3e331b55fae02a2c03fb090cdd0ee53c.ppt
- Количество слайдов: 34

SOA Technology Briefing MITRE, Mc. Lean, VA October 2006 Comparing USPS Postal. One, NIH e. Receipts and Amazon. com for e. Gov and SOA David RR Webber Dr. Alan Harbitter webberd@od. nih. gov Alan. harbitter@nortelgov. com 1
Overview n Nortel Government Solutions (NGS) staff has implemented two widely differing solutions for high visibility e-Government systems. n How do these two approaches compare and contrast and what are the lessons learned compared to a commercial approach such as Amazon. com? n Special Focus - e. Government Security aspects n Q&A 2
Quick History n Notion of using Internet to securely exchange business information w. XML started in 1997 w. B 2 B work on XML/edi and eb. XML web. XML specification – May 11 th, 2001 w. Web services – started 2000 as ‘quick fix’ w. WSDL and XSD developed by W 3 C n Web services used by Amazon and e. Bay n Marketing of SOA emerges 3
What exactly is SOA? n SOA still very much dependent on the focus of the advocate n Some commonly accepted wisdoms w Using internet TCP/IP based exchanges w Both “real time” and “batch” services w Need registry to manage content / services w Robust Security and Authentication w Partner profiles - Mo. U, roles, context w Rule based business information handling w Business process formalization 4
CIO’s perception of SOA Today n Independent of underlying technology n A general model for offering computing and information services in large, loosely coupled, highly distributed environment. n The standardized and probably most widely associated implementation technology is web services n But many look to implement SOA with specific vendor legacy technologies e. g. IBM MQ series, BEA, Oracle, SAP, etc 5

Where is SOA Today? n Many camps of vendor driven interests w. WS/I , W 3 C, OMG, OASIS, more n Many components as open specifications n Marketplace still sorting out winners and losers of key components wsecurity, registry, messaging, transactions, business process n Loose coupling – concept but not reality n Poor understanding of applicability of B 2 B batch delivery – push / pull / staged 6

Quick look - what exactly is SOA? n Using Amazon web services n Contrast and compare simple web service model to SOA requirements 1 n Web Services – Amazon AWS 2 AWS 3 (TALKING POINTS) Security / Role / Access? Rapid deployment Legal position Simplicity of Content Degrading content at peak times Transient value-less content Agility / loose coupling 7
NIH e. RECEIPTS & USPS POSTALONE 8

NIH Grants Management n NIH issues billions of dollars in grant awards to investigators worldwide annually n Receives 70, 000+ research and training grant applications n Handling 20, 000+ pages of paper n To electronically receive, verify and accept ALL Research/Research related Grant Applications n. Securely manage each step of the process 9
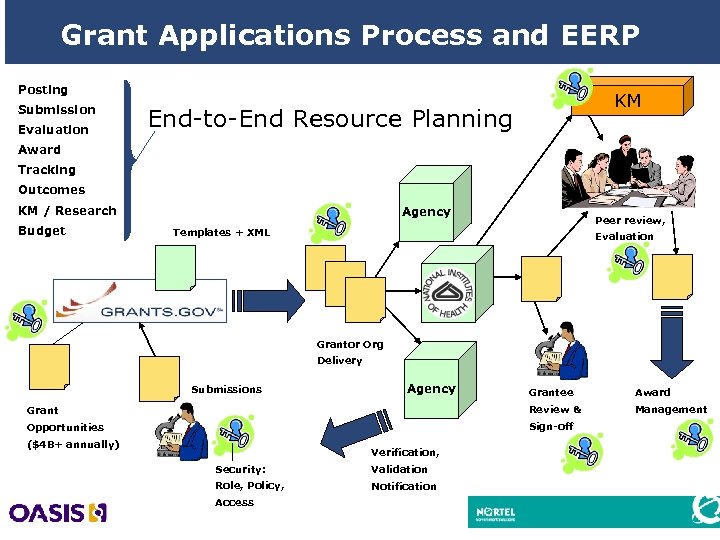
Grant Applications Process and EERP Posting Submission Evaluation KM End-to-End Resource Planning Award Tracking Outcomes KM / Research Budget Agency Peer review, Templates + XML Evaluation NIH Grantor Org Delivery Agency Submissions Grantee Award Grant Review & Management Opportunities Sign-off ($4 B+ annually) Verification, Security: Validation Role, Policy, Notification Access 10

