86b600d3f79085e2c6aca72893d4534c.ppt
- Количество слайдов: 26
 Technology Solutions n Protecting Internet communications (encryption) v Symmetric Key Encryption v Public key Encryption (simple case, Hash+certificate, Digital envelope, Certification authority and Public key infrastructure) n Securing channels of communication (SSL, S-HTTP, VPNs) n Protecting networks (firewalls + Proxy Servers) n Protecting servers and clients Copyright © 2010 Pearson Education, Inc. Slide 5 -1
Technology Solutions n Protecting Internet communications (encryption) v Symmetric Key Encryption v Public key Encryption (simple case, Hash+certificate, Digital envelope, Certification authority and Public key infrastructure) n Securing channels of communication (SSL, S-HTTP, VPNs) n Protecting networks (firewalls + Proxy Servers) n Protecting servers and clients Copyright © 2010 Pearson Education, Inc. Slide 5 -1
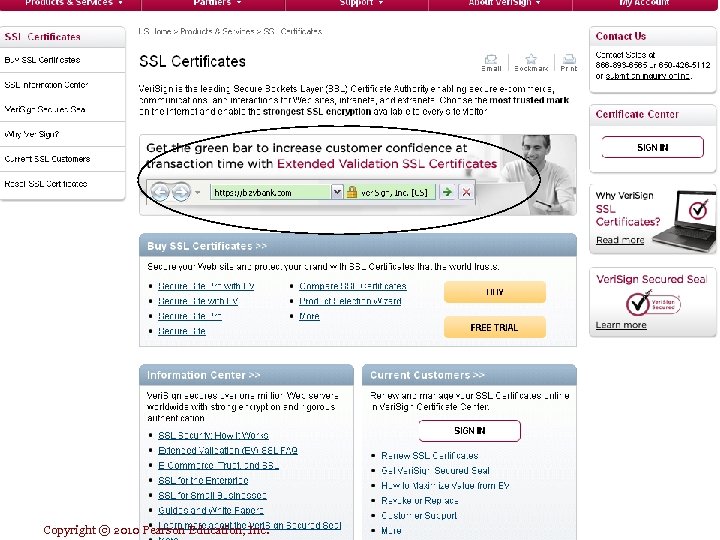
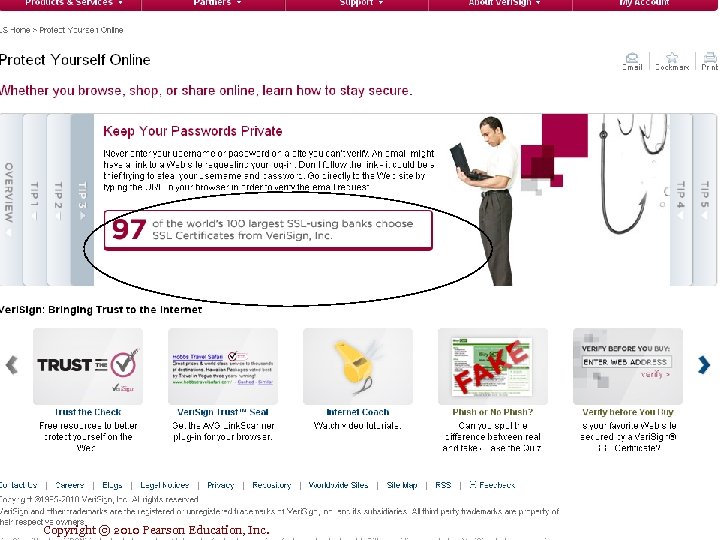
 Securing Channels of Communication ( encryption implementation) n 1. Secure Sockets Layer (SSL): n Secure Socket Layer (SSL) is a protocol that encrypts data between the shopper's computer and the site's server. v Look for “S” in browser (https instead of http) v Look for “small Pad Lock “ in Browser It means you are using SSL to establish a secure negotiation session through session key. Secure Negotiated Session: A client – server session (duration) in which the URL of the requested documents along with the contents, contents of forms, and the cookies exchanged , are encrypted. Session key: A session key is a unique symmetric encryption key chosen just for this single secure session. Once used , it is gone forever. Copyright © 2010 Pearson Education, Inc. Slide 5 -2
