b47d37df3b8cdd34022a6298a8715c05.ppt
- Количество слайдов: 31
 Spam, Spit and Spim CS 5480/6480 17 -Sep-2008 Matthew J. Probst *with some slides/graphics adapted from J. F Kurose and K. W. Ross
Spam, Spit and Spim CS 5480/6480 17 -Sep-2008 Matthew J. Probst *with some slides/graphics adapted from J. F Kurose and K. W. Ross
 Announcements • HW 1 due by 11: 59 pm MT 18 -Sep-08 (tomorrow). • Hard copy can be turned in now or you can hand it in the cs 5480/6480 box outside the So. C office
Announcements • HW 1 due by 11: 59 pm MT 18 -Sep-08 (tomorrow). • Hard copy can be turned in now or you can hand it in the cs 5480/6480 box outside the So. C office
 Spammers: Cost to send? Assuming a $10/mo dialup account: • 13. 4 million messages per month might be sent… • A cost of about 1 penny per 14, 300 messages • Free trials and virus infected computers (zombies/bots) make it free! • Side benefits of bots to spammers: Email address harvesting.
Spammers: Cost to send? Assuming a $10/mo dialup account: • 13. 4 million messages per month might be sent… • A cost of about 1 penny per 14, 300 messages • Free trials and virus infected computers (zombies/bots) make it free! • Side benefits of bots to spammers: Email address harvesting.
 $ $ You: Cost to Receive? $$ • 10+ Billion spam received each day • At 5 seconds per spam (to recognize & delete). . • That’s 50 billion seconds of lost productivity each day (39, 457 work years) • Assuming $36 k average income person: $1. 5 Billion per day in lost productivity to economy.
$ $ You: Cost to Receive? $$ • 10+ Billion spam received each day • At 5 seconds per spam (to recognize & delete). . • That’s 50 billion seconds of lost productivity each day (39, 457 work years) • Assuming $36 k average income person: $1. 5 Billion per day in lost productivity to economy.
 Driving Business Incentives? • Pump and dump penny-stocks • Scams-Nigerian investments, phishing, etc. • Botnet Viruses • Meds • Insurance • Porn • Loans/Mortgages • Others… ROI? Assuming: 13. 4 M spam/month @ 0. 05% take rate (1/2000) on a $20 pill that “cures cancer, eliminates all joint pain AND pleases your significant other”, you could make $134 K/month
Driving Business Incentives? • Pump and dump penny-stocks • Scams-Nigerian investments, phishing, etc. • Botnet Viruses • Meds • Insurance • Porn • Loans/Mortgages • Others… ROI? Assuming: 13. 4 M spam/month @ 0. 05% take rate (1/2000) on a $20 pill that “cures cancer, eliminates all joint pain AND pleases your significant other”, you could make $134 K/month
