e6608d2cdbe922044736a81697e40434.ppt
- Количество слайдов: 75

Social Networking

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • Definition of SNS: “web-based services that allow individuals to (1) construct a public or semi-public profile within a bounded system, (2) articulate a list of other users with whom they share a connection, and (3) view and traverse their list of connections and those made by others within the system. ” • They avoid using the term networking because it implies that people are primarily using the sites to make new contacts as opposed to keeping up with existing relationships • Authors present a timeline of SNS history dating back to 1997 • Note that SNS sites differentiate themselves primarily by their default and customizable structures related to visibility and access • Reasons that people connect to one another are varied, and on some sites the links are not bi-directional, so one can be a “fan” but not necessarily a confirmed friend

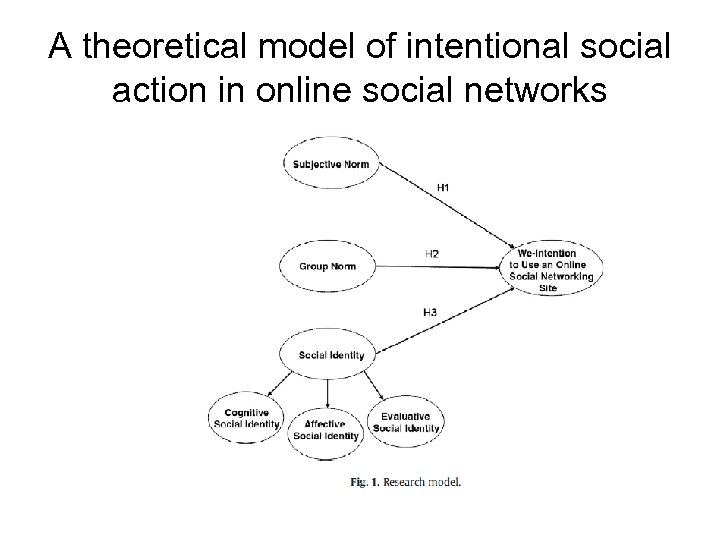
A theoretical model of intentional social action in online social networks • Most approaches to technology adoption are based on individual decision making • Authors present a research model on intentional social action in online social networks • Use the notion of collective intention • Another objective to validate existing measures of collective intention and to validate three modes of social influence in the context of social networks

A theoretical model of intentional social action in online social networks • explores the role of compliance (subjective norm), internalization (group norm), and identification (social identity) in explaining collective intention (we-Intention) to participate in social networks • We-intentions, reflecting group influences and group influence on individual decision making is most appropriate to understanding participation in social networks • Definition we-intention (Tuomela) “commitment of an individual to participate in joint action, and involves in an implicit and explicit agreement between the participants to engage in that joint action”
A theoretical model of intentional social action in online social networks

A theoretical model of intentional social action in online social networks • Some findings indicate that compliance (subjective norm) is important in the early stages of technology acceptance and that as the user gains experience, internalization (group norm) plays more of a role (note: internalization used a little differently here than Kelman’s original intent) • Hypotheses • “H 1. A stronger subjective norm leads to a higher level of We. Intention to participate in an online social networking site. ” • “H 2. Stronger group norm leads to a higher level of We-Intention to participate in an online social networking site. • “

A theoretical model of intentional social action in online social networks • Components of the social identity form of influence: – “▪ Cognitive social identity: The self-categorization process renders the self stereotypically interchangeable with other group members, and stereotypically distinct from outsiders. – ▪ Evaluative social identity: The evaluation of selfworth on the basis of belonging to a particular group. – ▪ Affective social identity: A sense of emotional involvement with the group, which is characterized by identification with, involvement in, and emotional attachment to the group. ”

A theoretical model of intentional social action in online social networks • “H 3. A stronger social identity leads to a higher level of We-Intention to participate in an online social networking site. ” – Expected significant main effects for each of the components of social identity • Methods – Facebook users who responded to a solicitation on one of several student groups on the site were instructed to think about up to five friends they interacted with on Facebook • Collected 389 usable online questionnaires • • • Measure of We-Intention “ WE 1: I intend that our group (i. e. , the group that I identified above) interacts on Facebook together sometime during the next 2 weeks. Dholakia et al. WE 2: We (i. e. , the group that I identified above) intend to interact on Facebook together sometime during the next 2 weeks. (2004) [Seven-point “Strongly disagree to Strongly agree” scale]
All about me: Disclosure in online social networking profiles: The case of FACEBOOK • Among the privacy concerns that some facebook users have is concern about identity theft and threats to personal security • “The overarching goal of the present research was to gain a better understanding of what can be found in online social networking profiles, specifically, FACEBOOK™. ” • “Apart from collecting data on the kinds of information users were choosing to include (and exclude) in their personal profiles, the study examines the impact of individual characteristics on the type of information that is likely to be present in an online profile (i. e. , information that is self-disclosed as a function of characteristicsincluding age, gender and relationship status)”

