9647ad8f7ef3cebd9d03a9096f130e1e.ppt
- Количество слайдов: 66
 TELEMEDICINE
TELEMEDICINE
 Why Use Protocol Architecture? Data communications requires complex procedures Systems negotiate preparedness Applications negotiate preparedness Sender identifies data path/receiver Translation of file formats For all tasks to occur, high level of cooperation is required 2
Why Use Protocol Architecture? Data communications requires complex procedures Systems negotiate preparedness Applications negotiate preparedness Sender identifies data path/receiver Translation of file formats For all tasks to occur, high level of cooperation is required 2
 Modular Approach Breaks complex tasks into subtasks Each module handles specific subset of tasks Communication occurs between different modules on the same system between similar modules on different systems 3
Modular Approach Breaks complex tasks into subtasks Each module handles specific subset of tasks Communication occurs between different modules on the same system between similar modules on different systems 3
 Advantages of Modularity Easier application development Network can change without all programs being modified 4
Advantages of Modularity Easier application development Network can change without all programs being modified 4
 Three-Layer Model Distributed data communications involves three primary components: Networks Computers Applications Three corresponding layers Network access layer Transport layer Application layer 5
Three-Layer Model Distributed data communications involves three primary components: Networks Computers Applications Three corresponding layers Network access layer Transport layer Application layer 5
 Network Access Layer Concerned with exchange of data between computer and network Includes addressing, routing, prioritizing, etc Different networks require different software at this layer Example: X. 25 standard for network access procedures on packet-switching networks 6
Network Access Layer Concerned with exchange of data between computer and network Includes addressing, routing, prioritizing, etc Different networks require different software at this layer Example: X. 25 standard for network access procedures on packet-switching networks 6
 Transport Layer Concerned with reliable transfer of information between applications Independent of the nature of the application Includes aspects like flow control and error checking 7
Transport Layer Concerned with reliable transfer of information between applications Independent of the nature of the application Includes aspects like flow control and error checking 7
 Application Layer Logic needed to support various applications Each type of application (file transfer, remote access) requires different software on this layer 8
Application Layer Logic needed to support various applications Each type of application (file transfer, remote access) requires different software on this layer 8
 Addressing Each computer on a network requires a unique address on that network Each application requires a unique address within the computer to allow support for multiple applications (service access points, or SAP) 9
Addressing Each computer on a network requires a unique address on that network Each application requires a unique address within the computer to allow support for multiple applications (service access points, or SAP) 9
 Data Transmission Application layer creates data block Transport layer appends header to create PDU (protocol data unit) Destination SAP, Sequence #, Error. Detection Code Network layer appends another header Destination computer, facilities (e. g. “priority”) 10
Data Transmission Application layer creates data block Transport layer appends header to create PDU (protocol data unit) Destination SAP, Sequence #, Error. Detection Code Network layer appends another header Destination computer, facilities (e. g. “priority”) 10
 Simplified Architecture 11
Simplified Architecture 11
 Standardized Protocol Architectures Vendors like standards because they make their products more marketable Customers like standards because they enable products from different vendors to interoperate Two protocol standards are wellknown: TCP/IP: widely implemented OSI: less used, but widely known and still useful for modeling/conceptualizing 12
Standardized Protocol Architectures Vendors like standards because they make their products more marketable Customers like standards because they enable products from different vendors to interoperate Two protocol standards are wellknown: TCP/IP: widely implemented OSI: less used, but widely known and still useful for modeling/conceptualizing 12
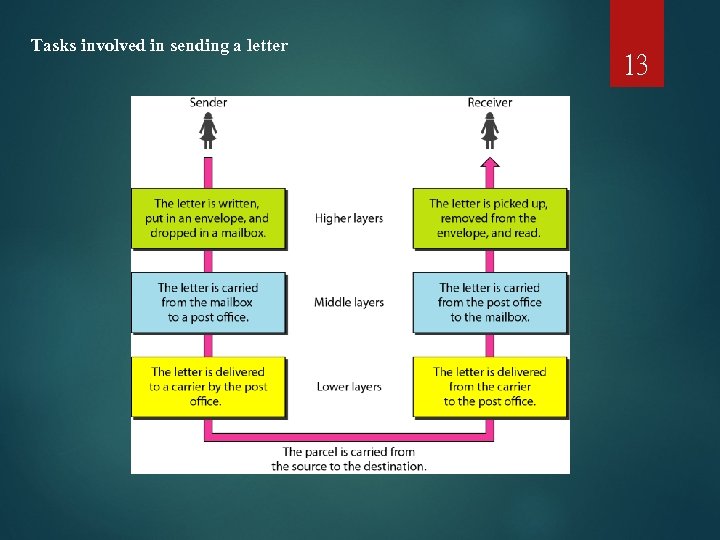 Tasks involved in sending a letter 13
Tasks involved in sending a letter 13
 Introduction OSI The Open System Interconnection Reference Model (OSI Reference Model or OSI Model) is an abstract description for layered communications and computer network protocol design. It divides network architecture into seven layers which, from top to bottom, are the Application, Presentation, Session, Transport, Network, Data Link, and Physical Layers. It is therefore often referred to as the OSI Seven Layer Model. 14
