cc39b882f0ee268fbac5bfb0356d2ff6.ppt
- Количество слайдов: 27

Systems Management Luke Simmons Luke. Simmons@us. ibm. com 1
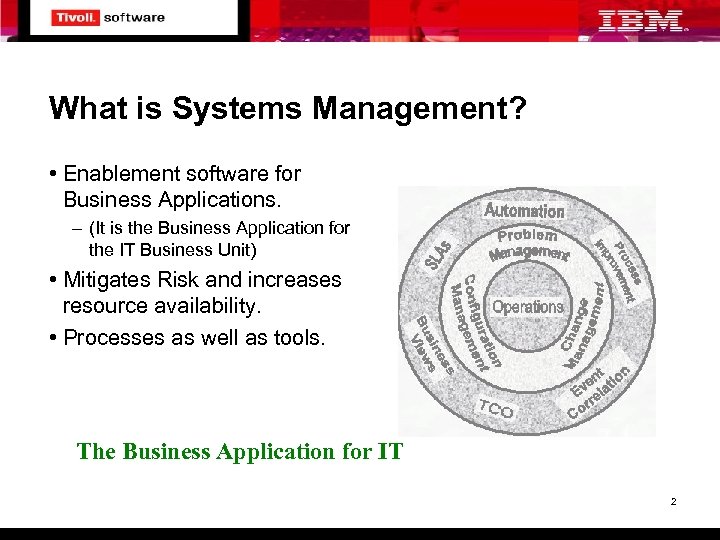
What is Systems Management? • Enablement software for Business Applications. – (It is the Business Application for the IT Business Unit) • Mitigates Risk and increases resource availability. • Processes as well as tools. The Business Application for IT 2

Systems Management Functions Change & Configuratio n Managemen t Life Cycle management • Reduce costs • Gain automated control • Improve efficiencies Security Align e-business and security • Mitigate risks • Consistently enforce policies • Reduce administration costs Business Impact Management Change & Performance Configuratio& Availability n Core Services Security Storage Performance & Availability Business success dependent on IT availability • Integrated best practices for rapid ROI • Improve ROI with predictive service level management Storage Continuance through policy-based automation • Backup & recover information assets • Enhance business continuity • Accelerate ROI • Simplify storage management 3

Performance & Availability Concerns • Growth in the number of managed resources. – Vs. relative stability of IT Staffing and Budgets. • Complexity of large business applications. – Visibility and Cost. • Web-based Applications – Problems affect REAL customers. • Increasing Importance of IT to the Business. – Meeting Service Level Agreements. 4

Goal: Show Impact to Business Owners Business Indicators Health of Key Applications 5

Monitoring e-business Resources • Identify, localize, and cure at the resource level • Health console shows status of each resource • Automate corrective actions at the source of the problem • Notify central operations as needed Host Databases Dumb Terminals Host Systems Clients Distributed Databases Servers Increase the availability of e -business infrastructure Application Servers Browsers Web/Edge Servers 6

Management Layers • Top Level Shows Overall Business Impact Management Impact in the context of a cross discipline analysis, predict, optimize, analyze, account, report business application. • The bottom layer collects the data and takes automated Event Correlation and Automationaction. Cross system & domain root cause analysis • The Middle Layer has the intelligence to take action Monitor Systems and Applications based on multiple events. Discover, collect metrics, probe (e. g. user experience), perform local analysis, filter, concentrate, determine root cause, take automated action 7

The Security Landscape • Automated Identity Management • Consistent Access Control • Privacy Policy Enforcement • Security Impact Management 8

Two Questions: Do you know who has access to what systems in your organization? People (employees, contractors, partners & customers) How long does it take you to find this out? Dealing with change (policy, security, privacy, timing, access, audit) 9

The Problem Space MANAGING EXTERNAL USERS RAPID PROVISIONING Knowing who to grant access privileges to and when to revoke them Rapidly granting access to resources required to be productive BUSINESS POLICY ENFORCEMENT Instantly and automatically enforcing new and changing business policies HELP DESK COSTS Reducing IT costs associated with user accounts and passwords RESOURCE EXPLOSION Controlling access to multiple disparate systems RECONCILATION Finding and removing orphan accounts; preventing them from reoccurring ACCESS REVOCATION Instantly and automatically revoking access privileges for unauthorized users x 10

Manual Provisioning BACKLOGS • Today most organizations use manual processes to provision user access rights There are many barriers to successful provisioning REQUESTS DELAYED New Users Provisioned Users Administrators GROWING RESOURCES Request for Access Generated MISSING AUDIT TRAIL Policy & Role Examined ERRORS IT In. Box Approval INCOMPLETE REQUEST FORMS Routing 11

