1410 1591 1628 1723 1764 1827 1905 11
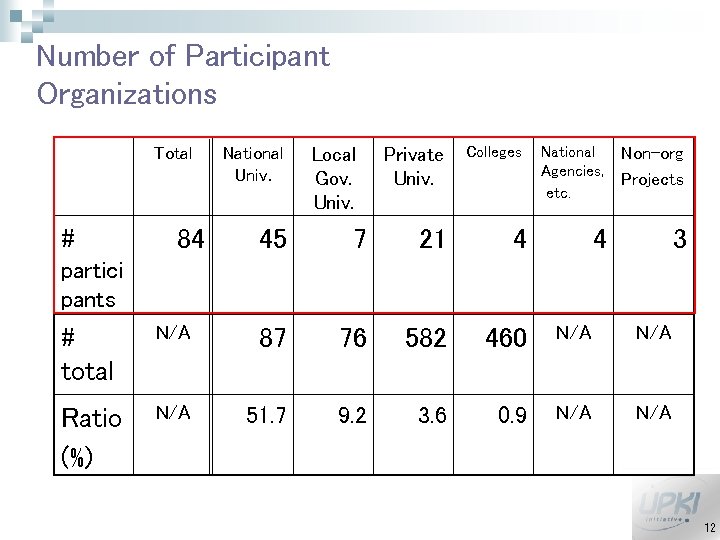 Number of Participant Organizations Total # 84 National Univ. Local Gov. Univ. Private Univ. Colleges National Agencies, etc. Non-org Projects 4 3 45 7 21 4 partici pants # total N/A 87 76 582 460 N/A Ratio (%) N/A 51. 7 9. 2 3. 6 0. 9 N/A 12
Number of Participant Organizations Total # 84 National Univ. Local Gov. Univ. Private Univ. Colleges National Agencies, etc. Non-org Projects 4 3 45 7 21 4 partici pants # total N/A 87 76 582 460 N/A Ratio (%) N/A 51. 7 9. 2 3. 6 0. 9 N/A 12
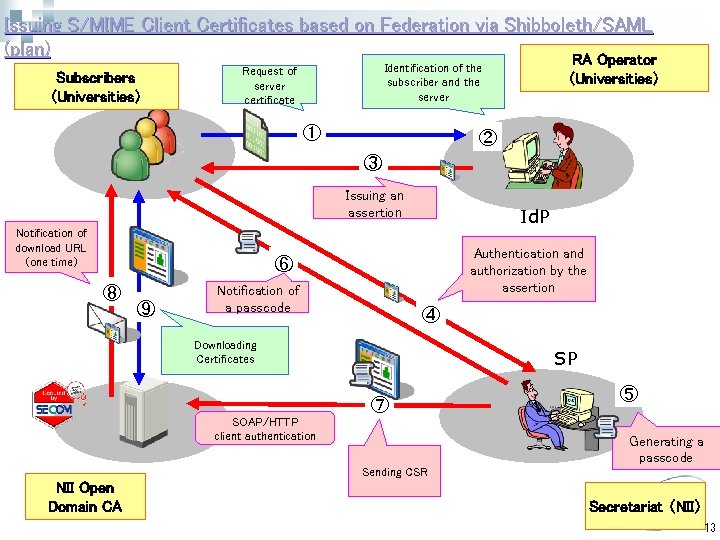 Issuing S/MIME Client Certificates based on Federation via Shibboleth/SAML (plan) RA Operator Subscribers (Universities) Identification of the subscriber and the server Request of server certificate ① (Universities) ② ③ Issuing an assertion Notification of download URL (one time) Id. P Authentication and authorization by the assertion ⑥ ⑧ ⑨ Notification of a passcode ④ Downloading Certificates SP ⑦ SOAP/HTTP client authentication ⑤ Generating a passcode Sending CSR NII Open Domain CA Secretariat (NII) 13
Issuing S/MIME Client Certificates based on Federation via Shibboleth/SAML (plan) RA Operator Subscribers (Universities) Identification of the subscriber and the server Request of server certificate ① (Universities) ② ③ Issuing an assertion Notification of download URL (one time) Id. P Authentication and authorization by the assertion ⑥ ⑧ ⑨ Notification of a passcode ④ Downloading Certificates SP ⑦ SOAP/HTTP client authentication ⑤ Generating a passcode Sending CSR NII Open Domain CA Secretariat (NII) 13
