8f17ba2e28eacefbf3dc86e4b2275d41.ppt
- Количество слайдов: 77
 STATE CRIME COMMAND Statewide Specialist Response
STATE CRIME COMMAND Statewide Specialist Response
 e. Medical Crime STATE CRIME COMMAND FRAUD & CYBER CRIME GROUP Presenter: Detective Superintendent Brian Hay
e. Medical Crime STATE CRIME COMMAND FRAUD & CYBER CRIME GROUP Presenter: Detective Superintendent Brian Hay
 AGENDA • Cyber crime • Medical environments • Social Engineering • Dark Markets • Case examples • Prevention Strategies
AGENDA • Cyber crime • Medical environments • Social Engineering • Dark Markets • Case examples • Prevention Strategies

 Cyber Crime
Cyber Crime
 Question? What do you do if your PC’s wifi is hijacked, mac address compromised, you’re trojanised by a keylogger, impregnated and zombied by a botnet, used to commit DDo. S attacks, become a purveyor of phishing SPAM, a vector of drive-by exploit malware and used to extort money from innocent cyber based commercial interests? ? ?
Question? What do you do if your PC’s wifi is hijacked, mac address compromised, you’re trojanised by a keylogger, impregnated and zombied by a botnet, used to commit DDo. S attacks, become a purveyor of phishing SPAM, a vector of drive-by exploit malware and used to extort money from innocent cyber based commercial interests? ? ?
 Situation • Cyber crime is an unknown quantity • Rarely is cyber crime reported to police • Cyber crime is destined to grow – rapidly! • Cyber criminals are industrialised and Internationally networked in real time – law enforcement is not! • Police are not at the coal face
Situation • Cyber crime is an unknown quantity • Rarely is cyber crime reported to police • Cyber crime is destined to grow – rapidly! • Cyber criminals are industrialised and Internationally networked in real time – law enforcement is not! • Police are not at the coal face
 Situation Most cyber criminals are overseas and will never be caught Cyber crime represents the greatest challenge to law enforcement in the history of policing And…. .
Situation Most cyber criminals are overseas and will never be caught Cyber crime represents the greatest challenge to law enforcement in the history of policing And…. .
 The view of ASD? If you’re connected to the internet you’re already compromised!
The view of ASD? If you’re connected to the internet you’re already compromised!
 Key Influencers • Internet Reach • Globalisation • Driving of digital economy • Apathy and denial • Lack of security skills and knowledge • Significant criminal R & D
Key Influencers • Internet Reach • Globalisation • Driving of digital economy • Apathy and denial • Lack of security skills and knowledge • Significant criminal R & D
 Internet Reach • Australia – 89% connectivity • Rest of World – 34% • Nigeria – 8% (160 m) • India – 12% (1. 3 b) • China – 38% (1. 3 b) • China – 100, 000 Hackers
Internet Reach • Australia – 89% connectivity • Rest of World – 34% • Nigeria – 8% (160 m) • India – 12% (1. 3 b) • China – 38% (1. 3 b) • China – 100, 000 Hackers
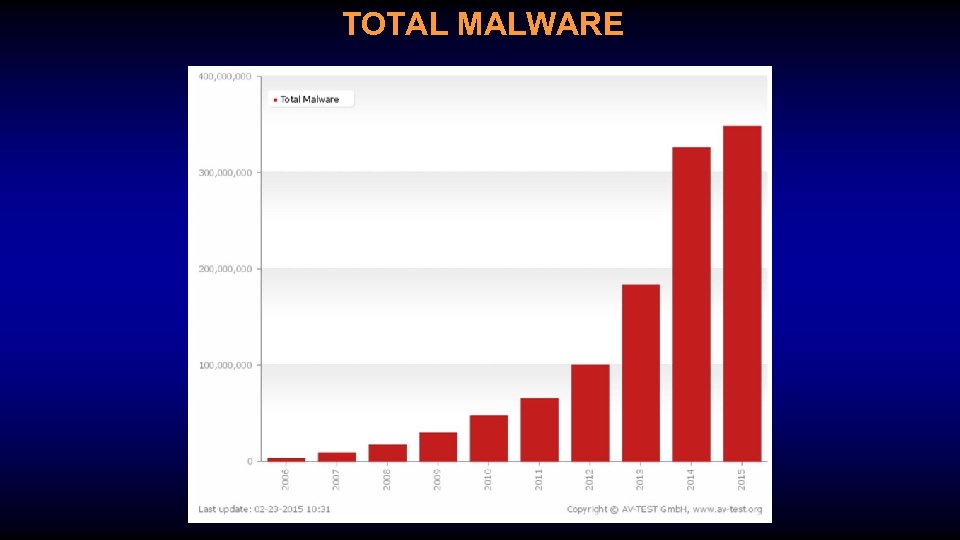 TOTAL MALWARE
TOTAL MALWARE
 A FEW FACTS • The AV Test Institute registers over 390, 000 new pieces of malware every day • Malware for smart phones outstripped malware for PC’s since 2012 • 49% of Top 100 Google Sites are malicious • On average it takes 230 days before a breach is detected.
A FEW FACTS • The AV Test Institute registers over 390, 000 new pieces of malware every day • Malware for smart phones outstripped malware for PC’s since 2012 • 49% of Top 100 Google Sites are malicious • On average it takes 230 days before a breach is detected.
 Potentially the Greatest Vulnerability… besides you? • The more you put on it the bigger a target it becomes • Apps ballistic! • Blue tooth vulnerabilities • Steal the data • Steal the photos • The mobile botnet • Turn it into a listening device • Track your every move with GPS
Potentially the Greatest Vulnerability… besides you? • The more you put on it the bigger a target it becomes • Apps ballistic! • Blue tooth vulnerabilities • Steal the data • Steal the photos • The mobile botnet • Turn it into a listening device • Track your every move with GPS
 SMART PHONE REVOLUTION • 50 Billion in 5 years! • They are not just a phone! • The malware is here!
SMART PHONE REVOLUTION • 50 Billion in 5 years! • They are not just a phone! • The malware is here!
