86d15642604193ea930071f418b12bef.ppt
- Количество слайдов: 36

SQL Server Database Forensics Kevvie Fowler, GCFA Gold, CISSP, MCTS, MCDBA, MCSD, MCSE Sector, 2007

SQL Server Forensics | Why are Databases Critical Assets? n Why are databases critical assets? n Databases hold critical information n Industry trends are scaling in versus out n Database servers today hold more sensitive information than ever before n Data security legislations & regulations dictate that security breaches must be reported n The Canadian Internet Policy and Public Interest Clinic (CIPPIC) is calling for a data security breach notification law in Canada n Database security breaches are “Front Page” news n TJ Maxx | 45. 7 million credit/debit cards disclosed n Card. Systems Solutions | 200, 000 credit/debit cards disclosed 2
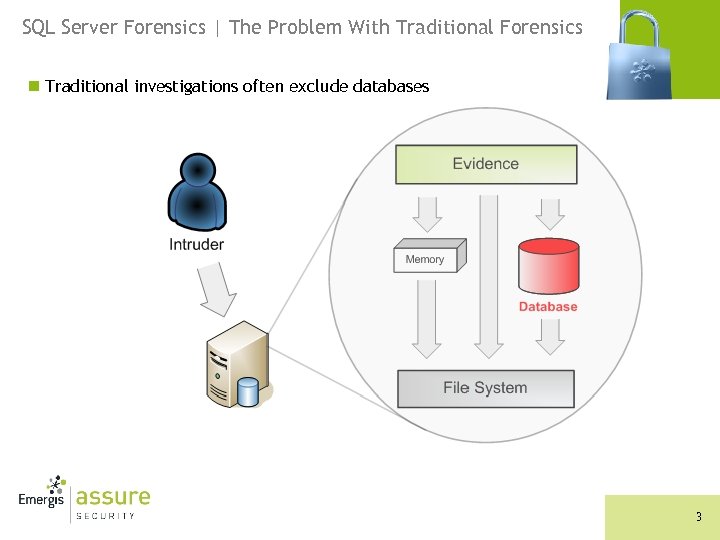
SQL Server Forensics | The Problem With Traditional Forensics n Traditional investigations often exclude databases 3

SQL Server Forensics | The Solution n Database Forensics Directly focuses on the identification, preservation and analysis of database data Benefits n Retrace user DML & DDL operations n Identify data pre and post transaction n Recover previously deleted data rows n Can help prove/disprove the occurrence of a data security breach n Can determine the scope of a database intrusion n For the “real world”: No dependency on 3 rd party auditing tools or pre-configured DML or DDL triggers 4
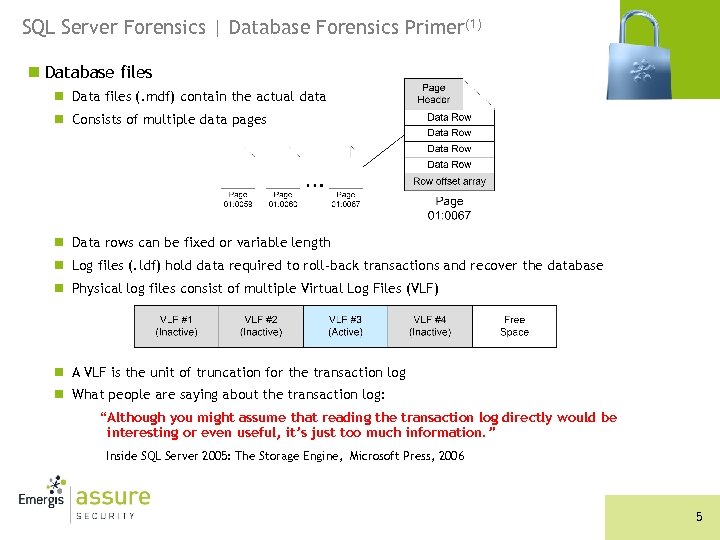