Introduction OSI The Open System Interconnection Reference Model (OSI Reference Model or OSI Model) is an abstract description for layered communications and computer network protocol design. It divides network architecture into seven layers which, from top to bottom, are the Application, Presentation, Session, Transport, Network, Data Link, and Physical Layers. It is therefore often referred to as the OSI Seven Layer Model. 14
 OSI History In 1978, the International Standars Organization (ISO) began to develop its OSI framework architecture. OSI has two major components: an abstract model of networking, called the Basic Reference Model or seven-layer model, and a set of specific protocols. 15
OSI History In 1978, the International Standars Organization (ISO) began to develop its OSI framework architecture. OSI has two major components: an abstract model of networking, called the Basic Reference Model or seven-layer model, and a set of specific protocols. 15
 OSI History The concept of a 7 layer model was provided by the work of Charles Bachman, then of Honeywell. Various aspects of OSI design evolved from experiences with the Advanced Research Projects Agency Network (ARPANET) and the fledgling Internet. 16
OSI History The concept of a 7 layer model was provided by the work of Charles Bachman, then of Honeywell. Various aspects of OSI design evolved from experiences with the Advanced Research Projects Agency Network (ARPANET) and the fledgling Internet. 16
 OSI Layers 17 OSI Model Data unit Layer Function 7. Application Host layers 6. Presentation Data representation, encryption and decryption 5. Session Data Network process to application Interhost communication Segments 4. Transport Packet 3. Network Path determination and logical addressing Frame 2. Data Link Physical addressing Bit Media layers End-to-end connections and reliability, Flow control 1. Physical Media, signal and binary transmission Going from layer 1 to 7: Please Do Not Throw Sausage Pizza Away Going from layer 7 to 1: All People Seem To Need Data Processing
OSI Layers 17 OSI Model Data unit Layer Function 7. Application Host layers 6. Presentation Data representation, encryption and decryption 5. Session Data Network process to application Interhost communication Segments 4. Transport Packet 3. Network Path determination and logical addressing Frame 2. Data Link Physical addressing Bit Media layers End-to-end connections and reliability, Flow control 1. Physical Media, signal and binary transmission Going from layer 1 to 7: Please Do Not Throw Sausage Pizza Away Going from layer 7 to 1: All People Seem To Need Data Processing
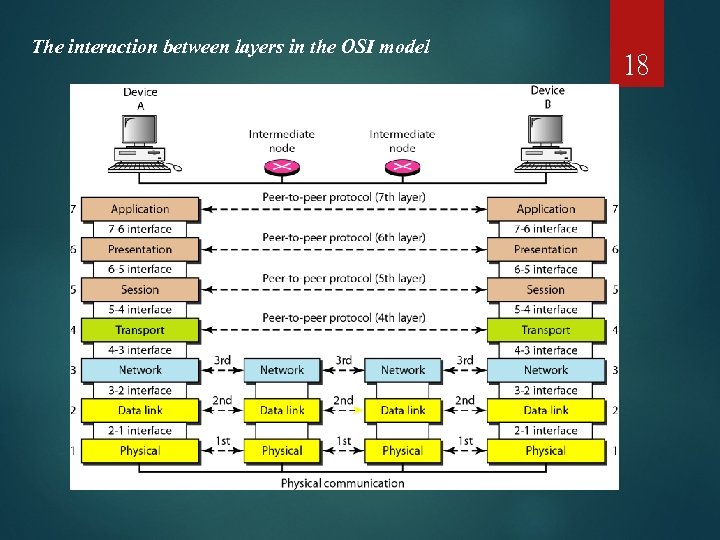 The interaction between layers in the OSI model 18
The interaction between layers in the OSI model 18
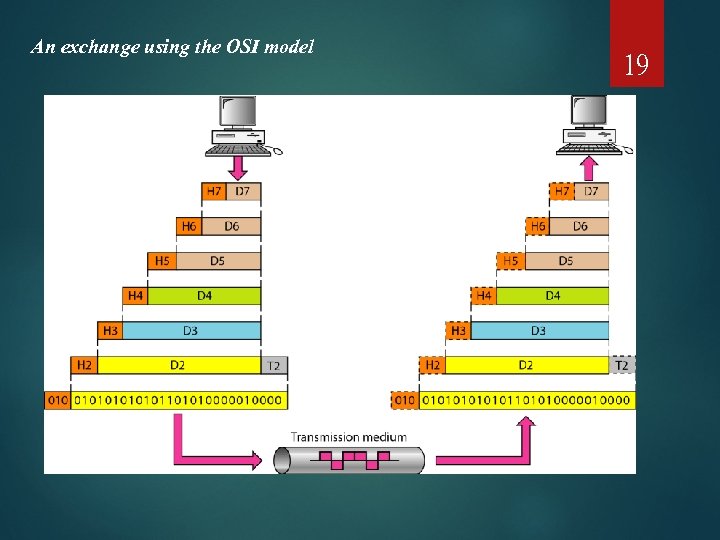 An exchange using the OSI model 19
An exchange using the OSI model 19
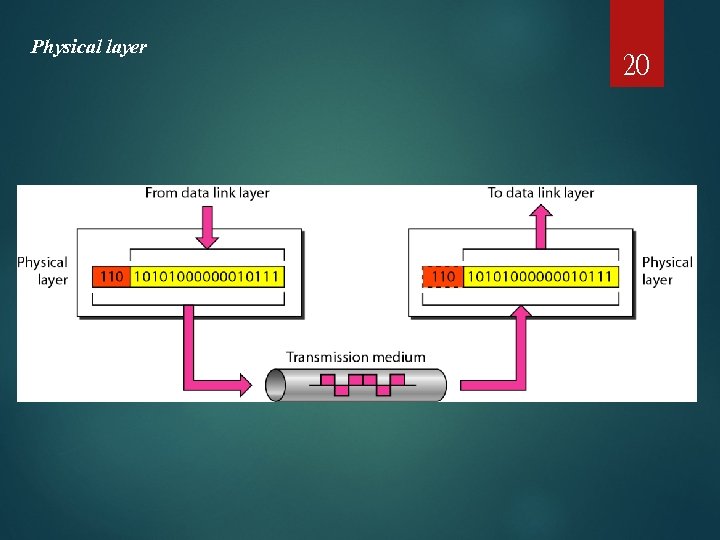 Physical layer 20
Physical layer 20
 Layer 1: Physical Layer The Physical Layer defines the electrical and physical specifications for devices. In particular, it defines the relationship between a device and a physical medium. This includes the layout of pin, voltages, cable specification, hubs, repeaters, network adapters, host bus adapters, and more. 21
Layer 1: Physical Layer The Physical Layer defines the electrical and physical specifications for devices. In particular, it defines the relationship between a device and a physical medium. This includes the layout of pin, voltages, cable specification, hubs, repeaters, network adapters, host bus adapters, and more. 21
 Layer 1: Physical Layer The major functions and services performed by the Physical Layer are: Establishment and termination of a connection to a communication medium. Participation in the process whereby the communication resources are effectively shared among multiple users. For example, flow control. Modulation, or conversion between the representation of digital data in user equipment and the corresponding signals transmitted over a communications channel. These are signals operating over the physical cabling (such as copper and optical fiber) or over a radio link. 22
Layer 1: Physical Layer The major functions and services performed by the Physical Layer are: Establishment and termination of a connection to a communication medium. Participation in the process whereby the communication resources are effectively shared among multiple users. For example, flow control. Modulation, or conversion between the representation of digital data in user equipment and the corresponding signals transmitted over a communications channel. These are signals operating over the physical cabling (such as copper and optical fiber) or over a radio link. 22
 Layer 1: Physical Layer con. 23 The same applies to local-area networks, such as Ethernet. ITU-T( International Telecommunication Union Telecommunication Standardization Sector) and IEEE 802. 1 I. Personal area networks such as Bluetooth and IEEE 802. 15. 4.
