64582a0532fabb8334071319d2f8421d.ppt
- Количество слайдов: 24
 Stuxnet, Duqu és társai – kifinomult internetes kártevők kifejlesztése, átalakítása, továbbfejlesztése Stuxnet, Duqu and others – development and operation of sophisticated pieces of malware used in the Middle East Boldizsár Bencsáth Ph. D Budapest University of Technology and Economics Department of Telecommunications Laboratory of Cryptography and System Security (Cry. S Lab) www. crysys. hu joint work with Levente Buttyán, Gábor Pék, and Márk Félegyházi
Stuxnet, Duqu és társai – kifinomult internetes kártevők kifejlesztése, átalakítása, továbbfejlesztése Stuxnet, Duqu and others – development and operation of sophisticated pieces of malware used in the Middle East Boldizsár Bencsáth Ph. D Budapest University of Technology and Economics Department of Telecommunications Laboratory of Cryptography and System Security (Cry. S Lab) www. crysys. hu joint work with Levente Buttyán, Gábor Pék, and Márk Félegyházi
 Stuxnet (June 2010) § § “the Most Menacing Malware in History” (Kim Zetter, Wired) targeted the Natanz nuclear facility in Iran modified PLCs (Programmable Logic Controllers) destroyed hundreds of uranium centrifuges Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 2
Stuxnet (June 2010) § § “the Most Menacing Malware in History” (Kim Zetter, Wired) targeted the Natanz nuclear facility in Iran modified PLCs (Programmable Logic Controllers) destroyed hundreds of uranium centrifuges Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 2
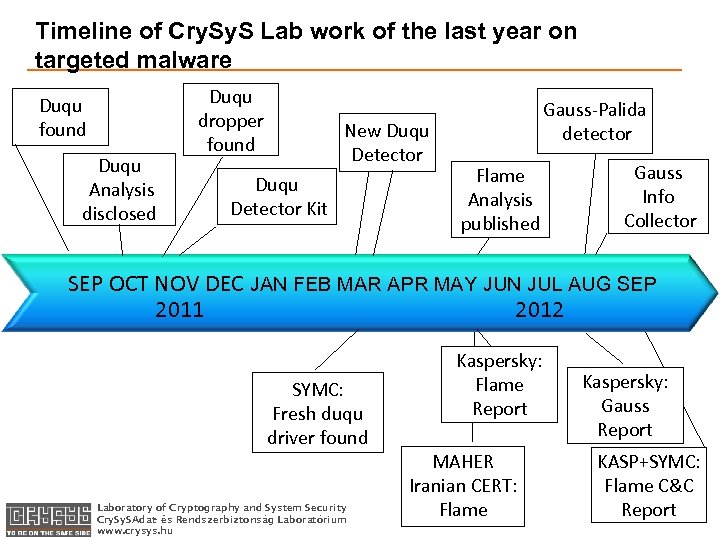 Timeline of Cry. S Lab work of the last year on targeted malware Duqu found Duqu Analysis disclosed Duqu dropper found New Duqu Detector Kit Gauss-Palida detector Flame Analysis published Gauss Info Collector SEP OCT NOV DEC JAN FEB MAR APR MAY JUN JUL AUG SEP 2011 2012 SYMC: Fresh duqu driver found Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu Kaspersky: Flame Report MAHER Iranian CERT: Flame Kaspersky: Gauss Report KASP+SYMC: Flame C&C Report
Timeline of Cry. S Lab work of the last year on targeted malware Duqu found Duqu Analysis disclosed Duqu dropper found New Duqu Detector Kit Gauss-Palida detector Flame Analysis published Gauss Info Collector SEP OCT NOV DEC JAN FEB MAR APR MAY JUN JUL AUG SEP 2011 2012 SYMC: Fresh duqu driver found Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu Kaspersky: Flame Report MAHER Iranian CERT: Flame Kaspersky: Gauss Report KASP+SYMC: Flame C&C Report
 Our contributions § discovery, naming, and first analysis of Duqu – – – § identification of the dropper – – – § info-stealer component creates files with names starting with ~DQ our analysis focused on showing the similarities to Stuxnet we shared our report with major anti-virus vendors and Microsoft MS Word document with a 0 -day Windows kernel exploit we shared the anonymized dropper with Microsoft first patch in December 2011, further patches in May 2012 development of the Duqu Detector Toolkit – – – focus on heuristic anomaly detection detects live Duqu instances and remains of earlier infections also detects Stuxnet !! open-source distribution (to be used in critical infrastructures) 12000+ downloads from 150 countries Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 4
Our contributions § discovery, naming, and first analysis of Duqu – – – § identification of the dropper – – – § info-stealer component creates files with names starting with ~DQ our analysis focused on showing the similarities to Stuxnet we shared our report with major anti-virus vendors and Microsoft MS Word document with a 0 -day Windows kernel exploit we shared the anonymized dropper with Microsoft first patch in December 2011, further patches in May 2012 development of the Duqu Detector Toolkit – – – focus on heuristic anomaly detection detects live Duqu instances and remains of earlier infections also detects Stuxnet !! open-source distribution (to be used in critical infrastructures) 12000+ downloads from 150 countries Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 4
