beafa17c6a62778129f55c19ba4b8599.ppt
- Количество слайдов: 40

Survey on Authentication Protocols for Mobile Devices By Muhammad Hasan, Lihua Duan, Tarik El Amsy Course : 60 -564 Instructor: Dr. A. K. Aggarwal Winter, 2006

Outline n Introduction n Background Information n Discussion of the Selected Papers n Testing Methodologies n Conclusion n References

Introduction n Challenges on security and quality of service (QOS) of Wireless Networks: n n Unprotected open mediums Burst volume of communications n IETF AAA Working Group n AAA (Authentication, Authorization, and Accounting ) n Several AAA protocols proposed : n n RADIUS DIAMETER
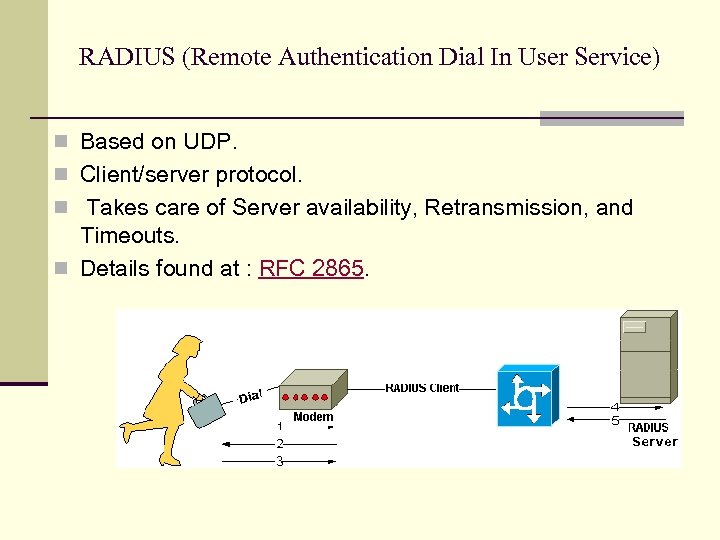
RADIUS (Remote Authentication Dial In User Service) n Based on UDP. n Client/server protocol. n Takes care of Server availability, Retransmission, and Timeouts. n Details found at : RFC 2865.
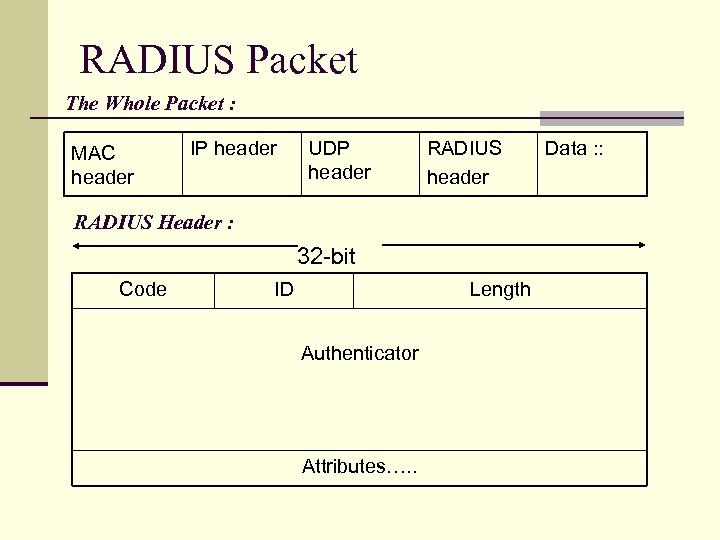
RADIUS Packet The Whole Packet : MAC header IP header UDP header RADIUS Header : 32 -bit Code ID Length Authenticator Attributes…. . Data : :
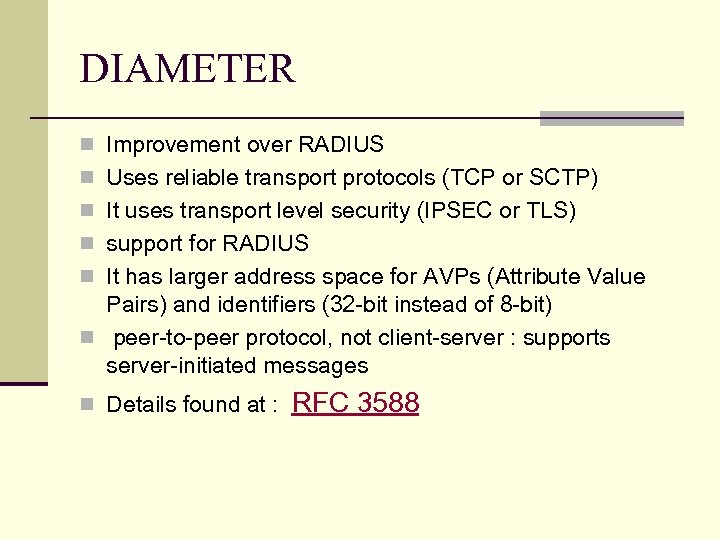
