6a7806dc4b092d96df61f9644ffda203.ppt
- Количество слайдов: 23
 SPKI analysis in strand space Alex Vidergar, 1 Lt, USAF Air Force Institute of Technology Graduate School of Computer Science & Engineering Thesis Advisor: Robert Graham, Maj, USAF
SPKI analysis in strand space Alex Vidergar, 1 Lt, USAF Air Force Institute of Technology Graduate School of Computer Science & Engineering Thesis Advisor: Robert Graham, Maj, USAF
 Overview n SPKI • what it is and why we use it n Strand Space • How this tool was used effectively n Example Analysis • Transport Layer Security (TLS) n Conclusions about new security properties • Authorizations
Overview n SPKI • what it is and why we use it n Strand Space • How this tool was used effectively n Example Analysis • Transport Layer Security (TLS) n Conclusions about new security properties • Authorizations
 Simple Public Key Infrastructure n n Championed by Ron Rivest (RSA) and Carl Ellison (Intel) Simple Distributed Security Infrastructure (SDSI) and SPKI merged in the 90 s Developed to overcome shortcoming in the currently deployed PKI (X. 509) Two types of certificates Name & Authorization
Simple Public Key Infrastructure n n Championed by Ron Rivest (RSA) and Carl Ellison (Intel) Simple Distributed Security Infrastructure (SDSI) and SPKI merged in the 90 s Developed to overcome shortcoming in the currently deployed PKI (X. 509) Two types of certificates Name & Authorization
 X. 509 Shortcomings n Unrealistic Goals • Global reach of the x. 500 directory • Single global standard • Unique names in one namespace n Privacy • Participation in the network may unwillingly revealing details about organization n Lack of Flexibility • Updated information impossible • Multiple keys unsupported
X. 509 Shortcomings n Unrealistic Goals • Global reach of the x. 500 directory • Single global standard • Unique names in one namespace n Privacy • Participation in the network may unwillingly revealing details about organization n Lack of Flexibility • Updated information impossible • Multiple keys unsupported
 SPKI Solutions n Egalitarian Design • Every Principal acts as Certificate Authority (CA) • Local Names n n Humans tend to relate well to things they name themselves Local name space • Allows unique names to be applied as understood by the principals that will be using them • Fully qualified names act globally n Alice’s Bob’s Charlie ≠ Allison’s Bob’s Charlie
SPKI Solutions n Egalitarian Design • Every Principal acts as Certificate Authority (CA) • Local Names n n Humans tend to relate well to things they name themselves Local name space • Allows unique names to be applied as understood by the principals that will be using them • Fully qualified names act globally n Alice’s Bob’s Charlie ≠ Allison’s Bob’s Charlie
 SPKI Solutions n Delegation of Authority • Delegation bit • University Example University Enrollment n Course Enrollment n • Department n School - student
SPKI Solutions n Delegation of Authority • Delegation bit • University Example University Enrollment n Course Enrollment n • Department n School - student
 SPKI: Authorization Tags n Customized to applications • Once again not standardized • Flexibility n Security through obscurity? • What is access of 10 mean? • More importantly, meaningful to the issuers of access to a resource
SPKI: Authorization Tags n Customized to applications • Once again not standardized • Flexibility n Security through obscurity? • What is access of 10 mean? • More importantly, meaningful to the issuers of access to a resource
 SPKI: Flexibility or Meager Design? n Constant theme of Flexibility • Very Vague Specification n Highly customizable • Requires diligence in implementation Easily integrated into a system n Potential security issues may arise n Solution: Strand space analysis