SQL Server Forensics | Database Forensics Primer(1) n Database files n Data files (. mdf) contain the actual data n Consists of multiple data pages n Data rows can be fixed or variable length n Log files (. ldf) hold data required to roll-back transactions and recover the database n Physical log files consist of multiple Virtual Log Files (VLF) n A VLF is the unit of truncation for the transaction log n What people are saying about the transaction log: “Although you might assume that reading the transaction log directly would be interesting or even useful, it’s just too much information. ” Inside SQL Server 2005: The Storage Engine, Microsoft Press, 2006 5
SQL Server Forensics | Database Forensics Primer(2) Inside the transaction log: 1. Current. LSN 25. CHKPT End DB Version 50. Savepoint Name 76. Meta Status 2. Operation 26. Minimum LSN 51. Rowbits First Bit 77. File Status 3. Context 27. Dirty Pages 52. Rowbits Bit Count 78. File ID 4. Transaction ID 28. Oldest Replicated Begin LSN 53. Rowbits Bit Value 79. Physical Name 5. Tag Bits 29. Next Replicated End LSN 54. Number of Locks 80. Logical Name 6. Log Record Fixed Length 30. Last Distributed End LSN 55. Lock Information 81. Format LSN 7. Log Record Length 31. Server UID 56. LSN Before Writes 82. Rowset. ID 8. Previous. LSN 32. UID 57. Pages Written 83. Text. Ptr 9. Flag Bits 33. SPID 58. Data Pages Delta 84. Column Offset 10. Log Reserve 34. Begin. Log Status 59. Reserved Pages Delta 85. Flags 11. Alloc. Unit. ID 35. Xact Type 60. Used Pages Delta 86. Text Size 12. Alloc. Unit. Name 36. Begin Time 61. Data Rows Delta 87. Offset 13. Page ID 37. Transaction Name 62. Command Type 88. Old Size 14. Slot ID 38. Transaction SID 63. Publication ID 89. New Size 15. Previous Page LSN 39. End Time 64. Article ID 90. Description 16. Partion. ID 40. Transaction