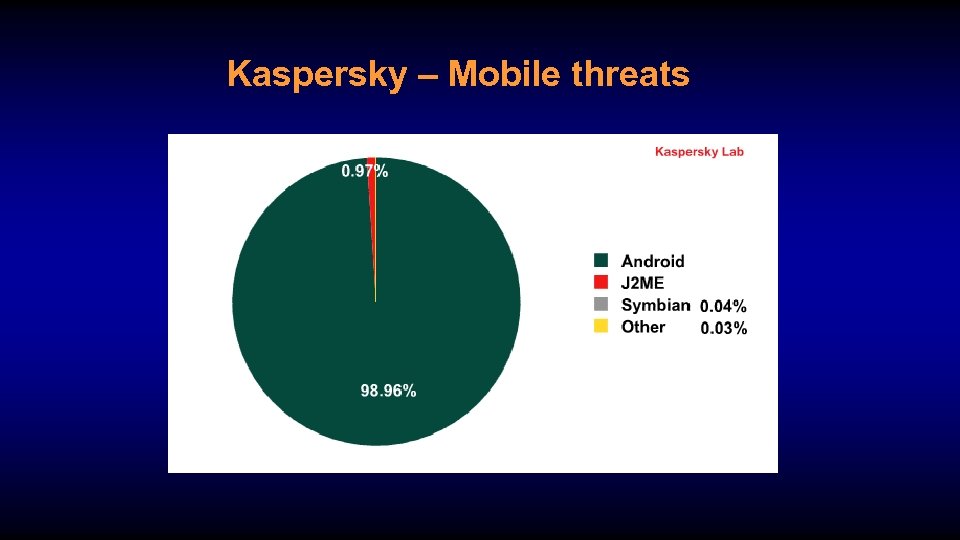 Kaspersky – Mobile threats
Kaspersky – Mobile threats
 The e. Medical Environment • Great adopters of technology • Proliferation of wireless devices • Increased potential for remote activities • Increased centralisation of national data
The e. Medical Environment • Great adopters of technology • Proliferation of wireless devices • Increased potential for remote activities • Increased centralisation of national data
 Technology
Technology
 Is it all secure? Is your data safe?
Is it all secure? Is your data safe?
 e. Medical Potential Compromises • The clinic • The professional • The administrator • The network • The computer, smartphone, ipad • The database • The USB
e. Medical Potential Compromises • The clinic • The professional • The administrator • The network • The computer, smartphone, ipad • The database • The USB
 The Social Engineering Threat
The Social Engineering Threat
