669a4234a6965d81be332fa8bf37bea5.ppt
- Количество слайдов: 42
 ‘SYSTEMIC ELECTRONIC ATTACK THE FUTURE IS NOW’
‘SYSTEMIC ELECTRONIC ATTACK THE FUTURE IS NOW’
 An Information & Communications Technology view of Information Operations Jurgen Opfer MIEEE, MAIPIO jurgen. opfer@oldcrows. org. au
An Information & Communications Technology view of Information Operations Jurgen Opfer MIEEE, MAIPIO jurgen. opfer@oldcrows. org. au
 What is being attacked?
What is being attacked?
 Who is doing the attacks?
Who is doing the attacks?
 How are they attacking?
How are they attacking?
 What are the defences?
What are the defences?
 Extent of the problem
Extent of the problem
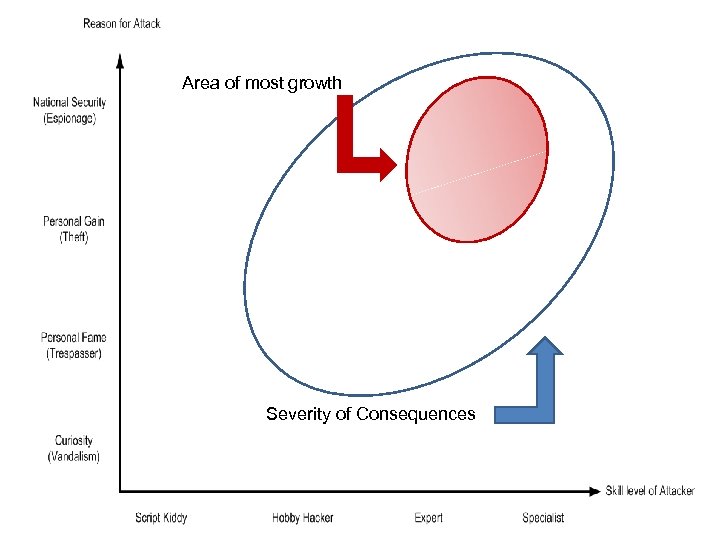 Area of most growth Severity of Consequences
Area of most growth Severity of Consequences
 Our Defense networks are constantly under attack. They are probed thousands of times per DAY and scanned millions of times per DAY. And the frequency and sophistication of attacks are increasing exponentially. ” “Attackers range from teenage hackers to more than 100 foreign intelligence agencies” US Deputy Defense Secretary William Lynn October 2009
Our Defense networks are constantly under attack. They are probed thousands of times per DAY and scanned millions of times per DAY. And the frequency and sophistication of attacks are increasing exponentially. ” “Attackers range from teenage hackers to more than 100 foreign intelligence agencies” US Deputy Defense Secretary William Lynn October 2009
 Many of the world’s conflicts are not wars at all. There is a fading of the borderline between “defence” and “security” as non-state actors adopt weapons and tactics, and act across borders, and nation-states hire cyber criminals to perform espionage and potentially sabotage as well Defense Technology International January 2010
Many of the world’s conflicts are not wars at all. There is a fading of the borderline between “defence” and “security” as non-state actors adopt weapons and tactics, and act across borders, and nation-states hire cyber criminals to perform espionage and potentially sabotage as well Defense Technology International January 2010
 “I fear that the western world’s defence and security forces are now so focused on counter -terrorism, that we’ve lost sight of the real, and lingering problems of espionage” . . . Private conversation with senior Australian Intelligence Officer
“I fear that the western world’s defence and security forces are now so focused on counter -terrorism, that we’ve lost sight of the real, and lingering problems of espionage” . . . Private conversation with senior Australian Intelligence Officer
 Selected Terms
Selected Terms
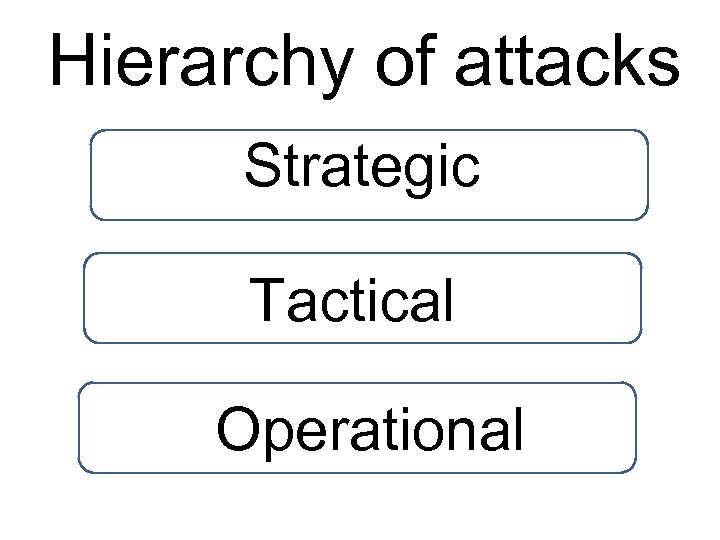 Hierarchy of attacks Strategic Tactical Operational
Hierarchy of attacks Strategic Tactical Operational

 Some recent Attacks US Navy EP-3 forced down by China 2001 followed by cyber exchange Israel cyber attack before bombing Nuclear facilities in Syria 2007 Russian Mafiya vs Europe’s most wired country ‘Estonia’ 2007 Russia vs Georgia’s military & infrastructure 2008 Israel /Hamas Dec 08 -Jan 2009 China /USA 2009 Hackers vs Australian Federal Police 2009 Anonymous group hacks federal parliament Feb 2010
