3832dbcdd488f4bbf4aaeed4ab6af9e5.ppt
- Количество слайдов: 33
 Technologies for IPR and data protection Theodore S. Papatheodorou & Dimitris K. Tsolis (University of Patras) Vito Cappellini & Alessandro Piva (University of Florence) Parma, 21 November 2003
Technologies for IPR and data protection Theodore S. Papatheodorou & Dimitris K. Tsolis (University of Patras) Vito Cappellini & Alessandro Piva (University of Florence) Parma, 21 November 2003
 Historical Note • “Technologies for IPR and Data Protection”: – Appeared firstly during the NRG meeting at Corfu (Greek Presidency – 26 th June 2003). – Is a joint initiative of Greece and Italy. Useful contributions were made by Mr. David Dawson (UK).
Historical Note • “Technologies for IPR and Data Protection”: – Appeared firstly during the NRG meeting at Corfu (Greek Presidency – 26 th June 2003). – Is a joint initiative of Greece and Italy. Useful contributions were made by Mr. David Dawson (UK).
 Introduction • Objectives of the presentation. – Summarize technological solutions for copyright protection and management, which are proposed, implemented and applied to cultural applications, European projects, etc. – Collect recommendations, key points and limitations of these technological solutions.
Introduction • Objectives of the presentation. – Summarize technological solutions for copyright protection and management, which are proposed, implemented and applied to cultural applications, European projects, etc. – Collect recommendations, key points and limitations of these technological solutions.
 IPR & IST • IPR protection and management is an issue that is gradually becoming critical: – Advances in technology have improved the ability to reproduce, distribute, manage and publish information. – The information structure has been integrated into everyday life, affecting directly, amongst others, the IPR legislation. – Lack of awareness of both content holders and content users is observed.
IPR & IST • IPR protection and management is an issue that is gradually becoming critical: – Advances in technology have improved the ability to reproduce, distribute, manage and publish information. – The information structure has been integrated into everyday life, affecting directly, amongst others, the IPR legislation. – Lack of awareness of both content holders and content users is observed.
 Technological Solutions Overview Proposals and Practices across MS are mainly focusing on: – How to provide access without giving up control. A complete technological schema includes: 1. Technical Protection Means (TPM). ð A TPM is a technology that supports users, content owners and organizations to secure and protect digital content (text, image, video, sound, graphics) from unauthorized use. The definition implies the traceability of an improper use. 2. ð Digital Rights Management Systems (DRMS). Systems which are supporting the management of rights of digital content for providers and users including time and usage based business models.
Technological Solutions Overview Proposals and Practices across MS are mainly focusing on: – How to provide access without giving up control. A complete technological schema includes: 1. Technical Protection Means (TPM). ð A TPM is a technology that supports users, content owners and organizations to secure and protect digital content (text, image, video, sound, graphics) from unauthorized use. The definition implies the traceability of an improper use. 2. ð Digital Rights Management Systems (DRMS). Systems which are supporting the management of rights of digital content for providers and users including time and usage based business models.
 TPM / DRM & Legislation • TPM / DRM are legally protected by the EC Directive 2001/29, from acts of circumvention and other attacks. • Legislation harmonization for all MS is required.
TPM / DRM & Legislation • TPM / DRM are legally protected by the EC Directive 2001/29, from acts of circumvention and other attacks. • Legislation harmonization for all MS is required.
