7b3eb69a58a74a21a1045a50dfe509cd.ppt
- Количество слайдов: 11
 TC 57 IEC TC 57 WG 15 - Security Status & Roadmap, July 2008 Frances Cleveland Convenor WG 15
TC 57 IEC TC 57 WG 15 - Security Status & Roadmap, July 2008 Frances Cleveland Convenor WG 15
 TC 57 Scope of WG 15 on Security 4 Undertake the development of standards for security of the communication protocols defined by the IEC TC 57, specifically the IEC 60870 -5 series, the IEC 60870 -6 series, the IEC 61850 series, the IEC 61970 series, and the IEC 61968 series. 4 Undertake the development of standards and/or technical reports on end-to-end security issues. WG 15 Status October 2007 3
TC 57 Scope of WG 15 on Security 4 Undertake the development of standards for security of the communication protocols defined by the IEC TC 57, specifically the IEC 60870 -5 series, the IEC 60870 -6 series, the IEC 61850 series, the IEC 61970 series, and the IEC 61968 series. 4 Undertake the development of standards and/or technical reports on end-to-end security issues. WG 15 Status October 2007 3
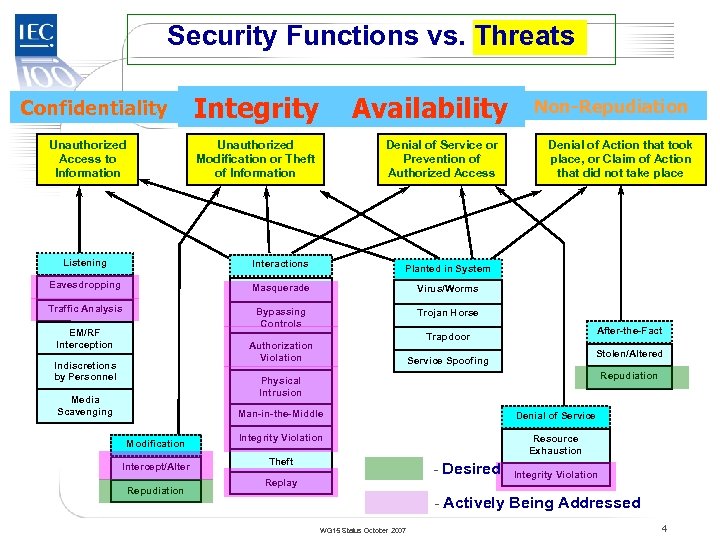 Security Functions vs. Threats TC 57 Confidentiality Unauthorized Access to Information Integrity Availability Unauthorized Modification or Theft of Information Denial of Service or Prevention of Authorized Access Listening Interactions Masquerade Virus/Worms Traffic Analysis Bypassing Controls Denial of Action that took place, or Claim of Action that did not take place Planted in System Eavesdropping Non-Repudiation Trojan Horse EM/RF Interception Authorization Violation Indiscretions by Personnel After-the-Fact Trapdoor Stolen/Altered Service Spoofing Repudiation Physical Intrusion Media Scavenging Man-in-the-Middle Modification Intercept/Alter Repudiation Denial of Service Integrity Violation Resource Exhaustion Theft - Desired Replay Integrity Violation - Actively Being Addressed WG 15 Status October 2007 4
Security Functions vs. Threats TC 57 Confidentiality Unauthorized Access to Information Integrity Availability Unauthorized Modification or Theft of Information Denial of Service or Prevention of Authorized Access Listening Interactions Masquerade Virus/Worms Traffic Analysis Bypassing Controls Denial of Action that took place, or Claim of Action that did not take place Planted in System Eavesdropping Non-Repudiation Trojan Horse EM/RF Interception Authorization Violation Indiscretions by Personnel After-the-Fact Trapdoor Stolen/Altered Service Spoofing Repudiation Physical Intrusion Media Scavenging Man-in-the-Middle Modification Intercept/Alter Repudiation Denial of Service Integrity Violation Resource Exhaustion Theft - Desired Replay Integrity Violation - Actively Being Addressed WG 15 Status October 2007 4