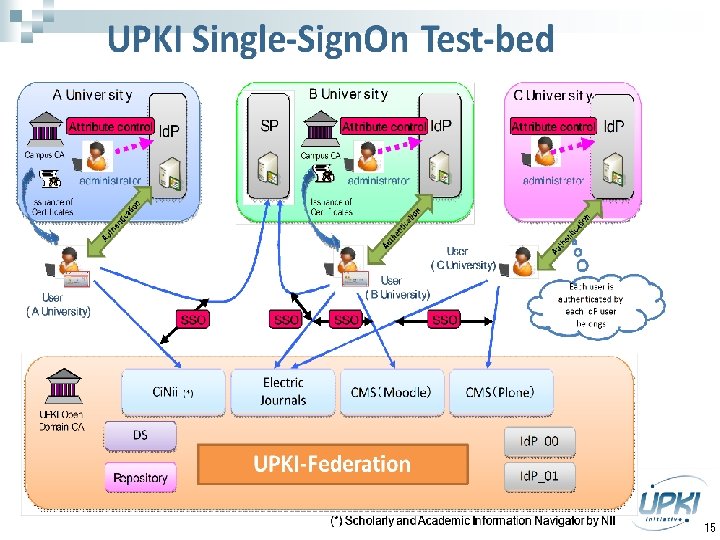
 UPKI Single Sign-On Testbed n n Leveraging PKI and Shibboleth (SAML) technologies, UPKI-Federation that enables secure Single Sign-On for inter-Universities services such as electronic journals is under development. The project is trial stage since Sept. 2008. 14
UPKI Single Sign-On Testbed n n Leveraging PKI and Shibboleth (SAML) technologies, UPKI-Federation that enables secure Single Sign-On for inter-Universities services such as electronic journals is under development. The project is trial stage since Sept. 2008. 14
 15
15
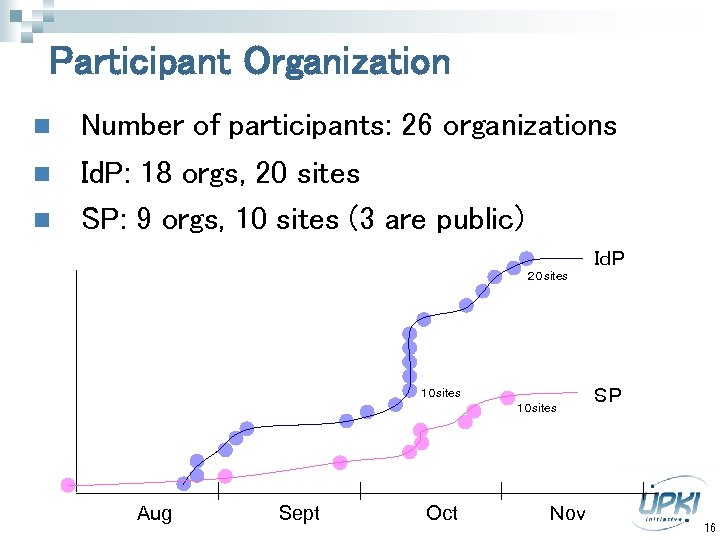 Participant Organization n Number of participants: 26 organizations Id. P: 18 orgs, 20 sites SP: 9 orgs, 10 sites (3 are public) IdP 20 sites 10 sites Aug Sept Oct Nov SP 16
Participant Organization n Number of participants: 26 organizations Id. P: 18 orgs, 20 sites SP: 9 orgs, 10 sites (3 are public) IdP 20 sites 10 sites Aug Sept Oct Nov SP 16
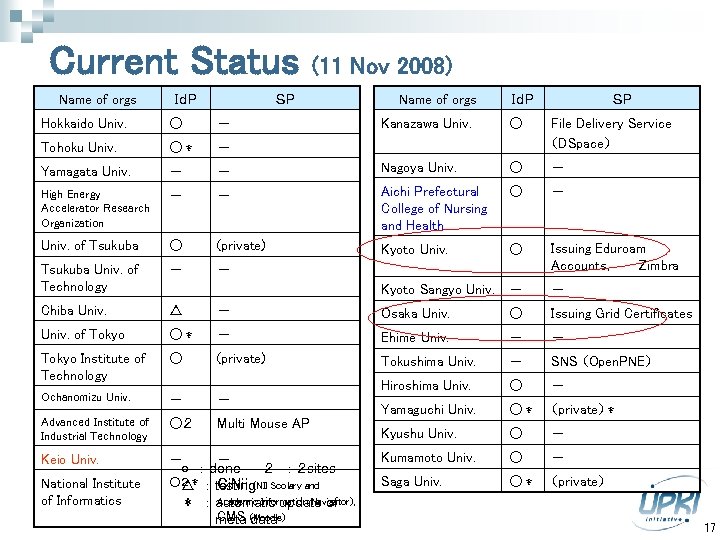 Current Status Name of orgs IdP (11 Nov 2008) SP Hokkaido Univ. ○ - Tohoku Univ. ○* - High Energy Accelerator Research Organization IdP - Yamagata Univ. Name of orgs SP Kanazawa Univ. ○ File Delivery Service (DSpace) - Nagoya Univ. ○ - - - Aichi Prefectural College of Nursing and Health ○ - Univ. of Tsukuba ○ (private) Kyoto Univ. ○ Tsukuba Univ. of Technology - - Issuing Eduroam Accounts, Zimbra Kyoto Sangyo Univ. - - Chiba Univ. △ - Osaka Univ. ○ Issuing Grid Certificates Univ. of Tokyo ○* - Ehime Univ. - - Tokyo Institute