7128bde515bcbf64d1dd1fd8c706a816.ppt
- Количество слайдов: 25
 Software Jyoti Tandukar Vice President, IT Professional Forum Associate Professor, Institute of Engineering CEO, Alternative Technology
Software Jyoti Tandukar Vice President, IT Professional Forum Associate Professor, Institute of Engineering CEO, Alternative Technology
 http: //www. strategypage. com/
http: //www. strategypage. com/
 Computer Controlled System • Demonstration of controlling camera using computer • X-Y control can be built/commercially available • Attachment of a firearm, and wireless connection makes it precision remote controlled killing machine • Multiple units of such devices means you can see the enemy coming from any direction, but the enemy cannot see you • The audience may be able to bring forth more ideas of possibilities.
Computer Controlled System • Demonstration of controlling camera using computer • X-Y control can be built/commercially available • Attachment of a firearm, and wireless connection makes it precision remote controlled killing machine • Multiple units of such devices means you can see the enemy coming from any direction, but the enemy cannot see you • The audience may be able to bring forth more ideas of possibilities.
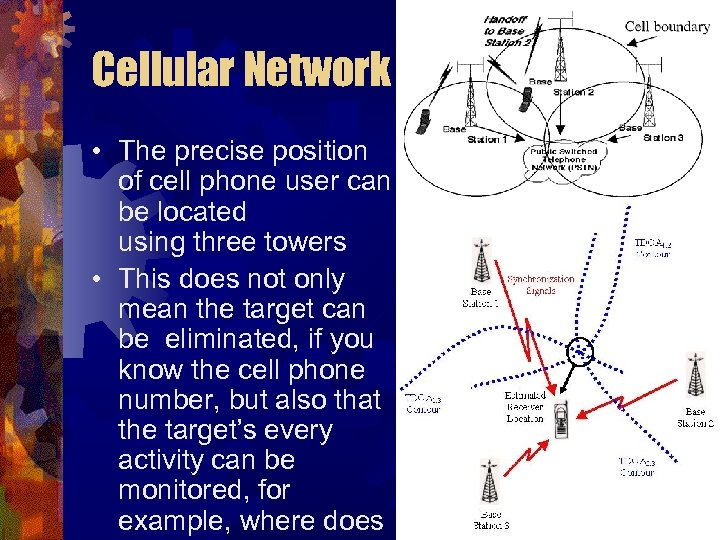 Cellular Network • The precise position of cell phone user can be located using three towers • This does not only mean the target can be eliminated, if you know the cell phone number, but also that the target’s every activity can be monitored, for example, where does
Cellular Network • The precise position of cell phone user can be located using three towers • This does not only mean the target can be eliminated, if you know the cell phone number, but also that the target’s every activity can be monitored, for example, where does
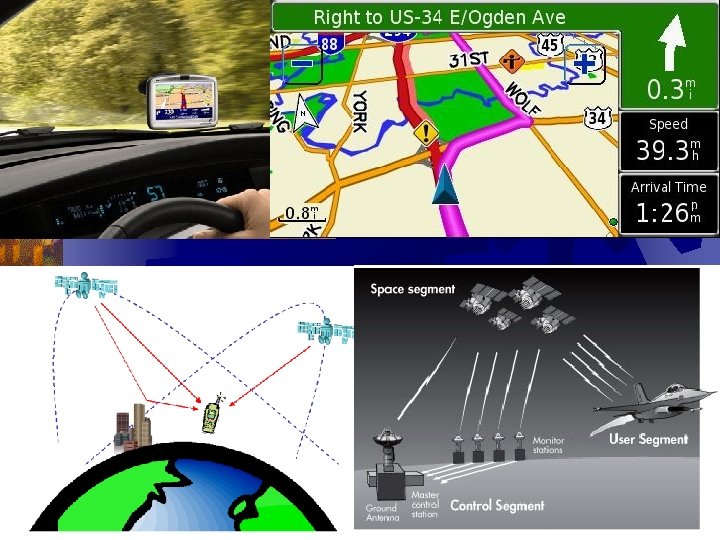
 Global Positioning System (GPS) • GPS is the only fully-functional satellite navigation system. More than two dozen GPS satellites orbit the Earth, transmitting radio signals which allow GPS receivers to determine their location, speed and direction. • The GPS includes a feature called Selective Availability (SA) that introduces intentional errors between 0 meters and up to a hundred meters (300 ft) into the publicly available navigation signals, making it difficult to use for guiding long range missiles to precise targets. Additional accuracy was available in the signal, but in an encrypted form that was only available to the United States military, its allies and a few others, mostly government users. http: //en. wikipedia. org/wiki/Global_Positioning
Global Positioning System (GPS) • GPS is the only fully-functional satellite navigation system. More than two dozen GPS satellites orbit the Earth, transmitting radio signals which allow GPS receivers to determine their location, speed and direction. • The GPS includes a feature called Selective Availability (SA) that introduces intentional errors between 0 meters and up to a hundred meters (300 ft) into the publicly available navigation signals, making it difficult to use for guiding long range missiles to precise targets. Additional accuracy was available in the signal, but in an encrypted form that was only available to the United States military, its allies and a few others, mostly government users. http: //en. wikipedia. org/wiki/Global_Positioning
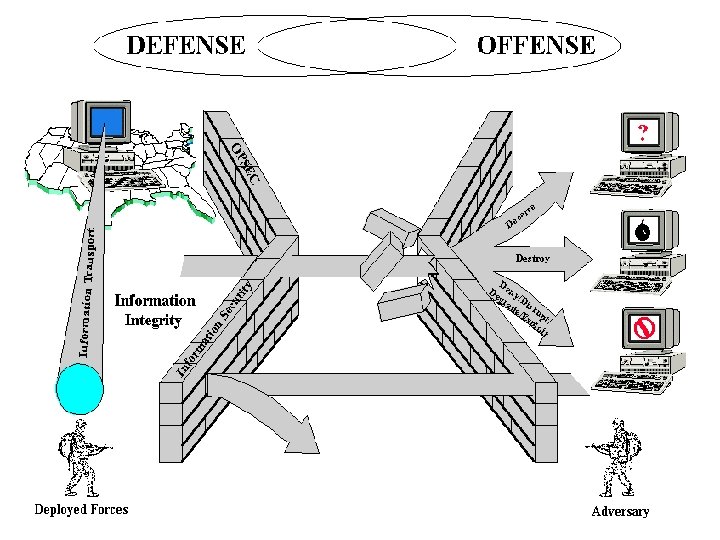
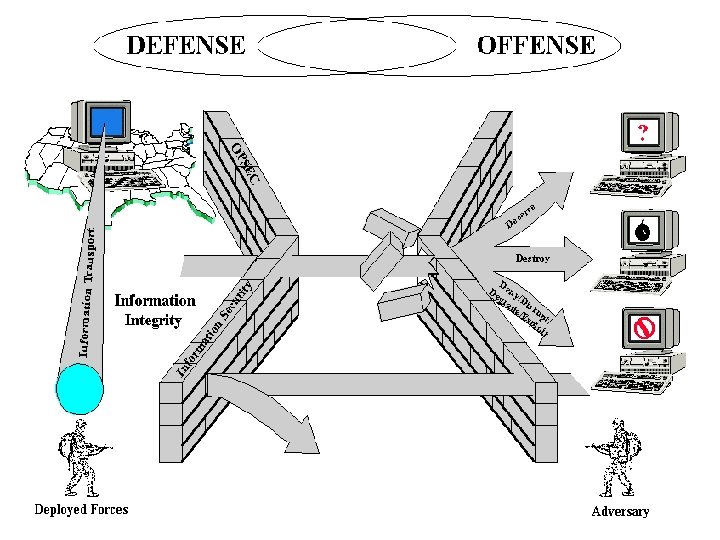
 Information Warfare • Information Warfare is any action to Deny, Exploit, Corrupt or Destroy the enemy’s information and its functions; protecting ourselves against those actions and exploiting our own military information functions