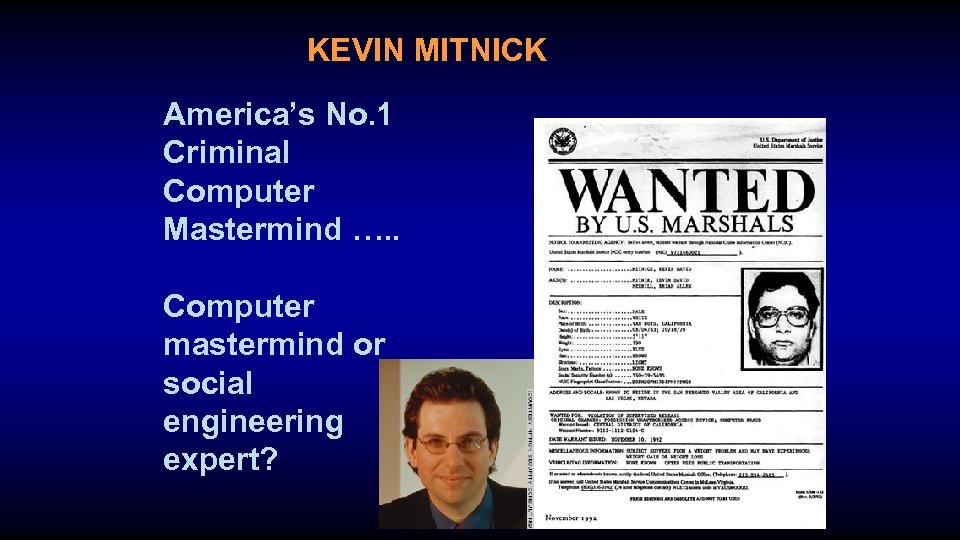 KEVIN MITNICK America’s No. 1 Criminal Computer Mastermind …. . Computer mastermind or social engineering expert?
KEVIN MITNICK America’s No. 1 Criminal Computer Mastermind …. . Computer mastermind or social engineering expert?
 US Military Breach
US Military Breach
 THE GULF WAR
THE GULF WAR
 Who wants the data? ? ?
Who wants the data? ? ?
 What are the criminal commodities? • Identity data • Financial data • Medical data • medical insurance fraud • extortion • employment • identity take over (drugs & $$) •
What are the criminal commodities? • Identity data • Financial data • Medical data • medical insurance fraud • extortion • employment • identity take over (drugs & $$) •
 Stop thinking medical – Start thinking identity! Old Mrs Smith’s medical file might not be worth a lot, but her identity is… could you be civilly liable for losing it?
Stop thinking medical – Start thinking identity! Old Mrs Smith’s medical file might not be worth a lot, but her identity is… could you be civilly liable for losing it?