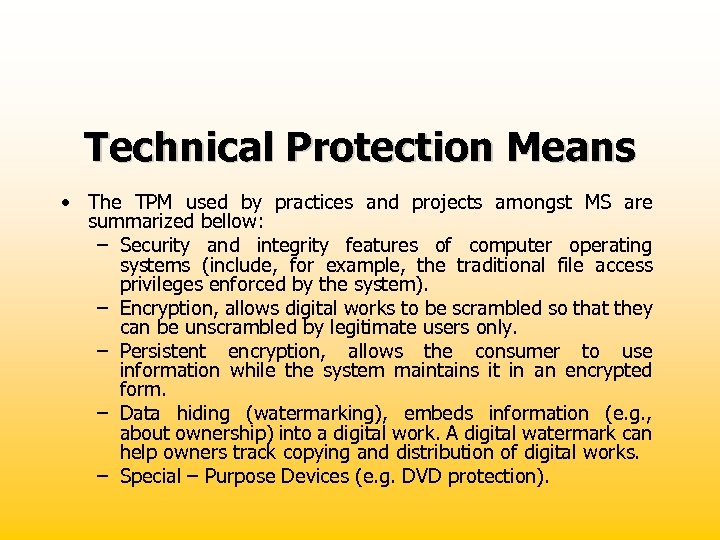 Technical Protection Means • The TPM used by practices and projects amongst MS are summarized bellow: – Security and integrity features of computer operating systems (include, for example, the traditional file access privileges enforced by the system). – Encryption, allows digital works to be scrambled so that they can be unscrambled by legitimate users only. – Persistent encryption, allows the consumer to use information while the system maintains it in an encrypted form. – Data hiding (watermarking), embeds information (e. g. , about ownership) into a digital work. A digital watermark can help owners track copying and distribution of digital works. – Special – Purpose Devices (e. g. DVD protection).
Technical Protection Means • The TPM used by practices and projects amongst MS are summarized bellow: – Security and integrity features of computer operating systems (include, for example, the traditional file access privileges enforced by the system). – Encryption, allows digital works to be scrambled so that they can be unscrambled by legitimate users only. – Persistent encryption, allows the consumer to use information while the system maintains it in an encrypted form. – Data hiding (watermarking), embeds information (e. g. , about ownership) into a digital work. A digital watermark can help owners track copying and distribution of digital works. – Special – Purpose Devices (e. g. DVD protection).
 Data Hiding • Multidisciplinary research field that combines signal processing with cryptography, communication and coding theory. • Data hiding techniques were first applied to copyright protection applications. • Used to verify whether the content has been modified since its distribution. Fragile watermarks. • Used to embed hidden labels and annotations into the host data. Robust watermarks.
Data Hiding • Multidisciplinary research field that combines signal processing with cryptography, communication and coding theory. • Data hiding techniques were first applied to copyright protection applications. • Used to verify whether the content has been modified since its distribution. Fragile watermarks. • Used to embed hidden labels and annotations into the host data. Robust watermarks.
 What makes a TPM successful? • Usability. A difficult to use protection system may discourage users from using it. • Appropriateness to the content. The cost of designing, developing, and deploying the system has to be in harmony with the type of the content. – For inexpensive content which is already available in a reasonably priced, non-Internet medium, there is no point to an expensive TPM that drives up the price of Internet delivery. • Appropriateness to the threat. Preventing honest customers from making copies may require nothing more that a reasonably priced product, a good distribution system, and a clear set of instructions. – Preventing “electronic theft” of extremely valuable content that must at some point reside to a computer network requires a very sophisticated TPM, and even the best available with current technology may not be efficient. • The cost-benefit analysis is difficult but necessary.
What makes a TPM successful? • Usability. A difficult to use protection system may discourage users from using it. • Appropriateness to the content. The cost of designing, developing, and deploying the system has to be in harmony with the type of the content. – For inexpensive content which is already available in a reasonably priced, non-Internet medium, there is no point to an expensive TPM that drives up the price of Internet delivery. • Appropriateness to the threat. Preventing honest customers from making copies may require nothing more that a reasonably priced product, a good distribution system, and a clear set of instructions. – Preventing “electronic theft” of extremely valuable content that must at some point reside to a computer network requires a very sophisticated TPM, and even the best available with current technology may not be efficient. • The cost-benefit analysis is difficult but necessary.
 Digital Rights Management - 1 – Identification Systems. Aiming at facilitating persistent identification and interoperable exchange of Intellectual Property on digital networks • Persistent URLS. Digital Object Identifier. • Custom made identification systems. – Metadata for IPR management. Dublin Core and DIG 35. – Languages. Programming languages based on metadata sets and W 3 C standards: • Extensible Access Control Markup Language, OASIS Rights Language, Extensible Rights Markup Language, IEEE LTSC DREL Project, INDECS – Rights Data Dictionary, MPEG Rights Expression Language, Open Digital Rights Language.