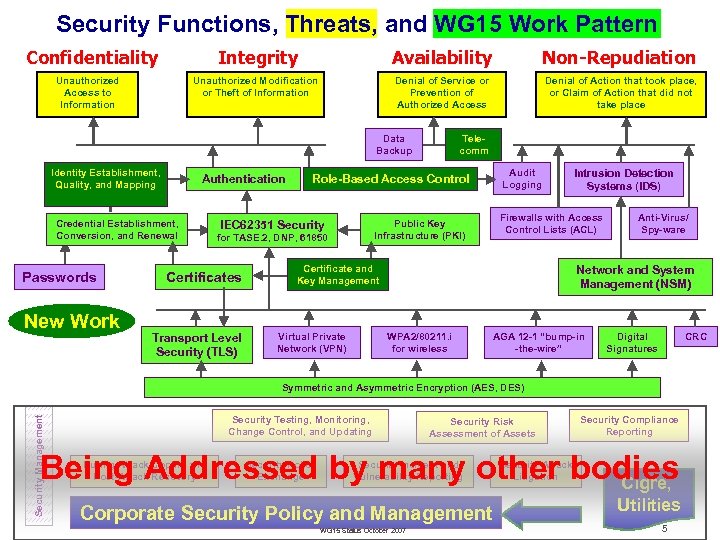 Security Functions, Threats, and WG 15 Work Pattern Integrity Availability Non-Repudiation Unauthorized Modification or Theft of Information Denial of Service or Prevention of Authorized Access Denial of Action that took place, or Claim of Action that did not take place Confidentiality Unauthorized Access to Information Data Backup Identity Establishment, Quality, and Mapping Authentication Credential Establishment, Conversion, and Renewal Passwords New Work Certificate and Key Management Virtual Private Network (VPN) Intrusion Detection Systems (IDS) Firewalls with Access Control Lists (ACL) Public Key Infrastructure (PKI) for TASE. 2, DNP, 61850 Transport Level Security (TLS) Audit Logging Role-Based Access Control IEC 62351 Security Certificates Telecomm Anti-Virus/ Spy-ware Network and System Management (NSM) WPA 2/80211. i for wireless AGA 12 -1 “bump-in -the-wire” Digital Signatures CRC Security Management Symmetric and Asymmetric Encryption (AES, DES) Security Testing, Monitoring, Change Control, and Updating Security Risk Assessment of Assets Security Compliance Reporting Being Addressed by many other bodies Cigre, During-Attack Coping and Post-Attack Recovery Security Policy Exchange Security Incident and Vulnerability Reporting Corporate Security Policy and Management WG 15 Status October 2007 Security Attack Litigation Utilities 5
Security Functions, Threats, and WG 15 Work Pattern Integrity Availability Non-Repudiation Unauthorized Modification or Theft of Information Denial of Service or Prevention of Authorized Access Denial of Action that took place, or Claim of Action that did not take place Confidentiality Unauthorized Access to Information Data Backup Identity Establishment, Quality, and Mapping Authentication Credential Establishment, Conversion, and Renewal Passwords New Work Certificate and Key Management Virtual Private Network (VPN) Intrusion Detection Systems (IDS) Firewalls with Access Control Lists (ACL) Public Key Infrastructure (PKI) for TASE. 2, DNP, 61850 Transport Level Security (TLS) Audit Logging Role-Based Access Control IEC 62351 Security Certificates Telecomm Anti-Virus/ Spy-ware Network and System Management (NSM) WPA 2/80211. i for wireless AGA 12 -1 “bump-in -the-wire” Digital Signatures CRC Security Management Symmetric and Asymmetric Encryption (AES, DES) Security Testing, Monitoring, Change Control, and Updating Security Risk Assessment of Assets Security Compliance Reporting Being Addressed by many other bodies Cigre, During-Attack Coping and Post-Attack Recovery Security Policy Exchange Security Incident and Vulnerability Reporting Corporate Security Policy and Management WG 15 Status October 2007 Security Attack Litigation Utilities 5
