0d94b1a6189465334e538f44ae34ab9d.ppt
- Количество слайдов: 32

Swift: Secure Web Applications via Automatic Partitioning Stephen Chong, Jed Liu, Andrew C. Myers, Xin Qi, K. Vikram, Lantian Zheng, Xin Zheng Cornell University SOSP 2007 (October 15) Speaker: K. Vikram Splitting Webapps via Information Flow Types

Can we make web applications secure? • Ubiquitous, important, yet insecure – 61% of Internet vulnerabilities affect webapps* – Cross-site scripting, SQL injection, Information Leakage, etc. • Development methods lack security reasoning – Distributed system in multiple languages • Client: CSS, XHTML, Java. Script, Flash • Server: PHP, ASP, Ruby, SQL – Ajax/Web 2. 0: Complex Java. Script UIs generating HTTP requests
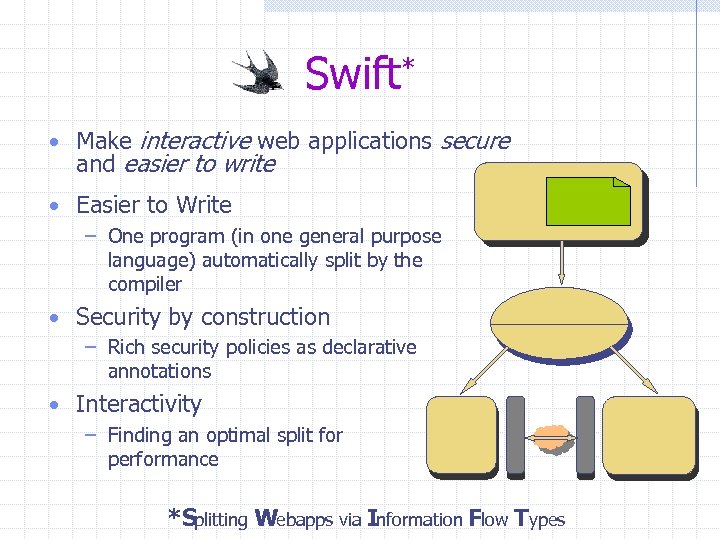
Swift* • Make interactive web applications secure and easier to write • Easier to Write – One program (in one general purpose language) automatically split by the compiler • Security by construction – Rich security policies as declarative annotations • Interactivity – Finding an optimal split for performance *Splitting Webapps via Information Flow Types
