39de010ea7932665e15e6d6a87ee10d3.ppt
- Количество слайдов: 24

Symmetric Key Ciphers

Stream Ciphers • Begin with a secret key (seed( • Generate a stream of keying material • i-th bit/byte of keying stream is a function of the key and the first i-1 stream bits. • Combine the stream with the plaintext to produce the ciphertext (typically by XOR( • Synchronous
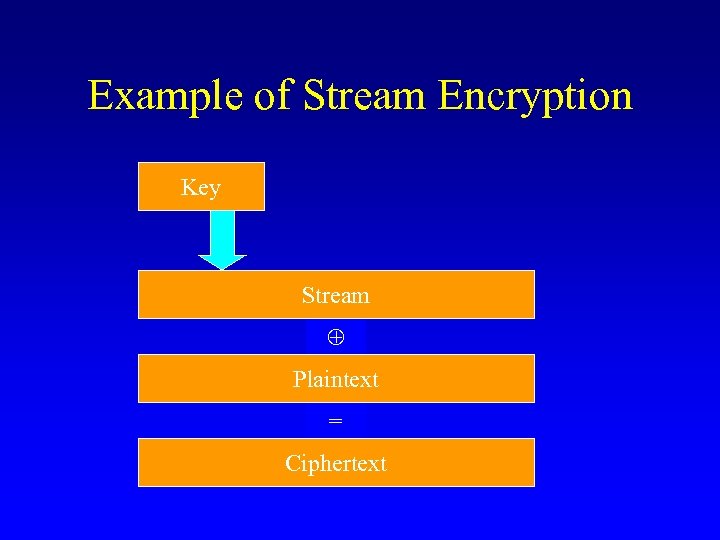
Example of Stream Encryption Key Stream Plaintext = Ciphertext
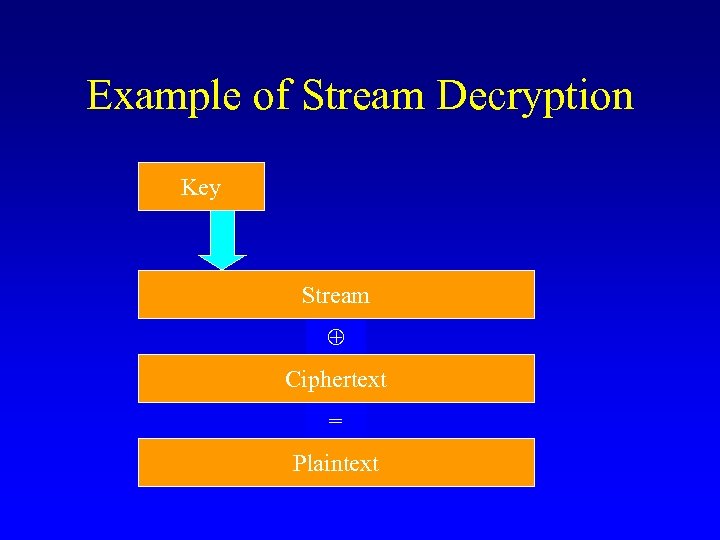
Example of Stream Decryption Key Stream Ciphertext = Plaintext

Real Stream Ciphers • • Most pre-WWII machines German Enigma LFSR A 5 1/2– encrypting GSM handset to base station communication • RC-4

RC-4 in WEP • WEP – Wired Equivalent Privacy, the security protocol of 802. 11 • RC-4 keys are inserted manually to all base stations and handsets in LAN • Encryption is on a network, not point to point, basis • MAC payload is encrypted • Synchronization per MAC frame • Previous standard – 40 bit key, next version 128 bits.

RC-4 in SSL • Point to point communication at the TCP level. • RC-4 keys are exchanged by handshake protocol. • RC-4 keys are used to encrypt single session. • 40 bits to 128 bits in TLS

Attacks on RC-4 • • Short key attack Attacks on WEP implementation of RC-4 Malleability attacks Invariants, non-uniform distribution etc.
Block Ciphers • Encrypt a block of input to a block of output • Typically, the two blocks are of the same length • In most symmetric key systems block size is 64 bits • In newer systems, especially AES it is 128 bits • In some Public key systems the ciphertext is longer than the plaintext and longer than 128 bits • Different modes for encrypting more than a block
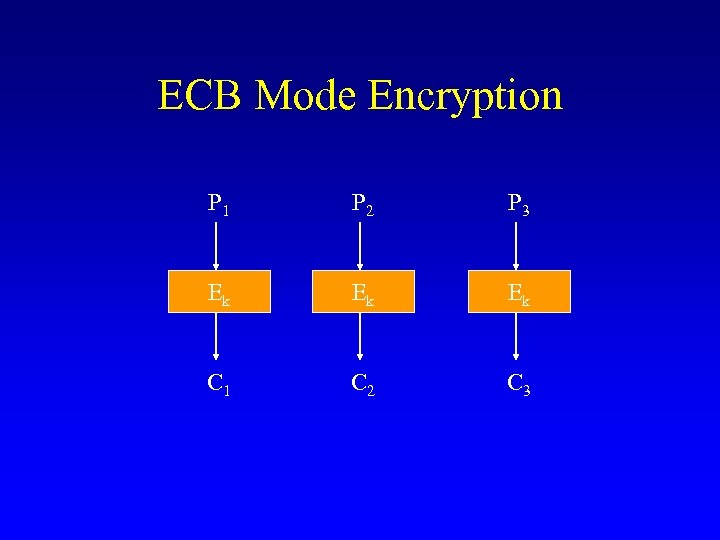
ECB Mode Encryption P 1 P 2 P 3 Ek Ek Ek C 1 C 2 C 3