Information Warfare • Information Warfare is any action to Deny, Exploit, Corrupt or Destroy the enemy’s information and its functions; protecting ourselves against those actions and exploiting our own military information functions
 http: //www. strategypage. com/
http: //www. strategypage. com/
 Gulf War Example • During the Gulf War, the information offensives of the multilateral forces were significant. • 1) Computer viruses were used to destroy the computer systems of Iraq's air defense system and thus paralyze it, and • 2) Stealth aircraft were used to launch precision-guided bombs against the communications building and the command center, thus achieving information suppression. http: //ntrg. cs. tcd. ie/undergrad/4 ba 2. 02/infowar/mil
Gulf War Example • During the Gulf War, the information offensives of the multilateral forces were significant. • 1) Computer viruses were used to destroy the computer systems of Iraq's air defense system and thus paralyze it, and • 2) Stealth aircraft were used to launch precision-guided bombs against the communications building and the command center, thus achieving information suppression. http: //ntrg. cs. tcd. ie/undergrad/4 ba 2. 02/infowar/mil
 The War in Future • The war of the future may not be fought with missiles and tanks, but with computer viruses and logic bombs • Information warfare is a strategy for undermining a military enemy's data and information systems, while defending and leveraging one's own information edge • This type of war has no front line; potential battlefields are anywhere networked systems can be accessed --oil and gas pipelines, electric power grids, telephone switching
The War in Future • The war of the future may not be fought with missiles and tanks, but with computer viruses and logic bombs • Information warfare is a strategy for undermining a military enemy's data and information systems, while defending and leveraging one's own information edge • This type of war has no front line; potential battlefields are anywhere networked systems can be accessed --oil and gas pipelines, electric power grids, telephone switching
 The Future (contd. ) • Almost everything the modern military does-from designing weapons and guiding missiles to training, and mobilizing soldiers--depends upon computer-driven information networks. • Information warfare can take countless forms: trains and planes can be misrouted and caused to collide, stock exchanges can be sabotaged by electronic "sniffers" which disrupt international fund-transfer networks, and the signals of television and radio stations can be "jammed" and taken over and used for a misinformation campaign.
The Future (contd. ) • Almost everything the modern military does-from designing weapons and guiding missiles to training, and mobilizing soldiers--depends upon computer-driven information networks. • Information warfare can take countless forms: trains and planes can be misrouted and caused to collide, stock exchanges can be sabotaged by electronic "sniffers" which disrupt international fund-transfer networks, and the signals of television and radio stations can be "jammed" and taken over and used for a misinformation campaign.
 Incidences in Past • If this sounds like the stuff of sci-fi novels, consider that many of these types of attacks are already occurring with alarming frequency. • During the Gulf War, Dutch hackers stole information about U. S. troop movements from U. S. Defense Department computers and tried to sell it to the Iraqis, who thought it was a hoax and turned it down. • And in January 1999, U. S. Air Intelligence computers were hit by a coordinated attack, part of which appeared to come from Russia. http: //www. history. com/exhibits/science_war/i