DIAMETER n Improvement over RADIUS n Uses reliable transport protocols (TCP or SCTP) n It uses transport level security (IPSEC or TLS) n support for RADIUS n It has larger address space for AVPs (Attribute Value Pairs) and identifiers (32 -bit instead of 8 -bit) n peer-to-peer protocol, not client-server : supports server-initiated messages n Details found at : RFC 3588
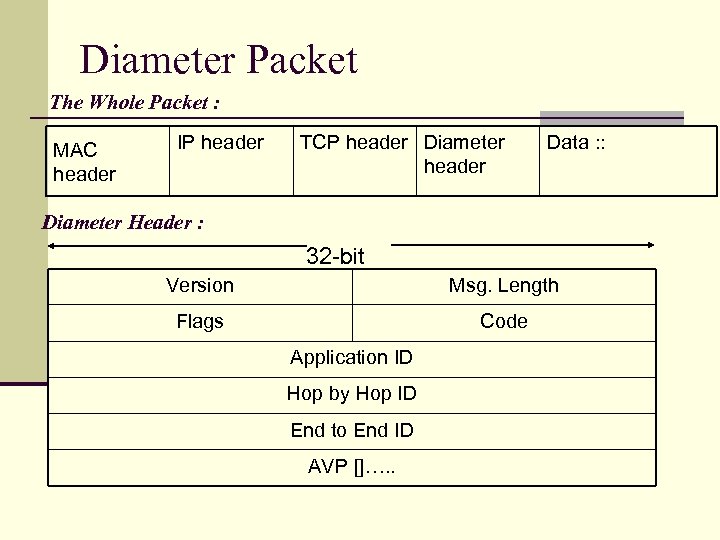
Diameter Packet The Whole Packet : MAC header IP header TCP header Diameter header Data : : Diameter Header : 32 -bit Version Msg. Length Flags Code Application ID Hop by Hop ID End to End ID AVP []…. .
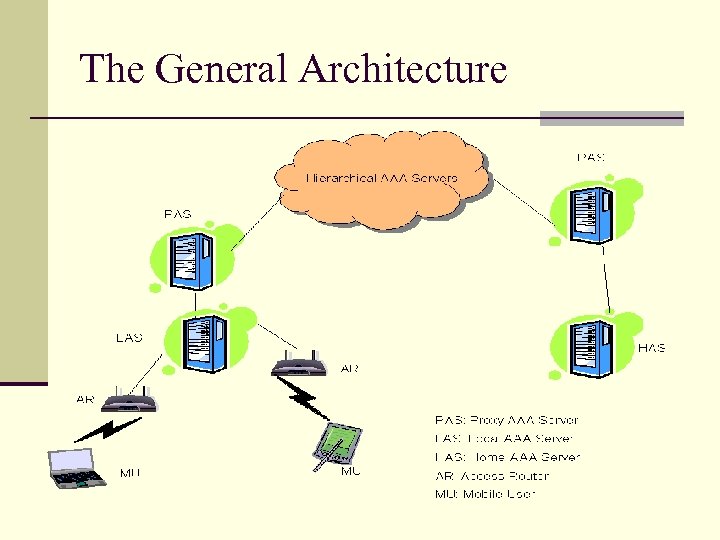
The General Architecture
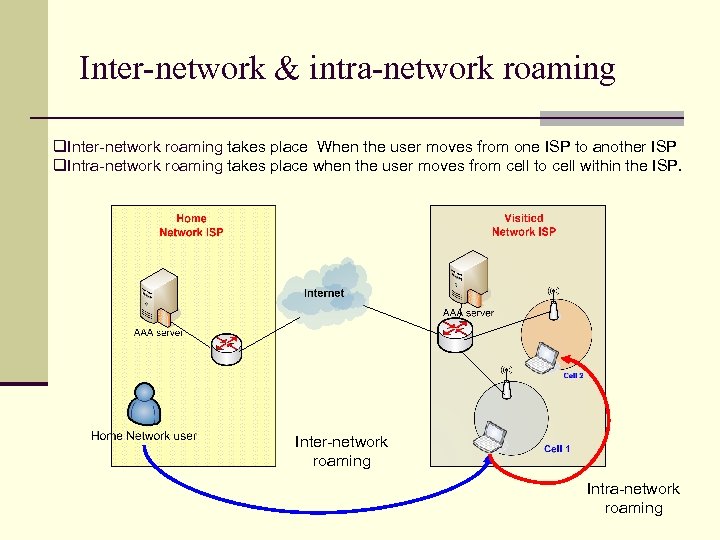
Inter-network & intra-network roaming q. Inter-network roaming takes place When the user moves from one ISP to another ISP q. Intra-network roaming takes place when the user moves from cell to cell within the ISP. Inter-network roaming Intra-network roaming
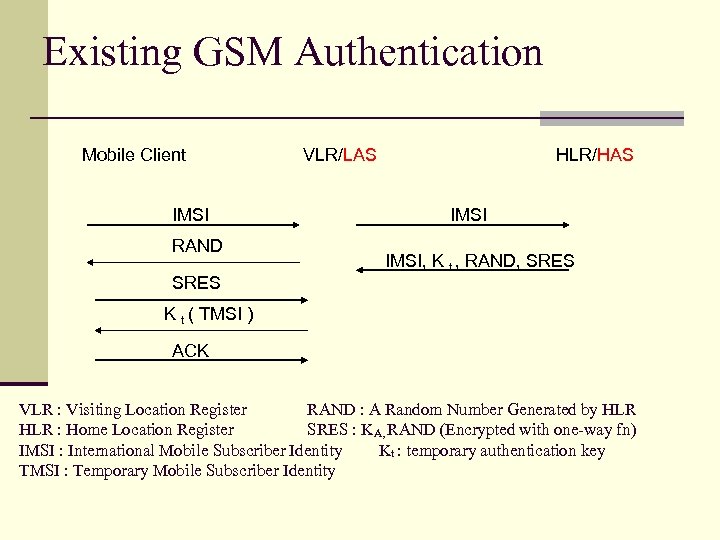
Existing GSM Authentication Mobile Client IMSI RAND SRES VLR/LAS HLR/HAS IMSI, K t , RAND, SRES K t ( TMSI ) ACK VLR : Visiting Location Register RAND : A Random Number Generated by HLR : Home Location Register SRES : KA, RAND (Encrypted with one-way fn) IMSI : International Mobile Subscriber Identity Kt : temporary authentication key TMSI : Temporary Mobile Subscriber Identity

