f11b7103cbb59a0665fd2ed7ec66b500.ppt
- Количество слайдов: 32
 SYZYGY Engineering Internet Protocol version 6 and Network Centric Operations Key Concepts Will Ivancic SYZYGY Engineering ivancic@syzygyengineering. com © 2004 Syzygy Engineering – Will Ivancic
SYZYGY Engineering Internet Protocol version 6 and Network Centric Operations Key Concepts Will Ivancic SYZYGY Engineering ivancic@syzygyengineering. com © 2004 Syzygy Engineering – Will Ivancic
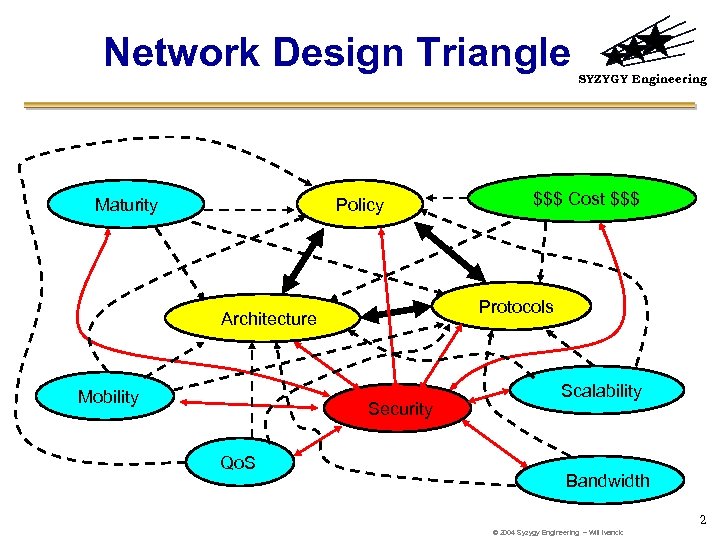 Network Design Triangle Maturity Policy Security Qo. S $$$ Cost $$$ Protocols Architecture Mobility SYZYGY Engineering Scalability Bandwidth 2 © 2004 Syzygy Engineering – Will Ivancic
Network Design Triangle Maturity Policy Security Qo. S $$$ Cost $$$ Protocols Architecture Mobility SYZYGY Engineering Scalability Bandwidth 2 © 2004 Syzygy Engineering – Will Ivancic
 Policy Source: http: //minhdo. bitterjerksociety. org/gallery/page_03. htm SYZYGY Engineering 3
Policy Source: http: //minhdo. bitterjerksociety. org/gallery/page_03. htm SYZYGY Engineering 3
 IPv 6 Functional Capabilities • Expanded Addressing and Routing • Simplified Header Format • Extension Headers and Options – Options are placed in separate headers after the core routing information – Options do not necessarily have to be processed in core network (speed) • Authentication and Encryption Support – Required in ALL implementations of IPv 6! © 2004 Syzygy Engineering – Will Ivancic SYZYGY Engineering • Autoconfiguration • Source Routing Support – Ad Hoc Network – Route Optimization for Mobility • Simple and Flexible Transition – – Incremental Upgrade Incremental Deployment Easy Addressing ( Low Startup Costs • Quality of Service Capabilities – Real-Time Traffic – Traffic Class – Flow labels 4
IPv 6 Functional Capabilities • Expanded Addressing and Routing • Simplified Header Format • Extension Headers and Options – Options are placed in separate headers after the core routing information – Options do not necessarily have to be processed in core network (speed) • Authentication and Encryption Support – Required in ALL implementations of IPv 6! © 2004 Syzygy Engineering – Will Ivancic SYZYGY Engineering • Autoconfiguration • Source Routing Support – Ad Hoc Network – Route Optimization for Mobility • Simple and Flexible Transition – – Incremental Upgrade Incremental Deployment Easy Addressing ( Low Startup Costs • Quality of Service Capabilities – Real-Time Traffic – Traffic Class – Flow labels 4
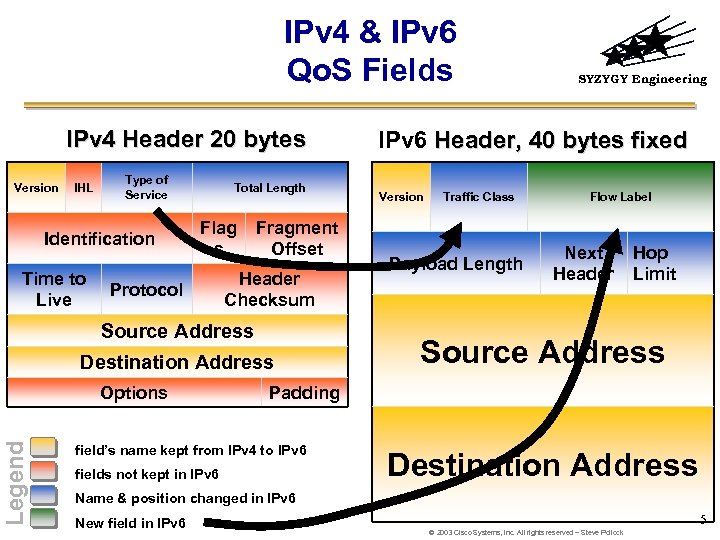 IPv 4 & IPv 6 Qo. S Fields IPv 4 Header 20 bytes Version IHL Type of Service Identification Time to Live Total Length Flag s Protocol Fragment Offset Header Checksum Source Address Destination Address Legend Options SYZYGY Engineering IPv 6 Header, 40 bytes fixed Version Traffic Class Payload Length Flow Label Next Header Hop Limit Source Address Padding field’s name kept from IPv 4 to IPv 6 fields not kept in IPv 6 Destination Address Name & position changed in IPv 6 New field in IPv 6 5 © 2003 Cisco Systems, Inc. All rights reserved – Steve Pollock
IPv 4 & IPv 6 Qo. S Fields IPv 4 Header 20 bytes Version IHL Type of Service Identification Time to Live Total Length Flag s Protocol Fragment Offset Header Checksum Source Address Destination Address Legend Options SYZYGY Engineering IPv 6 Header, 40 bytes fixed Version Traffic Class Payload Length Flow Label Next Header Hop Limit Source Address Padding field’s name kept from IPv 4 to IPv 6 fields not kept in IPv 6 Destination Address Name & position changed in IPv 6 New field in IPv 6 5 © 2003 Cisco Systems, Inc. All rights reserved – Steve Pollock
