01aba29301d05d0521bd03d2cabe439a.ppt
- Количество слайдов: 13

Supply Chain Security: “The Virtual Border” UNECE Trade Facilitation Conference Honorable D. Robert Quartel CEO and Chairman Freight. Desk Technologies www. freightdesk. com Proprietary and Confidential
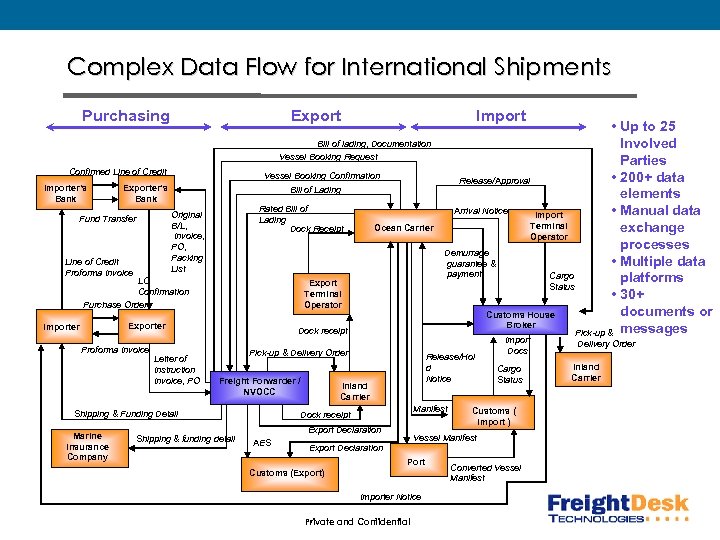
Complex Data Flow for International Shipments Purchasing Export Import Bill of lading, Documentation Vessel Booking Request Confirmed Line of Credit Importer’s Bank Vessel Booking Confirmation Exporter’s Bank Bill of Lading Rated Bill of Lading Dock Receipt Original B/L, Invoice, PO, Packing List Fund Transfer Line of Credit Proforma Invoice LC Confirmation Purchase Order Export Terminal Operator Exporter Importer Proforma Invoice Letter of Instruction Invoice, PO Dock receipt Pick-up & Delivery Order Freight Forwarder / NVOCC Shipping & Funding Detail Marine Insurance Company Ocean Carrier Shipping & funding detail Release/Hol d Notice Inland Carrier Manifest Dock receipt Export Declaration AES • Up to 25 Involved Parties • 200+ data Release/Approval elements Arrival Notice • Manual data Import Terminal exchange Operator processes Demurrage • Multiple data guarantee & payment Cargo platforms Status • 30+ documents or Customs House Broker Pick-up & messages Import Docs Cargo Status Customs ( Import ) Vessel Manifest Export Declaration Port Customs (Export) Importer Notice Private and Confidential Converted Vessel Manifest Delivery Order Inland Carrier
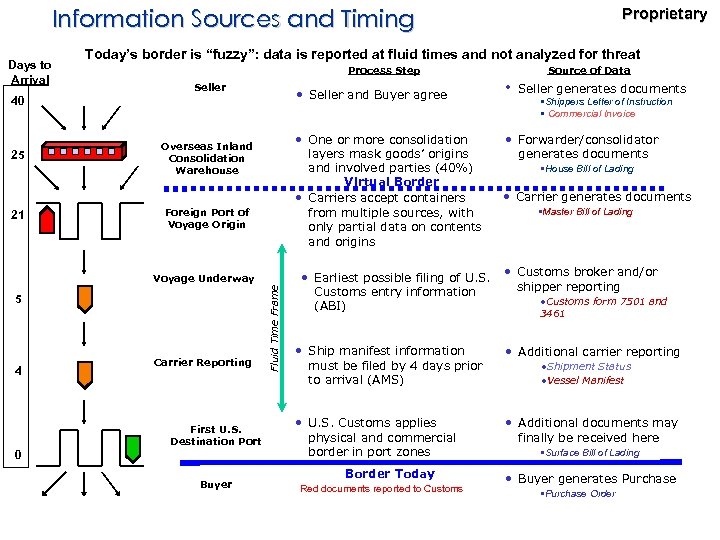
Information Sources and Timing Days to Arrival Today’s border is “fuzzy”: data is reported at fluid times and not analyzed for threat Process Step Seller • Seller and Buyer agree 40 25 21 • One or more consolidation layers mask goods’ origins and involved parties (40%) Virtual Border • Carriers accept containers from multiple sources, with only partial data on contents and origins Overseas Inland Consolidation Warehouse Foreign Port of Voyage Origin 5 Carrier Reporting First U. S. Destination Port 0 Buyer Fluid