7f5304e7abfeda1d2056d33f7ce55ad7.ppt
- Количество слайдов: 36
 Software Architectures Chapter 2: Architectural Styles CSE 333 Prof. Steven A. Demurjian, Sr. Computer Science & Engineering Department The University of Connecticut 371 Fairfield Road, Box U-255 Storrs, CT 06269 -2155 steve@engr. uconn. edu http: //www. engr. uconn. edu/~stev e (860) 486 - 4818 Copyright © 2000 by S. Demurjian, Storrs, CT. SWA-1. 1
Software Architectures Chapter 2: Architectural Styles CSE 333 Prof. Steven A. Demurjian, Sr. Computer Science & Engineering Department The University of Connecticut 371 Fairfield Road, Box U-255 Storrs, CT 06269 -2155 steve@engr. uconn. edu http: //www. engr. uconn. edu/~stev e (860) 486 - 4818 Copyright © 2000 by S. Demurjian, Storrs, CT. SWA-1. 1
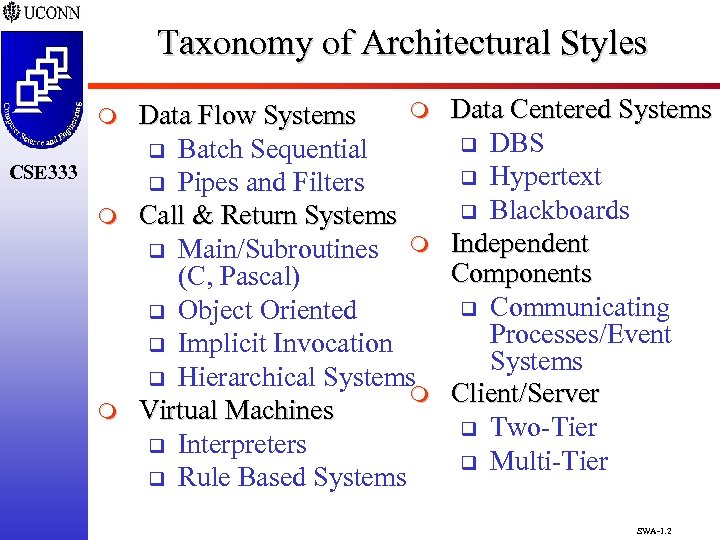 Taxonomy of Architectural Styles m CSE 333 m m m Data Flow Systems q Batch Sequential q Pipes and Filters Call & Return Systems m q Main/Subroutines (C, Pascal) q Object Oriented q Implicit Invocation q Hierarchical Systems m Virtual Machines q Interpreters q Rule Based Systems Data Centered Systems q DBS q Hypertext q Blackboards Independent Components q Communicating Processes/Event Systems Client/Server q Two-Tier q Multi-Tier SWA-1. 2
Taxonomy of Architectural Styles m CSE 333 m m m Data Flow Systems q Batch Sequential q Pipes and Filters Call & Return Systems m q Main/Subroutines (C, Pascal) q Object Oriented q Implicit Invocation q Hierarchical Systems m Virtual Machines q Interpreters q Rule Based Systems Data Centered Systems q DBS q Hypertext q Blackboards Independent Components q Communicating Processes/Event Systems Client/Server q Two-Tier q Multi-Tier SWA-1. 2
 Taxonomy of Architectural Styles m Establish Framework of … q Components CSE 333 Ø Building Blocks for Constructing Systems Ø A Major Unit of Functionality Ø Examples Include: Client, Server, Filter, Layer, DB q Connectors Ø Defining the Ways that Components Interact Ø What are the Protocols that Mandate the Allowable Interactions Among Components? Ø How are Protocols Enforced at Run/Design Time? Ø Examples Include: Procedure Call, Event Broadcast, DB Protocol, Pipe SWA-1. 3
Taxonomy of Architectural Styles m Establish Framework of … q Components CSE 333 Ø Building Blocks for Constructing Systems Ø A Major Unit of Functionality Ø Examples Include: Client, Server, Filter, Layer, DB q Connectors Ø Defining the Ways that Components Interact Ø What are the Protocols that Mandate the Allowable Interactions Among Components? Ø How are Protocols Enforced at Run/Design Time? Ø Examples Include: Procedure Call, Event Broadcast, DB Protocol, Pipe SWA-1. 3
 Overall Framework Consider a Question-Based Approach m CSE 333 m m m What Is the Design Vocabulary? q Connectors and Components What Are Allowable Structural Patterns? q Constraints on Combining Components & Connectors What Is the Underlying Conceptual Model? q Von Newman, Parallel, Agent, Etc. What Are Essential Invariants of a Style? q Limits on Allowable Components & Connectors Common Examples of Usage Advantages and Disadvantages of a Style Common Specializations of a Style SWA-1. 4