Digital Rights Management - 1 – Identification Systems. Aiming at facilitating persistent identification and interoperable exchange of Intellectual Property on digital networks • Persistent URLS. Digital Object Identifier. • Custom made identification systems. – Metadata for IPR management. Dublin Core and DIG 35. – Languages. Programming languages based on metadata sets and W 3 C standards: • Extensible Access Control Markup Language, OASIS Rights Language, Extensible Rights Markup Language, IEEE LTSC DREL Project, INDECS – Rights Data Dictionary, MPEG Rights Expression Language, Open Digital Rights Language.
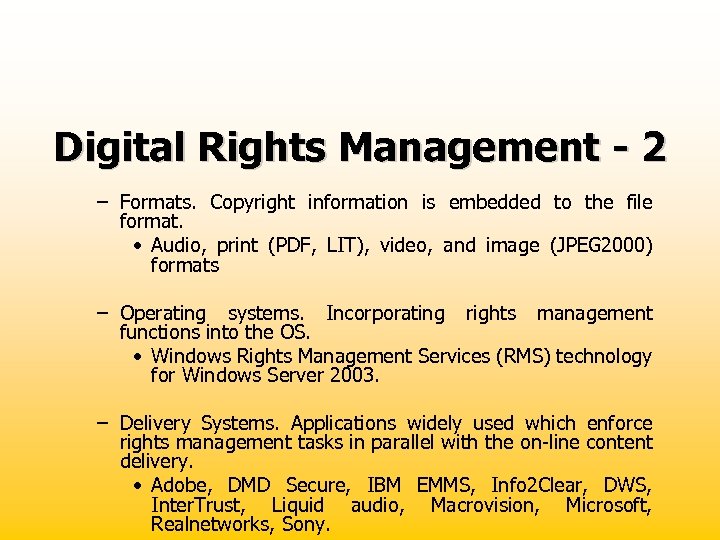 Digital Rights Management - 2 – Formats. Copyright information is embedded to the file format. • Audio, print (PDF, LIT), video, and image (JPEG 2000) formats – Operating systems. Incorporating rights management functions into the OS. • Windows Rights Management Services (RMS) technology for Windows Server 2003. – Delivery Systems. Applications widely used which enforce rights management tasks in parallel with the on-line content delivery. • Adobe, DMD Secure, IBM EMMS, Info 2 Clear, DWS, Inter. Trust, Liquid audio, Macrovision, Microsoft, Realnetworks, Sony.
Digital Rights Management - 2 – Formats. Copyright information is embedded to the file format. • Audio, print (PDF, LIT), video, and image (JPEG 2000) formats – Operating systems. Incorporating rights management functions into the OS. • Windows Rights Management Services (RMS) technology for Windows Server 2003. – Delivery Systems. Applications widely used which enforce rights management tasks in parallel with the on-line content delivery. • Adobe, DMD Secure, IBM EMMS, Info 2 Clear, DWS, Inter. Trust, Liquid audio, Macrovision, Microsoft, Realnetworks, Sony.
 What makes a DRM successful? – Interoperability. Rights expression languages is the key to interoperability. – Security in DRM. Pointer to TPM. – Usability. – Licensing negotiations tend to be extremely lengthy in practice. An adaptation to a more efficient electronic licensing model is necessary. – Reasonable Costs of DRM technologies. – Business Models. A DRM should be based upon a clear and welldefined business model.
What makes a DRM successful? – Interoperability. Rights expression languages is the key to interoperability. – Security in DRM. Pointer to TPM. – Usability. – Licensing negotiations tend to be extremely lengthy in practice. An adaptation to a more efficient electronic licensing model is necessary. – Reasonable Costs of DRM technologies. – Business Models. A DRM should be based upon a clear and welldefined business model.
 A Business Model - 1 • IMPRIMATUR Project, TRADEX. • Management of policies. – in DRM systems a policy is a conditional statement describing how to handle actions attempted on the content by an authorised user. • Players - Entities. The key entities can be listed as: – The author, who will be the creator of the copyrighted work. – The rights-holder (or copyright owner). – The creation provider (or service producer). – The media distributor (or service provider). – The IPR register or database. – The Unique Number issuer. – The controller. – The certification authority. – The purchaser.
A Business Model - 1 • IMPRIMATUR Project, TRADEX. • Management of policies. – in DRM systems a policy is a conditional statement describing how to handle actions attempted on the content by an authorised user. • Players - Entities. The key entities can be listed as: – The author, who will be the creator of the copyrighted work. – The rights-holder (or copyright owner). – The creation provider (or service producer). – The media distributor (or service provider). – The IPR register or database. – The Unique Number issuer. – The controller. – The certification authority. – The purchaser.