NIH Exchange - Design Goals n Automated registration of participants n Ability to self-certify exchange transactions n Version control and ability to approve partners n Centralized registry for participant management n Alignment of policy and security n Declared and shared business rule scripting n Integration through messaging services n Backend application integration services n Uses open public specifications and open source 11
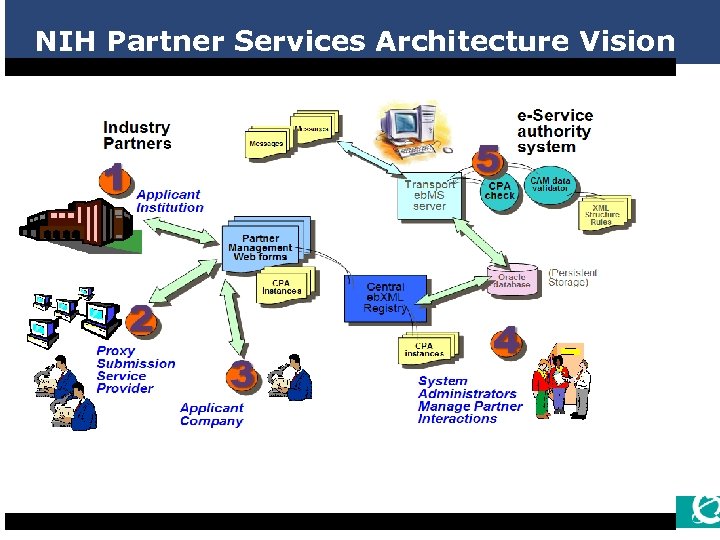
NIH Partner Services Architecture Vision 12
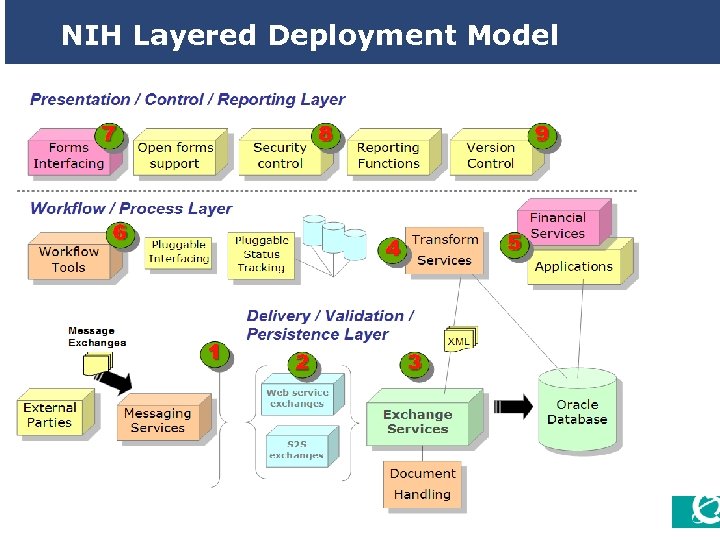
NIH Layered Deployment Model 13

Postal. One!® – Web-Based Enterprise Application n To electronically verify and accept ALL Business Mailings nationwide n 30, 000+ users n $32 Billion