Layer 1: Physical Layer con. 23 The same applies to local-area networks, such as Ethernet. ITU-T( International Telecommunication Union Telecommunication Standardization Sector) and IEEE 802. 1 I. Personal area networks such as Bluetooth and IEEE 802. 15. 4.
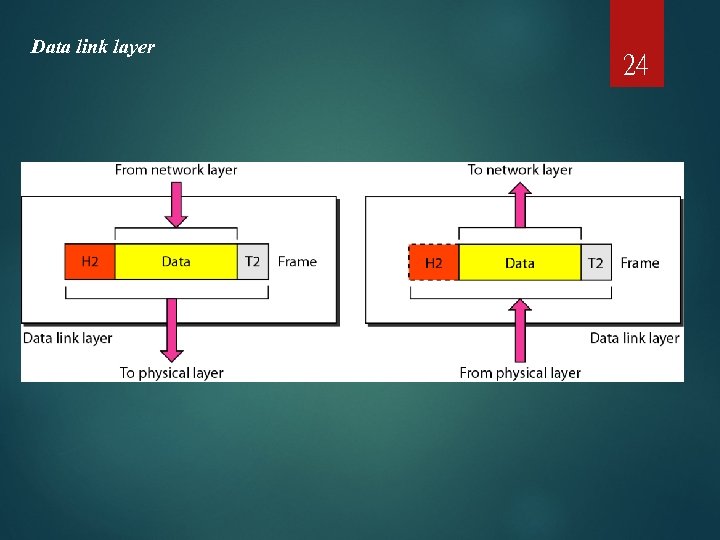 Data link layer 24
Data link layer 24
 Layer 2: Data Link Layer The Data Link Layer provides the functional and procedural means to transfer data between network entities and to detect and possibly correct errors that may occur in the Physical Layer. Originally, this layer was intended for point-to-point and point-to-multipoint media, characteristic of wide area media in the telephone system. The data link layer is divided into two sub-layers by IEEE. 25
Layer 2: Data Link Layer The Data Link Layer provides the functional and procedural means to transfer data between network entities and to detect and possibly correct errors that may occur in the Physical Layer. Originally, this layer was intended for point-to-point and point-to-multipoint media, characteristic of wide area media in the telephone system. The data link layer is divided into two sub-layers by IEEE. 25
 Layer 2: Data Link Layer 26 One is Media Access Control (MAC) and another is Logical Link Control (LLC). Mac is lower sub-layer, and it defines the way about the media access transfer, such as CSMA/CD/CA(Carrier Sense Multiple Access/Collision Detection/Collision Avoidance) LLC provides data transmission method in different network. It will re-package date and add a new header.
Layer 2: Data Link Layer 26 One is Media Access Control (MAC) and another is Logical Link Control (LLC). Mac is lower sub-layer, and it defines the way about the media access transfer, such as CSMA/CD/CA(Carrier Sense Multiple Access/Collision Detection/Collision Avoidance) LLC provides data transmission method in different network. It will re-package date and add a new header.
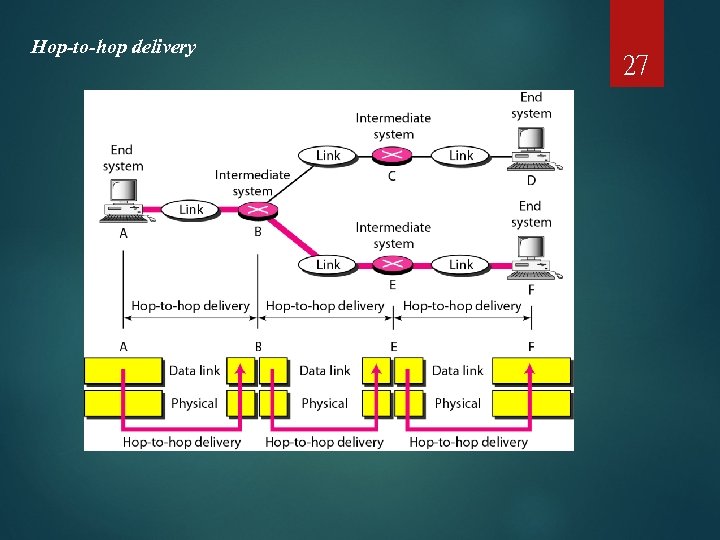 Hop-to-hop delivery 27
Hop-to-hop delivery 27
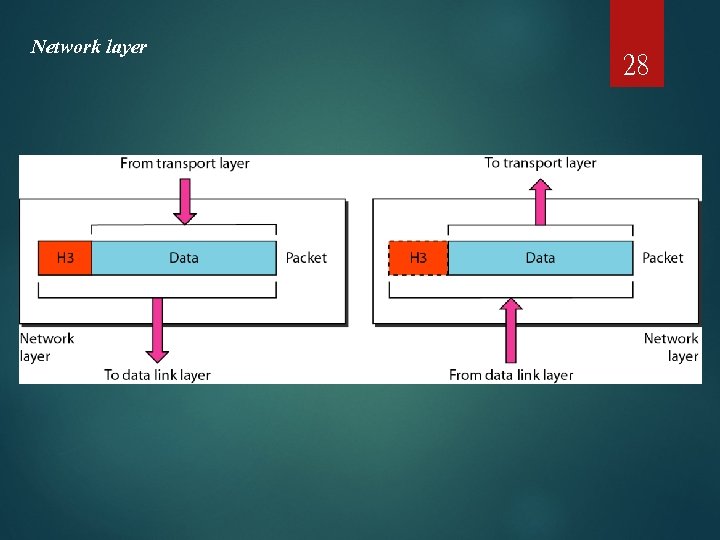 Network layer 28
Network layer 28
 Layer 3: Network Layer The Network Layer provides the functional and procedural means of transferring variable length data sequences from a source to a destination via one or more networks, while maintaining the quality of service requested by the Transport Layer. 29
Layer 3: Network Layer The Network Layer provides the functional and procedural means of transferring variable length data sequences from a source to a destination via one or more networks, while maintaining the quality of service requested by the Transport Layer. 29
 Layer 3: Network Layer The Network Layer performs perform fragmentation and reassembly, network routing functions, report delivery errors. Routers operate at this layer—sending data throughout the extended network and making the Internet possible. 30
Layer 3: Network Layer The Network Layer performs perform fragmentation and reassembly, network routing functions, report delivery errors. Routers operate at this layer—sending data throughout the extended network and making the Internet possible. 30
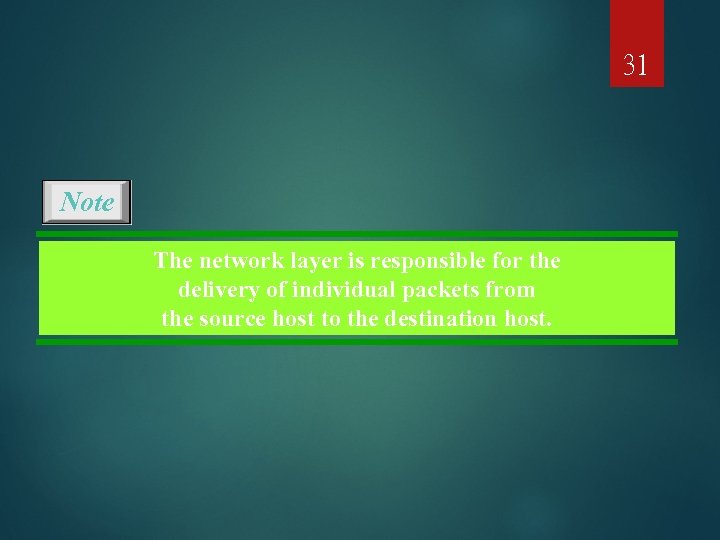 31 Note The network layer is responsible for the delivery of individual packets from the source host to the destination host.