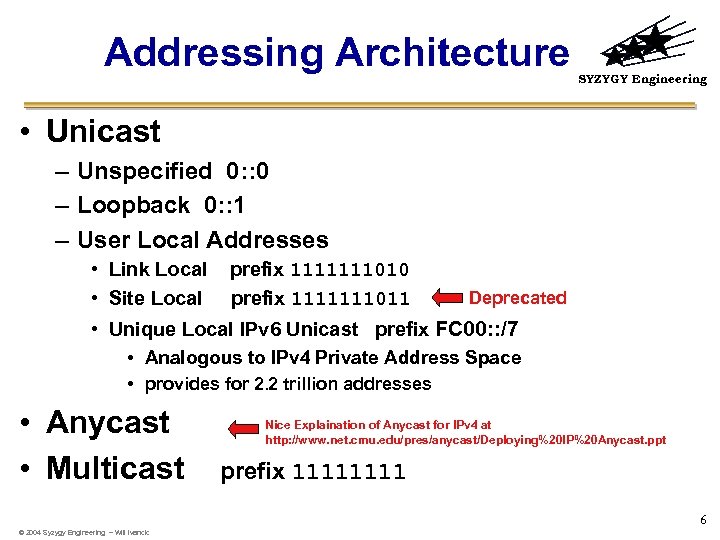 Addressing Architecture SYZYGY Engineering • Unicast – Unspecified 0: : 0 – Loopback 0: : 1 – User Local Addresses • Link Local • Site Local prefix 1111111010 prefix 1111111011 Deprecated • Unique Local IPv 6 Unicast prefix FC 00: : /7 • Analogous to IPv 4 Private Address Space • provides for 2. 2 trillion addresses • Anycast • Multicast Nice Explaination of Anycast for IPv 4 at http: //www. net. cmu. edu/pres/anycast/Deploying%20 IP%20 Anycast. ppt prefix 1111 6 © 2004 Syzygy Engineering – Will Ivancic
Addressing Architecture SYZYGY Engineering • Unicast – Unspecified 0: : 0 – Loopback 0: : 1 – User Local Addresses • Link Local • Site Local prefix 1111111010 prefix 1111111011 Deprecated • Unique Local IPv 6 Unicast prefix FC 00: : /7 • Analogous to IPv 4 Private Address Space • provides for 2. 2 trillion addresses • Anycast • Multicast Nice Explaination of Anycast for IPv 4 at http: //www. net. cmu. edu/pres/anycast/Deploying%20 IP%20 Anycast. ppt prefix 1111 6 © 2004 Syzygy Engineering – Will Ivancic
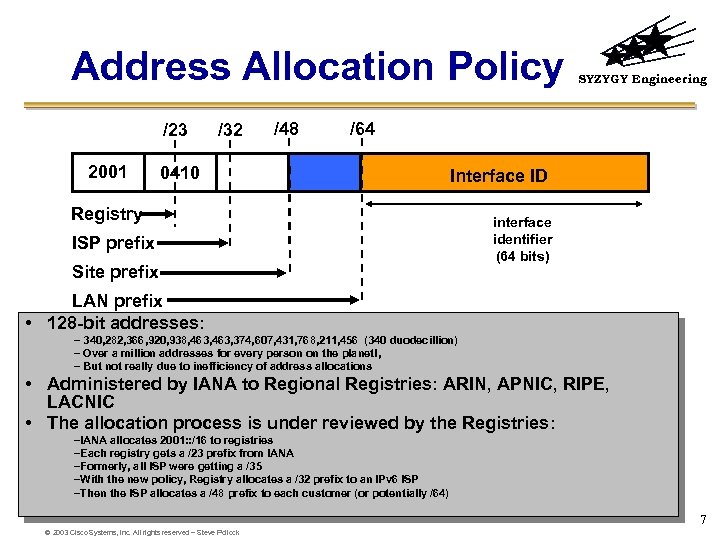 Address Allocation Policy /23 2001 /32 /48 SYZYGY Engineering /64 0410 Interface ID Registry ISP prefix Site prefix interface identifier (64 bits) LAN prefix • 128 -bit addresses: – 340, 282, 366, 920, 938, 463, 374, 607, 431, 768, 211, 456 (340 duodecillion) – Over a million addresses for every person on the planet!, – But not really due to inefficiency of address allocations • Administered by IANA to Regional Registries: ARIN, APNIC, RIPE, LACNIC • The allocation process is under reviewed by the Registries: –IANA allocates 2001: : /16 to registries –Each registry gets a /23 prefix from IANA –Formerly, all ISP were getting a /35 –With the new policy, Registry allocates a /32 prefix to an IPv 6 ISP –Then the ISP allocates a /48 prefix to each customer (or potentially /64) 7 © 2003 Cisco Systems, Inc. All rights reserved – Steve Pollock
Address Allocation Policy /23 2001 /32 /48 SYZYGY Engineering /64 0410 Interface ID Registry ISP prefix Site prefix interface identifier (64 bits) LAN prefix • 128 -bit addresses: – 340, 282, 366, 920, 938, 463, 374, 607, 431, 768, 211, 456 (340 duodecillion) – Over a million addresses for every person on the planet!, – But not really due to inefficiency of address allocations • Administered by IANA to Regional Registries: ARIN, APNIC, RIPE, LACNIC • The allocation process is under reviewed by the Registries: –IANA allocates 2001: : /16 to registries –Each registry gets a /23 prefix from IANA –Formerly, all ISP were getting a /35 –With the new policy, Registry allocates a /32 prefix to an IPv 6 ISP –Then the ISP allocates a /48 prefix to each customer (or potentially /64) 7 © 2003 Cisco Systems, Inc. All rights reserved – Steve Pollock
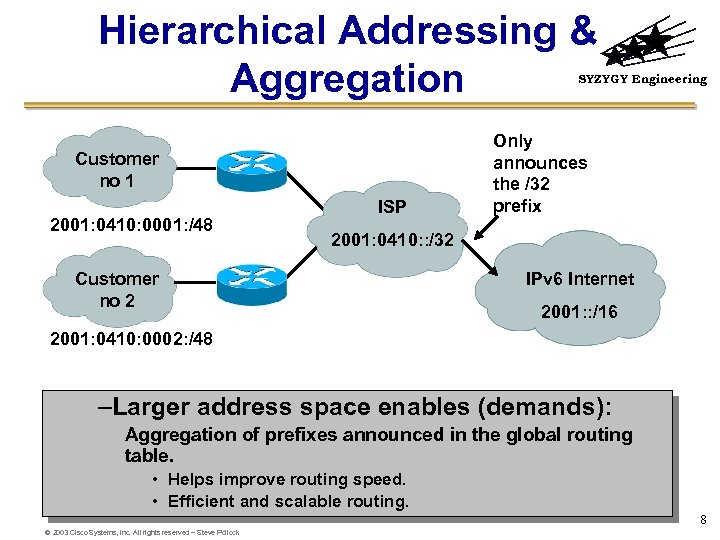 Hierarchical Addressing & Aggregation SYZYGY Engineering Customer no 1 2001: 0410: 0001: /48 ISP Only announces the /32 prefix 2001: 0410: : /32 Customer no 2 IPv 6 Internet 2001: : /16 2001: 0410: 0002: /48 –Larger address space enables (demands): Aggregation of prefixes announced in the global routing table. • Helps improve routing speed. • Efficient and scalable routing. 8 © 2003 Cisco Systems, Inc. All rights reserved – Steve Pollock
