8514192c5755784160598949d37cdffa.ppt
- Количество слайдов: 33

SSL-VPN Provision by Purpose and Access Privilege Management Jonas Gyllenhammar Senior Systems Engineer Secure Access Products – Northern Europe Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net
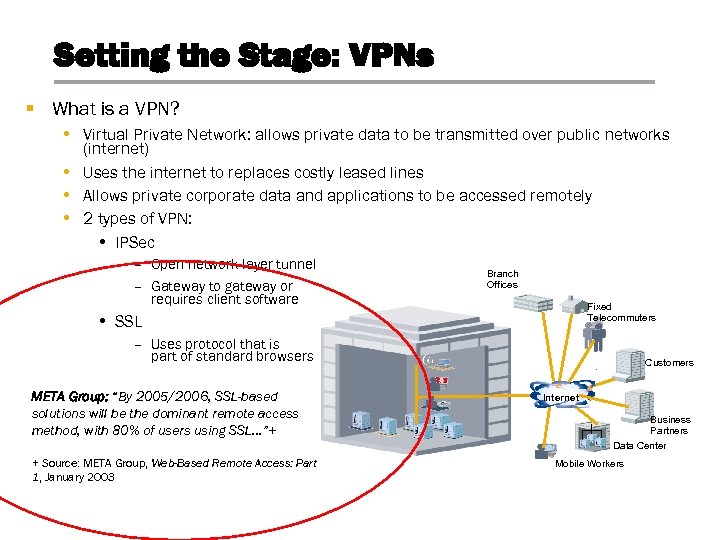
Setting the Stage: VPNs § What is a VPN? • Virtual Private Network: allows private data to be transmitted over public networks (internet) • Uses the internet to replaces costly leased lines • Allows private corporate data and applications to be accessed remotely • 2 types of VPN: • IPSec – Open network-layer tunnel – Gateway to gateway or requires client software Branch Offices Fixed Telecommuters • SSL – Uses protocol that is part of standard browsers META Group: “By 2005/2006, SSL-based solutions will be the dominant remote access method, with 80% of users using SSL…”+ Customers Internet Business Partners Data Center + Source: META Group, Web-Based Remote Access: Part 1, January 2003 Mobile Workers
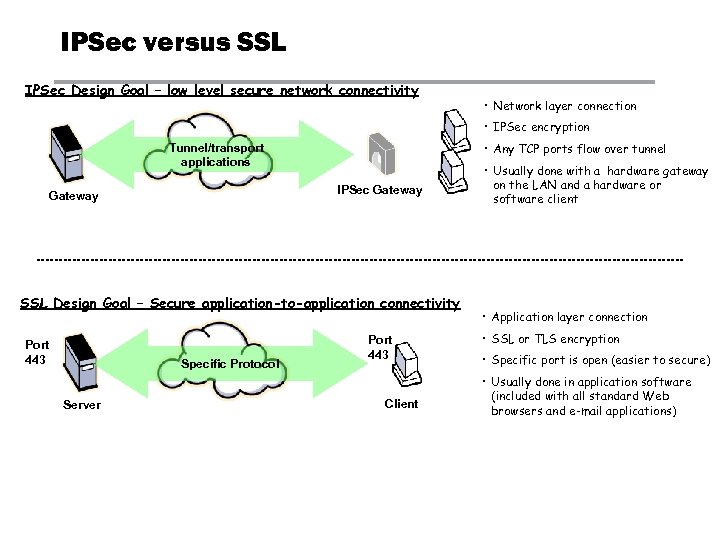
IPSec versus SSL IPSec Design Goal – low level secure network connectivity • Network layer connection • IPSec encryption • Any TCP ports flow over tunnel Tunnel/transport applications IPSec Gateway SSL Design Goal – Secure application-to-application connectivity Port 443 Specific Protocol Server Port 443 Client • Usually done with a hardware gateway on the LAN and a hardware or software client • Application layer connection • SSL or TLS encryption • Specific port is open (easier to secure) • Usually done in application software (included with all standard Web browsers and e-mail applications)

Avoid this…. .
