36befd7e3edee23d324b92f819263326.ppt
- Количество слайдов: 37
 Software Design Methodologies: UML in Action Dr. Mohamed Fayad, J. D. Edwards Professor Department of Computer Science & Engineering University of Nebraska, Lincoln Ferguson Hall, P. O. Box 880115 Lincoln, NE 68588 -0115 http: //www. cse. unl. edu/~fayad 3/16/2018
Software Design Methodologies: UML in Action Dr. Mohamed Fayad, J. D. Edwards Professor Department of Computer Science & Engineering University of Nebraska, Lincoln Ferguson Hall, P. O. Box 880115 Lincoln, NE 68588 -0115 http: //www. cse. unl. edu/~fayad 3/16/2018
 Lesson 5: Object Identification - 2 2 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 2 Object Identification- 2
Lesson 5: Object Identification - 2 2 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 2 Object Identification- 2
 Lesson Objectives + Learn how to identify: Associations and aggregations Attributes Behaviors Inheritance + Understand how to use the following approaches: Use Case CRC Questioning Techniques + Understand how to refine objects and associations + Learn how to define responsibility & collaborations + Learn how to eliminate unnecessary classes, associations, and attributes 3/16/2018 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 3 3 Object Identification- 2
Lesson Objectives + Learn how to identify: Associations and aggregations Attributes Behaviors Inheritance + Understand how to use the following approaches: Use Case CRC Questioning Techniques + Understand how to refine objects and associations + Learn how to define responsibility & collaborations + Learn how to eliminate unnecessary classes, associations, and attributes 3/16/2018 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 3 3 Object Identification- 2
 Automated Teller Machine (ATM) Stop bothering me! I told you I don’t have any money! 4 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 4 Object Identification- 2
Automated Teller Machine (ATM) Stop bothering me! I told you I don’t have any money! 4 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 4 Object Identification- 2
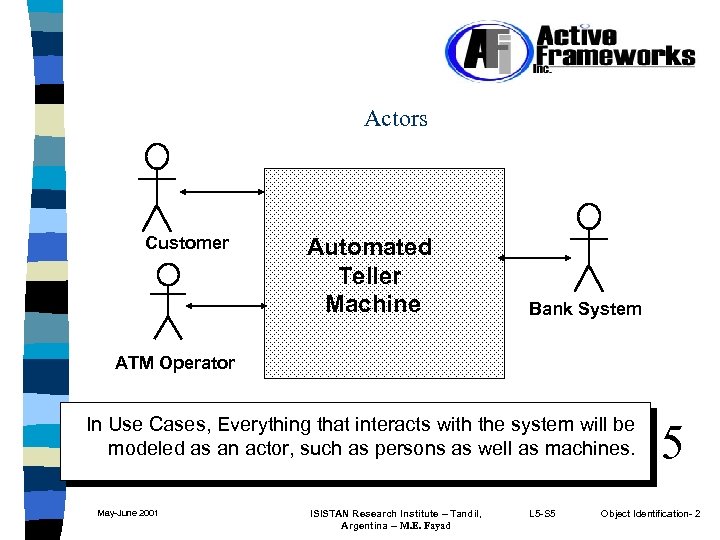 Actors Customer Automated Teller Machine Bank System ATM Operator In Use Cases, Everything that interacts with the system will be modeled as an actor, such as persons as well as machines. May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 5 5 Object Identification- 2
Actors Customer Automated Teller Machine Bank System ATM Operator In Use Cases, Everything that interacts with the system will be modeled as an actor, such as persons as well as machines. May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 5 5 Object Identification- 2
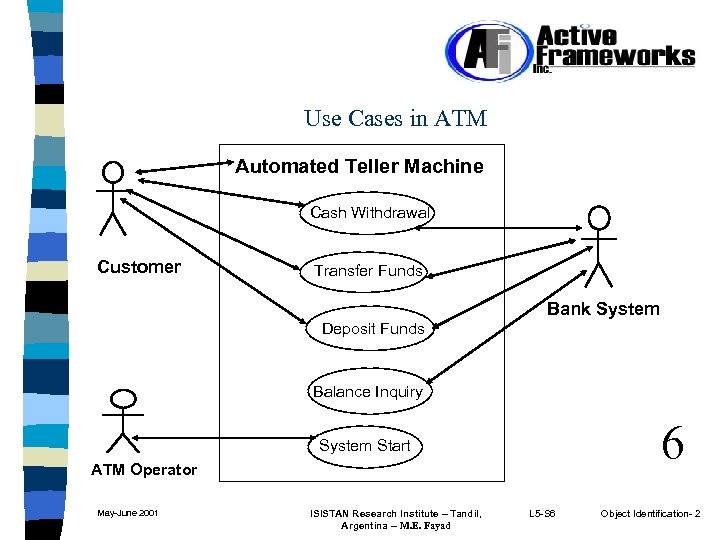 Use Cases in ATM Automated Teller Machine Cash Withdrawal Customer Transfer Funds Bank System Deposit Funds Balance Inquiry 6 System Start ATM Operator May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 6 Object Identification- 2
Use Cases in ATM Automated Teller Machine Cash Withdrawal Customer Transfer Funds Bank System Deposit Funds Balance Inquiry 6 System Start ATM Operator May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 6 Object Identification- 2
 A Use Case Description: Cash Withdrawal Use Case: Cash Withdrawal n When a customer inserts a card in the ATM, the machine reads the code from the card and checks if it is a valid card. If the card is valid then the machine queries the customer for a PIN number, else the card is ejected. n When the machine matches customer coded in the PIN number, the machine checks the validity of the PIN number. If the PIN number is correct and matches the card number then the machine asks for the desired transaction the customer wishes to perform. n When the customer selects cash withdrawal the machine asks for the desired amount with a warning indicating only multiple of $10 is allowed. n When. . May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 7 7 Object Identification- 2