31 Note The network layer is responsible for the delivery of individual packets from the source host to the destination host.
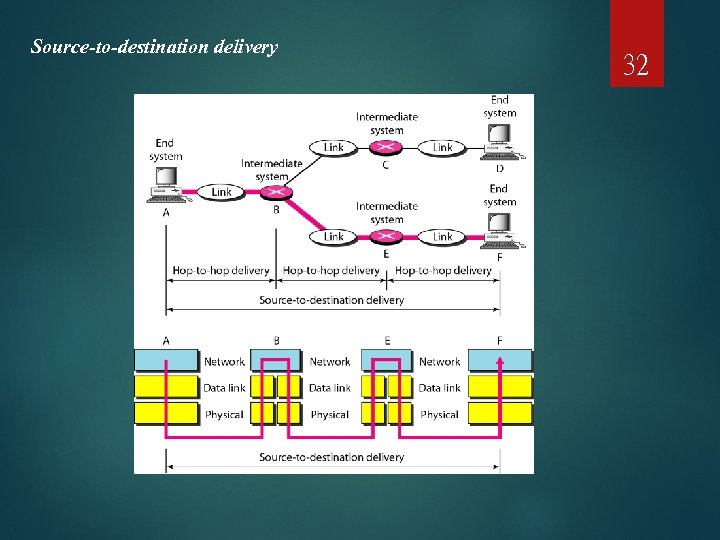 Source-to-destination delivery 32
Source-to-destination delivery 32
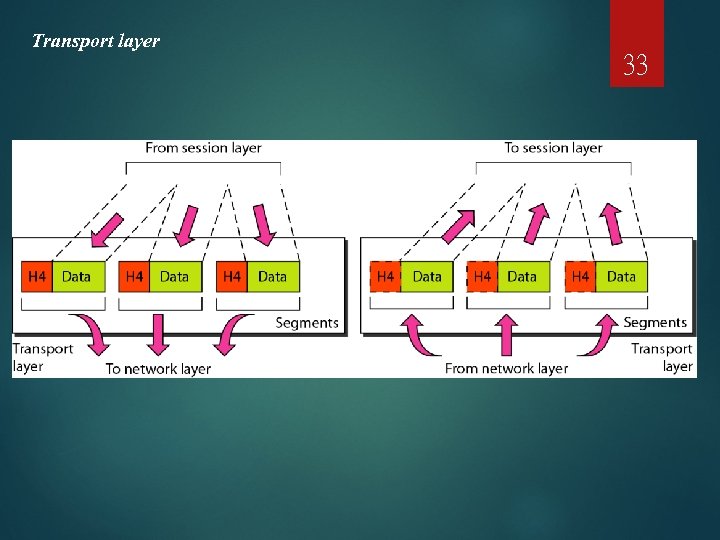 Transport layer 33
Transport layer 33
 Layer 4: Transport Layer The Transport Layer provides transparent transfer of data between end users, providing reliable data transfer services to the upper layers. The Transport Layer controls the reliability of a given link through flow control, segmentation/desegmentation, and error control. 34
Layer 4: Transport Layer The Transport Layer provides transparent transfer of data between end users, providing reliable data transfer services to the upper layers. The Transport Layer controls the reliability of a given link through flow control, segmentation/desegmentation, and error control. 34
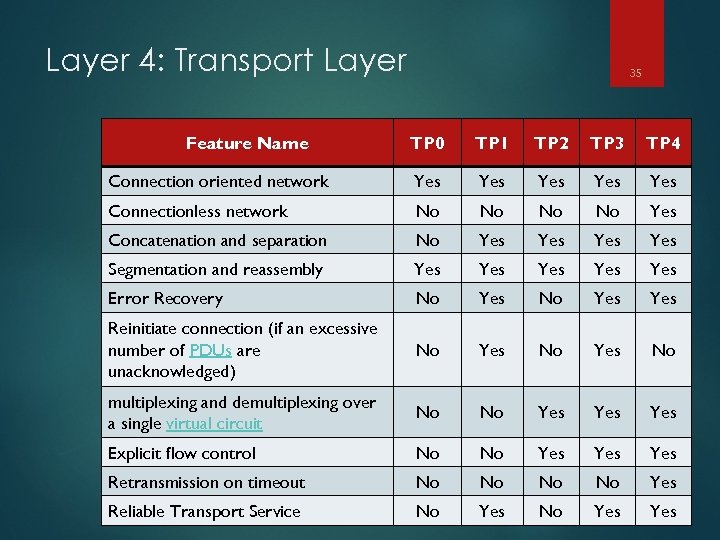 Layer 4: Transport Layer Feature Name 35 TP 0 TP 1 TP 2 TP 3 TP 4 Connection oriented network Yes Yes Yes Connectionless network No No Yes Concatenation and separation No Yes Yes Segmentation and reassembly Yes Yes Yes Error Recovery No Yes Yes Reinitiate connection (if an excessive number of PDUs are unacknowledged) No Yes No multiplexing and demultiplexing over a single virtual circuit No No Yes Yes Explicit flow control No No Yes Yes Retransmission on timeout No No Yes Reliable Transport Service No Yes Yes
Layer 4: Transport Layer Feature Name 35 TP 0 TP 1 TP 2 TP 3 TP 4 Connection oriented network Yes Yes Yes Connectionless network No No Yes Concatenation and separation No Yes Yes Segmentation and reassembly Yes Yes Yes Error Recovery No Yes Yes Reinitiate connection (if an excessive number of PDUs are unacknowledged) No Yes No multiplexing and demultiplexing over a single virtual circuit No No Yes Yes Explicit flow control No No Yes Yes Retransmission on timeout No No Yes Reliable Transport Service No Yes Yes
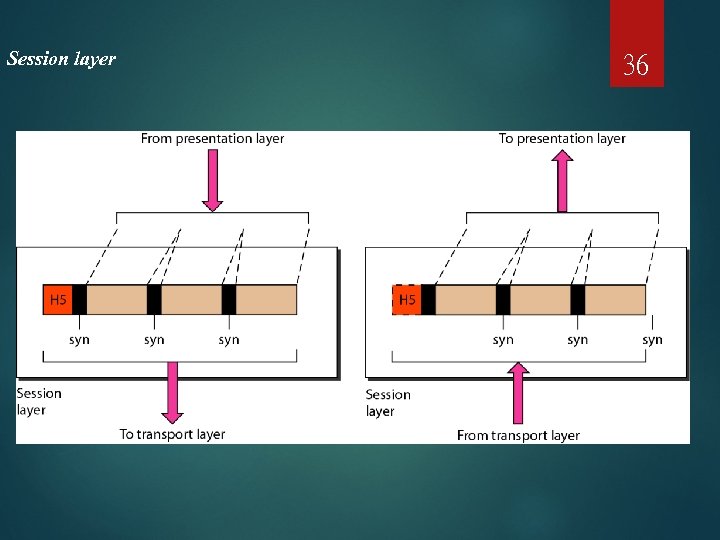 Session layer 36
Session layer 36
 37 Note The session layer is responsible for dialog control and synchronization.
37 Note The session layer is responsible for dialog control and synchronization.
 Layer 5: Session Layer The Session Layer controls the dialogues (connections) between computers. It establishes, manages and terminates the connections between the local and remote application. It provides for full-duplex, half-duplex, or simplex operation, and establishes checkpointing, adjournment, termination, and restart procedures. 38
Layer 5: Session Layer The Session Layer controls the dialogues (connections) between computers. It establishes, manages and terminates the connections between the local and remote application. It provides for full-duplex, half-duplex, or simplex operation, and establishes checkpointing, adjournment, termination, and restart procedures. 38
 Layer 5: Session Layer The OSI model made this layer responsible for graceful close of sessions, which is a property of the Transmission Control Protocol, and also for session check pointing and recovery, which is not usually used in the Internet Protocol Suite. The Session Layer is commonly implemented explicitly in application environments that use remote procedure calls. 39
Layer 5: Session Layer The OSI model made this layer responsible for graceful close of sessions, which is a property of the Transmission Control Protocol, and also for session check pointing and recovery, which is not usually used in the Internet Protocol Suite. The Session Layer is commonly implemented explicitly in application environments that use remote procedure calls. 39
