cc926d8ef8708e28f730470ecd3de568.ppt
- Количество слайдов: 27
 System Security and U. Rich Pethia Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 This work is sponsored by the U. S. Department of Defense. 1 2002 Carnegie Mellon University
System Security and U. Rich Pethia Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 This work is sponsored by the U. S. Department of Defense. 1 2002 Carnegie Mellon University
 CERT Coordination Center The SEI established the Computer Emergency Response Team Coordination Center in 1988. The CERT/CC’s mission is to respond to security emergencies on the Internet, serve as a focal point for reporting and resolving security vulnerabilities, serve as a model to help others establish incident response teams, and raise awareness of security issues. 2 2002 Carnegie Mellon University
CERT Coordination Center The SEI established the Computer Emergency Response Team Coordination Center in 1988. The CERT/CC’s mission is to respond to security emergencies on the Internet, serve as a focal point for reporting and resolving security vulnerabilities, serve as a model to help others establish incident response teams, and raise awareness of security issues. 2 2002 Carnegie Mellon University
 Activity Since 1988, the CERT/CC has responded to over 100, 000 security incidents that have affected hundreds of thousands of Internet sites; has worked over 5000 reported vulnerabilities, and has issued hundreds of advisories and bulletins. In addition, the CERT/CC has helped foster the creation of over 90 other incident response teams. 3 2002 Carnegie Mellon University
Activity Since 1988, the CERT/CC has responded to over 100, 000 security incidents that have affected hundreds of thousands of Internet sites; has worked over 5000 reported vulnerabilities, and has issued hundreds of advisories and bulletins. In addition, the CERT/CC has helped foster the creation of over 90 other incident response teams. 3 2002 Carnegie Mellon University
 The Internet has Become Indispensable to Business, Government, Universities The Internet allows organizations to: • conduct electronic commerce • provide better customer service • collaborate with business & research partners • reduce communications costs • improve internal communication • access needed information rapidly 4 2002 Carnegie Mellon University
The Internet has Become Indispensable to Business, Government, Universities The Internet allows organizations to: • conduct electronic commerce • provide better customer service • collaborate with business & research partners • reduce communications costs • improve internal communication • access needed information rapidly 4 2002 Carnegie Mellon University
 The Risks While computer networks revolutionize the way you do business, the risks computer networks introduce can be fatal to a business. Network attacks lead to lost: • money • time • products • reputation • lives • sensitive information 5 2002 Carnegie Mellon University
The Risks While computer networks revolutionize the way you do business, the risks computer networks introduce can be fatal to a business. Network attacks lead to lost: • money • time • products • reputation • lives • sensitive information 5 2002 Carnegie Mellon University
 Incidents Reported to CERT/CC 6 2002 Carnegie Mellon University
Incidents Reported to CERT/CC 6 2002 Carnegie Mellon University
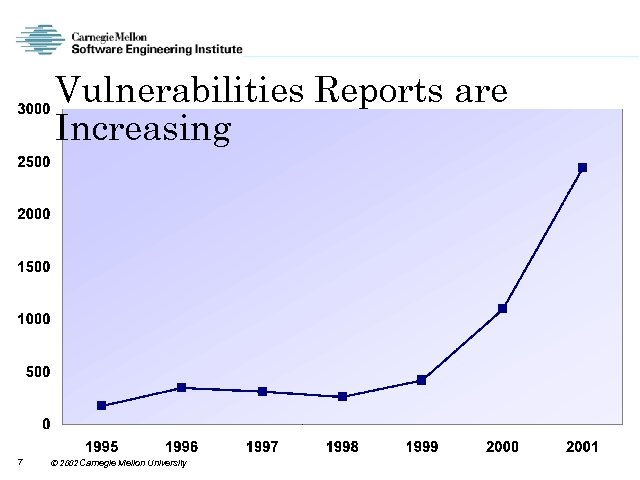 Vulnerabilities Reports are Increasing 7 2002 Carnegie Mellon University