Incidences in Past • If this sounds like the stuff of sci-fi novels, consider that many of these types of attacks are already occurring with alarming frequency. • During the Gulf War, Dutch hackers stole information about U. S. troop movements from U. S. Defense Department computers and tried to sell it to the Iraqis, who thought it was a hoax and turned it down. • And in January 1999, U. S. Air Intelligence computers were hit by a coordinated attack, part of which appeared to come from Russia. http: //www. history. com/exhibits/science_war/i
 Threatening Possibilities • Imagine the impact on the United States if Wall Street were held hostage by a computer virus which threatened to destroy financial records • Ponder the effect on military operations if all phone lines for a US unified command were suddenly rerouted to the local pizza delivery shop • Contemplate the impact on morale if a military unit's pay records suddenly disappeared
Threatening Possibilities • Imagine the impact on the United States if Wall Street were held hostage by a computer virus which threatened to destroy financial records • Ponder the effect on military operations if all phone lines for a US unified command were suddenly rerouted to the local pizza delivery shop • Contemplate the impact on morale if a military unit's pay records suddenly disappeared
 Electromagnetic bomb • An electromagnetic bomb or E-bomb is a weapon designed to disable electronics on a wide scale with an electromagnetic pulse. • This shock wave will induce heavy currents in all electronic equipment that mainly contains semiconducting and conducting materials. This produces immense heat that melts the circuitry inside. As such, while not being directly responsible for the loss of lives, these weapons are capable of disabling electronic systems on which industrialized nations are highly dependent. • Devices that are susceptible to this type of damage, from most to least vulnerable: • Integrated circuits (ICs), CPUs, silicon chips. • Transistors. • Vacuum tubes (also known as thermionic valves). • Inductors, motors. • EMP specialized nuclear weapons belong to the third generation of nuclear weapons. • http: //en. wikipedia. org/wiki/Category: Weapo
Electromagnetic bomb • An electromagnetic bomb or E-bomb is a weapon designed to disable electronics on a wide scale with an electromagnetic pulse. • This shock wave will induce heavy currents in all electronic equipment that mainly contains semiconducting and conducting materials. This produces immense heat that melts the circuitry inside. As such, while not being directly responsible for the loss of lives, these weapons are capable of disabling electronic systems on which industrialized nations are highly dependent. • Devices that are susceptible to this type of damage, from most to least vulnerable: • Integrated circuits (ICs), CPUs, silicon chips. • Transistors. • Vacuum tubes (also known as thermionic valves). • Inductors, motors. • EMP specialized nuclear weapons belong to the third generation of nuclear weapons. • http: //en. wikipedia. org/wiki/Category: Weapo
 News Clips http: //www. strategypage. com/
News Clips http: //www. strategypage. com/
