eaff7d67880bb3f9abe64f48e8a5321e.ppt
- Количество слайдов: 20
 SSL / TLS in ITDS Arun Vishwanathan 23 rd Dec 2003
SSL / TLS in ITDS Arun Vishwanathan 23 rd Dec 2003
 Agenda Introduction to SSL/TLS Digital Certificates How SSL works SSL/TLS differences SSL/TLS jargon in ITDS Security in ITDS using SSL/TLS ldapsearch with SSL demystified Pointers and References
Agenda Introduction to SSL/TLS Digital Certificates How SSL works SSL/TLS differences SSL/TLS jargon in ITDS Security in ITDS using SSL/TLS ldapsearch with SSL demystified Pointers and References
 Introduction to SSL/TLS The Problem TCP/IP protocol does not provide any security. Any transactions have to be made over an insecure network by default. Everything that passes between server and client may be eavesdropped, altered and modified. The security problems have become the number one obstacle for expansion of Web.
Introduction to SSL/TLS The Problem TCP/IP protocol does not provide any security. Any transactions have to be made over an insecure network by default. Everything that passes between server and client may be eavesdropped, altered and modified. The security problems have become the number one obstacle for expansion of Web.
 Introduction cont… The Solution SSL and TLS can layer on top of any transport protocol, they are not TCP/IP dependant, and can run under application protocols such as HTTP, FTP and TELNET etc. Both SSL and TSL provide authentication, confidentiality and integrity. They give protection against message tampering, eavesdropping and spoofing. We can thus achieve secure communication over an insecure protocol in an application independent way.
Introduction cont… The Solution SSL and TLS can layer on top of any transport protocol, they are not TCP/IP dependant, and can run under application protocols such as HTTP, FTP and TELNET etc. Both SSL and TSL provide authentication, confidentiality and integrity. They give protection against message tampering, eavesdropping and spoofing. We can thus achieve secure communication over an insecure protocol in an application independent way.
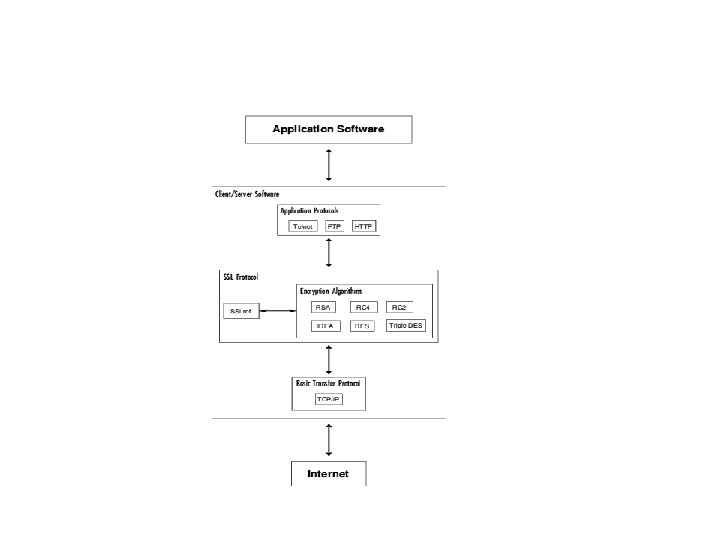 SSL/TLS on the Stack
SSL/TLS on the Stack
 Digital Certificates (Quick Detour) Digital certificates allow unique identification of an entity; they are, in essence, electronic ID cards issued by trusted parties. Digital certificates allow a user to verify to whom a certificate is issued as well as the issuer of the certificate. Digital certificates are the vehicle that SSL uses for public-key cryptography. A digital certificate serves two purposes: it establishes the owner’s identity, it makes the owner’s public key available. A digital certificate is issued by a trusted authority—a certificate authority (CA)—and it is issued only for a limited time.