The Guess-the-Number Game K. Vikram Swift Cornell University
The Guess-the-Number Game K. Vikram Swift Cornell University
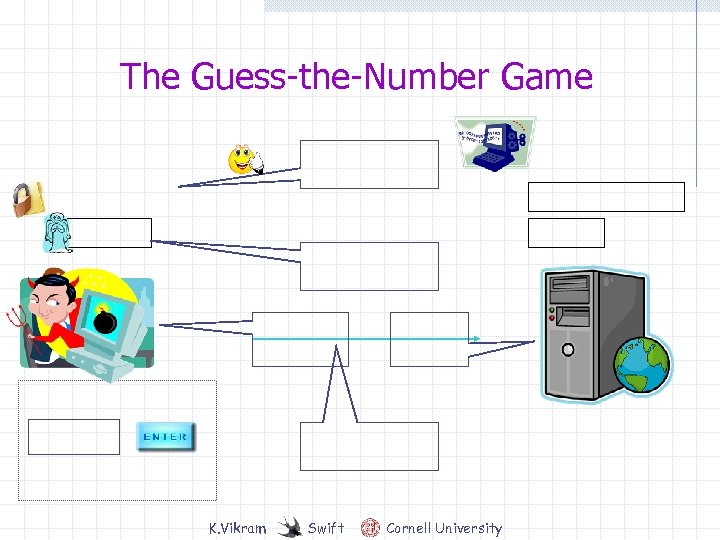
The Guess-the-Number Game K. Vikram Swift Cornell University
The Guess-the-Number Game A secure optimal split K. Vikram Swift Cornell University
K. Vikram Swift Cornell University
K. Vikram Swift Cornell University
K. Vikram Swift Cornell University
K. Vikram Swift Cornell University
K. Vikram Swift Cornell University
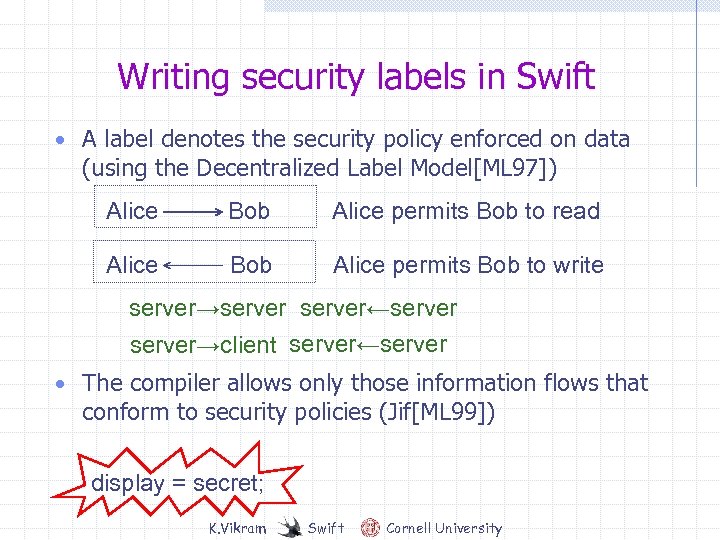
Writing security labels in Swift • A label denotes the security policy enforced on data (using the Decentralized Label Model[ML 97]) Alice Bob Alice permits Bob to read Alice Bob Alice permits Bob to write server→server←server→client server←server • The compiler allows only those information flows that conform to security policies (Jif[ML 99]) display = secret; K. Vikram Swift Cornell University
K. Vikram Swift Cornell University
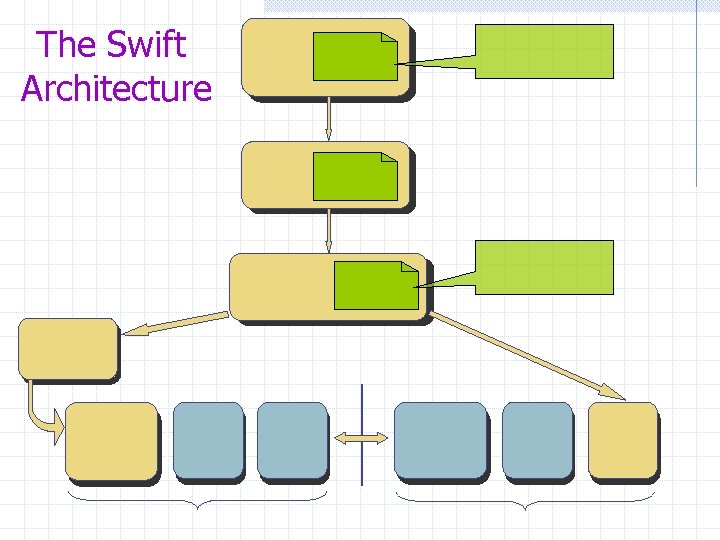
