8ae53fc91a9e44fd323373cd039a1b09.ppt
- Количество слайдов: 37
 Spycraft: Keeping your sources safe STEVE DOIG CRONKITE SCHOOL OF JOURNALISM ARIZONA STATE UNIVERSITY
Spycraft: Keeping your sources safe STEVE DOIG CRONKITE SCHOOL OF JOURNALISM ARIZONA STATE UNIVERSITY
 Why spycraft for reporters? Need to keep identity of confidential sources secret from subpoena or government snooping. Need to keep identity of confidential whistleblowers secret from corporations. Need to travel in places where governments detain journalists.
Why spycraft for reporters? Need to keep identity of confidential sources secret from subpoena or government snooping. Need to keep identity of confidential whistleblowers secret from corporations. Need to travel in places where governments detain journalists.
 Examples National Security Agency revelations Barry Bearak of the NY Times in Zimbabwe Hewlett Packard board leaks Secret subpoena of AP phone records Fox News reporter’s email contents
Examples National Security Agency revelations Barry Bearak of the NY Times in Zimbabwe Hewlett Packard board leaks Secret subpoena of AP phone records Fox News reporter’s email contents
 You’ve been warned. . . “We’re not going to subpoena reporters in the future. We don’t need to. We know who you’re talking to. ” -- A national security official to Lucy Dalglish of the RCFP
You’ve been warned. . . “We’re not going to subpoena reporters in the future. We don’t need to. We know who you’re talking to. ” -- A national security official to Lucy Dalglish of the RCFP
 What I’ll cover Keeping internet searches private Making and receiving untraceable calls Keeping email private Encryption/decryption programs Keeping your computer clean Tricking keyloggers
What I’ll cover Keeping internet searches private Making and receiving untraceable calls Keeping email private Encryption/decryption programs Keeping your computer clean Tricking keyloggers
 Private internet searching NSA monitors search terms AOL debacle: 36 million search terms of 650, 000 users (http: //www. aolstalker. com/) Subpoenas to your IT department or IP provider Alternative: www. ixquick. com: No IP addresses kept, no cookies, search terms deleted within 48 hours Duck. Go. com: nothing kept Anonymizer. com? : Anonymizer Universal ($80)
Private internet searching NSA monitors search terms AOL debacle: 36 million search terms of 650, 000 users (http: //www. aolstalker. com/) Subpoenas to your IT department or IP provider Alternative: www. ixquick. com: No IP addresses kept, no cookies, search terms deleted within 48 hours Duck. Go. com: nothing kept Anonymizer. com? : Anonymizer Universal ($80)
 Torproject. org TOR enables anonymous browsing Bounces your browsing through a worldwide net of relays Get through national firewalls Used by journalists, activists, bloggers, NGOs, companies, et al.
Torproject. org TOR enables anonymous browsing Bounces your browsing through a worldwide net of relays Get through national firewalls Used by journalists, activists, bloggers, NGOs, companies, et al.
 Keeping identity private in calls *67 blocks Caller ID in Canada Old NYT caller ID: 111 -1111 “Spoof” your Caller ID with Spoof. Card (www. spoofcard. com) -- $10/60 minutes Crazycall. net (international) Also do voice changing
Keeping identity private in calls *67 blocks Caller ID in Canada Old NYT caller ID: 111 -1111 “Spoof” your Caller ID with Spoof. Card (www. spoofcard. com) -- $10/60 minutes Crazycall. net (international) Also do voice changing
 Cellphone cautions GIS-equipped cellphones track your location Cellphones also track location by cell tower triangulation Cellphones and wireless phones can be heard by scanners Cellphones can be bugged
Cellphone cautions GIS-equipped cellphones track your location Cellphones also track location by cell tower triangulation Cellphones and wireless phones can be heard by scanners Cellphones can be bugged
 Cellphone spyware Listen to calls, extract SMS, view photos, read call logs ($60)
Cellphone spyware Listen to calls, extract SMS, view photos, read call logs ($60)
 Pre-paid cell phones No-contract cell phones and SIM cards IMPORTANT: Buy with cash, and top up with cash Canada: Rogers, 7 -Eleven, et al. Phones as cheap as $10 -$20 Pre-paid cards as cheap as 10 cents/minute in US
Pre-paid cell phones No-contract cell phones and SIM cards IMPORTANT: Buy with cash, and top up with cash Canada: Rogers, 7 -Eleven, et al. Phones as cheap as $10 -$20 Pre-paid cards as cheap as 10 cents/minute in US
 Voice over Internet Protocol (Vo. IP) Internet voice calls Beware “man in the middle” attacks (NSA, for instance) Skype encrypts voice/video data stream But there is an NSA back door… Zfone with Vo. IP clients like Apple i. Chat, Gizmo, Google. Talk, Magic Jack (but not Skype)
Voice over Internet Protocol (Vo. IP) Internet voice calls Beware “man in the middle” attacks (NSA, for instance) Skype encrypts voice/video data stream But there is an NSA back door… Zfone with Vo. IP clients like Apple i. Chat, Gizmo, Google. Talk, Magic Jack (but not Skype)
 Silent Circle Started by PGP inventor Phil Zimmerman App for i. Phone or Android Encrypts phone, text, video chat But secure email server has been shut down! $10/month Prepaid “Rōnin card” – get service anonymously
Silent Circle Started by PGP inventor Phil Zimmerman App for i. Phone or Android Encrypts phone, text, video chat But secure email server has been shut down! $10/month Prepaid “Rōnin card” – get service anonymously
 Keeping identity private in email Use free “throwaway” email addresses from Yahoo, etc. Anonymizer. com: Nyms software creates throwaway email addresses that will forward to your real address ($20/yr) Other remailers: Mixmaster, Quick. Silver, et al.