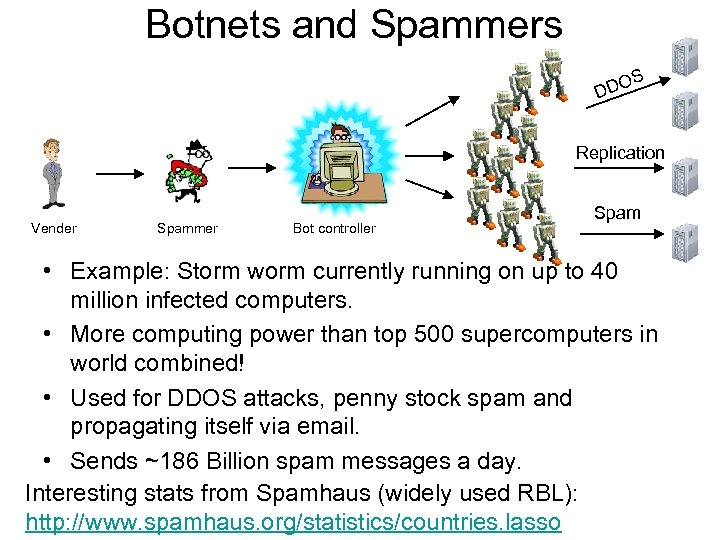 Botnets and Spammers S O DD Replication Vender Spammer Bot controller Spam • Example: Storm worm currently running on up to 40 million infected computers. • More computing power than top 500 supercomputers in world combined! • Used for DDOS attacks, penny stock spam and propagating itself via email. • Sends ~186 Billion spam messages a day. Interesting stats from Spamhaus (widely used RBL): http: //www. spamhaus. org/statistics/countries. lasso
Botnets and Spammers S O DD Replication Vender Spammer Bot controller Spam • Example: Storm worm currently running on up to 40 million infected computers. • More computing power than top 500 supercomputers in world combined! • Used for DDOS attacks, penny stock spam and propagating itself via email. • Sends ~186 Billion spam messages a day. Interesting stats from Spamhaus (widely used RBL): http: //www. spamhaus. org/statistics/countries. lasso
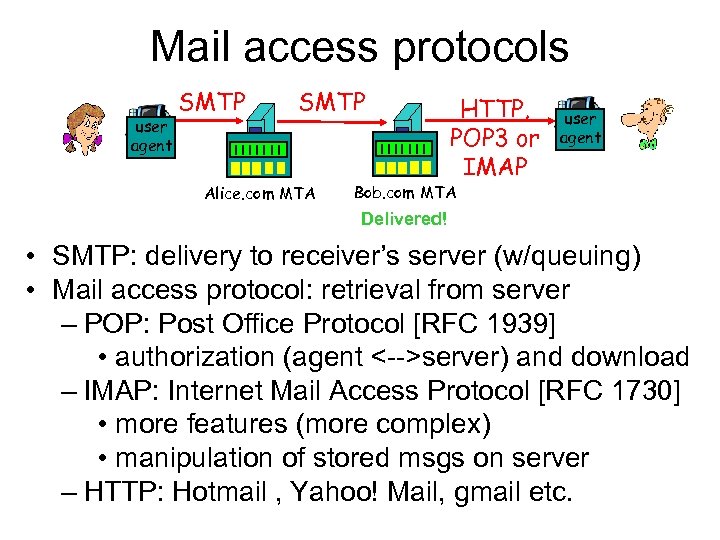 Mail access protocols user agent SMTP Alice. com MTA HTTP, POP 3 or IMAP user agent Bob. com MTA Delivered! • SMTP: delivery to receiver’s server (w/queuing) • Mail access protocol: retrieval from server – POP: Post Office Protocol [RFC 1939] • authorization (agent <-->server) and download – IMAP: Internet Mail Access Protocol [RFC 1730] • more features (more complex) • manipulation of stored msgs on server – HTTP: Hotmail , Yahoo! Mail, gmail etc.
Mail access protocols user agent SMTP Alice. com MTA HTTP, POP 3 or IMAP user agent Bob. com MTA Delivered! • SMTP: delivery to receiver’s server (w/queuing) • Mail access protocol: retrieval from server – POP: Post Office Protocol [RFC 1939] • authorization (agent <-->server) and download – IMAP: Internet Mail Access Protocol [RFC 1730] • more features (more complex) • manipulation of stored msgs on server – HTTP: Hotmail , Yahoo! Mail, gmail etc.
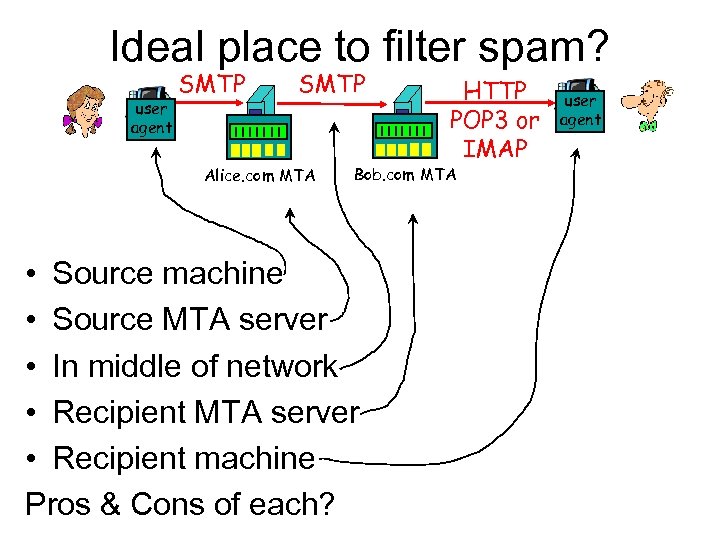 Ideal place to filter spam? user agent SMTP Alice. com MTA HTTP POP 3 or IMAP Bob. com MTA • Source machine • Source MTA server • In middle of network • Recipient MTA server • Recipient machine Pros & Cons of each? user agent