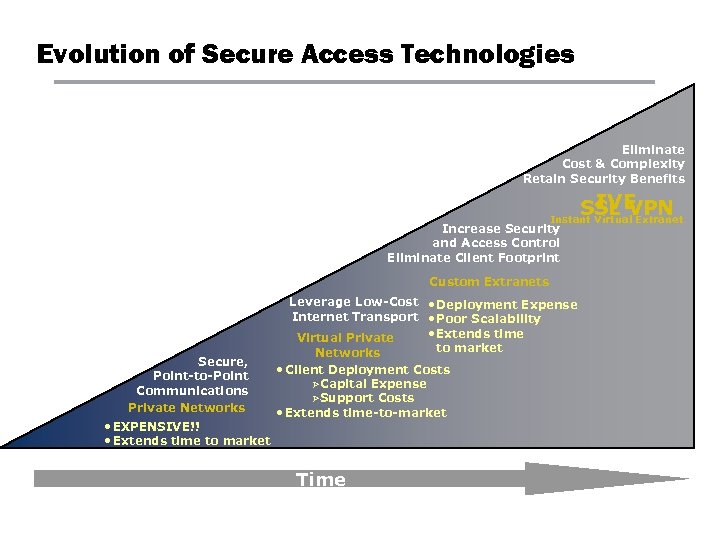
Evolution of Secure Access Technologies Eliminate Cost & Complexity Retain Security Benefits IVE SSL VPN Instant Virtual Extranet Increase Security and Access Control Eliminate Client Footprint Custom Extranets Secure, Point-to-Point Communications Private Networks • EXPENSIVE!! • Extends time to market Leverage Low-Cost • Deployment Expense Internet Transport • Poor Scalability • Extends time Virtual Private to market Networks • Client Deployment Costs ØCapital Expense ØSupport Costs • Extends time-to-market Time
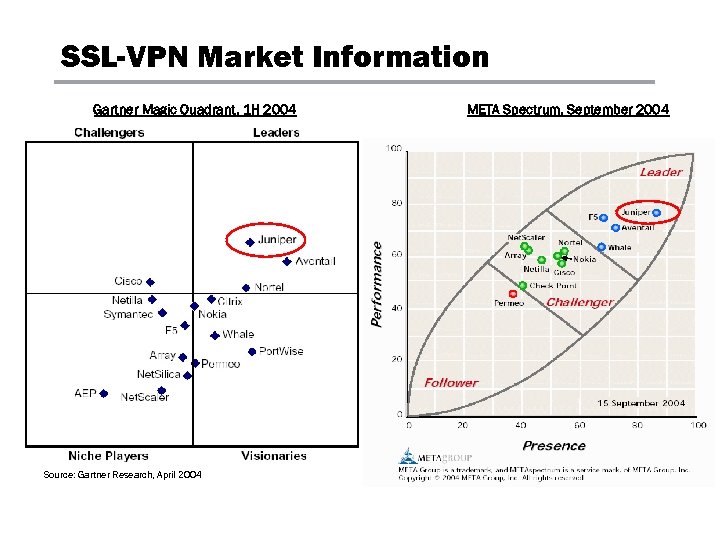
SSL-VPN Market Information Gartner Magic Quadrant, 1 H 2004 Source: Gartner Research, April 2004 META Spectrum, September 2004

A SSL-VPN is a. . SSL-VPN ≠ SSL-VPN
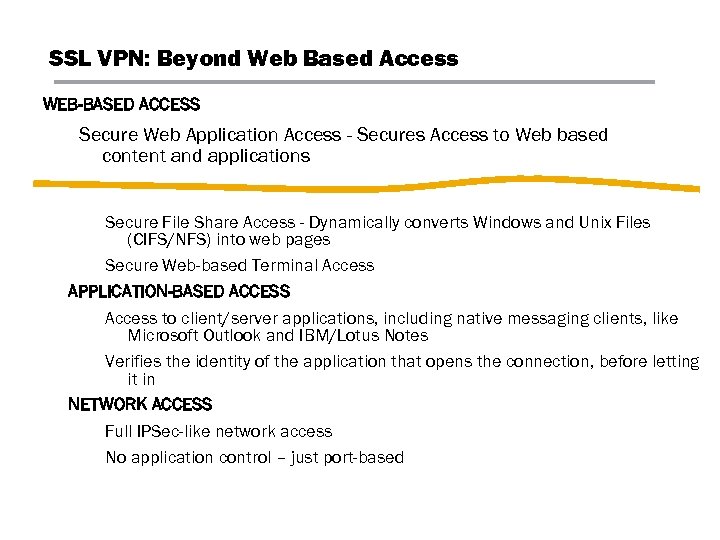
SSL VPN: Beyond Web Based Access WEB-BASED ACCESS Secure Web Application Access - Secures Access to Web based content and applications Secure File Share Access - Dynamically converts Windows and Unix Files (CIFS/NFS) into web pages Secure Web-based Terminal Access APPLICATION-BASED ACCESS Access to client/server applications, including native messaging clients, like Microsoft Outlook and IBM/Lotus Notes Verifies the identity of the application that opens the connection, before letting it in NETWORK ACCESS Full IPSec-like network access No application control – just port-based
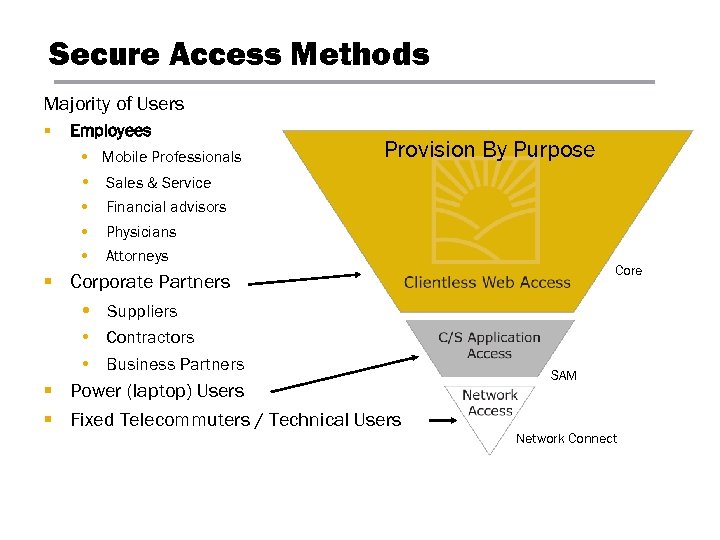
Secure Access Methods Majority of Users § Employees • Mobile Professionals Provision By Purpose • Sales & Service • Financial advisors • Physicians • Attorneys Core § Corporate Partners • Suppliers • Contractors • Business Partners § Power (laptop) Users § Fixed Telecommuters / Technical Users SAM Network Connect
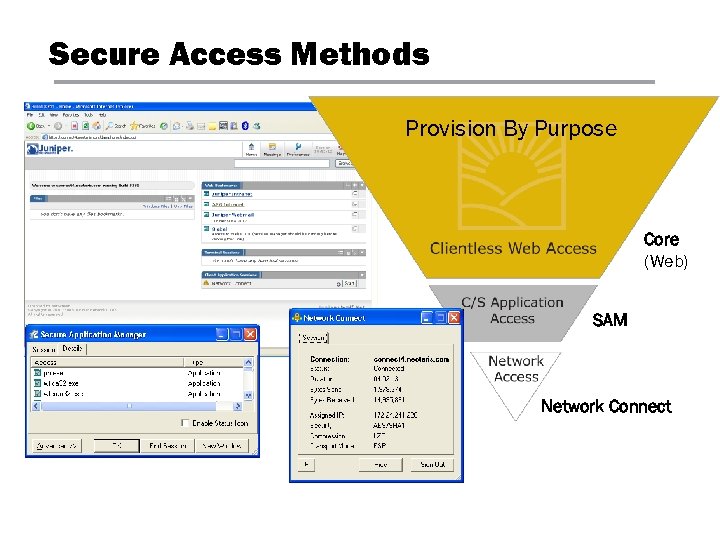
Secure Access Methods Provision By Purpose Core (Web) SAM Network Connect
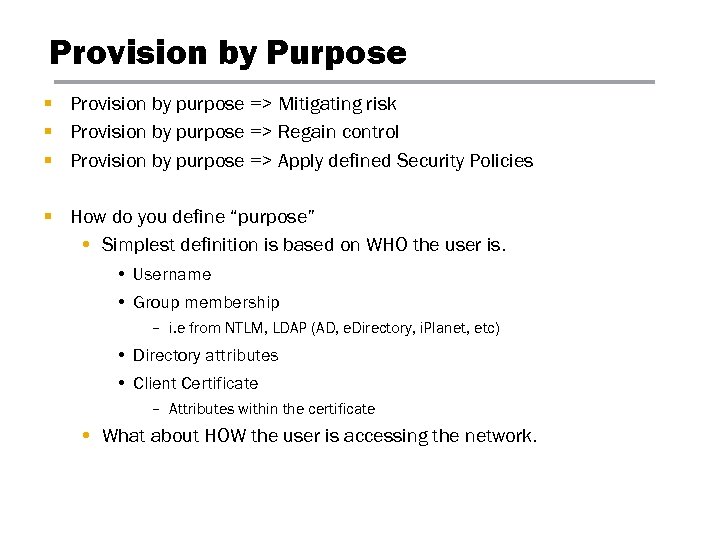