Securing Channels of Communication ( encryption implementation) n 1. Secure Sockets Layer (SSL): n Secure Socket Layer (SSL) is a protocol that encrypts data between the shopper's computer and the site's server. v Look for “S” in browser (https instead of http) v Look for “small Pad Lock “ in Browser It means you are using SSL to establish a secure negotiation session through session key. Secure Negotiated Session: A client – server session (duration) in which the URL of the requested documents along with the contents, contents of forms, and the cookies exchanged , are encrypted. Session key: A session key is a unique symmetric encryption key chosen just for this single secure session. Once used , it is gone forever. Copyright © 2010 Pearson Education, Inc. Slide 5 -2
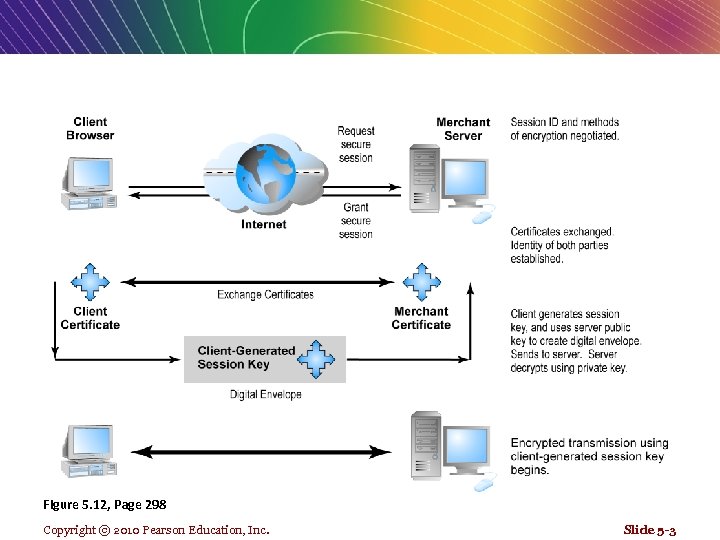 Figure 5. 12, Page 298 Copyright © 2010 Pearson Education, Inc. Slide 5 -3
Figure 5. 12, Page 298 Copyright © 2010 Pearson Education, Inc. Slide 5 -3
 Copyright © 2010 Pearson Education, Inc.
Copyright © 2010 Pearson Education, Inc.
 Copyright © 2010 Pearson Education, Inc.
Copyright © 2010 Pearson Education, Inc.
 Copyright © 2010 Pearson Education, Inc.
Copyright © 2010 Pearson Education, Inc.
 Copyright © 2010 Pearson Education, Inc.
Copyright © 2010 Pearson Education, Inc.
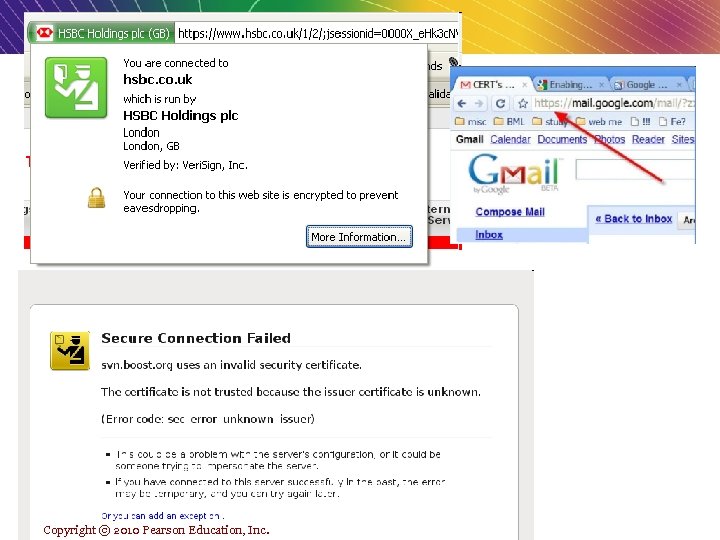
 v When your browser requests a secure page and add onto http and show a “pad lock” in browser. “S” v The browser send out the Public key and the certificate Checking things such as certificate comes from trusted party (CA) Certificate Currently valid the certificate has a relation with the site (for example citybank. com or amazon. com )from which is coming Copyright © 2010 Pearson Education, Inc.