Properties of ECB • • Simple and efficient Parallel implementation possible Does not conceal patterns Active insertion of blocks is possible
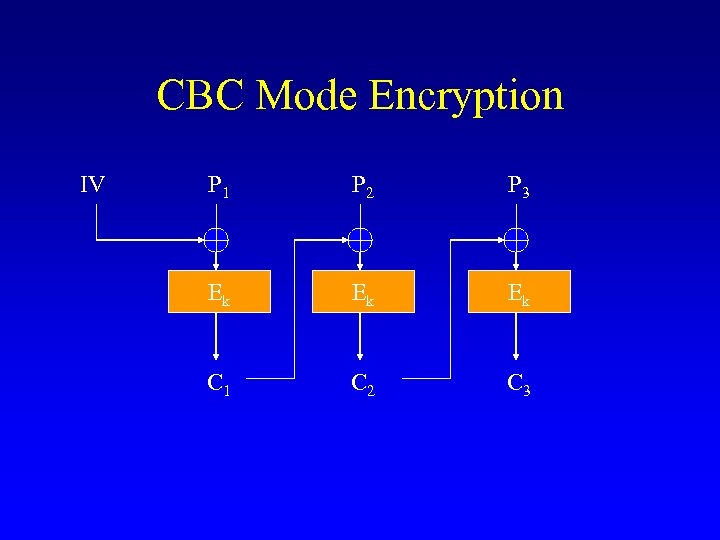
CBC Mode Encryption IV P 1 P 2 P 3 Ek Ek Ek C 1 C 2 C 3

Properties of CBC • • • Asynchronous stream cipher Conceals plaintext patterns (partially( No parallel implementation known Partial malleability Standard in most systems: SSL, IPSec etc.
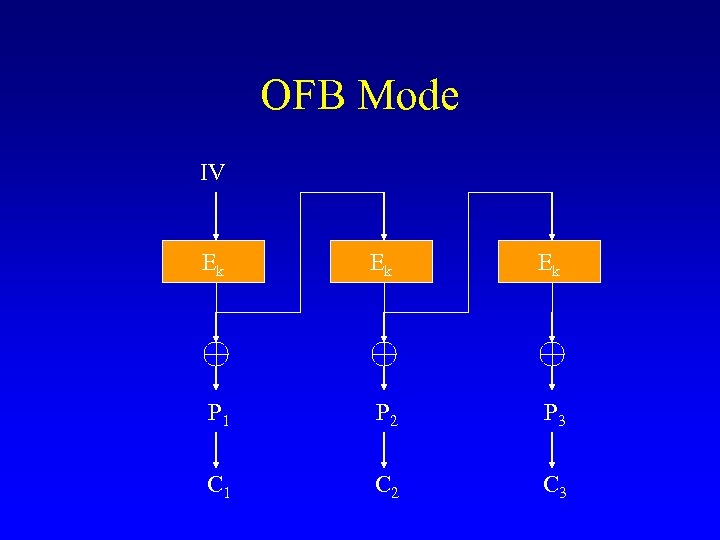
OFB Mode IV Ek Ek Ek P 1 P 2 P 3 C 1 C 2 C 3

Properties of OFB • • Synchronous stream cipher Pre-processing is possible Conceals plaintext patterns No parallel implementation known (except for XOR step( • Malleable (note that CBC is partially malleable(
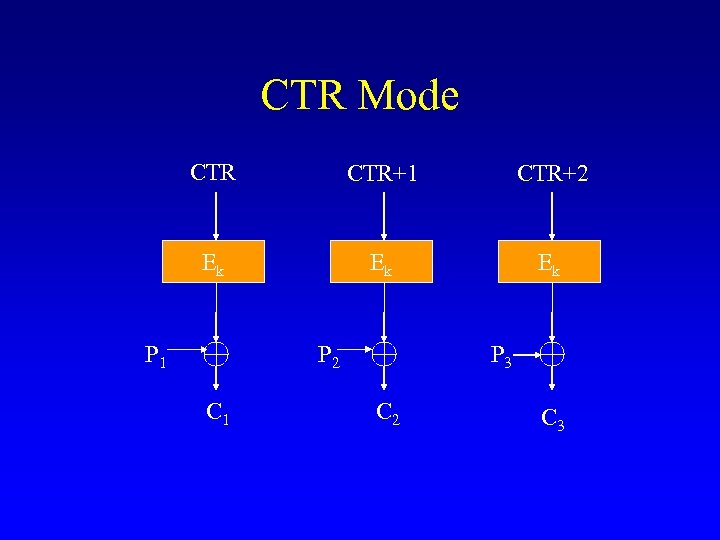
CTR Mode CTR+1 CTR+2 Ek Ek Ek P 1 P 2 C 1 P 3 C 2 C 3
Properties of CTR • • Pre-processing is possible Conceals plaintext patterns Allows parallel implementation Malleable

