e2047f14a4ffa1a2b1a3233aae4be952.ppt
- Количество слайдов: 12

So. BGP vs SBGP Sharon Goldberg Princeton Routing Security Seminar June 27, 2006 and July 11, 2006 Princeton University Lightwave Communications Research Laboratory

s. BGP Review • A purist approach to secure the control plane using a centralized security approach • Origin Authentication – Origin Authentication Public Key Infrastructure (PKI) – Signed “Address Attestations” • Path Authentication – Autonomous System (AS) PKI – Nested Signatures in UPDATE Messages (Route Attestations) Princeton University
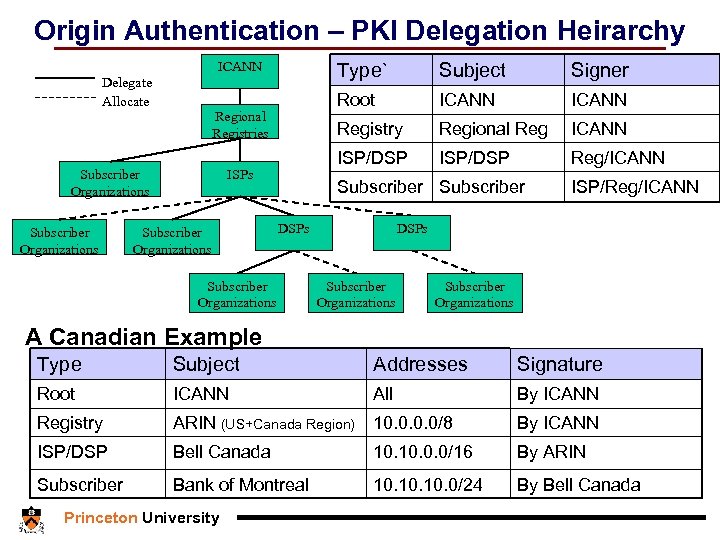
Origin Authentication – PKI Delegation Heirarchy ICANN Delegate Allocate Subscriber Organizations Signer ICANN Registry Regional Reg ICANN ISP/DSP ISPs Subject Root Regional Registries Subscriber Organizations Type` ISP/DSP Reg/ICANN Subscriber DSPs Subscriber Organizations ISP/Reg/ICANN DSPs Subscriber Organizations A Canadian Example Type Subject Addresses Signature Root ICANN All By ICANN Registry ARIN (US+Canada Region) 10. 0/8 By ICANN ISP/DSP Bell Canada 10. 0. 0/16 By ARIN Subscriber Bank of Montreal 10. 10. 0/24 By Bell Canada Princeton University
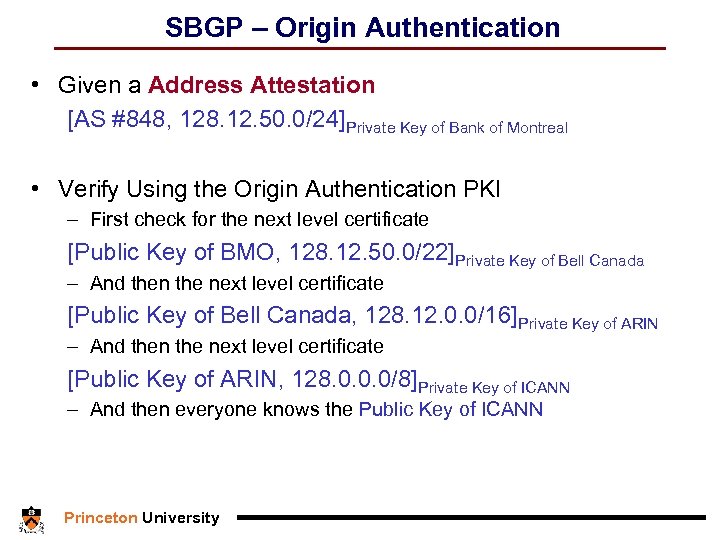
SBGP – Origin Authentication • Given a Address Attestation [AS #848, 128. 12. 50. 0/24]Private Key of Bank of Montreal • Verify Using the Origin Authentication PKI – First check for the next level certificate [Public Key of BMO, 128. 12. 50. 0/22]Private Key of Bell Canada – And then the next level certificate [Public Key of Bell Canada, 128. 12. 0. 0/16]Private Key of ARIN – And then the next level certificate [Public Key of ARIN, 128. 0. 0. 0/8]Private Key of ICANN – And then everyone knows the Public Key of ICANN Princeton University