in annual revenue collection for USPS n 100, 000+ transactions per day n Mission Critical application for USPS 14
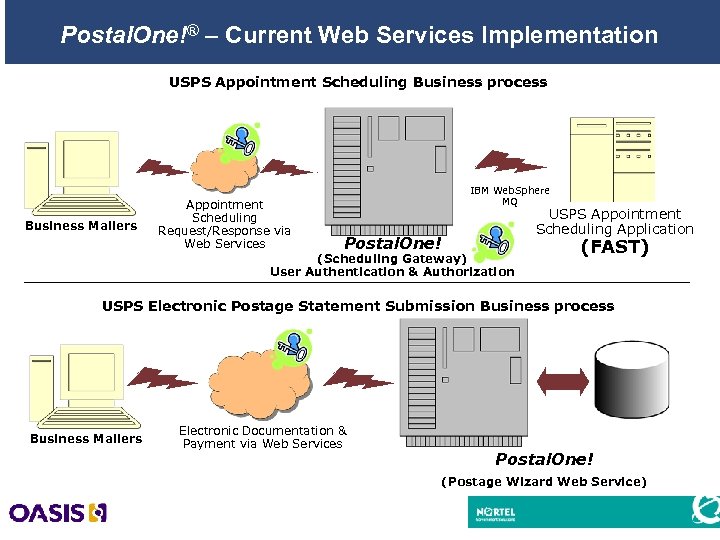
Postal. One!® – Current Web Services Implementation USPS Appointment Scheduling Business process Business Mailers Appointment Scheduling Request/Response via Web Services IBM Web. Sphere MQ Postal. One! USPS Appointment Scheduling Application (Scheduling Gateway) User Authentication & Authorization (FAST) USPS Electronic Postage Statement Submission Business process Business Mailers Electronic Documentation & Payment via Web Services Postal. One! (Postage Wizard Web Service) 15
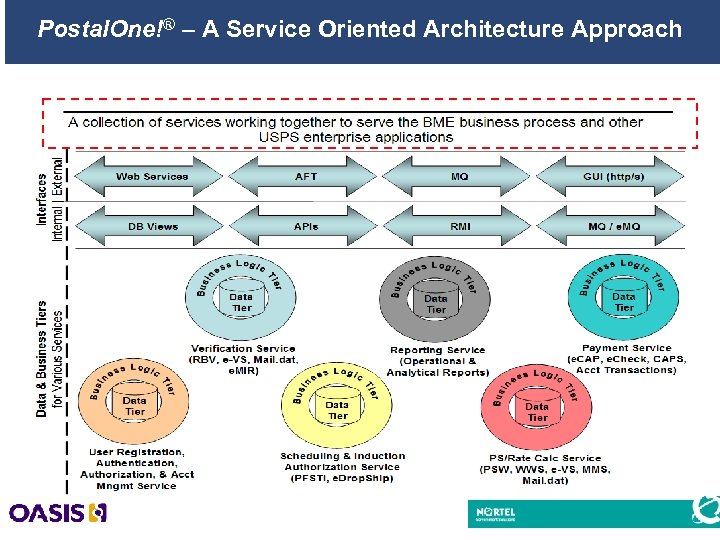
Postal. One!® – A Service Oriented Architecture Approach 16