All about me: Disclosure in online social networking profiles: The case of FACEBOOK • Study 1 • Primary purpose to develop a scoring instrument for what could be revealed on Facebook • Sample: data from 400 randomly selected, accessible, personal profiles from 8 Canadian FACEBOOK™ networks (four university, four community) was collected • “a final checklist comprised of 97 dichotomously scored items (i. e. , whether the piece of information was present or absent) and 3 identification items (i. e. , username link, the network searched, and the size of the overall network) was constructed” • The 400 participant profiles were rated against the checklist

All about me: Disclosure in online social networking profiles: The case of FACEBOOK • Most disclosed: “(available on 63% or more of the profiles) described personally identifying information (i. e. , birth date, gender, profile pictures, photo albums, tagged photos and general photos of the user) as well social connections (i. e. , groups joined, and friends viewable). In addition, education information (college/university attended) and regular update information(status, wall and mini-feed) were included. Finally, playful communications such as acceptance of pokes, messages, and gifts and applications were frequently provided” • Least disclosed: ” key personal information (zip/postal code), phone numbers (both land line and mobile), home address, city or town, website and former name. Inaddition, there was also limited amount of information provided regarding some aspects of educational experience (i. e. , school mailbox, courses, degree, awards, and room). Finally, optional ‘‘wallfeatures” (i. e. , Super Wall and Advanced Wall) market place listings”

All about me: Disclosure in online social networking profiles: The case of FACEBOOK • People on average disclosed only 25% of what it was possible to disclose • Study 2 explored two types of threats, identity theft and theft to self or groups because of being associated with certain activities or persons • Three disclosure categories developed “The first category reflected personal identity information, the second involved sensitive personal information, and the third involved potentially stigmatizing information. Thematic analysis was conducted to construct each of the three categories”
All about me: Disclosure in online social networking profiles: The case of FACEBOOK • Used research assistants and even the police to develop personal identity index ranging from 0 -8: street address, city/town, postal code, gender, birth day, birth year, profile picture and email • Sensitive personal information “email, employer, job position, status, mini-feed, regular wall, profile picture, photo albums, self-selected photos, tagged photos, message, poke, send a gift, and friends viewable (possible scores ranged from 0 to 14). ”
All about me: Disclosure in online social networking profiles: The case of FACEBOOK • Potentially stigmatizing information: “religious views, political views, birth year, sexual orientation, photos, friends viewable, interests, activities, favorite music, favorite movies, favorite TV shows, favorite books, favorite quotes, and about me (possible scores ranged from 0 to 14). ” • Findings: • 1. “Specifically, users who provided information about their gender (present or absent), relationship status, and age disclosed more default/standard information, more sensitive personal information, and more potentially stigmatizing information in their online profiles than their peers who did not disclose their gender, relationship status or age” • 2. “users who indicated their relationship status as either single or in a relationship disclosed significantly more default/standard information … and sensitive personal Information …than users who did not indicate their relationship status”
All about me: Disclosure in online social networking profiles: The case of FACEBOOK • Single users shared the most stigmatizing information, then users in a relationship, and last those who didn’t indicate status • No effects for age or type of network • As age increased, disclosure decreased • Study 3 • “Through discussion and then factor analysis , the following 11 scales were created: • “personal information, photo and update information, work information, education information, message and poke acceptance (whether users allow for receipt of private messages and nudges from other users), photo album and profile picture information, age information, contact information, view information, other wall presence, and relationship information”
All about me: Disclosure in online social networking profiles: The case of FACEBOOK • Findings • “users who belonged to a community network were more likely to include their political and religious views in their personal profiles than were their university network counterparts” • “users who indicated their gender, also had higher levels of disclosure for: personal information, photo and update information, education information, photo album and profile picture information, and age information”
All about me: Disclosure in online social networking profiles: The case of FACEBOOK • More findings • “males expressed more information about their political and religious views than did females” • “disclosing one’s relationship status was related to higher levels of disclosure of various topics, including: personal information, photo and update information, photo album and profile picture information, age information; and view information” • “Users who disclosed their age also disclosed more education information” • Age predicted disclosure on 5 of the ten topics • Single users disclosed more on most of the topics

A theoretical model of intentional social action in online social networks • Results – Did structural equation modeling • Although there was a significant chi-square, all of the other indicators were good, indicating that the model was a good fit to the data Model accounted for 32% of the variance in We-Intention • Hypotheses: all factors (except group norm) had a significant effect on We-Intention, with subjective norm the strongest, • “social identity is a second-order factor with cognitive social identity, affective social identity, and evaluative social identity as secondorder factors exhibiting significant impact on We-Intention to use an online social networking site” • Interesting that subjective norm is still influential even after they are actively using Facebook-counter to prediction

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • Some sites which now support SN did not originally start out that way, and their original forms varied • Attribute decline of Friendster (although they do boast 73 million profiles on the site currently) to technology problems, cultural clashes as the general public became aware of the site, Fakester issues, announcement that they would become fee-based • Notes migration of photo and videosharing sites to SNS • My. Space offered new features with page customization, connection to bands, acceptance of minors • Proliferation of non-US SNS which have received little attention from US scholars

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • Some SNS sites have thrived by restricting public access, creating boundaries and exclusivity of one kind or another • Some government agencies and corporations have restricted usage of SNS for their employees • Difference between SNS and earlier online communities forums may be the organization not around common interests but around the social networks of individual members • “The world is composed of networks, not groups”

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • SNS research topics – Impression management and friendship performance • Profiles and friendship networks as tools of identity management; friends provide context or a backdrop for impression formation • Articles on this topic we’ve read include – Tong, S. T. , Van Der Heide, B. , Langwell, L, & Walther, J. (2008). Too much of a good thing? The relationship between number of friends and interpersonal impressions on Facebook. – Zhao, S. , Grasmuck, S. , & Martin, J. (2008). Identity construction on Facebook: Digital empowerment in anchored relationships.