Overall Framework Consider a Question-Based Approach m CSE 333 m m m What Is the Design Vocabulary? q Connectors and Components What Are Allowable Structural Patterns? q Constraints on Combining Components & Connectors What Is the Underlying Conceptual Model? q Von Newman, Parallel, Agent, Etc. What Are Essential Invariants of a Style? q Limits on Allowable Components & Connectors Common Examples of Usage Advantages and Disadvantages of a Style Common Specializations of a Style SWA-1. 4
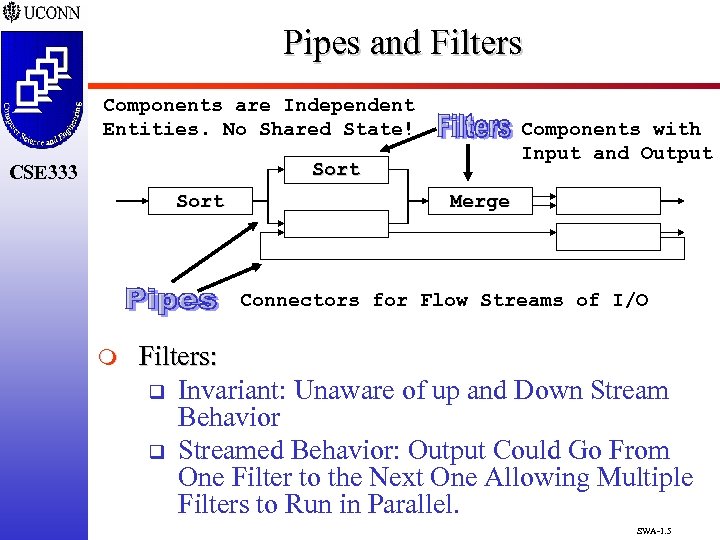 Pipes and Filters Components are Independent Entities. No Shared State! Components with Input and Output Sort CSE 333 Sort Merge Connectors for Flow Streams of I/O m Filters: q Invariant: Unaware of up and Down Stream Behavior q Streamed Behavior: Output Could Go From One Filter to the Next One Allowing Multiple Filters to Run in Parallel. SWA-1. 5
Pipes and Filters Components are Independent Entities. No Shared State! Components with Input and Output Sort CSE 333 Sort Merge Connectors for Flow Streams of I/O m Filters: q Invariant: Unaware of up and Down Stream Behavior q Streamed Behavior: Output Could Go From One Filter to the Next One Allowing Multiple Filters to Run in Parallel. SWA-1. 5
 Pipes and Filters m CSE 333 m m Possible Specializations: q Pipelines - Linear Sequence q Bounded - Limits on Data Amounts q Typed Pipes - Known Data Format What is a Classic Example? Other Examples: q Compilers q Sequential Processes q Parallel Processes SWA-1. 6
Pipes and Filters m CSE 333 m m Possible Specializations: q Pipelines - Linear Sequence q Bounded - Limits on Data Amounts q Typed Pipes - Known Data Format What is a Classic Example? Other Examples: q Compilers q Sequential Processes q Parallel Processes SWA-1. 6
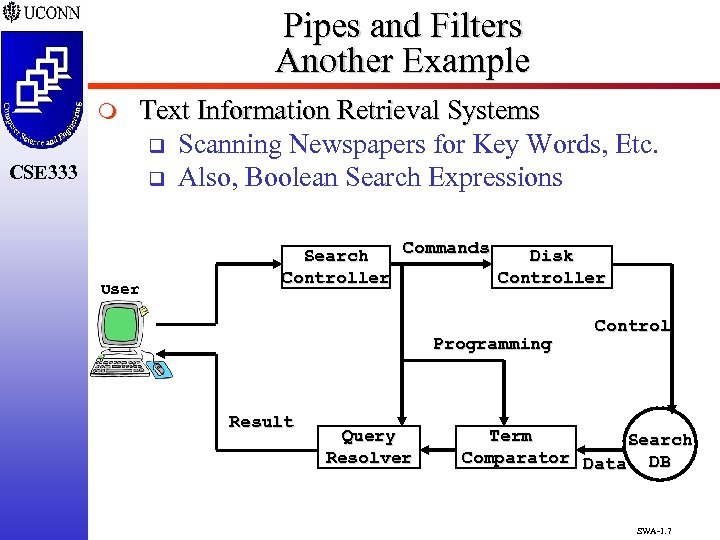 Pipes and Filters Another Example m CSE 333 Text Information Retrieval Systems q Scanning Newspapers for Key Words, Etc. q Also, Boolean Search Expressions User Commands Search Disk Controller Programming Result Query Resolver Control Term Search Comparator Data DB SWA-1. 7
Pipes and Filters Another Example m CSE 333 Text Information Retrieval Systems q Scanning Newspapers for Key Words, Etc. q Also, Boolean Search Expressions User Commands Search Disk Controller Programming Result Query Resolver Control Term Search Comparator Data DB SWA-1. 7
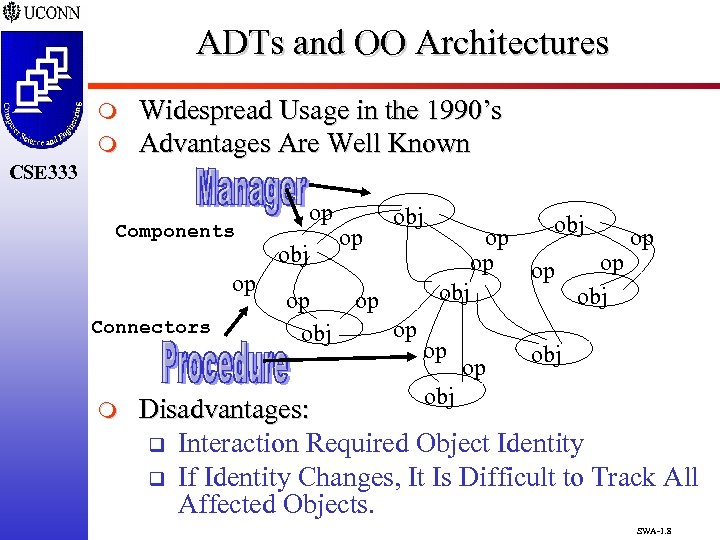 ADTs and OO Architectures m m Widespread Usage in the 1990’s Advantages Are Well Known CSE 333 Components op Connectors m op obj op op op obj obj op op obj Disadvantages: q Interaction Required Object Identity q If Identity Changes, It Is Difficult to Track All Affected Objects. SWA-1. 8
ADTs and OO Architectures m m Widespread Usage in the 1990’s Advantages Are Well Known CSE 333 Components op Connectors m op obj op op op obj obj op op obj Disadvantages: q Interaction Required Object Identity q If Identity Changes, It Is Difficult to Track All Affected Objects. SWA-1. 8
 Implicit Invocation m CSE 333 m m Similar to OO in the Sense that Components Can Call Services on Other Components How Does this Work? q Components Have List of Events they can Raise and List of Procedures to Handle Events q When Event is Raised, it is Broadcast q All Components that Have Procedure to Handle Broadcast Event will Act Upon it q The Component That Raised the Event has no Knowledge of Which Component(s) will Handle Event What are Some Examples? SWA-1. 9