Strong Password Protocols n The aim of strong password protocols is to authenticate the user while protecting the password against dictionary attacks by online eavesdroppers. n Two earlier strong password protocols : EKE and protocol of Gong. et al.

EKE (Encrypted Key Exchange) Protocol : n It provides secure authentication between user and a server using a weak secret. n Generates per session public- private key pairs. n Major Drawback : Doing private key operations on client side makes it infeasible to use with computationally restricted devices ( Mobile devices). n In 2002 Zhu et al. presents a variant of RSA-EKE for mobile devices.

The protocol of Gong et al. n Contains a trusted third party which is continuously available online as in Kerberos. n The parties in the system authenticate each other by the help of the trusted server.

Paper 1 GSM User Authentication Protocol By Özer Aydemir, Ali Aydın Selçuk TÜBTAK UEKAE LTAREN Research Center Ankara TURKEY Dept. of Computer Eng. Bilkent University Ankara TURKEY

Paper 1 : GSM User Authentication Protocol (GUAP) n Objectives : n User can authenticate with his/her password instead of the embedded key. n Breaks the dependency on the SIM card during authentication. n Users will be able to reach their accounts without their SIM cards, via any cellular phone, Internet, or a special network

GUAP ( Cont. ) n Resembles the approach of Gong et al. n Three entities involved in the authentication. n VLR plays the trusted server role n Random nonces for freshness guarantee of the sessions.
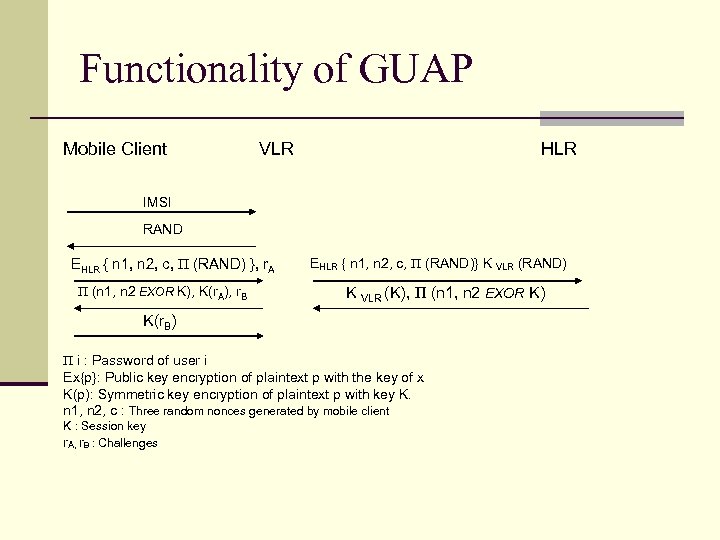
Functionality of GUAP Mobile Client VLR HLR IMSI RAND EHLR { n 1, n 2, c, Π (RAND) }, r. A Π (n 1, n 2 EXOR K), K(r. A), r. B EHLR { n 1, n 2, c, Π (RAND)} K VLR (RAND) K VLR (K), Π (n 1, n 2 EXOR K) K(r. B) Π i : Password of user i Ex{p}: Public key encryption of plaintext p with the key of x K(p): Symmetric key encryption of plaintext p with key K. n 1, n 2, c : Three random nonces generated by mobile client K : Session key r. A, r. B : Challenges

Security Issues : n The existence of the correct n 1 value in the fifth message indicates that it is the HLR that has decrypted the first message and sending this output. n The random nonce n 2 protects HLR’s response encrypted by π against dictionary attacks on π by an attacker who gets to know k or by VLR. n Random c protects first message against regeneration by VLR.

