00cb59d7e0008a26c61990e1aa3033dc.ppt
- Количество слайдов: 32
 Situational Crime Prevention and the Mitigation of Cloud Computing Threats Chaz Vidal Supervisor: Raymond Choo
Situational Crime Prevention and the Mitigation of Cloud Computing Threats Chaz Vidal Supervisor: Raymond Choo
 Agenda • • • Introduction Cloud Computing Cybercrime and the Cloud Situational Crime Prevention SCP and Cybercrime Research Questions Conceptual Model Methodology Future Work 2
Agenda • • • Introduction Cloud Computing Cybercrime and the Cloud Situational Crime Prevention SCP and Cybercrime Research Questions Conceptual Model Methodology Future Work 2
 Introduction • Cloud Computing and Services has emerged as viable platform for the deployment of key computing resources. • Security of the Cloud Computing platform is a primary challenge in the deployment and acceptance of cloud computing services. • Attacks on Cloud environment may be considered as cybercrime and that situational crime prevention theories could be used to protect the cloud 3
Introduction • Cloud Computing and Services has emerged as viable platform for the deployment of key computing resources. • Security of the Cloud Computing platform is a primary challenge in the deployment and acceptance of cloud computing services. • Attacks on Cloud environment may be considered as cybercrime and that situational crime prevention theories could be used to protect the cloud 3
 Cloud Computing • Model for enabling network access to configurable computing resources quickly and with minimal interaction from service providers (Mell &Grance, NIST 2011) • Different models • Software as a Service • Platform as a Service • Infrastructure as a Service • Different delivery structures • • Private Public Community Hybrid • Although ubiquitious, security is still a primary concern for those who choose to use Cloud Computing. 4
Cloud Computing • Model for enabling network access to configurable computing resources quickly and with minimal interaction from service providers (Mell &Grance, NIST 2011) • Different models • Software as a Service • Platform as a Service • Infrastructure as a Service • Different delivery structures • • Private Public Community Hybrid • Although ubiquitious, security is still a primary concern for those who choose to use Cloud Computing. 4
 Cybercrime and the Cloud • Cloud Technology Vulnerabilities exploited for criminal gain and compromising information security • Virtual machine extraction of private information (Zhang et al. 2012) • Utilizing Cloud Computing servers for DDo. S attacks (Dawoud, Takouna & Meinel 2010) • Storage of contraband or illegal material on cloud storage. (Choo 2010) • Cybercrime as defined by the Australia Cybercrime Working Group (2013) • Crimes directed at networked technologies • Crimes where computers or ICT technologies are an integral part of of an offence. 5