of Technology ○ (private) Tokushima Univ. - SNS (Open. PNE) Ochanomizu Univ. - - Hiroshima Univ. ○ - Advanced Institute of Industrial Technology ○2 Multi Mouse AP Yamaguchi Univ. ○* (private)* Kyushu Univ. ○ - Keio Univ. - - ○ : done 2 : 2 sites ○2* testing Scolary and △ : Ci. Nii (NII Academic Information Navigator) * : automatic update of , CMS data meta (Moodle) Kumamoto Univ. ○ - Saga Univ. ○* (private) National Institute of Informatics 17
Current Status Name of orgs IdP (11 Nov 2008) SP Hokkaido Univ. ○ - Tohoku Univ. ○* - High Energy Accelerator Research Organization IdP - Yamagata Univ. Name of orgs SP Kanazawa Univ. ○ File Delivery Service (DSpace) - Nagoya Univ. ○ - - - Aichi Prefectural College of Nursing and Health ○ - Univ. of Tsukuba ○ (private) Kyoto Univ. ○ Tsukuba Univ. of Technology - - Issuing Eduroam Accounts, Zimbra Kyoto Sangyo Univ. - - Chiba Univ. △ - Osaka Univ. ○ Issuing Grid Certificates Univ. of Tokyo ○* - Ehime Univ. - - Tokyo Institute of Technology ○ (private) Tokushima Univ. - SNS (Open. PNE) Ochanomizu Univ. - - Hiroshima Univ. ○ - Advanced Institute of Industrial Technology ○2 Multi Mouse AP Yamaguchi Univ. ○* (private)* Kyushu Univ. ○ - Keio Univ. - - ○ : done 2 : 2 sites ○2* testing Scolary and △ : Ci. Nii (NII Academic Information Navigator) * : automatic update of , CMS data meta (Moodle) Kumamoto Univ. ○ - Saga Univ. ○* (private) National Institute of Informatics 17