Begin 65. Partial Status 91. Bulk allocated extent count 17. Row. Flags 41. Replicated Records 66. Command 92. Bulk rowinsert. ID 18. Num Elements 42. Oldest Active LSN 67. Byte Offset 93. Bulk allocationunit. ID 19. Offset in Row 43. Server Name 68. New Value 94. Bulk allocation first IAM Page ID 20. Checkpoint Begin 44. Database Name 69. Old Value 95. Bulk allocated extent ids 21. CHKPT Begin DB Version 45. Mark Name 70. New Split Page 96. Row. Log Contents 0 22. Max. XDESID 46. Master XDESID 71. Rows Deleted 97. Row. Log Contents 1 23. Num Transactions 47. Master DBID 72. Bytes Freed 98. Row. Log Contents 2 24. Checkpoint End 48. Prep. Log. Begin LSN 73. CI Table ID 99. Row. Log Contents 3 49. Prepare. Time 74. CI Index ID 100. Rowlog Contents 4 50. Virtual Clock 75. FIlegroup ID 101. Log Record 51. Previous Savepoint 6
SQL Server Forensics | Database Forensics Primer(3) n Server Process ID (SPID) n A unique value used by SQL Server to track a given session within the database server n Transaction log activity is logged against the executing SPID n Data type storage and retrieval n 31 different data types n Data types are stored and retrieved differently within SQL Server n Little-endian ordering (LEO) is applicable to selected data types n Storing and retrieving value: 21976 in various data types results in the following: Procedure Cache n Contains ad-hoc and parameterized statements 7
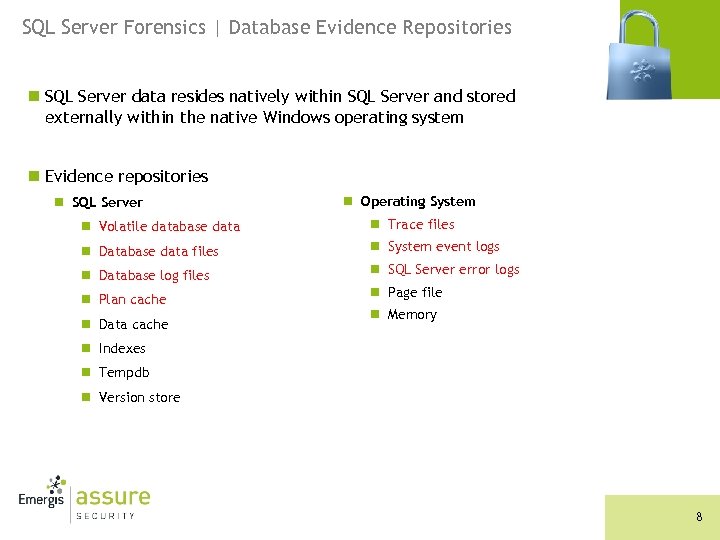