Hierarchical Addressing & Aggregation SYZYGY Engineering Customer no 1 2001: 0410: 0001: /48 ISP Only announces the /32 prefix 2001: 0410: : /32 Customer no 2 IPv 6 Internet 2001: : /16 2001: 0410: 0002: /48 –Larger address space enables (demands): Aggregation of prefixes announced in the global routing table. • Helps improve routing speed. • Efficient and scalable routing. 8 © 2003 Cisco Systems, Inc. All rights reserved – Steve Pollock
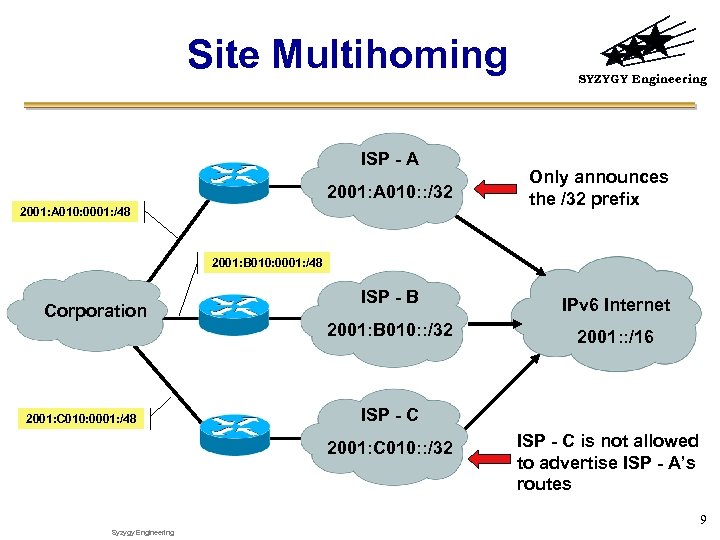 Site Multihoming ISP - A 2001: A 010: : /32 2001: A 010: 0001: /48 SYZYGY Engineering Only announces the /32 prefix 2001: B 010: 0001: /48 Corporation 2001: C 010: 0001: /48 ISP - B IPv 6 Internet 2001: B 010: : /32 2001: : /16 ISP - C 2001: C 010: : /32 ISP - C is not allowed to advertise ISP - A’s routes 9 Syzygy Engineering
Site Multihoming ISP - A 2001: A 010: : /32 2001: A 010: 0001: /48 SYZYGY Engineering Only announces the /32 prefix 2001: B 010: 0001: /48 Corporation 2001: C 010: 0001: /48 ISP - B IPv 6 Internet 2001: B 010: : /32 2001: : /16 ISP - C 2001: C 010: : /32 ISP - C is not allowed to advertise ISP - A’s routes 9 Syzygy Engineering
 Policy Proposal 2005 -1: Provider-independent IPv 6 Assignments for End Sites SYZYGY Engineering • 6. 5. 8. Direct assignments from ARIN to end-user organizations – 6. 5. 8. 1. Criteria • To qualify for a direct assignment, an organization must: not be an IPv 6 LIR; and • qualify for an IPv 4 assignment or allocation from ARIN under the IPv 4 policy currently in effect. – 6. 5. 8. 2. Initial assignment size • Organizations that meet the direct assignment criteria are eligible to receive a direct assignment. The minimum size of the assignment is /48. Organizations requesting a larger assignment must provide documentation justifying the need for additional subnets. • These assignments shall be made from a distinctly identified prefix and shall be made with a reservation for growth of at least a /44. – 6. 5. 8. 3. Subsequent assignment size • Additional assignments may be made when the need for additional subnets is justified. When possible, assignments will be made from an adjacent address block. 10
Policy Proposal 2005 -1: Provider-independent IPv 6 Assignments for End Sites SYZYGY Engineering • 6. 5. 8. Direct assignments from ARIN to end-user organizations – 6. 5. 8. 1. Criteria • To qualify for a direct assignment, an organization must: not be an IPv 6 LIR; and • qualify for an IPv 4 assignment or allocation from ARIN under the IPv 4 policy currently in effect. – 6. 5. 8. 2. Initial assignment size • Organizations that meet the direct assignment criteria are eligible to receive a direct assignment. The minimum size of the assignment is /48. Organizations requesting a larger assignment must provide documentation justifying the need for additional subnets. • These assignments shall be made from a distinctly identified prefix and shall be made with a reservation for growth of at least a /44. – 6. 5. 8. 3. Subsequent assignment size • Additional assignments may be made when the need for additional subnets is justified. When possible, assignments will be made from an adjacent address block. 10
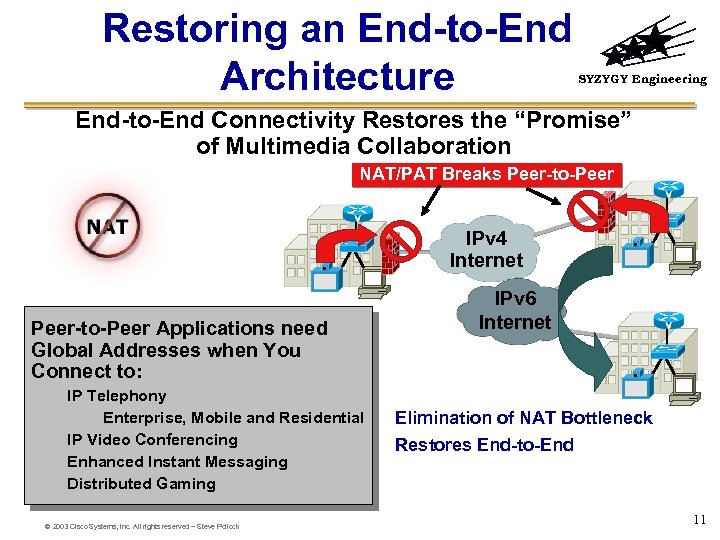 Restoring an End-to-End Architecture SYZYGY Engineering End-to-End Connectivity Restores the “Promise” of Multimedia Collaboration NAT/PAT Breaks Peer-to-Peer IPv 4 Internet Peer-to-Peer Applications need Global Addresses when You Connect to: IP Telephony Enterprise, Mobile and Residential IP Video Conferencing Enhanced Instant Messaging Distributed Gaming © 2003 Cisco Systems, Inc. All rights reserved – Steve Pollock IPv 6 Internet Elimination of NAT Bottleneck Restores End-to-End 11