Cybercrime and the Cloud • Cloud Technology Vulnerabilities exploited for criminal gain and compromising information security • Virtual machine extraction of private information (Zhang et al. 2012) • Utilizing Cloud Computing servers for DDo. S attacks (Dawoud, Takouna & Meinel 2010) • Storage of contraband or illegal material on cloud storage. (Choo 2010) • Cybercrime as defined by the Australia Cybercrime Working Group (2013) • Crimes directed at networked technologies • Crimes where computers or ICT technologies are an integral part of of an offence. 5
 Cybercrime Growth • Cybercrime incidents estimated cost $12 M each. (Paganini 2013) • Small and Medium business are growing targets for cybercrime. (Hutchings 2013) • These businesses are moving to cloud based resources because of cost effectiveness but criminals are expected to follow suit. • Number of incidences of cyber-crime against cloud services set to rise. (Price Waterhouse Coopers 2014) • Techniques to prevent or counteract cybercrime can be used based on traditional crime theories. 6
Cybercrime Growth • Cybercrime incidents estimated cost $12 M each. (Paganini 2013) • Small and Medium business are growing targets for cybercrime. (Hutchings 2013) • These businesses are moving to cloud based resources because of cost effectiveness but criminals are expected to follow suit. • Number of incidences of cyber-crime against cloud services set to rise. (Price Waterhouse Coopers 2014) • Techniques to prevent or counteract cybercrime can be used based on traditional crime theories. 6
 Situational Crime Prevention • Crime science seeks to explain how crime transpires. (Hartel, Junger & Wieringa 2010) • Different from criminology which seeks to frame the crime in the context of criminals and their motivations. • Prominent approach is Crime Opportunity Theory (Felson & Clarke 1998) • Opportunity “plays a role in all crime” • Aspects of Crime Opportunity Theory • Routine Activity • Crime Pattern • Rational Choice 7
Situational Crime Prevention • Crime science seeks to explain how crime transpires. (Hartel, Junger & Wieringa 2010) • Different from criminology which seeks to frame the crime in the context of criminals and their motivations. • Prominent approach is Crime Opportunity Theory (Felson & Clarke 1998) • Opportunity “plays a role in all crime” • Aspects of Crime Opportunity Theory • Routine Activity • Crime Pattern • Rational Choice 7
 Situational Crime Prevention • SCP Theory (Clarke, R 1997) • Directed at highly specific forms of crime • Management of the environment of crime • Makes crime less rewarding, more risky and less excusable for offenders • Physical crime changes introduced • More lighting • Frequent policing/monitoring • Removing expensive goods from shop fronts. 8
Situational Crime Prevention • SCP Theory (Clarke, R 1997) • Directed at highly specific forms of crime • Management of the environment of crime • Makes crime less rewarding, more risky and less excusable for offenders • Physical crime changes introduced • More lighting • Frequent policing/monitoring • Removing expensive goods from shop fronts. 8