Digital Certificates (Quick Detour) Digital certificates allow unique identification of an entity; they are, in essence, electronic ID cards issued by trusted parties. Digital certificates allow a user to verify to whom a certificate is issued as well as the issuer of the certificate. Digital certificates are the vehicle that SSL uses for public-key cryptography. A digital certificate serves two purposes: it establishes the owner’s identity, it makes the owner’s public key available. A digital certificate is issued by a trusted authority—a certificate authority (CA)—and it is issued only for a limited time.
 Format of Digital Certificates The digital certificate contains specific pieces of information about the identity of the certificate owner and about the certificate authority: Owner’s distinguished name. Owner’s public key. Date the digital certificate was issued. Date the digital certificate expires. Issuer’s distinguished name. This is the distinguished name of the CA. Issuer’s digital signature.
Format of Digital Certificates The digital certificate contains specific pieces of information about the identity of the certificate owner and about the certificate authority: Owner’s distinguished name. Owner’s public key. Date the digital certificate was issued. Date the digital certificate expires. Issuer’s distinguished name. This is the distinguished name of the CA. Issuer’s digital signature.
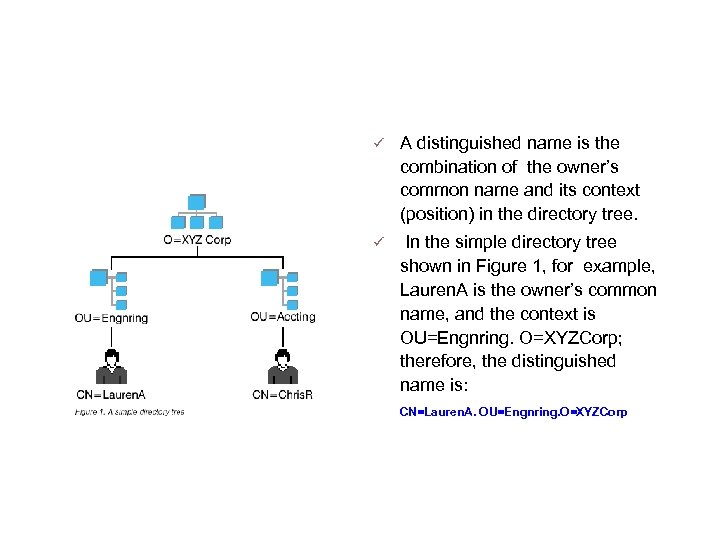 Distinguished Names A distinguished name is the combination of the owner’s common name and its context (position) in the directory tree. In the simple directory tree shown in Figure 1, for example, Lauren. A is the owner’s common name, and the context is OU=Engnring. O=XYZCorp; therefore, the distinguished name is: CN=Lauren. A. OU=Engnring. O=XYZCorp
Distinguished Names A distinguished name is the combination of the owner’s common name and its context (position) in the directory tree. In the simple directory tree shown in Figure 1, for example, Lauren. A is the owner’s common name, and the context is OU=Engnring. O=XYZCorp; therefore, the distinguished name is: CN=Lauren. A. OU=Engnring. O=XYZCorp
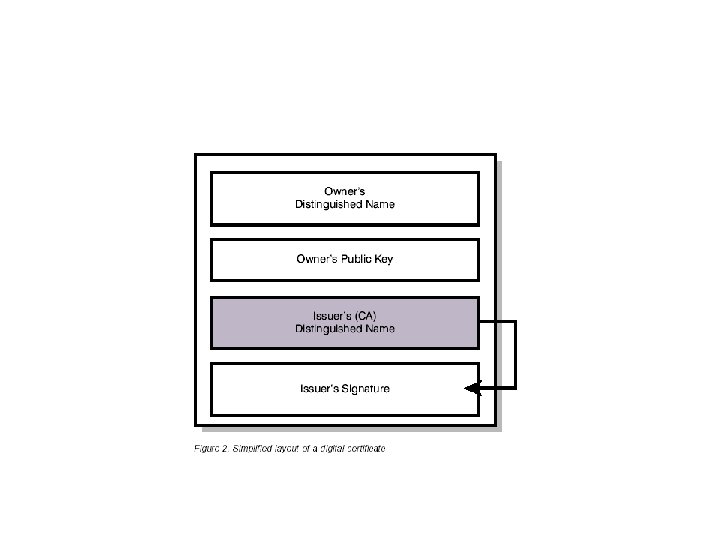 Simple Layout of a digital Certificate
Simple Layout of a digital Certificate
 How SSL works SSL is a protocol that provides privacy and integrity between two communicating applications using TCP/IP. The data going back and forth between client and server is encrypted using a symmetric algorithm such as DES or RC 4. A public-key algorithm—usually RSA—is used for the exchange of the encryption keys and for digital signatures. The algorithm uses the public key in the server’s digital certificate.