Restoring an End-to-End Architecture SYZYGY Engineering End-to-End Connectivity Restores the “Promise” of Multimedia Collaboration NAT/PAT Breaks Peer-to-Peer IPv 4 Internet Peer-to-Peer Applications need Global Addresses when You Connect to: IP Telephony Enterprise, Mobile and Residential IP Video Conferencing Enhanced Instant Messaging Distributed Gaming © 2003 Cisco Systems, Inc. All rights reserved – Steve Pollock IPv 6 Internet Elimination of NAT Bottleneck Restores End-to-End 11
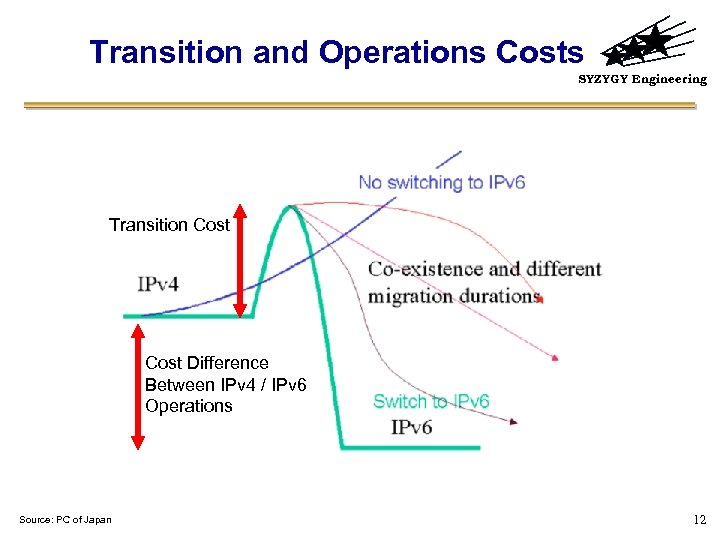 Transition and Operations Costs SYZYGY Engineering Transition Cost Difference Between IPv 4 / IPv 6 Operations Source: PC of Japan 12
Transition and Operations Costs SYZYGY Engineering Transition Cost Difference Between IPv 4 / IPv 6 Operations Source: PC of Japan 12
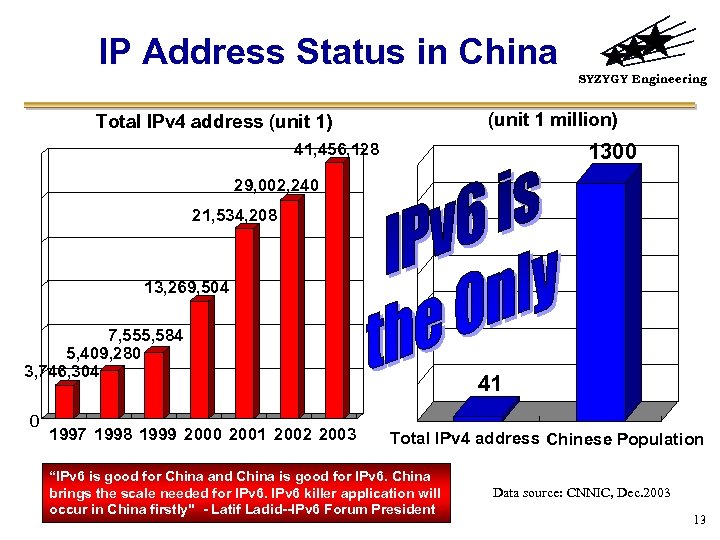 IP Address Status in China SYZYGY Engineering (unit 1 million) Total IPv 4 address (unit 1) 1300 41, 456, 128 29, 002, 240 21, 534, 208 13, 269, 504 7, 555, 584 5, 409, 280 3, 746, 304 0 1997 1998 1999 2000 2001 2002 2003 41 Total IPv 4 address Chinese Population “IPv 6 is good for China and China is good for IPv 6. China brings the scale needed for IPv 6 killer application will occur in China firstly" - Latif Ladid--IPv 6 Forum President Data source: CNNIC, Dec. 2003 13
IP Address Status in China SYZYGY Engineering (unit 1 million) Total IPv 4 address (unit 1) 1300 41, 456, 128 29, 002, 240 21, 534, 208 13, 269, 504 7, 555, 584 5, 409, 280 3, 746, 304 0 1997 1998 1999 2000 2001 2002 2003 41 Total IPv 4 address Chinese Population “IPv 6 is good for China and China is good for IPv 6. China brings the scale needed for IPv 6 killer application will occur in China firstly" - Latif Ladid--IPv 6 Forum President Data source: CNNIC, Dec. 2003 13
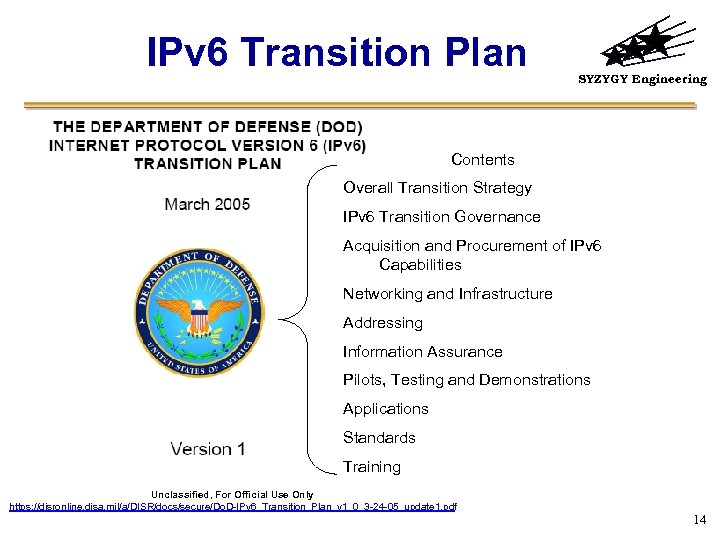 IPv 6 Transition Plan SYZYGY Engineering Contents Overall Transition Strategy IPv 6 Transition Governance Acquisition and Procurement of IPv 6 Capabilities Networking and Infrastructure Addressing Information Assurance Pilots, Testing and Demonstrations Applications Standards Training Unclassified, For Official Use Only https: //disronline. disa. mil/a/DISR/docs/secure/Do. D-IPv 6_Transition_Plan_v 1_0_3 -24 -05_update 1. pdf 14
IPv 6 Transition Plan SYZYGY Engineering Contents Overall Transition Strategy IPv 6 Transition Governance Acquisition and Procurement of IPv 6 Capabilities Networking and Infrastructure Addressing Information Assurance Pilots, Testing and Demonstrations Applications Standards Training Unclassified, For Official Use Only https: //disronline. disa. mil/a/DISR/docs/secure/Do. D-IPv 6_Transition_Plan_v 1_0_3 -24 -05_update 1. pdf 14
 IPv 6 Transition Plan SYZYGY Engineering https: //disronline. disa. mil/a/DISR/docs/secure/Do. D_IPv 6_Transition_Plan_v 2_Final. pdf 15
IPv 6 Transition Plan SYZYGY Engineering https: //disronline. disa. mil/a/DISR/docs/secure/Do. D_IPv 6_Transition_Plan_v 2_Final. pdf 15
 Potential Showstoppers to Fully IP-based SYZYGY Engineering Tactical Operations Today Further research in the following areas is required in order to enhance the IPv 6 protocol suite to support Network Enabled Command: – Embedding/ Encapsulation of legacy systems by means of interoperable gateways – Potential of Anycast Addressing to foster SOA, • Service Discovery protocols such as IPSec Discovery need standardization; – Global IP Security Architecture needs to encompass both deployable and highly dynamic domains supporting all kinds of host and network mobility, • Scalable Tactical PKI, e. g. CA and distributed Sub-CAs; – Optimization of MANET routing mechanisms, • Need to find a compromise between low routing overhead of reactive routing and instant route availability of proactive routing, • True multicast routing in the mobile domain; – Qo. S that considers the heterogeneous (e. g. in terms of bandwidth and latency) and dynamic availability of communication links, – Work on standardized service interoperability profiles; – IPv 6 (multicast) enabled applications. 16