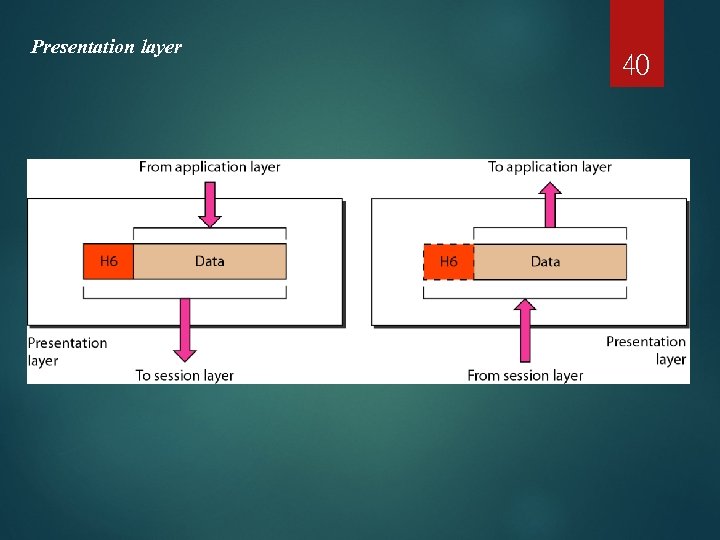 Presentation layer 40
Presentation layer 40
 41 Note The presentation layer is responsible for translation, compression, and encryption.
41 Note The presentation layer is responsible for translation, compression, and encryption.
 Layer 6: Presentation Layer The Presentation Layer establishes a context between Application Layer entities, in which the higher-layer entities can use different syntax and semantics, as long as the presentation service understands both and the mapping between them. This layer provides independence from differences in data representation (e. g. , encryption) by translating from application to network format, and vice versa. This layer formats and encrypts data to be sent across a network, providing freedom from compatibility problems. It is sometimes called the syntax layer. 42
Layer 6: Presentation Layer The Presentation Layer establishes a context between Application Layer entities, in which the higher-layer entities can use different syntax and semantics, as long as the presentation service understands both and the mapping between them. This layer provides independence from differences in data representation (e. g. , encryption) by translating from application to network format, and vice versa. This layer formats and encrypts data to be sent across a network, providing freedom from compatibility problems. It is sometimes called the syntax layer. 42
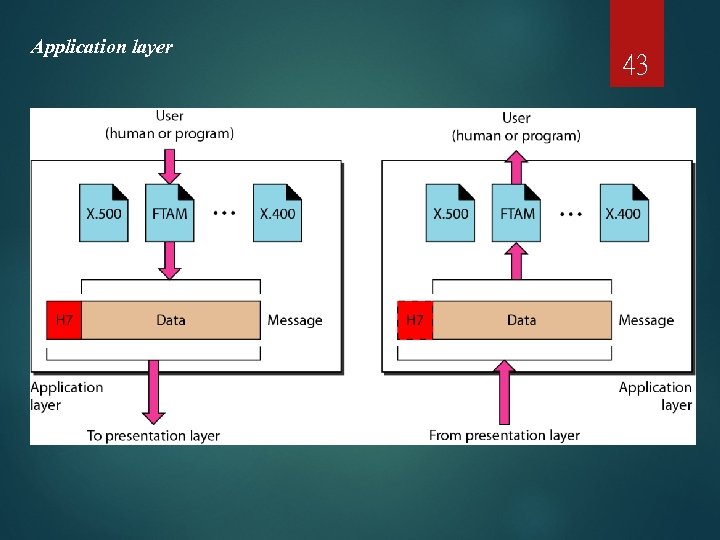 Application layer 43
Application layer 43
 Layer 7: Application Layer The application layer is the OSI layer closest to the end user, which means that both the OSI application layer and the user interact directly with the software application. Application layer functions typically include: identifying communication partners, determining resource availability, synchronizing communication. 44
Layer 7: Application Layer The application layer is the OSI layer closest to the end user, which means that both the OSI application layer and the user interact directly with the software application. Application layer functions typically include: identifying communication partners, determining resource availability, synchronizing communication. 44
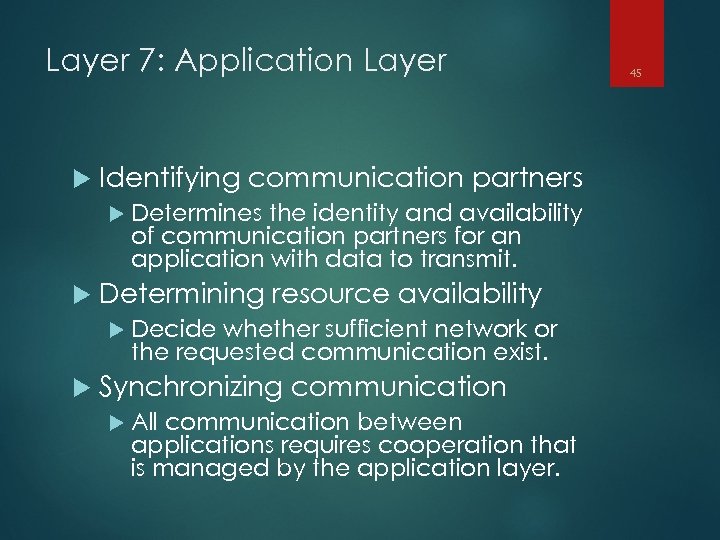 Layer 7: Application Layer Identifying communication partners Determines the identity and availability of communication partners for an application with data to transmit. Determining resource availability Decide whether sufficient network or the requested communication exist. Synchronizing communication All communication between applications requires cooperation that is managed by the application layer. 45