v When your browser requests a secure page and add onto http and show a “pad lock” in browser. “S” v The browser send out the Public key and the certificate Checking things such as certificate comes from trusted party (CA) Certificate Currently valid the certificate has a relation with the site (for example citybank. com or amazon. com )from which is coming Copyright © 2010 Pearson Education, Inc.
 SSL provide: Data encryption, Server Authentication , optional Client authentication, message integrity. Note: In practice, most private individuals (for example you are placing order on Amazon, or viewing your account on citibank site) do not have a digital certificate. In this case , the merchant server will not request a certificate , but the client browser will request the merchant certificate once a secure session is called for by the server. v SET ( Secure Electronic Transaction Protocol): - An open standard for the v require all parties (receiver/sender) to a transaction to use digital certificate. e-commerce industry developed and offered by Master. Card and Visa as a way to facilitate and encourage improved security for credit card transactions Uses a digital certificate to verify a sender’s/receiver’s identity Copyright © 2010 Pearson Education, Inc.
SSL provide: Data encryption, Server Authentication , optional Client authentication, message integrity. Note: In practice, most private individuals (for example you are placing order on Amazon, or viewing your account on citibank site) do not have a digital certificate. In this case , the merchant server will not request a certificate , but the client browser will request the merchant certificate once a secure session is called for by the server. v SET ( Secure Electronic Transaction Protocol): - An open standard for the v require all parties (receiver/sender) to a transaction to use digital certificate. e-commerce industry developed and offered by Master. Card and Visa as a way to facilitate and encourage improved security for credit card transactions Uses a digital certificate to verify a sender’s/receiver’s identity Copyright © 2010 Pearson Education, Inc.
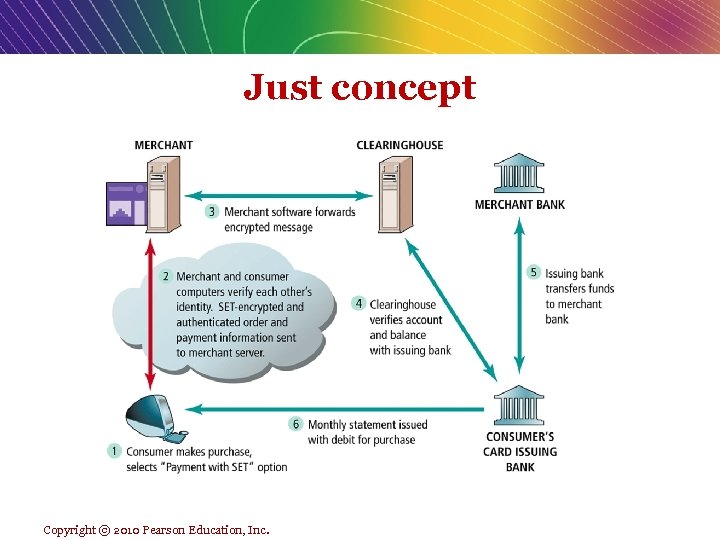 Just concept Copyright © 2010 Pearson Education, Inc.
Just concept Copyright © 2010 Pearson Education, Inc.