A Use Case Description: Cash Withdrawal Use Case: Cash Withdrawal n When a customer inserts a card in the ATM, the machine reads the code from the card and checks if it is a valid card. If the card is valid then the machine queries the customer for a PIN number, else the card is ejected. n When the machine matches customer coded in the PIN number, the machine checks the validity of the PIN number. If the PIN number is correct and matches the card number then the machine asks for the desired transaction the customer wishes to perform. n When the customer selects cash withdrawal the machine asks for the desired amount with a warning indicating only multiple of $10 is allowed. n When. . May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 7 7 Object Identification- 2
 Candidate Objects n n n n n Account ATM Balance Inquiry Bank Card Reader Cancel Key Cash Dispenser Deposit Slot Deposit Funds Display Screen (Bank System Interface) Menu (Graphical User Interface) May-June 2001 • User Message • Numeric Keypad • Numeric Input Key • PIN • Cash • Receipt Printer • Special Input Key • Transfer Funds • Cash Withdrawal ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 8 L 5 -S 8 Object Identification- 2
Candidate Objects n n n n n Account ATM Balance Inquiry Bank Card Reader Cancel Key Cash Dispenser Deposit Slot Deposit Funds Display Screen (Bank System Interface) Menu (Graphical User Interface) May-June 2001 • User Message • Numeric Keypad • Numeric Input Key • PIN • Cash • Receipt Printer • Special Input Key • Transfer Funds • Cash Withdrawal ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 8 L 5 -S 8 Object Identification- 2
 System Responsibilities & Collaborations n Define Responsibilities – What are the goals of the system – What must objects know to meet goals – What steps must each object accomplish n Determine Collaborations – Decompose responsibilities into interactions among objects – Define clients and servers 9 – Where should knowledge be held May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 9 Object Identification- 2
System Responsibilities & Collaborations n Define Responsibilities – What are the goals of the system – What must objects know to meet goals – What steps must each object accomplish n Determine Collaborations – Decompose responsibilities into interactions among objects – Define clients and servers 9 – Where should knowledge be held May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 9 Object Identification- 2
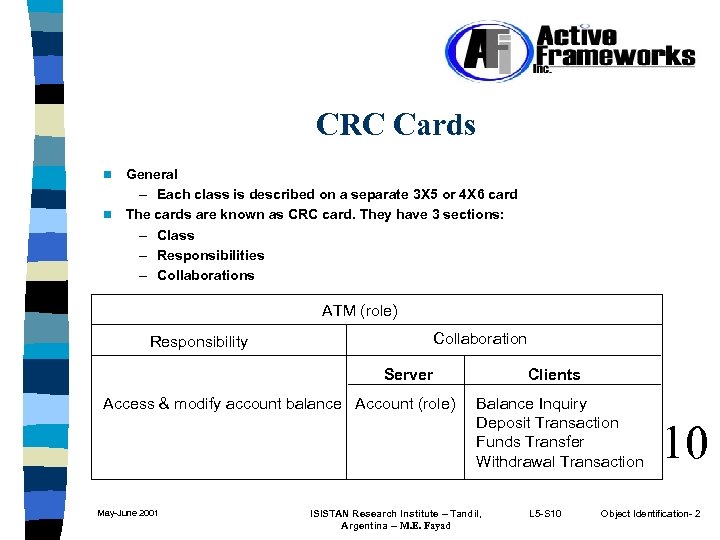 CRC Cards General – Each class is described on a separate 3 X 5 or 4 X 6 card n The cards are known as CRC card. They have 3 sections: – Class – Responsibilities – Collaborations n ATM (role) Responsibility Collaboration Server Access & modify account balance Account (role) May-June 2001 Clients Balance Inquiry Deposit Transaction Funds Transfer Withdrawal Transaction ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 10 10 Object Identification- 2
CRC Cards General – Each class is described on a separate 3 X 5 or 4 X 6 card n The cards are known as CRC card. They have 3 sections: – Class – Responsibilities – Collaborations n ATM (role) Responsibility Collaboration Server Access & modify account balance Account (role) May-June 2001 Clients Balance Inquiry Deposit Transaction Funds Transfer Withdrawal Transaction ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 10 10 Object Identification- 2