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • SNS research topics, cont’d – Networks and network structure-using massive datasets collected by programs like Fetch (from Fetch Technologies, a company started by USC researchers) or donated by the SNS itself • Article on SNS networks we’ve read – Liu, H. (2007). Social network profiles as taste performances. • This category could also include typologies of users or profiles

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • Researchers in this area want to understand large scale structural features – Ex. Backstrom et al. , “Group Formation in Large Social Networks: Membership, Growth, and Evolution, ” a study of Live. Journa, l asked: – “What are the structural features that affect if someone will join a particular subgroup, and – “How does the probability of joining a subgroup p depend on the number of friends k who are already members of the group? ” • In the groups examined p was a negatively accelerating function of k - a law of diminishing returns in that k keeps affecting p but at an increasingly smaller rate • Other influential factors are not just the number of friends but, for moderate values of k, whether or not those friends are mutually connected to each other • Groups with very large number of triangles of mutual friends seem to grow more slowly

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • Bridging online and offline social networks – Primary motivation for using SNS seems to be to connect to friends rather than to meet strangers • How will this be affected by LBS? One of the basic findings in social psychology of friendship is that physical proximity is often a sufficient basis for friendship formation, while similarity is necessary for people to maintain friendship relationship with geographically distant others • Reading from our syllabus – Chan, D. K. , & Cheng, G. (2004). A comparison of offline and online friendship qualities at different stages of relationship development.

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • Privacy – Several researchers have been interested in the extent to which information supplied to SNS for public consumption can compromise the privacy or the personal identity of members, particularly young people who seem to be somewhat less concerned about privacy issues • For example, Stutzman, “An Evaluation of Identity-Sharing Behavior in Social Network Communities, ” surveyed students using Facebook Friendster and My. Space to found out what they were revealing about themselves on the sites. He found that most of them thought that maintaining privacy was very important, and were not confident that their personal information was safe on these sites, but they were not particularly concerned about it • See also Wolak, J. , Finkelhor, D. , * Mitchell, K. (2008). Is talking online to unknown people always risky? Distinguishing online interaction styles in a national sample of youth internet users from our readings on “The Dark Side of CMC” – Are Facebook profiles public or private? Do police have the right to “search” them?

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • Other study areas • Boundaries on SNS; – Study conducted at Georgia Tech found that 1/3 of students surveyed did not believe professors should be allowed on Facebook (2006 pub date) – Contact with professor on Facebook had no impact, positive or negative, on ratings of professor

boyd, d. m. , & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. • Future research – Need for experimental, longitudinal studies – More studies outside US

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Networks where user-owned or created content is shared are becoming more commonplace • Not much is known about the norms and values surrounding the online “giving” of content for semi-public consumption • This would lie somewhere along a continuum from posting a file on a web page which anybody can access to attaching a file to email (the private end of the continuum) – The authors refer to this as the “Space where directed content and social relationships co-evolve”

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Studies of contributions of end-user content online have focused either on motivations for sharing or on issues related to social loafing where selfish users download but do not contribute • Little explicit attention to the recipient end in terms of users’ feelings about to whom they want to contribute – Aspects of the sharing experience seem to have much in common with an anthropological take on gift-giving

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Gifting: three central concepts: social bonds, otherorientedness and reciprocity – Interesting why they chose a gift-giving perspective, as opposed to, say, authorship, or other perspectives such as self-promotion or desire for social influence • Two modes of gift transfers (coercion and exchange are not considered) – Reciprocity – Pure gift-giving – Coercion and Exchange vs. Reciprocity and Pure Gift-Giving continuum- categories arrayed along a continuum anchored by • Self-centered motivations vs Other-oriented motivations • Economic man vs Social bonds • Cost–benefit vs. Reciprocal ambiguity

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Researchers are interested in the end of the continuum where it is uncertain whether or if you will get something in return, and if so, what you will get • Digital goods have the characteristic that you can give them without losing them, and that once you give them you lose control over how they are distributed to others • Affordances of Internet allow digital goods to be transferred at little or no cost • Sharing networks are increasingly taking on a social component which factors into how and with whom goods are shared (e. g. influenced by the existence of affinity groups and subnetworks) as well as on the willingness to engage in pure gifting as opposed to exchange or reciprocity

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Research questions: what end-user concerns characterize semipublic content contributions on the Internet? – what is given, to whom, how, and why – Authors looked at Flickr, a photo-sharing network • Principal activities consist of uploading photos, tagging (applying metadata to photos) • Tags can be searched, result in user-generated “folksonomies” or taxonomy of pictures • Users can look at photos bookmarked as favorites by others as well as others’ contacts • Users can get comments on their photos, and there are feedback mechanisms including popularity ratings • Users can create groups • On Flickr, social networks emerge from sharing of material