Vulnerabilities Reports are Increasing 7 2002 Carnegie Mellon University
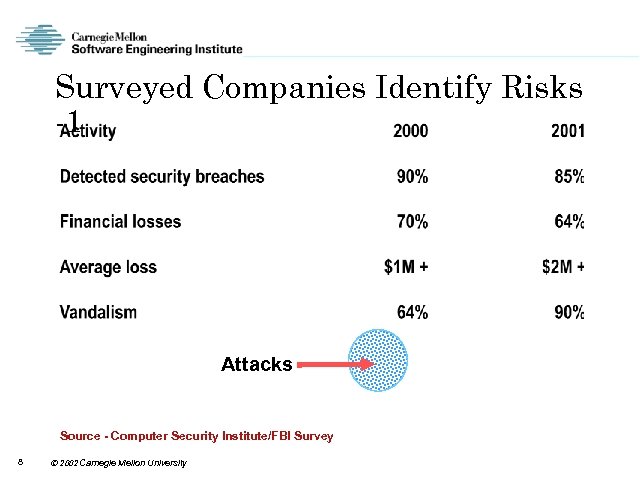 Surveyed Companies Identify Risks -1 Attacks Source - Computer Security Institute/FBI Survey 8 2002 Carnegie Mellon University
Surveyed Companies Identify Risks -1 Attacks Source - Computer Security Institute/FBI Survey 8 2002 Carnegie Mellon University
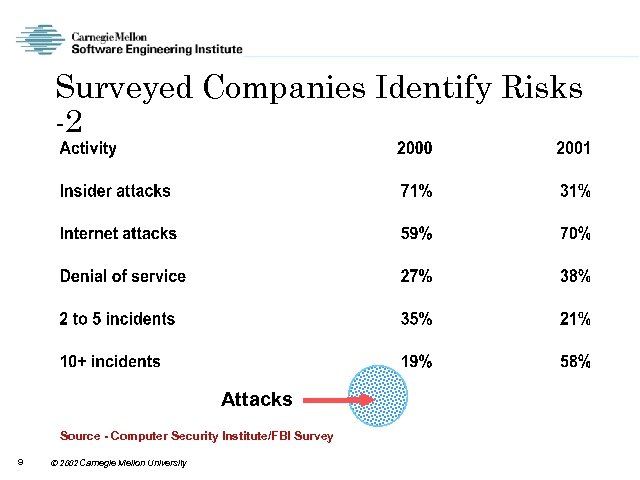 Surveyed Companies Identify Risks -2 Attacks Source - Computer Security Institute/FBI Survey 9 2002 Carnegie Mellon University
Surveyed Companies Identify Risks -2 Attacks Source - Computer Security Institute/FBI Survey 9 2002 Carnegie Mellon University
 How Did We Get Here? 10 2002 Carnegie Mellon University
How Did We Get Here? 10 2002 Carnegie Mellon University
 The Problem In the rush to benefit from using the Internet, organizations often overlook significant risks. • the engineering practices and technology used by system providers do not produce systems that are immune to attack • network and system operators do not have the people and practices to defend against attacks and minimize damage • policy and law in cyber-space are immature and lag the pace of change 11 2002 Carnegie Mellon University
The Problem In the rush to benefit from using the Internet, organizations often overlook significant risks. • the engineering practices and technology used by system providers do not produce systems that are immune to attack • network and system operators do not have the people and practices to defend against attacks and minimize damage • policy and law in cyber-space are immature and lag the pace of change 11 2002 Carnegie Mellon University
 Strain on System Administrators - 1 There is continued movement to complex, client-server, peer to peer, and heterogeneous configurations with distributed management. There is little evidence of security improvements in most products; new vulnerabilities are found routinely. Comprehensive security solutions are lacking; current tools address only parts of the problem. 12 2002 Carnegie Mellon University
Strain on System Administrators - 1 There is continued movement to complex, client-server, peer to peer, and heterogeneous configurations with distributed management. There is little evidence of security improvements in most products; new vulnerabilities are found routinely. Comprehensive security solutions are lacking; current tools address only parts of the problem. 12 2002 Carnegie Mellon University
 Strain on System Administrators - 2 Engineering for ease of use has not been matched by engineering for ease of secure administration • ease of use and increased utility are driving a dramatic explosion in use • system administration and security administration are more difficult than a decade ago • this growing gap brings increased vulnerability 13 2002 Carnegie Mellon University
Strain on System Administrators - 2 Engineering for ease of use has not been matched by engineering for ease of secure administration • ease of use and increased utility are driving a dramatic explosion in use • system administration and security administration are more difficult than a decade ago • this growing gap brings increased vulnerability 13 2002 Carnegie Mellon University
 Other Reasons for Concern Many security audits and evaluations only skim the surface of the organization and its technology; major risks are often overlooked. Lack of understanding leads to reliance on partial solutions. 14 2002 Carnegie Mellon University