 Other Techniques Help Refine Objects Ü Generalize and Specialize objects Ü Associate Objects Ü Recognize Accidental Objects Ü Challenging and Testing Objects Ü Ask Questions May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 11 L 5 -S 11 Object Identification- 2
Other Techniques Help Refine Objects Ü Generalize and Specialize objects Ü Associate Objects Ü Recognize Accidental Objects Ü Challenging and Testing Objects Ü Ask Questions May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 11 L 5 -S 11 Object Identification- 2
 Explore Generalizations and Specializations n Generalization exposes commonalities n Exercise helps to identify new classes n Considerations for generalizations and specializations – Is it in the problem domain? – Is it within the system’s responsibilities? – Will there be inheritance? May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 12 L 5 -S 12 Object Identification- 2
Explore Generalizations and Specializations n Generalization exposes commonalities n Exercise helps to identify new classes n Considerations for generalizations and specializations – Is it in the problem domain? – Is it within the system’s responsibilities? – Will there be inheritance? May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 12 L 5 -S 12 Object Identification- 2
 Avoid Accidental Objects n Essential objects represent genuine high-level abstractions n Accidental objects represent qualitative judgments May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 13 13 Object Identification- 2
Avoid Accidental Objects n Essential objects represent genuine high-level abstractions n Accidental objects represent qualitative judgments May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 13 13 Object Identification- 2
 Challenge Objects n Needed Remembrance -- attributes n Needed Behavior -- methods n Usually Multiple Services per Object n Usually More than One Object per Class 14 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 14 Object Identification- 2
Challenge Objects n Needed Remembrance -- attributes n Needed Behavior -- methods n Usually Multiple Services per Object n Usually More than One Object per Class 14 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 14 Object Identification- 2
 Other Object Tests n Uniformity Test – Each instance must have the same set of characteristics and be subject to the same rules - Car license n More than a Name Test – Every object has attributes, if not it is probably an attribute of another object -- home address n Or Test – If inclusion criteria should not use “OR” in any significant way -- driver’s license number or learner’s permit number n More Than a List Test – If inclusion criteria is only a list of instances -- decadent foods includes croissant , cappuccino, chocolate pie, ice cream. May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 15 15 Object Identification- 2
Other Object Tests n Uniformity Test – Each instance must have the same set of characteristics and be subject to the same rules - Car license n More than a Name Test – Every object has attributes, if not it is probably an attribute of another object -- home address n Or Test – If inclusion criteria should not use “OR” in any significant way -- driver’s license number or learner’s permit number n More Than a List Test – If inclusion criteria is only a list of instances -- decadent foods includes croissant , cappuccino, chocolate pie, ice cream. May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 15 15 Object Identification- 2
 Final Object Checklist ü Something universal and real for reuse ü Should encapsulate some reasonably complex behavior to justify existence ü Methods that don’t make use of its current class’s own attributes is probably encapsulated in the wrong object. ü Small and simple stable interfaces ü Self sufficient and complete May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 16 16 Object Identification- 2