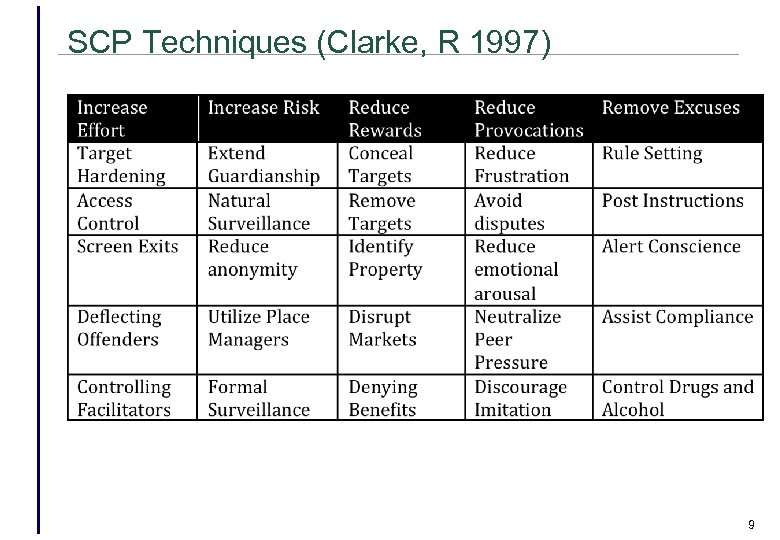 SCP Techniques (Clarke, R 1997) 9
SCP Techniques (Clarke, R 1997) 9
 Preventing Cybercrime in the Cloud • Traditional Methods (Vidal and Choo 2015) • Implementation of security policies ala ISO 27002 standards to implement security controls and increase security awareness. • Technology solutions to mitigate known Cloud Computing threats. • Crime Opportunity theories used in previous research: • Routine Activity Theory to model incidence of internet fraud. (Pratt 2010) • Phishing attempts to show where victimization rates are higher. (Leukfeldt 2014) • General cyber crime prevention using SCP (Beebe & Rao 2005) • Relationships of Information Security and SCP (Willison & Backhouse 2006) 10
Preventing Cybercrime in the Cloud • Traditional Methods (Vidal and Choo 2015) • Implementation of security policies ala ISO 27002 standards to implement security controls and increase security awareness. • Technology solutions to mitigate known Cloud Computing threats. • Crime Opportunity theories used in previous research: • Routine Activity Theory to model incidence of internet fraud. (Pratt 2010) • Phishing attempts to show where victimization rates are higher. (Leukfeldt 2014) • General cyber crime prevention using SCP (Beebe & Rao 2005) • Relationships of Information Security and SCP (Willison & Backhouse 2006) 10
 Cloud Computing and SCP • Given the available material and research, there is a lack of specific models that uses SCP against Cloud Computing threats. • Challenging because SCP needs to be addressed for specific types of crime and Cloud Computing can have varied threats against it. 11
Cloud Computing and SCP • Given the available material and research, there is a lack of specific models that uses SCP against Cloud Computing threats. • Challenging because SCP needs to be addressed for specific types of crime and Cloud Computing can have varied threats against it. 11
 Research Questions • Can SCP be utilized to develop a Conceptual Model for Cloud Computing Security? • Will the deployment of this Conceptual Model aid in change the environment sufficiently to affect Cloud Computing threats? • Will a Private Cloud Service Provider be receptive to the deployment of additional security measures? • Will Private Cloud Service consumers be affected by the deployment of additional security measures? 12
Research Questions • Can SCP be utilized to develop a Conceptual Model for Cloud Computing Security? • Will the deployment of this Conceptual Model aid in change the environment sufficiently to affect Cloud Computing threats? • Will a Private Cloud Service Provider be receptive to the deployment of additional security measures? • Will Private Cloud Service consumers be affected by the deployment of additional security measures? 12