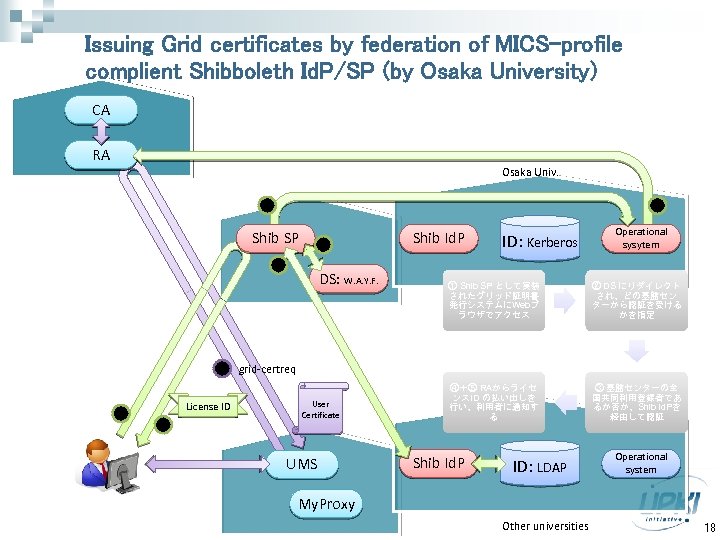 Issuing Grid certificates by federation of MICS-profile complient Shibboleth Id. P/SP (by Osaka University) CA RA Osaka Univ. 4 5 Shib SP 2 3 7 1 License ID 6 DS: W. A. Y. F. Shib Id. P ID: Kerberos Operational sysytem ① Shib SP として実装 されたグリッド証明書 発行システムにWebブ ラウザでアクセス ② DS にリダイレクト され、どの基盤セン ターから認証を受ける かを指定 ④+⑤ RAからライセ ンスID の払い出しを 行い、利用者に通知す る ③ 基盤センターの全 国共同利用登録者であ るか否か、Shib Id. Pを 経由して認証 grid-certreq User Certificate UMS Shib Id. P ID: LDAP Operational system My. Proxy Other universities 18
Issuing Grid certificates by federation of MICS-profile complient Shibboleth Id. P/SP (by Osaka University) CA RA Osaka Univ. 4 5 Shib SP 2 3 7 1 License ID 6 DS: W. A. Y. F. Shib Id. P ID: Kerberos Operational sysytem ① Shib SP として実装 されたグリッド証明書 発行システムにWebブ ラウザでアクセス ② DS にリダイレクト され、どの基盤セン ターから認証を受ける かを指定 ④+⑤ RAからライセ ンスID の払い出しを 行い、利用者に通知す る ③ 基盤センターの全 国共同利用登録者であ るか否か、Shib Id. Pを 経由して認証 grid-certreq User Certificate UMS Shib Id. P ID: LDAP Operational system My. Proxy Other universities 18
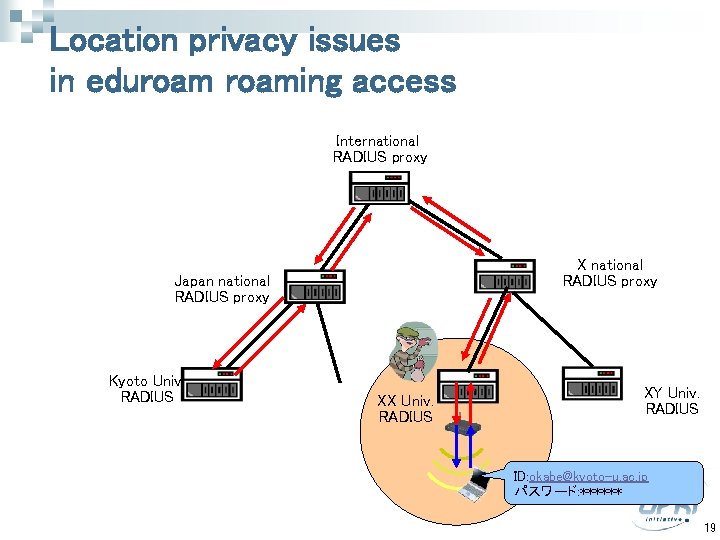 Location privacy issues in eduroaming access International RADIUS proxy X national RADIUS proxy Japan national RADIUS proxy Kyoto Univ. RADIUS XX Univ. RADIUS XY Univ. RADIUS ID: okabe@kyoto-u. ac. jp パスワード: ****** 19
Location privacy issues in eduroaming access International RADIUS proxy X national RADIUS proxy Japan national RADIUS proxy Kyoto Univ. RADIUS XX Univ. RADIUS XY Univ. RADIUS ID: okabe@kyoto-u. ac. jp パスワード: ****** 19
 Location Privacy issues in eduroaming access International RADIUS proxy X national RADIUS proxy Japan national RADIUS proxy Kyoto Univ. RADIUS XX Univ. RADIUS ID: okabe@kyoto-u. ac. jp パスワード: ****** XY Univ. RADIUS 20