Provision by Purpose § Provision by purpose => Mitigating risk § Provision by purpose => Regain control § Provision by purpose => Apply defined Security Policies § How do you define “purpose” • Simplest definition is based on WHO the user is. • Username • Group membership – i. e from NTLM, LDAP (AD, e. Directory, i. Planet, etc) • Directory attributes • Client Certificate – Attributes within the certificate • What about HOW the user is accessing the network.
Provision by Purpose – Continued § Access Privilege Management • Traditionally the “purpose” is only defined based on WHO the user is, Group membership, etc • Another component that is important is the users environment. Essentially meaning HOW the user is accessing the system • From what IP Subnet/Range • What type of Client Machine – Anti. Virus, Personal. FW, Registry settings, Processes running, open ports… § Security Policies normally has to be updated • Normally lacks policies for un-managed PCs • Normally lacks policies for where IP (Intellectual Property) can reside • SSL-VPN Platform must be flexible enough to adapt to all various Polices.
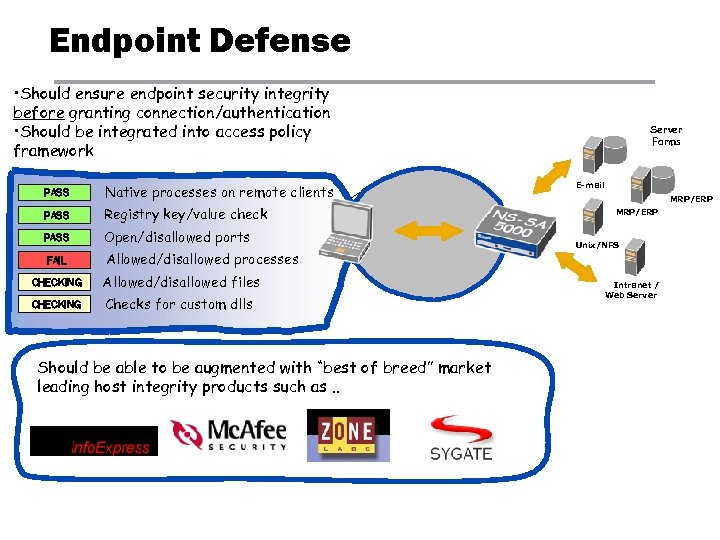
Endpoint Defense • Should ensure endpoint security integrity before granting connection/authentication • Should be integrated into access policy framework PASS Native processes on remote clients PASS Registry key/value check PASS Open/disallowed ports FAIL Allowed/disallowed processes CHECKING Allowed/disallowed files CHECKING Checks for custom dlls Should be able to be augmented with “best of breed” market leading host integrity products such as. . Server Farms E-mail MRP/ERP Unix/NFS Intranet / Web Server

End Point Security Initiative Members include: More members on https: //www. trustedcomputinggroup. org/about/members/
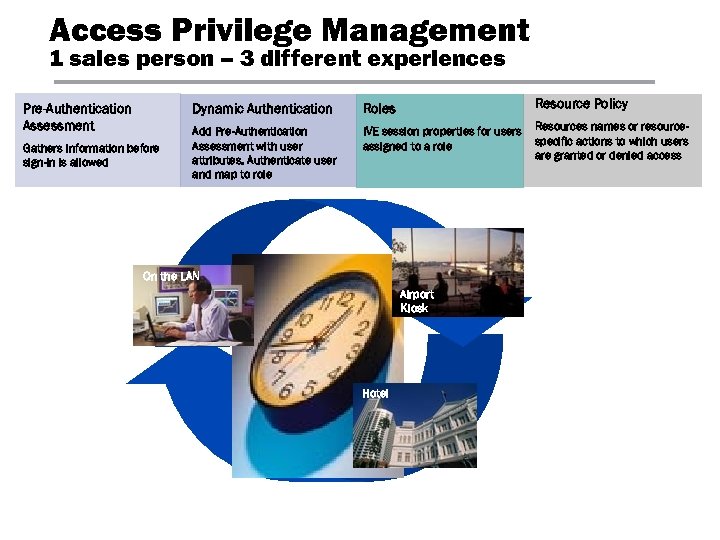