 EMP Warhead Tested • January 11, 2006: Britain, which has taken the lead in developing EMP (Electro. Magnetic Pulse) devices, is testing a new EMP warhead with the United States. This weapon is intended for use in cruise missiles or UAVs, for attacks on enemy command control centers. Some of these operations are in bunkers that are well protected from bombs. But an EMP device could at least damage some of the electronics used in those locations. An EMP warhead would also be useful when the target is surrounded by civilians, an increasingly common tactic with some governments, who know that Western governments are more reluctant to kill non-military personnel. • As electronics got smaller over the last few decades, they became more vulnerable to EMP. You can build EMP shielding into electronic components, but this increases size, weight and cost. These are also usually custom jobs, not available for all components, or to all customers. Because of this, several countries have been researching ways to generate an EMP without a nuclear weapon. Britain has had the most success, and has successfully tested their device several times in the
EMP Warhead Tested • January 11, 2006: Britain, which has taken the lead in developing EMP (Electro. Magnetic Pulse) devices, is testing a new EMP warhead with the United States. This weapon is intended for use in cruise missiles or UAVs, for attacks on enemy command control centers. Some of these operations are in bunkers that are well protected from bombs. But an EMP device could at least damage some of the electronics used in those locations. An EMP warhead would also be useful when the target is surrounded by civilians, an increasingly common tactic with some governments, who know that Western governments are more reluctant to kill non-military personnel. • As electronics got smaller over the last few decades, they became more vulnerable to EMP. You can build EMP shielding into electronic components, but this increases size, weight and cost. These are also usually custom jobs, not available for all components, or to all customers. Because of this, several countries have been researching ways to generate an EMP without a nuclear weapon. Britain has had the most success, and has successfully tested their device several times in the
 Taiwan Creates Its Own Smart Bombs • • • March 21, 2006: Taiwan has been building their own version of the American JSOW (Joint Stand Off Weapon) Also called the AGM-154 A, the Taiwanese version is called the Wan Chien. Taiwan recently made a very public announcement about Wan Chien, which was another way of sending a "don't attack us" message to China. JSOW is basically a smart bomb with wings. That enables it to glide up to 70 kilometers from the aircraft dropping it, to a target on the ground. Range is about 25 kilometers if dropped from low altitude. JSOW also contains more elaborate fins and software that enables it to follow a specific route. Like the wingless JDAM smart bomb, JSOW uses GPS and inertial guidance (as a backup) to find its target. Like JDAM, JSOW hits within 30 feet of its aiming point. The U. S. pays about $250, 000 for each JSOW. The Taiwanese could use their Wan Chien. JSOW as a form of HARM to take out the latest Chinese air defense radars, by adding additional sensors to the guidance system. Taiwan is also building its own version of HARM, called Tien Chien 2 A. JDAM technology is a lot simpler than these two other projects, and Taiwan could easily design and build its own. Refusing to sell them just costs the U. S. export sales. On the other hand, it allows the United States to tell China that it didn't sell JDAM to Taiwan, thus defusing tensions over Taiwan. In reality, of course, Taiwan can just go build