Location Privacy issues in eduroaming access International RADIUS proxy X national RADIUS proxy Japan national RADIUS proxy Kyoto Univ. RADIUS XX Univ. RADIUS ID: okabe@kyoto-u. ac. jp パスワード: ****** XY Univ. RADIUS 20
 Solution n n Use of a tentative account with specified duration The ccount carries no privacy information like Who he is (or what is his e-mail address) p Which university he belongs p 21
Solution n n Use of a tentative account with specified duration The ccount carries no privacy information like Who he is (or what is his e-mail address) p Which university he belongs p 21
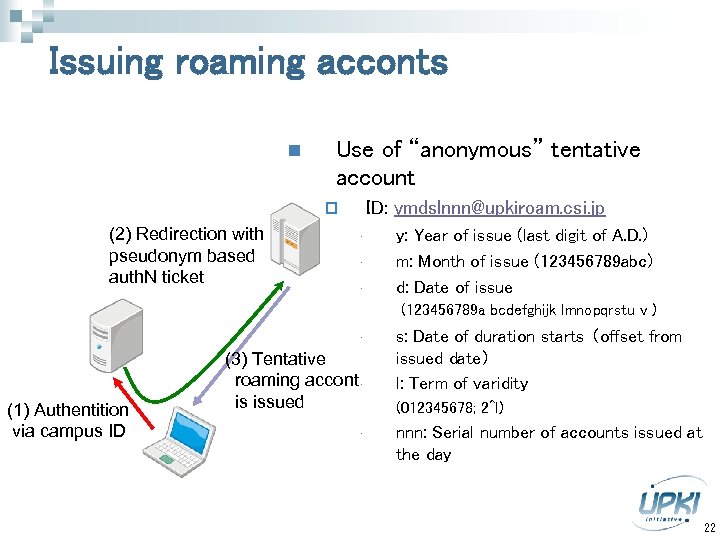 Issuing roaming acconts n Use of “anonymous” tentative account ID: ymdslnnn@upkiroam. csi. jp p (2) Redirection with pseudonym based auth. N ticket • • • y: Year of issue (last digit of A. D. ) m: Month of issue (123456789 abc) d: Date of issue (123456789 a bcdefghijk lmnopqrstu v ) • (1) Authentition via campus ID (3) Tentative roaming accont • is issued • s: Date of duration starts (offset from issued date) l: Term of varidity (012345678; 2^l) nnn: Serial number of accounts issued at the day 22
Issuing roaming acconts n Use of “anonymous” tentative account ID: ymdslnnn@upkiroam. csi. jp p (2) Redirection with pseudonym based auth. N ticket • • • y: Year of issue (last digit of A. D. ) m: Month of issue (123456789 abc) d: Date of issue (123456789 a bcdefghijk lmnopqrstu v ) • (1) Authentition via campus ID (3) Tentative roaming accont • is issued • s: Date of duration starts (offset from issued date) l: Term of varidity (012345678; 2^l) nnn: Serial number of accounts issued at the day 22