Implicit Invocation m CSE 333 m m Similar to OO in the Sense that Components Can Call Services on Other Components How Does this Work? q Components Have List of Events they can Raise and List of Procedures to Handle Events q When Event is Raised, it is Broadcast q All Components that Have Procedure to Handle Broadcast Event will Act Upon it q The Component That Raised the Event has no Knowledge of Which Component(s) will Handle Event What are Some Examples? SWA-1. 9
 Implicit Invocation m CSE 333 m Advantages q No Need to Know the Targeted Components q Single Event can Impact Multiple Components q New Event Handlers can Easily be Added q New Events Can then be Raised Disadvantages q No Control Over the Order of Processing When an Event is Raised q No Control Over “Who” and “How Many” Process Events q Very Non-Deterministic System Behavior SWA-1. 10
Implicit Invocation m CSE 333 m Advantages q No Need to Know the Targeted Components q Single Event can Impact Multiple Components q New Event Handlers can Easily be Added q New Events Can then be Raised Disadvantages q No Control Over the Order of Processing When an Event is Raised q No Control Over “Who” and “How Many” Process Events q Very Non-Deterministic System Behavior SWA-1. 10
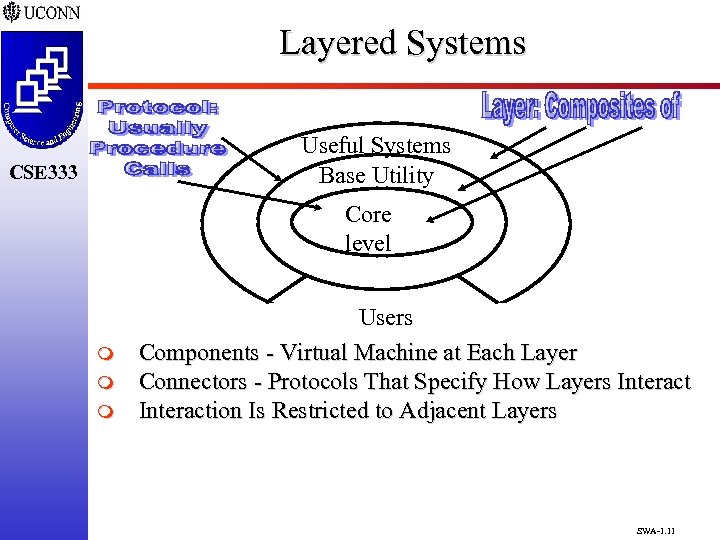 Layered Systems Useful Systems Base Utility CSE 333 Core level m m m Users Components - Virtual Machine at Each Layer Connectors - Protocols That Specify How Layers Interaction Is Restricted to Adjacent Layers SWA-1. 11
Layered Systems Useful Systems Base Utility CSE 333 Core level m m m Users Components - Virtual Machine at Each Layer Connectors - Protocols That Specify How Layers Interaction Is Restricted to Adjacent Layers SWA-1. 11
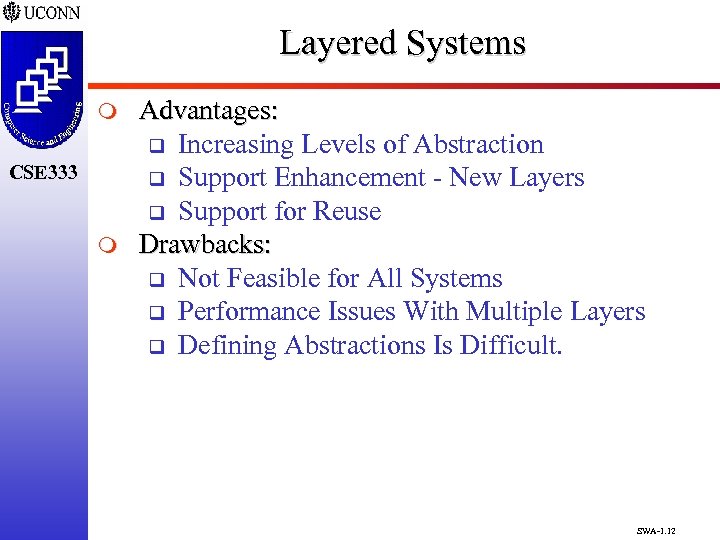 Layered Systems m CSE 333 m Advantages: q Increasing Levels of Abstraction q Support Enhancement - New Layers q Support for Reuse Drawbacks: q Not Feasible for All Systems q Performance Issues With Multiple Layers q Defining Abstractions Is Difficult. SWA-1. 12
Layered Systems m CSE 333 m Advantages: q Increasing Levels of Abstraction q Support Enhancement - New Layers q Support for Reuse Drawbacks: q Not Feasible for All Systems q Performance Issues With Multiple Layers q Defining Abstractions Is Difficult. SWA-1. 12
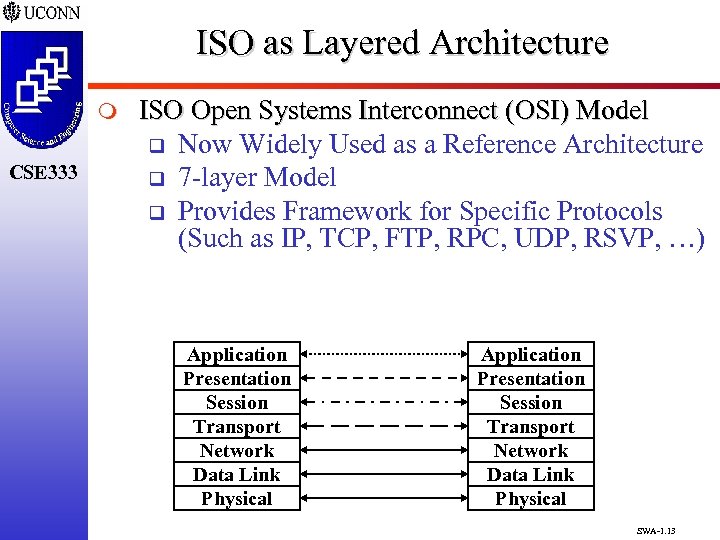 ISO as Layered Architecture m CSE 333 ISO Open Systems Interconnect (OSI) Model q Now Widely Used as a Reference Architecture q 7 -layer Model q Provides Framework for Specific Protocols (Such as IP, TCP, FTP, RPC, UDP, RSVP, …) Application Presentation Session Transport Network Data Link Physical SWA-1. 13
ISO as Layered Architecture m CSE 333 ISO Open Systems Interconnect (OSI) Model q Now Widely Used as a Reference Architecture q 7 -layer Model q Provides Framework for Specific Protocols (Such as IP, TCP, FTP, RPC, UDP, RSVP, …) Application Presentation Session Transport Network Data Link Physical SWA-1. 13