Layer 7: Application Layer Identifying communication partners Determines the identity and availability of communication partners for an application with data to transmit. Determining resource availability Decide whether sufficient network or the requested communication exist. Synchronizing communication All communication between applications requires cooperation that is managed by the application layer. 45
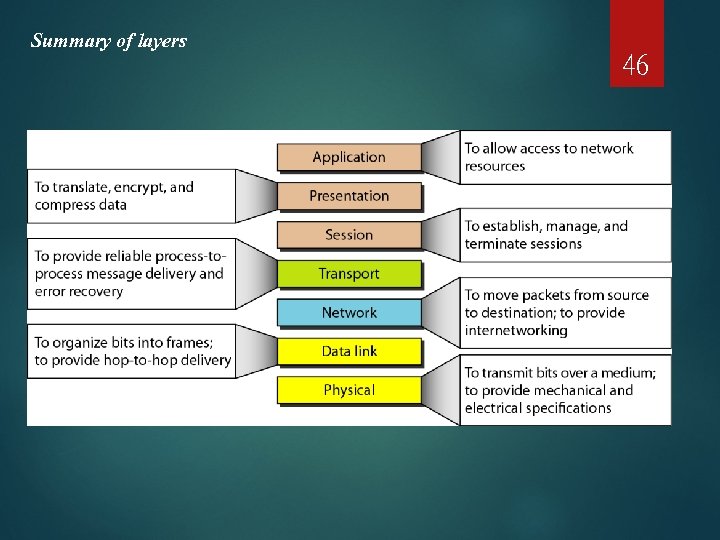 Summary of layers 46
Summary of layers 46
 OSI Feature Open system standards over the world Rigorously defined structured, hierarchical network model Complete description of the function Provide standard test procedures 47
OSI Feature Open system standards over the world Rigorously defined structured, hierarchical network model Complete description of the function Provide standard test procedures 47
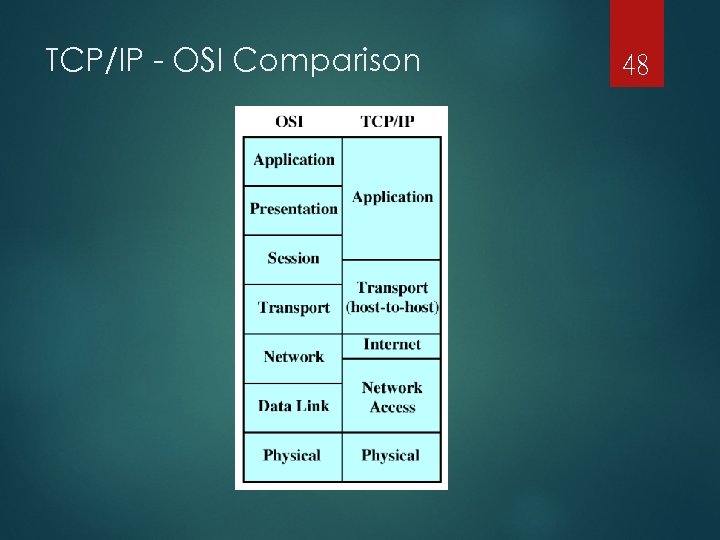 TCP/IP - OSI Comparison 48
TCP/IP - OSI Comparison 48
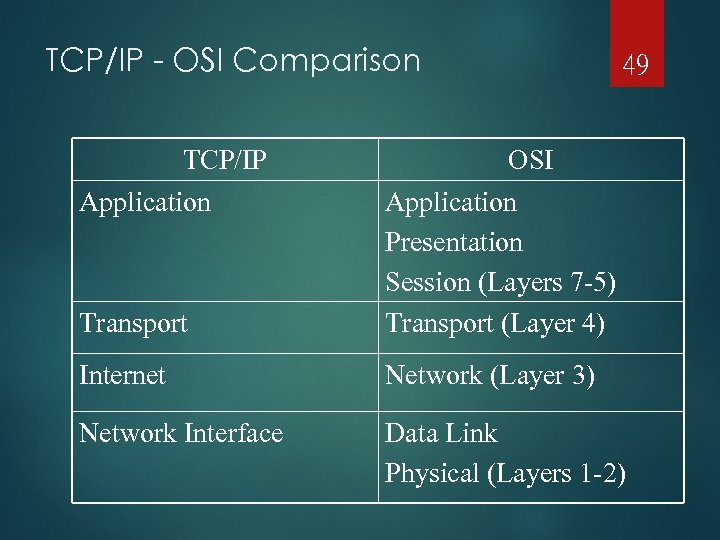 TCP/IP - OSI Comparison TCP/IP Application 49 OSI Transport Application Presentation Session (Layers 7 -5) Transport (Layer 4) Internet Network (Layer 3) Network Interface Data Link Physical (Layers 1 -2)
TCP/IP - OSI Comparison TCP/IP Application 49 OSI Transport Application Presentation Session (Layers 7 -5) Transport (Layer 4) Internet Network (Layer 3) Network Interface Data Link Physical (Layers 1 -2)
 TCP/IP Transmission Control Protocol/Internet Protocol Developed by DARPA No official protocol standard 50 Identifies 5 Layers Application Host-to-Host (transport) Internet Network Access Physical
TCP/IP Transmission Control Protocol/Internet Protocol Developed by DARPA No official protocol standard 50 Identifies 5 Layers Application Host-to-Host (transport) Internet Network Access Physical
 TCP/IP Physical Layer Physical interface between a DTE (Data Terminal Equipment) (e. g. computer or terminal) and a transmission medium Specifies: Characteristics of medium Nature of signals Data rate 51
TCP/IP Physical Layer Physical interface between a DTE (Data Terminal Equipment) (e. g. computer or terminal) and a transmission medium Specifies: Characteristics of medium Nature of signals Data rate 51
 TCP/IP Network Access Exchange of data between systems on a shared network Utilizes address of host and destination Can also prioritize transmission Software at this layer depends on network Segregation means that no other software needs to be concerned about net specifics 52
TCP/IP Network Access Exchange of data between systems on a shared network Utilizes address of host and destination Can also prioritize transmission Software at this layer depends on network Segregation means that no other software needs to be concerned about net specifics 52
 TCP/IP Internet Layer An Internet is an interconnection of two or more networks Internet layer handles tasks similar to network access layer, but between networks rather than between nodes on a network Uses IP for addressing and routing across networks Implemented in workstations and routers 53