Paper 2 Improving mobile authentication with new AAA protocols n n n by H. Kim and H. Afifi Proc. IEEE Int. Conf. on Communications, May 2003 An authentication protocol by combining the AAA framework and the USIM authentication mechanism
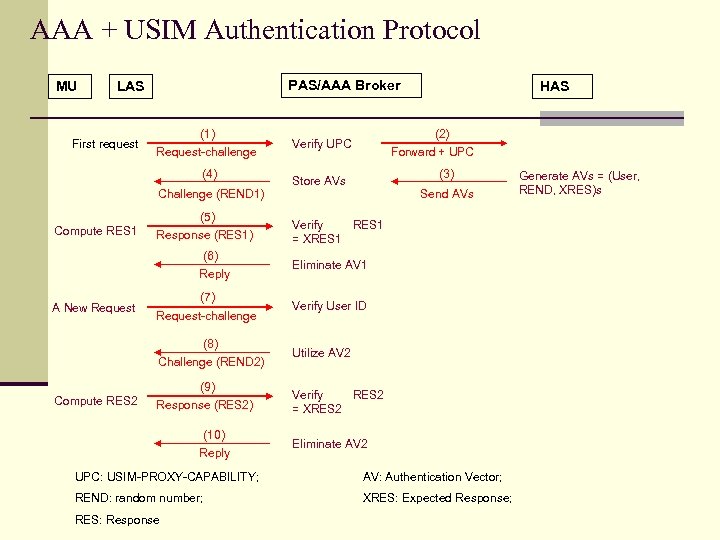
AAA + USIM Authentication Protocol MU PAS/AAA Broker LAS First request (1) Request-challenge (4) Challenge (REND 1) (5) Compute RES 1 Response (RES 1) (6) Reply A New Request (7) Request-challenge (8) Challenge (REND 2) (9) Compute RES 2 Response (RES 2) (10) Reply HAS (2) Verify UPC Forward + UPC (3) Store AVs Send AVs Verify RES 1 = XRES 1 Eliminate AV 1 Verify User ID Utilize AV 2 Verify RES 2 = XRES 2 Eliminate AV 2 UPC: USIM-PROXY-CAPABILITY; AV: Authentication Vector; REND: random number; XRES: Expected Response; RES: Response Generate AVs = (User, REND, XRES)s

Some Issues n USIM-PROXY-CAPABILITY (UPC) in the request message is forwarded to HAS through LASs n One of PASs can choose to become a broker by checking if UPC field exists in the request message n The number of AVs generated at HAS is an optimization problem

Paper 3 A lightweight authentication protocol with local security association control in mobile networks n n n by W. Liang and W. Wang Proc. IEEE Military Communications Conference, 2004 An authentication protocol by introducing local security association with optimal life time for mobile user
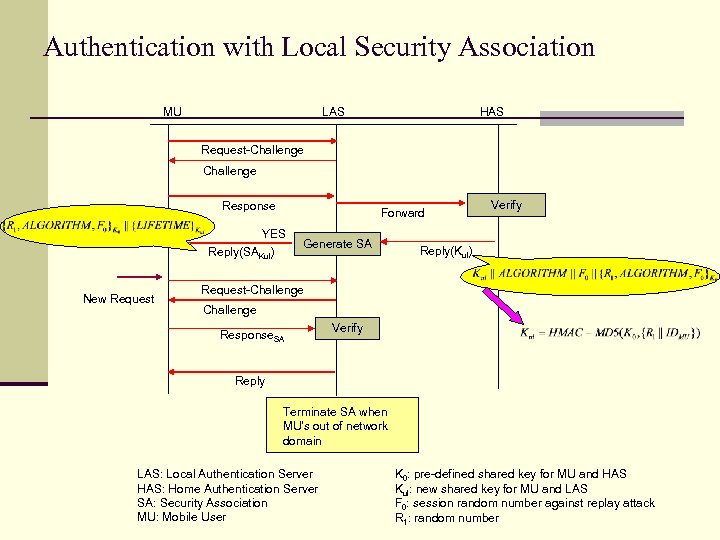
Authentication with Local Security Association MU LAS HAS Request-Challenge Response Forward YES Reply(SAKul) New Request Generate SA Verify Reply(Kul) Request-Challenge Response. SA Verify Reply Terminate SA when MU's out of network domain LAS: Local Authentication Server HAS: Home Authentication Server SA: Security Association MU: Mobile User K 0: pre-defined shared key for MU and HAS Kul: new shared key for MU and LAS F 0: session random number against replay attack R 1: random number
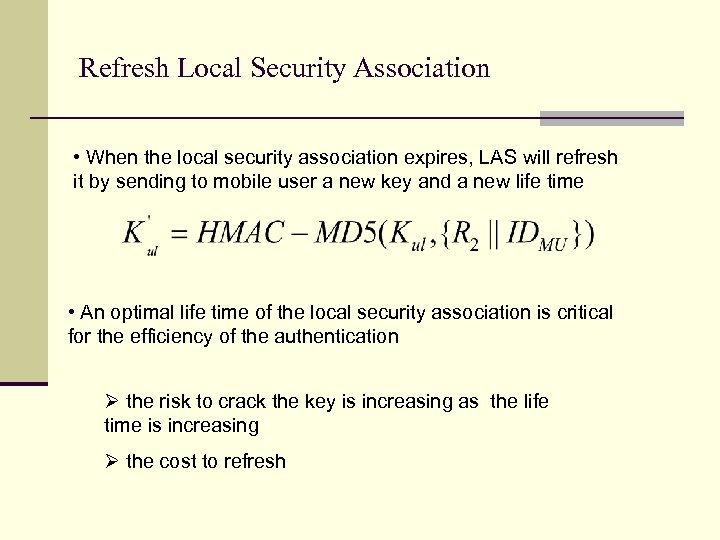
Refresh Local Security Association • When the local security association expires, LAS will refresh it by sending to mobile user a new key and a new life time • An optimal life time of the local security association is critical for the efficiency of the authentication Ø the risk to crack the key is increasing as the life time is increasing Ø the cost to refresh