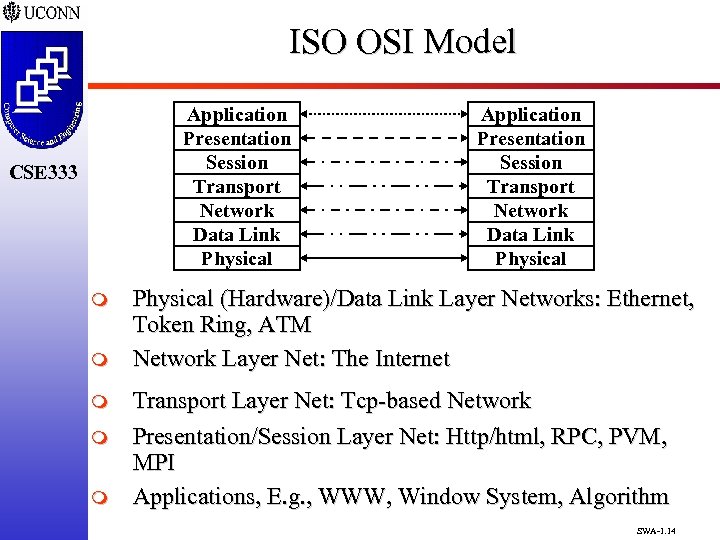 ISO OSI Model Application Presentation Session Transport Network Data Link Physical CSE 333 m m m Application Presentation Session Transport Network Data Link Physical (Hardware)/Data Link Layer Networks: Ethernet, Token Ring, ATM Network Layer Net: The Internet Transport Layer Net: Tcp-based Network Presentation/Session Layer Net: Http/html, RPC, PVM, MPI Applications, E. g. , WWW, Window System, Algorithm SWA-1. 14
ISO OSI Model Application Presentation Session Transport Network Data Link Physical CSE 333 m m m Application Presentation Session Transport Network Data Link Physical (Hardware)/Data Link Layer Networks: Ethernet, Token Ring, ATM Network Layer Net: The Internet Transport Layer Net: Tcp-based Network Presentation/Session Layer Net: Http/html, RPC, PVM, MPI Applications, E. g. , WWW, Window System, Algorithm SWA-1. 14
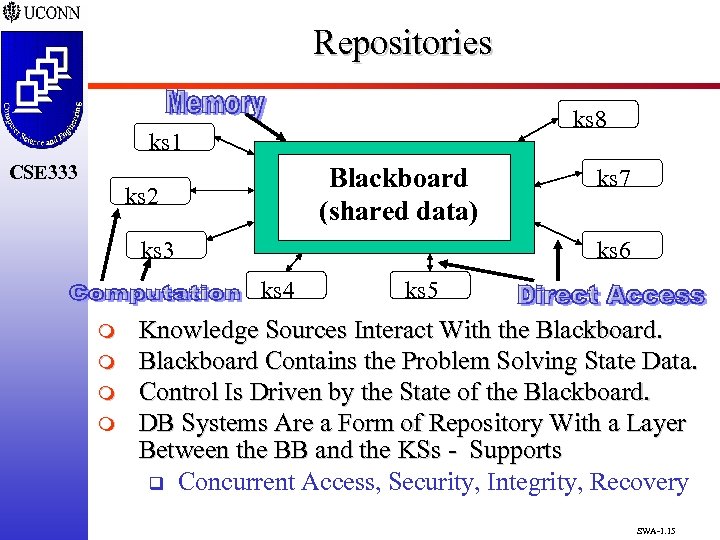 Repositories ks 8 ks 1 CSE 333 Blackboard (shared data) ks 2 ks 3 ks 6 ks 4 m m ks 7 ks 5 Knowledge Sources Interact With the Blackboard Contains the Problem Solving State Data. Control Is Driven by the State of the Blackboard. DB Systems Are a Form of Repository With a Layer Between the BB and the KSs - Supports q Concurrent Access, Security, Integrity, Recovery SWA-1. 15
Repositories ks 8 ks 1 CSE 333 Blackboard (shared data) ks 2 ks 3 ks 6 ks 4 m m ks 7 ks 5 Knowledge Sources Interact With the Blackboard Contains the Problem Solving State Data. Control Is Driven by the State of the Blackboard. DB Systems Are a Form of Repository With a Layer Between the BB and the KSs - Supports q Concurrent Access, Security, Integrity, Recovery SWA-1. 15
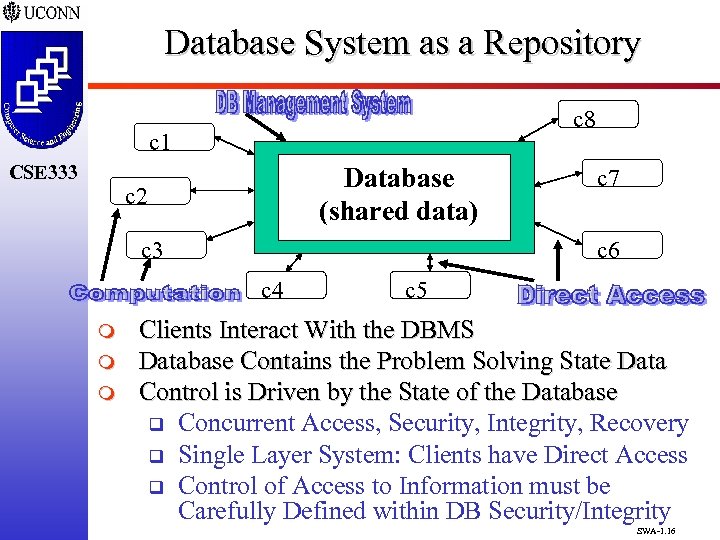 Database System as a Repository c 8 c 1 CSE 333 Database (shared data) c 2 c 3 c 6 c 4 m m m c 7 c 5 Clients Interact With the DBMS Database Contains the Problem Solving State Data Control is Driven by the State of the Database q Concurrent Access, Security, Integrity, Recovery q Single Layer System: Clients have Direct Access q Control of Access to Information must be Carefully Defined within DB Security/Integrity SWA-1. 16
Database System as a Repository c 8 c 1 CSE 333 Database (shared data) c 2 c 3 c 6 c 4 m m m c 7 c 5 Clients Interact With the DBMS Database Contains the Problem Solving State Data Control is Driven by the State of the Database q Concurrent Access, Security, Integrity, Recovery q Single Layer System: Clients have Direct Access q Control of Access to Information must be Carefully Defined within DB Security/Integrity SWA-1. 16
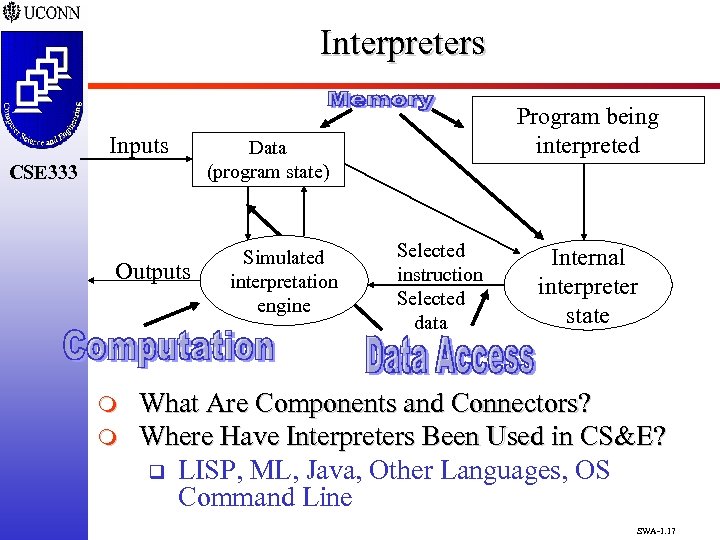 Interpreters Inputs CSE 333 Outputs m m Program being interpreted Data (program state) Simulated interpretation engine Selected instruction Selected data Internal interpreter state What Are Components and Connectors? Where Have Interpreters Been Used in CS&E? q LISP, ML, Java, Other Languages, OS Command Line SWA-1. 17
Interpreters Inputs CSE 333 Outputs m m Program being interpreted Data (program state) Simulated interpretation engine Selected instruction Selected data Internal interpreter state What Are Components and Connectors? Where Have Interpreters Been Used in CS&E? q LISP, ML, Java, Other Languages, OS Command Line SWA-1. 17