Potential Showstoppers to Fully IP-based SYZYGY Engineering Tactical Operations Today Further research in the following areas is required in order to enhance the IPv 6 protocol suite to support Network Enabled Command: – Embedding/ Encapsulation of legacy systems by means of interoperable gateways – Potential of Anycast Addressing to foster SOA, • Service Discovery protocols such as IPSec Discovery need standardization; – Global IP Security Architecture needs to encompass both deployable and highly dynamic domains supporting all kinds of host and network mobility, • Scalable Tactical PKI, e. g. CA and distributed Sub-CAs; – Optimization of MANET routing mechanisms, • Need to find a compromise between low routing overhead of reactive routing and instant route availability of proactive routing, • True multicast routing in the mobile domain; – Qo. S that considers the heterogeneous (e. g. in terms of bandwidth and latency) and dynamic availability of communication links, – Work on standardized service interoperability profiles; – IPv 6 (multicast) enabled applications. 16
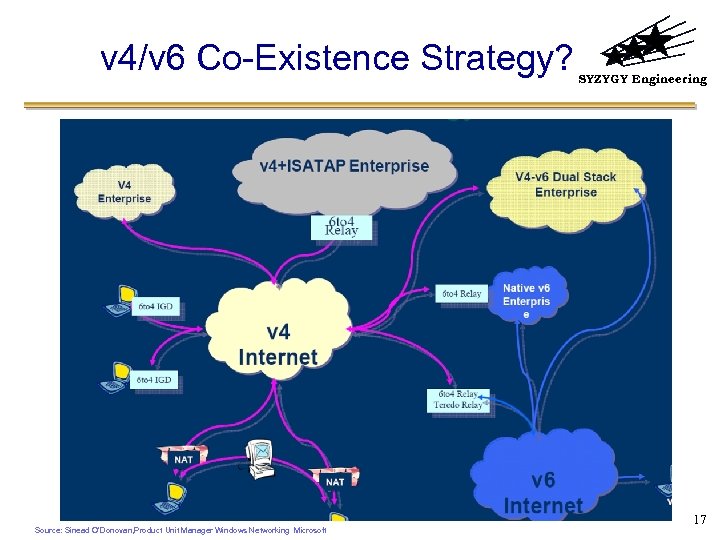 v 4/v 6 Co-Existence Strategy? Source: Sinead O’Donovan, Product Unit Manager Windows Networking Microsoft SYZYGY Engineering 17
v 4/v 6 Co-Existence Strategy? Source: Sinead O’Donovan, Product Unit Manager Windows Networking Microsoft SYZYGY Engineering 17
 Key Technology Enablers SYZYGY Engineering • Zero Configuration in • PKI, IKE and Key rapidly deployed and Management and Applications mobile networks – DNS, DHCP and KEY Servers 18 © 2004 Syzygy Engineering – Will Ivancic
Key Technology Enablers SYZYGY Engineering • Zero Configuration in • PKI, IKE and Key rapidly deployed and Management and Applications mobile networks – DNS, DHCP and KEY Servers 18 © 2004 Syzygy Engineering – Will Ivancic
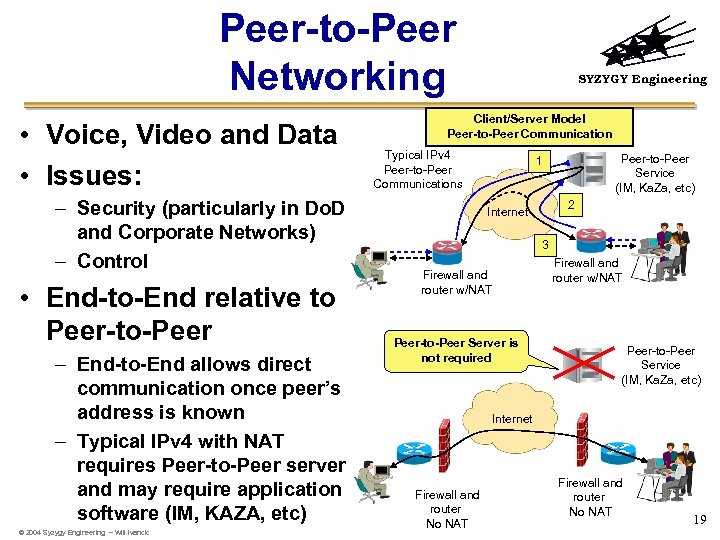 Peer-to-Peer Networking • Voice, Video and Data • Issues: – Security (particularly in Do. D and Corporate Networks) – Control • End-to-End relative to Peer-to-Peer – End-to-End allows direct communication once peer’s address is known – Typical IPv 4 with NAT requires Peer-to-Peer server and may require application software (IM, KAZA, etc) © 2004 Syzygy Engineering – Will Ivancic SYZYGY Engineering Client/Server Model Peer-to-Peer Communication Typical IPv 4 Peer-to-Peer Communications Peer-to-Peer Service (IM, Ka. Za, etc) 1 2 Internet 3 Firewall and router w/NAT Peer-to-Peer Server is not required Peer-to-Peer Service (IM, Ka. Za, etc) Internet Firewall and router No NAT 19
Peer-to-Peer Networking • Voice, Video and Data • Issues: – Security (particularly in Do. D and Corporate Networks) – Control • End-to-End relative to Peer-to-Peer – End-to-End allows direct communication once peer’s address is known – Typical IPv 4 with NAT requires Peer-to-Peer server and may require application software (IM, KAZA, etc) © 2004 Syzygy Engineering – Will Ivancic SYZYGY Engineering Client/Server Model Peer-to-Peer Communication Typical IPv 4 Peer-to-Peer Communications Peer-to-Peer Service (IM, Ka. Za, etc) 1 2 Internet 3 Firewall and router w/NAT Peer-to-Peer Server is not required Peer-to-Peer Service (IM, Ka. Za, etc) Internet Firewall and router No NAT 19