Paper 4 Localized Authentication for Wireless LAN Inter-network Roaming By Men Long , Chwan-Hwa “John” Wu , J. David Irwin Department of Electrical and Computer Engineering Auburn University
Localizing the Authentication n A new approach in which an initial mutual authentication between a visited network and a roaming user can be performed locally without any intervention by the user’s home network. n Advantages are low time delay and robustness. n A practical certificate structure x. 509 n Authentication adapts the SSL v 3. 0 handshake protocol. n Local AAA server will approve or reject the authentication request. Home network AAA will not be part of the process
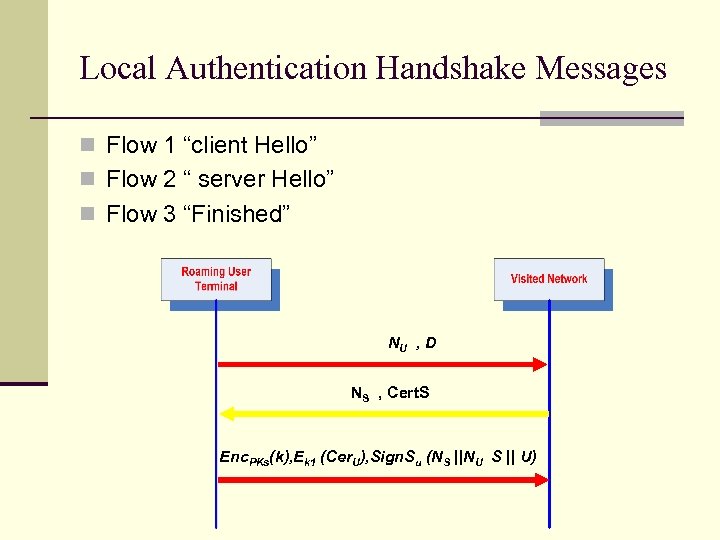
Local Authentication Handshake Messages n Flow 1 “client Hello” n Flow 2 “ server Hello” n Flow 3 “Finished” NU , D NS , Cert. S Enc. PKs(k), Ek 1 (Cer. U), Sign. Su (NS ||NU S || U)
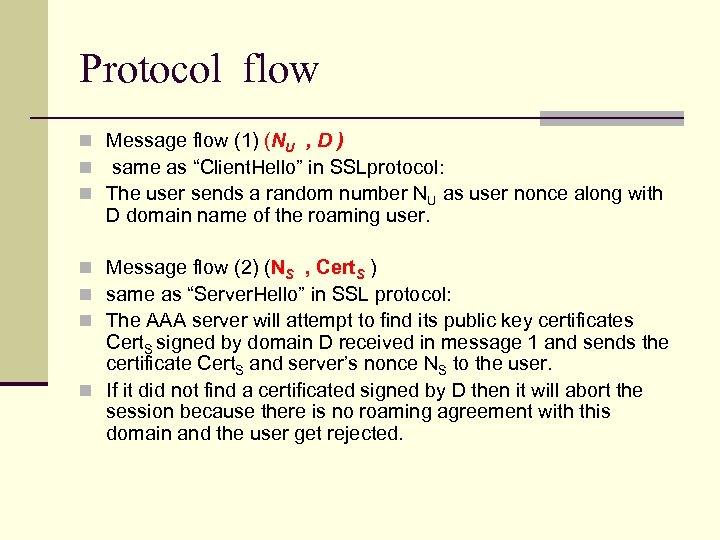
Protocol flow n Message flow (1) (NU , D ) n same as “Client. Hello” in SSLprotocol: n The user sends a random number NU as user nonce along with D domain name of the roaming user. n Message flow (2) (NS , Cert. S ) n same as “Server. Hello” in SSL protocol: n The AAA server will attempt to find its public key certificates Cert. S signed by domain D received in message 1 and sends the certificate Cert. S and server’s nonce NS to the user. n If it did not find a certificated signed by D then it will abort the session because there is no roaming agreement with this domain and the user get rejected.
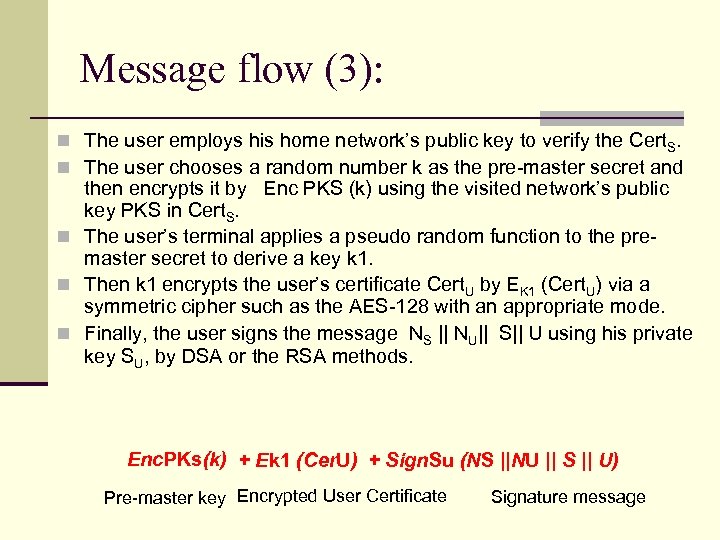
Message flow (3): n The user employs his home network’s public key to verify the Cert. S. n The user chooses a random number k as the pre-master secret and then encrypts it by Enc PKS (k) using the visited network’s public key PKS in Cert. S. n The user’s terminal applies a pseudo random function to the premaster secret to derive a key k 1. n Then k 1 encrypts the user’s certificate Cert. U by EK 1 (Cert. U) via a symmetric cipher such as the AES-128 with an appropriate mode. n Finally, the user signs the message NS || NU|| S|| U using his private key SU, by DSA or the RSA methods. Enc. PKs(k) + Ek 1 (Cer. U) + Sign. Su (NS ||NU || S || U) Pre-master key Encrypted User Certificate Signature message