Automated Identity Management Automatically provision of user access rights Enable user self-service password management Delegate administrative responsibility as needed Automate identity change management and approval process Automated approval workflow Change/Suspend Security Admin Sources of User Information Delegate to local administration ! Collect/Detect Local Changes 12
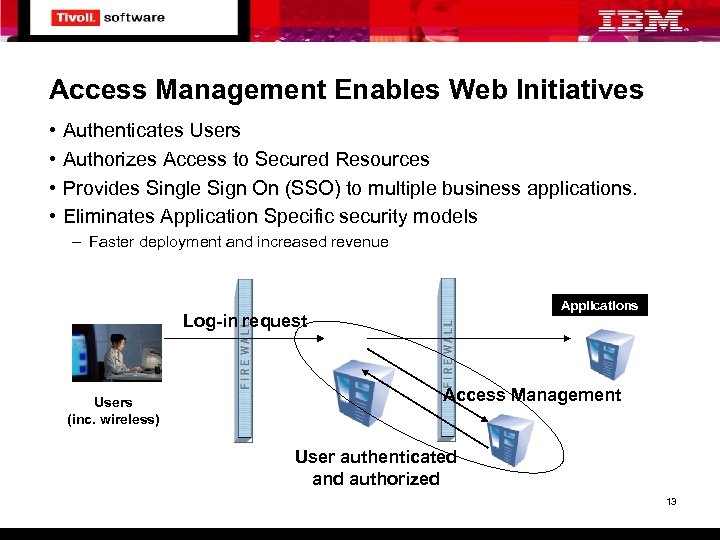
Access Management Enables Web Initiatives • • Authenticates Users Authorizes Access to Secured Resources Provides Single Sign On (SSO) to multiple business applications. Eliminates Application Specific security models – Faster deployment and increased revenue Applications Log-in request Users (inc. wireless) Access Management User authenticated and authorized 13
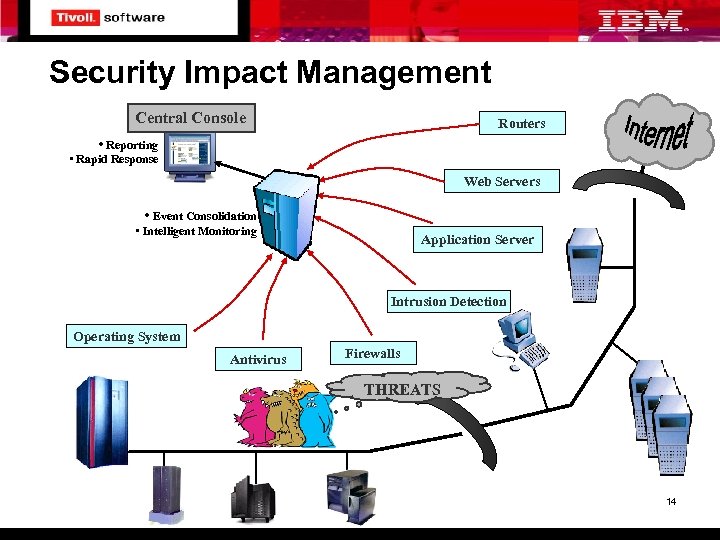
Security Impact Management Central Console Routers • Reporting • Rapid Response Web Servers • Event Consolidation • Intelligent Monitoring Application Server Intrusion Detection Operating System Antivirus Firewalls THREATS 14