Other Reasons for Concern Many security audits and evaluations only skim the surface of the organization and its technology; major risks are often overlooked. Lack of understanding leads to reliance on partial solutions. 14 2002 Carnegie Mellon University
 More Sophisticated Intruders are • growing in number and type • building technical knowledge and skills • gaining leverage through automation • building skills in vulnerability discovery • becoming more skilled at masking their behavior 15 2002 Carnegie Mellon University
More Sophisticated Intruders are • growing in number and type • building technical knowledge and skills • gaining leverage through automation • building skills in vulnerability discovery • becoming more skilled at masking their behavior 15 2002 Carnegie Mellon University
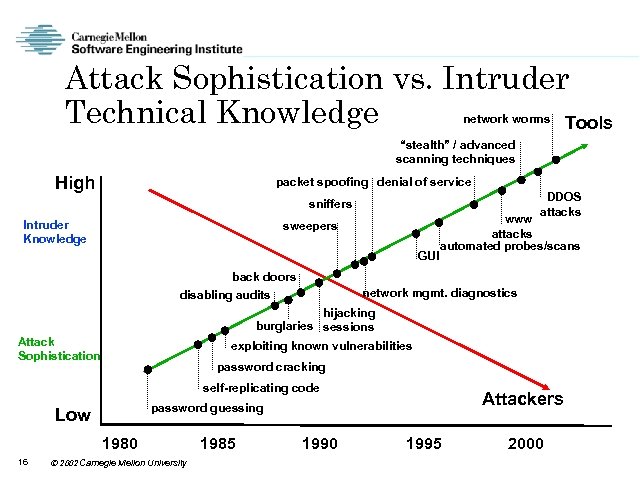 Attack Sophistication vs. Intruder Technical Knowledge Tools network worms “stealth” / advanced scanning techniques High packet spoofing denial of service DDOS attacks sniffers Intruder Knowledge sweepers GUI back doors disabling audits www attacks automated probes/scans network mgmt. diagnostics hijacking burglaries sessions Attack Sophistication exploiting known vulnerabilities password cracking self-replicating code Low 1980 16 Attackers password guessing 2002 Carnegie Mellon University 1985 1990 1995 2000
Attack Sophistication vs. Intruder Technical Knowledge Tools network worms “stealth” / advanced scanning techniques High packet spoofing denial of service DDOS attacks sniffers Intruder Knowledge sweepers GUI back doors disabling audits www attacks automated probes/scans network mgmt. diagnostics hijacking burglaries sessions Attack Sophistication exploiting known vulnerabilities password cracking self-replicating code Low 1980 16 Attackers password guessing 2002 Carnegie Mellon University 1985 1990 1995 2000
 So What? 17 2002 Carnegie Mellon University
So What? 17 2002 Carnegie Mellon University
 Its going to get worse - 1 Explosive growth of the Internet continues • where will all the capable system administrators come from? Market growth will drive vendors • time to market, features, performance, cost are primary • “invisible” quality features such as security are secondary 18 2002 Carnegie Mellon University
Its going to get worse - 1 Explosive growth of the Internet continues • where will all the capable system administrators come from? Market growth will drive vendors • time to market, features, performance, cost are primary • “invisible” quality features such as security are secondary 18 2002 Carnegie Mellon University
 Its going to get worse - 2 More sensitive applications connected to the Internet • low cost of communications, ease of connection, and power of products engineered for the Internet will drive out other forms of networking • hunger for connectivity, data and benefits of electronic interaction will continue to push widespread use of Internet technology 19 2002 Carnegie Mellon University
Its going to get worse - 2 More sensitive applications connected to the Internet • low cost of communications, ease of connection, and power of products engineered for the Internet will drive out other forms of networking • hunger for connectivity, data and benefits of electronic interaction will continue to push widespread use of Internet technology 19 2002 Carnegie Mellon University