Ideal place to filter spam? user agent SMTP Alice. com MTA HTTP POP 3 or IMAP Bob. com MTA • Source machine • Source MTA server • In middle of network • Recipient MTA server • Recipient machine Pros & Cons of each? user agent
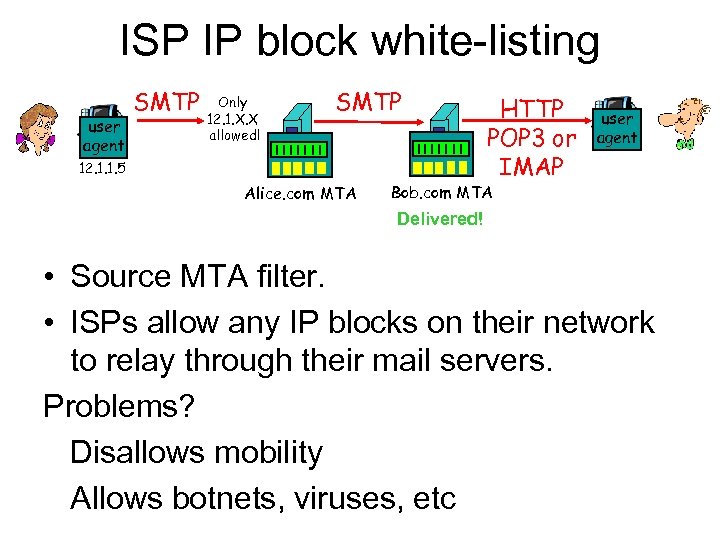 ISP IP block white-listing user agent SMTP Only 12. 1. X. X allowed! SMTP 12. 1. 1. 5 Alice. com MTA HTTP POP 3 or IMAP user agent Bob. com MTA Delivered! • Source MTA filter. • ISPs allow any IP blocks on their network to relay through their mail servers. Problems? Disallows mobility Allows botnets, viruses, etc
ISP IP block white-listing user agent SMTP Only 12. 1. X. X allowed! SMTP 12. 1. 1. 5 Alice. com MTA HTTP POP 3 or IMAP user agent Bob. com MTA Delivered! • Source MTA filter. • ISPs allow any IP blocks on their network to relay through their mail servers. Problems? Disallows mobility Allows botnets, viruses, etc
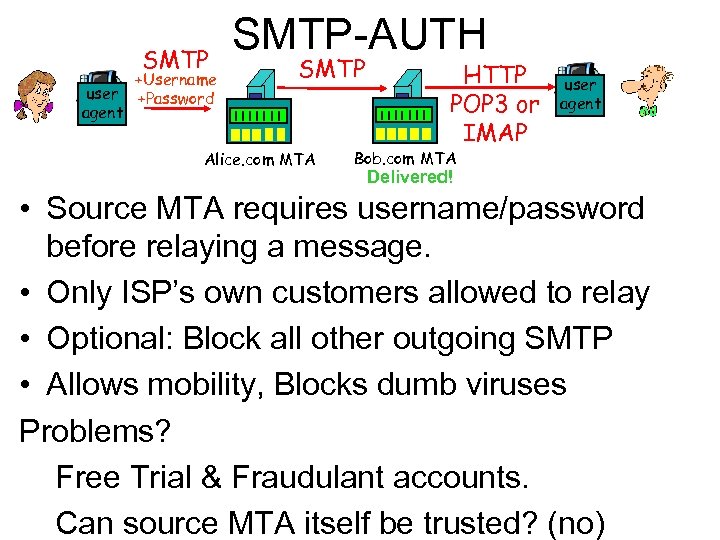 SMTP user agent +Username +Password SMTP-AUTH SMTP Alice. com MTA HTTP POP 3 or IMAP user agent Bob. com MTA Delivered! • Source MTA requires username/password before relaying a message. • Only ISP’s own customers allowed to relay • Optional: Block all other outgoing SMTP • Allows mobility, Blocks dumb viruses Problems? Free Trial & Fraudulant accounts. Can source MTA itself be trusted? (no)
SMTP user agent +Username +Password SMTP-AUTH SMTP Alice. com MTA HTTP POP 3 or IMAP user agent Bob. com MTA Delivered! • Source MTA requires username/password before relaying a message. • Only ISP’s own customers allowed to relay • Optional: Block all other outgoing SMTP • Allows mobility, Blocks dumb viruses Problems? Free Trial & Fraudulant accounts. Can source MTA itself be trusted? (no)
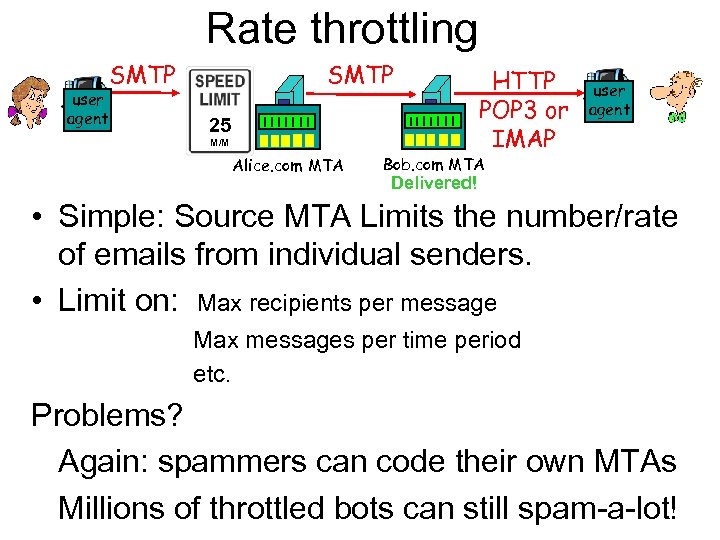 Rate throttling user agent SMTP 25 M/M Alice. com MTA HTTP POP 3 or IMAP user agent Bob. com MTA Delivered! • Simple: Source MTA Limits the number/rate of emails from individual senders. • Limit on: Max recipients per message Max messages per time period etc. Problems? Again: spammers can code their own MTAs Millions of throttled bots can still spam-a-lot!
Rate throttling user agent SMTP 25 M/M Alice. com MTA HTTP POP 3 or IMAP user agent Bob. com MTA Delivered! • Simple: Source MTA Limits the number/rate of emails from individual senders. • Limit on: Max recipients per message Max messages per time period etc. Problems? Again: spammers can code their own MTAs Millions of throttled bots can still spam-a-lot!