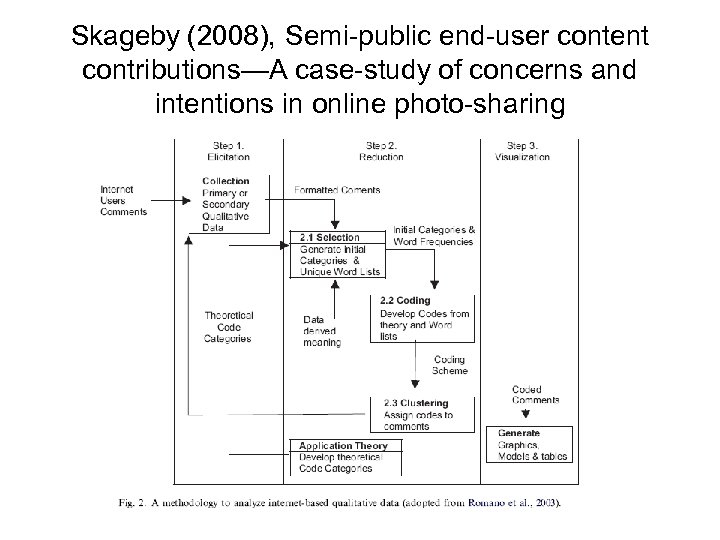
Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Data: – Analyzed 760 forum posts (no details on how these were selected were provided) – Did follow-up interviews with 17 users – Used a sort of grounded theory process using the whom, what, how and why categories for coding, while looking for emergent features
Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Results • What: Social content and metadata • “Novice users quickly became aware that when providing material for others in a networked environment, you are also exposing links to other files, metadata, conversations, persons or even networks and vividly described difficulties and concerns they had when facing this fact” – Ex. Being OK with making their photos public but not the tags, especially if tagged with the names of friends or other users – Ex. That their pictures could be used in somebody else’s offsite blog with a track back to them on Flickr-allowed unathorized people to have a path into your life – Ex. Concerns about visibility of contacts-friends might have photos they don’t want their parents to see

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Other concerns – Not being able to upload photos anonymously – Being named as a contact whether you liked it or not – Wanting to make friends’ comments on photos separately not viewable by family (and perhaps vice versa) – So any discussion of end—user digital content needs to include the associated metadata like tags, including the social metadata (network of contacts, friends’ comments on photos, etc)

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Whom: recipients and their relationships • A flaw in Flickr was that the level of settings for privacy was not graduated enough-ex. Friends and family lumped together, only a few categories (public, contacts, friends and family, private) • Ex. Child of divorce has photos with Mom’s side of family, Dad’s side and don’t want to subject one to the other but still want to share photos with family • Groups were used to address certain pictures to particular groups of recipients on a long-term basis but was not a good solution for short-term or one-time occasions

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Groups often subdivided into splinter groups who did not subscribe to the rules of the larger group about what sorts of pictures could be posted • How: sociotechnical means – Dealing with the issues of not being able to precisely and on-the-fly control the recipients for pictures led people to either develop technical workarounds, which may have led them offsite, or to simply refrain from posting – Wanted a mechanism for “banning”-making public material semi-public if the content was offensive

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • Why: semi-public motivations – – – did not want to trouble others with nonrelevant goods; receivers requested it an offline (intimate) social bond perceived similarities with receivers intended a (personalized) experience with the goods; experienced a conflict of interest between different receiving relations and groups – the gift, if provided publicly, might produce requests for additional gifts

Skageby (2008), Semi-public end-user content contributions—A case-study of concerns and intentions in online photo-sharing • People need to be able to put relations into silos (sometimes temporary) and to “gift material in excludable ways” • Need to be able to “control the digital rights” • The presence of tags, links, commenting mechanisms, publishing photos straight to blogs, etc. all raise the costs of gifting • The association of the photos with all of this metadata increases the likelihood of a desire for semi-public gifting and technical mechanisms to support it • Some users wanted to be able to make it clear that their photos were in the public domain and free for anyone to use for any purpose • Interesting to think about their data from a perspective other than gifting, say impression management or self-as -source
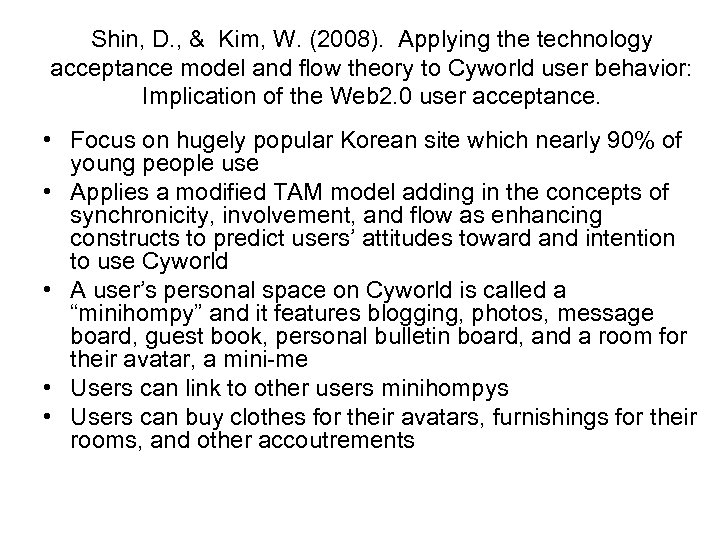
Shin, D. , & Kim, W. (2008). Applying the technology acceptance model and flow theory to Cyworld user behavior: Implication of the Web 2. 0 user acceptance. • Focus on hugely popular Korean site which nearly 90% of young people use • Applies a modified TAM model adding in the concepts of synchronicity, involvement, and flow as enhancing constructs to predict users’ attitudes toward and intention to use Cyworld • A user’s personal space on Cyworld is called a “minihompy” and it features blogging, photos, message board, guest book, personal bulletin board, and a room for their avatar, a mini-me • Users can link to other users minihompys • Users can buy clothes for their avatars, furnishings for their rooms, and other accoutrements