Strengthening a Cipher • Enlarge key in a cipher family – usually possible in public key systems • Design multiple key lengths – AES • Whitening - the DESX idea • Iterated ciphers – Triple DES (3 -DES), triple IDEA and so on
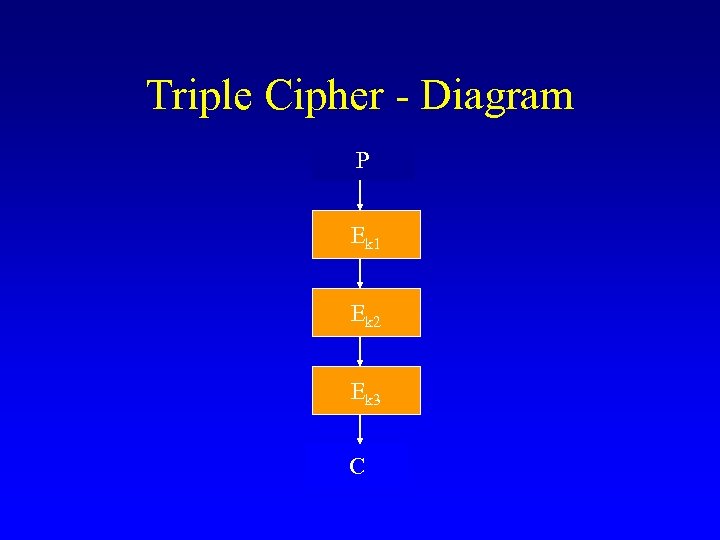
Triple Cipher - Diagram P Ek 1 Ek 2 Ek 3 C
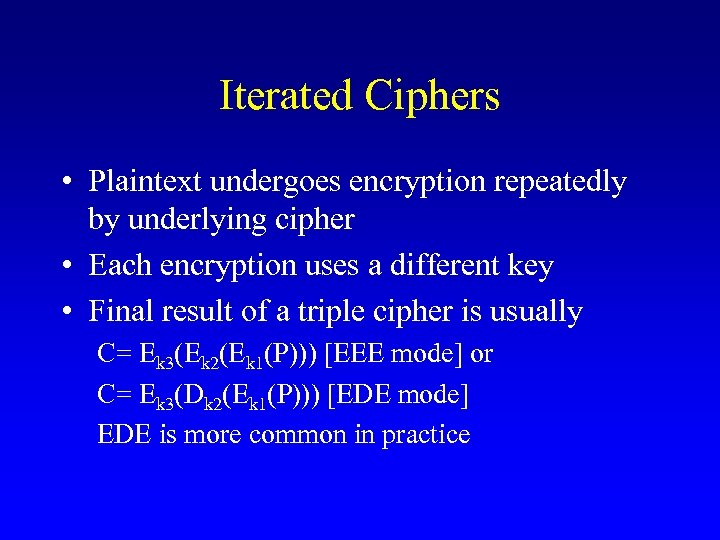
Iterated Ciphers • Plaintext undergoes encryption repeatedly by underlying cipher • Each encryption uses a different key • Final result of a triple cipher is usually C= Ek 3(Ek 2(Ek 1(P))) [EEE mode] or C= Ek 3(Dk 2(Ek 1(P))) [EDE mode] EDE is more common in practice

Meet in the Middle Attack • Double ciphers are rarely used due to this attack • Attack requires – Known plaintext – 2 k+1 encryptions and decryptions – b 2 k storage space • A square root of trivial attacking time at the expense of storage

Meet in the Middle (cont(. • Given a plaintext-ciphertext pair (p, c) – Calculate a table of Dk 2(c) for any k 2 – Test if Ek 1(p) is in table for any k 1 – May have to repeat several times

Two or Three Keys • Sometimes only two keys are used in 3 -DES • Identical key must be at beginning and end • Legal advantage due to smaller overall key size • Used as a KEK in the BPI protocol which secures the DOCSIS cable modem standard

Real World Block Ciphers • • DES, 3 -DES AES (Rijndael) RC-2, RC-5, RC-6 IDEA Blowfish, Cast Gost Kasumi (F 8, A 5/3) Camellia
39de010ea7932665e15e6d6a87ee10d3.ppt