 New “IPv 6 Capable” Definition – SYZYGY Engineering • A product must meet the IPv 6 base requirements (defined in “Do. D IPv 6 Standard Profiles for IPv 6 Capable Products”) and support requirements for one (or more) product categories. – e. g. Workstations, routers, switches, security devices, firewalls, etc. . . • And support the IPv 6 version of any IPv 6 protocol functional categories required for its function within the Do. D Global Information Grid (GIG) • Official Site – (May require Certificate or Common Access Card to obtain access http: //jitc. fhu. disa. mil/adv_ip/register. html – Otherwise try http: //jitc. fhu. disa. mil/adv_ip/register/docs/disr_ipv 6_product_profile_draft. pdf 20
New “IPv 6 Capable” Definition – SYZYGY Engineering • A product must meet the IPv 6 base requirements (defined in “Do. D IPv 6 Standard Profiles for IPv 6 Capable Products”) and support requirements for one (or more) product categories. – e. g. Workstations, routers, switches, security devices, firewalls, etc. . . • And support the IPv 6 version of any IPv 6 protocol functional categories required for its function within the Do. D Global Information Grid (GIG) • Official Site – (May require Certificate or Common Access Card to obtain access http: //jitc. fhu. disa. mil/adv_ip/register. html – Otherwise try http: //jitc. fhu. disa. mil/adv_ip/register/docs/disr_ipv 6_product_profile_draft. pdf 20
 What is Mobility? • Transportable – Telecommuter – Traveler – Relatively static once connected – Single point of connection – Connectivity • IPv 6 Autoconfiguration • VPN SYZYGY Engineering • Mobile – Mobile Devices • PDAs • Cell Phones – Mobile Networks • Trains • Planes • Automobiles – Connectivity • Mobile-IP • Networks in Motion (NEMO) • Ad Hoc Networks 21 © 2004 Syzygy Engineering – Will Ivancic
What is Mobility? • Transportable – Telecommuter – Traveler – Relatively static once connected – Single point of connection – Connectivity • IPv 6 Autoconfiguration • VPN SYZYGY Engineering • Mobile – Mobile Devices • PDAs • Cell Phones – Mobile Networks • Trains • Planes • Automobiles – Connectivity • Mobile-IP • Networks in Motion (NEMO) • Ad Hoc Networks 21 © 2004 Syzygy Engineering – Will Ivancic
 Mobile Networking Solutions SYZYGY Engineering • Routing Protocols – Route Optimization – Convergence Time – Sharing Infrastructure – who owns the network? • Mobile-IP – – Route Optimization Convergence Time Sharing Infrastructure Security – Relatively Easy to Secure • Domain Name Servers – Route Optimization – Convergence Time – Reliability 22 Source – Will Ivancic
Mobile Networking Solutions SYZYGY Engineering • Routing Protocols – Route Optimization – Convergence Time – Sharing Infrastructure – who owns the network? • Mobile-IP – – Route Optimization Convergence Time Sharing Infrastructure Security – Relatively Easy to Secure • Domain Name Servers – Route Optimization – Convergence Time – Reliability 22 Source – Will Ivancic
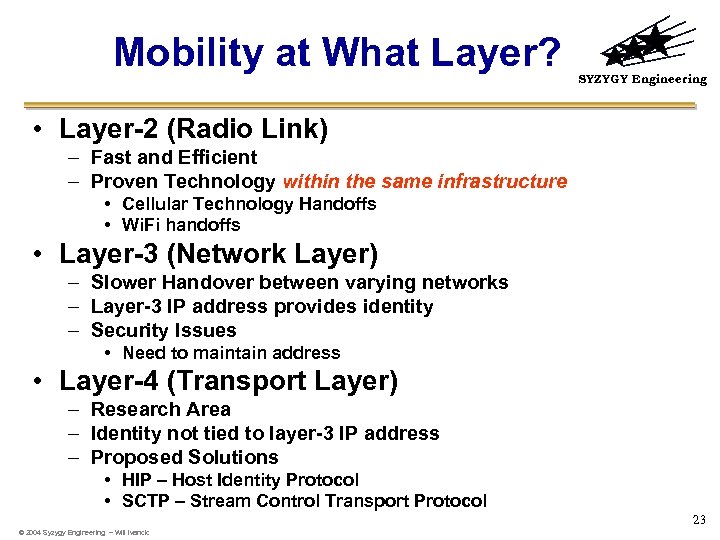 Mobility at What Layer? SYZYGY Engineering • Layer-2 (Radio Link) – Fast and Efficient – Proven Technology within the same infrastructure • Cellular Technology Handoffs • Wi. Fi handoffs • Layer-3 (Network Layer) – Slower Handover between varying networks – Layer-3 IP address provides identity – Security Issues • Need to maintain address • Layer-4 (Transport Layer) – Research Area – Identity not tied to layer-3 IP address – Proposed Solutions • HIP – Host Identity Protocol • SCTP – Stream Control Transport Protocol 23 © 2004 Syzygy Engineering – Will Ivancic