Access Privilege Management 1 sales person – 3 different experiences Dynamic Authentication Pre-Authentication Assessment Gathers information before sign-in is allowed Roles Resource Policy Add Pre-Authentication Assessment with user attributes. Authenticate user and map to role IVE session properties for users assigned to a role Resources names or resourcespecific actions to which users are granted or denied access On the LAN Airport Kiosk Hotel
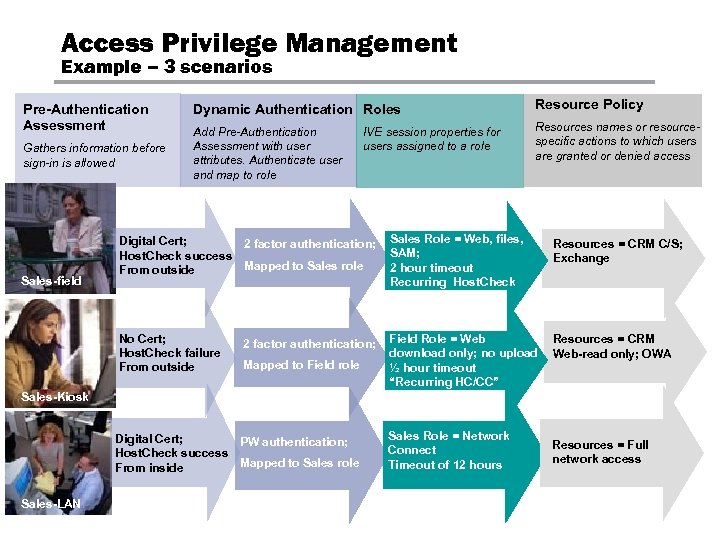
Access Privilege Management Example – 3 scenarios Pre-Authentication Assessment Gathers information before sign-in is allowed Dynamic Authentication Roles Resource Policy Add Pre-Authentication Assessment with user attributes. Authenticate user and map to role Resources names or resourcespecific actions to which users are granted or denied access IVE session properties for users assigned to a role Sales Role = Web, files, SAM; 2 hour timeout Recurring Host. Check Resources = CRM C/S; Exchange No Cert; Host. Check failure From outside Sales-field Digital Cert; 2 factor authentication; Host. Check success Mapped to Sales role From outside Field Role = Web download only; no upload ½ hour timeout “Recurring HC/CC” Resources = CRM Web-read only; OWA 2 factor authentication; Mapped to Field role Sales-Kiosk Digital Cert; PW authentication; Host. Check success Mapped to Sales role From inside Sales-LAN Sales Role = Network Connect Timeout of 12 hours Resources = Full network access
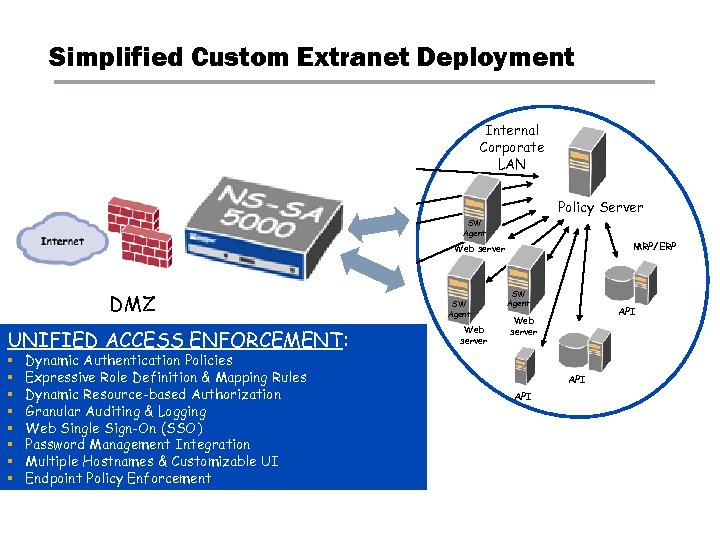
Simplified Custom Extranet Deployment SW Agent Web server SW Agent DMZ Web server SW Agent Policy Server SW Agent MRP/ERP Web server SW Agent Web UNIFIED ACCESS ENFORCEMENT: server Web SW Agent Internal Corporate LAN § Dynamic Authentication Policies server § Expressive Role Definition & Mapping Rules §Extensive Deployment Requirements: Dynamic Resource-based Authorization §§Duplication & Migration of Servers into DMZ Granular Auditing & Logging §§Harden OS/Server Farms & Ongoing Patch Maintenance Web Single Sign-On (SSO) §§Maintenance of public facing infrastructure Password Management Integration §§AAA Limitation to only Customizable UI resources Multiple Hostnames & those integrated §§Custom API development for non-Web content Endpoint Policy Enforcement API SW Agent Web server SW Agent API Web server API