Some recent Attacks US Navy EP-3 forced down by China 2001 followed by cyber exchange Israel cyber attack before bombing Nuclear facilities in Syria 2007 Russian Mafiya vs Europe’s most wired country ‘Estonia’ 2007 Russia vs Georgia’s military & infrastructure 2008 Israel /Hamas Dec 08 -Jan 2009 China /USA 2009 Hackers vs Australian Federal Police 2009 Anonymous group hacks federal parliament Feb 2010

 Operation Orchard Computer Trojan Helped Expose Secret Syrian Nuclear reactor “The Trojan was planted on a laptop of a Syrian official while he was staying in London” Erich Follath & Holger Stark Der Spiegel
Operation Orchard Computer Trojan Helped Expose Secret Syrian Nuclear reactor “The Trojan was planted on a laptop of a Syrian official while he was staying in London” Erich Follath & Holger Stark Der Spiegel

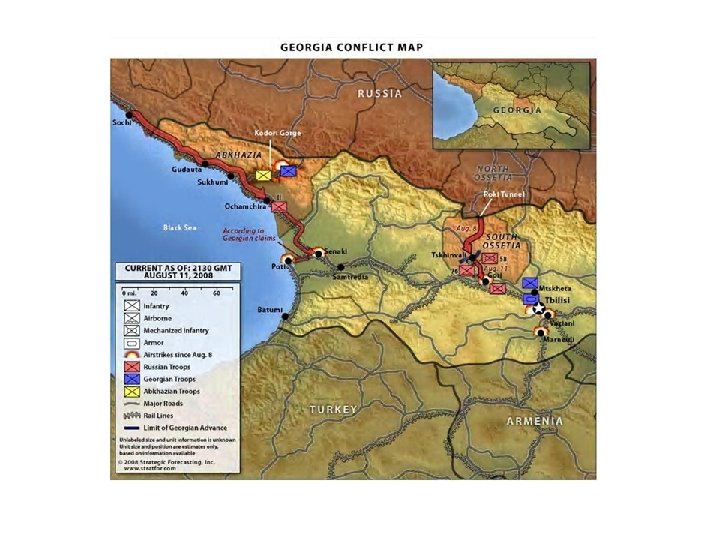
 “Their ‘cyber special operations forces’ isolated the president by disabling all his cyber connectivity, then their ‘cyber air force’ carpet bombed the entire national network, and finally their ‘cyber Delta force’ infiltrated and rewrote code that kept their network from working correctly even after it was brought back up. It was a highly sophisticated attack” General Peter Pace USMC (Retired) addressing USCCU about Russia cyber attacking Georgia
“Their ‘cyber special operations forces’ isolated the president by disabling all his cyber connectivity, then their ‘cyber air force’ carpet bombed the entire national network, and finally their ‘cyber Delta force’ infiltrated and rewrote code that kept their network from working correctly even after it was brought back up. It was a highly sophisticated attack” General Peter Pace USMC (Retired) addressing USCCU about Russia cyber attacking Georgia
 US Army District of Washington web site was hacked from Turkey After Israel “Operation Cast Lead” started in Gaza Dec 2008
US Army District of Washington web site was hacked from Turkey After Israel “Operation Cast Lead” started in Gaza Dec 2008

 Google Likely Saying Goodbye To China In mid- December, Google said in a blog posting yesterday, the company discovered "a highly sophisticated and targeted attack on our corporate infrastructure originating from China that resulted in theft of intellectual property from Google. However, it soon became clear that what at first appeared to be solely a security incident--albeit significant one--was something quite different. " First, Google said, it found out that the attack on it apparently was part of a coordinated attack against at least 20 other large companies, many of which seem to be US- based. According to the Washington Post, it was more like 34 companies. Second, Google says it has evidence suggesting that "a primary goal of the attackers was accessing the Gmail accounts of Chinese human rights activists. " Google also said that it didn't believe that more than two GMail accounts were successfully accessed, however. Third, Google did find that dozens of accounts of "US- , China- and Europe- based Gmail users who are advocates of human rights in China appear to have been routinely accessed by third parties" apparently through persistent phishing and other malware attacks. As a result, this and other problems with its operations in China