SQL Server Forensics | Database Evidence Repositories n SQL Server data resides natively within SQL Server and stored externally within the native Windows operating system n Evidence repositories n SQL Server n Operating System n Volatile database data n Trace files n Database data files n System event logs n Database log files n SQL Server error logs n Plan cache n Data cache n Page file n Memory n Indexes n Tempdb n Version store 8

SQL Server Forensics | Investigation Tools n SQL Server Management Studio Express n SQLCMD n Windows Forensic Toolchest n DDDCFLDD n MD 5 SUM n NetcatCrypt. Cat n Win. Hex n Native SQL Server DMO’s and statements n Dynamic Management Views (DMV) n Database Consistency Checker (DBCC) commands n FN_* 9

SQL Server Forensics | Evidence Collection(1) Evidence Collection 10

SQL Server Forensics | Evidence Collection(2) n Determine the scope of evidence collection n Prioritize evidence collection 1. Volatile database data (sessions/connections, active requests, active users, memory, etc. ) 2. Transaction logs 3. Database files 4. SQL Server error logs 5. System event logs 6. Trace files 11
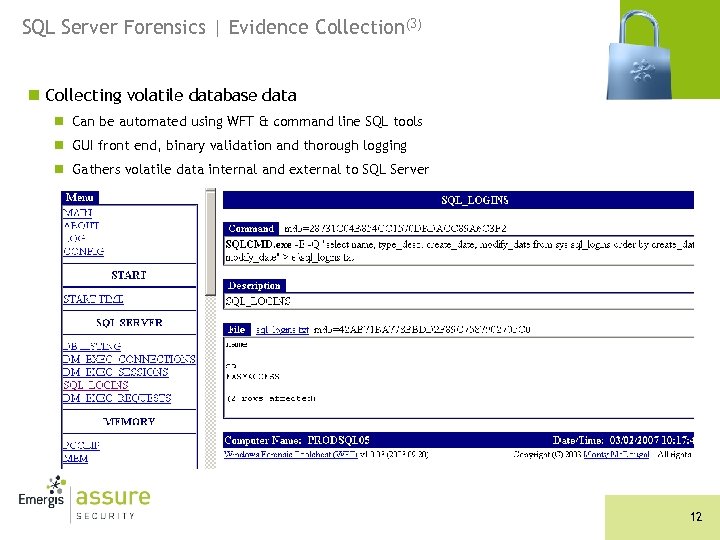
SQL Server Forensics | Evidence Collection(3) n Collecting volatile database data n Can be automated using WFT & command line SQL tools n GUI front end, binary validation and thorough logging n Gathers volatile data internal and external to SQL Server 12
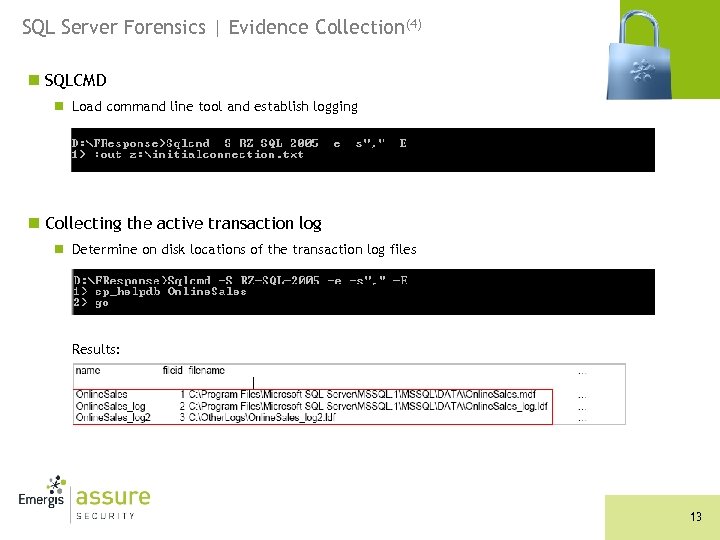
SQL Server Forensics | Evidence Collection(4) n SQLCMD n Load command line tool and establish logging n Collecting the active transaction log n Determine on disk locations of the transaction log files Results: 13
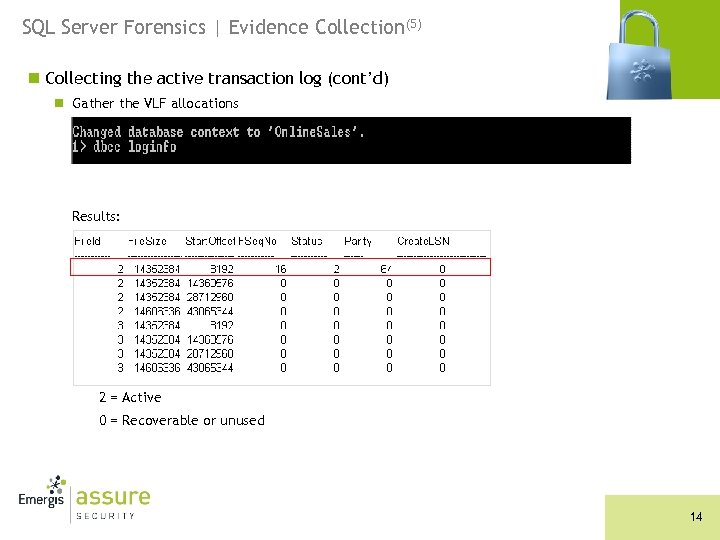
SQL Server Forensics | Evidence Collection(5) n Collecting the active transaction log (cont’d) n Gather the VLF allocations Results: 2 = Active 0 = Recoverable or unused 14