 n 2. S-HTTP: v An extension to the HTTP protocol to support sending data securely over the World Wide Web. v Provides a secure message-oriented communications protocol designed for use in conjunction with HTTP. v Not all browsers and not all web sites support s-http. v When there is SHTTP in url , then it mean the target server is S – HTTP capable. v Using S – http any message may be signed, AUTHENTICATED, v S-http use RSA encryption algorithm. v Basically s-http attempts to make http more secure. ENCRYPTED, OR combination of these. However, S-HTTP was never fully accepted by Web browser vendors such as Microsoft and Netscape. Instead, a similar protocol called SSL (Secure Sockets Layer) became more popular. Copyright © 2010 Pearson Education, Inc. v
n 2. S-HTTP: v An extension to the HTTP protocol to support sending data securely over the World Wide Web. v Provides a secure message-oriented communications protocol designed for use in conjunction with HTTP. v Not all browsers and not all web sites support s-http. v When there is SHTTP in url , then it mean the target server is S – HTTP capable. v Using S – http any message may be signed, AUTHENTICATED, v S-http use RSA encryption algorithm. v Basically s-http attempts to make http more secure. ENCRYPTED, OR combination of these. However, S-HTTP was never fully accepted by Web browser vendors such as Microsoft and Netscape. Instead, a similar protocol called SSL (Secure Sockets Layer) became more popular. Copyright © 2010 Pearson Education, Inc. v
 n 3. Virtual Private Network (VPN): v A well-designed VPN can greatly benefit a company. For example, it can: v Extend geographic connectivity v Improve security v Provide faster ROI (return on investment) than traditional WAN v Reduce operational costs versus traditional WAN v Allows remote users to securely access internal network via the Internet, using Point-to-Point Tunneling Protocol (PPTP) n Two VPN technologies are currently in use: site-to-site VPNs and remote access VPNs. Copyright © 2010 Pearson Education, Inc.
n 3. Virtual Private Network (VPN): v A well-designed VPN can greatly benefit a company. For example, it can: v Extend geographic connectivity v Improve security v Provide faster ROI (return on investment) than traditional WAN v Reduce operational costs versus traditional WAN v Allows remote users to securely access internal network via the Internet, using Point-to-Point Tunneling Protocol (PPTP) n Two VPN technologies are currently in use: site-to-site VPNs and remote access VPNs. Copyright © 2010 Pearson Education, Inc.
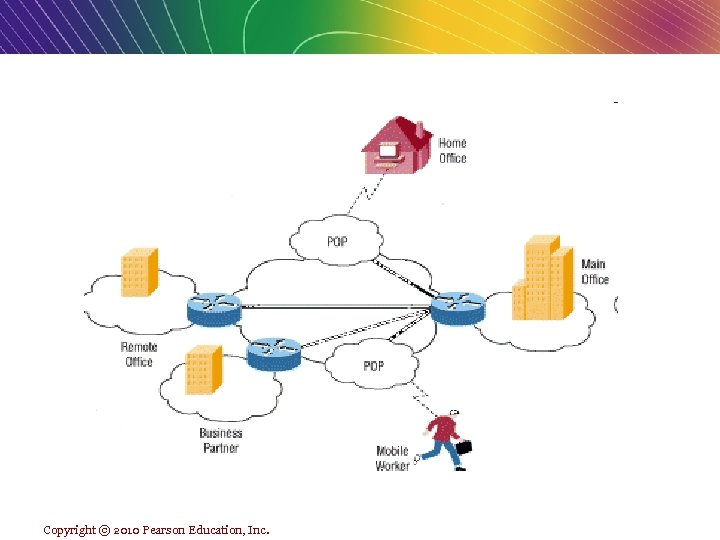 Copyright © 2010 Pearson Education, Inc.
Copyright © 2010 Pearson Education, Inc.
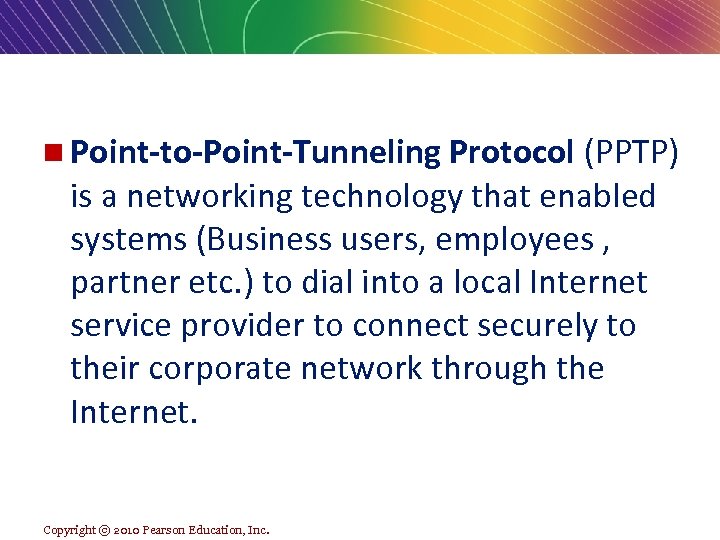 n Point-to-Point-Tunneling Protocol (PPTP) is a networking technology that enabled systems (Business users, employees , partner etc. ) to dial into a local Internet service provider to connect securely to their corporate network through the Internet. Copyright © 2010 Pearson Education, Inc.