has led Google "to conclude that we should review the feasibility of our business operations in China. We have decided we are no longer willing to continue censoring our results on Google. cn, and so over the next few weeks we will be discussing with the Chinese government the basis on which we could operate an unfiltered search engine within the law, if at all. We recognize that this may well mean having to shut down Google. cn, and potentially our offices in China. " Needless to say, Google's announcement has set off a firestorm that more than one newspaper has said may impact US- China relations.
Google Likely Saying Goodbye To China In mid- December, Google said in a blog posting yesterday, the company discovered "a highly sophisticated and targeted attack on our corporate infrastructure originating from China that resulted in theft of intellectual property from Google. However, it soon became clear that what at first appeared to be solely a security incident--albeit significant one--was something quite different. " First, Google said, it found out that the attack on it apparently was part of a coordinated attack against at least 20 other large companies, many of which seem to be US- based. According to the Washington Post, it was more like 34 companies. Second, Google says it has evidence suggesting that "a primary goal of the attackers was accessing the Gmail accounts of Chinese human rights activists. " Google also said that it didn't believe that more than two GMail accounts were successfully accessed, however. Third, Google did find that dozens of accounts of "US- , China- and Europe- based Gmail users who are advocates of human rights in China appear to have been routinely accessed by third parties" apparently through persistent phishing and other malware attacks. As a result, this and other problems with its operations in China has led Google "to conclude that we should review the feasibility of our business operations in China. We have decided we are no longer willing to continue censoring our results on Google. cn, and so over the next few weeks we will be discussing with the Chinese government the basis on which we could operate an unfiltered search engine within the law, if at all. We recognize that this may well mean having to shut down Google. cn, and potentially our offices in China. " Needless to say, Google's announcement has set off a firestorm that more than one newspaper has said may impact US- China relations.
 Google probing possible inside help on attack Mon Jan 18, 8: 55 am ET SHANGHAI (Reuters) – Google is investigating whether one or more employees may have helped facilitate a cyber- attack that the U. S. search giant said it was a victim of in mid - December, two sources told Reuters on Monday. Google, the world's most popular search engine, said last week it may pull out of the world's biggest Internet market by users after reporting it had been hit by a "sophisticated" cyber- attack on its network that resulted in theft of its intellectual property. The sources, who are familiar with the situation, told Reuters that the attack, which targeted people who have access to specific parts of Google networks, may have been facilitated by people working in Google China's office.