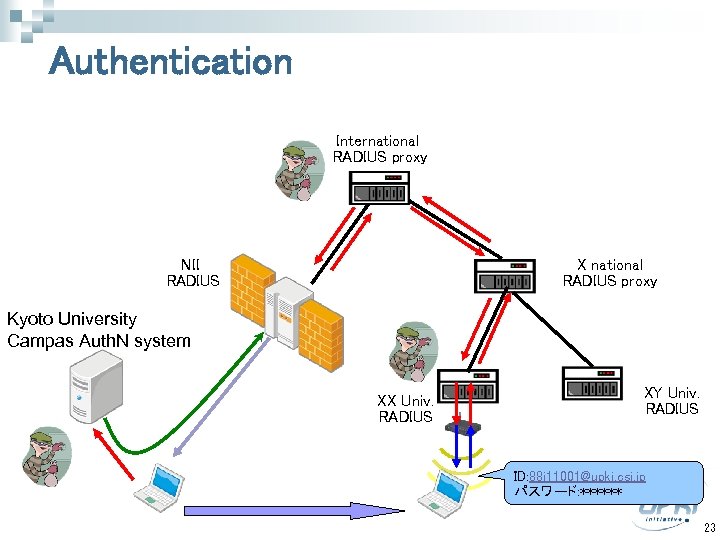 Authentication International RADIUS proxy NII RADIUS X national RADIUS proxy Kyoto University Campas Auth. N system XX Univ. RADIUS XY Univ. RADIUS ID: 88 j 11001@upki. csi. jp パスワード: ****** 23
Authentication International RADIUS proxy NII RADIUS X national RADIUS proxy Kyoto University Campas Auth. N system XX Univ. RADIUS XY Univ. RADIUS ID: 88 j 11001@upki. csi. jp パスワード: ****** 23
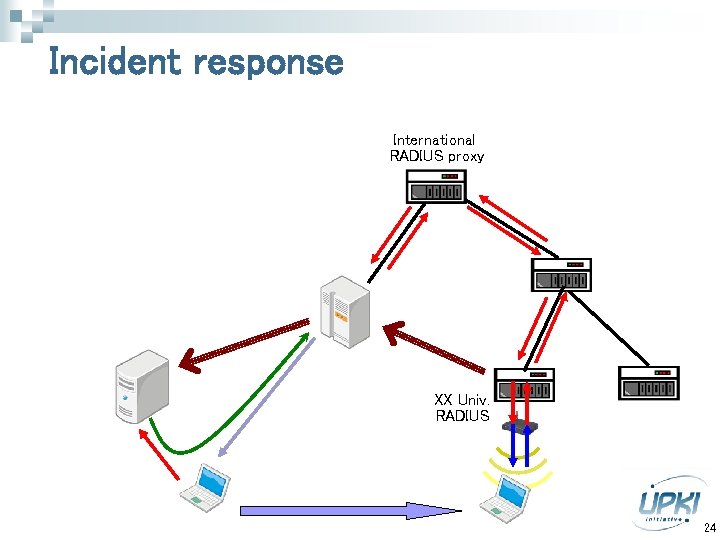 Incident response International RADIUS proxy XX Univ. RADIUS 24
Incident response International RADIUS proxy XX Univ. RADIUS 24
 Shibboleth using PKI authentication n Objectives; p n To design architecture for Japanese Academic Federation that is suitable for Japanese institutions base on UPKI infrastructure Challenges; To develop necessary functions to connect Shibboleth and UPKI infrastructure p To evaluate usability and operability of Shib-PKI architecture p 25
Shibboleth using PKI authentication n Objectives; p n To design architecture for Japanese Academic Federation that is suitable for Japanese institutions base on UPKI infrastructure Challenges; To develop necessary functions to connect Shibboleth and UPKI infrastructure p To evaluate usability and operability of Shib-PKI architecture p 25
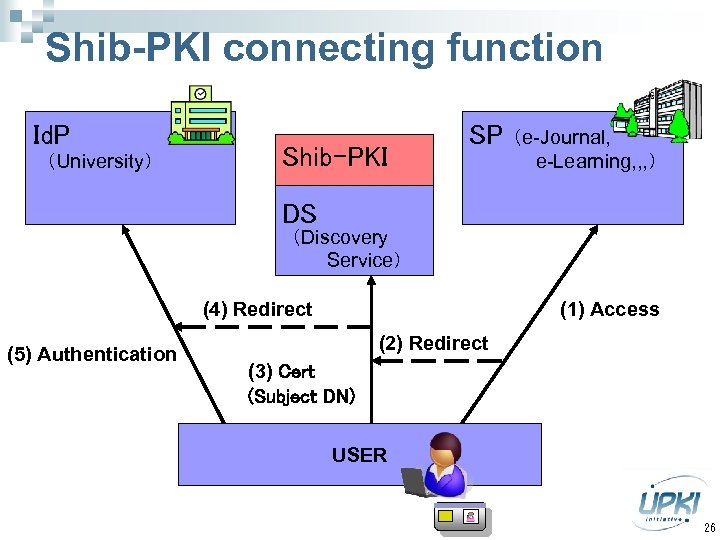 Shib-PKI connecting function Id. P (University) Shib-PKI SP (e-Journal, e-Learning, , , ) DS (Discovery Service) (4) Redirect (5) Authentication (1) Access (2) Redirect (3) Cert (Subject DN) USER 26