 Market Value? • Social Security No. = $1 • Medical File = $50
Market Value? • Social Security No. = $1 • Medical File = $50
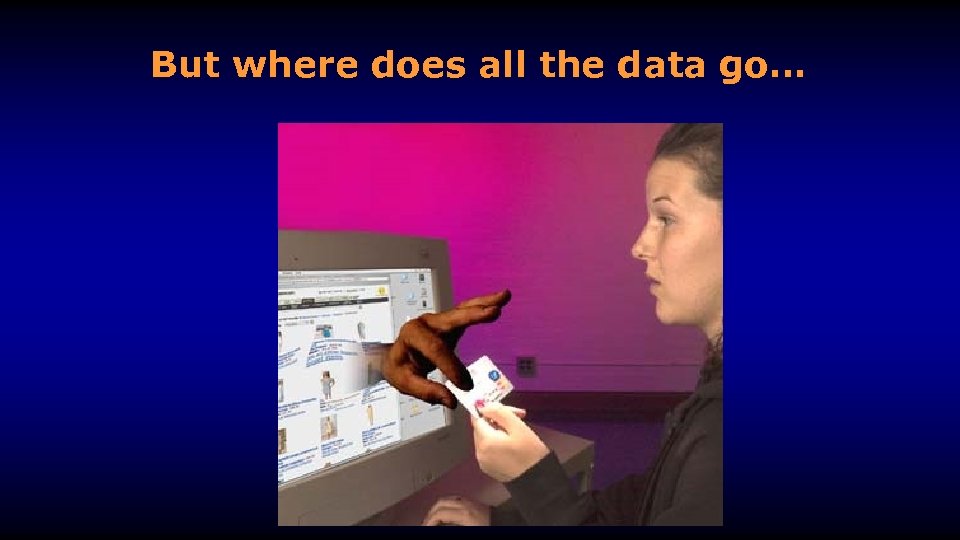 But where does all the data go…
But where does all the data go…
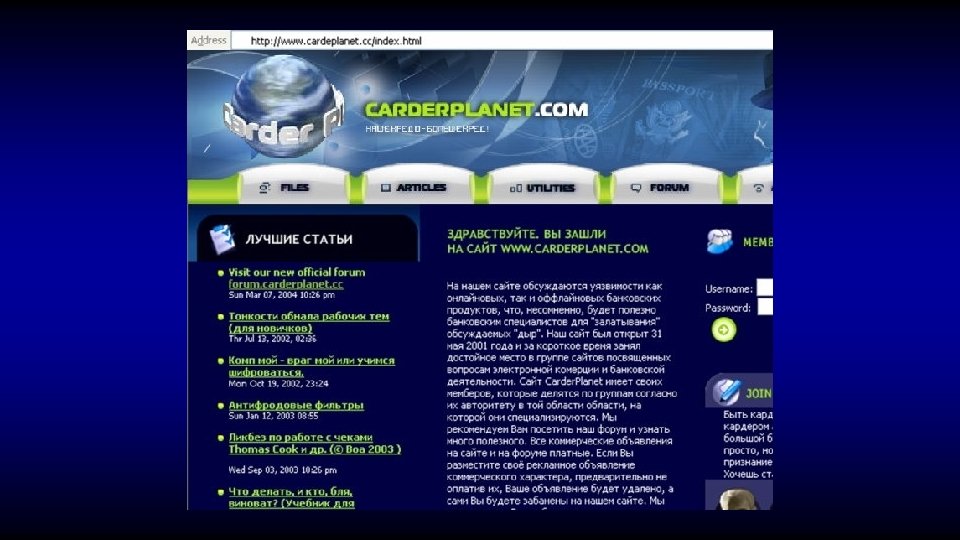
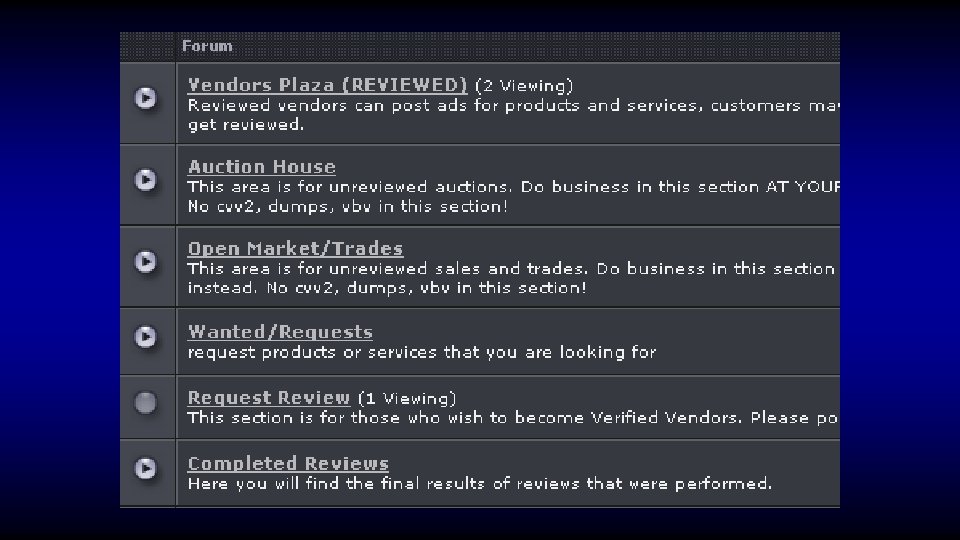
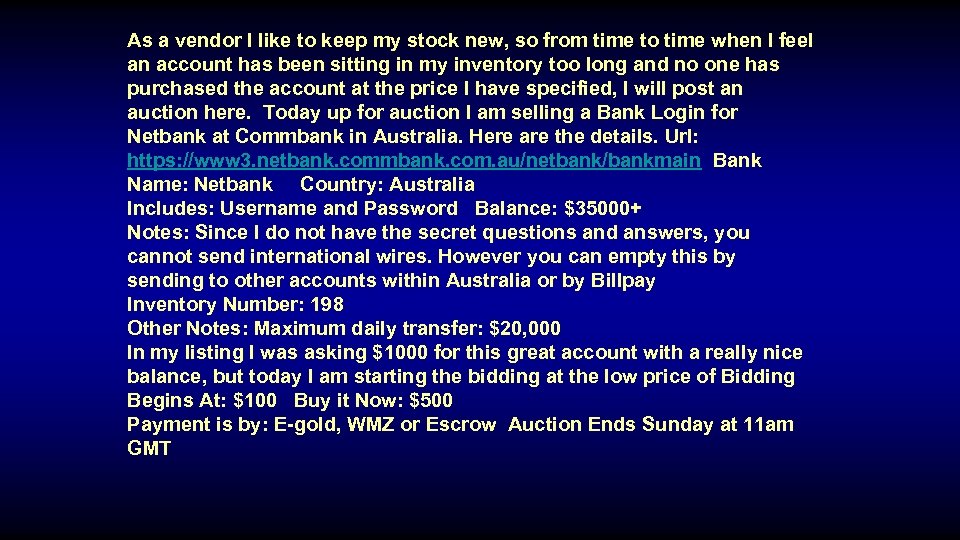 As a vendor I like to keep my stock new, so from time to time when I feel an account has been sitting in my inventory too long and no one has purchased the account at the price I have specified, I will post an auction here. Today up for auction I am selling a Bank Login for Netbank at Commbank in Australia. Here are the details. Url: https: //www 3. netbank. commbank. com. au/netbank/bankmain Bank Name: Netbank Country: Australia Includes: Username and Password Balance: $35000+ Notes: Since I do not have the secret questions and answers, you cannot send