 A Business Model - 2 The transactions: • Transfer of the work: the work object of the trading can be transferred from the creator, to the creation provider, then to the media distributor and finally to the purchaser. • Transfer of values: this is the exchange of money given for compensating the use of the multimedia work. • Assignment of rights: the rights on the multimedia creation can be transferred from the original creator to a rights-holder. • Assignment of a unique number identifier: this is requested by the creation provider and provided by the unique number issuer. • Transfer of IPR information: it is usually the rights-holder that is charged to upload the correct IPR information into the IPR database, making them available for the other parties.
A Business Model - 2 The transactions: • Transfer of the work: the work object of the trading can be transferred from the creator, to the creation provider, then to the media distributor and finally to the purchaser. • Transfer of values: this is the exchange of money given for compensating the use of the multimedia work. • Assignment of rights: the rights on the multimedia creation can be transferred from the original creator to a rights-holder. • Assignment of a unique number identifier: this is requested by the creation provider and provided by the unique number issuer. • Transfer of IPR information: it is usually the rights-holder that is charged to upload the correct IPR information into the IPR database, making them available for the other parties.
 Key & Open Issues, Technical – 1 • Technology provides means and not answers to social, legal and economic questions. • There is not a TPM that can protect perfectly. Technology changes rapidly, making previously secure systems progressively less secure. • The key measure of success for a TPM / DRM system is that it should make easier for users to be honest, rather than placing major barriers in their access to digital content. • Some TPM are designed to keep honest people honest and others (more ambitious) provide for robust security. • The quality and cost of a TPM / DRM should be in harmony with the resources it protects. • TPM / DRM almost invariably cause some inconvenience to the user.
Key & Open Issues, Technical – 1 • Technology provides means and not answers to social, legal and economic questions. • There is not a TPM that can protect perfectly. Technology changes rapidly, making previously secure systems progressively less secure. • The key measure of success for a TPM / DRM system is that it should make easier for users to be honest, rather than placing major barriers in their access to digital content. • Some TPM are designed to keep honest people honest and others (more ambitious) provide for robust security. • The quality and cost of a TPM / DRM should be in harmony with the resources it protects. • TPM / DRM almost invariably cause some inconvenience to the user.
 Key & Open Issues, Technical – 2 • While TPM and DRM are often viewed as tools for providing financial profit, this view point is too narrow. Technical protection offers additional important services, including verifying the authenticity of information and of the users involved in the content transactions. • A TPM will not (probably) contribute to an increase of revenue. • Technical implementations of protection mechanisms are difficult to sustain because of annual renewal costs • In one vision of the future, implementations are leading to the development and widespread adoption of hardware based, endto-end systems that facilitate control of digital IP. These “trusted systems” constitute an open research area.
Key & Open Issues, Technical – 2 • While TPM and DRM are often viewed as tools for providing financial profit, this view point is too narrow. Technical protection offers additional important services, including verifying the authenticity of information and of the users involved in the content transactions. • A TPM will not (probably) contribute to an increase of revenue. • Technical implementations of protection mechanisms are difficult to sustain because of annual renewal costs • In one vision of the future, implementations are leading to the development and widespread adoption of hardware based, endto-end systems that facilitate control of digital IP. These “trusted systems” constitute an open research area.
 Open Issues - Standards • Further standardization of emerging technologies for IPR protection is an open issue. • Even if certain practices have been promoted, the incorporation of trust management elements in existing IPR standards is an open issue too. • There is no common agreement of the resolution of images and the format of multi-media content that should be made publicly accessible.
Open Issues - Standards • Further standardization of emerging technologies for IPR protection is an open issue. • Even if certain practices have been promoted, the incorporation of trust management elements in existing IPR standards is an open issue too. • There is no common agreement of the resolution of images and the format of multi-media content that should be made publicly accessible.
 Open Issues - Other Business Models • A model for enabling the use of materials for e. Learning does not exist and is considered necessary. • There are few models that enable true publiclyaccessible digital libraries. • Only those policies that can be reliably expressed through binary decisions (yes/no) can be automated successfully. • There could be a role for a Trusted Third Party to act on behalf of the Cultural Sector.