The Swift Architecture
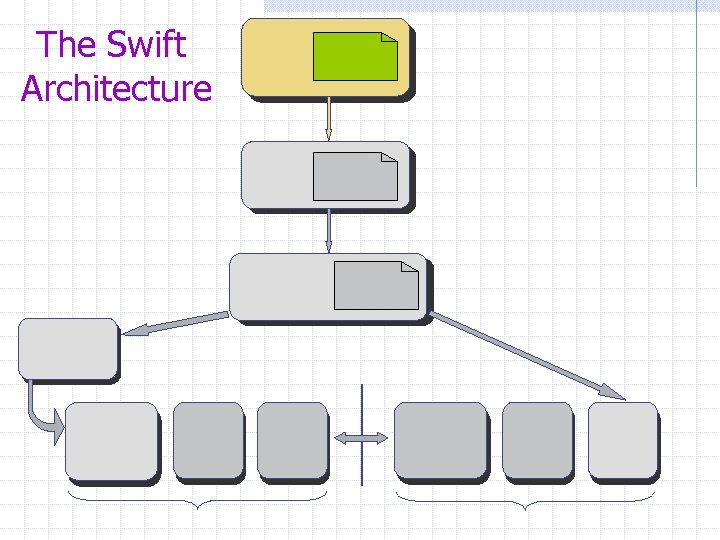
The Swift Architecture
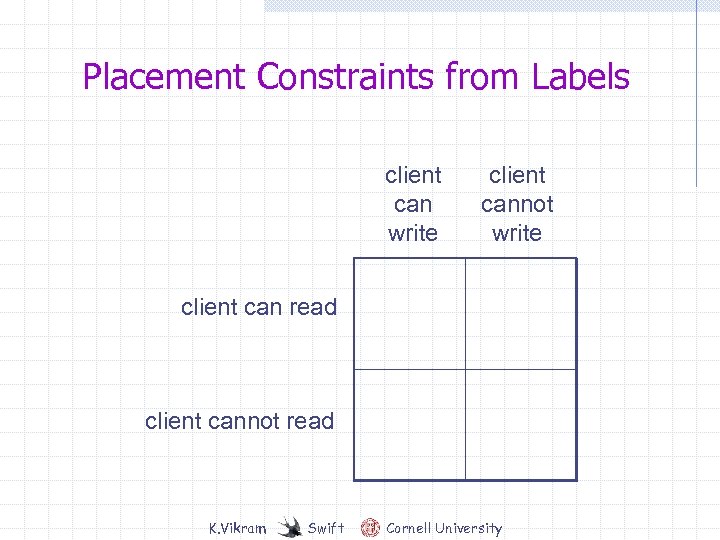
Placement Constraints from Labels client can write client cannot write client can read client cannot read K. Vikram Swift Cornell University
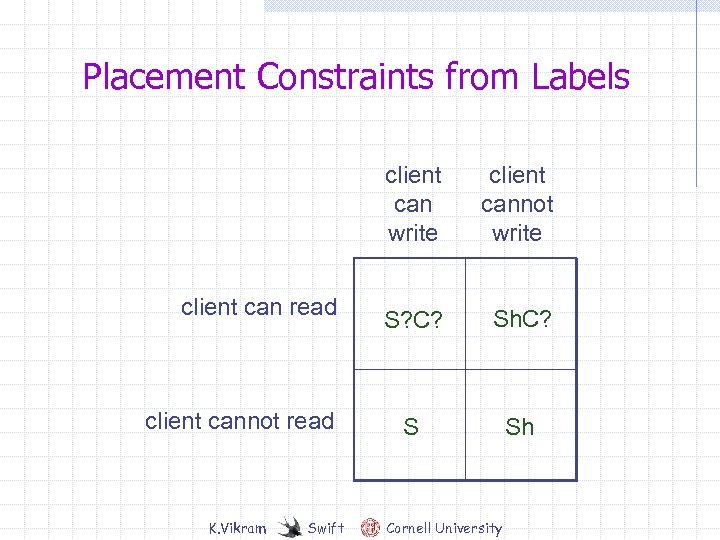
Placement Constraints from Labels client can write client can read client cannot read K. Vikram Swift client cannot write S? C? Sh. C? S Sh Cornell University
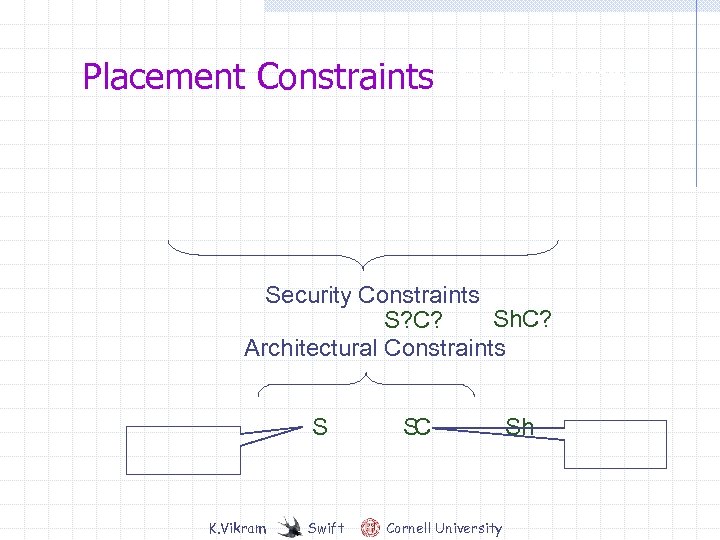
Placement Constraints from Labels Security Constraints Sh. C? S? C? Architectural Constraints S K. Vikram Swift S C Cornell University Sh
K. Vikram Swift Cornell University
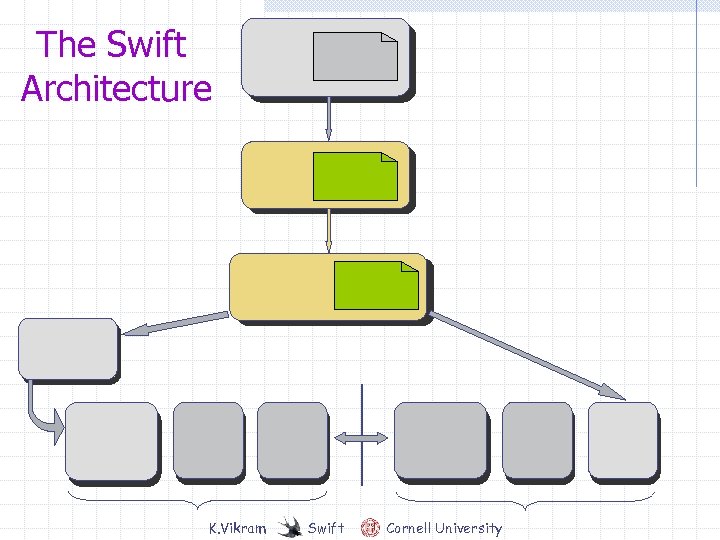
The Swift Architecture K. Vikram Swift Cornell University
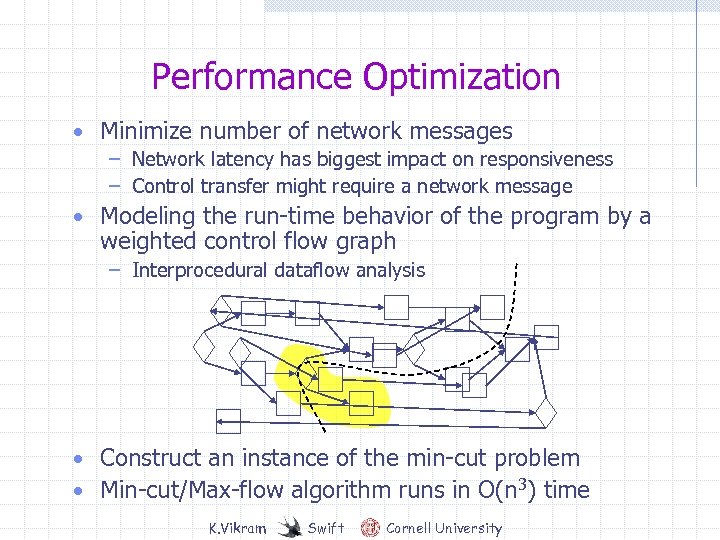
Performance Optimization • Minimize number of network messages – Network latency has biggest impact on responsiveness – Control transfer might require a network message • Modeling the run-time behavior of the program