 s. Ky. WIper/Flame § In May/2012 we participated in an international collaboration to investigate a novel malware, we called it s. Ky. WIper § 27/05 – National CERT of IRAN (Maher) disclosed they are investigating a malware “Flamer” § 28/05 – Cry. S released initial tech report on Flame/s. Ky. WIper; Kasperksy released details about their work on “Flame”. – 65000+ distinct IP downloads from 188 countries § We give no details what was exactly the collaboration, with whom we were working on and how -> potential personal risks to be avoided. Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
s. Ky. WIper/Flame § In May/2012 we participated in an international collaboration to investigate a novel malware, we called it s. Ky. WIper § 27/05 – National CERT of IRAN (Maher) disclosed they are investigating a malware “Flamer” § 28/05 – Cry. S released initial tech report on Flame/s. Ky. WIper; Kasperksy released details about their work on “Flame”. – 65000+ distinct IP downloads from 188 countries § We give no details what was exactly the collaboration, with whom we were working on and how -> potential personal risks to be avoided. Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Gauss (July 2012) § Gauss is an information stealer malware based on the Flame platform – Found by Kaspersky Lab – injects its modules into different browsers in order to intercept user sessions and steal passwords, cookies and browser history – collects information about the computer’s network connections – collects information about processes and folders – collects information about BIOS, CMOS RAM – collects information about local, network and removable drives – infects USB drives with a spy module in order to steal information from other computers – interacts with a command control server, sends the information collected, downloads additional modules § infections date back to September-October 2011 § thousands of victims, mainly in Lebanon, Israel, and the Palestinian Territory Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 6
Gauss (July 2012) § Gauss is an information stealer malware based on the Flame platform – Found by Kaspersky Lab – injects its modules into different browsers in order to intercept user sessions and steal passwords, cookies and browser history – collects information about the computer’s network connections – collects information about processes and folders – collects information about BIOS, CMOS RAM – collects information about local, network and removable drives – infects USB drives with a spy module in order to steal information from other computers – interacts with a command control server, sends the information collected, downloads additional modules § infections date back to September-October 2011 § thousands of victims, mainly in Lebanon, Israel, and the Palestinian Territory Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 6
 Our contribution to Gauss story § Gauss was discovered analyzed by Kaspersky Lab § in a very short time after the publication of the Kaspersky report, we provided an on-line Gauss Detector Service at gauss. crysys. hu – Gauss installs a font called Palida Narrow on victim computers – purpose is unknown (Paladin Arrow? ) – our service checks the presence of the Palida Narrow font on client computers § serving 85000+ requests, found ~100 positives and notified them mainly in Lebanon and the US Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 7