July 6, 2002 Free Prozac in the Junk Mail Draws a Lawsuit By Adam Liptak FORT LAUDERDALE, Fla. , July 3 — The unsolicited Prozac arrived in a handaddressed manila envelope. It came from a Walgreen’s drugstore not far from here, and there was a "Dear Patient" form letter inside. Eckerd Reaches Settlement Over Its Marketing Practices Dow Jones Newswires Updated July 10, 2002 J. C. Penney Co. 's Eckerd division agreed to change its marketing policy in a settlement with the Florida attorney general's office over complaints that the drugstore chain had violated patient-privacy laws. 15
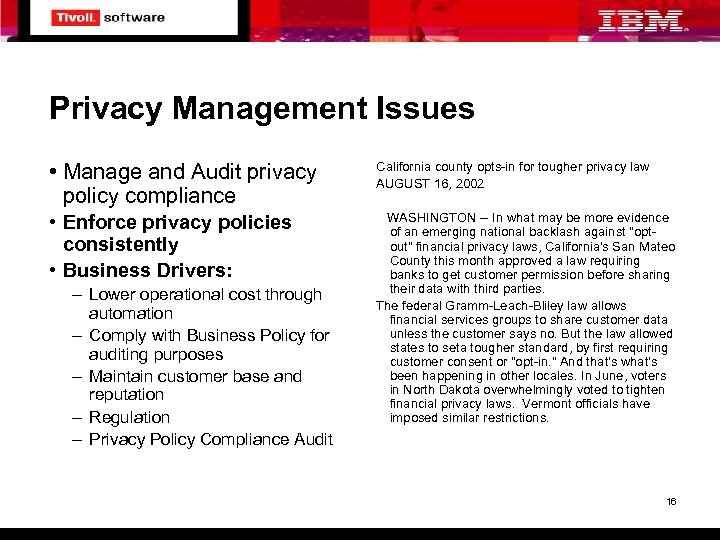
Privacy Management Issues • Manage and Audit privacy policy compliance California county opts-in for tougher privacy law AUGUST 16, 2002 • Enforce privacy policies consistently • Business Drivers: WASHINGTON -- In what may be more evidence of an emerging national backlash against "optout" financial privacy laws, California's San Mateo County this month approved a law requiring banks to get customer permission before sharing their data with third parties. The federal Gramm-Leach-Bliley law allows financial services groups to share customer data unless the customer says no. But the law allowed states to seta tougher standard, by first requiring customer consent or "opt-in. " And that's what's been happening in other locales. In June, voters in North Dakota overwhelmingly voted to tighten financial privacy laws. Vermont officials have imposed similar restrictions. – Lower operational cost through automation – Comply with Business Policy for auditing purposes – Maintain customer base and reputation – Regulation – Privacy Policy Compliance Audit 16

Privacy Flow End Users 1 Define Privacy Policies and PII Types Privacy Manager 2 Associates Data with condensed privacy statements CPO Staff Submission Monitor Data Store Describe & Classify Storage Locations and Map to PII types s te a er ts n r Ge po Re Records details about the access to PII Access/ Enforcement Monitor 3 Auditor Applications 17
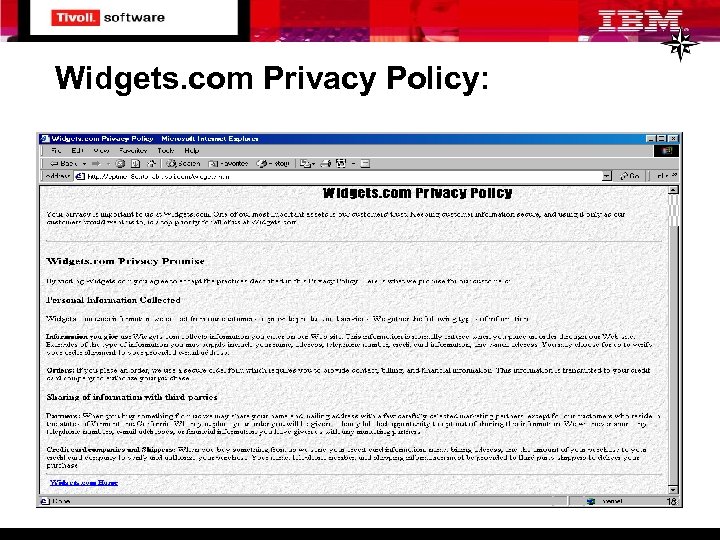
Widgets. com Privacy Policy: 18
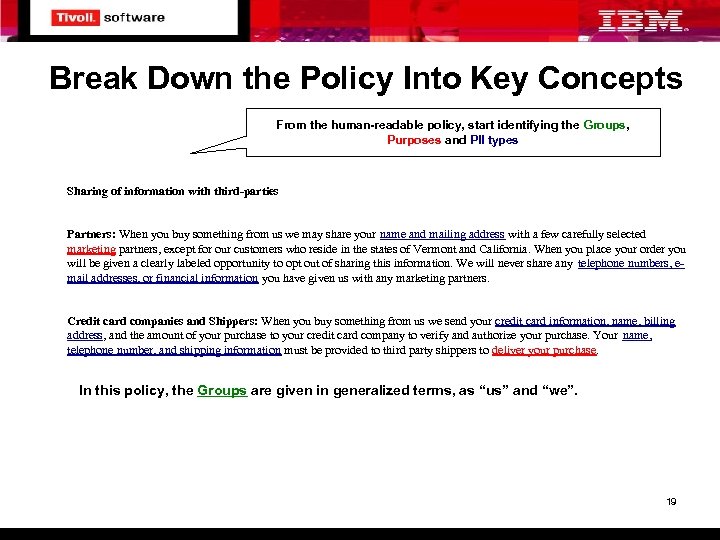
Break Down the Policy Into Key Concepts From the human-readable policy, start identifying the Groups, Purposes and PII types Sharing of information with third-parties Partners: When you buy something from us we may share your name and mailing address with a few carefully selected marketing partners, except for our customers who reside in the states of Vermont and California. When you place your order you will be given a clearly labeled opportunity to opt out of sharing this information. We will never share any telephone numbers, email addresses, or financial information you have given us with any marketing partners. Credit card companies and Shippers: When you buy something from us we send your credit card information, name, billing address, and the amount of your purchase to your credit card company to verify and authorize your purchase. Your name, telephone number, and shipping information must be provided to third party shippers to deliver your purchase. In this policy, the Groups are given in generalized terms, as “us” and “we”. 19