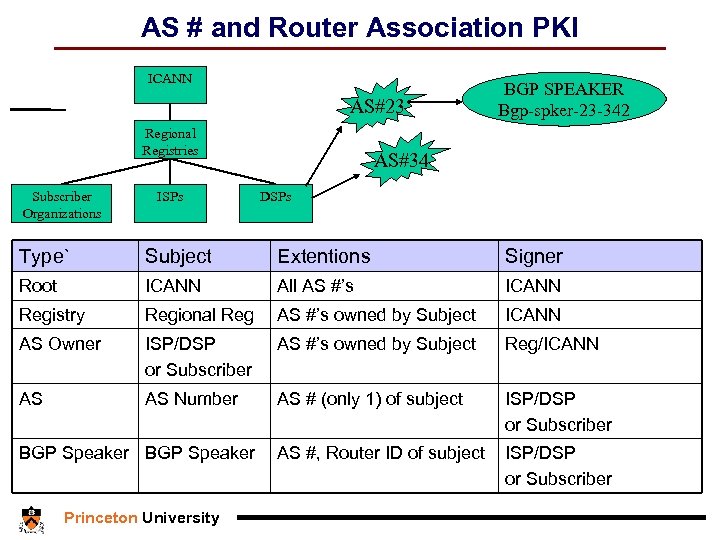
AS # and Router Association PKI ICANN AS#23 Regional Registries Subscriber Organizations ISPs BGP SPEAKER Bgp-spker-23 -342 AS#34 DSPs Type` Subject Extentions Signer Root ICANN All AS #’s ICANN Registry Regional Reg AS #’s owned by Subject ICANN AS Owner ISP/DSP or Subscriber AS #’s owned by Subject Reg/ICANN AS AS Number AS # (only 1) of subject ISP/DSP or Subscriber AS #, Router ID of subject ISP/DSP or Subscriber BGP Speaker Princeton University
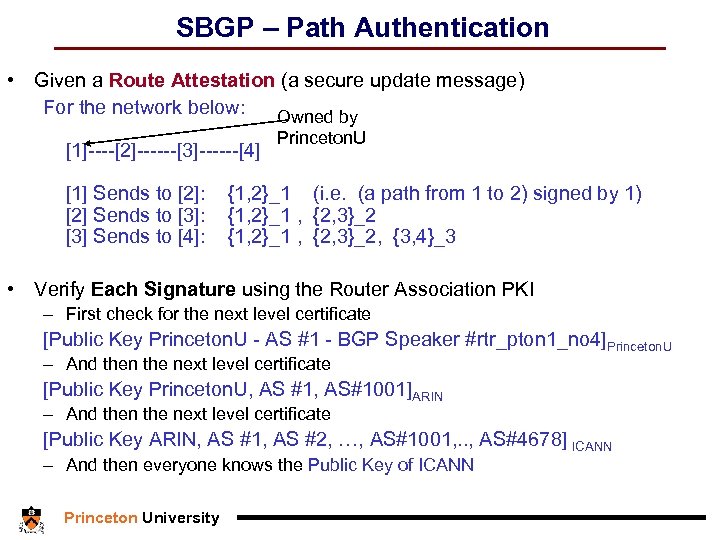
SBGP – Path Authentication • Given a Route Attestation (a secure update message) For the network below: Owned by [1]----[2]------[3]------[4] Princeton. U [1] Sends to [2]: {1, 2}_1 (i. e. (a path from 1 to 2) signed by 1) [2] Sends to [3]: {1, 2}_1 , {2, 3}_2 [3] Sends to [4]: {1, 2}_1 , {2, 3}_2, {3, 4}_3 • Verify Each Signature using the Router Association PKI – First check for the next level certificate [Public Key Princeton. U - AS #1 - BGP Speaker #rtr_pton 1_no 4]Princeton. U – And then the next level certificate [Public Key Princeton. U, AS #1, AS#1001]ARIN – And then the next level certificate [Public Key ARIN, AS #1, AS #2, …, AS#1001, . . , AS#4678] ICANN – And then everyone knows the Public Key of ICANN Princeton University
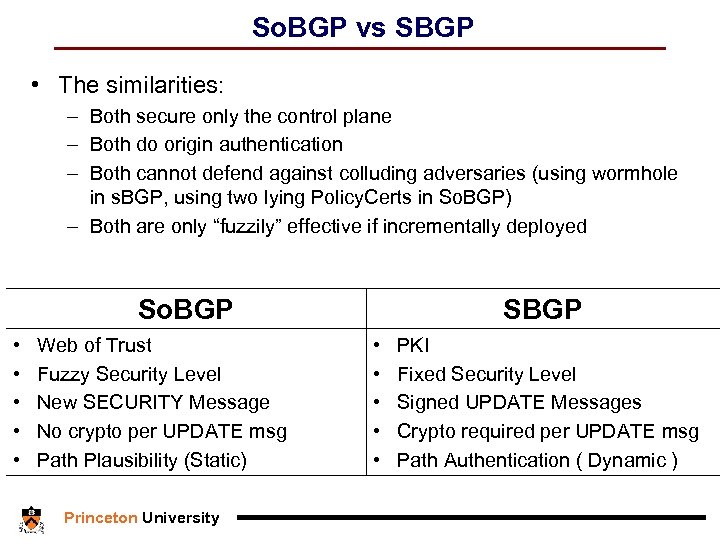