 TC 57 Status of Security Documents, May 2007 4 IEC 62351: Data and Communications Security 4 Part 1: Introduction 4 Part 2: Glossary 4 Part 3: Security for profiles including TCP/IP 4 Part 4: Security for profiles including MMS 4 Part 5: Security for IEC 60870 -5 and derivatives 4 Part 6: Security for IEC 61850 profiles 4 Part 7: Objects for Network Management Issued as CD, (NWIP) Submitted as DTS ver 2 January 2007. Comments being awaited Submitted as Technical Specifications in Dec 2006, being finalized by IEC WG 15 Status October 2007 7
TC 57 Status of Security Documents, May 2007 4 IEC 62351: Data and Communications Security 4 Part 1: Introduction 4 Part 2: Glossary 4 Part 3: Security for profiles including TCP/IP 4 Part 4: Security for profiles including MMS 4 Part 5: Security for IEC 60870 -5 and derivatives 4 Part 6: Security for IEC 61850 profiles 4 Part 7: Objects for Network Management Issued as CD, (NWIP) Submitted as DTS ver 2 January 2007. Comments being awaited Submitted as Technical Specifications in Dec 2006, being finalized by IEC WG 15 Status October 2007 7
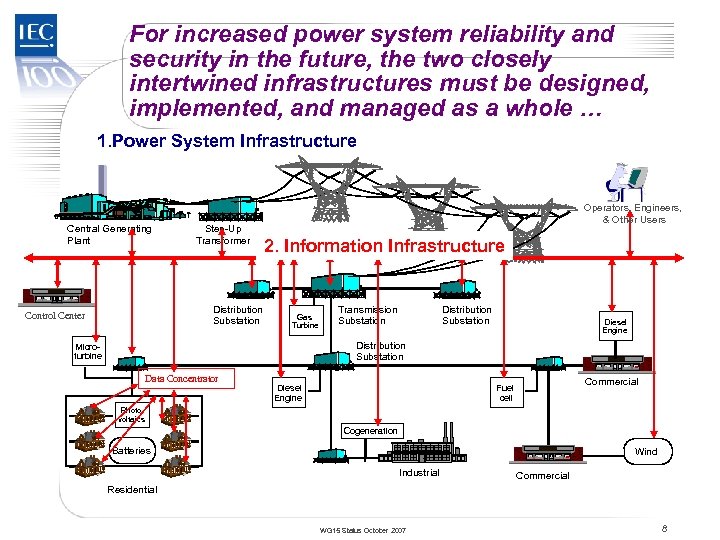 TC 57 For increased power system reliability and security in the future, the two closely intertwined infrastructures must be designed, implemented, and managed as a whole … 1. Power System Infrastructure Central Generating Plant Step-Up Transformer Distribution Substation Control Center Operators, Engineers, & Other Users 2. Information Infrastructure Gas Turbine Transmission Substation Distribution Substation Diesel Engine Distribution Substation Microturbine Data Concentrator Diesel Engine Commercial Fuel cell Photo voltaics Cogeneration Batteries Wind Industrial Commercial Residential WG 15 Status October 2007 8
TC 57 For increased power system reliability and security in the future, the two closely intertwined infrastructures must be designed, implemented, and managed as a whole … 1. Power System Infrastructure Central Generating Plant Step-Up Transformer Distribution Substation Control Center Operators, Engineers, & Other Users 2. Information Infrastructure Gas Turbine Transmission Substation Distribution Substation Diesel Engine Distribution Substation Microturbine Data Concentrator Diesel Engine Commercial Fuel cell Photo voltaics Cogeneration Batteries Wind Industrial Commercial Residential WG 15 Status October 2007 8