Taiwan Creates Its Own Smart Bombs • • • March 21, 2006: Taiwan has been building their own version of the American JSOW (Joint Stand Off Weapon) Also called the AGM-154 A, the Taiwanese version is called the Wan Chien. Taiwan recently made a very public announcement about Wan Chien, which was another way of sending a "don't attack us" message to China. JSOW is basically a smart bomb with wings. That enables it to glide up to 70 kilometers from the aircraft dropping it, to a target on the ground. Range is about 25 kilometers if dropped from low altitude. JSOW also contains more elaborate fins and software that enables it to follow a specific route. Like the wingless JDAM smart bomb, JSOW uses GPS and inertial guidance (as a backup) to find its target. Like JDAM, JSOW hits within 30 feet of its aiming point. The U. S. pays about $250, 000 for each JSOW. The Taiwanese could use their Wan Chien. JSOW as a form of HARM to take out the latest Chinese air defense radars, by adding additional sensors to the guidance system. Taiwan is also building its own version of HARM, called Tien Chien 2 A. JDAM technology is a lot simpler than these two other projects, and Taiwan could easily design and build its own. Refusing to sell them just costs the U. S. export sales. On the other hand, it allows the United States to tell China that it didn't sell JDAM to Taiwan, thus defusing tensions over Taiwan. In reality, of course, Taiwan can just go build
 Smart Bomb vs Smart Shell Smackdown Coming Soon • • • June 2, 2006: After many delays, the U. S. Air Force has finally begun production of the 250 pound Small Diameter Bomb (SDB). The SDB was supposed to enter service in 2005, in the wake of the 2004 introduction of the 500 pound JDAM. But there were many technical problems with the SDB. That's because this was not just another "dumb bomb" with a GPS guidance kit attached. The SDB had a more effective warhead design and guidance system. It's shape is more like that of a missile than a bomb (70 inches long, 190 millimeters in diameter), with the guidance system built in. The smaller "bang" from the SDB will result in fewer civilian casualties when used in an urban area. Friendly troops can be closer to the target when an SDB explodes. While the 500, 1, 000 and 2, 000 pound bombs have a spectacular effect when they go off, they are often overkill. The troops on the ground would rather have more, smaller, GPS bombs available. This caused the 500 pound JDAM to get developed quickly and put into service. But what the air force really wants is to equip the B-1 with SDBs, as this bomber could carry as many as 216 of them. The new F-22 and F-35 warplanes are stealthy and normally carry their bombs internally. This limits how many they can carry, but with the SDB, an F-22 can carry eight of them. The Navy F-18 could easily carry 24 SDBs. The SDBs are carried on a special carriage, which holds four of them. The carriage is mounted on a bomber just like a single larger (500, 1, 000 or 2, 000) pound bomb would be. The SDB is basically an unpowered missile, which can glide long distances. This makes the SDB even more compact, capable and expensive (about $70, 000 each. ) JDAM (a guidance kit attached to a dumb bomb) only cost about $26, 000. The small wings allow the SDB to glide up to 70 -80 kilometers (from high