SQL Server Forensics | Evidence Collection(6) n Collecting the active transaction log (cont’d) n Fn_dblog filters transactions by: n Target database object n Specific columns n SPID and/or date/time range Select * from : : fn_dblog(NULL, NULL) n DBCC Log n More resource intensive n Dumps transaction log in its entirety dbcc log(<databasename>, 3) 0 = minimal info 1 = slightly more info 2 = detailed info including (page id, slot id, etc. ) 3 = full information about each operation 4 = full information on each operation in addition to hex dump of current data row 15
SQL Server Forensics | Evidence Collection(7) n Collecting the database plan cache n Collecting the plan cache select * from sys. dm_exec_cached_plans cross apply sys. dm_exec_sql_text(plan_handle) n Collect additional plan cache specifics - select * from sys. dm_exec_query_stats - select * from sys. dm_exec_cached_plans cross apply sys. dm_exec_plan_attributes(plan_handle) n Collecting database data files & logs (\Microsoft SQL ServerMSSQL. 1MSSQLDATA) n Collecting default trace files (\Microsoft SQL ServerMSSQL. 1MSSQLLOG) n Collecting SQL Server error logs (\Microsoft SQL ServerMSSQL. 1MSSQLLOG) n Collecting system event log (WFT) 16

SQL Server Forensics | Evidence Analysis(1) Evidence Analysis 17
SQL Server Forensics | Evidence Analysis(2) n Windows event log n SQL Server authentication data (failures, successful log-on/off) n SQL Server startup and shutdown n IP addresses of SQL Server client connections n Error log n SQL Server authentication data (failures, successful log-on/off) n SQL Server startup and shutdown n IP addresses of SQL Server client connections 18