Final Object Checklist ü Something universal and real for reuse ü Should encapsulate some reasonably complex behavior to justify existence ü Methods that don’t make use of its current class’s own attributes is probably encapsulated in the wrong object. ü Small and simple stable interfaces ü Self sufficient and complete May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 16 16 Object Identification- 2
 Questioning Techniques Help Elicit Domain Knowledge n Play Twenty Questions – Is it animal, vegetable, or mineral? – Does it have fur or feathers? – Can it fly? n Define Boundaries – What else? – What about. . ? n Quantify Qualities as Attributes – How fast? – How hot? May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 17 L 5 -S 17 Object Identification- 2
Questioning Techniques Help Elicit Domain Knowledge n Play Twenty Questions – Is it animal, vegetable, or mineral? – Does it have fur or feathers? – Can it fly? n Define Boundaries – What else? – What about. . ? n Quantify Qualities as Attributes – How fast? – How hot? May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 17 L 5 -S 17 Object Identification- 2
 Eliminating Unnecessary Associations n Irrelevant Associations – outside problem domain n Implementation Associations – Examples: concurrent process, contains a list n Associations Between Eliminated Classes May-June 2001 18 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 18 Object Identification- 2
Eliminating Unnecessary Associations n Irrelevant Associations – outside problem domain n Implementation Associations – Examples: concurrent process, contains a list n Associations Between Eliminated Classes May-June 2001 18 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 18 Object Identification- 2
 Eliminating Unnecessary Associations (cont’d) n Actions or Transient Events – Examples: “Interacts with the Robot”, “ATM accepts cash card. ” n Ternary Associations – Decompose as binary associations or rephrase to one binary association. n Derived Associations – These are redundant – Examples: “Younger than. . ” derived from age May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 19 19 Object Identification- 2
Eliminating Unnecessary Associations (cont’d) n Actions or Transient Events – Examples: “Interacts with the Robot”, “ATM accepts cash card. ” n Ternary Associations – Decompose as binary associations or rephrase to one binary association. n Derived Associations – These are redundant – Examples: “Younger than. . ” derived from age May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 19 19 Object Identification- 2
 Refine Association List Choose meaningful association names n Add role names where appropriate n Add attributes or associations which qualify existing associations n – Example: “Standard Oil of Ohio” uses state attribute to qualify company name. Specify one-to-many and many-to-many associations in the class diagram n Add missing associations n – Not in problem statement – from knowledge of application domain May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 20 L 5 -S 20 Object Identification- 2
Refine Association List Choose meaningful association names n Add role names where appropriate n Add attributes or associations which qualify existing associations n – Example: “Standard Oil of Ohio” uses state attribute to qualify company name. Specify one-to-many and many-to-many associations in the class diagram n Add missing associations n – Not in problem statement – from knowledge of application domain May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 20 L 5 -S 20 Object Identification- 2