 Its going to get worse - 3 The death of the firewall • traditional approaches depend on complete administrative control and strong perimeter controls • today’s business practices and wide area networks violate these basic principles -no central point of network control -more interconnections with customers, suppliers, partners -more network applications - “the network is the computer” -who’s an “insider”and who’s an “outsider” 20 2002 Carnegie Mellon University
Its going to get worse - 3 The death of the firewall • traditional approaches depend on complete administrative control and strong perimeter controls • today’s business practices and wide area networks violate these basic principles -no central point of network control -more interconnections with customers, suppliers, partners -more network applications - “the network is the computer” -who’s an “insider”and who’s an “outsider” 20 2002 Carnegie Mellon University
 What Can You Do Now? 21 2002 Carnegie Mellon University
What Can You Do Now? 21 2002 Carnegie Mellon University
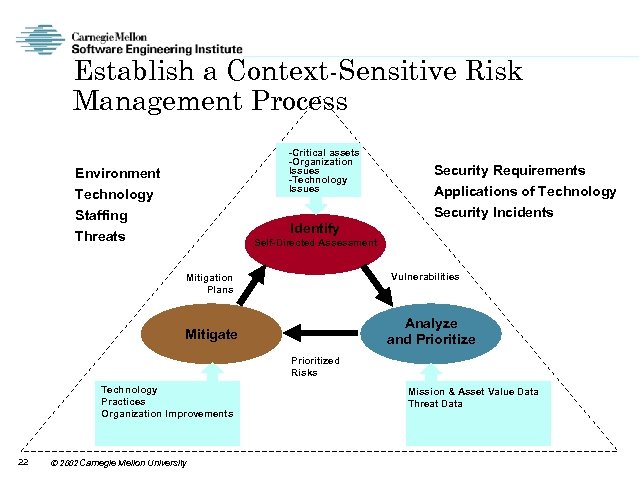 Establish a Context-Sensitive Risk Management Process -Critical assets -Organization Issues -Technology Issues Environment Technology Staffing Threats Identify Security Requirements Applications of Technology Security Incidents Self-Directed Assessment Vulnerabilities Mitigation Plans Analyze and Prioritize Mitigate Prioritized Risks Technology Practices Organization Improvements 22 2002 Carnegie Mellon University Mission & Asset Value Data Threat Data
Establish a Context-Sensitive Risk Management Process -Critical assets -Organization Issues -Technology Issues Environment Technology Staffing Threats Identify Security Requirements Applications of Technology Security Incidents Self-Directed Assessment Vulnerabilities Mitigation Plans Analyze and Prioritize Mitigate Prioritized Risks Technology Practices Organization Improvements 22 2002 Carnegie Mellon University Mission & Asset Value Data Threat Data
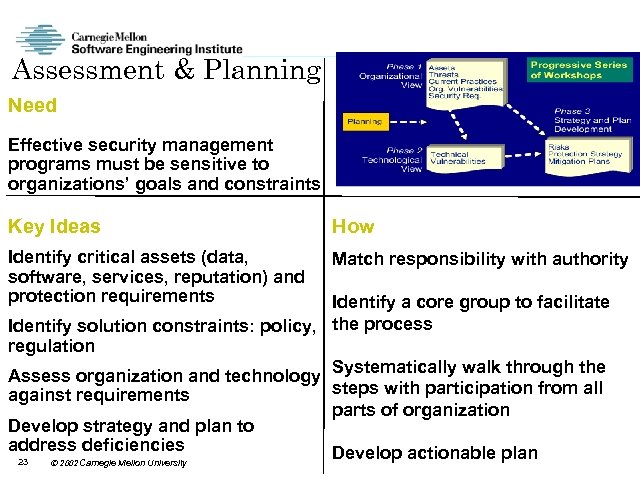 Assessment & Planning Need Effective security management programs must be sensitive to organizations’ goals and constraints. Key Ideas How Identify critical assets (data, software, services, reputation) and protection requirements Match responsibility with authority Identify a core group to facilitate Identify solution constraints: policy, the process regulation Systematically walk through the Assess organization and technology steps with participation from all against requirements parts of organization Develop strategy and plan to address deficiencies Develop actionable plan 23 2002 Carnegie Mellon University
Assessment & Planning Need Effective security management programs must be sensitive to organizations’ goals and constraints. Key Ideas How Identify critical assets (data, software, services, reputation) and protection requirements Match responsibility with authority Identify a core group to facilitate Identify solution constraints: policy, the process regulation Systematically walk through the Assess organization and technology steps with participation from all against requirements parts of organization Develop strategy and plan to address deficiencies Develop actionable plan 23 2002 Carnegie Mellon University