n Point-to-Point-Tunneling Protocol (PPTP) is a networking technology that enabled systems (Business users, employees , partner etc. ) to dial into a local Internet service provider to connect securely to their corporate network through the Internet. Copyright © 2010 Pearson Education, Inc.
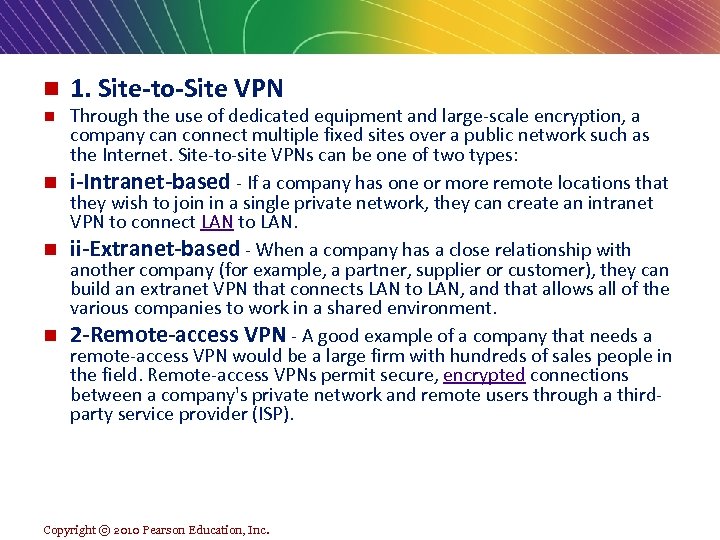 n 1. Site-to-Site VPN Through the use of dedicated equipment and large-scale encryption, a company can connect multiple fixed sites over a public network such as the Internet. Site-to-site VPNs can be one of two types: n i-Intranet-based - If a company has one or more remote locations that they wish to join in a single private network, they can create an intranet VPN to connect LAN to LAN. n ii-Extranet-based - When a company has a close relationship with another company (for example, a partner, supplier or customer), they can build an extranet VPN that connects LAN to LAN, and that allows all of the various companies to work in a shared environment. n 2 -Remote-access VPN - A good example of a company that needs a remote-access VPN would be a large firm with hundreds of sales people in the field. Remote-access VPNs permit secure, encrypted connections between a company's private network and remote users through a thirdparty service provider (ISP). n Copyright © 2010 Pearson Education, Inc.
n 1. Site-to-Site VPN Through the use of dedicated equipment and large-scale encryption, a company can connect multiple fixed sites over a public network such as the Internet. Site-to-site VPNs can be one of two types: n i-Intranet-based - If a company has one or more remote locations that they wish to join in a single private network, they can create an intranet VPN to connect LAN to LAN. n ii-Extranet-based - When a company has a close relationship with another company (for example, a partner, supplier or customer), they can build an extranet VPN that connects LAN to LAN, and that allows all of the various companies to work in a shared environment. n 2 -Remote-access VPN - A good example of a company that needs a remote-access VPN would be a large firm with hundreds of sales people in the field. Remote-access VPNs permit secure, encrypted connections between a company's private network and remote users through a thirdparty service provider (ISP). n Copyright © 2010 Pearson Education, Inc.