Google probing possible inside help on attack Mon Jan 18, 8: 55 am ET SHANGHAI (Reuters) – Google is investigating whether one or more employees may have helped facilitate a cyber- attack that the U. S. search giant said it was a victim of in mid - December, two sources told Reuters on Monday. Google, the world's most popular search engine, said last week it may pull out of the world's biggest Internet market by users after reporting it had been hit by a "sophisticated" cyber- attack on its network that resulted in theft of its intellectual property. The sources, who are familiar with the situation, told Reuters that the attack, which targeted people who have access to specific parts of Google networks, may have been facilitated by people working in Google China's office.
 Professor: “. . . what interesting problems she had found in her work. ” Major X: “the press had concluded that these attacks were coming from Nth Korea. North Korea has expanded its ‘cyber combat’ unit in charge of intelligence gathering through the internet claimed a source in Asia. ” “The General Staff of the Nth Korean Peoples Army has for years been running what it calls the ‘technology reconnaissance team’ which consists of about 100 hackers, mostly graduates of a leading military academy in Pyongyang. ” Professor: “Do you think this is coming from Korea? ” Major X: “No, I don’t think they’re that good” Professor: “Where are they from? ” Major X: “A lot of things that we see are coming from a single IP address in China. They are making no effort to disguise the origin” Professor: “So either they’re being brazen, or someone is doing a good job of making you believe they’re being brazen” Professor Alan Grier speaking with a Major after she attended DEF CON IEEE Computer Dec 09
Professor: “. . . what interesting problems she had found in her work. ” Major X: “the press had concluded that these attacks were coming from Nth Korea. North Korea has expanded its ‘cyber combat’ unit in charge of intelligence gathering through the internet claimed a source in Asia. ” “The General Staff of the Nth Korean Peoples Army has for years been running what it calls the ‘technology reconnaissance team’ which consists of about 100 hackers, mostly graduates of a leading military academy in Pyongyang. ” Professor: “Do you think this is