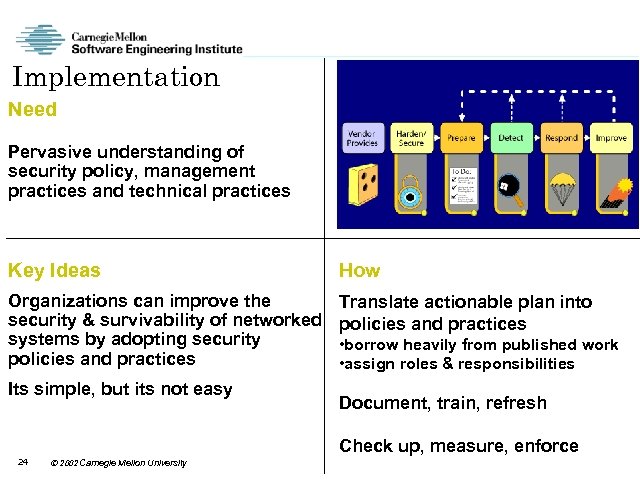 Implementation Need Pervasive understanding of security policy, management practices and technical practices Key Ideas How Organizations can improve the security & survivability of networked systems by adopting security policies and practices Translate actionable plan into policies and practices Its simple, but its not easy • borrow heavily from published work • assign roles & responsibilities Document, train, refresh Check up, measure, enforce 24 2002 Carnegie Mellon University
Implementation Need Pervasive understanding of security policy, management practices and technical practices Key Ideas How Organizations can improve the security & survivability of networked systems by adopting security policies and practices Translate actionable plan into policies and practices Its simple, but its not easy • borrow heavily from published work • assign roles & responsibilities Document, train, refresh Check up, measure, enforce 24 2002 Carnegie Mellon University
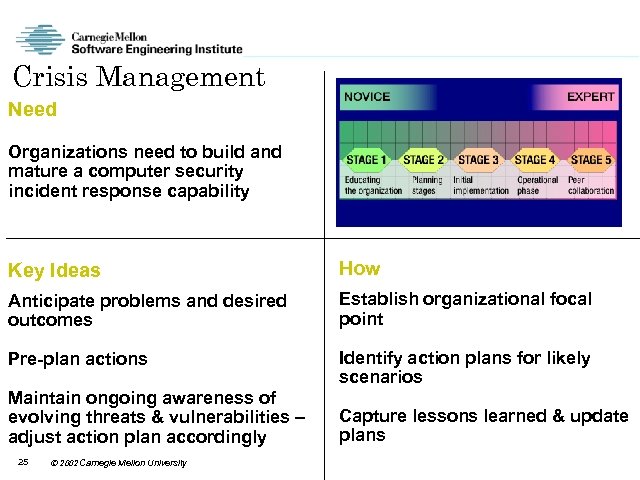 Crisis Management Need Organizations need to build and mature a computer security incident response capability Key Ideas How Anticipate problems and desired outcomes Establish organizational focal point Pre-plan actions Identify action plans for likely scenarios Maintain ongoing awareness of evolving threats & vulnerabilities – adjust action plan accordingly Capture lessons learned & update plans 25 2002 Carnegie Mellon University
Crisis Management Need Organizations need to build and mature a computer security incident response capability Key Ideas How Anticipate problems and desired outcomes Establish organizational focal point Pre-plan actions Identify action plans for likely scenarios Maintain ongoing awareness of evolving threats & vulnerabilities – adjust action plan accordingly Capture lessons learned & update plans 25 2002 Carnegie Mellon University
 Get Plugged In Need Many of today’s solutions won’t work tomorrow. Key Ideas How Structured networking helps organizations stay on top of a dynamic and rapidly changing problem Identify networking opportunities (ISA, ISACs, ISSA, Infra. Guard, I 4, FIRST, etc. ) Sharing lessons learned leads to better practices and policies 26 2002 Carnegie Mellon University Plug in to group(s) of choice Participate!
Get Plugged In Need Many of today’s solutions won’t work tomorrow. Key Ideas How Structured networking helps organizations stay on top of a dynamic and rapidly changing problem Identify networking opportunities (ISA, ISACs, ISSA, Infra. Guard, I 4, FIRST, etc. ) Sharing lessons learned leads to better practices and policies 26 2002 Carnegie Mellon University Plug in to group(s) of choice Participate!
 CERT Contact Information 24 -hour hotline: Fax: +1 412 268 6989 Web site: http: //www. cert. org/ Electronic mail: cert@cert. org US mail: 27 +1 412 268 7090 CERT personnel answer 8: 30 a. m. — 8: 00 p. m. EST(GMT-5) / EDT(GMT-4), and are on call for emergencies during other hours. CERT Coordination Center Software Engineering Institute Carnegie Mellon University 4500 Fifth Avenue Pittsburgh PA 15213 -3890 USA 2002 Carnegie Mellon University
CERT Contact Information 24 -hour hotline: Fax: +1 412 268 6989 Web site: http: //www. cert. org/ Electronic mail: cert@cert. org US mail: 27 +1 412 268 7090 CERT personnel answer 8: 30 a. m. — 8: 00 p. m. EST(GMT-5) / EDT(GMT-4), and are on call for emergencies during other hours. CERT Coordination Center Software Engineering Institute Carnegie Mellon University 4500 Fifth Avenue Pittsburgh PA 15213 -3890 USA 2002 Carnegie Mellon University