Smart Bomb vs Smart Shell Smackdown Coming Soon • • • June 2, 2006: After many delays, the U. S. Air Force has finally begun production of the 250 pound Small Diameter Bomb (SDB). The SDB was supposed to enter service in 2005, in the wake of the 2004 introduction of the 500 pound JDAM. But there were many technical problems with the SDB. That's because this was not just another "dumb bomb" with a GPS guidance kit attached. The SDB had a more effective warhead design and guidance system. It's shape is more like that of a missile than a bomb (70 inches long, 190 millimeters in diameter), with the guidance system built in. The smaller "bang" from the SDB will result in fewer civilian casualties when used in an urban area. Friendly troops can be closer to the target when an SDB explodes. While the 500, 1, 000 and 2, 000 pound bombs have a spectacular effect when they go off, they are often overkill. The troops on the ground would rather have more, smaller, GPS bombs available. This caused the 500 pound JDAM to get developed quickly and put into service. But what the air force really wants is to equip the B-1 with SDBs, as this bomber could carry as many as 216 of them. The new F-22 and F-35 warplanes are stealthy and normally carry their bombs internally. This limits how many they can carry, but with the SDB, an F-22 can carry eight of them. The Navy F-18 could easily carry 24 SDBs. The SDBs are carried on a special carriage, which holds four of them. The carriage is mounted on a bomber just like a single larger (500, 1, 000 or 2, 000) pound bomb would be. The SDB is basically an unpowered missile, which can glide long distances. This makes the SDB even more compact, capable and expensive (about $70, 000 each. ) JDAM (a guidance kit attached to a dumb bomb) only cost about $26, 000. The small wings allow the SDB to glide up to 70 -80 kilometers (from high
 Lasers and GPS Kill Together • September 23, 2006: The U. S. Air Force has completed flight tests of the LJDAM (Laser Joint Direct Attack Munition). The main difference between JDAM and LJDAM is the sensor unit. The GPS sensor on JDAM has a laser seeker sensor added, turning the JDAM into the LJDAM. The aircraft dropping the bomb uses its laser designator to track the moving target, and the LFDAM bomb hits the moving target. Last year, an LJDAM hit a vehicle moving at 24 kilometers an hour. Earlier this year, the latest version of LJDAM hit a vehicle moving at 40 kilometers an hour. The most recent test was with a target moving at 64 kilometers an hour. Because of the string of successful tests, LJDAM will probably enter service next year. It will be useful against enemy convoys of moving vehicles, since the smallest LJDAM uses a 500 pound bomb. Aircraft equipped with LJDAM will not have to rely on missiles to hit moving targets. Moreover, the LJDAM is also more accurate against stationary targets, which is sometimes a major factor during urban combat.
Lasers and GPS Kill Together • September 23, 2006: The U. S. Air Force has completed flight tests of the LJDAM (Laser Joint Direct Attack Munition). The main difference between JDAM and LJDAM is the sensor unit. The GPS sensor on JDAM has a laser seeker sensor added, turning the JDAM into the LJDAM. The aircraft dropping the bomb uses its laser designator to track the moving target, and the LFDAM bomb hits the moving target. Last year, an LJDAM hit a vehicle moving at 24 kilometers an hour. Earlier this year, the latest version of LJDAM hit a vehicle moving at 40 kilometers an hour. The most recent test was with a target moving at 64 kilometers an hour. Because of the string of successful tests, LJDAM will probably enter service next year. It will be useful against enemy convoys of moving vehicles, since the smallest LJDAM uses a 500 pound bomb. Aircraft equipped with LJDAM will not have to rely on missiles to hit moving targets. Moreover, the LJDAM is also more accurate against stationary targets, which is sometimes a major factor during urban combat.