Creating Policy Rules From the Key Concepts After identifying the basic pieces of the policy statements, we can start to form the policy statements. We can break the text down into 3 -4 policy statements that need to be a part of the privacy policy we want to implement into Privacy Manager. Widget's Billing Department will use credit card and address information to charge your credit card for the purchases you made. Widget's Shipping Department will use your address information to ship your order. If you opt-in, Widget's Shipping Department will use your e-mail address to notify you of your order's shipment status. Widget's Marketing Department will share your name and mailing address with selected marketing partners unless you opt out or if you live in Vermont or California. We’re now ready to build the policy in Privacy Manager…. . Note: EPA Privacy Agreements Framework can be used to generate these rules as well. 20

Thank You! Questions? 21

Industry Standard Definition • Information Technology Information Library (ITIL) • Defines Systems Management as a set of Deliverable Services • For more information see: – http: //www. itil. co. uk 22
ITIL/ITSM Descriptions • Service Delivery • Availability Management - Design, implement, manage and optimize the availability and use of IT services by customers in accordance with levels defined and authorized within Service level agreements. • Capacity Management - Ensure IT has sufficient resources to meet the defined service requirements of the business user community, now and in the future, at an optimal an agreed cost. • Continuity Management - Ensure the continuance of defined business operations by minimizing the effects of unexpected disruption to, or stoppage of IT services. • Financial Management - Ensure the balance between capacity and cost is maintained by identifying all costs necessary to provide services to the business, and establish a fair means by which an agreed percentage is recovered. • Service Level Management - Negotiation, definition, agreement and management of the quality, quantity and cost of information services in terms understood by the customer and measurable by the provider. • • Service Support • Change Management - Manage the cost effective implementation, with minimum risk, of approved changes to IT infrastructure components that support IT services. • Configuration Management - Identification, control, status accounting, relationship management and verification of IT infrastructure components. • Release Management - Plan, design, build, configure and test a release consisting of related changes to hardware and software components to the production environment in a risk free manner. • Incident Management - Ensure the continuity of services by resolving incidents as soon as possible, while being the main contact point for all questions, complaints or remarks regarding IT services. • Problem Management - Identification, management and elimination of problem causes, minimization of incidents and stabilization of IT services. http: //www. itil. co. uk/ 23

Measurable Productivity Improvements Customer: Need: Large Financial Services Provider Automate the administration of user access rights for 65, 000+ users Manage security of access privileges across 100’s of systems Insure security policy enforced across enterprise in an auditable fashion for regulation compliance Ensure that all private data is adequately protected § § Solution: Result: Automated Identity Management Same staff now manages 3 X the user population § Centralized reporting to insure regulatory compliance § 24

Return on investment Customer: Large Insurance Company Need: “Bulletproof” availability Solution: Results: Performance and Availability Management • • $3. 4 million ROI in eight months Cut outages by 31% Cut downtime by 40% Expect to save $40 million in five years 25

Return on investment Customer: Need: Solution: Results: Computer Equipment Manufacturer Manage large, complex, distributed e-business infrastructure Performance and Availability Management Availability of Easy Access online business consumer application has increased 4%, with each percent increase tied to almost $150 million in revenue 26

Predictive/proactive today Customer: Large Consulting Company Need: Increased effectiveness of applications on the web with a single sign-on across multiple Web environments Solution: Result: Access Management • • • Provides single secure sign-on functionality Automated identity management across legacy and Web environments Single security model for Web environments Reduced monthly identity administration cost by $75 K Reduced time to provision accounts from days to less than 5 minutes 27
cc39b882f0ee268fbac5bfb0356d2ff6.ppt