 Identifying Attributes n Attributes can be thought as a simple association with a value which is not an object – Examples: name, age, weight n Usually corresponding to nouns followed by possessive phrases – Examples: “color of the car”, “age of the donor” Less likely to be fully described in the problem statement n Included in the class box diagram n Not as relevant to the problem structure as associations n May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 21 21 Object Identification- 2
Identifying Attributes n Attributes can be thought as a simple association with a value which is not an object – Examples: name, age, weight n Usually corresponding to nouns followed by possessive phrases – Examples: “color of the car”, “age of the donor” Less likely to be fully described in the problem statement n Included in the class box diagram n Not as relevant to the problem structure as associations n May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 21 21 Object Identification- 2
 Attribute Types Œ Descriptive Attributes Naming Attributes Ž Referential Attributes 22 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 22 Object Identification- 2
Attribute Types Œ Descriptive Attributes Naming Attributes Ž Referential Attributes 22 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 22 Object Identification- 2
 Descriptive Attributes n Provide facts intrinsic to each instance of the object. – Examples Account. balance, Cat. weight – If the value of a descriptive attribute changes, it means only that some aspect of an instance has changed, but the instance is still the same instance. May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 23 23 Object Identification- 2
Descriptive Attributes n Provide facts intrinsic to each instance of the object. – Examples Account. balance, Cat. weight – If the value of a descriptive attribute changes, it means only that some aspect of an instance has changed, but the instance is still the same instance. May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 23 23 Object Identification- 2
 Naming Attributes n Are used to name or label instances. – Examples: Account. number, Flight. number – Names are typically somewhat arbitrary – Naming attributes are frequently used as an identifier or part of an identifier. – If the vale of a naming attribute changes, it means only that a new name has been given to exactly the same instance May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 24 24 Object Identification- 2
Naming Attributes n Are used to name or label instances. – Examples: Account. number, Flight. number – Names are typically somewhat arbitrary – Naming attributes are frequently used as an identifier or part of an identifier. – If the vale of a naming attribute changes, it means only that a new name has been given to exactly the same instance May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 24 24 Object Identification- 2
 Referential Attributes n Are used to tie an instance of one object to an instance of another. – Examples: Cat. owner name indicates which person owns this cat. – If the vale of a referential attribute changes, it means that different instances are now being associated. 25 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 25 Object Identification- 2
Referential Attributes n Are used to tie an instance of one object to an instance of another. – Examples: Cat. owner name indicates which person owns this cat. – If the vale of a referential attribute changes, it means that different instances are now being associated. 25 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 25 Object Identification- 2
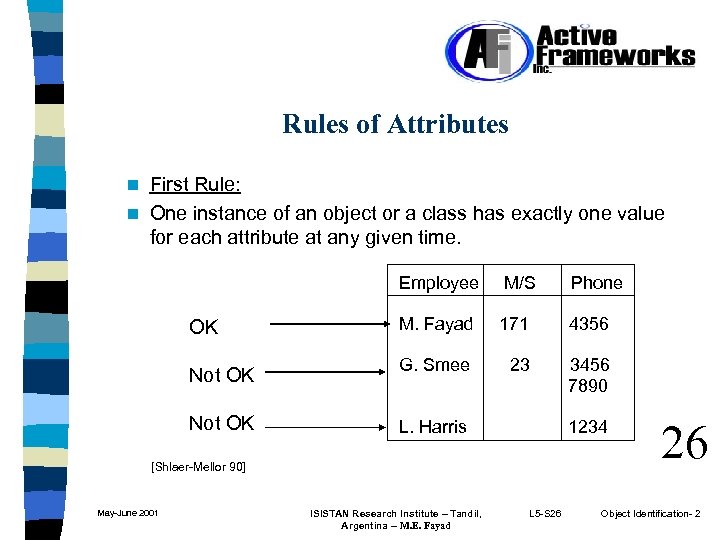 Rules of Attributes First Rule: n One instance of an object or a class has exactly one value for each attribute at any given time. n Employee OK Not OK M/S Phone M. Fayad 171 4356 G. Smee 23 3456 7890 L. Harris 1234 [Shlaer-Mellor 90] May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 26 26 Object Identification- 2