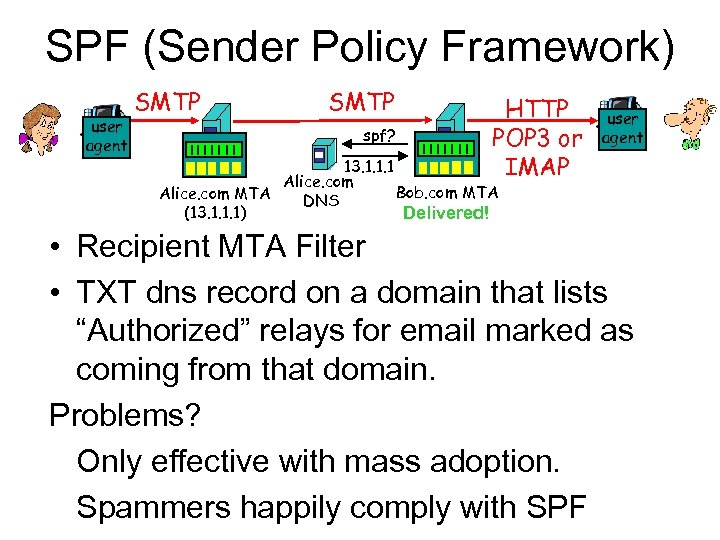 SPF (Sender Policy Framework) user agent SMTP spf? HTTP POP 3 or IMAP user agent 13. 1. 1. 1 Alice. com Bob. com MTA Alice. com MTA DNS (13. 1. 1. 1) Delivered! • Recipient MTA Filter • TXT dns record on a domain that lists “Authorized” relays for email marked as coming from that domain. Problems? Only effective with mass adoption. Spammers happily comply with SPF
SPF (Sender Policy Framework) user agent SMTP spf? HTTP POP 3 or IMAP user agent 13. 1. 1. 1 Alice. com Bob. com MTA Alice. com MTA DNS (13. 1. 1. 1) Delivered! • Recipient MTA Filter • TXT dns record on a domain that lists “Authorized” relays for email marked as coming from that domain. Problems? Only effective with mass adoption. Spammers happily comply with SPF
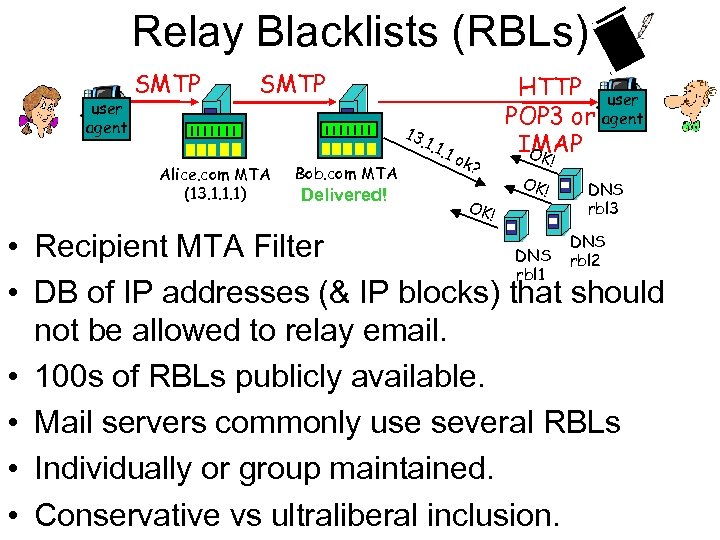 Relay Blacklists (RBLs) user agent SMTP 13. 1 Alice. com MTA (13. 1. 1. 1) Bob. com MTA Delivered! . 1. 1 ok? OK! HTTP user POP 3 or agent IMAP OK ! OK! DNS rbl 3 DNS • Recipient MTA Filter DNS rbl 2 rbl 1 • DB of IP addresses (& IP blocks) that should not be allowed to relay email. • 100 s of RBLs publicly available. • Mail servers commonly use several RBLs • Individually or group maintained. • Conservative vs ultraliberal inclusion.
Relay Blacklists (RBLs) user agent SMTP 13. 1 Alice. com MTA (13. 1. 1. 1) Bob. com MTA Delivered! . 1. 1 ok? OK! HTTP user POP 3 or agent IMAP OK ! OK! DNS rbl 3 DNS • Recipient MTA Filter DNS rbl 2 rbl 1 • DB of IP addresses (& IP blocks) that should not be allowed to relay email. • 100 s of RBLs publicly available. • Mail servers commonly use several RBLs • Individually or group maintained. • Conservative vs ultraliberal inclusion.
 Relay Blacklists (RBLs) cont. Problems? Take it or leave it one-size-fits-all. (Is either too aggressive or too passive). Central RBL servers easy to DDOS. If done within network, then prevents smtpauth.
Relay Blacklists (RBLs) cont. Problems? Take it or leave it one-size-fits-all. (Is either too aggressive or too passive). Central RBL servers easy to DDOS. If done within network, then prevents smtpauth.