international wires. However you can empty this by sending to other accounts within Australia or by Billpay Inventory Number: 198 Other Notes: Maximum daily transfer: $20, 000 In my listing I was asking $1000 for this great account with a really nice balance, but today I am starting the bidding at the low price of Bidding Begins At: $100 Buy it Now: $500 Payment is by: E-gold, WMZ or Escrow Auction Ends Sunday at 11 am GMT
As a vendor I like to keep my stock new, so from time to time when I feel an account has been sitting in my inventory too long and no one has purchased the account at the price I have specified, I will post an auction here. Today up for auction I am selling a Bank Login for Netbank at Commbank in Australia. Here are the details. Url: https: //www 3. netbank. commbank. com. au/netbank/bankmain Bank Name: Netbank Country: Australia Includes: Username and Password Balance: $35000+ Notes: Since I do not have the secret questions and answers, you cannot send international wires. However you can empty this by sending to other accounts within Australia or by Billpay Inventory Number: 198 Other Notes: Maximum daily transfer: $20, 000 In my listing I was asking $1000 for this great account with a really nice balance, but today I am starting the bidding at the low price of Bidding Begins At: $100 Buy it Now: $500 Payment is by: E-gold, WMZ or Escrow Auction Ends Sunday at 11 am GMT
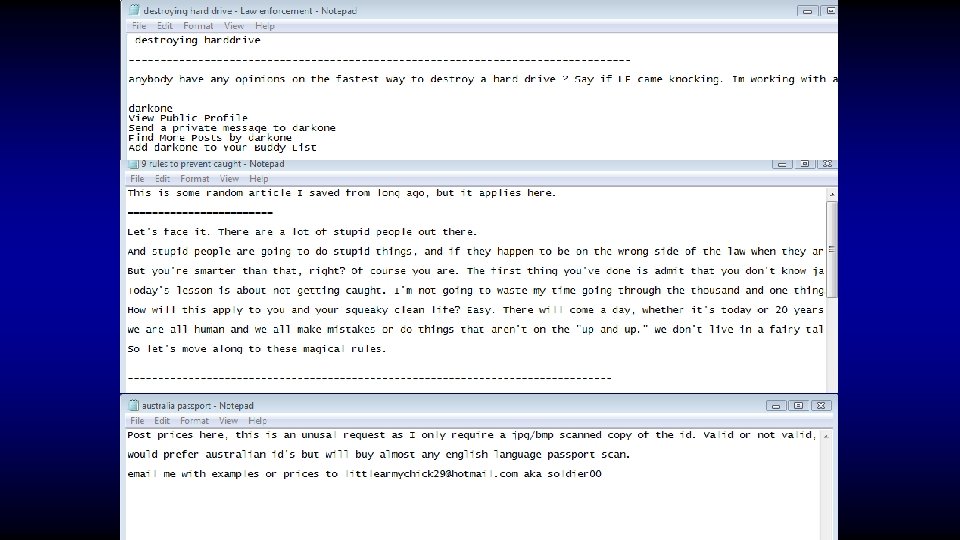
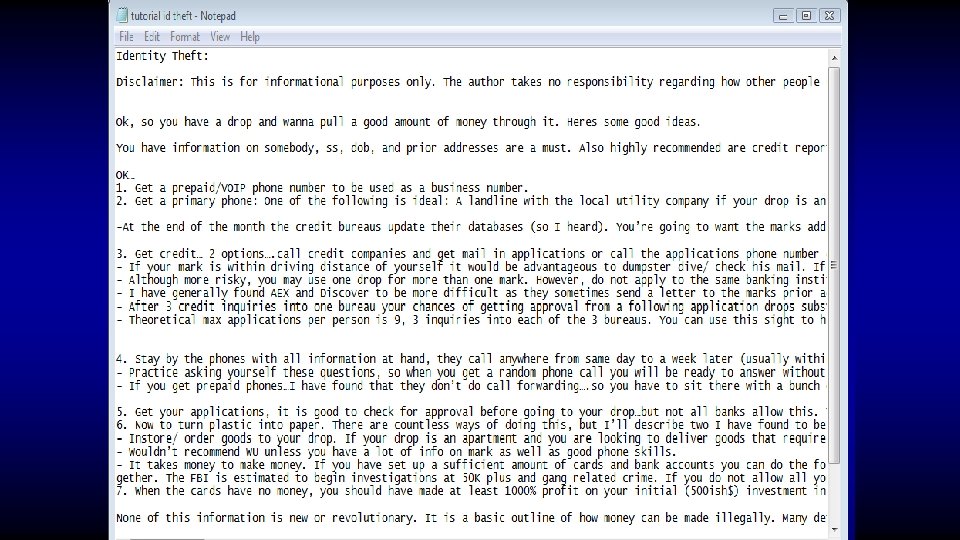
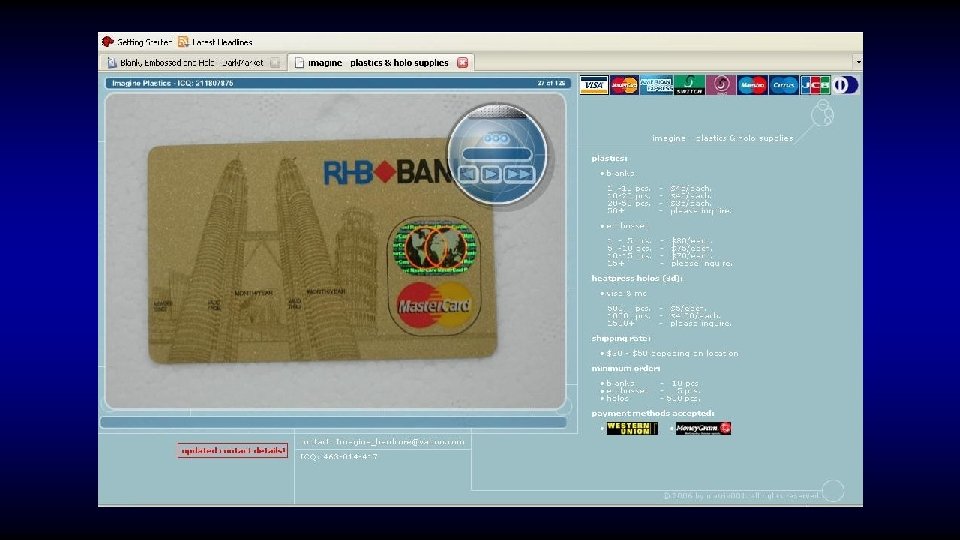


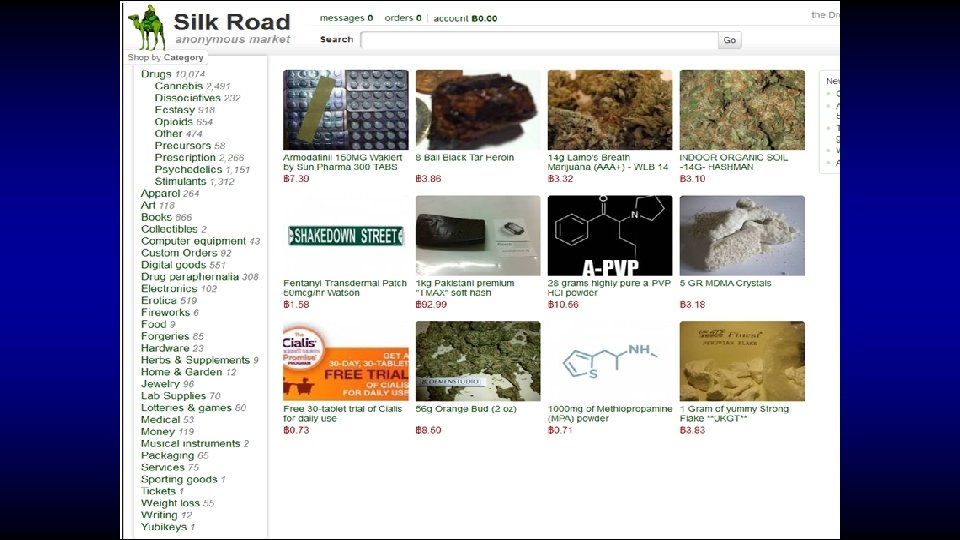
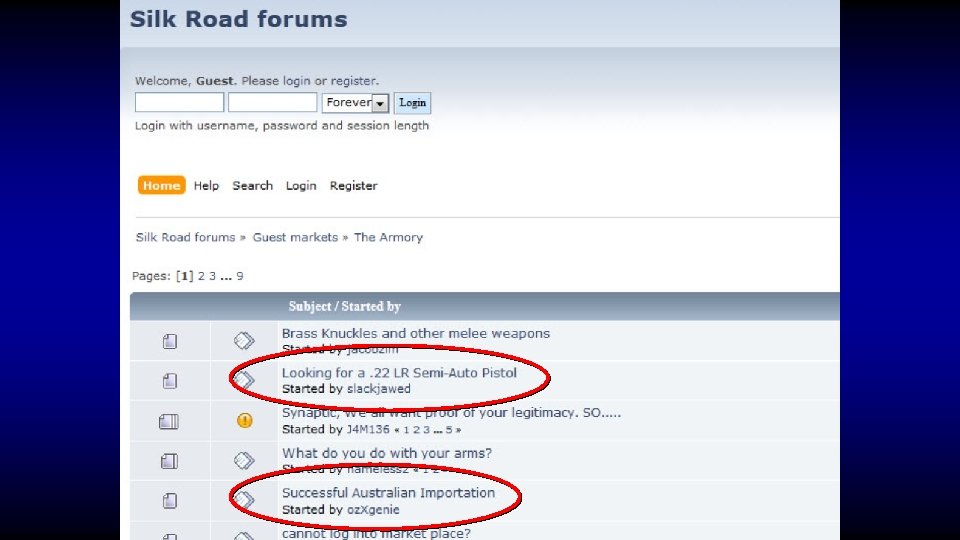
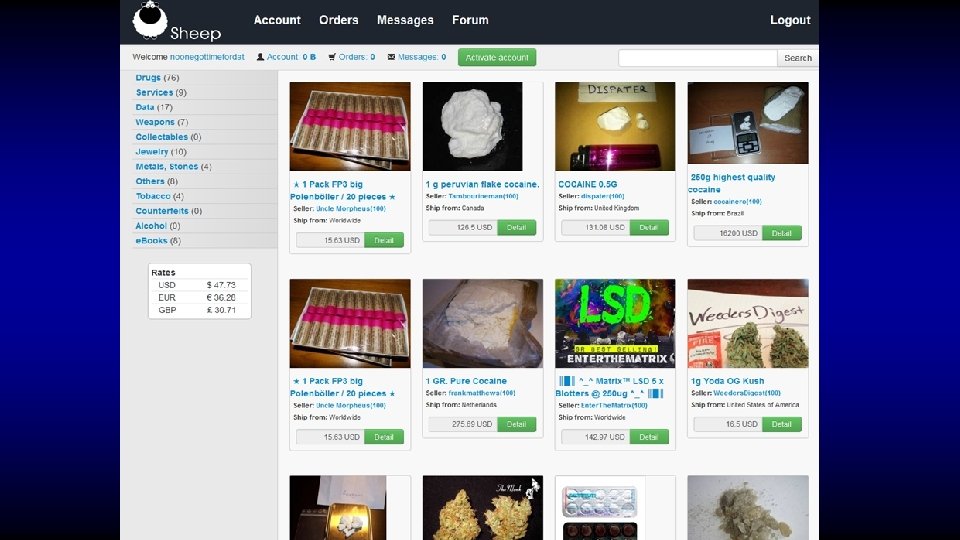
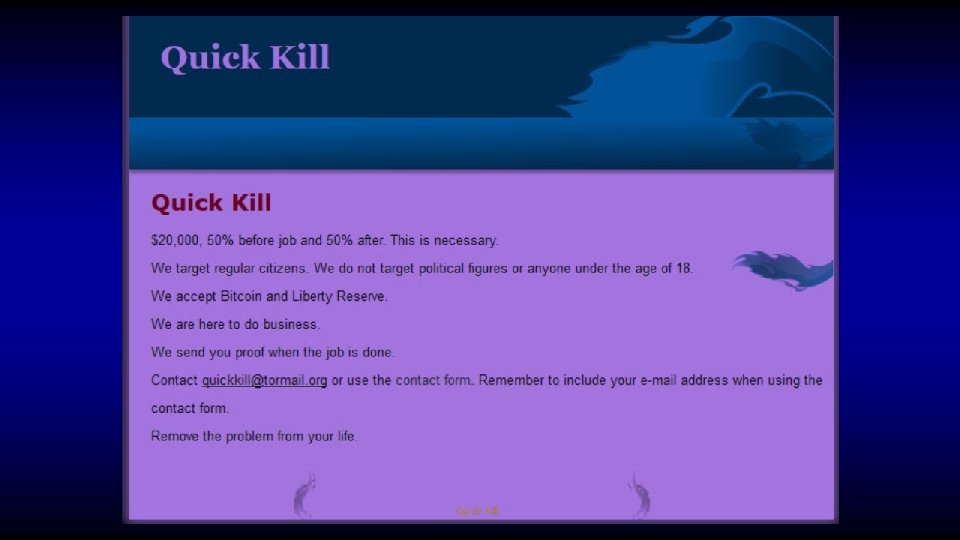
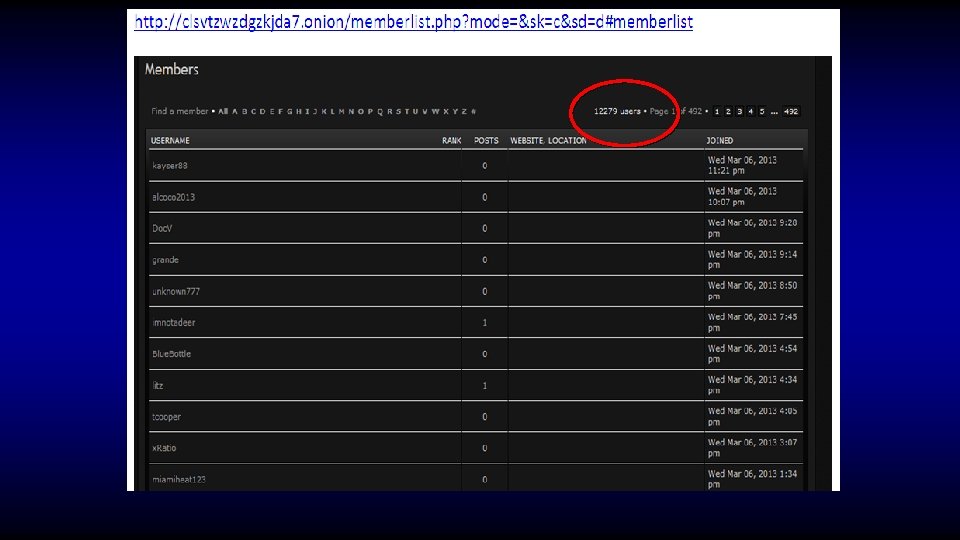
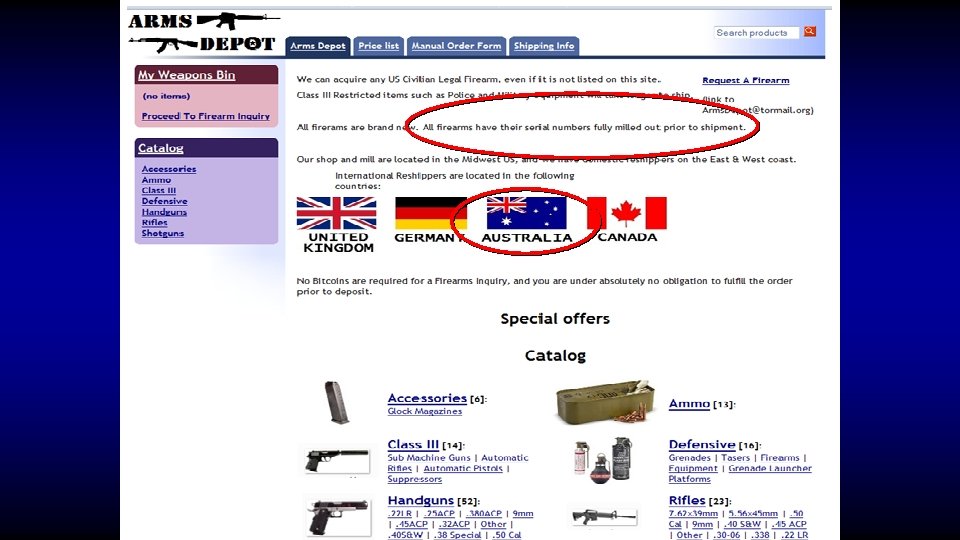
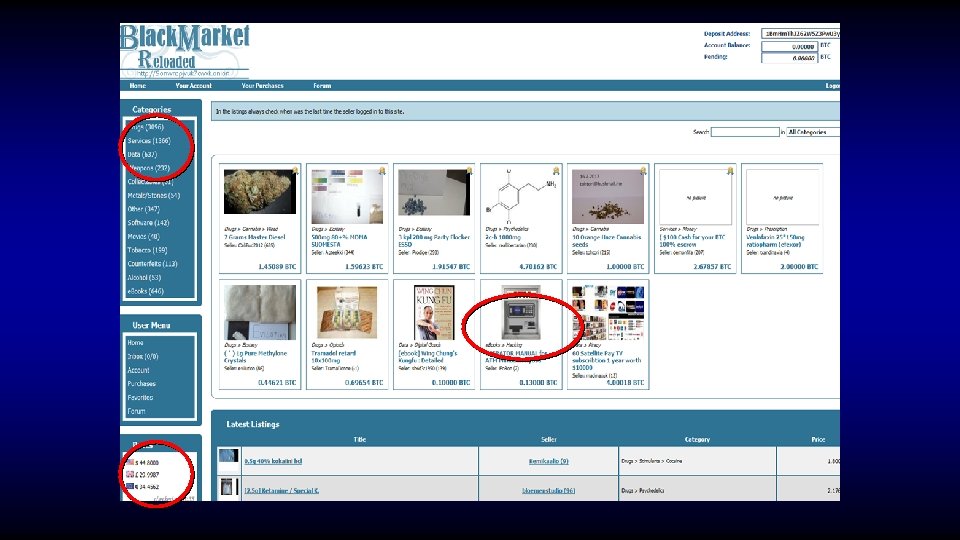
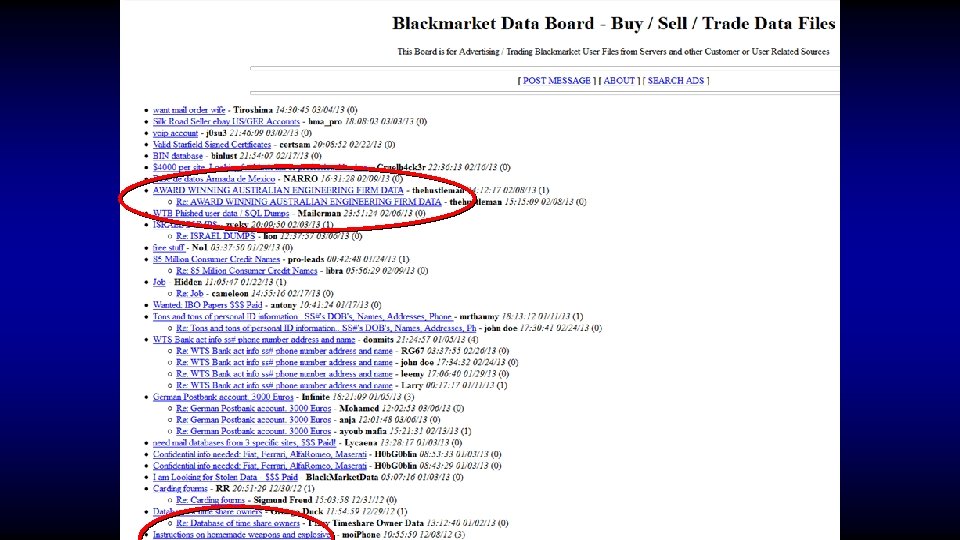
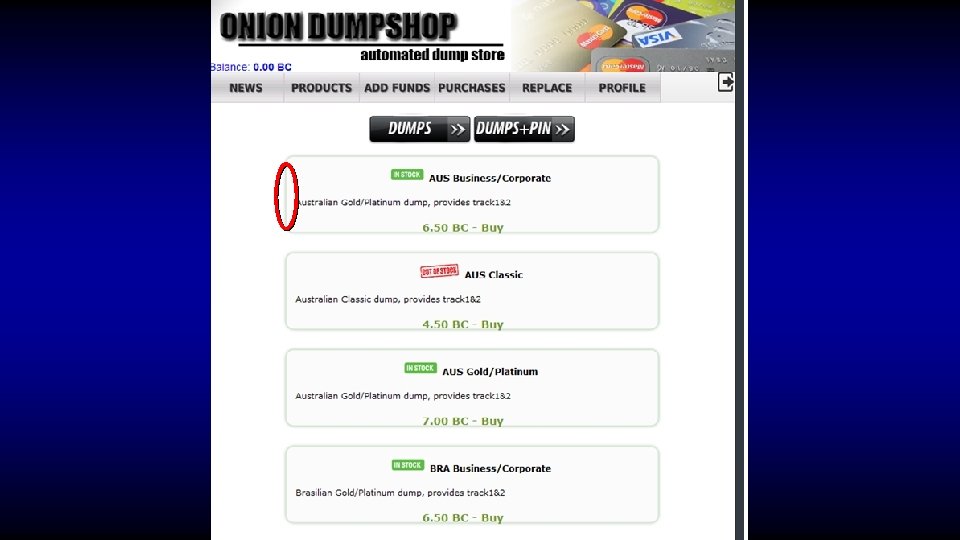
 Who said crime doesn’t pay?