Rules of Attributes First Rule: n One instance of an object or a class has exactly one value for each attribute at any given time. n Employee OK Not OK M/S Phone M. Fayad 171 4356 G. Smee 23 3456 7890 L. Harris 1234 [Shlaer-Mellor 90] May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 26 26 Object Identification- 2
 Rules of Attributes (cont’d) n Second Rule: n An attribute must contain no internal structure n Examples: – Age, balance, size are all OK. – A name consists of first name, middle initial, and last name (Not OK) – An address contains house number, street name, city, state, zip code, and country name (Not OK) May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 27 27 Object Identification- 2
Rules of Attributes (cont’d) n Second Rule: n An attribute must contain no internal structure n Examples: – Age, balance, size are all OK. – A name consists of first name, middle initial, and last name (Not OK) – An address contains house number, street name, city, state, zip code, and country name (Not OK) May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 27 27 Object Identification- 2
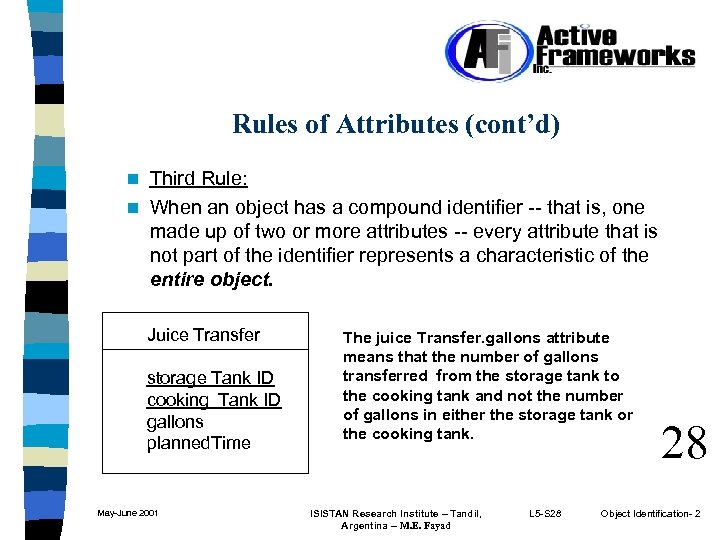 Rules of Attributes (cont’d) Third Rule: n When an object has a compound identifier -- that is, one made up of two or more attributes -- every attribute that is not part of the identifier represents a characteristic of the entire object. n Juice Transfer storage Tank ID cooking Tank ID gallons planned. Time May-June 2001 The juice Transfer. gallons attribute means that the number of gallons transferred from the storage tank to the cooking tank and not the number of gallons in either the storage tank or the cooking tank. ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 28 28 Object Identification- 2
Rules of Attributes (cont’d) Third Rule: n When an object has a compound identifier -- that is, one made up of two or more attributes -- every attribute that is not part of the identifier represents a characteristic of the entire object. n Juice Transfer storage Tank ID cooking Tank ID gallons planned. Time May-June 2001 The juice Transfer. gallons attribute means that the number of gallons transferred from the storage tank to the cooking tank and not the number of gallons in either the storage tank or the cooking tank. ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 28 28 Object Identification- 2
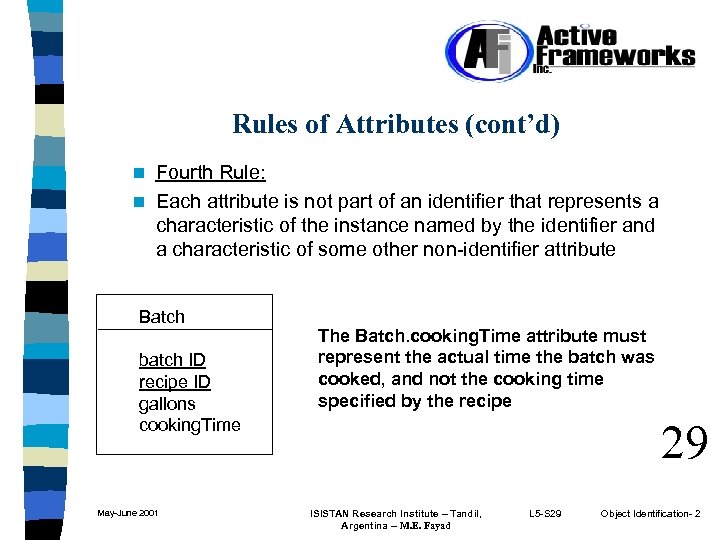 Rules of Attributes (cont’d) Fourth Rule: n Each attribute is not part of an identifier that represents a characteristic of the instance named by the identifier and a characteristic of some other non-identifier attribute n Batch batch ID recipe ID gallons cooking. Time May-June 2001 The Batch. cooking. Time attribute must represent the actual time the batch was cooked, and not the cooking time specified by the recipe 29 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 29 Object Identification- 2
Rules of Attributes (cont’d) Fourth Rule: n Each attribute is not part of an identifier that represents a characteristic of the instance named by the identifier and a characteristic of some other non-identifier attribute n Batch batch ID recipe ID gallons cooking. Time May-June 2001 The Batch. cooking. Time attribute must represent the actual time the batch was cooked, and not the cooking time specified by the recipe 29 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 29 Object Identification- 2
 Eliminating Unnecessary Attributes n Do not keep attributes that have an object as a value, they are associations n Do not keep attributes that depend on a context, these are qualifiers for associations n If an object can have more that one name, then the name qualifies an association of that object with another May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 30 30 Object Identification- 2