SQL Server Forensics | Evidence Analysis(3) n Default database trace n Complete authentication history n DDL operations (schema changes) n IP addresses of SQL Server client connections 19

SQL Server Forensics | Evidence Analysis(4) n Data files & log files n Attach files n Use to obtain on-demand schema info, data page contents, etc. n Active transaction log n Import into Excel / Access for viewing n Identify DML & DDL statements n Map transactions to a SPID 20
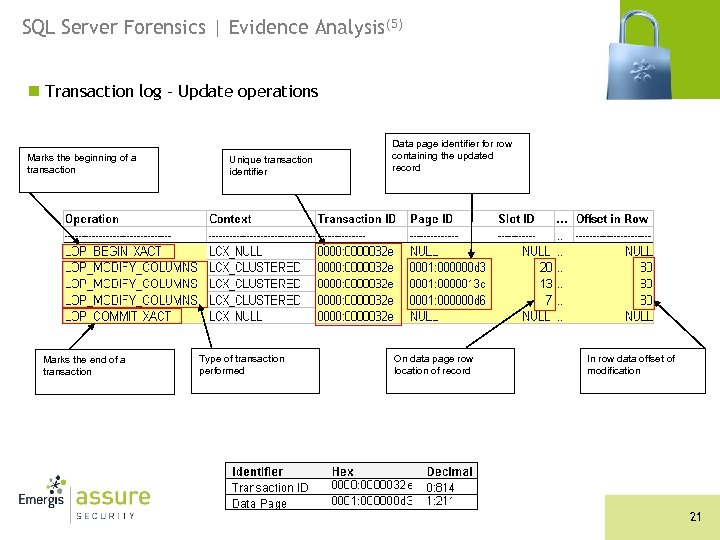
SQL Server Forensics | Evidence Analysis(5) n Transaction log – Update operations Marks the beginning of a transaction Marks the end of a transaction Unique transaction identifier Type of transaction performed Data page identifier for row containing the updated record On data page row location of record In row data offset of modification 21
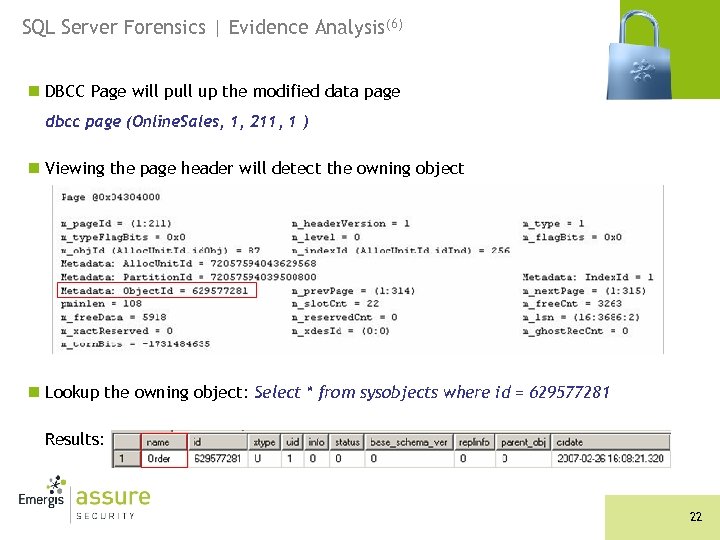
SQL Server Forensics | Evidence Analysis(6) n DBCC Page will pull up the modified data page dbcc page (Online. Sales, 1, 211, 1 ) n Viewing the page header will detect the owning object n Lookup the owning object: Select * from sysobjects where id = 629577281 Results: 22
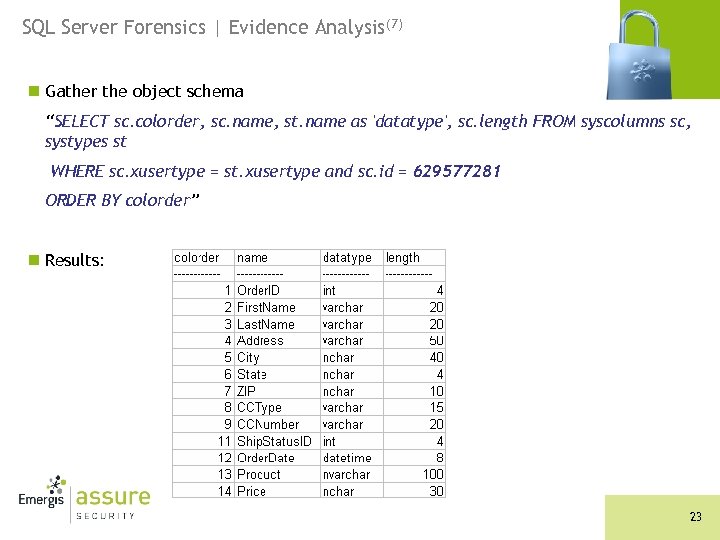
SQL Server Forensics | Evidence Analysis(7) n Gather the object schema “SELECT sc. colorder, sc. name, st. name as 'datatype', sc. length FROM syscolumns sc, systypes st WHERE sc. xusertype = st. xusertype and sc. id = 629577281 ORDER BY colorder” n Results: 23
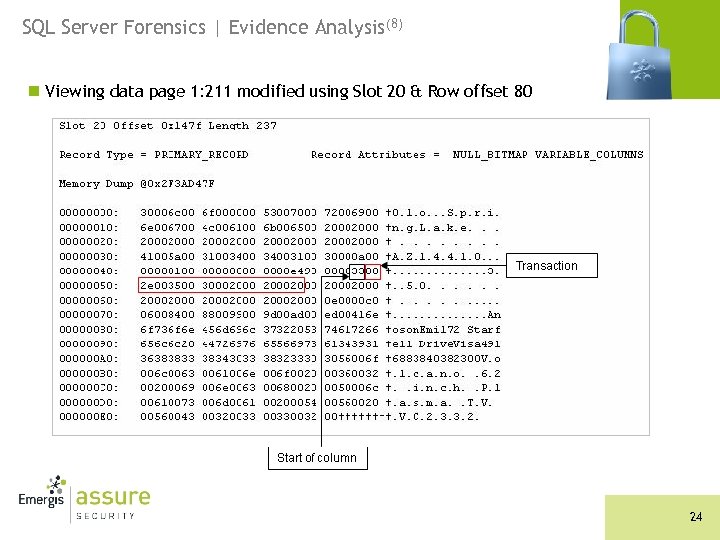
SQL Server Forensics | Evidence Analysis(8) n Viewing data page 1: 211 modified using Slot 20 & Row offset 80 24