Our contribution to Gauss story § Gauss was discovered analyzed by Kaspersky Lab § in a very short time after the publication of the Kaspersky report, we provided an on-line Gauss Detector Service at gauss. crysys. hu – Gauss installs a font called Palida Narrow on victim computers – purpose is unknown (Paladin Arrow? ) – our service checks the presence of the Palida Narrow font on client computers § serving 85000+ requests, found ~100 positives and notified them mainly in Lebanon and the US Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 7
 The Gödel module of Gauss § Gauss’ encrypted warhead § unlike in case of Stuxnet, Duqu, and Flame – the encryption is not simple XOR masking or byte substitution – the decryption key is not available in the malware itself § instead, Gauss uses RC 4 and constructs the key dynamically from strings found on the victim system – this payload is executed only on the designated target system(s) that has the right configuration resulting in the correct decryption key – analysis of intent and functioning is made impossible for the research community § the module is big enough to contain a Stuxnet-like SCADA targeted attack code and all the precautions used by the authors indicate that the target is indeed high profile § We created a free tool „Gauss Info Collector” to collect PATH and Program Files directory information from volunteers Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 8
The Gödel module of Gauss § Gauss’ encrypted warhead § unlike in case of Stuxnet, Duqu, and Flame – the encryption is not simple XOR masking or byte substitution – the decryption key is not available in the malware itself § instead, Gauss uses RC 4 and constructs the key dynamically from strings found on the victim system – this payload is executed only on the designated target system(s) that has the right configuration resulting in the correct decryption key – analysis of intent and functioning is made impossible for the research community § the module is big enough to contain a Stuxnet-like SCADA targeted attack code and all the precautions used by the authors indicate that the target is indeed high profile § We created a free tool „Gauss Info Collector” to collect PATH and Program Files directory information from volunteers Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 8
 Most interesting novelties of recent targeted malware § Stuxnet PLC module Injecting code into PLC and destroying uranium centrifuges is really fascinating § Stolen keys for signing drivers for Stuxnet (2 times) and Duqu (1 time) It is not usual to steal code signing keys for creating efficient malware § Duqu Windows kernel TTF exploit (CVE-2011 -3402) Gaining kernel level access with exploits is rare, especially in such a complicated manner § Flame MD 5 collision and Windows Update based propagation Possibly cryptographic breakthrough was needed and/or exceptional computational resources to create fake certificate by collision attack § Gauss Gödel module: encrypted payload which can be decrypted only on target Researchers also proposed the idea which is now in the wild: payload is only decryptable if proper PATH and „Program Files” contents are available: just on the target Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Most interesting novelties of recent targeted malware § Stuxnet PLC module Injecting code into PLC and destroying uranium centrifuges is really fascinating § Stolen keys for signing drivers for Stuxnet (2 times) and Duqu (1 time) It is not usual to steal code signing keys for creating efficient malware § Duqu Windows kernel TTF exploit (CVE-2011 -3402) Gaining kernel level access with exploits is rare, especially in such a complicated manner § Flame MD 5 collision and Windows Update based propagation Possibly cryptographic breakthrough was needed and/or exceptional computational