Who said crime doesn’t pay?
 The Cost? • Estimates of US Medical fraud range from $80 to $230 Billion per annum
The Cost? • Estimates of US Medical fraud range from $80 to $230 Billion per annum
 Medical ID Theft increases 22% in 2014! Why? • increased data breaches • rise of electronic health records • the increasing number of connected devices has created more entry points for attackers.
Medical ID Theft increases 22% in 2014! Why? • increased data breaches • rise of electronic health records • the increasing number of connected devices has created more entry points for attackers.
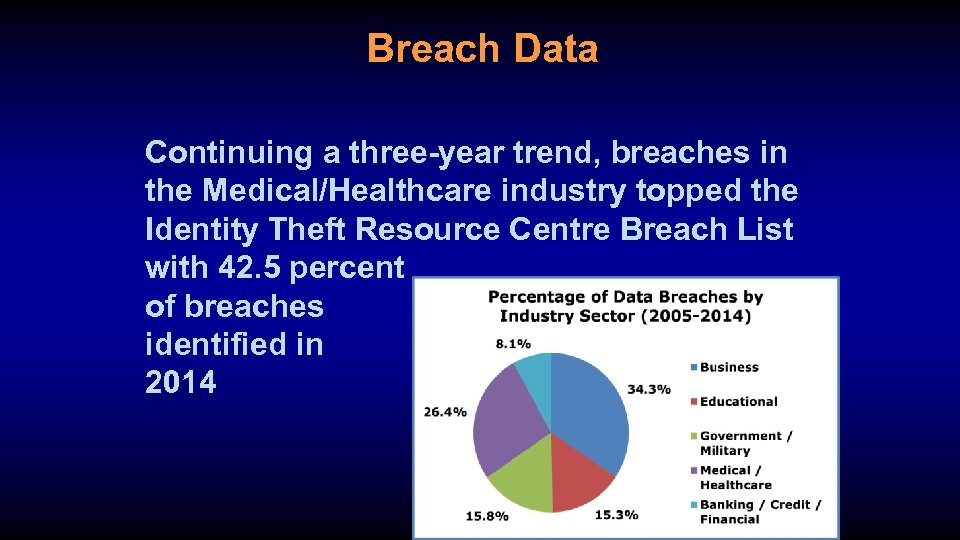 Breach Data Continuing a three-year trend, breaches in the Medical/Healthcare industry topped the Identity Theft Resource Centre Breach List with 42. 5 percent of breaches identified in 2014
Breach Data Continuing a three-year trend, breaches in the Medical/Healthcare industry topped the Identity Theft Resource Centre Breach List with 42. 5 percent of breaches identified in 2014
 Cases May 2012 Medical Technician at Washington’s Howard University Medical Centre charged for stealing patient’s personal and medical information
Cases May 2012 Medical Technician at Washington’s Howard University Medical Centre charged for stealing patient’s personal and medical information
 Cases May 2012, Utah Health Department massive data breach – Eastern European Hackers – 280, 000 identities and files stolen
Cases May 2012, Utah Health Department massive data breach – Eastern European Hackers – 280, 000 identities and files stolen
 Cases July 2012, Chicago – hackers broke in to a medical practices and encrypted data and then demanded a payment to unlock.
Cases July 2012, Chicago – hackers broke in to a medical practices and encrypted data and then demanded a payment to unlock.
 You Are Compromised! “Essentially, criminals have come to understand that using your medical credentials—your name, Social Security Number and health insurance numbers—to order goods and services that are never delivered and to bill organizations like Medicare and Medicaid, those activities are more profitable than drugs, prostitution, and other crimes they may pursue. ” For this reason, medical identities are 20 to 50 times more valuable to criminals than financial identities. Rick Cam – President ID Experts
You Are Compromised! “Essentially, criminals have come to understand that using your medical credentials—your name, Social Security Number and health insurance numbers—to order goods and services that are never delivered and to bill organizations like Medicare and Medicaid, those activities are more profitable than drugs, prostitution, and other crimes they may pursue. ” For this reason, medical identities are 20 to 50 times more valuable to criminals than financial identities. Rick Cam – President ID Experts
 You Are Compromised! Identity theft is so pervasive in health care that, according to a 2013 ID Experts data security Survey of 91 healthcare organisations, 90% of respondents had experienced a data breach in the previous two years and 38% had more than five incidents.
You Are Compromised! Identity theft is so pervasive in health care that, according to a 2013 ID Experts data security Survey of 91 healthcare organisations, 90% of respondents had experienced a data breach in the previous two years and 38% had more than five incidents.
 What can go wrong? In Oregon, a pregnant woman delivered a baby addicted to crack using another woman’s social security number—and then abandoned the baby. Police arrested the victim and put her children into protective custody. Another woman couldn’t get physical therapy following neck surgery because a Miami clinic that she had never visited claimed her insurance benefits had been maxed out.
What can go wrong? In Oregon, a pregnant woman delivered a baby addicted to crack using another woman’s social security number—and then abandoned the baby. Police arrested the victim and put her children into protective custody. Another woman couldn’t get physical therapy following neck surgery because a Miami clinic that she had never visited claimed her insurance benefits had been maxed out.
 Lack of prevention Unlike the financial services industry, health care companies lack measures to adequately prevent identity theft, even as they continue to digitize medical records and other sensitive information. 31 August 2014
Lack of prevention Unlike the financial services industry, health care companies lack measures to adequately prevent identity theft, even as they continue to digitize medical records and other sensitive information. 31 August 2014
 Medical Device Hacking Jay Radcliffe successfully hacked his own insulin pump and discovered massive loopholes for cybercriminals. There is no cross-medical industry protocol for coding QA and testing; as a result, software holes often aren't discovered until equipment fails in the field.
Medical Device Hacking Jay Radcliffe successfully hacked his own insulin pump and discovered massive loopholes for cybercriminals. There is no cross-medical industry protocol for coding QA and testing; as a result, software holes often aren't discovered until equipment fails in the field.