Time Frame Voyage Underway 4 Proprietary • Earliest possible filing of U. S. Customs entry information (ABI) Source of Data • Seller generates documents • Shippers Letter of Instruction • Commercial Invoice • Forwarder/consolidator generates documents • House Bill of Lading • Carrier generates documents • Master Bill of Lading • Customs broker and/or shipper reporting • Customs form 7501 and 3461 • Ship manifest information must be filed by 4 days prior to arrival (AMS) • Additional carrier reporting • U. S. Customs applies physical and commercial border in port zones • Additional documents may finally be received here Border Today Red documents reported to Customs • Shipment Status • Vessel Manifest • Surface Bill of Lading • Buyer generates Purchase • Purchase Order
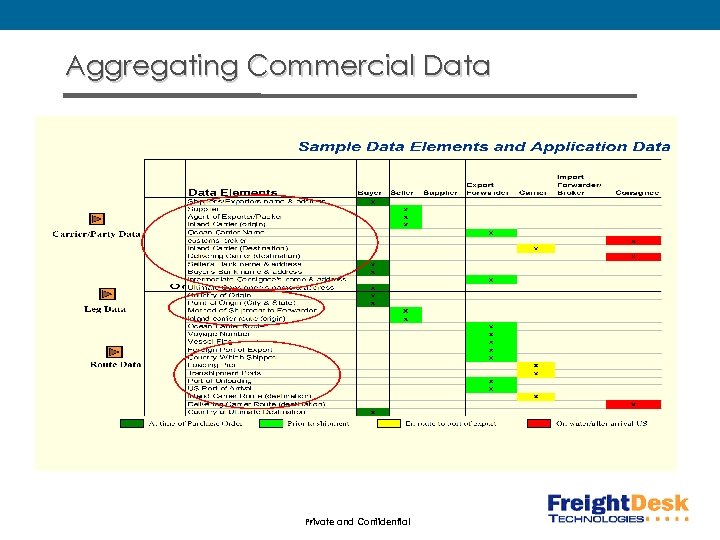
Aggregating Commercial Data Private and Confidential
Dual Purpose Information • BUSINESS: In-transit VISIBILITY for the purposes of contract management, planning, process tracking, risk mitigation, documentation, etc. • GOVERNMENT: Process and regulatory TRANSPARENCY for the purposes of anti-corruption, counter-terrorism, trade processing, health and safety, etc Private and Confidential
Commercial Data Is Critical to Security: - Cargo – What is being transported? Carriers – Who is handling the cargo? Conveyance – What is the route, how is it moving? Commerce – Who are the parties to the transaction? Private and Confidential
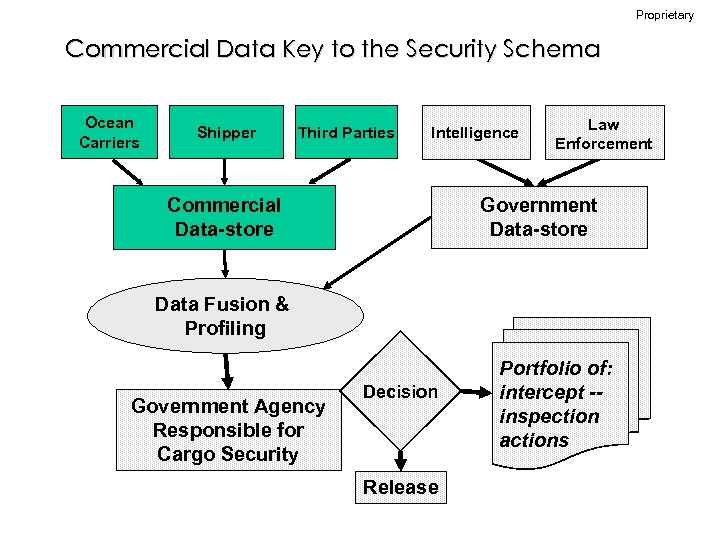
Proprietary Commercial Data Key to the Security Schema Ocean Carriers Shipper Third Parties Intelligence Commercial Data-store Law Enforcement Government Data-store Data Fusion & Profiling Government Agency Responsible for Cargo Security Decision Release Portfolio of: intercept -inspection actions
Data Mining for Threat and Risk Assessment • Employs a synergistic array of data mining techniques • Knowledge based, both specific and general • Based on rules and known facts • Statistical patterns and profiling • Mathematical models for risk assessment and threat identification • Evolutionary algorithms to detect changes in patterns and discover new patterns Private and Confidential