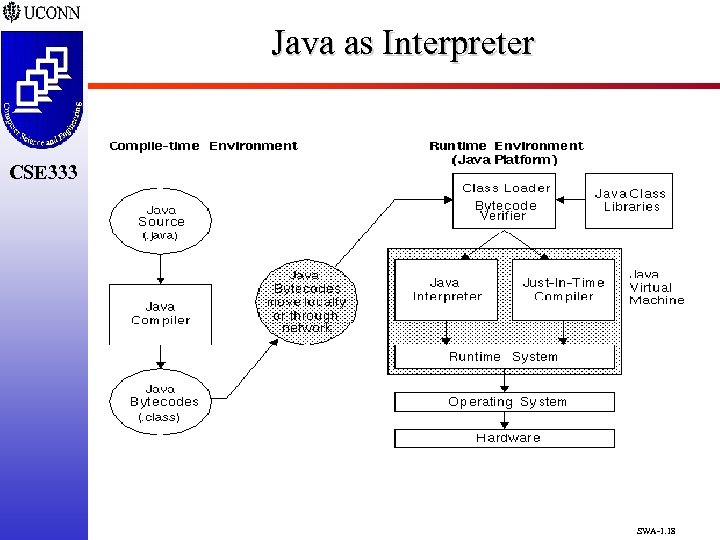 Java as Interpreter CSE 333 SWA-1. 18
Java as Interpreter CSE 333 SWA-1. 18
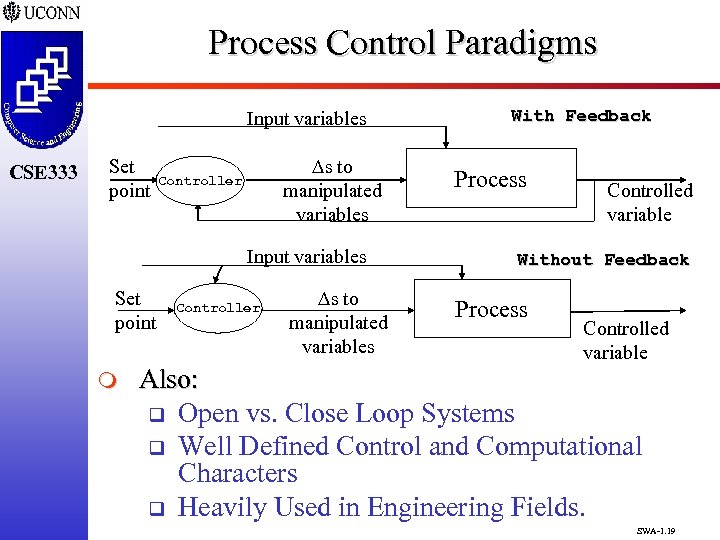 Process Control Paradigms Input variables CSE 333 Set point Ds to manipulated variables Controller Input variables Set point m Controller Ds to manipulated variables With Feedback Process Controlled variable Without Feedback Process Controlled variable Also: q Open vs. Close Loop Systems q Well Defined Control and Computational Characters q Heavily Used in Engineering Fields. SWA-1. 19
Process Control Paradigms Input variables CSE 333 Set point Ds to manipulated variables Controller Input variables Set point m Controller Ds to manipulated variables With Feedback Process Controlled variable Without Feedback Process Controlled variable Also: q Open vs. Close Loop Systems q Well Defined Control and Computational Characters q Heavily Used in Engineering Fields. SWA-1. 19
 Process Architecture UML Statechart Diagram? CSE 333 SWA-1. 20
Process Architecture UML Statechart Diagram? CSE 333 SWA-1. 20
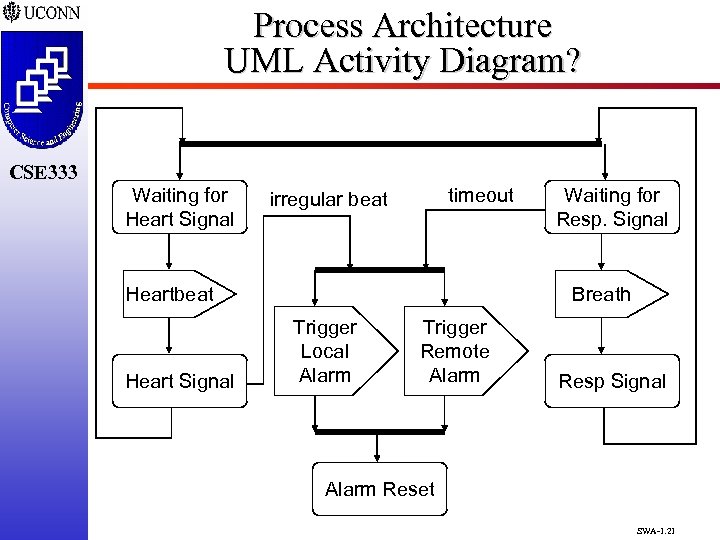 Process Architecture UML Activity Diagram? CSE 333 Waiting for Heart Signal timeout irregular beat Heart Signal Waiting for Resp. Signal Breath Trigger Local Alarm Trigger Remote Alarm Resp Signal Alarm Reset SWA-1. 21
Process Architecture UML Activity Diagram? CSE 333 Waiting for Heart Signal timeout irregular beat Heart Signal Waiting for Resp. Signal Breath Trigger Local Alarm Trigger Remote Alarm Resp Signal Alarm Reset SWA-1. 21
 Client/Server Single and Multi-Tier Architectures m CSE 333 m Widespread use in Practice for All Types of Distributed Systems and Applications Two Kinds of Components q Servers: Provide Services - May be Unaware of Clients Ø Web Servers (unaware? ) Ø Database Servers and Functional Servers (aware? ) q Clients: Request Services from Servers Ø Must Identify Servers Ø May Need to Identify Self Ø A Server Can be Client of Another Server SWA-1. 22
Client/Server Single and Multi-Tier Architectures m CSE 333 m Widespread use in Practice for All Types of Distributed Systems and Applications Two Kinds of Components q Servers: Provide Services - May be Unaware of Clients Ø Web Servers (unaware? ) Ø Database Servers and Functional Servers (aware? ) q Clients: Request Services from Servers Ø Must Identify Servers Ø May Need to Identify Self Ø A Server Can be Client of Another Server SWA-1. 22
 Client/Server Single and Multi-Tier Architectures m CSE 333 m m Normally, Clients and Servers are Independent Processes Running in Parallel Connectors Provide Means for Service Requests and Answers to be Passes Among Clients/Servers Connectors May be RPC, RMI, etc. Advantages q Parallelism, Independence q Separation of Concerns, Abstraction q Others? Disadvantages q Complex Implementation Mechanisms q Scalability, Correctness, Real-Time Limits q Others? SWA-1. 23