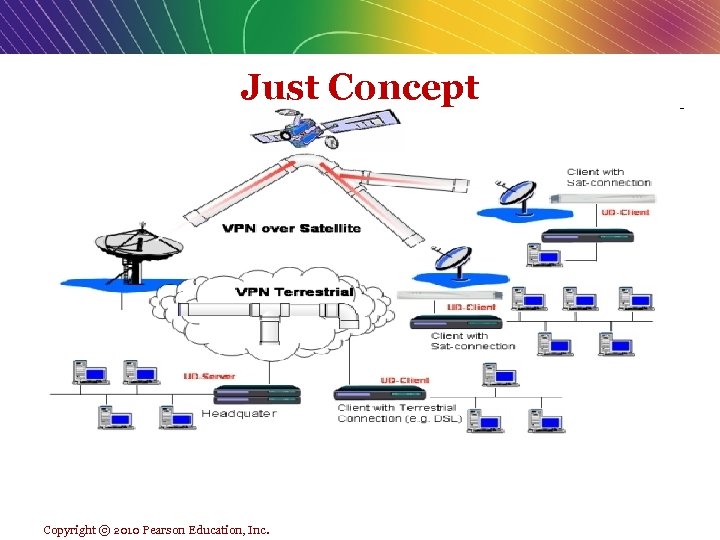 Just Concept Copyright © 2010 Pearson Education, Inc.
Just Concept Copyright © 2010 Pearson Education, Inc.
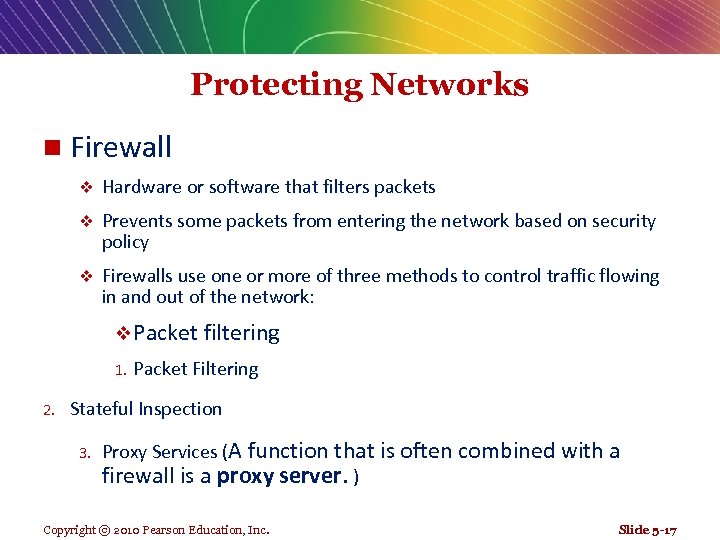 Protecting Networks n Firewall v Hardware or software that filters packets v Prevents some packets from entering the network based on security policy v Firewalls use one or more of three methods to control traffic flowing in and out of the network: v Packet filtering 1. 2. Packet Filtering Stateful Inspection 3. Proxy Services (A function that is often combined with a firewall is a proxy server. ) Copyright © 2010 Pearson Education, Inc. Slide 5 -17
Protecting Networks n Firewall v Hardware or software that filters packets v Prevents some packets from entering the network based on security policy v Firewalls use one or more of three methods to control traffic flowing in and out of the network: v Packet filtering 1. 2. Packet Filtering Stateful Inspection 3. Proxy Services (A function that is often combined with a firewall is a proxy server. ) Copyright © 2010 Pearson Education, Inc. Slide 5 -17
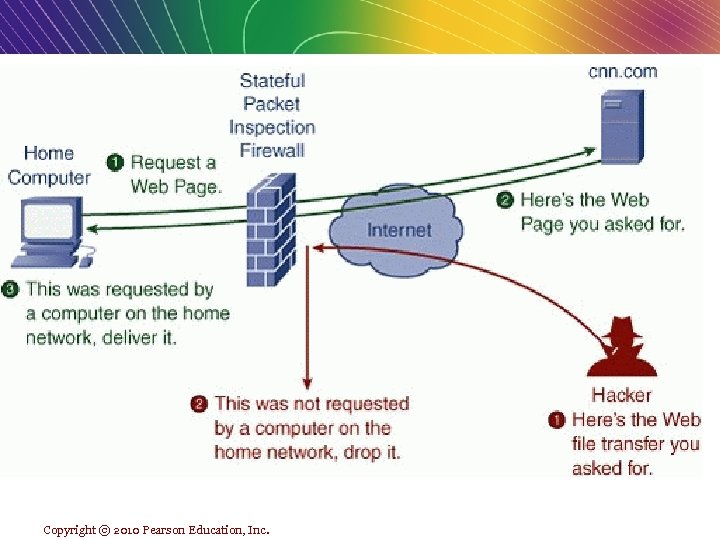 Copyright © 2010 Pearson Education, Inc.