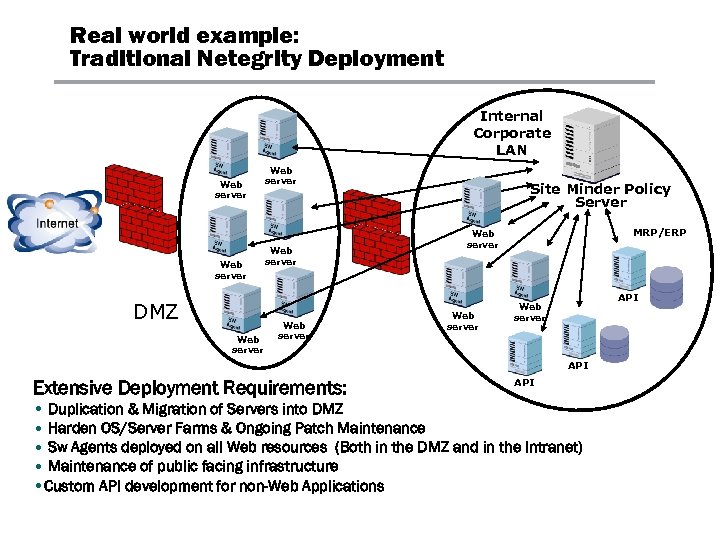
Real world example: Traditional Netegrity Deployment Internal Corporate LAN Web server DMZ Web server Site Minder Policy Server MRP/ERP Web server API Extensive Deployment Requirements: API • Duplication & Migration of Servers into DMZ • Harden OS/Server Farms & Ongoing Patch Maintenance • Sw Agents deployed on all Web resources (Both in the DMZ and in the Intranet) • Maintenance of public facing infrastructure • Custom API development for non-Web Applications
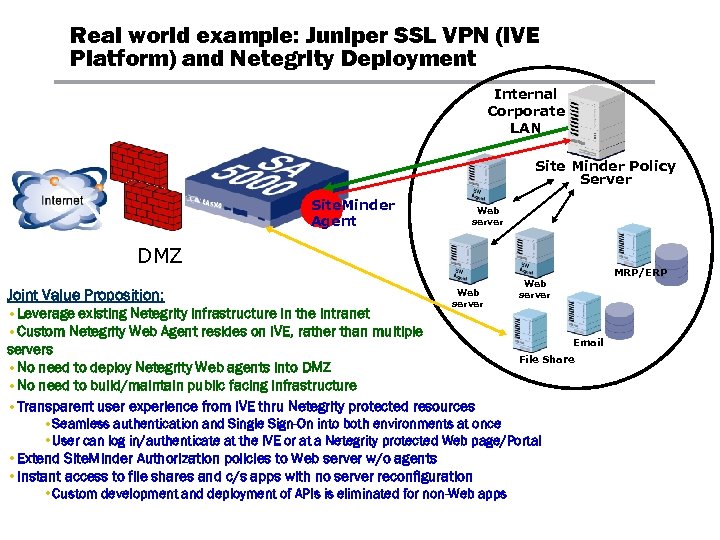
Real world example: Juniper SSL VPN (IVE Platform) and Netegrity Deployment Internal Corporate LAN Site Minder Policy Server Site. Minder Agent Web server API DMZ Joint Value Proposition: • Leverage existing Netegrity infrastructure in the intranet • Custom Netegrity Web Agent resides on IVE, rather than multiple MRP/ERP Web server Email servers File Share • No need to deploy Netegrity Web agents into DMZ • No need to build/maintain public facing infrastructure • Transparent user experience from IVE thru Netegrity protected resources • Seamless authentication and Single Sign-On into both environments at once • User can log in/authenticate at the IVE or at a Netegrity protected Web page/Portal • Extend Site. Minder Authorization policies to Web server w/o agents • Instant access to file shares and c/s apps with no server reconfiguration • Custom development and deployment of APIs is eliminated for non-Web apps
The Travel booking experience… User Autheticatation and verification
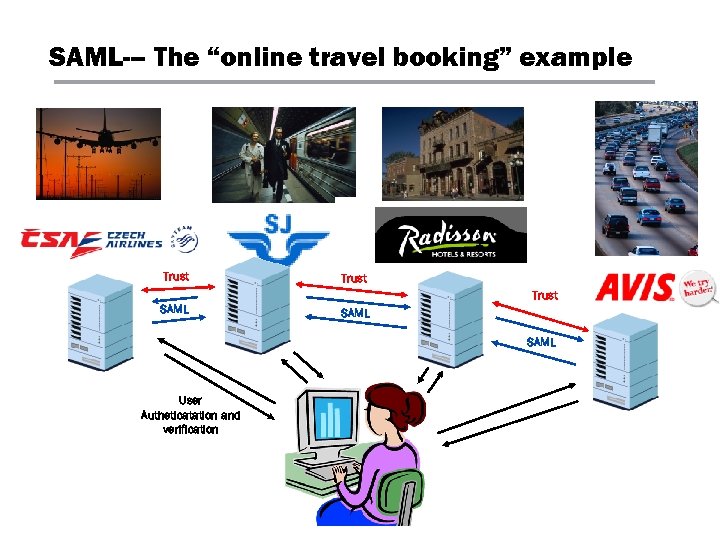
SAML-– The “online travel booking” example Trust SAML User Autheticatation and verification