Shin, D. , & Kim, W. (2008). Applying the technology acceptance model and flow theory to Cyworld user behavior: Implication of the Web 2. 0 user acceptance. • Technology acceptance model – Offshoot of theory of reasoned action – Attitude toward an action, subjective norm both influence behavioral intention – Behavioral intention is known to be a strong predictor of actually taking an action – Perceived usefulness and perceived ease of use are major factors influencing behavioral intention to use a technology; didn’t see ease of use in this application – Three new variables specific to Cyworld incorporated into the model: synchronicity, involvement, and flow experience

Shin, D. , & Kim, W. (2008). Applying the technology acceptance model and flow theory to Cyworld user behavior: Implication of the Web 2. 0 user acceptance. H 6: There is a positive relationship between perceived involvement and H 1: Attitude toward Cyworld is positively related to the intention to perceived enjoyment. H 7: There is a positive relationship use Cyworld. H 2: There is a positive relationship between perceived involvement and between perceived usefulness and attitude toward Web 2. 0. (? ) H 8: There is a positive relationship intention to use Cyworld. H 3: There is a positive relationship between perceived synchronicity between perceived usefulness and perceived usefulness. H 9: There is a positive relationship attitude toward Cyworld. H 4: There is a positive relationship between perceived synchronicity between perceived enjoyment and attitude toward Cyworld. intention to use Cyworld. H 10: Flow experience has a strong H 5: There is a positive relationship effect on intention to use Cyworld • Hypotheses: • • • between perceived enjoyment and attitude toward Cyworld.

Shin, D. , & Kim, W. (2008). Applying the technology acceptance model and flow theory to Cyworld user behavior: Implication of the Web 2. 0 user acceptance. • Got a sample of 950 home pages using the “random home page finder” feature of Cyworld (now that’s convenient! Wonder how “random” it really is) • Posted recruitment information and a copy of the survey instrument on the users’ bulletin boards (wow, this is a researcher’s dream! Especially when combined with the nonymity feature which ties the user to a state issued ID number) • 352 respondents completed the survey for a very good response rate of 37% (by my calculations; the researchers claim a response rate of 43. 3% (maybe some confusion here as to whether this represented a total after a second wave of posting surveys) • No information is provided on how concepts were measured, reliability of measure, etc.

Shin, D. , & Kim, W. (2008). Applying the technology acceptance model and flow theory to Cyworld user behavior: Implication of the Web 2. 0 user acceptance. • Results – Used SEM to analyze the data – The author does not report the chi-square result for some reason (probably significant given such a large sample size? ) but the other indicators suggest that the model is a good fit – Eight of the ten hypotheses were supported, and two rejected (some of the significance levels were p<. 10 which is not a very stringent criterion) – Rejected hypotheses were the direct paths from perceived usefulness and perceived enjoyment to intention to use Cyworld – Perceived usefulness is usually a good predictor in TAM studies
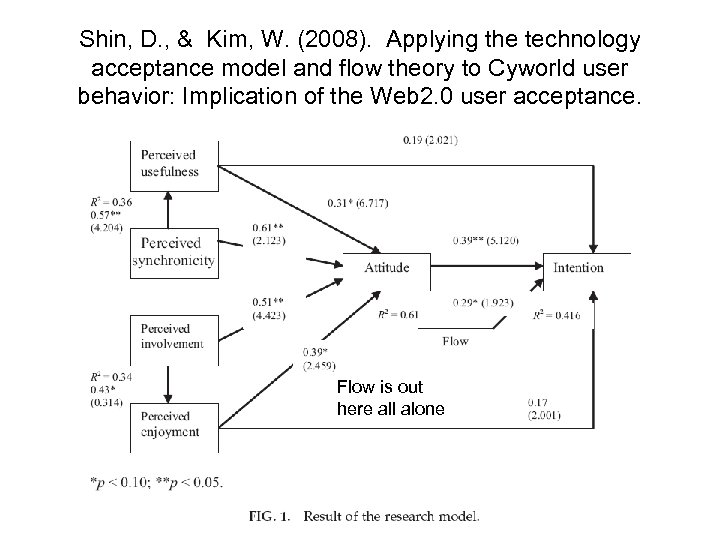
Shin, D. , & Kim, W. (2008). Applying the technology acceptance model and flow theory to Cyworld user behavior: Implication of the Web 2. 0 user acceptance. Flow is out here all alone