How SSL works SSL is a protocol that provides privacy and integrity between two communicating applications using TCP/IP. The data going back and forth between client and server is encrypted using a symmetric algorithm such as DES or RC 4. A public-key algorithm—usually RSA—is used for the exchange of the encryption keys and for digital signatures. The algorithm uses the public key in the server’s digital certificate.
 The four principles of Security Confidentiality (privacy) Authentication (who created or sent the data) Integrity (has not been altered) Non-repudiation (the order is final) We will see how SSL achieves all of these !!!
The four principles of Security Confidentiality (privacy) Authentication (who created or sent the data) Integrity (has not been altered) Non-repudiation (the order is final) We will see how SSL achieves all of these !!!
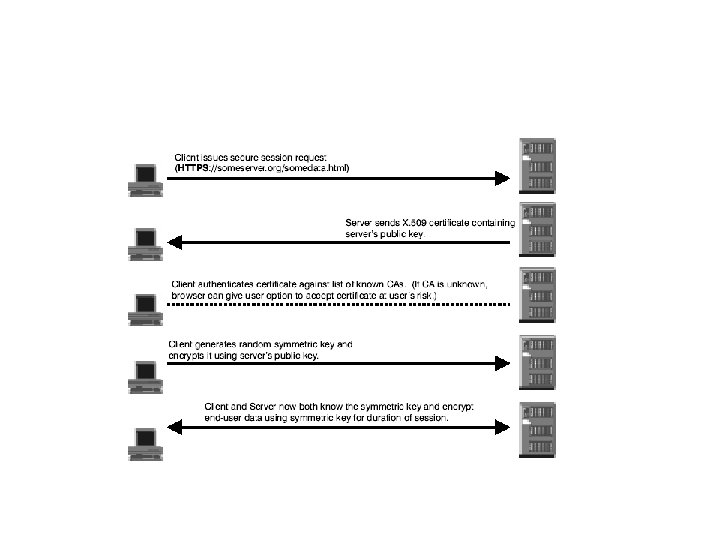 A Simple SSL session
A Simple SSL session
 The details (Step 1) Step 1 Client sends a client “hello” message with the version of SSL. the cipher suites supported by the client. the data compression methods supported by the client. a 28 -byte random number.
The details (Step 1) Step 1 Client sends a client “hello” message with the version of SSL. the cipher suites supported by the client. the data compression methods supported by the client. a 28 -byte random number.
 Details Cont. . (Step 2) Step 2 The server responds with a server “hello” message that contains the cryptographic method (cipher suite) the data compression method selected by the server the session ID another random number.
Details Cont. . (Step 2) Step 2 The server responds with a server “hello” message that contains the cryptographic method (cipher suite) the data compression method selected by the server the session ID another random number.