So. BGP vs SBGP • The similarities: – Both secure only the control plane – Both do origin authentication – Both cannot defend against colluding adversaries (using wormhole in s. BGP, using two lying Policy. Certs in So. BGP) – Both are only “fuzzily” effective if incrementally deployed So. BGP • Web of Trust • Fuzzy Security Level • New SECURITY Message • No crypto per UPDATE msg • Path Plausibility (Static) Princeton University SBGP • PKI • Fixed Security Level • Signed UPDATE Messages • Crypto required per UPDATE msg • Path Authentication ( Dynamic )
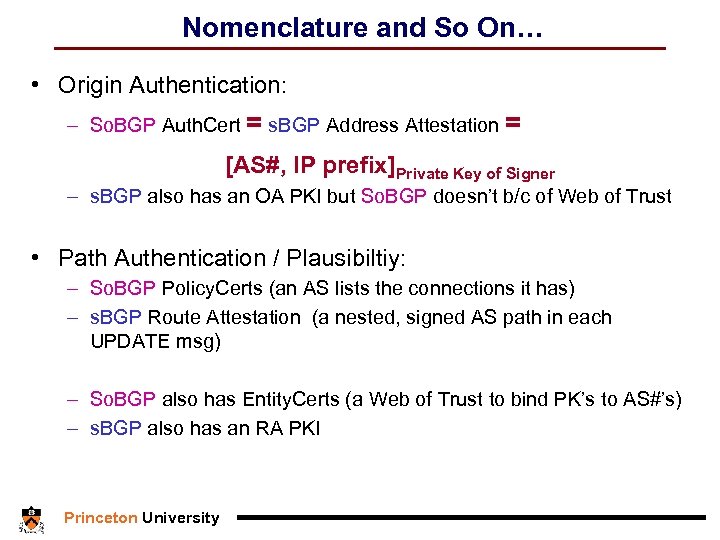
Nomenclature and So On… • Origin Authentication: – So. BGP Auth. Cert = s. BGP Address Attestation = [AS#, IP prefix]Private Key of Signer – s. BGP also has an OA PKI but So. BGP doesn’t b/c of Web of Trust • Path Authentication / Plausibiltiy: – So. BGP Policy. Certs (an AS lists the connections it has) – s. BGP Route Attestation (a nested, signed AS path in each UPDATE msg) – So. BGP also has Entity. Certs (a Web of Trust to bind PK’s to AS#’s) – s. BGP also has an RA PKI Princeton University
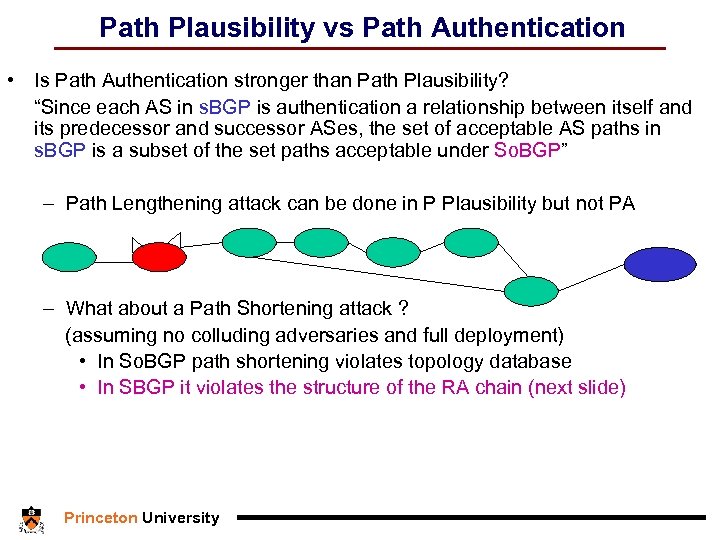
Path Plausibility vs Path Authentication • Is Path Authentication stronger than Path Plausibility? “Since each AS in s. BGP is authentication a relationship between itself and its predecessor and successor ASes, the set of acceptable AS paths in s. BGP is a subset of the set paths acceptable under So. BGP” – Path Lengthening attack can be done in P Plausibility but not PA – What about a Path Shortening attack ? (assuming no colluding adversaries and full deployment) • In So. BGP path shortening violates topology database • In SBGP it violates the structure of the RA chain (next slide) Princeton University