Shin, D. , & Kim, W. (2008). Applying the technology acceptance model and flow theory to Cyworld user behavior: Implication of the Web 2. 0 user acceptance. • • • There is an error on page 381 where instead of saying that perceived usefulness and perceived enjoyment would mediate the relationship between perceived synchronicity and perceived intention, the text states perceived involvement. The only variable which had a direct effect on behavioral intention was perceived flow The effects of perceived synchronicity and perceived involvement on intention were mediated by perceived usefulness and perceived enjoyment However, the direct effects of perceived synchronicity and involvement on attitude were stronger than their mediated effects through, respectively, perceived usefulness and perceived enjoyment Lack of direct effect of usefulness and enjoyment on intention to use suggests that maybe there is something different about this particular technology that requires a higher level of usefulness or enjoyment to predict regular use – It may be that since everybody uses Cyworld it is a less discretionary choice and you may not need to enjoy it or even find it particularly useful to feel you need to use it?

Donath (2007). Signals in Social Supernets. • Grooming, Gossip, and Online Friending • Are social networks sites going to provide the tools that are needed to be able to efficiently expand the scale of one’s social networks? • Presumably there are limits to the number of contacts one can manage f 2 f or through conventional means – While apes use grooming to nourish and maintain their social ties, they can only pick so many lice – Humans are able to use language to accomplish many of the same relational formation and maintenance tasks, but again their resources to do this are limited given the many demands of daily living – Author argues that although tools like email enable you to keep in touch with or send news to multiple others, there is a greater need to be able to keep up with the news of others in context, to learn about their relationships, and to have a basis for the development of trust – These are the services that social networks would seek to provide, enabling social networks of much greater scale

Donath (2007). Signals in Social Supernets. • Author’s goal to offer a theoretical framework for assessing the potential of SNS to transform social relations and to provide guidance to designers for making SNS better social tools • The analysis is based on signaling theory, which “models why some communications are reliably honest and others are not” • Thus a central focus is on how SNS can more fully address the issue of interpersonal trust, particularly as it affects the establishment of reliable identity

Donath (2007). Signals in Social Supernets. • Signaling theory – The extent to which we require communications to be scrupulously honest is highly variable and depends on the consequences of dishonesty in a particular context – On a message board talking about sports it may not matter so much as it would on, say, a forum talking about brain cancer – To be a reliable signal, the costs of deceptively producing the signal must outweigh the benefits. • What types of signals and situations bring this about?

Donath (2007). Signals in Social Supernets • assessment signals to produce the signal you have to possess the quality • "Strategic" or "handicap" signals You show that you have a lot of something by conspicously wasting it, such as light a cigar with $100 bills – Only reliable as to the cost of the specific display (the smoker may have used up the entire week’s pay on that cigar) and not to any other qualities – Conventional signals are indicators like age or gender that are not inherently reliable but can be checked for authenticity • A ring on the left hand, fourth finger, is a conventional signal but it can be worn by single people to ward off unwanted attentions, or left off by potential cheaters, and there will be people in the individual’s social world who will know whether the signal is accurate or not

Donath (2007). Signals in Social Supernets • Signals can vary with respect to how costly deception is – It may not be very costly to describe yourself on your profile as “fun-loving” or show yourself in a photo at a party, but it may be very costly to describe yourself as tall and blonde, both in terms of those in your network who know you to be dark and petite, in the effort required to find a picture that will confirm the description, and in the disappointment persons who meet you for the first time and discover that you have exaggerated • SNS can invent ways to make it more costly to be dishonest (for example to claim someone as a contact when they’re not really known to you) but people can usually find a way to circumvent these precautions – Requiring confirmation of the friendship should make it more costly, but in fact most people don’t like to reject friend requests and agree even if they barely know someone or think they might know them

Donath (2007). Signals in Social Supernets • Trust and Identity in Large Mobile Societies • Can SNSs provide a means for extending trust and assessing reliability? – Theoretically the links to others provide a means for vetting, although if all of the friends are in on it or approve of it a person can provide a completely false persona on the profile with the sanction and complicity of the friend network – The social context provided by friend networks helps to resolve ambiguities and offers evidence of how one treats social relations and is treated by them-you are tied to the identity developed within that nexus of social contacts – One of the greatest benefits of SNS is to add trust to weak ties – Weak ties can be extremely beneficial in connecting you to useful resources and persons you would not otherwise encounter – Site designs that make adding contacts too easy compromise the trust aspect of social networks

Donath (2007). Signals in Social Supernets – It’s a good idea to increase the “costs” of indiscriminately creating links, such as penalizing people for too many declined links, or allowing people to whom you link the ability to post on your page (you should know them reasonably well to have confidence that you won’t be embarrassed by what they post) • Types of Relationships – The combination of strong ties to provide a context for trust, and a network of heterogeneous weak ties to extend access to persons and resources beyond the immediate social circle suggests that the possibility of creating a social supernet is viable – Mere presence of a friend link is not very informative – More information about the closeness of a relationship can be gleaned from other activities such as wall posts, comments on each others posts, videos, photos, mutual tagging, etc – Time spent on maintaining the relationship digitally may signal closeness or just somebody with time on their hands