SPKI: Flexibility or Meager Design? n Constant theme of Flexibility • Very Vague Specification n Highly customizable • Requires diligence in implementation Easily integrated into a system n Potential security issues may arise n Solution: Strand space analysis
 Strand Space n Existing Strand Space Model • Public Key Protocol n n n Diffie-Hellman Injective hash function Signatures in addition to encryptions • Mixed Strand Space n n n Disparate protocols operating in the same space Respect Disjoint Encryption
Strand Space n Existing Strand Space Model • Public Key Protocol n n n Diffie-Hellman Injective hash function Signatures in addition to encryptions • Mixed Strand Space n n n Disparate protocols operating in the same space Respect Disjoint Encryption
 Strand Space : Merge n Mixed PKI Strand Space • Amalgamation of needed features of previous strand space models • Ideal environment for testing SPKI protocols being integrated into other systems
Strand Space : Merge n Mixed PKI Strand Space • Amalgamation of needed features of previous strand space models • Ideal environment for testing SPKI protocols being integrated into other systems
 TLS : Analysis n Ideal analysis protocol: Transport Layer Security n n Arguably the most widely used Internet protocol for secure transactions Intrinsic use of certificates • Uses x. 509 n Layered protocol execution • TLS > DH > Resume
TLS : Analysis n Ideal analysis protocol: Transport Layer Security n n Arguably the most widely used Internet protocol for secure transactions Intrinsic use of certificates • Uses x. 509 n Layered protocol execution • TLS > DH > Resume
 TLS : modifications n TLS uses x. 509 certificates • Mayweh implements SSL with SPKI Substitute x. 509 for SPKI name certs n Functionally identical n Limited Network security n • Assumed operating in secure environment
TLS : modifications n TLS uses x. 509 certificates • Mayweh implements SSL with SPKI Substitute x. 509 for SPKI name certs n Functionally identical n Limited Network security n • Assumed operating in secure environment
 TLS : the sweet Onion n TLS is a layer of protocols • TLS itself is a shell n Arranges for other protocols to run • Does not provide security n Security provided by sub protocols • Diffie-Hellman • RSA
TLS : the sweet Onion n TLS is a layer of protocols • TLS itself is a shell n Arranges for other protocols to run • Does not provide security n Security provided by sub protocols • Diffie-Hellman • RSA
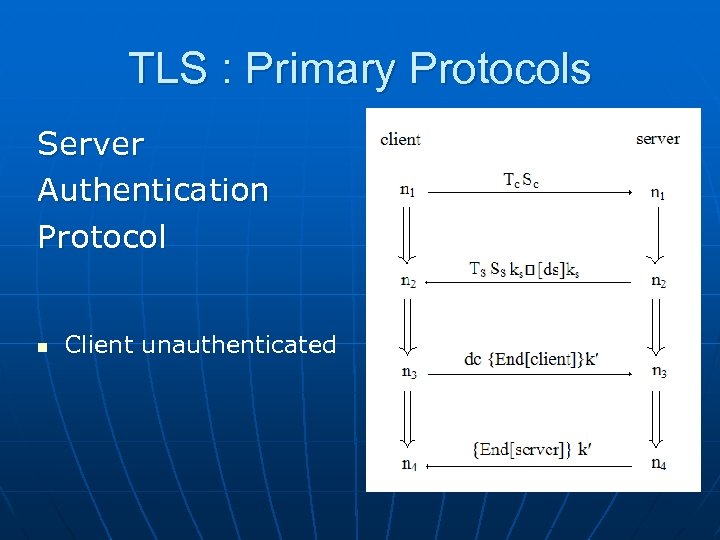 TLS : Primary Protocols Server Authentication Protocol n Client unauthenticated
TLS : Primary Protocols Server Authentication Protocol n Client unauthenticated
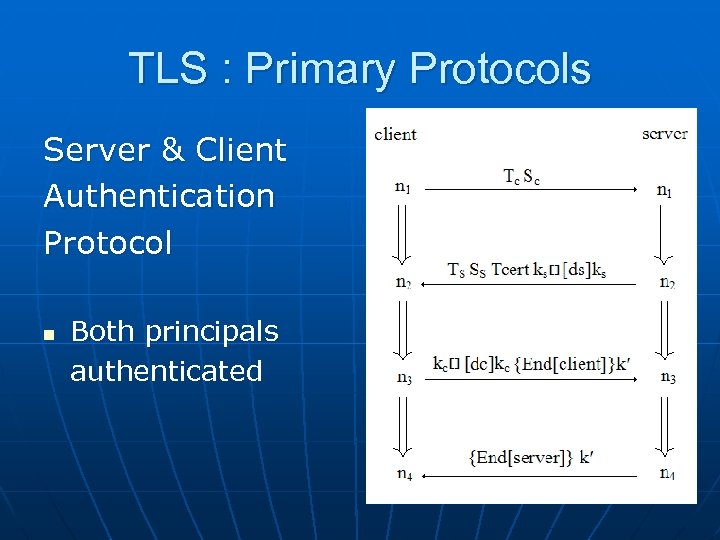 TLS : Primary Protocols Server & Client Authentication Protocol n Both principals authenticated
TLS : Primary Protocols Server & Client Authentication Protocol n Both principals authenticated
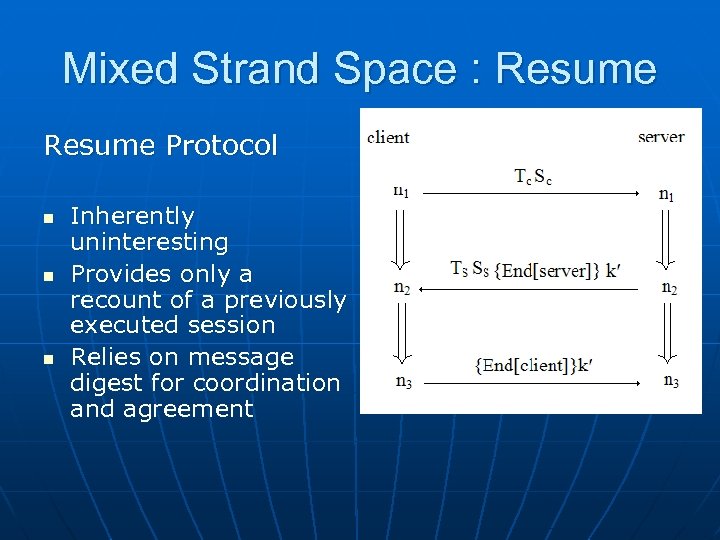 Mixed Strand Space : Resume Protocol n n n Inherently uninteresting Provides only a recount of a previously executed session Relies on message digest for coordination and agreement
Mixed Strand Space : Resume Protocol n n n Inherently uninteresting Provides only a recount of a previously executed session Relies on message digest for coordination and agreement
 Mixed Strand Space : Certificate Chain Discovery n n Certificate Chain Discovery Protocol Designed from the ground up with TLS in mind • establish authentication of CA • validation of certificate • maintain security of primary protocol
Mixed Strand Space : Certificate Chain Discovery n n Certificate Chain Discovery Protocol Designed from the ground up with TLS in mind • establish authentication of CA • validation of certificate • maintain security of primary protocol