Copyright © 2010 Pearson Education, Inc.
 Protecting Networks n Proxy servers (proxies) v Proxy servers can also be configured separately. v In the field of networking, a proxy server is defined as a system or a program that process the requests of clients and by forwarding queries and request to other systems or servers on the internet. v Proxy servers also improve Web performance by storing frequently used pages locally and reducing upload times. (mean cache) Copyright © 2010 Pearson Education, Inc.
Protecting Networks n Proxy servers (proxies) v Proxy servers can also be configured separately. v In the field of networking, a proxy server is defined as a system or a program that process the requests of clients and by forwarding queries and request to other systems or servers on the internet. v Proxy servers also improve Web performance by storing frequently used pages locally and reducing upload times. (mean cache) Copyright © 2010 Pearson Education, Inc.
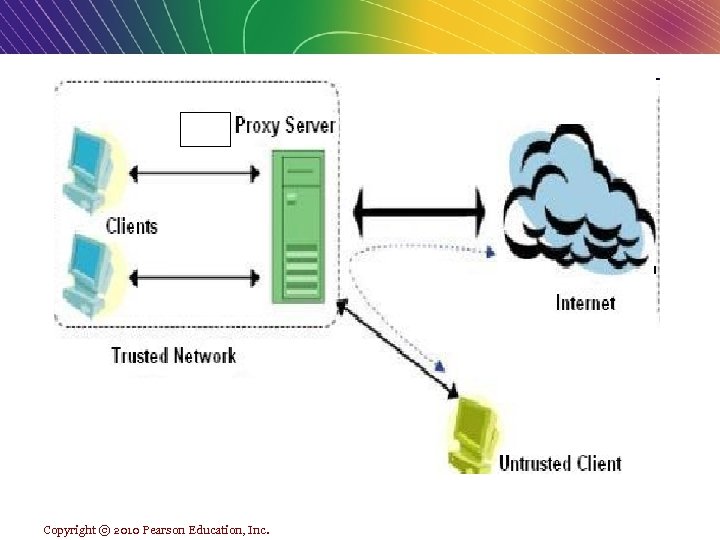 Copyright © 2010 Pearson Education, Inc.
Copyright © 2010 Pearson Education, Inc.