Open Issues - Other Business Models • A model for enabling the use of materials for e. Learning does not exist and is considered necessary. • There are few models that enable true publiclyaccessible digital libraries. • Only those policies that can be reliably expressed through binary decisions (yes/no) can be automated successfully. • There could be a role for a Trusted Third Party to act on behalf of the Cultural Sector.
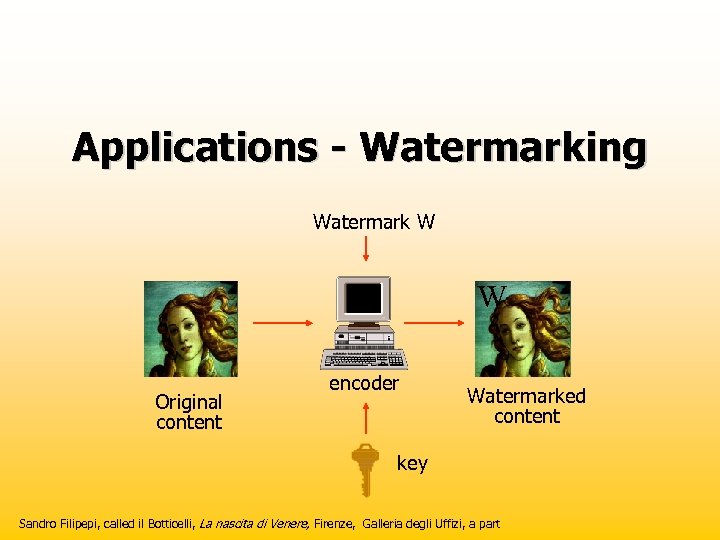 Applications - Watermarking Watermark W W Original content encoder Watermarked content key Sandro Filipepi, called il Botticelli, La nascita di Venere, Firenze, Galleria degli Uffizi, a part
Applications - Watermarking Watermark W W Original content encoder Watermarked content key Sandro Filipepi, called il Botticelli, La nascita di Venere, Firenze, Galleria degli Uffizi, a part