Eliminating Unnecessary Attributes n Do not keep attributes that have an object as a value, they are associations n Do not keep attributes that depend on a context, these are qualifiers for associations n If an object can have more that one name, then the name qualifies an association of that object with another May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 30 30 Object Identification- 2
 Eliminating Unnecessary Attributes (cont’d) n Do not put attributes of the association in one or the other of the objects involved in the association, put the attributes in the association itself n Eliminate attributes which are only used internally by the object n Keep initial analysis of attributes at a high level n Eliminate attributes which are too low level n Attributes which are in some instances of a class, but not in others, indicate that the class should be split into two or more classes May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 31 31 Object Identification- 2
Eliminating Unnecessary Attributes (cont’d) n Do not put attributes of the association in one or the other of the objects involved in the association, put the attributes in the association itself n Eliminate attributes which are only used internally by the object n Keep initial analysis of attributes at a high level n Eliminate attributes which are too low level n Attributes which are in some instances of a class, but not in others, indicate that the class should be split into two or more classes May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 31 31 Object Identification- 2
 Identifying Inheritance n Identify classes which share common information n Three basic approaches: n Bottom Up – Look for classes with repeated associations, attributes or behaviors, and group together into higher level classes – This approach is easier for inexperienced modelers n Top Down – Look for Noun phrases describing different kinds of things in the problem statement. – Examples: Family cars, Sports cars, Luxury cars n Combination of the two approaches works the best. – Do Top Down when doing initial analysis – Identify repeated information in the late passes. May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 32 32 Object Identification- 2
Identifying Inheritance n Identify classes which share common information n Three basic approaches: n Bottom Up – Look for classes with repeated associations, attributes or behaviors, and group together into higher level classes – This approach is easier for inexperienced modelers n Top Down – Look for Noun phrases describing different kinds of things in the problem statement. – Examples: Family cars, Sports cars, Luxury cars n Combination of the two approaches works the best. – Do Top Down when doing initial analysis – Identify repeated information in the late passes. May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 32 32 Object Identification- 2
 Identifying Inheritance (cont’d) n Always use the “AKO” test – All inheritance specifications should identify one or more classes which are “A Kind Of” a higher level class. – NEVER use inheritance for “Part / Part-of” relationships n Use multiple inheritance only when necessary – Some object-oriented programming languages do not even have this feature. 33 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 33 Object Identification- 2
Identifying Inheritance (cont’d) n Always use the “AKO” test – All inheritance specifications should identify one or more classes which are “A Kind Of” a higher level class. – NEVER use inheritance for “Part / Part-of” relationships n Use multiple inheritance only when necessary – Some object-oriented programming languages do not even have this feature. 33 May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 33 Object Identification- 2