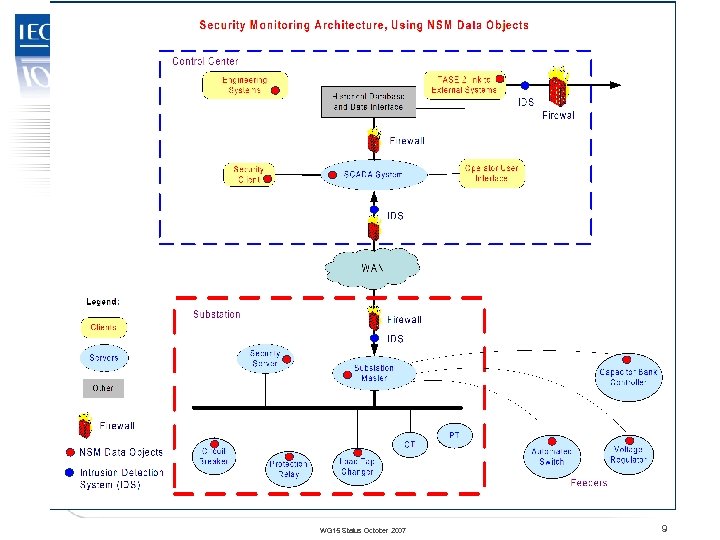 TC 57 Security Monitoring Architecture Using NSM WG 15 Status October 2007 9
TC 57 Security Monitoring Architecture Using NSM WG 15 Status October 2007 9
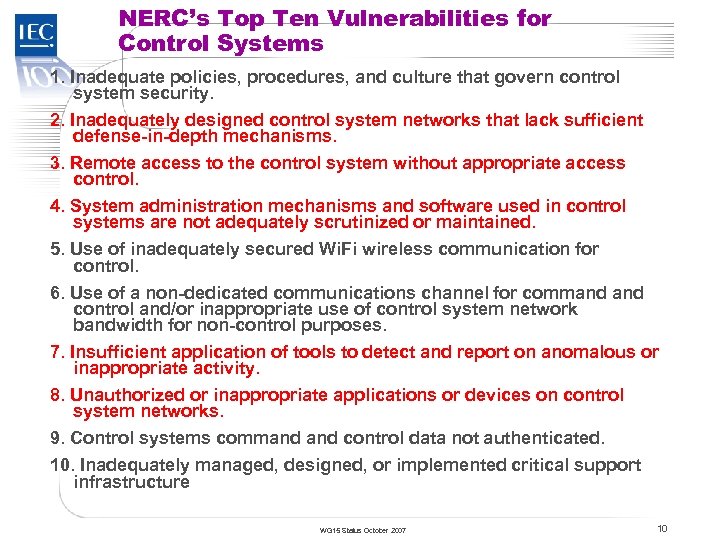 TC 57 NERC’s Top Ten Vulnerabilities for Control Systems 1. Inadequate policies, procedures, and culture that govern control system security. 2. Inadequately designed control system networks that lack sufficient defense-in-depth mechanisms. 3. Remote access to the control system without appropriate access control. 4. System administration mechanisms and software used in control systems are not adequately scrutinized or maintained. 5. Use of inadequately secured Wi. Fi wireless communication for control. 6. Use of a non-dedicated communications channel for command control and/or inappropriate use of control system network bandwidth for non-control purposes. 7. Insufficient application of tools to detect and report on anomalous or inappropriate activity. 8. Unauthorized or inappropriate applications or devices on control system networks. 9. Control systems command control data not authenticated. 10. Inadequately managed, designed, or implemented critical support infrastructure WG 15 Status October 2007 10
TC 57 NERC’s Top Ten Vulnerabilities for Control Systems 1. Inadequate policies, procedures, and culture that govern control system security. 2. Inadequately designed control system networks that lack sufficient defense-in-depth mechanisms. 3. Remote access to the control system without appropriate access control. 4. System administration mechanisms and software used in control systems are not adequately scrutinized or maintained. 5. Use of inadequately secured Wi. Fi wireless communication for control. 6. Use of a non-dedicated communications channel for command control and/or inappropriate use of control system network bandwidth for non-control purposes. 7. Insufficient application of tools to detect and report on anomalous or inappropriate activity. 8. Unauthorized or inappropriate applications or devices on control system networks. 9. Control systems command control data not authenticated. 10. Inadequately managed, designed, or implemented critical support infrastructure WG 15 Status October 2007 10
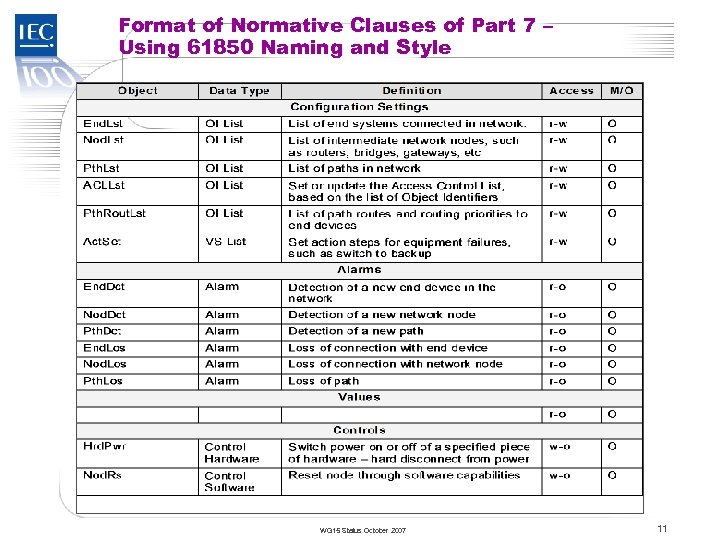 TC 57 Format of Normative Clauses of Part 7 – Using 61850 Naming and Style WG 15 Status October 2007 11