coming from Korea? ” Major X: “No, I don’t think they’re that good” Professor: “Where are they from? ” Major X: “A lot of things that we see are coming from a single IP address in China. They are making no effort to disguise the origin” Professor: “So either they’re being brazen, or someone is doing a good job of making you believe they’re being brazen” Professor Alan Grier speaking with a Major after she attended DEF CON IEEE Computer Dec 09
 “. . . depicting China as a threat to space & cyber security is perhaps hasty when one contrast NASA’s budget of $17 B with China’s stated $500 M space budget. Its recent supercomputer, the 17 th most powerful in the world, made headlines but China still has leaps and bounds before. . . matching the US in computer power. . China possesses a mere 16 supercomputers in comparison to America’s 291” Captain Timothy Hsia, US Army December 09 US Naval Institute Proceedings
“. . . depicting China as a threat to space & cyber security is perhaps hasty when one contrast NASA’s budget of $17 B with China’s stated $500 M space budget. Its recent supercomputer, the 17 th most powerful in the world, made headlines but China still has leaps and bounds before. . . matching the US in computer power. . China possesses a mere 16 supercomputers in comparison to America’s 291” Captain Timothy Hsia, US Army December 09 US Naval Institute Proceedings

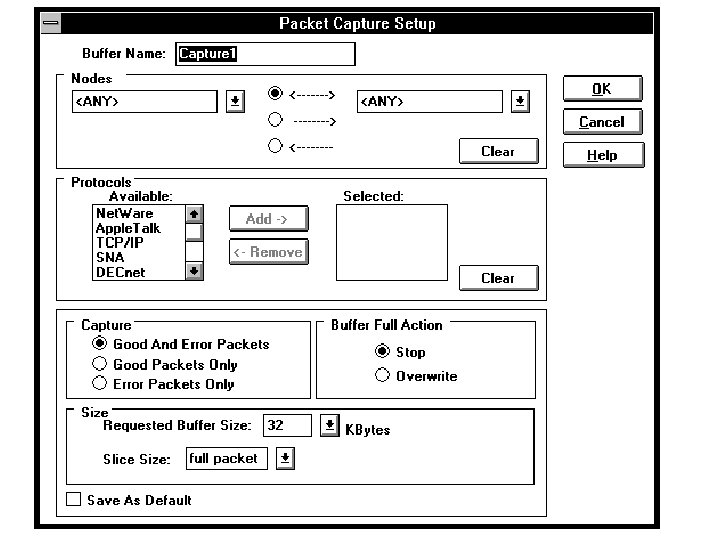
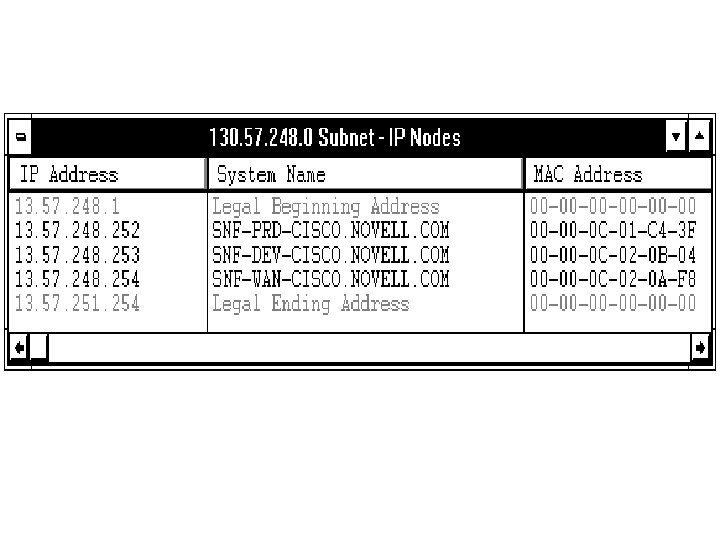
 Some Attack Tools Ping target Patches & updates Tracert destination Insiders Pathping target USB Ports Netsh diag (switches) Next Generation Jammer Nmap Supershark Megapanzer Black. Ice Pwdump Satan (Saint) Superscan Skypetrojan
Some Attack Tools Ping target Patches & updates Tracert destination Insiders Pathping target USB Ports Netsh diag (switches) Next Generation Jammer Nmap Supershark Megapanzer Black. Ice Pwdump Satan (Saint) Superscan Skypetrojan
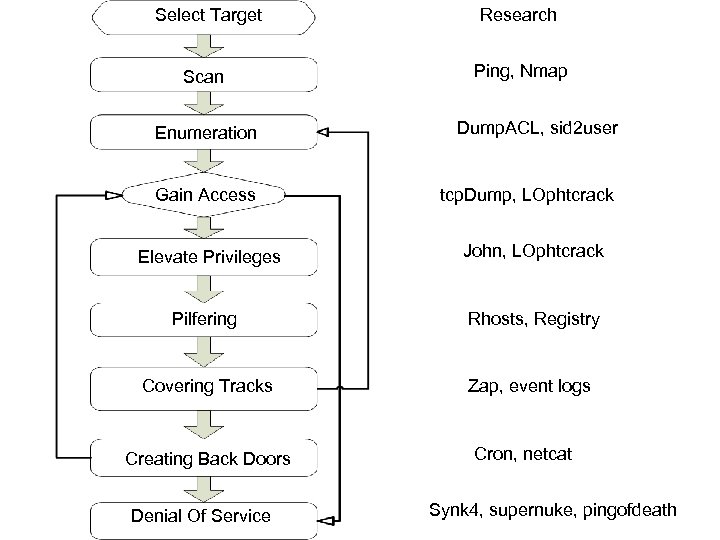 Select Target Research Scan (ping) Scan Ping, Nmap Enumeration Dump. ACL, sid 2 user Gain Access tcp. Dump, LOphtcrack Escalate Privilege Elevate Privileges John, LOphtcrack Pilfering Rhosts, Registry Covering Tracks Creating Back Doors Denial Of Service Zap, event logs Cron, netcat Synk 4, supernuke, pingofdeath