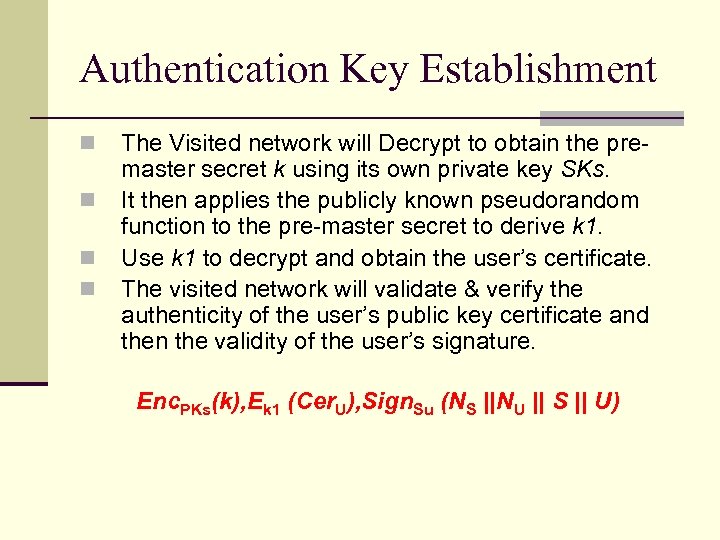
Authentication Key Establishment n n The Visited network will Decrypt to obtain the premaster secret k using its own private key SKs. It then applies the publicly known pseudorandom function to the pre-master secret to derive k 1. Use k 1 to decrypt and obtain the user’s certificate. The visited network will validate & verify the authenticity of the user’s public key certificate and then the validity of the user’s signature. Enc. PKs(k), Ek 1 (Cer. U), Sign. Su (NS ||NU || S || U)
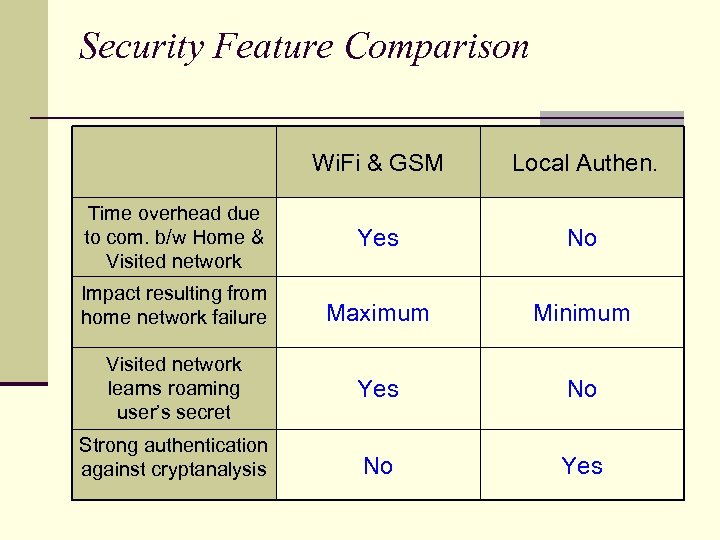
Security Feature Comparison Wi. Fi & GSM Local Authen. Time overhead due to com. b/w Home & Visited network Yes No Impact resulting from home network failure Maximum Minimum Visited network learns roaming user’s secret Yes No Strong authentication against cryptanalysis No Yes
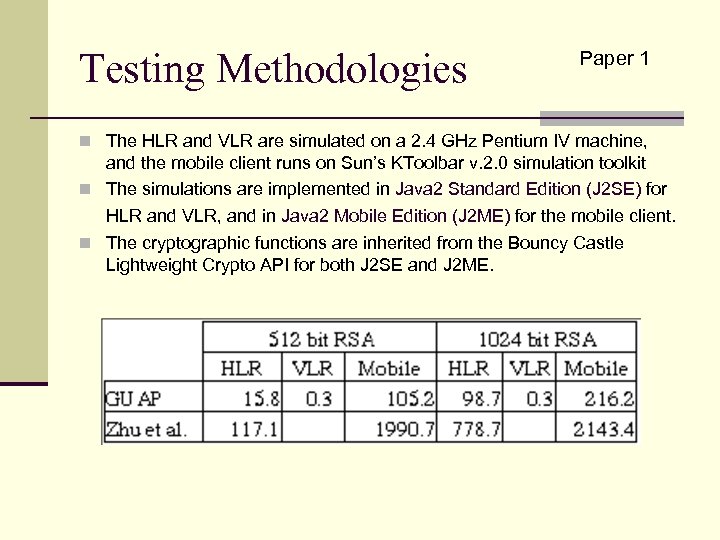
Testing Methodologies Paper 1 n The HLR and VLR are simulated on a 2. 4 GHz Pentium IV machine, and the mobile client runs on Sun’s KToolbar v. 2. 0 simulation toolkit n The simulations are implemented in Java 2 Standard Edition (J 2 SE) for HLR and VLR, and in Java 2 Mobile Edition (J 2 ME) for the mobile client. n The cryptographic functions are inherited from the Bouncy Castle Lightweight Crypto API for both J 2 SE and J 2 ME.
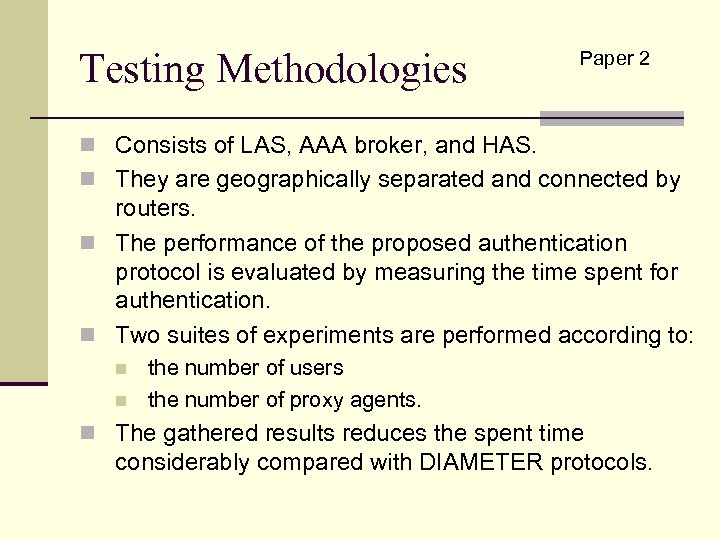
Testing Methodologies Paper 2 n Consists of LAS, AAA broker, and HAS. n They are geographically separated and connected by routers. n The performance of the proposed authentication protocol is evaluated by measuring the time spent for authentication. n Two suites of experiments are performed according to: n n the number of users the number of proxy agents. n The gathered results reduces the spent time considerably compared with DIAMETER protocols.