 New Tools • October 24, 2006: The U. S. Department of Defense, which has been working on Information War strategy and tactics for two decades now, has developed a new doctrine for this form of combat. The new ideas including better tracking of who is doing what, and making Information War tools available to more troops, at all levels. The new program will spend at least $330 million over the next six years. • One of the first tasks is to build a system for monitoring the "battlefield. " That is, a computer based system that will monitor what's happening in the media around the world, as it applies to Department of Defense operations. Such systems have long been in use by firms in the world financial markets, and it may well be that the Department of Defense got some of these new ideas from there. Meanwhile, the Information War tactics at all levels of the military will be upgraded and coordinated to make the most of positive media, and limit damage from negative stories (especially ones that are false or misleading. ) • This new approach was prompted by several factors. First, Islamic terrorists have been very successful at using, and exploiting, the media. Second, the troops have been taking
New Tools • October 24, 2006: The U. S. Department of Defense, which has been working on Information War strategy and tactics for two decades now, has developed a new doctrine for this form of combat. The new ideas including better tracking of who is doing what, and making Information War tools available to more troops, at all levels. The new program will spend at least $330 million over the next six years. • One of the first tasks is to build a system for monitoring the "battlefield. " That is, a computer based system that will monitor what's happening in the media around the world, as it applies to Department of Defense operations. Such systems have long been in use by firms in the world financial markets, and it may well be that the Department of Defense got some of these new ideas from there. Meanwhile, the Information War tactics at all levels of the military will be upgraded and coordinated to make the most of positive media, and limit damage from negative stories (especially ones that are false or misleading. ) • This new approach was prompted by several factors. First, Islamic terrorists have been very successful at using, and exploiting, the media. Second, the troops have been taking
 First True Battlefield Internet Used • December 8, 2006: The U. S. Army conducted its first successful test of CNRS (Communications Network Radio System. ) This is basically battlefield wi-fi, which supplies everyone on the network, including infantry, with access to a common network. The test used Stryker armored vehicles, which already have a pretty heavy duty commo setup, and radio equipped infantry. Taking a cue from the Internet, CNRS is self-forming and self-healing. That means, every user who logs on to the net, can serve as an access point for anyone within range. This is called a MESH network, and is being used to establish wi-fi over a large area, for things like municipal wi-fi. The military is taking a lot of civilian Internet technology, adding some
First True Battlefield Internet Used • December 8, 2006: The U. S. Army conducted its first successful test of CNRS (Communications Network Radio System. ) This is basically battlefield wi-fi, which supplies everyone on the network, including infantry, with access to a common network. The test used Stryker armored vehicles, which already have a pretty heavy duty commo setup, and radio equipped infantry. Taking a cue from the Internet, CNRS is self-forming and self-healing. That means, every user who logs on to the net, can serve as an access point for anyone within range. This is called a MESH network, and is being used to establish wi-fi over a large area, for things like municipal wi-fi. The military is taking a lot of civilian Internet technology, adding some
 HTS-7 • October 19, 2006: The U. S. Air Force received the first fifteen new HARM Targeting System HTS-7 electronic warfare pods, and got them ahead of time (which is always a good sign). The HARM (High speed, Anti-Radiation Missile) has been around since the 1960 s, and is fired at enemy radars and other transmitters (radio), usually as part of shutting down enemy air defenses. The HTS is the device you mount on the electronic warfare aircraft (in this case, usually an F-16) that is carrying the HARMs and leading missions to destroy enemy air defenses. The latest HTS ("Revision 7", thus HTS 7), has better electronics and software for detecting enemy transmissions before the aircraft is close enough to launch a HARM (about 150 kilometers for the current