Donath (2007). Signals in Social Supernets • Reducing receiver costs – Time spent carefully checking out potential friends before accepting them may be paid for by freedom from spam or unwanted posts on ones profile page – Applications which visualize social networks may help to reduce the costs of vigilance in assessing the reliability of information about a potential contact – Would have the effect of making people more aware of the impression created not just by their profile but also by the totality of their network connections – Could also make things like the homogeneity or heterogenity of one’s network visible, as well as the frequency of one’s contact with network members or other indicators

Donath (2007). Signals in Social Supernets • Fashion and the Display of Information-Based Status – Being in fashion/at the forefront with respect to applications signals status, innovativeness and “fitness” in the constantly evolving online world • Information Exposure: Signaling Imperviousness – Posting risky or too revealing information is a way of signaling imperviousness to danger, demonstrating cool in the sense of composure and fearlessness – Or they may just be stupid

Donath (2007). Signals in Social Supernets People no longer need personal relationships to meet their basic survival needs (? ) The strengths of SNS may lie in their ability to provide access to information while helping them to maintain a socially local network of relationships (strong plus weak ties, bridging and bonding, etc)

Donath (2007). Signals in Social Supernets • The current generation of teens who are ubiquitously connected to IM, My. Space, etc. have acquired and continue to invent and appropriate entirely new ways to use the media they consume, particularly SNS, to indicate and infer popularity, their friends and romantic interests, and social skill • Their breakups and makeups are there for the whole world to follow if they wish it to be so • SNS may reduce anonymity and loneliness • LB Mo. Sos in particular may leverage physical proximity to provide a context and occasion for new relationship formation • Novelty and the continuous updating of personal information about one’s contacts may be sufficient to keep people connected to SNS and make the social supernet idea feasible

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube. • Defines SNS in terms of the ability to publicly articulate connections between people • The presence of the connection and not the nature or strength of the connection is what is made explicit • Connections can be made through varying media • These media circuits could be made through the telephone, as in immigrants from Mexico staying in touch with loved ones at home, or through sharing videos with a subset of friends on You. Tube

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • On You. Tube, sharing videos with one set of friends and not with others indicates that there are different media circuits in operation, and there are different social configurations • People share technically substandard video on You. Tube for the same reasons they IM, not to impart high quality information but to display affinity • Private vs. public-what is hidden or withdrawn vs. what is open and accessible; also, what is individual vs. what is collective • Both of these factors can be applied to video; how much information is available about the individual, and with whom (and how many) the information is shared (to whom it “belongs”)

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • Fractalization(? ) of the public and private • Who can access, manipulation and distribute information differs greatly by context, so what is private in one context could rightly be viewed as public in another • Use the image of a fractal, as a larger image which, when you inspect its component parts, has smaller versions of the larger one, and still smaller versions, etc – A somewhat strained metaphor (rooms in homes are private spaces within homes; homes are private spaces within neighborhoods; then it sort of breaks down…. – : Gal, ‘‘Whatever the local, historically specific content of the dichotomy, the distinction between public and private can be reproduced repeatedly by projecting it onto narrower contexts or broader ones’’ – Video sharing practices “subdivide in ways that reflect different relationship dynamics and social networks:

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • Method – Used a combination of qualitative methods including semi-structured interviews and observations of postings, examination of subscription and friending practices, attending events and meetups – 54 interviewees ranging in age from 9 to 43 – Lot of method variance-used phone, IM, and f 2 f methods to interview people

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • Used personal acquaintances of the researchers as subjects, which is not really the done thing although the farther out their networks they traveled the less it would be an issue • Asked them questions about pros and cons of posting on You. Tube, about the people they friended, difference between subscribing and friending, if they knew the people who commented on their videos, etc. • Some were highly visible posters, You. Tube celebrities, and some were scarcely known

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • Findings • Some media circuits reinforced social relationships that began in person, e. g. family members commenting on each other’s videos • People can complete media circuits to unknown others and expand their networks by posting videos for unknown others to see, or by commenting on videos posted by unknown others • You. Tube posters can expand or limit access to their videos by tagging in narrow ways (e. g. using your name as a tag) or by restricting access to friends only • Some friends who do not know each other well may make videos together and become friends (? How often does this happen? )

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • Technical issues don’t matter much – Creating and circulating videos is a process of defining and maintaining social networks – The public end of the continuum • Some video makers are quite public about their identity and make every effort to get a broad swath of the public to view their work including making their content appear to be as broadly relevant as possible – The private end of the continuum • Others keep their identity as video makers to themselves, target the content very narrowly, and restrict viewing to only a small group of friends

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • Some video makers may be publicly private, in that they reveal their identity but tag the content narrowly or cryptically or not at all or restrict who can view it • Some people post video that is intended only for a handful of insiders publicly, because they don’t want to require them to have accounts to view the videos, which are required of “friends” • The same poster could vary widely in terms of how publicly private they might be; some videos might be tagged in such a way as to invite broad viewing even though most are ‘restricted’ to friends by their very narrow or cryptic tagging