Mobility at What Layer? SYZYGY Engineering • Layer-2 (Radio Link) – Fast and Efficient – Proven Technology within the same infrastructure • Cellular Technology Handoffs • Wi. Fi handoffs • Layer-3 (Network Layer) – Slower Handover between varying networks – Layer-3 IP address provides identity – Security Issues • Need to maintain address • Layer-4 (Transport Layer) – Research Area – Identity not tied to layer-3 IP address – Proposed Solutions • HIP – Host Identity Protocol • SCTP – Stream Control Transport Protocol 23 © 2004 Syzygy Engineering – Will Ivancic
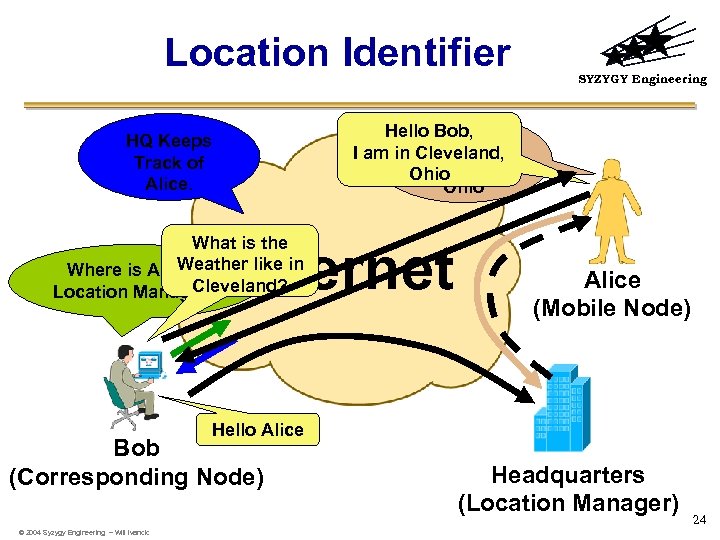 Location Identifier SYZYGY Engineering Hello Bob, I am in Cleveland, Ohio HQ Keeps Track of Alice. What is the Weather like in Where is Alice’s Cleveland? Location Manager? Internet Alice (Mobile Node) Hello Alice Bob (Corresponding Node) © 2004 Syzygy Engineering – Will Ivancic Headquarters (Location Manager) 24
Location Identifier SYZYGY Engineering Hello Bob, I am in Cleveland, Ohio HQ Keeps Track of Alice. What is the Weather like in Where is Alice’s Cleveland? Location Manager? Internet Alice (Mobile Node) Hello Alice Bob (Corresponding Node) © 2004 Syzygy Engineering – Will Ivancic Headquarters (Location Manager) 24
 Securing Networks SYZYGY Engineering • Constraints/Tools – Policy • Security Policy • Education • Enforcement – Architecture – Protocols • Must be done up front to be done well 25 © 2004 Syzygy Engineering – Will Ivancic
Securing Networks SYZYGY Engineering • Constraints/Tools – Policy • Security Policy • Education • Enforcement – Architecture – Protocols • Must be done up front to be done well 25 © 2004 Syzygy Engineering – Will Ivancic
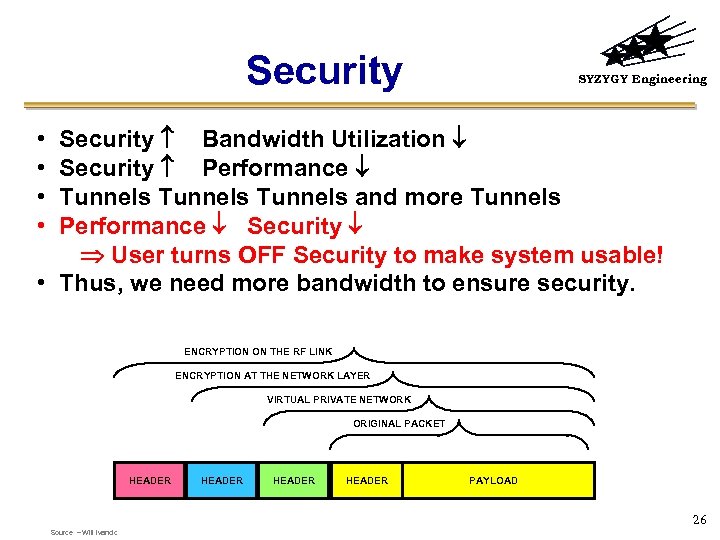 Security SYZYGY Engineering Security Bandwidth Utilization Security Performance Tunnels and more Tunnels Performance Security User turns OFF Security to make system usable! • Thus, we need more bandwidth to ensure security. • • ENCRYPTION ON THE RF LINK ENCRYPTION AT THE NETWORK LAYER VIRTUAL PRIVATE NETWORK ORIGINAL PACKET HEADER PAYLOAD 26 Source – Will Ivancic
Security SYZYGY Engineering Security Bandwidth Utilization Security Performance Tunnels and more Tunnels Performance Security User turns OFF Security to make system usable! • Thus, we need more bandwidth to ensure security. • • ENCRYPTION ON THE RF LINK ENCRYPTION AT THE NETWORK LAYER VIRTUAL PRIVATE NETWORK ORIGINAL PACKET HEADER PAYLOAD 26 Source – Will Ivancic
 Realities of ROI and Security SYZYGY Engineering • Network Security itself does not provide any type of ROI – it is about cost management • Example – You buy a Picasso straight from the artist and a safe to store it in. The safe adds no value to the painting – only helps prevent its loss (i. e. a cost to you) • An organization that fails to adequately prepare a robust security solution faces potential loss from: – – Lost productivity/Lost e-commerce revenue Regulatory penalties Tort litigation Long-term business loss from lost customer confidence 27 Source – Yurie Rich Command. Information
Realities of ROI and Security SYZYGY Engineering • Network Security itself does not provide any type of ROI – it is about cost management • Example – You buy a Picasso straight from the artist and a safe to store it in. The safe adds no value to the painting – only helps prevent its loss (i. e. a cost to you) • An organization that fails to adequately prepare a robust security solution faces potential loss from: – – Lost productivity/Lost e-commerce revenue Regulatory penalties Tort litigation Long-term business loss from lost customer confidence 27 Source – Yurie Rich Command. Information