Keeping identity private in email Use free “throwaway” email addresses from Yahoo, etc. Anonymizer. com: Nyms software creates throwaway email addresses that will forward to your real address ($20/yr) Other remailers: Mixmaster, Quick. Silver, et al.
 Email without sending email Trick used by CIA director David Petraeus and mistress Paula Broadwell Share an anonymous Gmail or Yahoo account Write messages as drafts, but don’t send them
Email without sending email Trick used by CIA director David Petraeus and mistress Paula Broadwell Share an anonymous Gmail or Yahoo account Write messages as drafts, but don’t send them
 Smuggling your text and pictures Use micro SD cards Up to 128 GB
Smuggling your text and pictures Use micro SD cards Up to 128 GB
 Cryptography Use code to make files on disk, phone, etc. , unreadable Avoid simple ciphers, one-time pads, etc. Public-key cryptography is best True. Crypt. org: Open source; no back door(? ) Plausible deniability with hidden volume Gnu. PG 2. 0 also open source Use a strong passphrase! Keep data on True. Crypt encrypted thumb drive
Cryptography Use code to make files on disk, phone, etc. , unreadable Avoid simple ciphers, one-time pads, etc. Public-key cryptography is best True. Crypt. org: Open source; no back door(? ) Plausible deniability with hidden volume Gnu. PG 2. 0 also open source Use a strong passphrase! Keep data on True. Crypt encrypted thumb drive
 Hidden USB drives
Hidden USB drives
 Email encryption MS Outlook will encrypt email Better: Gnu. PG 2. 0 (free) Uses public-key crypto Can be built into Gmail Enigmail for Mozilla
Email encryption MS Outlook will encrypt email Better: Gnu. PG 2. 0 (free) Uses public-key crypto Can be built into Gmail Enigmail for Mozilla