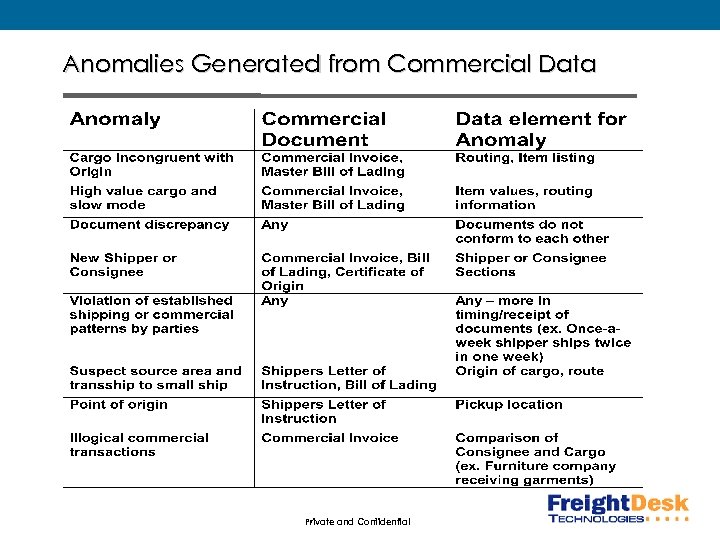
Anomalies Generated from Commercial Data Private and Confidential

A Global Issue • EC & US Customs, 22 October 2002 • “…. major principles for future co-operation were stressed, most particularly reciprocity…. common standards for selection…. ” • “…. agreed… to explore…. a declaration of principle to co-operate on a mutually acceptable container security system covering the whole EU…. ” • WCO and IMO are making it a mandate: IMO Secretary-General, William O’Neil, has strongly urged all parties concerned “to start putting in place all the necessary legislative, administrative and operational provisions needed…”. Private and Confidential
Principles of a Successful Data Effort • This IS a transportation and logistics issue, not just a maritime issue. • This IS NOT a compliance issue. A legal cargo can become a lethal cargo. • Security should be dynamic: The port and customs processing is a node within the process, not even the most important focus for security. • Profiling should and can begin in the Importing Country at the issuance of the purchase order from the buyer. • The shipper/importer should be responsible for the process, not the carriers. Private and Confidential

Issues for Small Importers and Exporters • Longer lead times for moving cargoes • Delays in trans-shipped containers • Negative impact vs. cargo originating in direct service countries • Many exports to smaller US companies that are not C-TPAT certified, and not in CSI ports • Technology infrastructure to comply with big country data requirements Another hurdle to competitiveness Private and Confidential
Benefits • • • Source-once, APPROPRIATELY to the process Flexible, intermodal, sourcing Profiling on demand (Dynamic, not Static) Business-process centric Goes beyond human expertise Private and Confidential
01aba29301d05d0521bd03d2cabe439a.ppt