 Technology and National Security The Goal: Power Projection • The ability to use force around the world in pursuit of US political objectives – Firepower – Efficiency – Accuracy – Speed – coordination
Technology and National Security The Goal: Power Projection • The ability to use force around the world in pursuit of US political objectives – Firepower – Efficiency – Accuracy – Speed – coordination
 Technology and National Security • • PGMs RMA Cyber war? Robotics?
Technology and National Security • • PGMs RMA Cyber war? Robotics?
 Precision-Guided Munitions (PGMs) Thanh Hoa Bridge (after)
Precision-Guided Munitions (PGMs) Thanh Hoa Bridge (after)
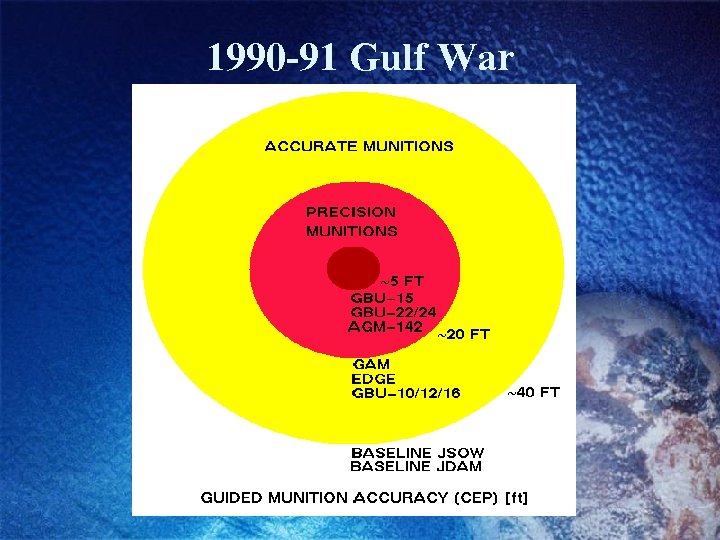 1990 -91 Gulf War
1990 -91 Gulf War
 Revolution in Military Affairs
Revolution in Military Affairs
 Lifting the Fog of War? US “Information Dominance” China’s response: Qiao Liang and Wang Xiangsui. Unrestricted Warfare (Beijing: PLA Literature and Arts Publishing House, February 1999)
Lifting the Fog of War? US “Information Dominance” China’s response: Qiao Liang and Wang Xiangsui. Unrestricted Warfare (Beijing: PLA Literature and Arts Publishing House, February 1999)
 Cyberspace: The New Realm of Warfare
Cyberspace: The New Realm of Warfare
 Cyber… 1. C 4 ISR 2. Cyberespionage 3. Critical Infrastructure Vulnerability 4. Cyberwar 1. Offensive 2. Defensive
Cyber… 1. C 4 ISR 2. Cyberespionage 3. Critical Infrastructure Vulnerability 4. Cyberwar 1. Offensive 2. Defensive
 1. C 4 ISR US military dependence on computers for: • • Command Control Communications Computers (internet, networks) Intelligence Surveillance Reconnaissance
1. C 4 ISR US military dependence on computers for: • • Command Control Communications Computers (internet, networks) Intelligence Surveillance Reconnaissance
 C 4 ISR • What we want: Dominance • Basic reality: Dependence • What we fear: Vulnerability
C 4 ISR • What we want: Dominance • Basic reality: Dependence • What we fear: Vulnerability
 2. Cyberespionage • Theft of material • Misinformation and alteration of data • Disruption of activities and communications • 21 st century spy game • Identification and attribution
2. Cyberespionage • Theft of material • Misinformation and alteration of data • Disruption of activities and communications • 21 st century spy game • Identification and attribution
 3. Critical Infrastructure Vulnerability
3. Critical Infrastructure Vulnerability
 4. Cyberwar?
4. Cyberwar?
 Real? 1. War just fought computer vs. computer 2. Cyber as an adjunct to traditional war
Real? 1. War just fought computer vs. computer 2. Cyber as an adjunct to traditional war
 US Cyber Command
US Cyber Command
 • Cyber deterrence – By punishment – By denial • • Cyber capability race Cyber-war/espionage control treaties? US-China Agreements 2015 “The Critical Infrastructure Non. Disruption Treaty”
• Cyber deterrence – By punishment – By denial • • Cyber capability race Cyber-war/espionage control treaties? US-China Agreements 2015 “The Critical Infrastructure Non. Disruption Treaty”