Security Considerations for Real World SOA Systems Dr. Alan Harbitter CTO, Nortel Government Solutions (Alan. Harbitter@nortelgov. com) 17

High-level Thoughts on Security and SOA n Probably the number one paranoia in SOA pilot -to-production transition is security—and rightly so. n SOA (web services), is generally thought of as service producer-to-consumer, not system-touser. But security has to be user-focused. n The mechanisms suggested by many of the standards assume in place security infrastructure beyond the “as-is. ” n The ROI for SOA is based on applications, so that’s how an organization is likely to start n But security should be institutionalized— beyond single applications. 18

Security Services Requirements n Confidentiality w Services and information provided are not accessible to unauthorized parties w Traffic patterns do not provide a “covert channel” n Integrity w Service and information provided is not inappropriately modified n Availability w Service is reliably provided at advertised hours n Authentication w Server, Service, User n Non-repudiation w Parties exchanging information can be positively identified and can not deny providing or receiving services 19
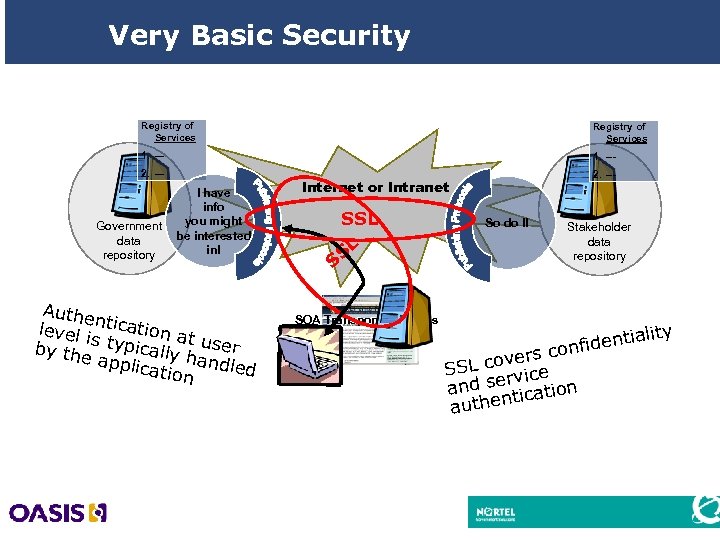
Very Basic Security Registry of Services 1. --- 2. --- Government data repository I have info you might be interested in! Authe level ntication a t i by thes typically user h appli cation andled Internet or Intranet SSL SL S SOA Transport Protocols 20 So do I! Stakeholder data repository ntiality nfide ers co v SSL co rvice and se tication authen
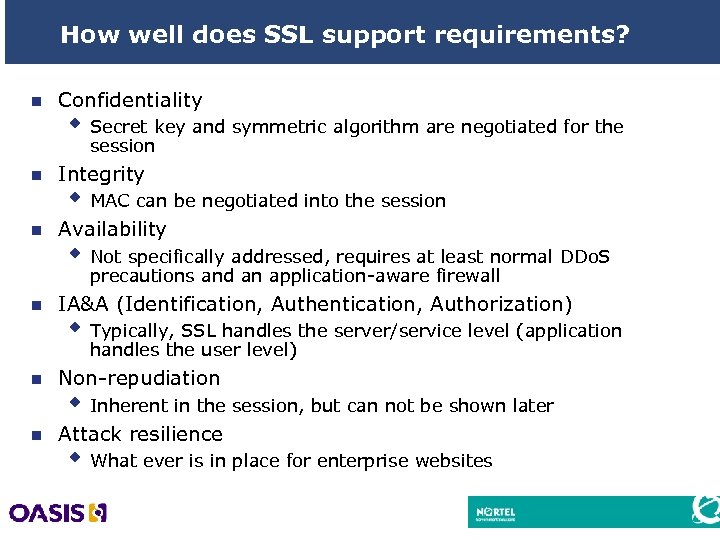
How well does SSL support requirements? n Confidentiality w Secret key and symmetric algorithm are negotiated for the session n Integrity n Availability w MAC can be negotiated into the session w Not specifically addressed, requires at least normal DDo. S precautions and an application-aware firewall n IA&A (Identification, Authentication, Authorization) w Typically, SSL handles the server/service level (application handles the user level) n Non-repudiation n Attack resilience w Inherent in the session, but can not be shown later w What ever is in place for enterprise websites 21
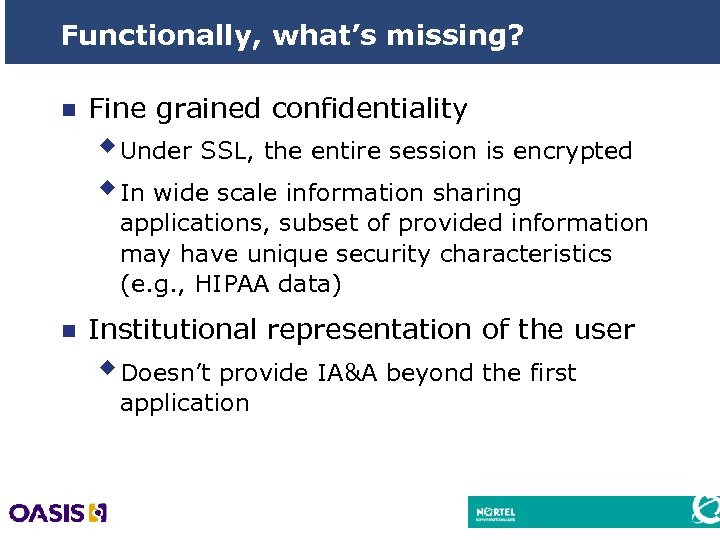
Functionally, what’s missing? n Fine grained confidentiality w Under SSL, the entire session is encrypted w In wide scale information sharing applications, subset of provided information may have unique security characteristics (e. g. , HIPAA data) n Institutional representation of the user w Doesn’t provide IA&A beyond the first application 22