 Identifying Behaviors n Done in latest stages n List of behaviors can become large and get detailed quickly. n May correspond to queries about attributes and associations – Operations to read or write attribute or association value – Examples: user name, property value, etc. n May correspond to events or activities – Examples: begin simulation, alert, calculate balance, computer distance May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 34 34 Object Identification- 2
Identifying Behaviors n Done in latest stages n List of behaviors can become large and get detailed quickly. n May correspond to queries about attributes and associations – Operations to read or write attribute or association value – Examples: user name, property value, etc. n May correspond to events or activities – Examples: begin simulation, alert, calculate balance, computer distance May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 34 34 Object Identification- 2
 Experience and Domain Knowledge n Good objects come from language of domain – If you are not an expert -- consult users n Experience will tune decisions – Slowly at first – Much faster later Just do it! May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 35 L 5 -S 35 Object Identification- 2
Experience and Domain Knowledge n Good objects come from language of domain – If you are not an expert -- consult users n Experience will tune decisions – Slowly at first – Much faster later Just do it! May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad 35 L 5 -S 35 Object Identification- 2
 Discussion Questions • • Describe third norm for testing objects • What are the differences between essential objects and accidental objects • What are questioning techniques and their purposes? • Describe how do you identify: associations , aggregations, inheritance, attributes, and behaviors • Describe how to refine objects and associations • May-June 2001 Define with examples: CRC cards, associate objects, referential attributes. Explain how to define responsibilities and collaborations ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 36 36 Object Identification- 2
Discussion Questions • • Describe third norm for testing objects • What are the differences between essential objects and accidental objects • What are questioning techniques and their purposes? • Describe how do you identify: associations , aggregations, inheritance, attributes, and behaviors • Describe how to refine objects and associations • May-June 2001 Define with examples: CRC cards, associate objects, referential attributes. Explain how to define responsibilities and collaborations ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 36 36 Object Identification- 2
 Questions for the Next Lecture Define: – Guidelines – Heuristics What do you think of these heuristics – A designer should distribute system intelligence uniformly among the top level classes in the system. – A designer should have 4. 6 top level classes per 1, 000 lines of code. – Eliminate classes that are outside the system May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 37 37 Object Identification- 2
Questions for the Next Lecture Define: – Guidelines – Heuristics What do you think of these heuristics – A designer should distribute system intelligence uniformly among the top level classes in the system. – A designer should have 4. 6 top level classes per 1, 000 lines of code. – Eliminate classes that are outside the system May-June 2001 ISISTAN Research Institute – Tandil, Argentina -- M. E. Fayad L 5 -S 37 37 Object Identification- 2