Select Target Research Scan (ping) Scan Ping, Nmap Enumeration Dump. ACL, sid 2 user Gain Access tcp. Dump, LOphtcrack Escalate Privilege Elevate Privileges John, LOphtcrack Pilfering Rhosts, Registry Covering Tracks Creating Back Doors Denial Of Service Zap, event logs Cron, netcat Synk 4, supernuke, pingofdeath
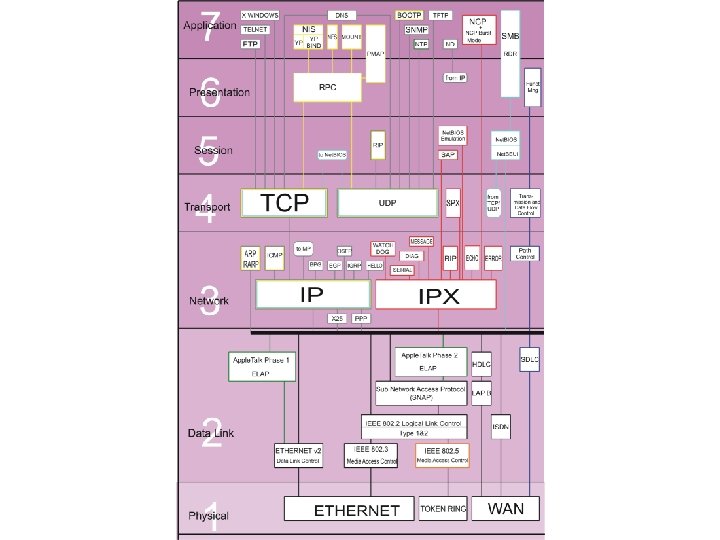
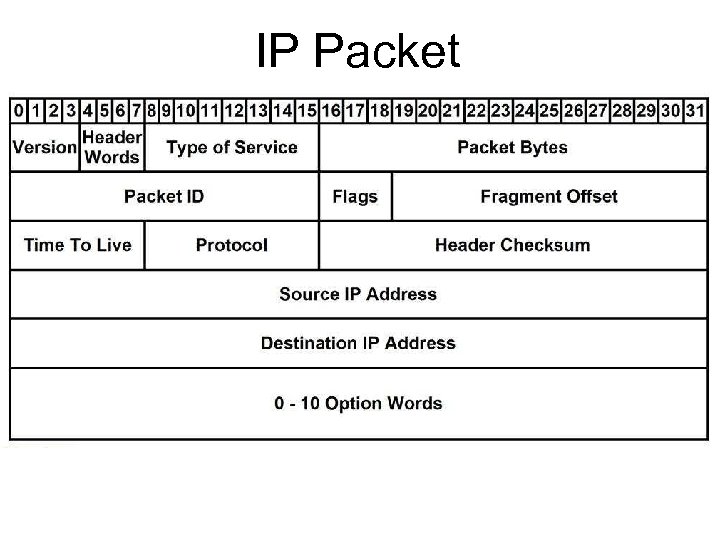 IP Packet
IP Packet
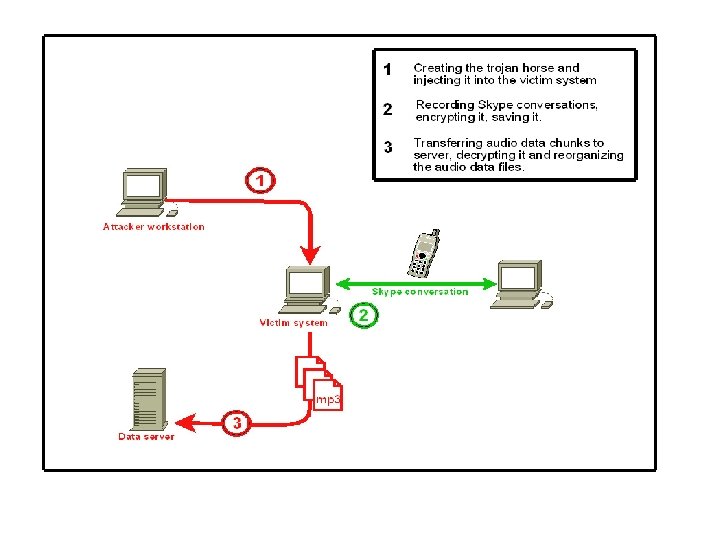
 Some defence Tools Netstat (switches) Ipconfig (switches) Check Router Status Air. Snare Honeypots P 0 f Superglue
Some defence Tools Netstat (switches) Ipconfig (switches) Check Router Status Air. Snare Honeypots P 0 f Superglue
 What is p 0 f v 2? P 0 f v 2 is a versatile passive OS fingerprinting tool. P 0 f can identify the operating system on: - machines that connect to your box (SYN mode), - machines you connect to (SYN+ACK mode), - machine you cannot connect to (RST+ mode), - machines whose communications you can observe. P 0 f can also do many other tricks, and can detect or measure the following: - firewall presence, NAT use (useful for policy enforcement), - existence of a load balancer setup, - the distance to the remote system and its uptime, - other guy's network hoockup (DSL, OC 3, avian carriers) and his ISP. All this even when the device in question is behind an overzealous packet firewall, when our favourite active scanner can't do much. P 0 f does not generate ANY additional network traffic, direct or indirect. No name lookups, no mysterious probes, no ARIN queries, nothing. Show me! 194. 236. 50. 173: 2502 - Linux 2. 2 (1) [Bonet Sweden] (up: 9 hrs) - > 217. 8. 32. 51: 80 (distance 5, link: ethernet/modem) >> Masquerade at 206. 157. 248. 34/ns 1. mosaicsoftware. com: indicators at 43%. >> Masquerade at 213. 158. 197. 100/ptcnat. era. pl: indicators at 60%. >> Masquerade at 216. 88. 158. 142/crawlers. looksmart. com: indicators at 52%. >> Masquerade at 193. 110. 121. 3/evil. tpi. pl: indicators at 86%. Why? P 0 f is quite useful for gathering all kinds of profiling information about your users, customers or attackers (IDS, honeypot, firewall), tech espionage (laugh. . . ), active or passive policy enforcement (restricting access for certain systems or otherwise handling them differently; or detecting guys with illegal network hookups using masquerade detection), content optimization, pen -testing (especially with SYN+ACK and RST+ACK modes), thru -firewall fingerprinting. . . plus all the tasks active fingerprinting is suitable for. P 0 f v 2 is lightweight, secure and fast enough to be run almost anywhere, hands -free for an extended period of time.