TCP/IP Internet Layer An Internet is an interconnection of two or more networks Internet layer handles tasks similar to network access layer, but between networks rather than between nodes on a network Uses IP for addressing and routing across networks Implemented in workstations and routers 53
 TCP/IP Transport Layer Also called host-to-host layer Reliable exchange of data between applications Uses TCP protocols for transmission 54
TCP/IP Transport Layer Also called host-to-host layer Reliable exchange of data between applications Uses TCP protocols for transmission 54
 TCP/IP Application Layer Logic needed to support variety of applications Separate module supports each type of application (e. g. file transfer) 55
TCP/IP Application Layer Logic needed to support variety of applications Separate module supports each type of application (e. g. file transfer) 55
 TCP & UDP Most TCP/IP applications use TCP for transport layer TCP provides a connection (logical association) between two entities to regulate flow check errors UDP (User Datagram Protocol) does not maintain a connection, and therefore does not guarantee delivery, preserve sequences, or protect against duplication 56
TCP & UDP Most TCP/IP applications use TCP for transport layer TCP provides a connection (logical association) between two entities to regulate flow check errors UDP (User Datagram Protocol) does not maintain a connection, and therefore does not guarantee delivery, preserve sequences, or protect against duplication 56
 IP and IPv 6 IP provides for 32 -bit source and destination addresses IPv 6 (1996 standard) provides for 128 -bit addresses Migraqtion to IPv 6 will be a very slow process 57
IP and IPv 6 IP provides for 32 -bit source and destination addresses IPv 6 (1996 standard) provides for 128 -bit addresses Migraqtion to IPv 6 will be a very slow process 57
 TCP/IP Applications SMTP (Simple Mail Transfer Protocol) Basic e-mail facility, transferring messages among hosts FTP (File Transfer Protocol) Sends files from one system to another on user command Telnet Remote login capability, allowing a user to emulate a terminal on the remote system 58
TCP/IP Applications SMTP (Simple Mail Transfer Protocol) Basic e-mail facility, transferring messages among hosts FTP (File Transfer Protocol) Sends files from one system to another on user command Telnet Remote login capability, allowing a user to emulate a terminal on the remote system 58
 Internetworking Interconnected networks, usually implies TCP/IP Can appear to users as a single large network The global Internet is the largest example, but intranets and extranets are also examples 59