SSL VPNs and SAML: SAML Background § SAML (Security Assertions Markup Language) is a common XML framework for exchanging security assertions between entities § Developed by the Security Services Technical Committee (SSTC) of the standards organization OASIS (the Organization for the Advancement of Structured Information Standards) § Broader goal: sharing auth & authz’ information across organizations – the “online travel booking” example § Current ratified standard is SAML Version 2. 0 § Defines use cases which warrant the need for a standard: most recognized of these • Web Single Sign On (SSO) • Centralized provisioning of Access Control Policies
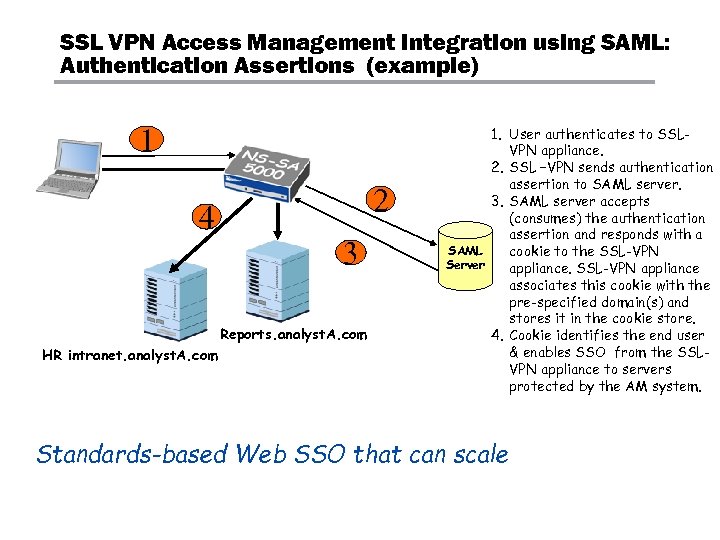
SSL VPN Access Management Integration using SAML: Authentication Assertions (example) 1 2 4 3 Reports. analyst. A. com HR intranet. analyst. A. com 1. User authenticates to SSLVPN appliance. 2. SSL –VPN sends authentication assertion to SAML server. 3. SAML server accepts (consumes) the authentication assertion and responds with a SAML cookie to the SSL-VPN Server appliance. SSL-VPN appliance associates this cookie with the pre-specified domain(s) and stores it in the cookie store. 4. Cookie identifies the end user & enables SSO from the SSLVPN appliance to servers protected by the AM system. Standards-based Web SSO that can scale
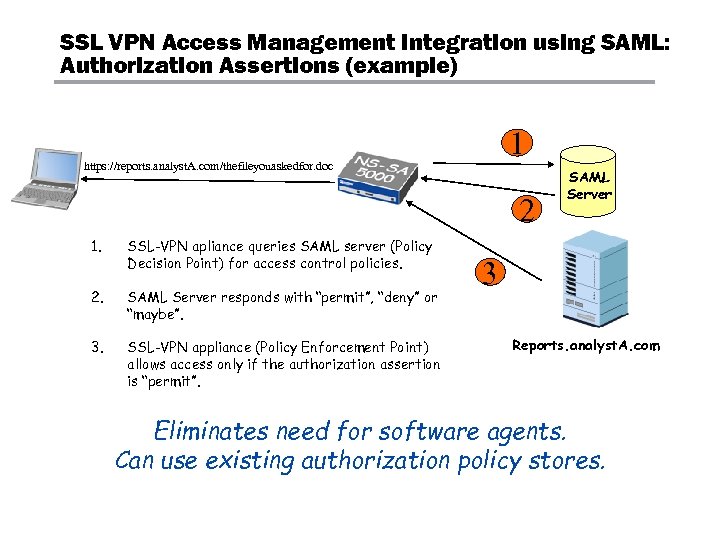
SSL VPN Access Management Integration using SAML: Authorization Assertions (example) 1 https: //reports. analyst. A. com/thefileyouaskedfor. doc 2 1. SSL-VPN apliance queries SAML server (Policy Decision Point) for access control policies. 2. SAML Server responds with “permit”, “deny” or “maybe”. 3. SSL-VPN appliance (Policy Enforcement Point) allows access only if the authorization assertion is “permit”. SAML Server 3 Reports. analyst. A. com Eliminates need for software agents. Can use existing authorization policy stores.