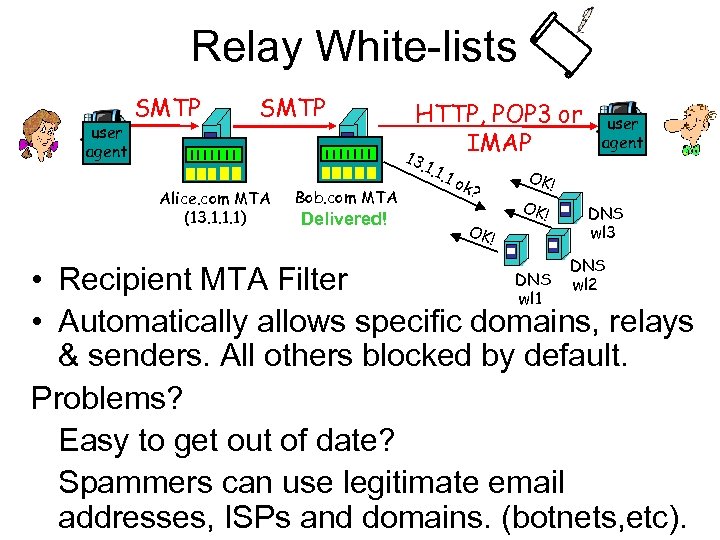 Relay White-lists user agent SMTP HTTP, POP 3 or IMAP 1 3. 1 Alice. com MTA (13. 1. 1. 1) Bob. com MTA Delivered! . 1. 1 ok? OK! user agent OK! DNS wl 3 DNS wl 2 DNS • Recipient MTA Filter wl 1 • Automatically allows specific domains, relays & senders. All others blocked by default. Problems? Easy to get out of date? Spammers can use legitimate email addresses, ISPs and domains. (botnets, etc).
Relay White-lists user agent SMTP HTTP, POP 3 or IMAP 1 3. 1 Alice. com MTA (13. 1. 1. 1) Bob. com MTA Delivered! . 1. 1 ok? OK! user agent OK! DNS wl 3 DNS wl 2 DNS • Recipient MTA Filter wl 1 • Automatically allows specific domains, relays & senders. All others blocked by default. Problems? Easy to get out of date? Spammers can use legitimate email addresses, ISPs and domains. (botnets, etc).
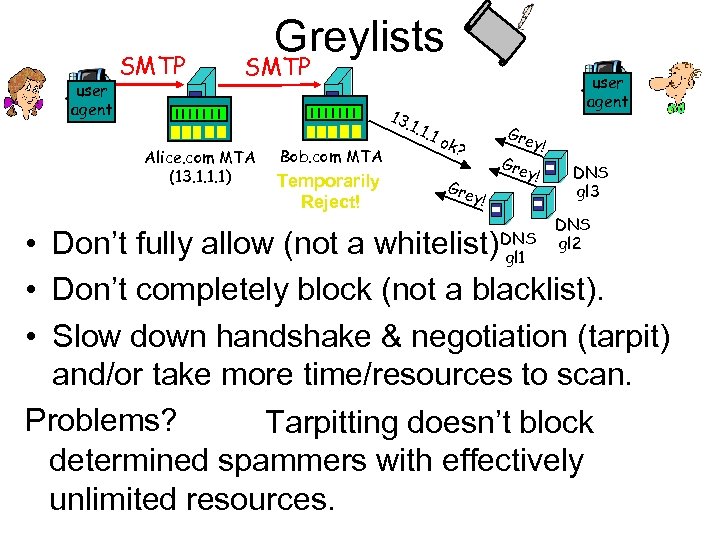 user agent SMTP Greylists SMTP 13. 1 user agent Alice. com MTA (13. 1. 1. 1) Bob. com MTA Temporarily Reject! . 1. 1 Gre ok? Gre y! y! y! DNS gl 3 DNS gl 2 • Don’t fully allow (not a whitelist) • Don’t completely block (not a blacklist). • Slow down handshake & negotiation (tarpit) and/or take more time/resources to scan. Problems? Tarpitting doesn’t block determined spammers with effectively unlimited resources. DNS gl 1
user agent SMTP Greylists SMTP 13. 1 user agent Alice. com MTA (13. 1. 1. 1) Bob. com MTA Temporarily Reject! . 1. 1 Gre ok? Gre y! y! y! DNS gl 3 DNS gl 2 • Don’t fully allow (not a whitelist) • Don’t completely block (not a blacklist). • Slow down handshake & negotiation (tarpit) and/or take more time/resources to scan. Problems? Tarpitting doesn’t block determined spammers with effectively unlimited resources. DNS gl 1
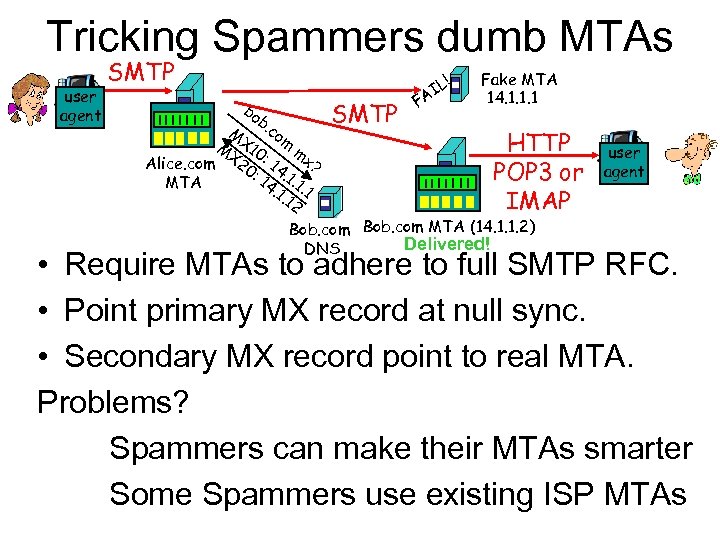 Tricking Spammers dumb MTAs user agent SMTP bo b. c M X 1 om M mx X 2 0: Alice. com ? 0: 14. 1. 1 14 MTA. 1. . 1 12 SMTP F ! IL A Fake MTA 14. 1. 1. 1 HTTP POP 3 or IMAP Bob. com MTA (14. 1. 1. 2) Delivered! DNS user agent • Require MTAs to adhere to full SMTP RFC. • Point primary MX record at null sync. • Secondary MX record point to real MTA. Problems? Spammers can make their MTAs smarter Some Spammers use existing ISP MTAs