resources to create fake certificate by collision attack § Gauss Gödel module: encrypted payload which can be decrypted only on target Researchers also proposed the idea which is now in the wild: payload is only decryptable if proper PATH and „Program Files” contents are available: just on the target Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Malware (families) of recent attacks § Stuxnet, Duqu modules + Wiper? – – – § At least the platform is created by same group. Complex, clean code, well tested. Only minimal part is delivered on victim file system. Uses different C&C for each target -> very hard to discover Duqu: Self-cleaning (suicide) after limited time -> to remain undetected Gauss and Flame +Wiper? – The code is much sloppier, bunch of code put together (possibly lack of cleanup garbage, unused code too) – Debug and similar information left widely in code helping analysis – High level code like LUA scripts, SQLite database, etc. – Most modules delivered to targets, and there are lots of targets – Huge C&C server infrastructure (35+ servers) – Flame C&C support three other malware: SP, SPE, IP § Shamoon – – § Likely not related to the above two Amateurish errors Major goal: wiping, but possibly also to obtain information From operation point of view, very hard to judge who is behind (targets: oil industry in Saudi Arabia, Qatar) Mahdi – Most likely not related to all above – Attacked middle east – Even more amateurish Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Malware (families) of recent attacks § Stuxnet, Duqu modules + Wiper? – – – § At least the platform is created by same group. Complex, clean code, well tested. Only minimal part is delivered on victim file system. Uses different C&C for each target -> very hard to discover Duqu: Self-cleaning (suicide) after limited time -> to remain undetected Gauss and Flame +Wiper? – The code is much sloppier, bunch of code put together (possibly lack of cleanup garbage, unused code too) – Debug and similar information left widely in code helping analysis – High level code like LUA scripts, SQLite database, etc. – Most modules delivered to targets, and there are lots of targets – Huge C&C server infrastructure (35+ servers) – Flame C&C support three other malware: SP, SPE, IP § Shamoon – – § Likely not related to the above two Amateurish errors Major goal: wiping, but possibly also to obtain information From operation point of view, very hard to judge who is behind (targets: oil industry in Saudi Arabia, Qatar) Mahdi – Most likely not related to all above – Attacked middle east – Even more amateurish Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Goals of Stuxnet/Duqu/Flame/Gauss § Stuxnet: Propagate and corrupt centrifuges through PLC code § Duqu: Info stealer for super-high profile targets – likely indirectly related to Iran nuclear plants § Flame: Info stealer, recently used against ~10 000 targets; extensive info stealing for the area of Iran and Sudan (25%!!) – C&C research shows more than 10 k targets; § Gauss: Info stealer, but for banking sector – mainly lebanese targets § Iranian “Wiper”: Nobody is sure § “HOT” Stuxnet-Duqu-Flame-Gauss area: Iran, Sudan, Lebanon, Israel/Palestinian territories, Turkey Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Goals of Stuxnet/Duqu/Flame/Gauss § Stuxnet: Propagate and corrupt centrifuges through PLC code § Duqu: Info stealer for super-high profile targets – likely indirectly related to Iran nuclear plants § Flame: Info stealer, recently used against ~10 000 targets; extensive info stealing for the area of Iran and Sudan (25%!!) – C&C research shows more than 10 k targets; § Gauss: Info stealer, but for banking sector – mainly lebanese targets § Iranian “Wiper”: Nobody is sure § “HOT” Stuxnet-Duqu-Flame-Gauss area: Iran, Sudan, Lebanon, Israel/Palestinian territories, Turkey Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Malware development § Possibly different, remote groups are creating individual malware platforms; malware modules; exploits; other tools § Distributed development has the advantage that groups use different coding technique, revealing the existence of one malware does not harm others’ success § The quality of the results might differ, but the operation can still be successful § Additional modules can be designed on an as-needed basis Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Malware development § Possibly different, remote groups are creating individual malware platforms; malware modules; exploits; other tools § Distributed development has the advantage that groups use different coding technique, revealing the existence of one malware does not harm others’ success § The quality of the results might differ, but the operation can still be successful § Additional modules can be designed on an as-needed basis Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Modus operandi Attacking teams have roles § C&C infrastructure maintenance, C&C domains § Infecting new victims (watering hole or spear phising type of attacks) § Obtaining infrastructure information, analysis and refinement of attack technique § Active attacks on victims for specific targets § Handling (encrypted) collected information § Analyzing collected information § For many steps possibly there are junior grade personnel and higher grade professionals Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Modus operandi Attacking teams have roles § C&C infrastructure maintenance, C&C domains § Infecting new victims (watering hole or spear phising type of attacks) § Obtaining infrastructure information, analysis and refinement of attack technique § Active attacks on victims for specific targets § Handling (encrypted) collected information § Analyzing collected information § For many steps possibly there are junior grade personnel and higher grade professionals Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
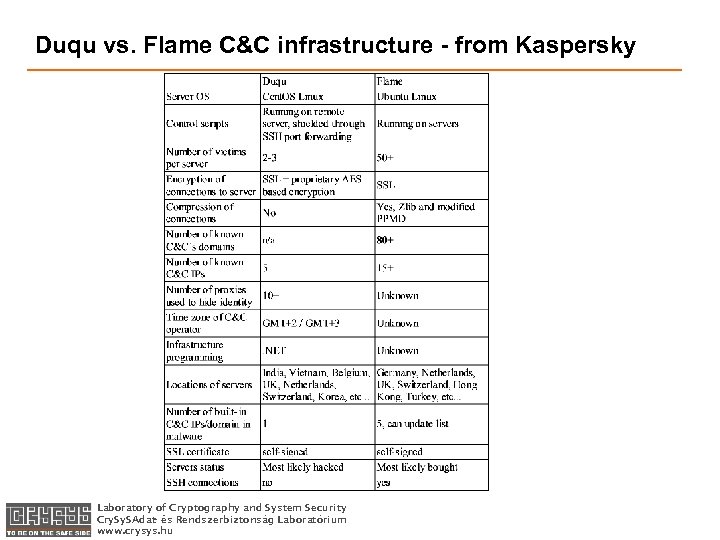 Duqu vs. Flame C&C infrastructure - from Kaspersky Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Duqu vs. Flame C&C infrastructure - from Kaspersky Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Complexity vs. analysis § Flame is just too complex to analyze within limited timeframe Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Complexity vs. analysis § Flame is just too complex to analyze within limited timeframe Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
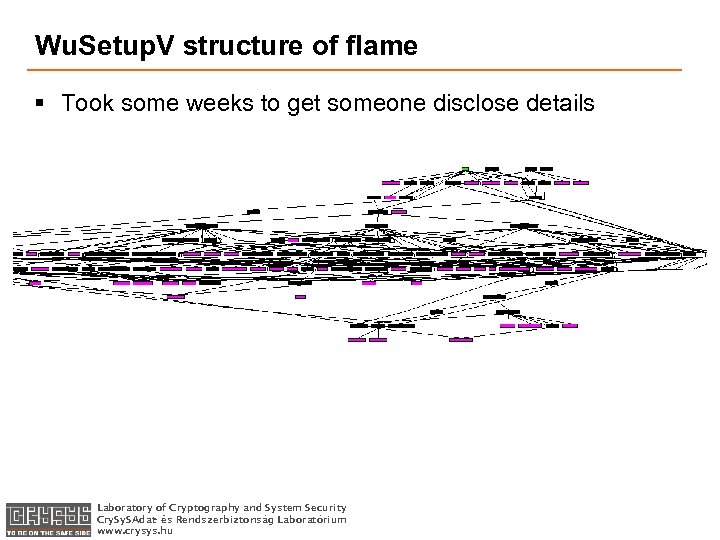 Wu. Setup. V structure of flame § Took some weeks to get someone disclose details Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Wu. Setup. V structure of flame § Took some weeks to get someone disclose details Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Duqu keylogger internal part § No detailed analysis on some aspects, after half a yer Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Duqu keylogger internal part § No detailed analysis on some aspects, after half a yer Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Duqu – jminet 7 driver structure § Still some find out interesting things in the code Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Duqu – jminet 7 driver structure § Still some find out interesting things in the code Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Browse 32 § Flame Suicide module, Browse 32 is 450 k large § High complexity: Why? – Known for weeks, detailed analysis: N/A Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Browse 32 § Flame Suicide module, Browse 32 is 450 k large § High complexity: Why? – Known for weeks, detailed analysis: N/A Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 Duqu/ Netp 191 main module uncompressed § Maybe just a bunch of libraries, but who no one can be sure Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Duqu/ Netp 191 main module uncompressed § Maybe just a bunch of libraries, but who no one can be sure Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