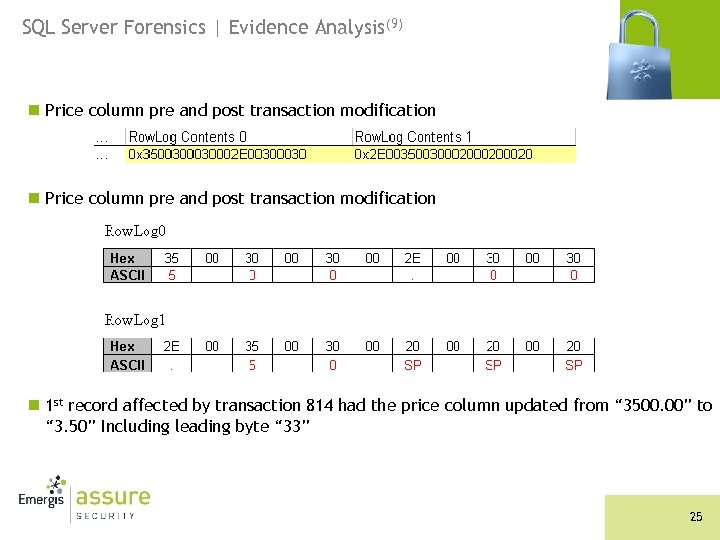
SQL Server Forensics | Evidence Analysis(9) n Price column pre and post transaction modification n 1 st record affected by transaction 814 had the price column updated from “ 3500. 00” to “ 3. 50” Including leading byte “ 33” 25
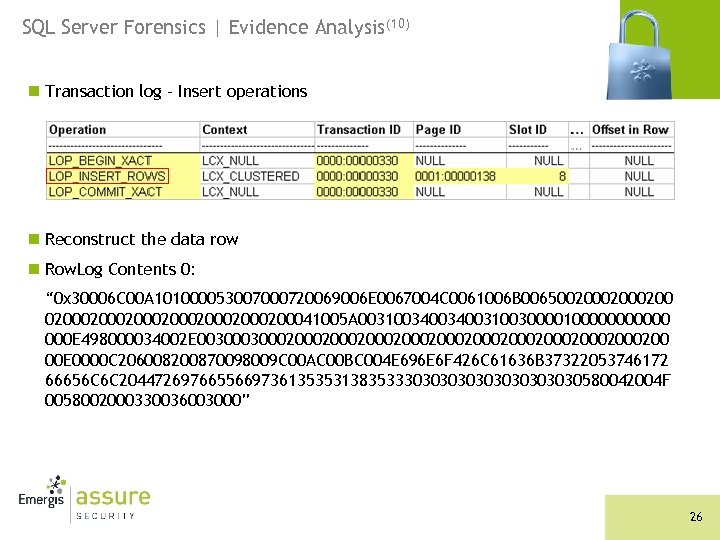
SQL Server Forensics | Evidence Analysis(10) n Transaction log - Insert operations n Reconstruct the data row n Row. Log Contents 0: “ 0 x 30006 C 00 A 101000053007000720069006 E 0067004 C 0061006 B 006500200020002000200041005 A 00310034003100300001000000 000 E 498000034002 E 00300020002000200020002000200 00 E 0000 C 206008200870098009 C 00 AC 00 BC 004 E 696 E 6 F 426 C 61636 B 37322053746172 66656 C 6 C 204472697665566973613535313835333030303030580042004 F 0058002000330036003000” 26
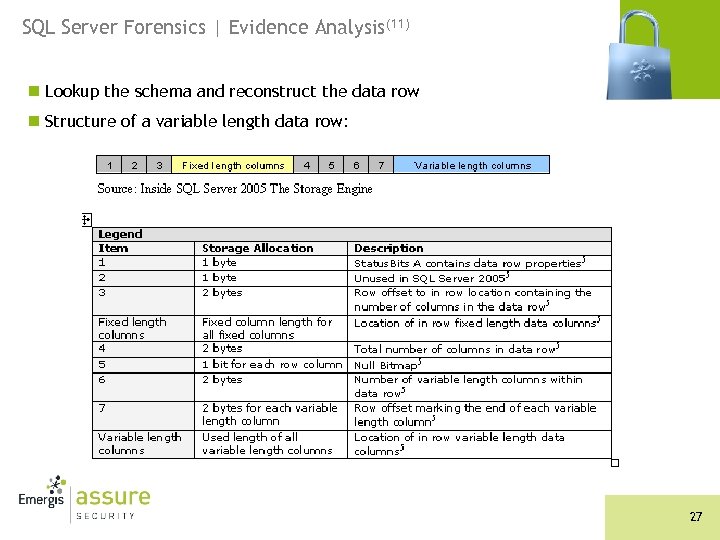
SQL Server Forensics | Evidence Analysis(11) n Lookup the schema and reconstruct the data row n Structure of a variable length data row: 27
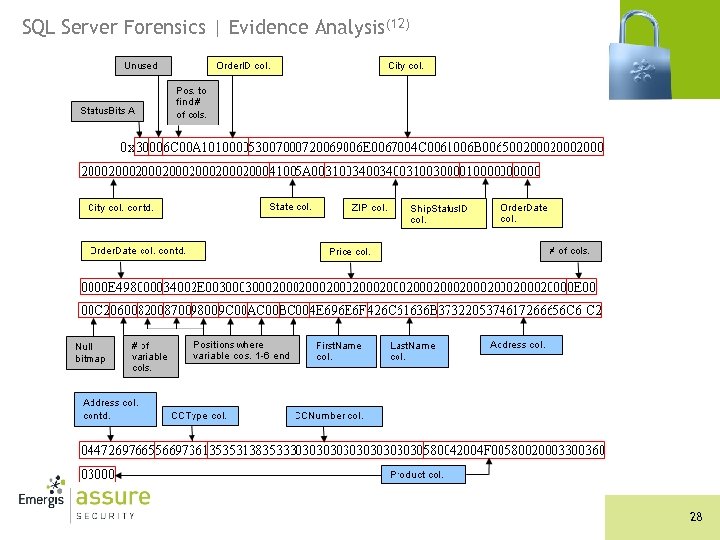
SQL Server Forensics | Evidence Analysis(12) 28

SQL Server Forensics | Evidence Analysis(13) n Swap the bytes (endian ordering) n Translate data types n The inserted record was: n Order. ID: 4122 n First. Name: Nino n Last. Name: Black n Address: 72 Starfell Drive n City: Spring. Lake n State: AZ n ZIP: 14410 n CCType: Visa n CCNumber: 55185300000 n Ship. Status. ID: 1 n Order. Date: March 1 st, 2007 n Product: XBOX 360 n Price: 4. 00 29
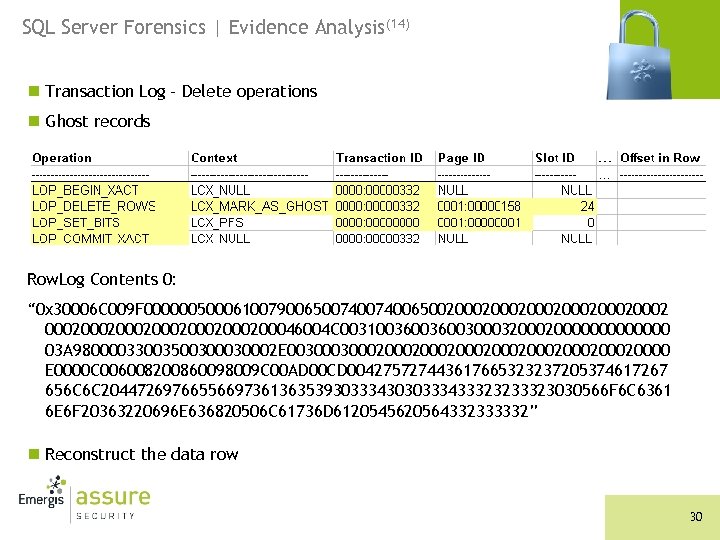
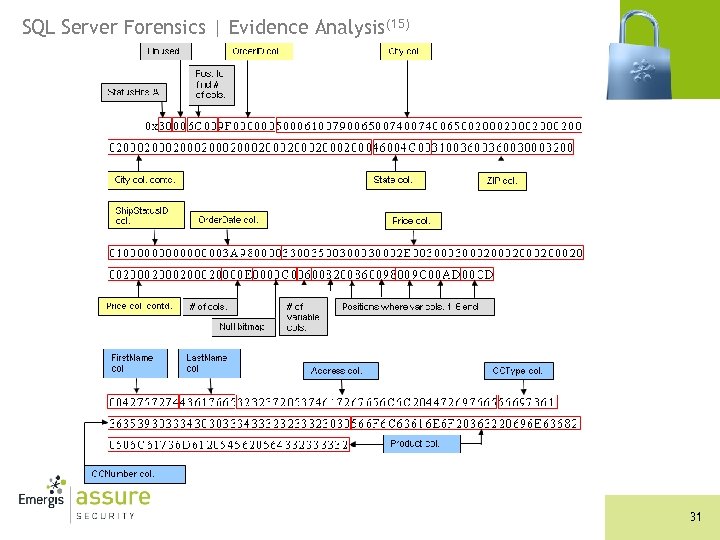