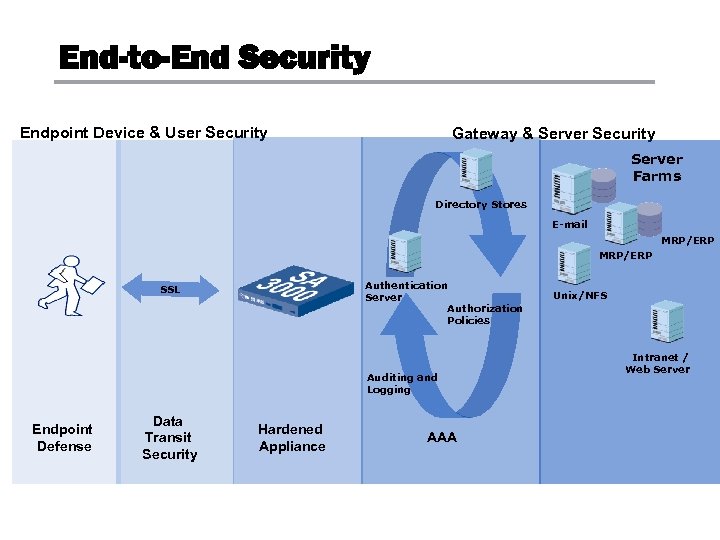
End-to-End Security Endpoint Device & User Security Gateway & Server Security Server Farms Directory Stores E-mail MRP/ERP Authentication Server Authorization Policies SSL Auditing and Logging Endpoint Defense Data Transit Security Hardened Appliance AAA Unix/NFS Intranet / Web Server
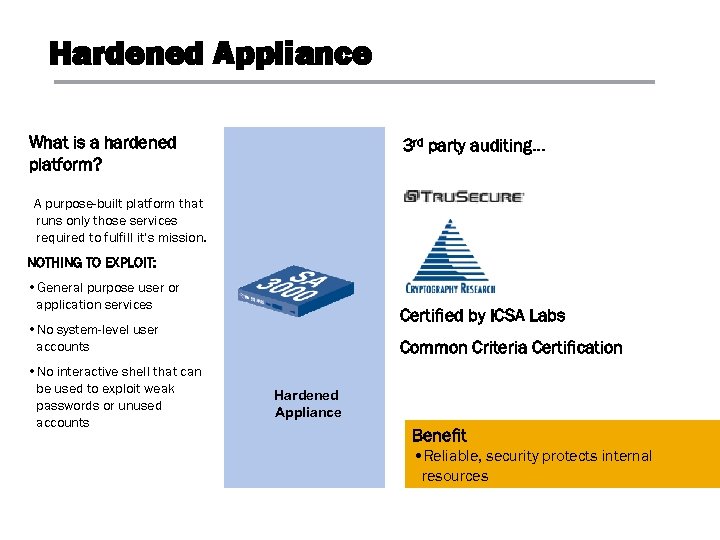
Hardened Appliance What is a hardened platform? 3 rd party auditing… A purpose-built platform that runs only those services required to fulfill it’s mission. NOTHING TO EXPLOIT: • General purpose user or application services Certified by ICSA Labs • No system-level user accounts • No interactive shell that can be used to exploit weak passwords or unused accounts Common Criteria Certification Hardened Appliance Benefit • Reliable, security protects internal resources
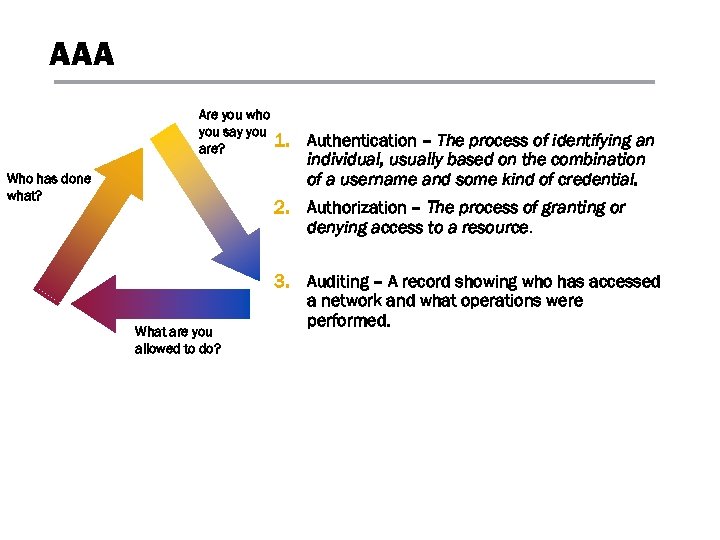
AAA Are you who you say you are? Who has done what? 1. Authentication – The process of identifying an individual, usually based on the combination of a username and some kind of credential. 2. Authorization – The process of granting or denying access to a resource. What are you allowed to do? 3. Auditing – A record showing who has accessed a network and what operations were performed.