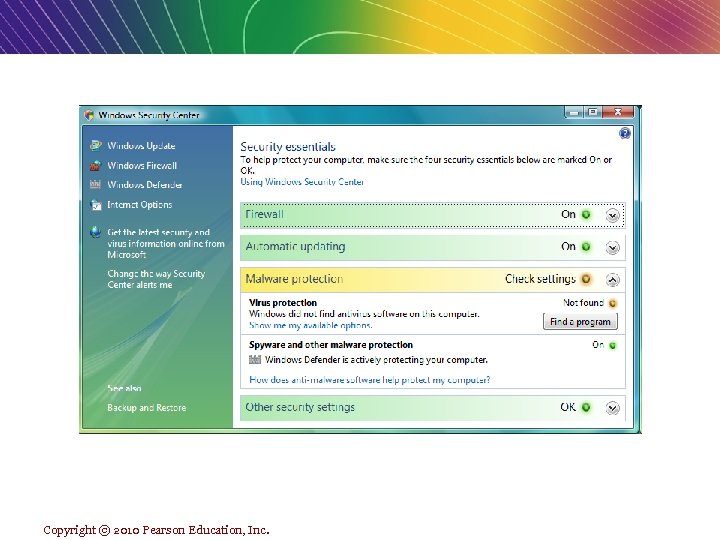
 Protecting Servers and Clients n 1 - Operating system security enhancements n Install a purchased copy of operating system (window). v Upgrades, patches : upgrades & Patches are autonomic; that is , when using windows xp or vista on the Internet , your are prompted and informed that operating system enhancements are available. v Active personal Firewall (Window firewall) v User can easily download these security patches for free. v The most common known worms and viruses can be prevented by simply keeping your server and client operating system and applications up to date. Copyright © 2010 Pearson Education, Inc. Slide 5 -21
Protecting Servers and Clients n 1 - Operating system security enhancements n Install a purchased copy of operating system (window). v Upgrades, patches : upgrades & Patches are autonomic; that is , when using windows xp or vista on the Internet , your are prompted and informed that operating system enhancements are available. v Active personal Firewall (Window firewall) v User can easily download these security patches for free. v The most common known worms and viruses can be prevented by simply keeping your server and client operating system and applications up to date. Copyright © 2010 Pearson Education, Inc. Slide 5 -21
 Copyright © 2010 Pearson Education, Inc.
Copyright © 2010 Pearson Education, Inc.
 Protecting Servers and Clients n 2 - Anti-virus software v Easiest and least expensive way to prevent threats to system integrity v For example, NOD 32, KESPERSKY, Symantec, AVGFREE PANDA ETC. v Requires daily updates Antivirus software will protect a computer from many, but not all, of the most common types of viruses. v The software will also destroy any viruses already present on the hard drive. v Premium – level anti – virus software is updated hourly. v v However, new viruses are being developed daily, so routine updates of the software needed to prevent new viruses from causing damage. Copyright © 2010 Pearson Education, Inc.
Protecting Servers and Clients n 2 - Anti-virus software v Easiest and least expensive way to prevent threats to system integrity v For example, NOD 32, KESPERSKY, Symantec, AVGFREE PANDA ETC. v Requires daily updates Antivirus software will protect a computer from many, but not all, of the most common types of viruses. v The software will also destroy any viruses already present on the hard drive. v Premium – level anti – virus software is updated hourly. v v However, new viruses are being developed daily, so routine updates of the software needed to prevent new viruses from causing damage. Copyright © 2010 Pearson Education, Inc.
 Just concept n Password policies (For e-commerce site) n Ensure that password policies are enforced for shoppers and internal users. A sample password policy, defined as part of the Federal Information Processing Standard (FIPS), is shown in the table below. Copyright © 2010 Pearson Education, Inc.
Just concept n Password policies (For e-commerce site) n Ensure that password policies are enforced for shoppers and internal users. A sample password policy, defined as part of the Federal Information Processing Standard (FIPS), is shown in the table below. Copyright © 2010 Pearson Education, Inc.
 Just concept Copyright © 2010 Pearson Education, Inc.
Just concept Copyright © 2010 Pearson Education, Inc.
 Just concept (Technology - Solution) your system is only as secure as the people who use it. Education is the best way to ensure that your customers take appropriate precautions: Install personal firewalls for the client machines. Store confidential information in encrypted form. Encrypt the stream using the Secure Socket Layer (SSL) protocol to protect information flowing between the client and the e-Commerce Web site. Use appropriate password policies, firewalls, and routine external security audits. Use threat model analysis, strict development policies (if developing software by outsourcing), and external security audits Copyright © 2010 Pearson Education, Inc.
Just concept (Technology - Solution) your system is only as secure as the people who use it. Education is the best way to ensure that your customers take appropriate precautions: Install personal firewalls for the client machines. Store confidential information in encrypted form. Encrypt the stream using the Secure Socket Layer (SSL) protocol to protect information flowing between the client and the e-Commerce Web site. Use appropriate password policies, firewalls, and routine external security audits. Use threat model analysis, strict development policies (if developing software by outsourcing), and external security audits Copyright © 2010 Pearson Education, Inc.