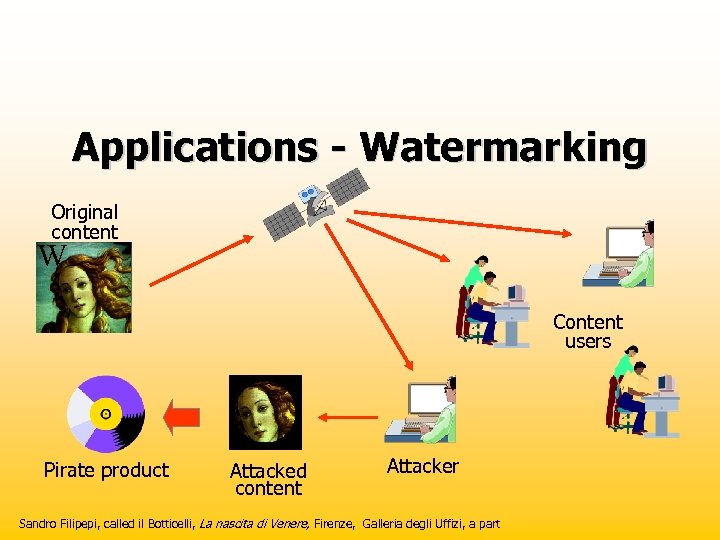 Applications - Watermarking Original content W Content users Pirate product Attacked content Attacker Sandro Filipepi, called il Botticelli, La nascita di Venere, Firenze, Galleria degli Uffizi, a part
Applications - Watermarking Original content W Content users Pirate product Attacked content Attacker Sandro Filipepi, called il Botticelli, La nascita di Venere, Firenze, Galleria degli Uffizi, a part
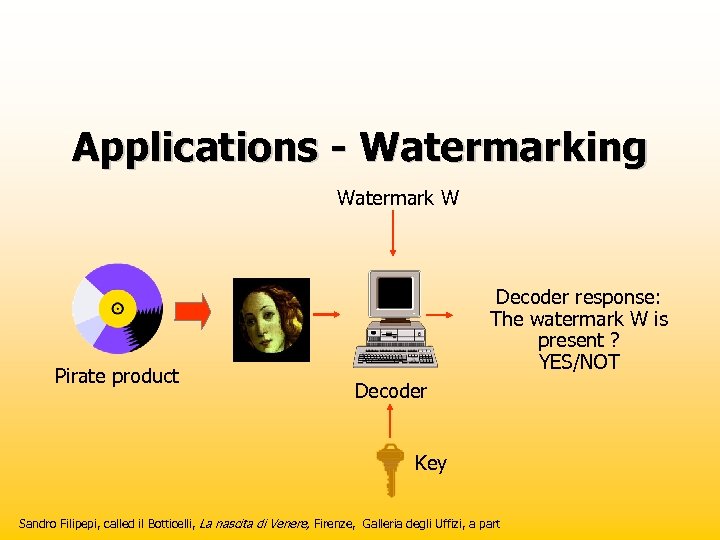 Applications - Watermarking Watermark W Pirate product Decoder response: The watermark W is present ? YES/NOT Decoder Key Sandro Filipepi, called il Botticelli, La nascita di Venere, Firenze, Galleria degli Uffizi, a part
Applications - Watermarking Watermark W Pirate product Decoder response: The watermark W is present ? YES/NOT Decoder Key Sandro Filipepi, called il Botticelli, La nascita di Venere, Firenze, Galleria degli Uffizi, a part