Tricking Spammers dumb MTAs user agent SMTP bo b. c M X 1 om M mx X 2 0: Alice. com ? 0: 14. 1. 1 14 MTA. 1. . 1 12 SMTP F ! IL A Fake MTA 14. 1. 1. 1 HTTP POP 3 or IMAP Bob. com MTA (14. 1. 1. 2) Delivered! DNS user agent • Require MTAs to adhere to full SMTP RFC. • Point primary MX record at null sync. • Secondary MX record point to real MTA. Problems? Spammers can make their MTAs smarter Some Spammers use existing ISP MTAs
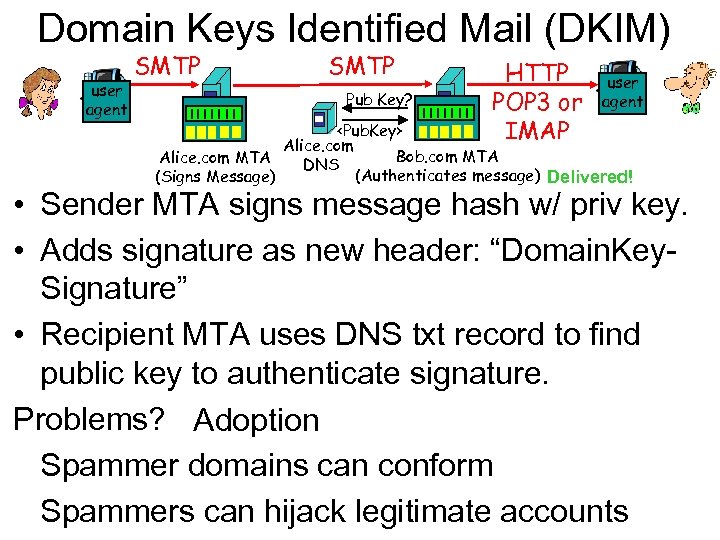 Domain Keys Identified Mail (DKIM) user agent SMTP Pub Key? HTTP POP 3 or IMAP user agent
Domain Keys Identified Mail (DKIM) user agent SMTP Pub Key? HTTP POP 3 or IMAP user agent
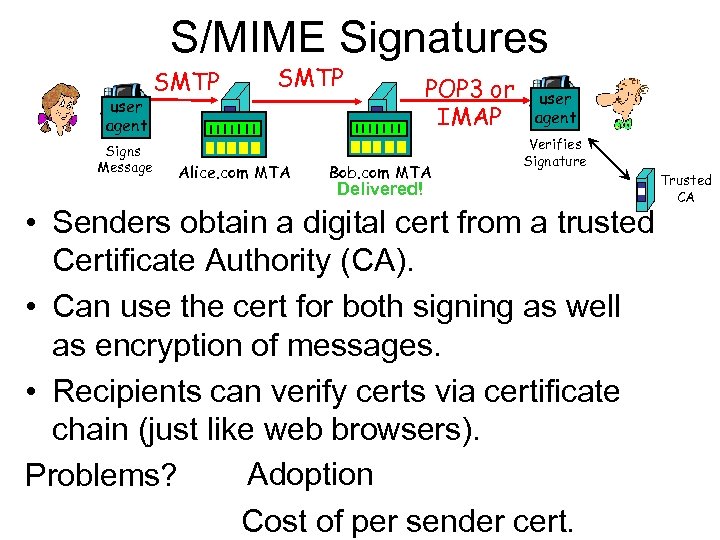 S/MIME Signatures user agent Signs Message SMTP Alice. com MTA POP 3 or IMAP Bob. com MTA user agent Verifies Signature Delivered! • Senders obtain a digital cert from a trusted Certificate Authority (CA). • Can use the cert for both signing as well as encryption of messages. • Recipients can verify certs via certificate chain (just like web browsers). Adoption Problems? Cost of per sender cert. Trusted CA
S/MIME Signatures user agent Signs Message SMTP Alice. com MTA POP 3 or IMAP Bob. com MTA user agent Verifies Signature Delivered! • Senders obtain a digital cert from a trusted Certificate Authority (CA). • Can use the cert for both signing as well as encryption of messages. • Recipients can verify certs via certificate chain (just like web browsers). Adoption Problems? Cost of per sender cert. Trusted CA
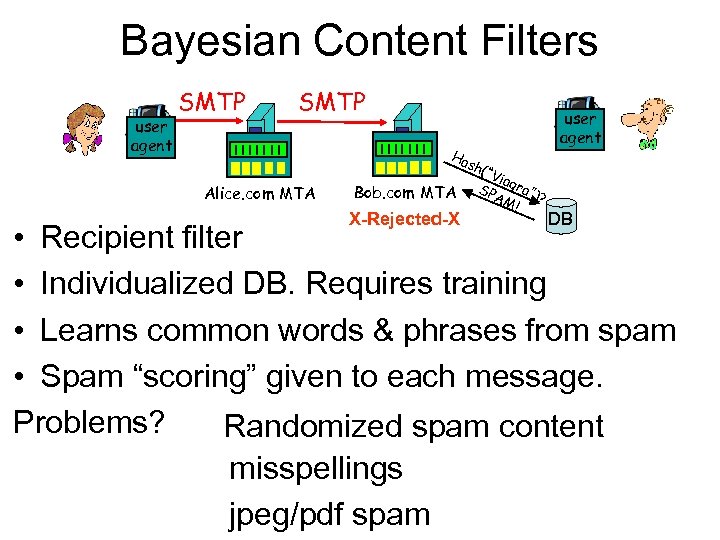 Bayesian Content Filters user agent SMTP Ha user agent Alice. com MTA Bob. com MTA X-Rejected-X sh( “ Via SP gra”) AM ? ! DB • Recipient filter • Individualized DB. Requires training • Learns common words & phrases from spam • Spam “scoring” given to each message. Problems? Randomized spam content misspellings jpeg/pdf spam