by a weighted control flow graph – Interprocedural dataflow analysis • Construct an instance of the min-cut problem • Min-cut/Max-flow algorithm runs in O(n 3) time K. Vikram Swift Cornell University
K. Vikram Swift Cornell University
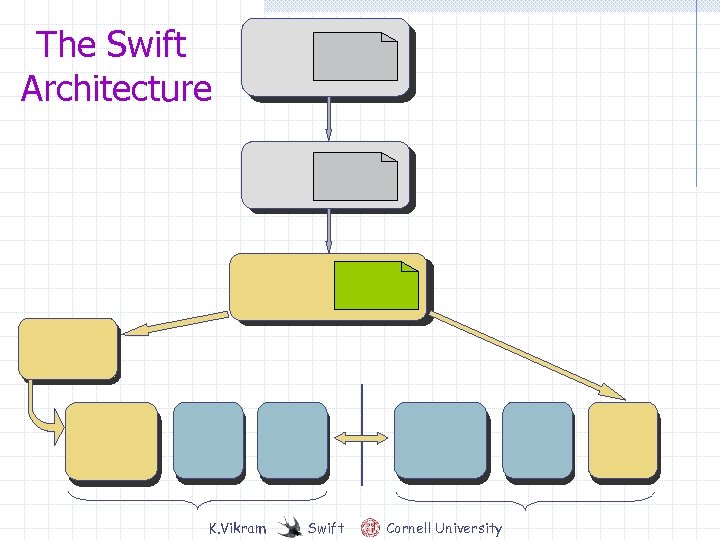
The Swift Architecture K. Vikram Swift Cornell University

• Client could cheat and request execution of arbitrary server code – Server keeps enough state about expected control flow • Client could corrupt local variables – Server does not accept updates for high integrity variables • Client cannot – Violate data integrity – Influence execution of high integrity code – Learn confidential values K. Vikram Swift Cornell University
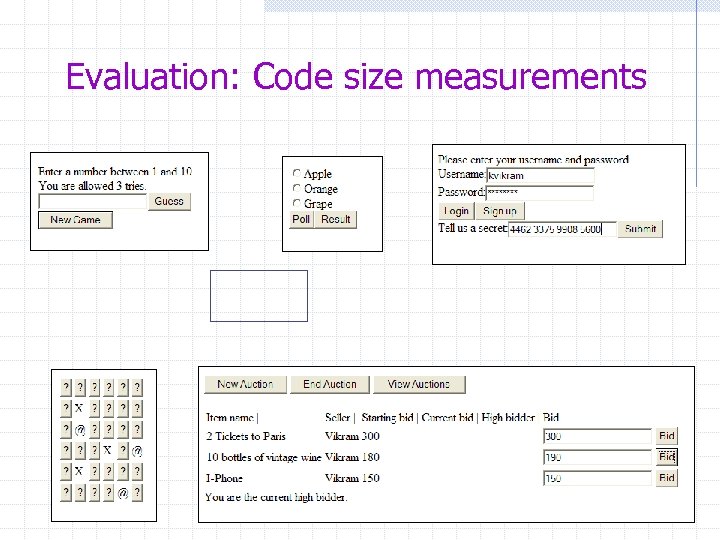
Evaluation: Code size measurements
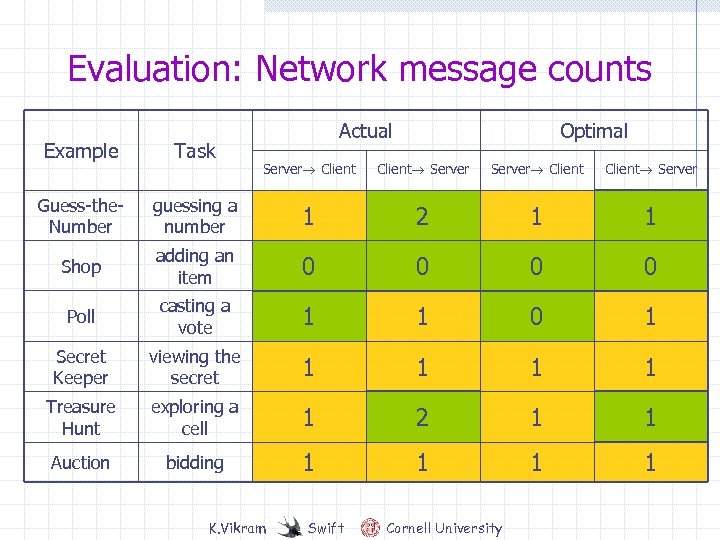
Evaluation: Network message counts Example Task Guess-the. Number Actual Optimal Server! Client! Server guessing a number 1 2 1 1 Shop adding an item 0 0 Poll casting a vote 1 1 0 1 Secret Keeper viewing the secret 1 1 Treasure Hunt exploring a cell 1 2 1 1 Auction bidding 1 1 K. Vikram Swift Cornell University
![Related Work Swift • Unified Programming Models – Links [CLWY 06] – Hop [SGL Related Work Swift • Unified Programming Models – Links [CLWY 06] – Hop [SGL](https://present5.com/presentation/0d94b1a6189465334e538f44ae34ab9d/image-31.jpg)
Related Work Swift • Unified Programming Models – Links [CLWY 06] – Hop [SGL 06] – Hilda [YGQDGS 07, YSRG 06] • Web Application Security – Static Analysis [HYHTLK 04, XA 06, JKK 06] – Dynamic Taint Tracking [HO 05, NGGE 05, XBS 06, CVM 07] • Security by construction – Jif/Split [ZZNM 02, ZCMZ 03] – Fairplay [MNPS 04] – SMCL [NS 07] K. Vikram Swift Cornell University

Conclusions/Questions? • Web applications are critical and handle sensitive data • Secure web applications are hard to write • The Swift programming system provides – Greater security assurance – A responsive interface – Cleaner programming model • http: //www. cs. cornell. edu/jif/swift/ K. Vikram Swift Cornell University
0d94b1a6189465334e538f44ae34ab9d.ppt