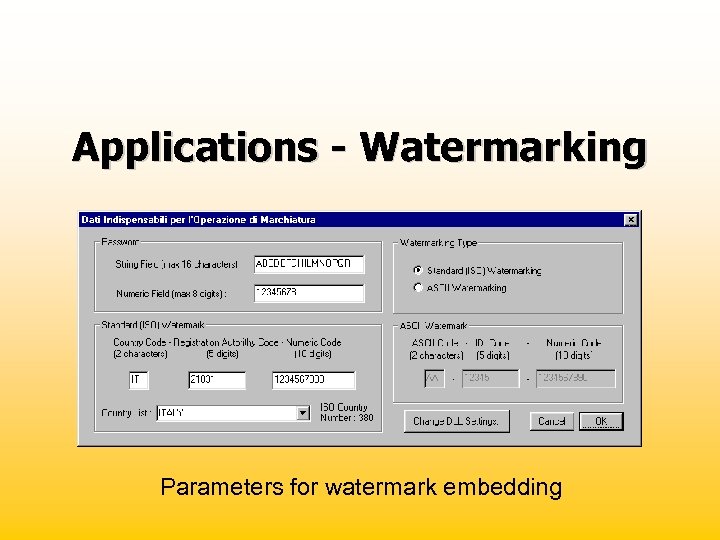 Applications - Watermarking Parameters for watermark embedding
Applications - Watermarking Parameters for watermark embedding
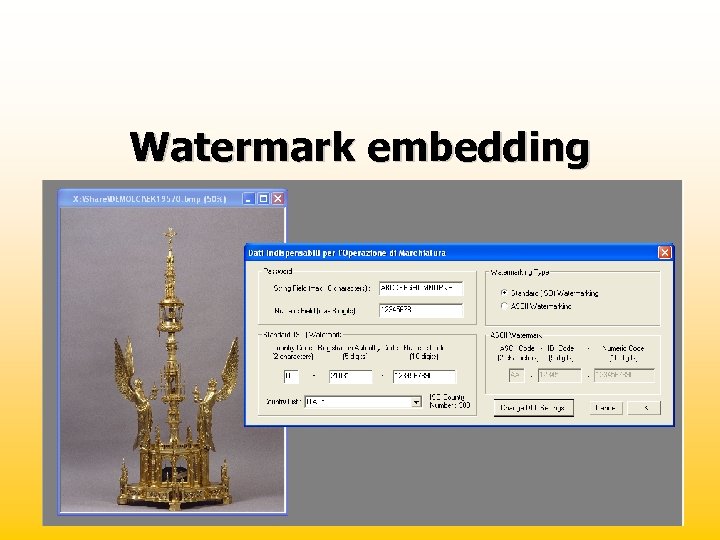 Watermark embedding
Watermark embedding
 Watermark embedding
Watermark embedding
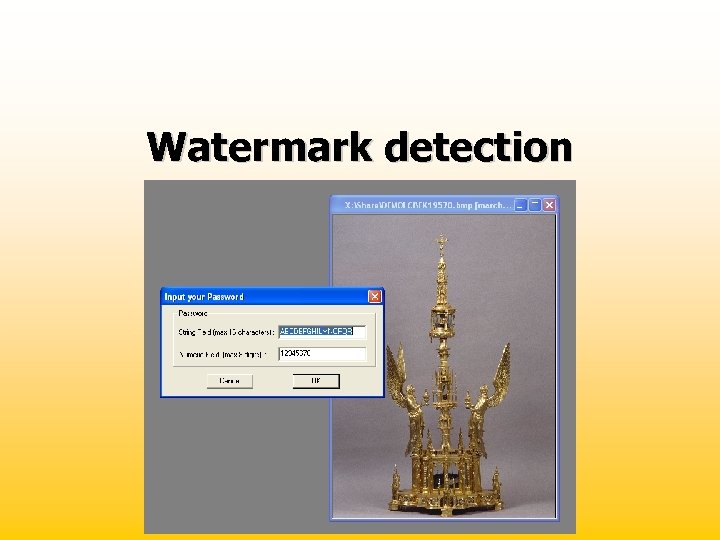 Watermark detection
Watermark detection
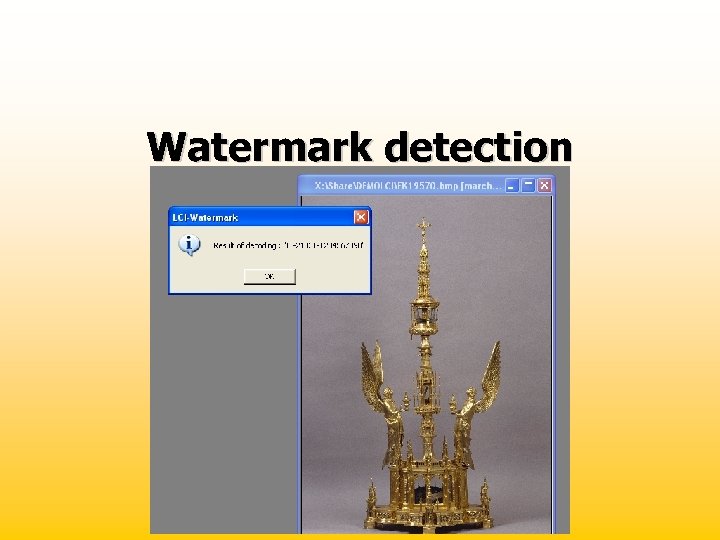 Watermark detection
Watermark detection
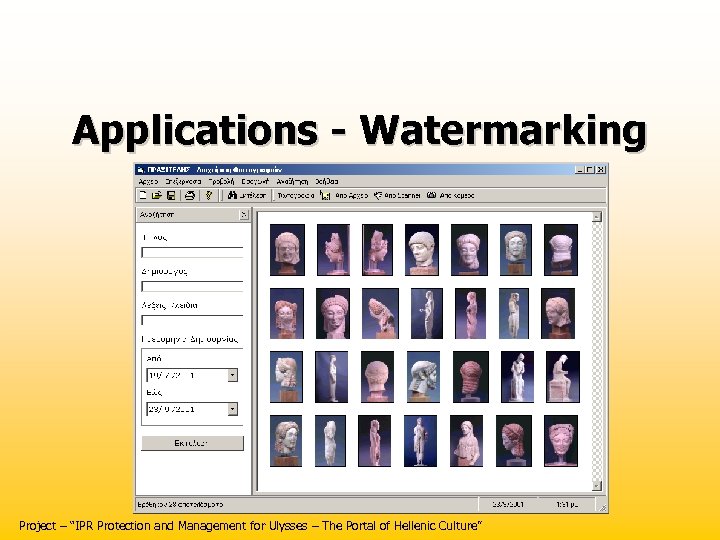 Applications - Watermarking Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
Applications - Watermarking Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
 Image Management Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