 Robotics
Robotics
 1. Robots Everywhere?
1. Robots Everywhere?
 2. Military Robots • Packbot
2. Military Robots • Packbot
 3. Robots to Do Specific Tasks UAVs • Predator Drone
3. Robots to Do Specific Tasks UAVs • Predator Drone
 • MARCBOT UGV
• MARCBOT UGV
 • Cormorant USV
• Cormorant USV
 BCB/AAI SQ-4 RECON Nano Quad-Rotor MAV/UAS/UAV (Micro Air Vehicle/Unmanned Aircraft System/Unmanned Aerial Vehicle)
BCB/AAI SQ-4 RECON Nano Quad-Rotor MAV/UAS/UAV (Micro Air Vehicle/Unmanned Aircraft System/Unmanned Aerial Vehicle)
 4. Robots Replacing Humans? • Autonomous Battlefield Robots?
4. Robots Replacing Humans? • Autonomous Battlefield Robots?
 Special Weapons Observation Reconnaissance Detection System (SWORDS)
Special Weapons Observation Reconnaissance Detection System (SWORDS)
 US Strategy • Quality over Quantity • Technological Superiority • Since WW II – Offset Strategies
US Strategy • Quality over Quantity • Technological Superiority • Since WW II – Offset Strategies
 First Offset Strategy: Eisenhower’s New Look (1950 s) The Problem The Solution
First Offset Strategy: Eisenhower’s New Look (1950 s) The Problem The Solution
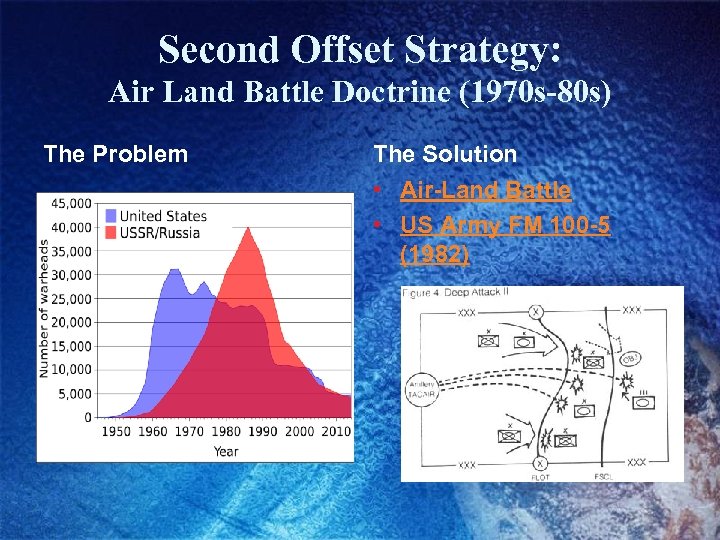 Second Offset Strategy: Air Land Battle Doctrine (1970 s-80 s) The Problem The Solution • Air-Land Battle • US Army FM 100 -5 (1982)
Second Offset Strategy: Air Land Battle Doctrine (1970 s-80 s) The Problem The Solution • Air-Land Battle • US Army FM 100 -5 (1982)
 Third Offset Strategy: Technology The Problem: • Anti-Access/Area-Denial strategies (A 2 AD) China’s DF-21 D Anti-ship Ballistic Missile
Third Offset Strategy: Technology The Problem: • Anti-Access/Area-Denial strategies (A 2 AD) China’s DF-21 D Anti-ship Ballistic Missile
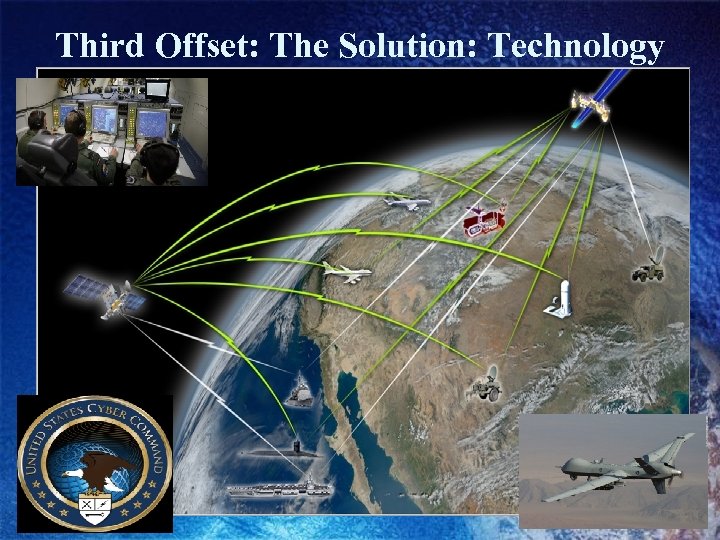 Third Offset: The Solution: Technology
Third Offset: The Solution: Technology
 Third Offset: The Difference 1. Speed of technological change 2. Range of adversaries 3. Private sector drives technological change
Third Offset: The Difference 1. Speed of technological change 2. Range of adversaries 3. Private sector drives technological change