SQL Server Forensics | Evidence Analysis(14) n Transaction Log – Delete operations n Ghost records Row. Log Contents 0: “ 0 x 30006 C 009 F 000000500061007900650074006500200020002000200046004 C 003100360030003200000000 03 A 9800003300350030002 E 00300020002000200020000 E 0000 C 006008200860098009 C 00 AD 00 CD 004275727443617665323237205374617267 656 C 6 C 204472697665566973613635393033343030333433323233323030566 F 6 C 6361 6 E 6 F 20363220696 E 636820506 C 61736 D 6120545620564332333332” n Reconstruct the data row 30
SQL Server Forensics | Evidence Analysis(15) 31

SQL Server Forensics | Evidence Analysis(16) n Swap the bytes (endian ordering) n Translate data types n The deleted record was: n Order. ID: 159 n First. Name: Burt n Last. Name: Cave n Address: 227 Stargell Drive n City: Payette n State: FL n ZIP: 16602 n CCType: Visa n CCNumber: 65903400343223200 n Ship. Status. ID: 1 n Order. Date: September 12 th, 2006 n Product: Volcano 62 inch Plasma TV VC 2332 n Price: 3500. 00 32
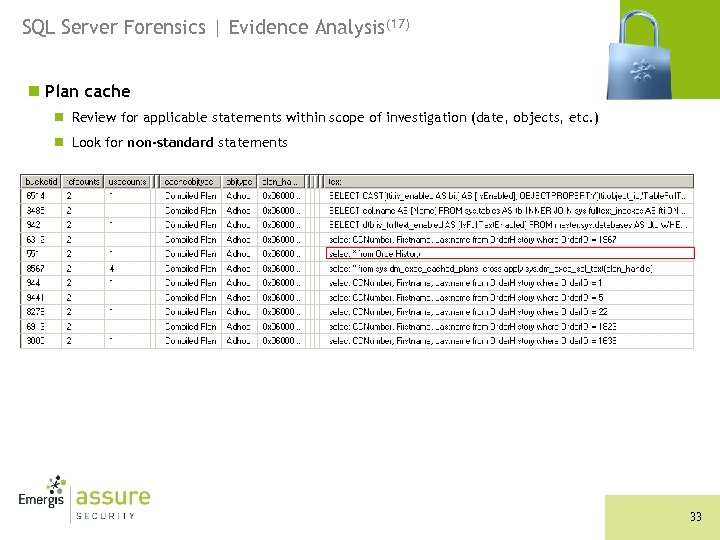
SQL Server Forensics | Evidence Analysis(17) n Plan cache n Review for applicable statements within scope of investigation (date, objects, etc. ) n Look for non-standard statements 33

SQL Server Forensics | Conclusion(1) Conclusion 34

SQL Server Forensics | Conclusion(2) n Conclusion n Don’t ignore the database when conducting computer forensics investigations n Database forensics techniques learned today can augment traditional forensics skills to uncover the data needed to support your case n SQL Server Forensic Analysis, Addison-Wesley Professional n “Rough cut” to release December 2007 | ISBN: 0321544374 n Final version to release Q 4, 2008 | ISBN: 0321544366 35

SQL Server Forensics | Questions ? ? ? 36
86d15642604193ea930071f418b12bef.ppt