Image Management Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
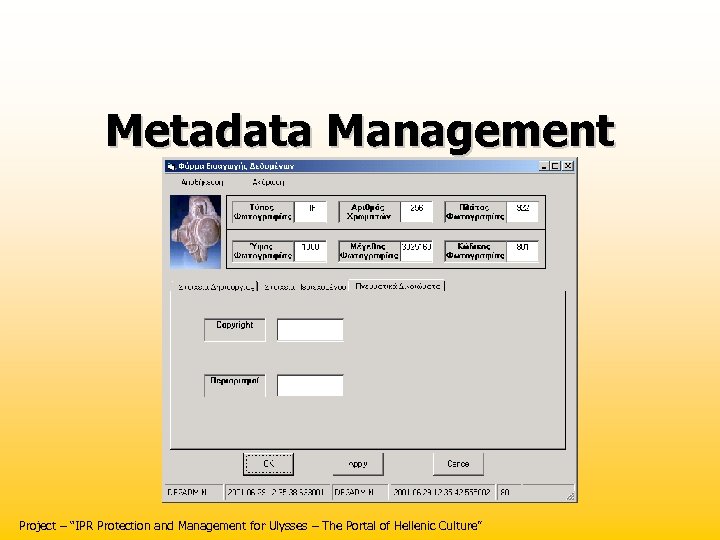 Metadata Management Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
Metadata Management Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
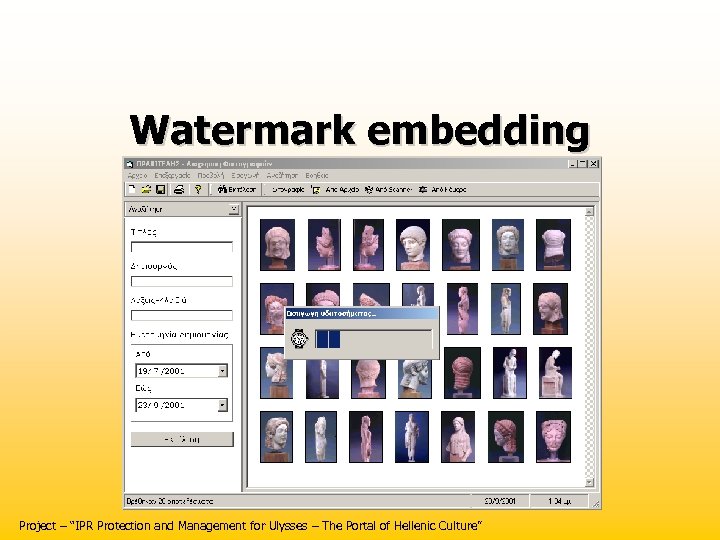 Watermark embedding Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
Watermark embedding Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
 Watermark detection Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
Watermark detection Project – “IPR Protection and Management for Ulysses – The Portal of Hellenic Culture”
 Acropolis CD-Rom Project – “Acropolis CD-ROM”
Acropolis CD-Rom Project – “Acropolis CD-ROM”
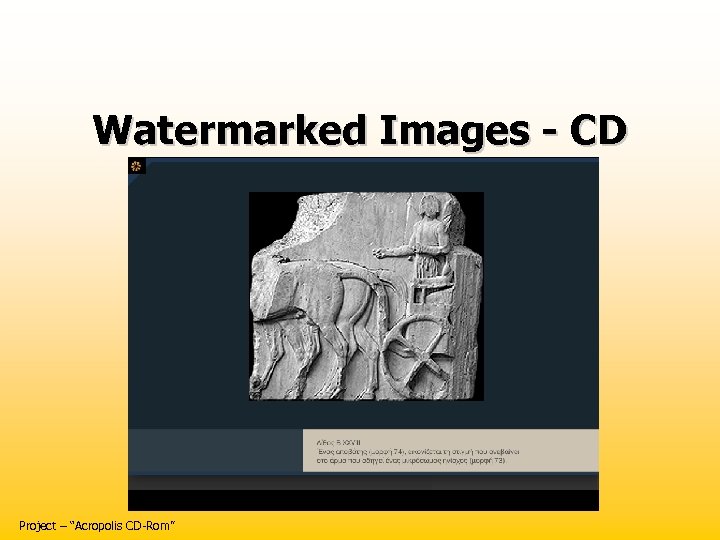 Watermarked Images - CD Project – “Acropolis CD-Rom”
Watermarked Images - CD Project – “Acropolis CD-Rom”