Internetworking Interconnected networks, usually implies TCP/IP Can appear to users as a single large network The global Internet is the largest example, but intranets and extranets are also examples 59
 Routers Equipment used to interconnect independent networks Several essential functions Provide a link between networks Provide routing and delivery of data between processes on systems from different networks Provide the above functions without requiring modification of the attached networks 60
Routers Equipment used to interconnect independent networks Several essential functions Provide a link between networks Provide routing and delivery of data between processes on systems from different networks Provide the above functions without requiring modification of the attached networks 60
 Router Issues Addressing schemes Maximum packet size Interfaces Reliability 61
Router Issues Addressing schemes Maximum packet size Interfaces Reliability 61
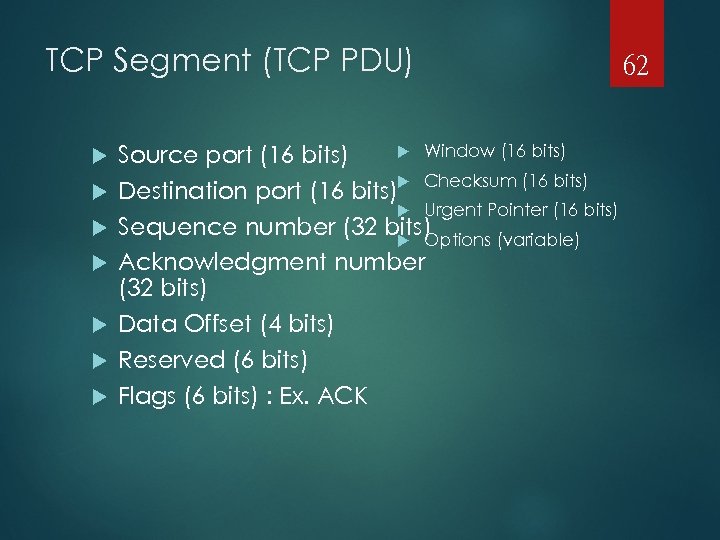 TCP Segment (TCP PDU) Window (16 bits) Source port (16 bits) Destination port (16 bits) Checksum (16 bits) Urgent Pointer (16 bits) Sequence number (32 bits) Options (variable) Acknowledgment number (32 bits) Data Offset (4 bits) Reserved (6 bits) Flags (6 bits) : Ex. ACK 62
TCP Segment (TCP PDU) Window (16 bits) Source port (16 bits) Destination port (16 bits) Checksum (16 bits) Urgent Pointer (16 bits) Sequence number (32 bits) Options (variable) Acknowledgment number (32 bits) Data Offset (4 bits) Reserved (6 bits) Flags (6 bits) : Ex. ACK 62
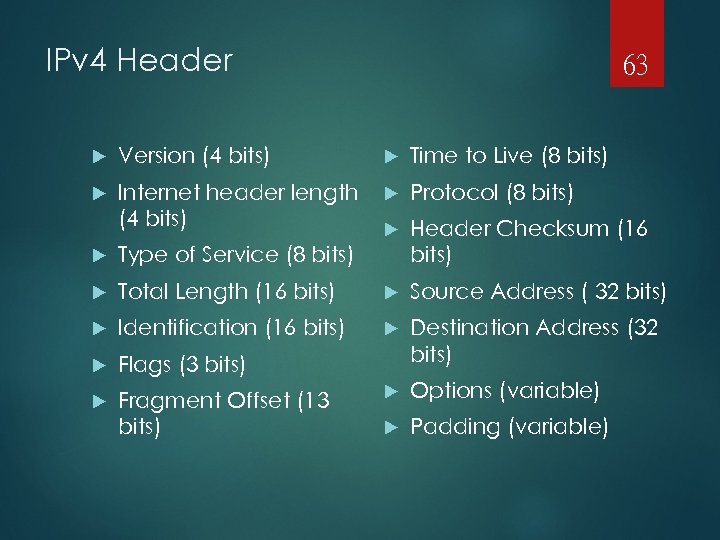 IPv 4 Header 63 Version (4 bits) Time to Live (8 bits) Internet header length (4 bits) Protocol (8 bits) Header Checksum (16 bits) Type of Service (8 bits) Total Length (16 bits) Source Address ( 32 bits) Identification (16 bits) Flags (3 bits) Destination Address (32 bits) Fragment Offset (13 bits) Options (variable) Padding (variable)
IPv 4 Header 63 Version (4 bits) Time to Live (8 bits) Internet header length (4 bits) Protocol (8 bits) Header Checksum (16 bits) Type of Service (8 bits) Total Length (16 bits) Source Address ( 32 bits) Identification (16 bits) Flags (3 bits) Destination Address (32 bits) Fragment Offset (13 bits) Options (variable) Padding (variable)
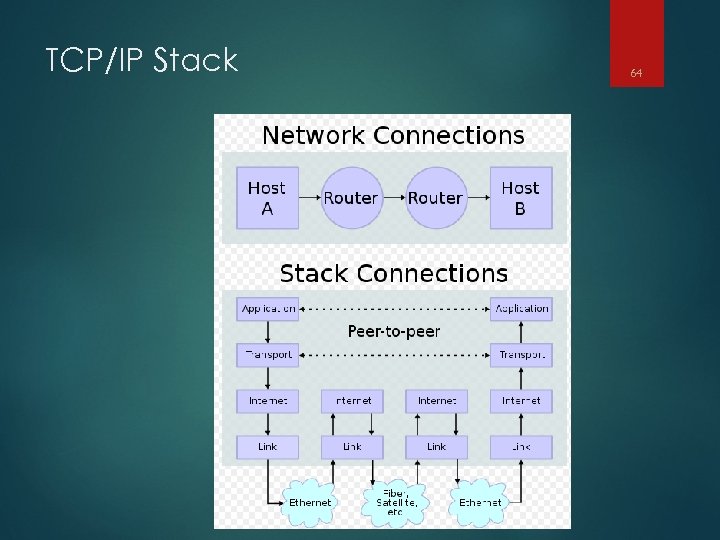 TCP/IP Stack 64
TCP/IP Stack 64
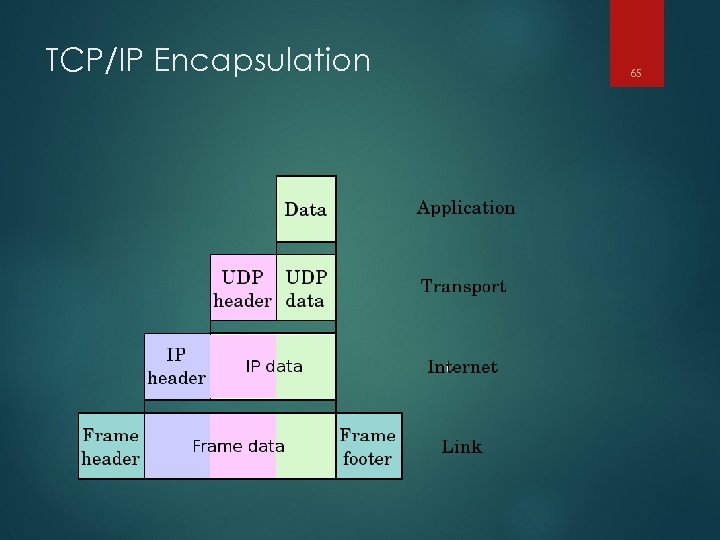 TCP/IP Encapsulation 65
TCP/IP Encapsulation 65
 Why Layering Considered Harmful? As a result of inter-layer dependencies, increased layering can quickly lead to violation of the Simplicity Principle. Industry experience has taught us that increased layering frequently increases complexity. 66
Why Layering Considered Harmful? As a result of inter-layer dependencies, increased layering can quickly lead to violation of the Simplicity Principle. Industry experience has taught us that increased layering frequently increases complexity. 66