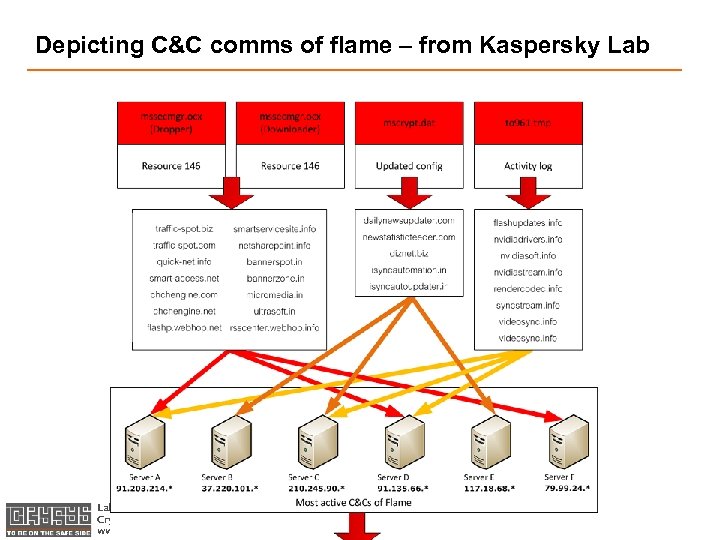 Depicting C&C comms of flame – from Kaspersky Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
Depicting C&C comms of flame – from Kaspersky Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu
 References § Duqu analysis B. Bencsáth, G. Pék, L. Buttyán, M. Félegyházi, Duqu: A Stuxnet-like malware found in the wild, Technical Report, Cry. S Lab, BME, 14 October 2011. available at www. crysys. hu/targeted-attacks. html § Duqu paper B. Bencsáth, G. Pék, L. Buttyán, M. Félegyházi, Duqu: Analysis, Detection, and Lessons Learned, ACM European Workshop on System Security (Euro. Sec) Bern, Switzerland, April 2012. available at www. crysys. hu/targeted-attacks. html § Duqu Detector Toolkit www. crysys. hu/duqudetector. html Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 22
References § Duqu analysis B. Bencsáth, G. Pék, L. Buttyán, M. Félegyházi, Duqu: A Stuxnet-like malware found in the wild, Technical Report, Cry. S Lab, BME, 14 October 2011. available at www. crysys. hu/targeted-attacks. html § Duqu paper B. Bencsáth, G. Pék, L. Buttyán, M. Félegyházi, Duqu: Analysis, Detection, and Lessons Learned, ACM European Workshop on System Security (Euro. Sec) Bern, Switzerland, April 2012. available at www. crysys. hu/targeted-attacks. html § Duqu Detector Toolkit www. crysys. hu/duqudetector. html Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 22
 References § s. Ky. WIper analysis s. Ky. WIper Analysis Team, s. Ky. WIper: A complex malware for targeted attacks, Technical Report, Cry. S Lab, BME, 28 May 2012. available at www. crysys. hu/targeted-attacks. html § on-line Gauss Detector Service gauss. crysys. hu § Cry. S blog site with some interesting articles on the topic including how windows update URL works blog. crysys. hu Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 23
References § s. Ky. WIper analysis s. Ky. WIper Analysis Team, s. Ky. WIper: A complex malware for targeted attacks, Technical Report, Cry. S Lab, BME, 28 May 2012. available at www. crysys. hu/targeted-attacks. html § on-line Gauss Detector Service gauss. crysys. hu § Cry. S blog site with some interesting articles on the topic including how windows update URL works blog. crysys. hu Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu 23
 Next steps § there’s room for innovation in defensive security technology § we are open for collaboration http: //www. crysys. hu/ Duqusubmit anonymous malware submission E 84 E 7 C 73 C 95 D 65 AD E 7 A 6 A 555 53 C 8 E 4 CC bencsath@crysys. hu PGP fingerprint 286 C A 586 6311 36 B 3 2 F 94 B 905 AFB 7 C 688 buttyan@crysys. hu PGP fingerprint 7 E 10 7013 706 B DCD 2 367 C 689 A 5 EA 5 696 E Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu PGP fingerprint: 17 F 0 A 1 A 1 64 CF 6 EFB 37 C 1 BAE 1 24
Next steps § there’s room for innovation in defensive security technology § we are open for collaboration http: //www. crysys. hu/ Duqusubmit anonymous malware submission E 84 E 7 C 73 C 95 D 65 AD E 7 A 6 A 555 53 C 8 E 4 CC bencsath@crysys. hu PGP fingerprint 286 C A 586 6311 36 B 3 2 F 94 B 905 AFB 7 C 688 buttyan@crysys. hu PGP fingerprint 7 E 10 7013 706 B DCD 2 367 C 689 A 5 EA 5 696 E Laboratory of Cryptography and System Security Cry. S Adat- és Rendszerbiztonság Laboratórium www. crysys. hu PGP fingerprint: 17 F 0 A 1 A 1 64 CF 6 EFB 37 C 1 BAE 1 24