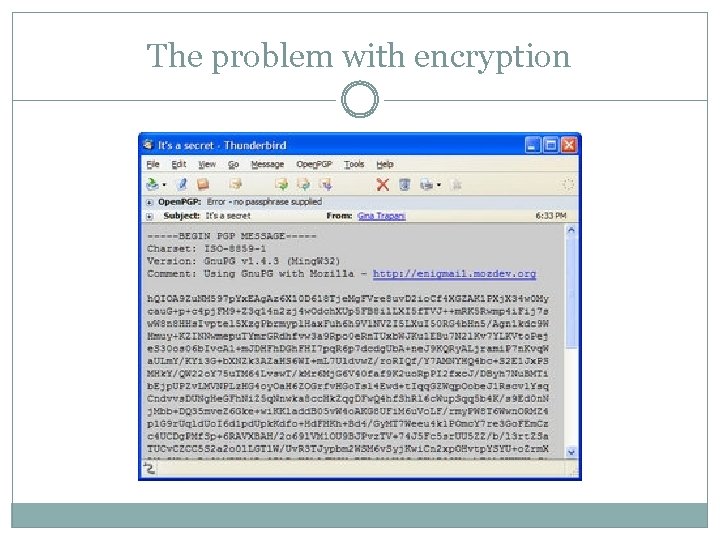 The problem with encryption
The problem with encryption
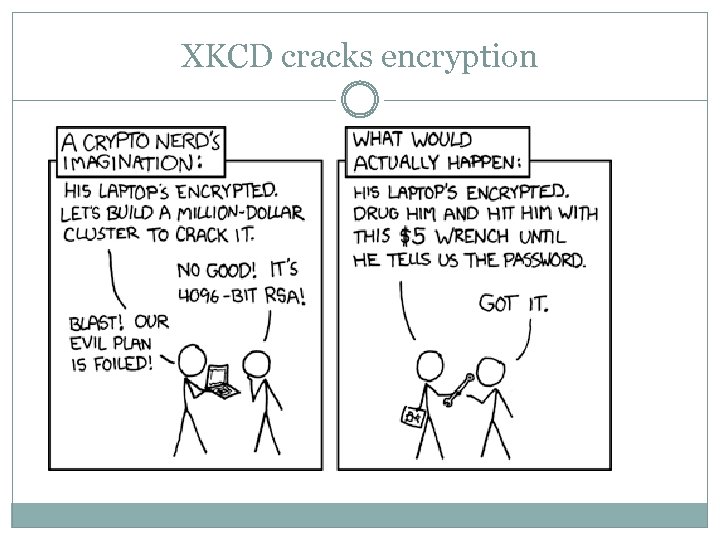 XKCD cracks encryption
XKCD cracks encryption
 Solution: Steganography Poe’s “Purloined Letter”: Hide in plain sight Message hidden in “covertext” of some sort: Plaintext MP 3 s, jpegs, video, Flash, etc. www. jjtc. com/Steganography/tools. html Open. Puff 4. 0 – deniable encryption using less secret data as a decoy New – hiding files in the silence of Skype conversations!
Solution: Steganography Poe’s “Purloined Letter”: Hide in plain sight Message hidden in “covertext” of some sort: Plaintext MP 3 s, jpegs, video, Flash, etc. www. jjtc. com/Steganography/tools. html Open. Puff 4. 0 – deniable encryption using less secret data as a decoy New – hiding files in the silence of Skype conversations!
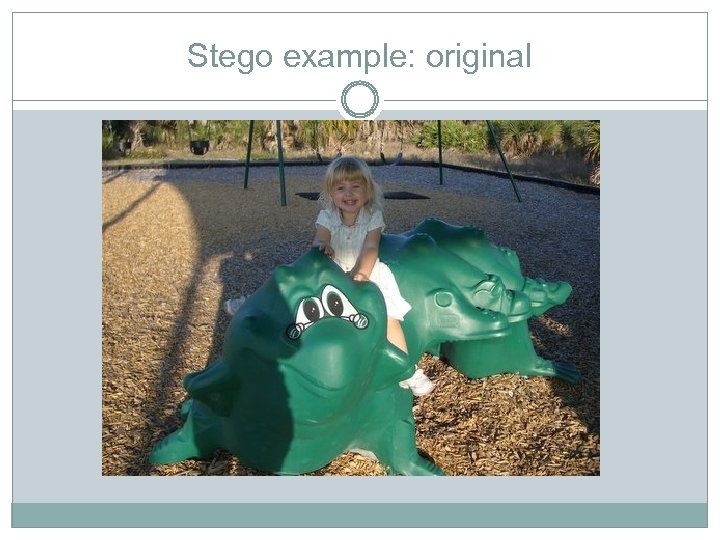 Stego example: original
Stego example: original
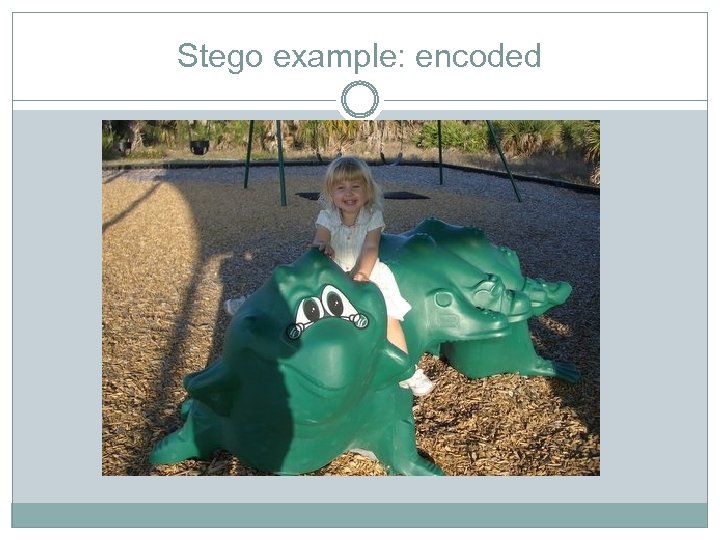 Stego example: encoded
Stego example: encoded
 Hiding directories Create hidden “safes” on computer “Safes” can be on USB drives, DVDs True. Crypt open-source on-the-fly encryption two-level hidden volume (plausible deniability)
Hiding directories Create hidden “safes” on computer “Safes” can be on USB drives, DVDs True. Crypt open-source on-the-fly encryption two-level hidden volume (plausible deniability)
 Watermarking, fingerprinting I E R G N J I
Watermarking, fingerprinting I E R G N J I
 Watermarking, fingerprinting Related to steganography Hidden information embedded in files Invisible watermarking uses variety of techniques: Shift lines, text and/or characters; deliberate misspellings, etc. Used to verify copyright, reveal image tampering, traitor tracing Watermarker. com: “Icemark” invisible watermark ($50) Strategy: Retype the document, adding your own variations… I E R