Client/Server Single and Multi-Tier Architectures m CSE 333 m m Normally, Clients and Servers are Independent Processes Running in Parallel Connectors Provide Means for Service Requests and Answers to be Passes Among Clients/Servers Connectors May be RPC, RMI, etc. Advantages q Parallelism, Independence q Separation of Concerns, Abstraction q Others? Disadvantages q Complex Implementation Mechanisms q Scalability, Correctness, Real-Time Limits q Others? SWA-1. 23
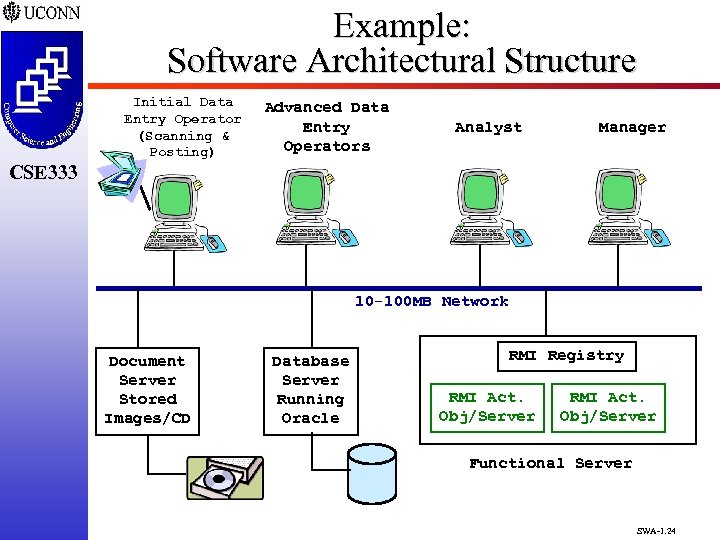 Example: Software Architectural Structure Initial Data Entry Operator (Scanning & Posting) Advanced Data Entry Operators Analyst Manager CSE 333 10 -100 MB Network Document Server Stored Images/CD Database Server Running Oracle RMI Registry RMI Act. Obj/Server Functional Server SWA-1. 24
Example: Software Architectural Structure Initial Data Entry Operator (Scanning & Posting) Advanced Data Entry Operators Analyst Manager CSE 333 10 -100 MB Network Document Server Stored Images/CD Database Server Running Oracle RMI Registry RMI Act. Obj/Server Functional Server SWA-1. 24
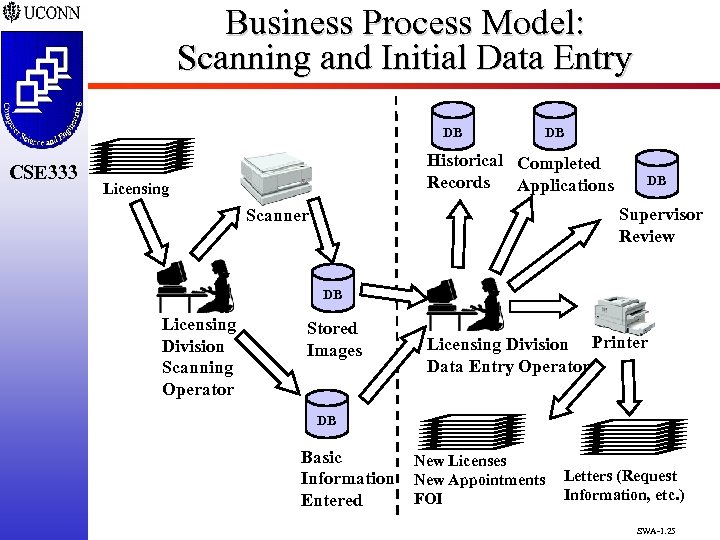 Business Process Model: Scanning and Initial Data Entry DB CSE 333 DB Historical Completed Records Applications Licensing DB Supervisor Review Scanner DB Licensing Division Scanning Operator Stored Images Licensing Division Printer Data Entry Operator DB Basic Information Entered New Licenses New Appointments FOI Letters (Request Information, etc. ) SWA-1. 25
Business Process Model: Scanning and Initial Data Entry DB CSE 333 DB Historical Completed Records Applications Licensing DB Supervisor Review Scanner DB Licensing Division Scanning Operator Stored Images Licensing Division Printer Data Entry Operator DB Basic Information Entered New Licenses New Appointments FOI Letters (Request Information, etc. ) SWA-1. 25
 Two-Tier Architecture m CSE 333 m m Small Manufacturer Previously on C++ New Order Entry, Inventory, and Invoicing Applications in Java Programming Language Existing Customer and Order Database Most of Business Logic in Stored Procedures Tool-generated GUI Forms for Java Objects SWA-1. 26
Two-Tier Architecture m CSE 333 m m Small Manufacturer Previously on C++ New Order Entry, Inventory, and Invoicing Applications in Java Programming Language Existing Customer and Order Database Most of Business Logic in Stored Procedures Tool-generated GUI Forms for Java Objects SWA-1. 26
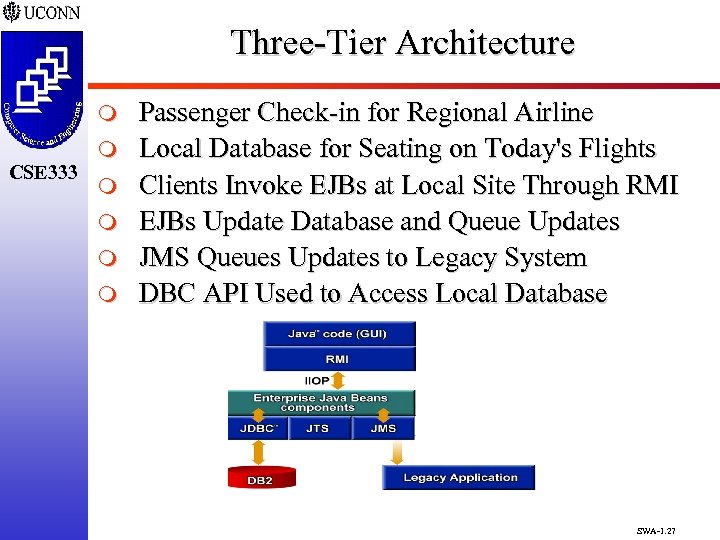 Three-Tier Architecture m CSE 333 m m m Passenger Check-in for Regional Airline Local Database for Seating on Today's Flights Clients Invoke EJBs at Local Site Through RMI EJBs Update Database and Queue Updates JMS Queues Updates to Legacy System DBC API Used to Access Local Database SWA-1. 27
Three-Tier Architecture m CSE 333 m m m Passenger Check-in for Regional Airline Local Database for Seating on Today's Flights Clients Invoke EJBs at Local Site Through RMI EJBs Update Database and Queue Updates JMS Queues Updates to Legacy System DBC API Used to Access Local Database SWA-1. 27
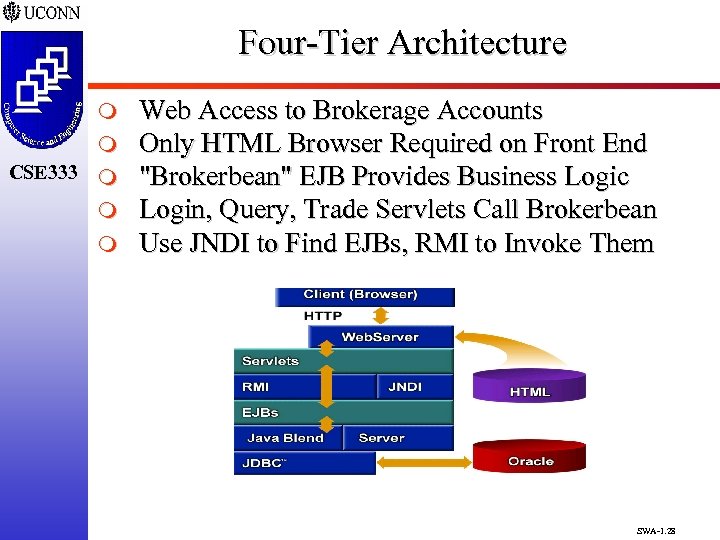 Four-Tier Architecture m m CSE 333 m m m Web Access to Brokerage Accounts Only HTML Browser Required on Front End "Brokerbean" EJB Provides Business Logic Login, Query, Trade Servlets Call Brokerbean Use JNDI to Find EJBs, RMI to Invoke Them SWA-1. 28