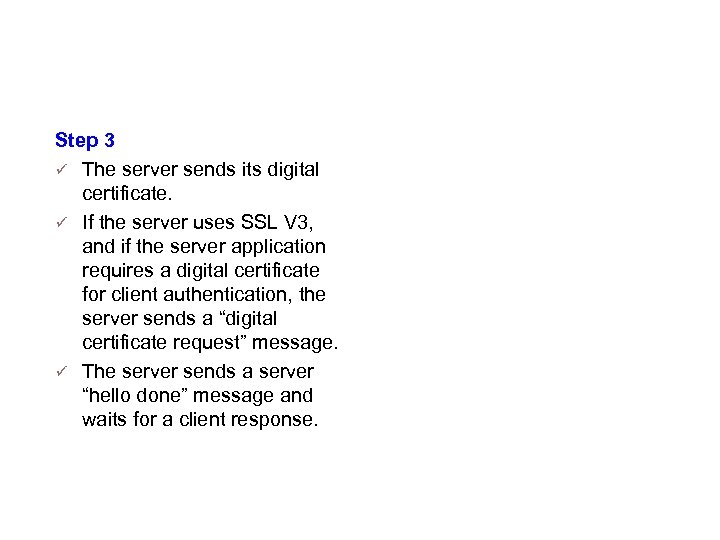 Details (Step 3) Step 3 The server sends its digital certificate. If the server uses SSL V 3, and if the server application requires a digital certificate for client authentication, the server sends a “digital certificate request” message. The server sends a server “hello done” message and waits for a client response.
Details (Step 3) Step 3 The server sends its digital certificate. If the server uses SSL V 3, and if the server application requires a digital certificate for client authentication, the server sends a “digital certificate request” message. The server sends a server “hello done” message and waits for a client response.
 Details Cont… (Step 4) Step 4 Upon receipt of the server “hello done” message, the client verifies the validity of the server’s digital certificate and checks that the server’s “hello” parameters are acceptable. If the server requested a client digital certificate, the client sends a digital certificate, or if no suitable digital certificate is available, the client sends a “no digital certificate” alert.
Details Cont… (Step 4) Step 4 Upon receipt of the server “hello done” message, the client verifies the validity of the server’s digital certificate and checks that the server’s “hello” parameters are acceptable. If the server requested a client digital certificate, the client sends a digital certificate, or if no suitable digital certificate is available, the client sends a “no digital certificate” alert.
 Details Cont … (Step 5) Step 5 The client sends a “client key exchange” message. This message contains the pre-master secret, a 46 -byte random number used in the generation of the symmetric encryption keys the message authentication code (MAC) keys, This is encrypted with the public key of the server.
Details Cont … (Step 5) Step 5 The client sends a “client key exchange” message. This message contains the pre-master secret, a 46 -byte random number used in the generation of the symmetric encryption keys the message authentication code (MAC) keys, This is encrypted with the public key of the server.
 Details Cont …. (Step 5 cont) Step 5 cont… If the client sent a digital certificate to the server, the client sends a “digital certificate verify” message signed with the client’s private key. By verifying the signature of this message, the server can explicitly verify the ownership of the client digital certificate.
Details Cont …. (Step 5 cont) Step 5 cont… If the client sent a digital certificate to the server, the client sends a “digital certificate verify” message signed with the client’s private key. By verifying the signature of this message, the server can explicitly verify the ownership of the client digital certificate.
 Details Cont … (Step 6) Step 6 The client uses a series of cryptographic operations to convert the pre-master secret into a master secret, from which all key material required for encryption and message authentication is derived. Then the client sends a “change cipher spec” message to make the server switch to the newly negotiated cipher suite.
Details Cont … (Step 6) Step 6 The client uses a series of cryptographic operations to convert the pre-master secret into a master secret, from which all key material required for encryption and message authentication is derived. Then the client sends a “change cipher spec” message to make the server switch to the newly negotiated cipher suite.
 Details … (Step 7) Step 7 The next message sent by the client (the “finished” message) is the first message encrypted with this cipher method and keys The server responds with a “change cipher spec” and a “finished” message of its own. The SSL handshake ends, and encrypted application data can be sent.
Details … (Step 7) Step 7 The next message sent by the client (the “finished” message) is the first message encrypted with this cipher method and keys The server responds with a “change cipher spec” and a “finished” message of its own. The SSL handshake ends, and encrypted application data can be sent.