Testing Methodologies n n n n Paper 4 , Localized Authentication Testing Methodology 2 phases Phase I, with a Pentium 4 (2. 2 GHz) and 512 MB RSA encryption or signature verification time is 0. 28 milliseconds while the RSA decryption or signature-signing time is 5. 53 milliseconds. Phase II ( SSL/TLS protocol ). laptop Pentium 4 (1. 8 GHz) & 256 MB memory and IMAP server The results indicate that the time delay per SSL channel setup averages 24 milliseconds. According to the data from the phases 1 and 2, the expected time delay for the proposed protocol is about 30=24+6 milliseconds.
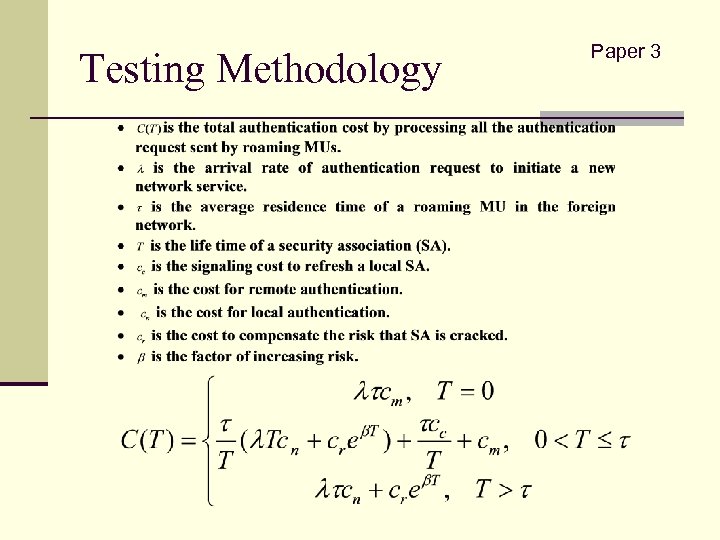
Testing Methodology Paper 3
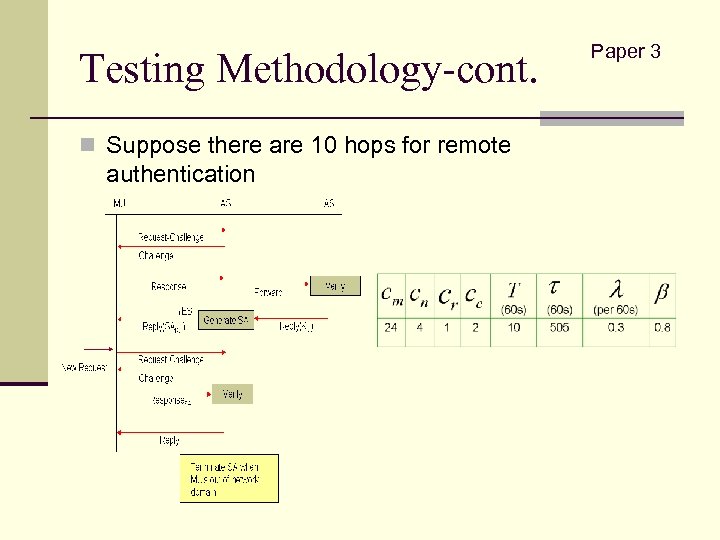
Testing Methodology-cont. n Suppose there are 10 hops for remote authentication Paper 3