Bayesian Content Filters user agent SMTP Ha user agent Alice. com MTA Bob. com MTA X-Rejected-X sh( “ Via SP gra”) AM ? ! DB • Recipient filter • Individualized DB. Requires training • Learns common words & phrases from spam • Spam “scoring” given to each message. Problems? Randomized spam content misspellings jpeg/pdf spam
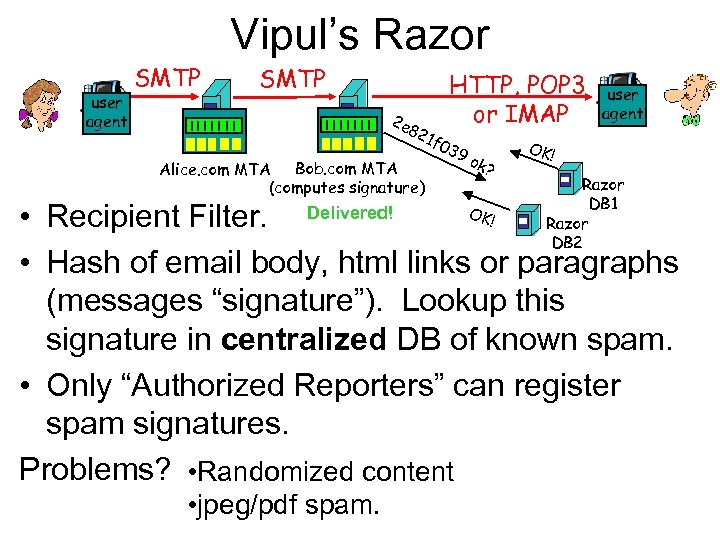 Vipul’s Razor user agent SMTP 2 e 82 Bob. com MTA Alice. com MTA (computes signature) 1 f 0 HTTP, POP 3 or IMAP 39 ok? user agent OK! Razor DB 1 Razor DB 2 OK! • Recipient Filter. Delivered! • Hash of email body, html links or paragraphs (messages “signature”). Lookup this signature in centralized DB of known spam. • Only “Authorized Reporters” can register spam signatures. Problems? • Randomized content • jpeg/pdf spam.
Vipul’s Razor user agent SMTP 2 e 82 Bob. com MTA Alice. com MTA (computes signature) 1 f 0 HTTP, POP 3 or IMAP 39 ok? user agent OK! Razor DB 1 Razor DB 2 OK! • Recipient Filter. Delivered! • Hash of email body, html links or paragraphs (messages “signature”). Lookup this signature in centralized DB of known spam. • Only “Authorized Reporters” can register spam signatures. Problems? • Randomized content • jpeg/pdf spam.
 Spam Training Honeypots • Dedicate an inbox to only attract and profile spam. • Randomly generated address: asdf@domain. com or common (but unused) address: bob@domain. com • Email received by this box can be fed to bayesian filter, vipuls razor & personal RBLs.
Spam Training Honeypots • Dedicate an inbox to only attract and profile spam. • Randomly generated address: asdf@domain. com or common (but unused) address: bob@domain. com • Email received by this box can be fed to bayesian filter, vipuls razor & personal RBLs.
 What is used today? • Combination of all of these techniques. • Spamassassin as an example. • RBLs are low hanging fruit… Commonly block 80%+ of spam.