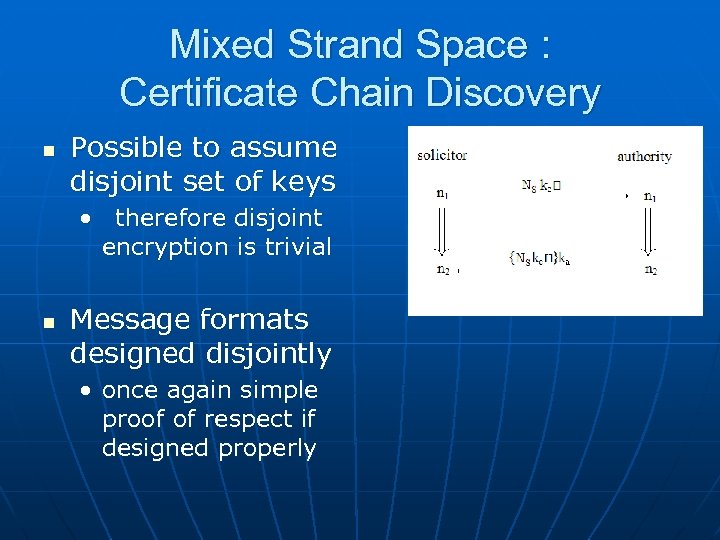 Mixed Strand Space : Certificate Chain Discovery n Possible to assume disjoint set of keys • therefore disjoint encryption is trivial n Message formats designed disjointly • once again simple proof of respect if designed properly
Mixed Strand Space : Certificate Chain Discovery n Possible to assume disjoint set of keys • therefore disjoint encryption is trivial n Message formats designed disjointly • once again simple proof of respect if designed properly
 Analysis n Respect • Concept born in paper Mixed Strand Spaces • Supplemented n Method for defining respect • Characterize test components • Identify sets of messages n Applied to Diffie-Hellman • Protocol design based on Respect n SPKI Certificate Chain Discovery • Disjoint Encryption • Respect of primary protocol’s test components • Necessary to Prove for each protocol as primary?
Analysis n Respect • Concept born in paper Mixed Strand Spaces • Supplemented n Method for defining respect • Characterize test components • Identify sets of messages n Applied to Diffie-Hellman • Protocol design based on Respect n SPKI Certificate Chain Discovery • Disjoint Encryption • Respect of primary protocol’s test components • Necessary to Prove for each protocol as primary?
 Analysis Disjoint Encryption • Protocol Independence through Disjoint Encryption • Better Refined concept of respect → Independence n n Disjoint set of test components Previous notion of Respect • covers naïve case of disjoint sets n Allows more complex secondary protocols to be designed • In the CCD Protocol Design Case n CCD design from respect is indeed Disjoint Encryption • Disjoint Outbound simple case: no shared terms • Disjoint Inbound • Visual representation of mixed strand spaces n Problematic with entwined sub-protocols
Analysis Disjoint Encryption • Protocol Independence through Disjoint Encryption • Better Refined concept of respect → Independence n n Disjoint set of test components Previous notion of Respect • covers naïve case of disjoint sets n Allows more complex secondary protocols to be designed • In the CCD Protocol Design Case n CCD design from respect is indeed Disjoint Encryption • Disjoint Outbound simple case: no shared terms • Disjoint Inbound • Visual representation of mixed strand spaces n Problematic with entwined sub-protocols
 Simple and Powerful n Signed statements are certifications n An authority is an authority • Certificate Authorities traditionally are simply name authorities n n Does not have to be limited to names Authorizations are thus provided by an authorization principal • Already incorporated with authorization certificates in SPKI standard n Explicit Rely-Guarantee Functionality
Simple and Powerful n Signed statements are certifications n An authority is an authority • Certificate Authorities traditionally are simply name authorities n n Does not have to be limited to names Authorizations are thus provided by an authorization principal • Already incorporated with authorization certificates in SPKI standard n Explicit Rely-Guarantee Functionality
 Summary n SPKI • Vague specification makes it flexible n n Requires diligence in implementation Strand Space • Mixed-PKI strand space n TLS • Ideal testing ground for SPKI analysis n Authorization • • Intrinsic to SPKI standard CA are trusted to provide
Summary n SPKI • Vague specification makes it flexible n n Requires diligence in implementation Strand Space • Mixed-PKI strand space n TLS • Ideal testing ground for SPKI analysis n Authorization • • Intrinsic to SPKI standard CA are trusted to provide
 Questions
Questions