What else is missing? n Non-repudiation is limited to the duration of the session (or application based) n Limited persistent security associations n There is no enterprise-wide statement and enforcement of policy n Security is dependent upon the organizational dynamic between application developers and infrastructure managers n Protection mechanisms befitting a mission critical application 23
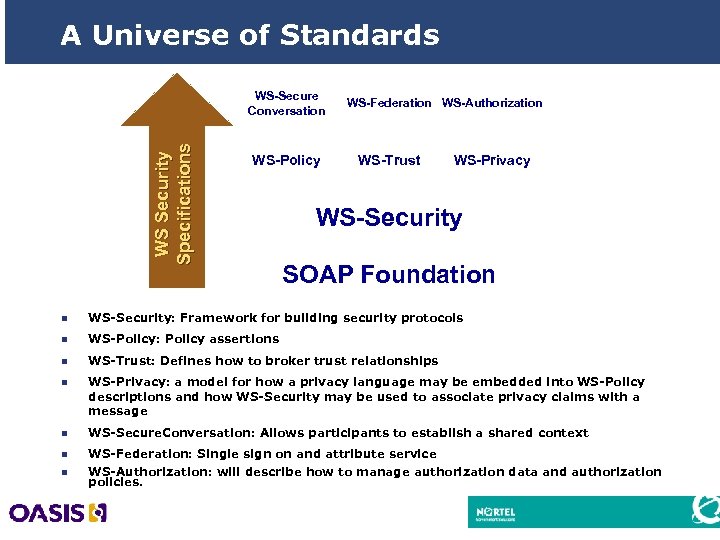
A Universe of Standards W S S e c u r i ty S p e c i fi c a ti o n s WS-Secure Conversation WS-Policy WS-Federation WS-Authorization WS-Trust WS-Privacy WS-Security SOAP Foundation n WS-Security: Framework for building security protocols n WS-Policy: Policy assertions n WS-Trust: Defines how to broker trust relationships n WS-Privacy: a model for how a privacy language may be embedded into WS-Policy descriptions and how WS-Security may be used to associate privacy claims with a message n WS-Secure. Conversation: Allows participants to establish a shared context n WS-Federation: Single sign on and attribute service n WS-Authorization: will describe how to manage authorization data and authorization policies. 24
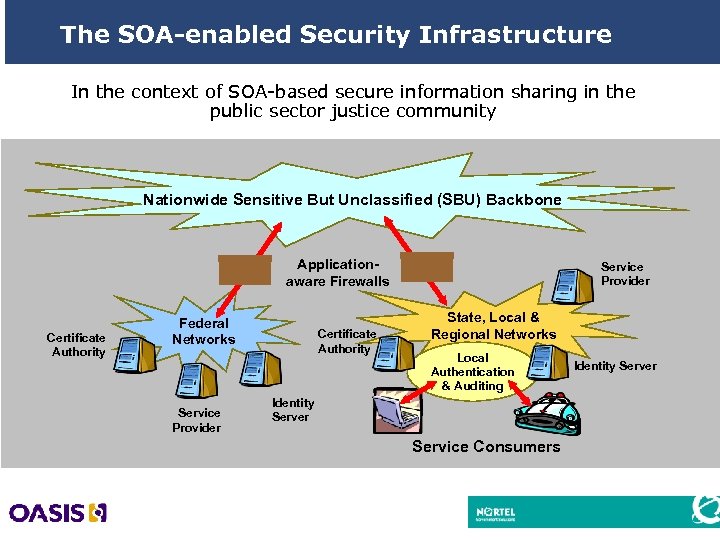
The SOA-enabled Security Infrastructure In the context of SOA-based secure information sharing in the public sector justice community Nationwide Sensitive But Unclassified (SBU) Backbone Applicationaware Firewalls Certificate Authority Federal Networks Service Provider Certificate Authority Service Provider State, Local & Regional Networks Local Authentication & Auditing Identity Server Service Consumers 25 Identity Server
Work for Government Implementers n For service owners, focus on applicationspecific details (where the devil is) w XML-based expression of identity, attributes, and privileges w Subject matter specific privacy tags n For infrastructure owners, focus on building the SOA-enabled infrastructure 26

SUMMARY 27

Lessons Learned n Providing self-service facilities is key to rapid adoption n Infrastructure exists today off-the-shelf to create pre-built templates for industry domains n Using open specifications allows integration into wide range of environments n Open source solutions allows partners to readily obtain technology n Use of partner id concept to manage partners and versioning interchanges 28
Challenges / Opportunities Today n Exposing synchronous and asynchronous interfacing to control content access n Open source solution components to allow unrestricted integration by partners n Leveraging loose coupling of web services n Combining best-of-breed solution with both eb. XML and Web services working together as formal model (e. g. Oracle SOA 10 g v 3 upgrade) n Industry best-practices and lessons learned (who has solved similar needs? ) 29

SOA – Future Challenges n As marketplace matures customers will demand core enabling components and features n Trend continuing toward services as solution not software (that’s good for services providers like us!) n Supporting complex infrastructure demands – such as ERP and BAM – will need robust rulebased solutions and tools n Integration with cool new desktop tools and services (Microsoft & Nortel) 30
Q&A Discussion Nortel Government Solutions For more information Visit our Website: http: //www. nortelgov. com 31

Acronym Soup n WSDL – web service description language n SOAP – simple object access protocol n eb. XML – e-Business XML n REST – Representational State Transfer – http-based exchanges n XSD – XML Schema (structure / layout) Definition n XML – e. Xtensible Markup Language n W 3 C – World Wide Web consortium n B 2 B – business to business n Mo. U – Memorandum of Understanding n TCP/IP – internet communications syntax 32
Project and Technology Resources n NIH e. RA Project site – http: //era. nih. gov n NIH S 2 S Resources site - http: //era. nih. gov/Electronic. Receipt/ n Commons online site – https: //commons. era. nih. gov/commons/ n Grants. gov online site – http: //www. grants. gov/Get. Started 33

Technology Resources n www. oasis-open. org n www. ebxml. org n www. freeb. XML. org www. ebxmlforum. org n www. apache. org 34
3e331b55fae02a2c03fb090cdd0ee53c.ppt