HTS-7 • October 19, 2006: The U. S. Air Force received the first fifteen new HARM Targeting System HTS-7 electronic warfare pods, and got them ahead of time (which is always a good sign). The HARM (High speed, Anti-Radiation Missile) has been around since the 1960 s, and is fired at enemy radars and other transmitters (radio), usually as part of shutting down enemy air defenses. The HTS is the device you mount on the electronic warfare aircraft (in this case, usually an F-16) that is carrying the HARMs and leading missions to destroy enemy air defenses. The latest HTS ("Revision 7", thus HTS 7), has better electronics and software for detecting enemy transmissions before the aircraft is close enough to launch a HARM (about 150 kilometers for the current
 Seven Ounce Wrist Computer • June 26, 2006: Noting the U. S. Army's interest in "wearable computers, " Eurotech has created a seven ounce PC that you wear on your wrist. The Zypad WL 1000 uses a 32 bit, 400 Mhz CPU, can run Linux or Windows CE, has 64 MB of flash RAM and ROM, an SD card slot for more memory (a gigabyte or more), a 3. 5 inch touch screen (240 x 320 QVGA). There also eleven backlit keys. The rechargeable battery claims up to eight hours operation. Also included are GPS, Bluetooth, 802. 11 g wifi, a USB 1. 1 port and stereo audio input and output. The system automatically goes into standby mode when the users arm is at his side. There is also a tilt switch mode, which reports the users location if the user falls down and remains motionless for a certain length of time. • The manufacturer sees a large military market, in all the services, and among combat and support troops. Industrial, medical and emergency services are also seen as users. The current version sells for $2, 500 and has been shown at several trade shows over the last few months.
Seven Ounce Wrist Computer • June 26, 2006: Noting the U. S. Army's interest in "wearable computers, " Eurotech has created a seven ounce PC that you wear on your wrist. The Zypad WL 1000 uses a 32 bit, 400 Mhz CPU, can run Linux or Windows CE, has 64 MB of flash RAM and ROM, an SD card slot for more memory (a gigabyte or more), a 3. 5 inch touch screen (240 x 320 QVGA). There also eleven backlit keys. The rechargeable battery claims up to eight hours operation. Also included are GPS, Bluetooth, 802. 11 g wifi, a USB 1. 1 port and stereo audio input and output. The system automatically goes into standby mode when the users arm is at his side. There is also a tilt switch mode, which reports the users location if the user falls down and remains motionless for a certain length of time. • The manufacturer sees a large military market, in all the services, and among combat and support troops. Industrial, medical and emergency services are also seen as users. The current version sells for $2, 500 and has been shown at several trade shows over the last few months.
 Boeing, IBM join hands on military information technology • Boeing and IBM said on Monday that they will join hands to develop ground and space-based systems to enhance US military communications, intelligence operations and homeland security. • The two companies said their agreement to form a strategic alliance brings together the second largest US defense contractor and the leader in information technology to address an estimated 200 billion US dollar market. • Through a 10 -year alliance, Boeing and IBM will develop advanced digital communications and information technologies for current and future US military and intelligence systems. • "These technologies will be critical for network-centric operations where satellites, aircraft, ships and submarines - as well as tanks, radios and even handheld computers - share information using the same interfaces, standards or protocols, " IBM said in a statement. • The conflicts of the future will be less dependent upon who has the most physical assets such as ships, planes and tanks, but determined by who has the best information and the most efficient means of sharing it among all elements of the fighting
Boeing, IBM join hands on military information technology • Boeing and IBM said on Monday that they will join hands to develop ground and space-based systems to enhance US military communications, intelligence operations and homeland security. • The two companies said their agreement to form a strategic alliance brings together the second largest US defense contractor and the leader in information technology to address an estimated 200 billion US dollar market. • Through a 10 -year alliance, Boeing and IBM will develop advanced digital communications and information technologies for current and future US military and intelligence systems. • "These technologies will be critical for network-centric operations where satellites, aircraft, ships and submarines - as well as tanks, radios and even handheld computers - share information using the same interfaces, standards or protocols, " IBM said in a statement. • The conflicts of the future will be less dependent upon who has the most physical assets such as ships, planes and tanks, but determined by who has the best information and the most efficient means of sharing it among all elements of the fighting
 Thank You
Thank You