Shib-PKI connecting function Id. P (University) Shib-PKI SP (e-Journal, e-Learning, , , ) DS (Discovery Service) (4) Redirect (5) Authentication (1) Access (2) Redirect (3) Cert (Subject DN) USER 26
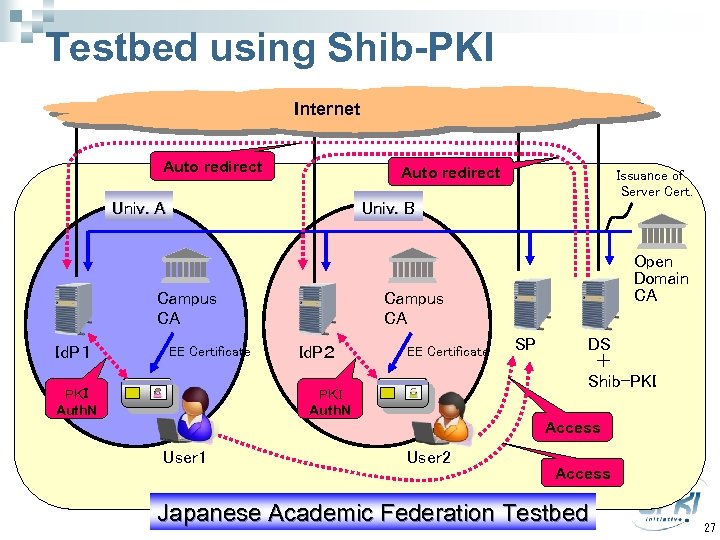 Testbed using Shib-PKI Internet Auto redirect Univ. A Univ. B Campus CA Id. P1 Issuance of Server Cert. EE Certificate PKI Auth. N Open Domain CA Campus CA Id. P2 EE Certificate PKI Auth. N SP DS + Shib-PKI Access User 1 User 2 Access Japanese Academic Federation Testbed 27
Testbed using Shib-PKI Internet Auto redirect Univ. A Univ. B Campus CA Id. P1 Issuance of Server Cert. EE Certificate PKI Auth. N Open Domain CA Campus CA Id. P2 EE Certificate PKI Auth. N SP DS + Shib-PKI Access User 1 User 2 Access Japanese Academic Federation Testbed 27
 Summary n UPKI: Japanese Academic Federation Ø Architecture design; Develop suitable architecture on UPKI infrastructure (three layers) taking institutions situations into consideration. Deployment of Shibboleth/SAML Ø Roadmap; FY 2007 Develop Shib-PKI and testbed FY 2008 Evaluate and develop architecture using testbed Small start with a few SP services FY 2009 Pilot Operation FY 2010~ Operational 28
Summary n UPKI: Japanese Academic Federation Ø Architecture design; Develop suitable architecture on UPKI infrastructure (three layers) taking institutions situations into consideration. Deployment of Shibboleth/SAML Ø Roadmap; FY 2007 Develop Shib-PKI and testbed FY 2008 Evaluate and develop architecture using testbed Small start with a few SP services FY 2009 Pilot Operation FY 2010~ Operational 28