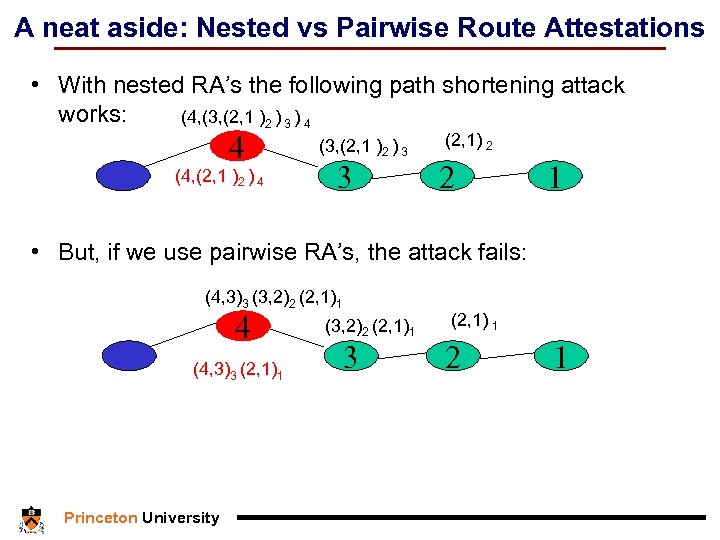
A neat aside: Nested vs Pairwise Route Attestations • With nested RA’s the following path shortening attack works: (4, (3, (2, 1 )2 ) 3 ) 4 4 (4, (2, 1 )2 ) 4 (3, (2, 1 )2 ) 3 3 (2, 1) 2 2 1 • But, if we use pairwise RA’s, the attack fails: (4, 3)3 (3, 2)2 (2, 1)1 4 (4, 3)3 (2, 1)1 Princeton University (3, 2)2 (2, 1)1 3 (2, 1) 1 2 1
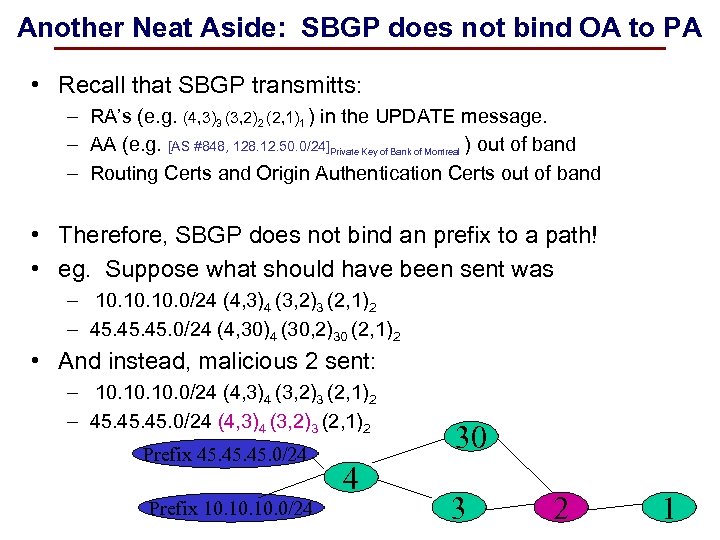
Another Neat Aside: SBGP does not bind OA to PA • Recall that SBGP transmitts: – RA’s (e. g. (4, 3)3 (3, 2)2 (2, 1)1 ) in the UPDATE message. – AA (e. g. [AS #848, 128. 12. 50. 0/24]Private Key of Bank of Montreal ) out of band – Routing Certs and Origin Authentication Certs out of band • Therefore, SBGP does not bind an prefix to a path! • eg. Suppose what should have been sent was – 10. 10. 0/24 (4, 3)4 (3, 2)3 (2, 1)2 – 45. 45. 0/24 (4, 30)4 (30, 2)30 (2, 1)2 • And instead, malicious 2 sent: – 10. 10. 0/24 (4, 3)4 (3, 2)3 (2, 1)2 – 45. 45. 0/24 (4, 3)4 (3, 2)3 (2, 1)2 Prefix 45. 45. 0/24 Prefix 10. 10. 0/24 Princeton University 4 30 3 2 1
So. BGP vs SBGP: Discussion • An now for Dan’s comments on performance… • How does Aggregation impact Origin Authentication? • With Web of Trust you can do anything!!! • Not so good with a centralized PKI. • SBGP vs So. BGP incremental deployment ? • Is Wo. T easier to deploy than PKI? • Benefits of partial deployment? • So. BGP has a new SECURITY message that could cause problems • Other thoughts? Princeton University
e2047f14a4ffa1a2b1a3233aae4be952.ppt