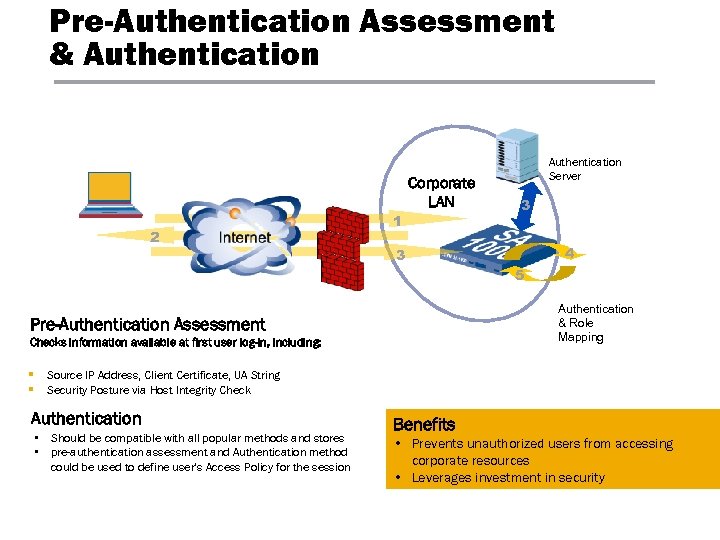
Pre-Authentication Assessment & Authentication 2 1 Corporate LAN Authentication Server 3 4 3 5 Authentication & Role Mapping Pre-Authentication Assessment Checks information available at first user log-in, including: § § Source IP Address, Client Certificate, UA String Security Posture via Host Integrity Check Authentication • Should be compatible with all popular methods and stores • pre-authentication assessment and Authentication method could be used to define user’s Access Policy for the session Benefits • Prevents unauthorized users from accessing corporate resources • Leverages investment in security
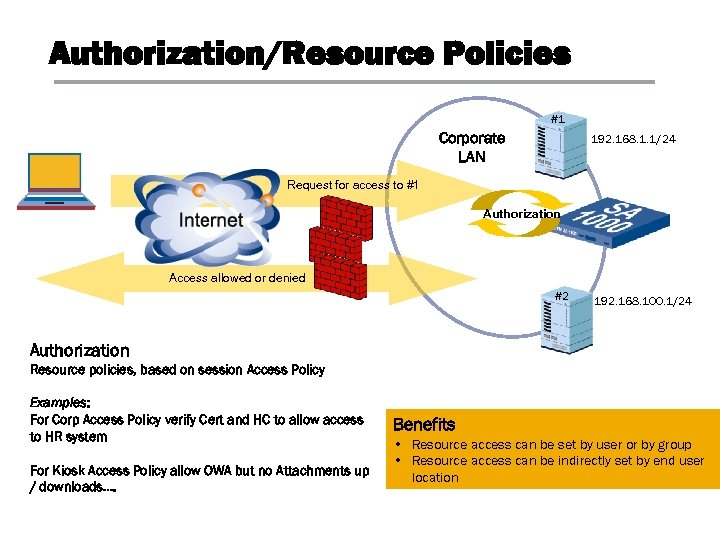
Authorization/Resource Policies #1 Corporate LAN 192. 168. 1. 1/24 Request for access to #1 Authorization Access allowed or denied #2 192. 168. 100. 1/24 Authorization Resource policies, based on session Access Policy Examples: For Corp Access Policy verify Cert and HC to allow access to HR system For Kiosk Access Policy allow OWA but no Attachments up / downloads…. Benefits • Resource access can be set by user or by group • Resource access can be indirectly set by end user location
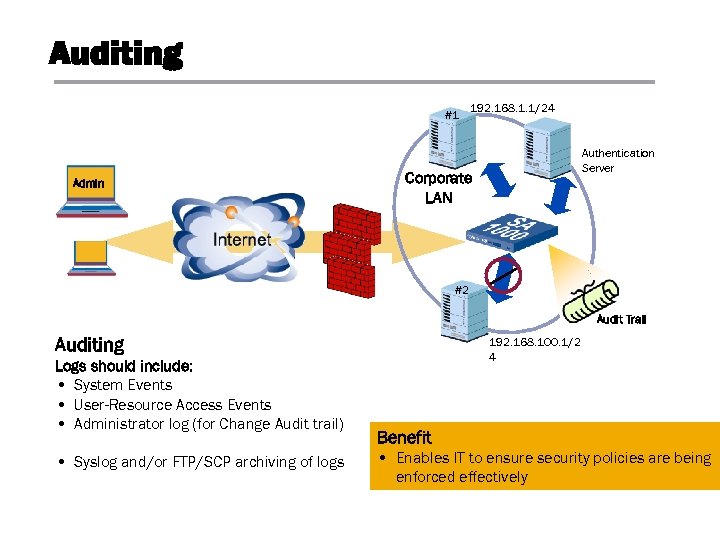
Auditing #1 Admin 192. 168. 1. 1/24 Authentication Server Corporate LAN #2 Audit Trail Auditing Logs should include: • System Events • User-Resource Access Events • Administrator log (for Change Audit trail) • Syslog and/or FTP/SCP archiving of logs 192. 168. 100. 1/2 4 Benefit • Enables IT to ensure security policies are being enforced effectively

Questions ? Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net

Tack !! Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net
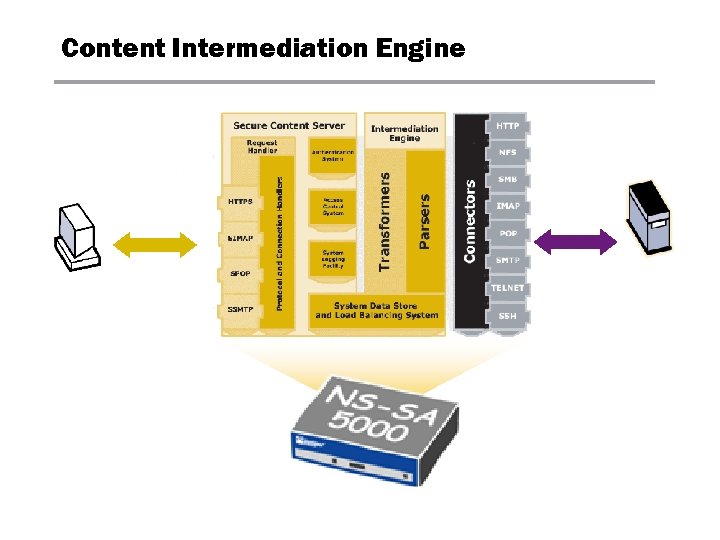
Content Intermediation Engine
8514192c5755784160598949d37cdffa.ppt