Conclusion n DIAMETER, RADIUS, EKE and Gong et al. ’s are some of the earliest standardized AAA authentication protocols. n To improve efficiency or adaptability, many new authentication protocols are proposed in the literature. We discuss four most recent ones. Ø Ø For those protocols aiming at improve efficiency, they usually share one common feature: reduce the number of remote authentications by transforming them into local authentications. For those protocols aiming at improve adaptability, they often try to relax some hardware limitation for authentication, such as the use of SIM card.

References n n n n n . B. Aboba and D. Simon, “PPP EAP TLS authentication protocol”, RFC 2716, October 1999. O. Aydemir and A. Selguk, “A strong user authentication protocol for GSM”, 14 th IEEE International Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprise, 2005, pp. 150 -153. S. M. Bellovin and M. Meritt, “Encrypted Key Exchange: Password based protocols secure against dictionary attacks”, in Proceedings of the IEEE Symposium on Security and Privacy, May, 1992, pp. 72 -84. L. Biunk and J. Vollbmcht, “PPP extensible authentication protocol”, RFC 2284, March 1998. L. De. Il’Uomo and E. Scanone, “The mobility management and authentication, authorization mechanisms in mobile networks beyond 3 G”, 12 th IEEE International Symposium on Personal, Indoor und Mobile Radio Communications, 2001, vol. 1, pp. c 44 -c 4 8. A. Freier, P. Karlton, and P. Kocher, “The SSL protocol version 3. 0”, available at: http: //wp. netscape. com/eng/ssl 3/draft 302. txt, Nov. 1996. S. Glass, T. Hiller, S. Jacobs, and C. Perkins, “Mobile IP authentication, authorization and Accounting Requirements”, RFC 2977, October 2000. L. Gong, T. M. A. Lomas, R. M. Needham, and J. H. Saltzer, “Protecting poorly chosen secrets from guessing attacks”, IEEE Journal on Selected Areas in Communication, Vol. 11, No. 5, June 1993, pp. 48 -656. H. Kim and H. Afifi, “Improving mobile authentication with new AAA protocols, ” Proc. IEEE Int. Conf. on Communications, Vol. 1, May 2003, pp. 497 -501. W. Liang and W. Wang, “A lightweight authentication protocol with local security association control in mobile networks”, IEEE Military Communications Conference (MILCOM 2004), Vol. 1, 2004, pp. 225 -231. n n n n H. -Y. Lin, L. Harn, and V. Kumar, “Authentication protocols in wireless communications”, CAUTO’ 95, 1995. M. Long, C. J. Wu, and J. D. Irwin, “Localized authentication for wireless LAN inter-networking roaming”, IEEE Wireless Communications and Networking Conference (WCNC), Vol. 1, 2004, pp. 264 -267 C. Perkins and P. Calhoun, “Mobile IPv 4 challenge/response extensions”, RFC 3012, November 2000. RFC 3588. Diameter Base Protocol. Available at: http: //www. ietf. org/rfc 3588. txt. C. Rigney et al. “RADIUS extensions”, RFC 2869, available at: http: //bgp. potaroo. net/ietf/html/ids-wg-radext. html. June 2000. R. Rivest, “The MD 5 message digest algorithm”, RFC 1321, April, 1992. S. Shieh, E. Ho, and Y. Huang, “An efficient authentication protocol for Mobile Networks”, Authentication Protocol hrn 01 of Information Science and Engineering, vol. 15, 1999, pp. 505 -520. W. Simpson, “PPP challenge handshake authentication protocol (CHAP), ” RFCI 334, August 1996. W. Stallings, “Network security essentials”, Applications and Standards, 2000. M. Xu and S. Upadhyaya, “Secure communication in KS”, in Vehculur Technology Conference, pp. 2193 -2197, 2001. http: //www. cisco. com/warp/public/707/32. html. http: //en. wikipedia. org/wiki/DIAMETER. KToolbar, A toolkit for J 2 ME, http: //java. sun. com/j 2 me. Lightweight Crypto API, Bouncy Castle, http: //www. bouncycastle. org

Special Thanks to: Dr. A. K. Aggarwal
Questions ?
beafa17c6a62778129f55c19ba4b8599.ppt