Four-Tier Architecture m m CSE 333 m m m Web Access to Brokerage Accounts Only HTML Browser Required on Front End "Brokerbean" EJB Provides Business Logic Login, Query, Trade Servlets Call Brokerbean Use JNDI to Find EJBs, RMI to Invoke Them SWA-1. 28
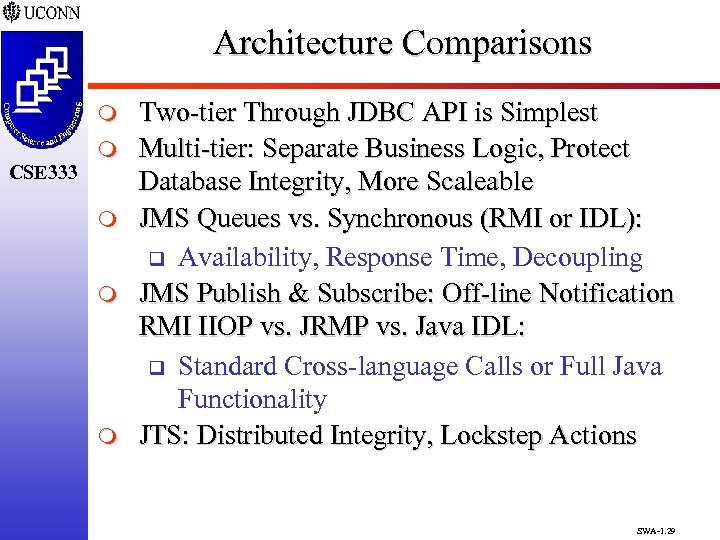 Architecture Comparisons m CSE 333 m m Two-tier Through JDBC API is Simplest Multi-tier: Separate Business Logic, Protect Database Integrity, More Scaleable JMS Queues vs. Synchronous (RMI or IDL): q Availability, Response Time, Decoupling JMS Publish & Subscribe: Off-line Notification RMI IIOP vs. JRMP vs. Java IDL: q Standard Cross-language Calls or Full Java Functionality JTS: Distributed Integrity, Lockstep Actions SWA-1. 29
Architecture Comparisons m CSE 333 m m Two-tier Through JDBC API is Simplest Multi-tier: Separate Business Logic, Protect Database Integrity, More Scaleable JMS Queues vs. Synchronous (RMI or IDL): q Availability, Response Time, Decoupling JMS Publish & Subscribe: Off-line Notification RMI IIOP vs. JRMP vs. Java IDL: q Standard Cross-language Calls or Full Java Functionality JTS: Distributed Integrity, Lockstep Actions SWA-1. 29
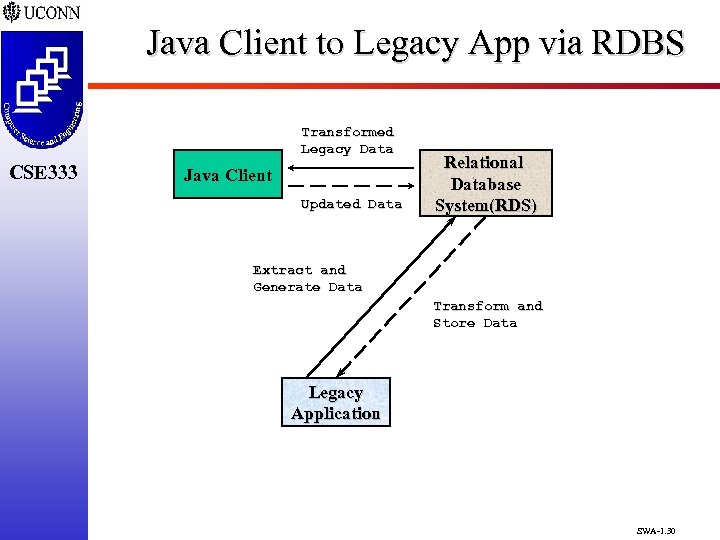 Java Client to Legacy App via RDBS Transformed Legacy Data CSE 333 Java Client Updated Data Relational Database System(RDS) Extract and Generate Data Transform and Store Data Legacy Application SWA-1. 30
Java Client to Legacy App via RDBS Transformed Legacy Data CSE 333 Java Client Updated Data Relational Database System(RDS) Extract and Generate Data Transform and Store Data Legacy Application SWA-1. 30
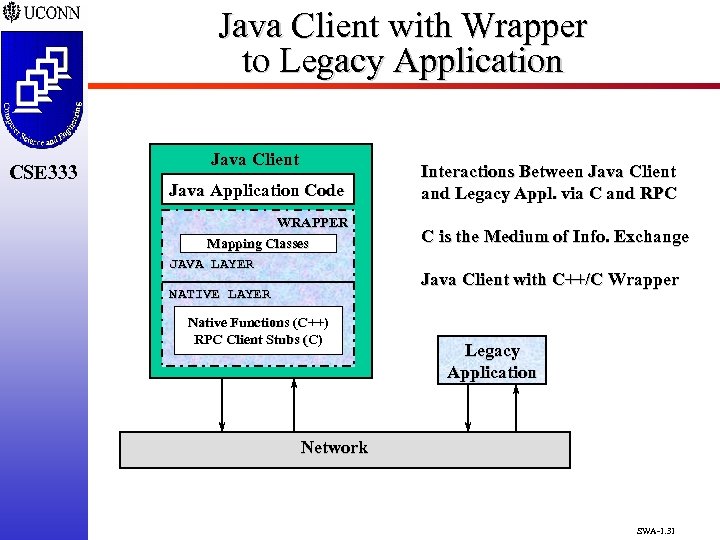 Java Client with Wrapper to Legacy Application CSE 333 Java Client Java Application Code WRAPPER Mapping Classes JAVA LAYER NATIVE LAYER Native Functions (C++) RPC Client Stubs (C) Interactions Between Java Client and Legacy Appl. via C and RPC C is the Medium of Info. Exchange Java Client with C++/C Wrapper Legacy Application Network SWA-1. 31
Java Client with Wrapper to Legacy Application CSE 333 Java Client Java Application Code WRAPPER Mapping Classes JAVA LAYER NATIVE LAYER Native Functions (C++) RPC Client Stubs (C) Interactions Between Java Client and Legacy Appl. via C and RPC C is the Medium of Info. Exchange Java Client with C++/C Wrapper Legacy Application Network SWA-1. 31
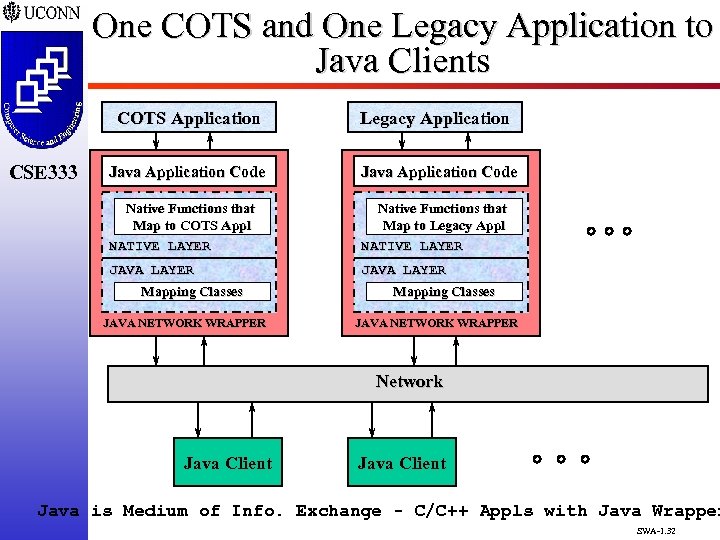 One COTS and One Legacy Application to Java Clients COTS Application Java Application Code Native Functions that Map to COTS Appl NATIVE LAYER Native Functions that Map to Legacy Appl NATIVE LAYER JAVA LAYER CSE 333 Legacy Application JAVA LAYER Mapping Classes JAVA NETWORK WRAPPER Network Java Client Java is Medium of Info. Exchange - C/C++ Appls with Java Wrapper SWA-1. 32
One COTS and One Legacy Application to Java Clients COTS Application Java Application Code Native Functions that Map to COTS Appl NATIVE LAYER Native Functions that Map to Legacy Appl NATIVE LAYER JAVA LAYER CSE 333 Legacy Application JAVA LAYER Mapping Classes JAVA NETWORK WRAPPER Network Java Client Java is Medium of Info. Exchange - C/C++ Appls with Java Wrapper SWA-1. 32