 The e. Medical migration now makes the medical environment and all those within it a legitimate target!
The e. Medical migration now makes the medical environment and all those within it a legitimate target!
 Should we allow social Networking in the Workplace?
Should we allow social Networking in the Workplace?
 SOCIAL NETWORKING PAGES
SOCIAL NETWORKING PAGES
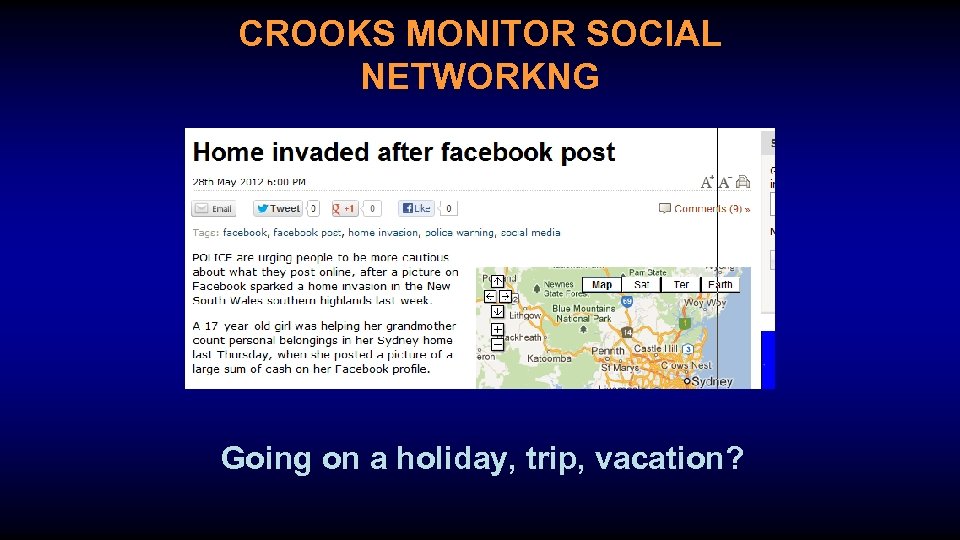 CROOKS MONITOR SOCIAL NETWORKNG Going on a holiday, trip, vacation?
CROOKS MONITOR SOCIAL NETWORKNG Going on a holiday, trip, vacation?
 Social Networking Sites “I’d rather have a rectal examination on live TV by a fellow with cold hands than have a Facebook page” – George Clooney
Social Networking Sites “I’d rather have a rectal examination on live TV by a fellow with cold hands than have a Facebook page” – George Clooney
 Facebook – the 20 Folder Test If you’re game….
Facebook – the 20 Folder Test If you’re game….

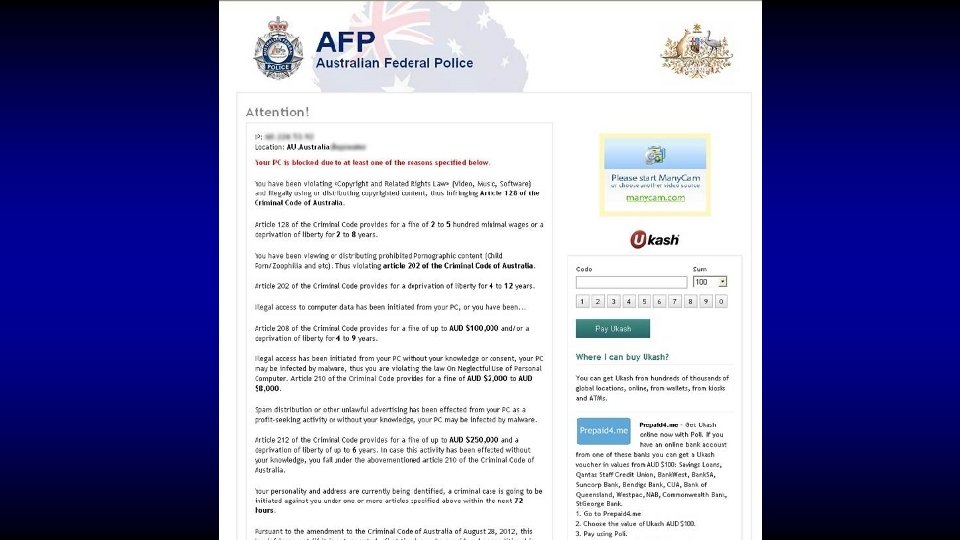
 Ransomware • Locks down your PC or Server • Infected by drive-by exploit or hack • Mobile ransomware • Attacking individuals & businesses
Ransomware • Locks down your PC or Server • Infected by drive-by exploit or hack • Mobile ransomware • Attacking individuals & businesses
 Australia Sep 2012 • 2 medical centres – server compromised - encrypted • then 4 medical centres • then 30+ businesses across the country • and the list is growing…
Australia Sep 2012 • 2 medical centres – server compromised - encrypted • then 4 medical centres • then 30+ businesses across the country • and the list is growing…
 The Internet is like the Pacific Highway • It’s not perfect • Some parts are better than others • There are some rules to regulate • There are risks to driving
The Internet is like the Pacific Highway • It’s not perfect • Some parts are better than others • There are some rules to regulate • There are risks to driving
 The Difference? • We’re trained and qualified before allowed on the highway • We are educated on the risks • We manage the risks and insure against them • We are educated on the rules and know the consequences
The Difference? • We’re trained and qualified before allowed on the highway • We are educated on the risks • We manage the risks and insure against them • We are educated on the rules and know the consequences
 Me? • I do internet banking • I purchase goods online • I use the internet every day • I value and support the internet
Me? • I do internet banking • I purchase goods online • I use the internet every day • I value and support the internet
 You Are Compromised! • Manage the risk • Focus on the internal not just external • Defend against social engineering • Understand that your data has value • Don’t leave the IT environment to your IT specialists
You Are Compromised! • Manage the risk • Focus on the internal not just external • Defend against social engineering • Understand that your data has value • Don’t leave the IT environment to your IT specialists
 Do You Have…. ? • A Cyber Security Strategy • A Cyber training plan • A Cyber Risk Management Plan • A Cyber Incident Response Plan • An effective governance framework for monitoring cyber activities
Do You Have…. ? • A Cyber Security Strategy • A Cyber training plan • A Cyber Risk Management Plan • A Cyber Incident Response Plan • An effective governance framework for monitoring cyber activities

 Contact Detective Superintendent Brian Hay hay. brianj@police. qld. gov. au
Contact Detective Superintendent Brian Hay hay. brianj@police. qld. gov. au
 QUESTIONS STATE CRIME OPERATIONS COMMAND Statewide Specialist Response
QUESTIONS STATE CRIME OPERATIONS COMMAND Statewide Specialist Response