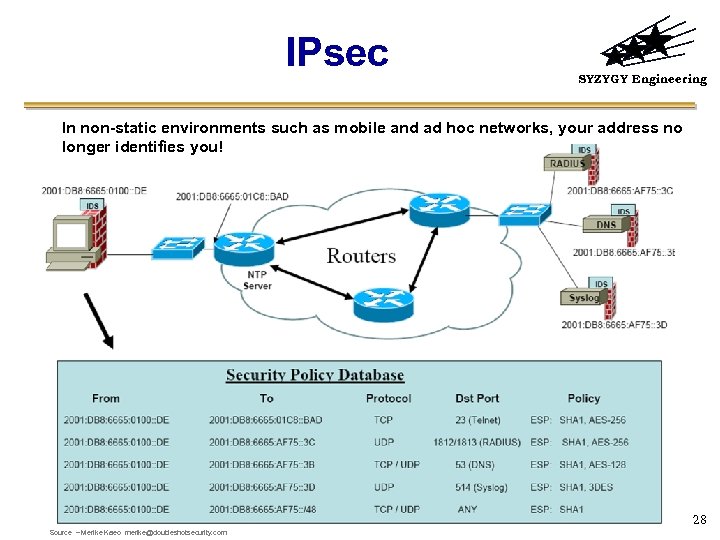 IPsec SYZYGY Engineering In non-static environments such as mobile and ad hoc networks, your address no longer identifies you! 28 Source – Merike Kaeo merike@doubleshotsecurity. com
IPsec SYZYGY Engineering In non-static environments such as mobile and ad hoc networks, your address no longer identifies you! 28 Source – Merike Kaeo merike@doubleshotsecurity. com
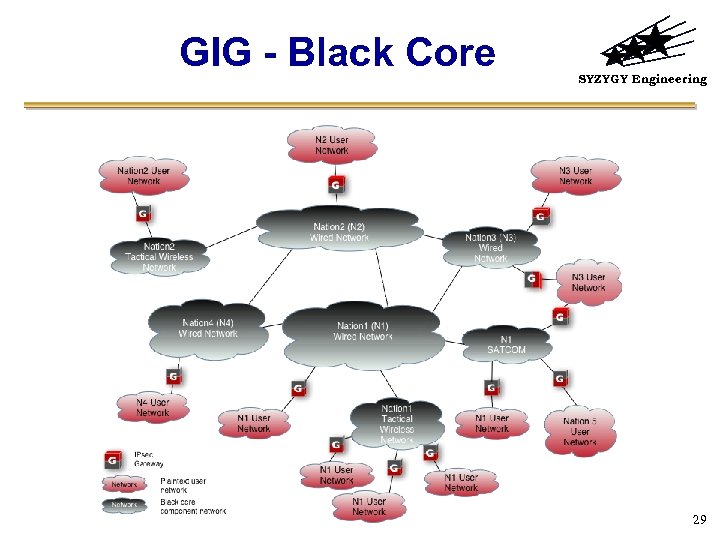 GIG - Black Core SYZYGY Engineering 29
GIG - Black Core SYZYGY Engineering 29
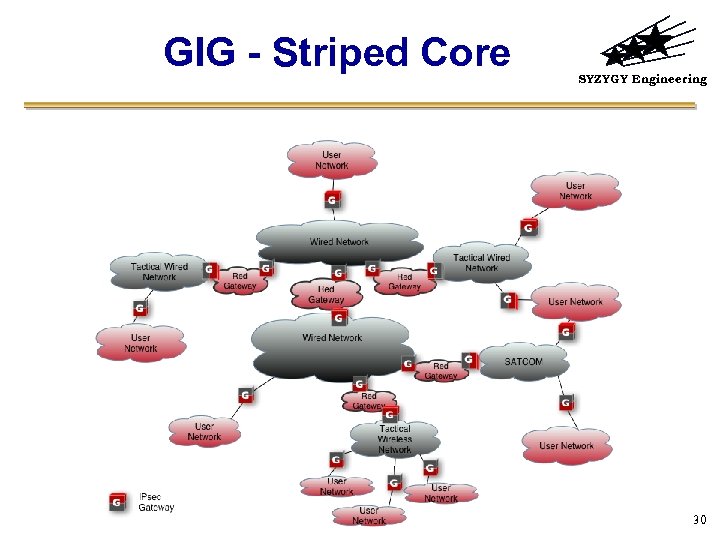 GIG - Striped Core SYZYGY Engineering 30
GIG - Striped Core SYZYGY Engineering 30
 Flow Label SYZYGY Engineering • Used by host to request special handling for certain packets • Unique flow is identified by source address and non-zero flow label – Expected use is per-flow end-to-end Qo. S • RSVP, Video, Gaming, VOIP – Without the flow label the classifier must use transport next header value and port numbers • Less efficient (need to parse the option headers) • May be impossible (due to fragmentation or IPsec ESP) • Layer violation may hinder introduction of new transport protocols • IPv 6 nodes not providing flow-specific treatment MUST ignore the field when receiving or forwarding a packet • Immature Technology – Research Area The Flow Label field is useless, unless it is actually used! 31 © 2004 Syzygy Engineering – Will Ivancic
Flow Label SYZYGY Engineering • Used by host to request special handling for certain packets • Unique flow is identified by source address and non-zero flow label – Expected use is per-flow end-to-end Qo. S • RSVP, Video, Gaming, VOIP – Without the flow label the classifier must use transport next header value and port numbers • Less efficient (need to parse the option headers) • May be impossible (due to fragmentation or IPsec ESP) • Layer violation may hinder introduction of new transport protocols • IPv 6 nodes not providing flow-specific treatment MUST ignore the field when receiving or forwarding a packet • Immature Technology – Research Area The Flow Label field is useless, unless it is actually used! 31 © 2004 Syzygy Engineering – Will Ivancic
 Flow Label Security Considerations SYZYGY Engineering • The IPsec protocol, as defined in [IPSec, AH, ESP], does not include the IPv 6 header's Flow Label in any of its cryptographic calculations – In the case of tunnel mode, it is the outer IPv 6 header's Flow Label that is not included • Modification of the Flow Label by a network node has no effect on IPsec end-to-end security – It cannot cause any IPsec integrity check to fail. – As a consequence, IPsec does not provide any defense against an adversary's modification of the Flow Label (i. e. , a man-in-the-middle attack). 32 © 2004 Syzygy Engineering – Will Ivancic
Flow Label Security Considerations SYZYGY Engineering • The IPsec protocol, as defined in [IPSec, AH, ESP], does not include the IPv 6 header's Flow Label in any of its cryptographic calculations – In the case of tunnel mode, it is the outer IPv 6 header's Flow Label that is not included • Modification of the Flow Label by a network node has no effect on IPsec end-to-end security – It cannot cause any IPsec integrity check to fail. – As a consequence, IPsec does not provide any defense against an adversary's modification of the Flow Label (i. e. , a man-in-the-middle attack). 32 © 2004 Syzygy Engineering – Will Ivancic