 Design Patterns Finer Grained Software Architectures m CSE 333 m m m Emerged as the Recognition that in Object. Oriented Systems Repetitions in Design Occurred Gained Prominence in 1995 with Publication of “Design Patterns: Elements of Reusable Object. Oriented Software”, Addison-Wesley q “… descriptions of communicating objects and classes that are customized to solve a general design problem in a particular context…” q Akin to Complicated Generic Usage of Patterns Requires q Consistent Format and Abstraction q Common Vocabulary and Descriptions Simple to Complex Patterns – Wide Range SWA-1. 33
Design Patterns Finer Grained Software Architectures m CSE 333 m m m Emerged as the Recognition that in Object. Oriented Systems Repetitions in Design Occurred Gained Prominence in 1995 with Publication of “Design Patterns: Elements of Reusable Object. Oriented Software”, Addison-Wesley q “… descriptions of communicating objects and classes that are customized to solve a general design problem in a particular context…” q Akin to Complicated Generic Usage of Patterns Requires q Consistent Format and Abstraction q Common Vocabulary and Descriptions Simple to Complex Patterns – Wide Range SWA-1. 33
 The Observer Pattern m CSE 333 m m Utilized to Define a One-to-Many Relationship Between Objects When Object Changes State – all Dependents are Notified and Automatically Updated Loosely Coupled Objects q When one Object (Subject – an Active Object) Changes State than Multiple Objects (Observers – Passive Objects) Notified q Observer Object Implements Interface to Specify the Way that Changes are to Occur q Two Interfaces and Two Concrete Classes SWA-1. 34
The Observer Pattern m CSE 333 m m Utilized to Define a One-to-Many Relationship Between Objects When Object Changes State – all Dependents are Notified and Automatically Updated Loosely Coupled Objects q When one Object (Subject – an Active Object) Changes State than Multiple Objects (Observers – Passive Objects) Notified q Observer Object Implements Interface to Specify the Way that Changes are to Occur q Two Interfaces and Two Concrete Classes SWA-1. 34
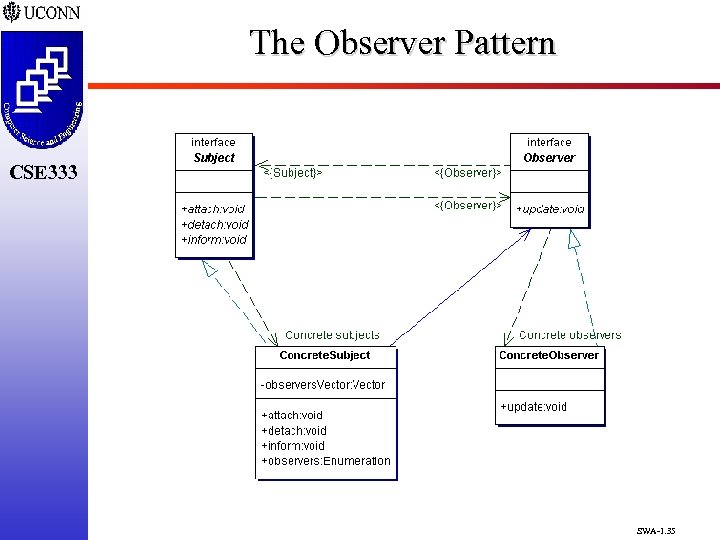 The Observer Pattern CSE 333 SWA-1. 35
The Observer Pattern CSE 333 SWA-1. 35
 Concluding Remarks m CSE 333 m m Architectural Styles Provide Patterns q Suppose Designing a New System q During Requirements Discovery, Behavior and Structure of System Will Emerge q Attempt to Match to Architectural Style q Modify, Extend Style as Needed By Choosing Existing Architectural Style q Know Advantages and Disadvantages q Ability to Focus in on Problem Areas and Bottlenecks q Can Adjust Architecture Accordingly Architectures Range from Large Scale to Small Scale in their Applicability SWA-1. 36
Concluding Remarks m CSE 333 m m Architectural Styles Provide Patterns q Suppose Designing a New System q During Requirements Discovery, Behavior and Structure of System Will Emerge q Attempt to Match to Architectural Style q Modify, Extend Style as Needed By Choosing Existing Architectural Style q Know Advantages and Disadvantages q Ability to Focus in on Problem Areas and Bottlenecks q Can Adjust Architecture Accordingly Architectures Range from Large Scale to Small Scale in their Applicability SWA-1. 36