What is used today? • Combination of all of these techniques. • Spamassassin as an example. • RBLs are low hanging fruit… Commonly block 80%+ of spam.
 Remaining Problems • Not only smtp needs protection (spit, spim) • Increased client mobility & P 2 P messaging • P 2 P spit (no reliance on central scanners or CA). • Fast vs slow path selection based on trust of sender & sender’s email path. • Fast reaction to entity behavior changes (i. Zombie? )
Remaining Problems • Not only smtp needs protection (spit, spim) • Increased client mobility & P 2 P messaging • P 2 P spit (no reliance on central scanners or CA). • Fast vs slow path selection based on trust of sender & sender’s email path. • Fast reaction to entity behavior changes (i. Zombie? )
 Idea: Micro-payments • Senders pay fraction of a cent for each email they send. • Won’t deter normal email users, but would definitely stop many spammers. • Variation: Rather than charge for each email… Force all email users to put $$ in escrow… only charging account upon receiving complaints.
Idea: Micro-payments • Senders pay fraction of a cent for each email they send. • Won’t deter normal email users, but would definitely stop many spammers. • Variation: Rather than charge for each email… Force all email users to put $$ in escrow… only charging account upon receiving complaints.
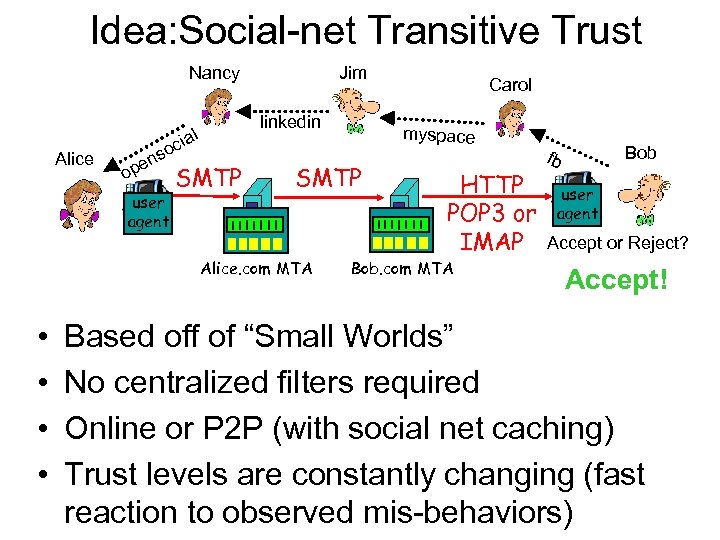 Idea: Social-net Transitive Trust Nancy Alice s n pe o user agent linkedin ial oc Jim SMTP • • myspace SMTP Alice. com MTA Carol HTTP POP 3 or IMAP Bob. com MTA Bob fb user agent Accept or Reject? Accept! Based off of “Small Worlds” No centralized filters required Online or P 2 P (with social net caching) Trust levels are constantly changing (fast reaction to observed mis-behaviors)
Idea: Social-net Transitive Trust Nancy Alice s n pe o user agent linkedin ial oc Jim SMTP • • myspace SMTP Alice. com MTA Carol HTTP POP 3 or IMAP Bob. com MTA Bob fb user agent Accept or Reject? Accept! Based off of “Small Worlds” No centralized filters required Online or P 2 P (with social net caching) Trust levels are constantly changing (fast reaction to observed mis-behaviors)
 P 2 P Experience & RBL • User agents collect their own experience (positive and negative) and share them with their social peers. • User agents generate their own personal RBLs mods based off of their “experience DB”. • User agents query for neighbor’s experiences via multicast.
P 2 P Experience & RBL • User agents collect their own experience (positive and negative) and share them with their social peers. • User agents generate their own personal RBLs mods based off of their “experience DB”. • User agents query for neighbor’s experiences via multicast.
 Dynamic Grey-listing • Selectively decide which message to send on fast-path (Layer 3) vs through tarpit (Layer-7. . for further inspection). • Fast path may include no scanning at all freeing up scanning resources to be used on un-trusted messages.
Dynamic Grey-listing • Selectively decide which message to send on fast-path (Layer 3) vs through tarpit (Layer-7. . for further inspection). • Fast path may include no scanning at all freeing up scanning resources to be used on un-trusted messages.
 fb, myspace, linkedin, etc
fb, myspace, linkedin, etc
 Best single current method of avoiding spam: HIDE! • Use BCC when two recipients have no need of knowing each other’s email addr. • Keep your anti virus software up to date (or use a Mac). • Don’t allow your email address to be posted on public web sites. • Use at least two email accounts… one for your smart friends (that know how to use bcc and how to keep their system’s virus free) and one for everyone else.
Best single current method of avoiding spam: HIDE! • Use BCC when two recipients have no need of knowing each other’s email addr. • Keep your anti virus software up to date (or use a Mac). • Don’t allow your email address to be posted on public web sites. • Use at least two email accounts… one for your smart friends (that know how to use bcc and how to keep their system’s virus free) and one for everyone else.
 Questions? • Questions / Comments / Feedback? *costume available at spamgift. com
Questions? • Questions / Comments / Feedback? *costume available at spamgift. com