Watermarking, fingerprinting Related to steganography Hidden information embedded in files Invisible watermarking uses variety of techniques: Shift lines, text and/or characters; deliberate misspellings, etc. Used to verify copyright, reveal image tampering, traitor tracing Watermarker. com: “Icemark” invisible watermark ($50) Strategy: Retype the document, adding your own variations… I E R
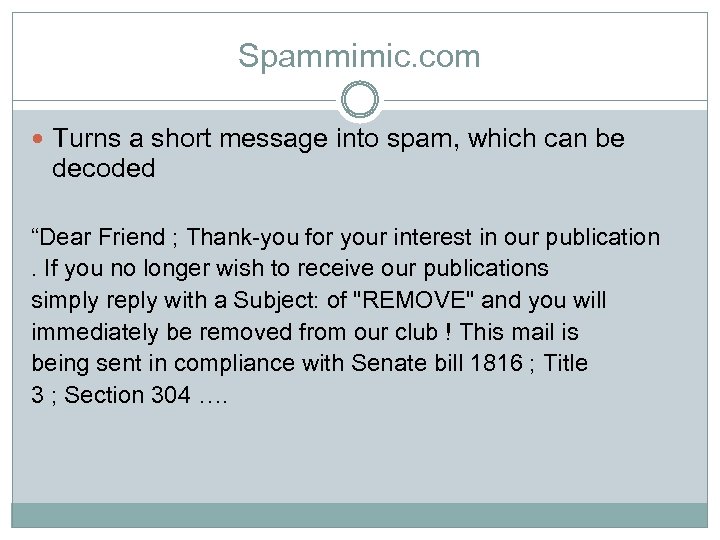 Spammimic. com Turns a short message into spam, which can be decoded “Dear Friend ; Thank-you for your interest in our publication. If you no longer wish to receive our publications simply reply with a Subject: of "REMOVE" and you will immediately be removed from our club ! This mail is being sent in compliance with Senate bill 1816 ; Title 3 ; Section 304 ….
Spammimic. com Turns a short message into spam, which can be decoded “Dear Friend ; Thank-you for your interest in our publication. If you no longer wish to receive our publications simply reply with a Subject: of "REMOVE" and you will immediately be removed from our club ! This mail is being sent in compliance with Senate bill 1816 ; Title 3 ; Section 304 ….
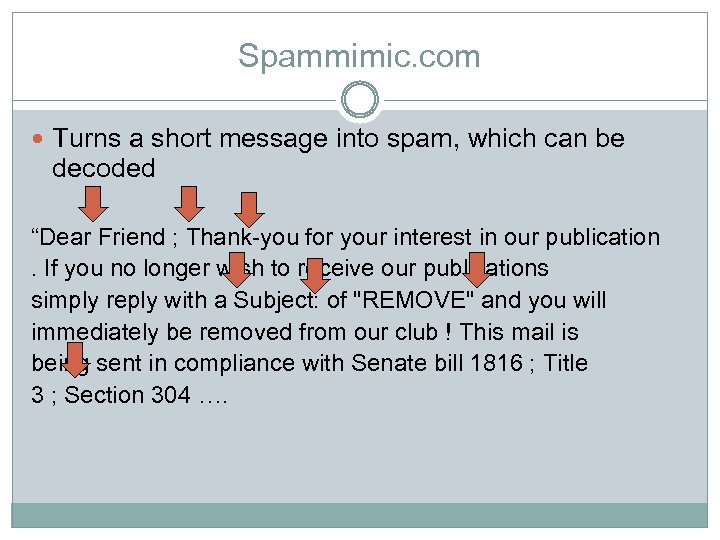 Spammimic. com Turns a short message into spam, which can be decoded “Dear Friend ; Thank-you for your interest in our publication. If you no longer wish to receive our publications simply reply with a Subject: of "REMOVE" and you will immediately be removed from our club ! This mail is being sent in compliance with Senate bill 1816 ; Title 3 ; Section 304 ….