TC 57 Format of Normative Clauses of Part 7 – Using 61850 Naming and Style WG 15 Status October 2007 11
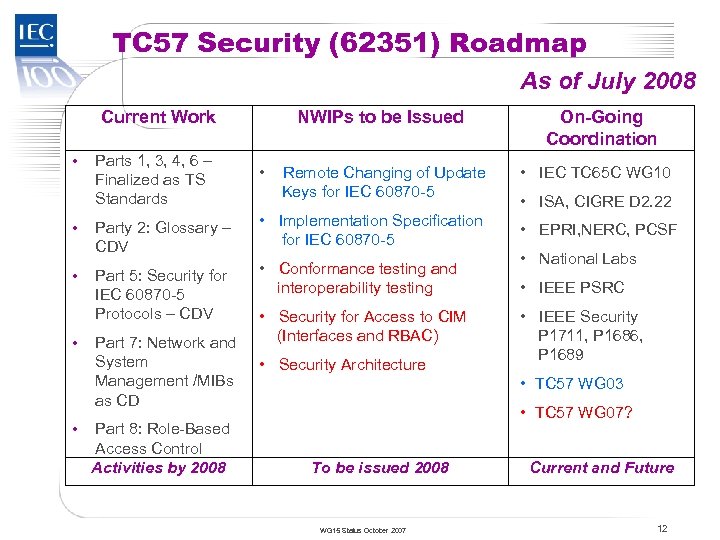 TC 57 Security (62351) Roadmap As of July 2008 Current Work • • • NWIPs to be Issued Parts 1, 3, 4, 6 – Finalized as TS Standards • Party 2: Glossary – CDV • Implementation Specification for IEC 60870 -5 Part 5: Security for IEC 60870 -5 Protocols – CDV • Conformance testing and interoperability testing Part 7: Network and System Management /MIBs as CD Part 8: Role-Based Access Control Activities by 2008 Remote Changing of Update Keys for IEC 60870 -5 • Security for Access to CIM (Interfaces and RBAC) • Security Architecture On-Going Coordination • IEC TC 65 C WG 10 • ISA, CIGRE D 2. 22 • EPRI, NERC, PCSF • National Labs • IEEE PSRC • IEEE Security P 1711, P 1686, P 1689 • TC 57 WG 03 • TC 57 WG 07? To be issued 2008 WG 15 Status October 2007 Current and Future 12
TC 57 Security (62351) Roadmap As of July 2008 Current Work • • • NWIPs to be Issued Parts 1, 3, 4, 6 – Finalized as TS Standards • Party 2: Glossary – CDV • Implementation Specification for IEC 60870 -5 Part 5: Security for IEC 60870 -5 Protocols – CDV • Conformance testing and interoperability testing Part 7: Network and System Management /MIBs as CD Part 8: Role-Based Access Control Activities by 2008 Remote Changing of Update Keys for IEC 60870 -5 • Security for Access to CIM (Interfaces and RBAC) • Security Architecture On-Going Coordination • IEC TC 65 C WG 10 • ISA, CIGRE D 2. 22 • EPRI, NERC, PCSF • National Labs • IEEE PSRC • IEEE Security P 1711, P 1686, P 1689 • TC 57 WG 03 • TC 57 WG 07? To be issued 2008 WG 15 Status October 2007 Current and Future 12
 TC 57 Role-Based Access Control 4 The scope of the proposed work is to define a specification for the use of Role Based Access Control not only in field devices but also for a whole system, consisting of field devices, station control and network control – the complete pyramid, in order to support end to end security. The specification will refer to the standards IEC 61970 CIM, IEC 61850 and IEC 62351 and also to ANSI INCITS 359 -2004. WG 15 Status October 2007 13
TC 57 Role-Based Access Control 4 The scope of the proposed work is to define a specification for the use of Role Based Access Control not only in field devices but also for a whole system, consisting of field devices, station control and network control – the complete pyramid, in order to support end to end security. The specification will refer to the standards IEC 61970 CIM, IEC 61850 and IEC 62351 and also to ANSI INCITS 359 -2004. WG 15 Status October 2007 13