What is p 0 f v 2? P 0 f v 2 is a versatile passive OS fingerprinting tool. P 0 f can identify the operating system on: - machines that connect to your box (SYN mode), - machines you connect to (SYN+ACK mode), - machine you cannot connect to (RST+ mode), - machines whose communications you can observe. P 0 f can also do many other tricks, and can detect or measure the following: - firewall presence, NAT use (useful for policy enforcement), - existence of a load balancer setup, - the distance to the remote system and its uptime, - other guy's network hoockup (DSL, OC 3, avian carriers) and his ISP. All this even when the device in question is behind an overzealous packet firewall, when our favourite active scanner can't do much. P 0 f does not generate ANY additional network traffic, direct or indirect. No name lookups, no mysterious probes, no ARIN queries, nothing. Show me! 194. 236. 50. 173: 2502 - Linux 2. 2 (1) [Bonet Sweden] (up: 9 hrs) - > 217. 8. 32. 51: 80 (distance 5, link: ethernet/modem) >> Masquerade at 206. 157. 248. 34/ns 1. mosaicsoftware. com: indicators at 43%. >> Masquerade at 213. 158. 197. 100/ptcnat. era. pl: indicators at 60%. >> Masquerade at 216. 88. 158. 142/crawlers. looksmart. com: indicators at 52%. >> Masquerade at 193. 110. 121. 3/evil. tpi. pl: indicators at 86%. Why? P 0 f is quite useful for gathering all kinds of profiling information about your users, customers or attackers (IDS, honeypot, firewall), tech espionage (laugh. . . ), active or passive policy enforcement (restricting access for certain systems or otherwise handling them differently; or detecting guys with illegal network hookups using masquerade detection), content optimization, pen -testing (especially with SYN+ACK and RST+ACK modes), thru -firewall fingerprinting. . . plus all the tasks active fingerprinting is suitable for. P 0 f v 2 is lightweight, secure and fast enough to be run almost anywhere, hands -free for an extended period of time.
 A Few Words about Web 2. 0
A Few Words about Web 2. 0