Spammimic. com Turns a short message into spam, which can be decoded “Dear Friend ; Thank-you for your interest in our publication. If you no longer wish to receive our publications simply reply with a Subject: of "REMOVE" and you will immediately be removed from our club ! This mail is being sent in compliance with Senate bill 1816 ; Title 3 ; Section 304 ….
 Cleaning your computer Deleting files doesn’t destroy them Need software that overwrites deleted file space, temp files, etc. Cyber. Scrub Privacy Suite ($60) Overwipes data files, erases other traces Ccleaner (free), Eraser 6. 0, other freeware Darik’s Boot and Nuke (CD wipes all drives)
Cleaning your computer Deleting files doesn’t destroy them Need software that overwrites deleted file space, temp files, etc. Cyber. Scrub Privacy Suite ($60) Overwipes data files, erases other traces Ccleaner (free), Eraser 6. 0, other freeware Darik’s Boot and Nuke (CD wipes all drives)
 Keyloggers Hidden program that captures keystrokes and sends them to whoever installed it. Common at internet cafes! FBI’s Magic Lantern keylogger Anti-spyware software will detect many – but not all – keyloggers. Stopgap protection: When typing password letters, type a few random letters elsewhere on window between each
Keyloggers Hidden program that captures keystrokes and sends them to whoever installed it. Common at internet cafes! FBI’s Magic Lantern keylogger Anti-spyware software will detect many – but not all – keyloggers. Stopgap protection: When typing password letters, type a few random letters elsewhere on window between each
 Hardware keyloggers Insert between keyboard and computer ($50 -$200)
Hardware keyloggers Insert between keyboard and computer ($50 -$200)
 Software keyloggers Installs software in 5 seconds ($99)
Software keyloggers Installs software in 5 seconds ($99)
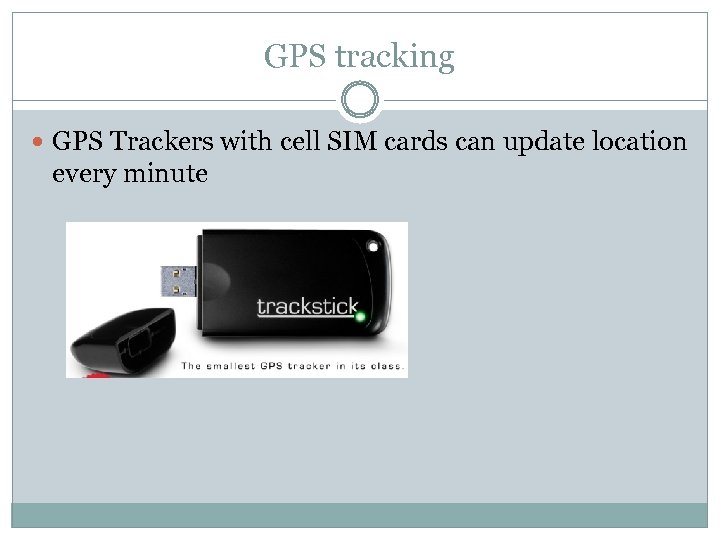 GPS tracking GPS Trackers with cell SIM cards can update location every minute
GPS tracking GPS Trackers with cell SIM cards can update location every minute
 Recommendations Assess the risk to your source Who wants your source’s identity? What are their capabilities? Discuss security with your sources Make security decisions sooner rather than later Consider low-tech face-to-face meetings
Recommendations Assess the risk to your source Who wants your source’s identity? What are their capabilities? Discuss security with your sources Make security decisions sooner rather than later Consider low-tech face-to-face meetings
 Some privacy resources privacy. org epic. org privacyinternational. org journalistsecurity. net/ securityinabox. org
Some privacy resources privacy. org epic. org privacyinternational. org journalistsecurity. net/ securityinabox. org
 Questions and ideas?
Questions and ideas?