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • Privately public • Videosharers keep their identity private but use tagging and public access to share the video as widely as possible, attract comment, etc – Can also accomplish this through various techniques internal to the video such as distorting voices on the video, wearing masks, not speaking, etc. – Want to stay anonymous so as not to attract attention from the workplace or encourage stalkers, among other motives for wanting to remain anonymous, or because one is engaging in activities that are best kept secret like surprising people • “When he [CT] makes videos with RJ, he reveals his face, name, and location. Yet when he made the. Vlad film, he withheld that information and sought more ‘‘privately public’’ connections to new fans”

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • Example of Mad. V, who encourages viewing by picking topics with broad appeal and friending generously – People pick up symbols from his videos and reproduce them in other social situations, extending his media circuit and expanding the influence of his social networks – People who make hateful comments or who try to reveal his identity are removed from subscriber lists and their comments deleted – He does not initiate friend requests or subscribe to other’s channels, and he is firmly at the center of his social network • Note that on Mad. V’s channel page he has a link to the JCMC article!

Lange, P. G. (2007). Publicly private and privately public: Social networking on You. Tube • When You. Tube was acquired by Google, the tags that were attached to videos then became part of the search process and the video might be more easily found and more frequently viewed • “On You. Tube, frequent interaction between video makers and viewers is a core component of participation on the site. Viewers and commenters are often themselves video makers, who comment with the strategic intent of forming social relationships with others who will support their work”
Spatially Bounded Online Social Networks and Social Capital: The Role of Facebook • Displaying your connections on a social networking site is a way of providing a warrant for your claims to your identity (Donath and boyd) • Social networking sites are distinct from earlier versions like newsgroups etc in that they provide a way for you to extend your offline social networks as well as meet new people-e. g. in the older groups the trajectory was from online meeting based around shared interests to offline meetings, whereas here there is movement in the other direction as well in order to maintain or strengthen or extend existing relationships • Geographical orientation of sites like Facebook may serve to enrich social capital in offline networks – Fewer people play with identities due to the tie to real-world existing connections – Donath and boyd hypothesize that sites like Facebook could increase an individuals’ number of weak ties, if not strengthen strong ties, eg. Increase social capital (information, connections, opportunities)

Spatially Bounded Online Social Networks and Social Capital: The Role of Facebook • • Bourdieu and Wacquant--social capital as “the sum of the resources, actual or virtual, that accrue to an individual or a group by virtue of possessing a durable network of more or less institutionalized relationships of mutual acquaintance and recognition” “For individuals, social capital allows individuals to benefit in a variety of ways in that participation in a social network allows a person to draw on resources from other members of the network and to leverage connections from multiple social contexts. These resources can take the form of important information, employment opportunities, personal relationships, or the capacity to organize groups (Paxton, 1999). Access to individuals outside one’s close circle provides access to non-redundant information, resulting in benefits such as employment connections” (p. 7, Ellison et al) Networks in which there are not direct links between all participants, what are called structural holes, are actually more efficient for the diffusion of information because of supporting the transfer of information between subgroups or from groups were it is old news to groups where it is new and useful Distinction between bridging social capital which is provided by social networks and bonding social capital (Putnam)

Spatially Bounded Online Social Networks and Social Capital: The Role of Facebook • Subjects were 286 undergrads at MSU • Were surveyed for demographic information, Facebook intensity (no. of friends, typical daily amount of time on the site, attachment to an integration into Facebook community), purposes of using Facebook (information, entertainment, looking up people, making new friends), perceived critical mass, self-esteem and satisfaction with life at college, measures of social capital (bridging, bonding, high school)

Spatially Bounded Online Social Networks and Social Capital: The Role of Facebook • Findings • Who is using Facebook? High penetration Almost all of the students were, and there were few differences between the ones who were and weren’t except that the weren’ts were a little older/more likely to be off campus, had significantly higher high school social capital although not the other two types • How were they using it? Reported an average of 10 -30 minutes a day and 150 -200 friends; for fun and killing time rather than gathering information, more for interacting with offline friends than meeting new people, especially keeping up with high school friends • Facebook appeared to have a large impact on student’s ability to develop bridging social capital on campus • Facebook use especially helpful in increasing social capital for those with low self-esteem and low satisfaction with student life

Spatially Bounded Online Social Networks and Social Capital: The Role of Facebook • Bonding social capital also predicted by Facebook intensity • General Internet use not related to social capital measures except for high school social capital • Usage characterized primarily as offline to online movement to strengthen and extend existing offline relationships – Features like the “birthday greeting” feature which was provided by the site were useful for increasing bonding social capital

Spatially Bounded Online Social Networks and Social Capital: The Role of Facebook • Haythornthwaite (2005) new media “create latent tie connectivity among group members that provides the technical means for activating weak ties” (p. 125). Latent ties are those social network ties that are “technically possible but not activated socially” (p. 137). Facebook enables participants to capitalize on weak ties (such as “friending” a friend of a friend) and convert latent ties to weak ties (such as looking up the profile of someone in a shared class and finding mutual areas of interest and possible discussion topics). ” • These weak ties will provide new information and new opportunities
e6608d2cdbe922044736a81697e40434.ppt