 Conceptual Model Components • Cloud Computing Threats • Cloud Security Alliances Top Cloud Threats (Cloud Security Alliance 2013) • Using technological and process/policy based solutions to populate the model • ISO 27002 Information Security Standards • ASD Top 35 Mitigation Strategies. • Change the environment for crime • • • Increase Effort Increase Risk Decrease Reward Remove Provocations Remove Excuses 13
Conceptual Model Components • Cloud Computing Threats • Cloud Security Alliances Top Cloud Threats (Cloud Security Alliance 2013) • Using technological and process/policy based solutions to populate the model • ISO 27002 Information Security Standards • ASD Top 35 Mitigation Strategies. • Change the environment for crime • • • Increase Effort Increase Risk Decrease Reward Remove Provocations Remove Excuses 13
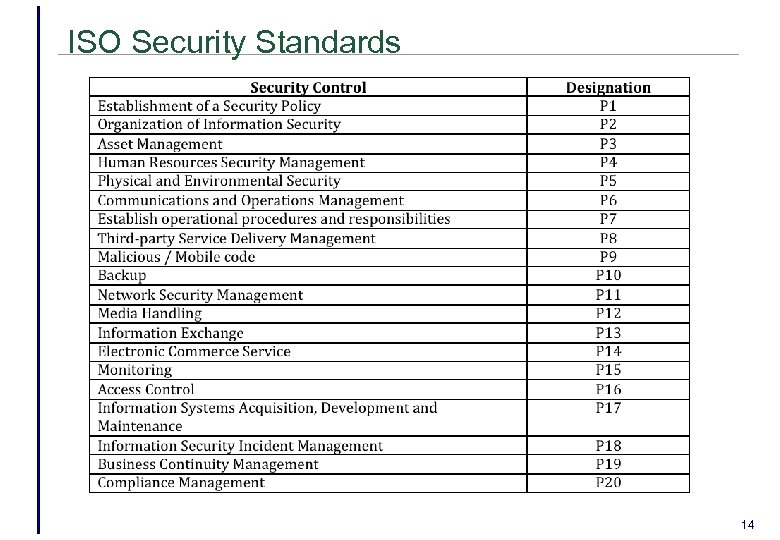 ISO Security Standards 14
ISO Security Standards 14
 ASD Top 35 Strategies to Mitigate Cyber Intrusions 15
ASD Top 35 Strategies to Mitigate Cyber Intrusions 15
 ASD Top 35 Strategies to Mitigate Cyber Intrusions 16
ASD Top 35 Strategies to Mitigate Cyber Intrusions 16
 CSA Top Threats • • • Data Breaches Data Loss Account or Service Traffic Hijacking Insecure Interfaces Denial of Service Malicious Insiders Abuse of Cloud Services Insufficient Due Diligence Shared Technology Vulnerabilities 17
CSA Top Threats • • • Data Breaches Data Loss Account or Service Traffic Hijacking Insecure Interfaces Denial of Service Malicious Insiders Abuse of Cloud Services Insufficient Due Diligence Shared Technology Vulnerabilities 17
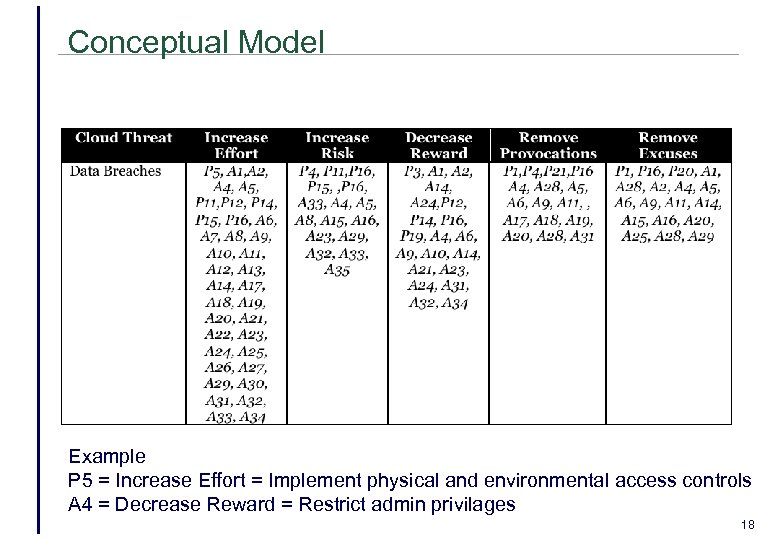 Conceptual Model Example P 5 = Increase Effort = Implement physical and environmental access controls A 4 = Decrease Reward = Restrict admin privilages 18
Conceptual Model Example P 5 = Increase Effort = Implement physical and environmental access controls A 4 = Decrease Reward = Restrict admin privilages 18
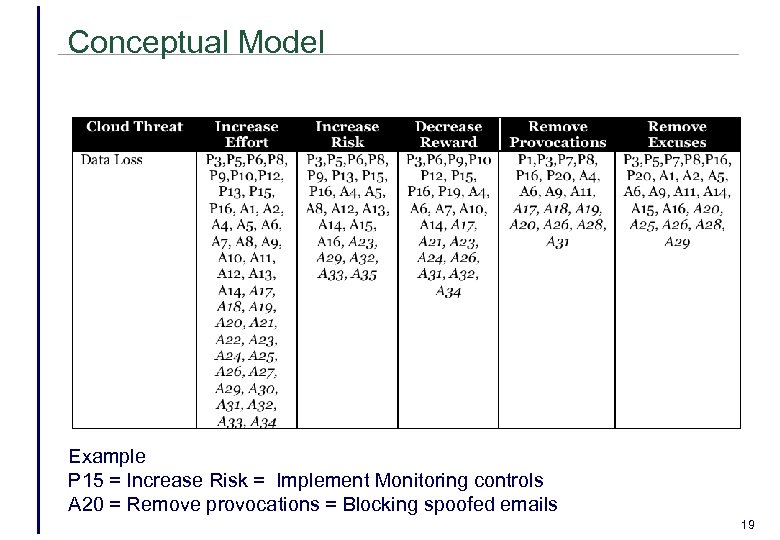 Conceptual Model Example P 15 = Increase Risk = Implement Monitoring controls A 20 = Remove provocations = Blocking spoofed emails 19
Conceptual Model Example P 15 = Increase Risk = Implement Monitoring controls A 20 = Remove provocations = Blocking spoofed emails 19
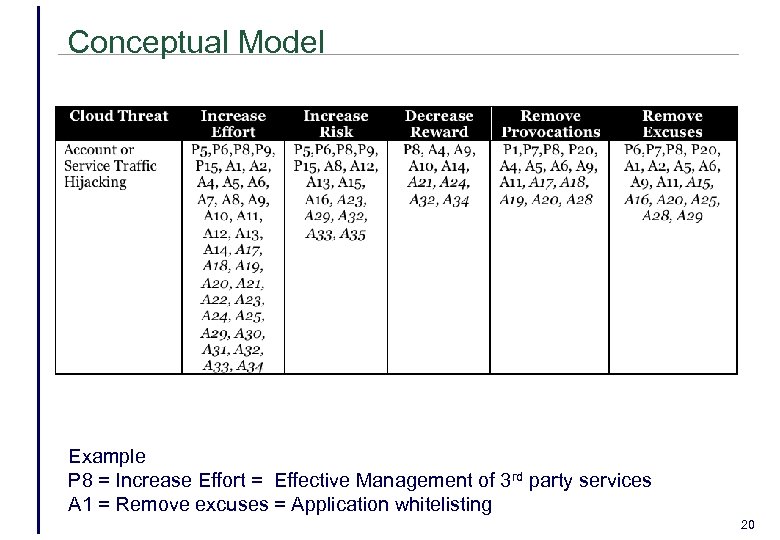 Conceptual Model Example P 8 = Increase Effort = Effective Management of 3 rd party services A 1 = Remove excuses = Application whitelisting 20
Conceptual Model Example P 8 = Increase Effort = Effective Management of 3 rd party services A 1 = Remove excuses = Application whitelisting 20
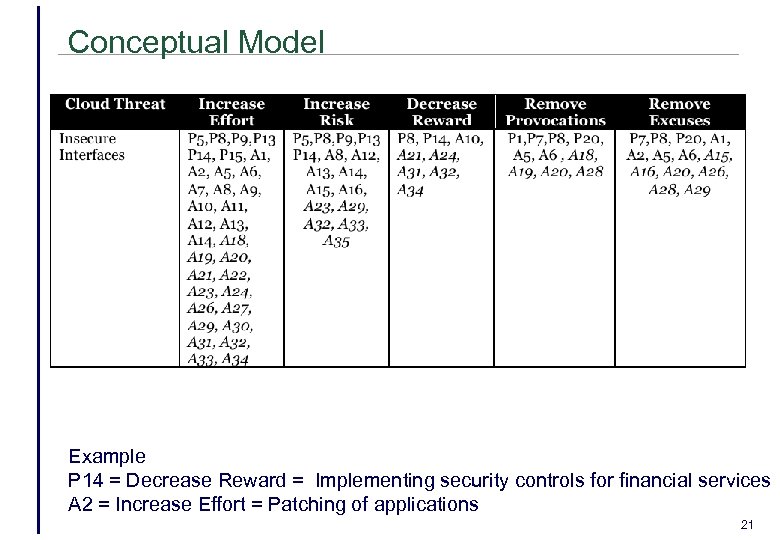 Conceptual Model Example P 14 = Decrease Reward = Implementing security controls for financial services A 2 = Increase Effort = Patching of applications 21
Conceptual Model Example P 14 = Decrease Reward = Implementing security controls for financial services A 2 = Increase Effort = Patching of applications 21
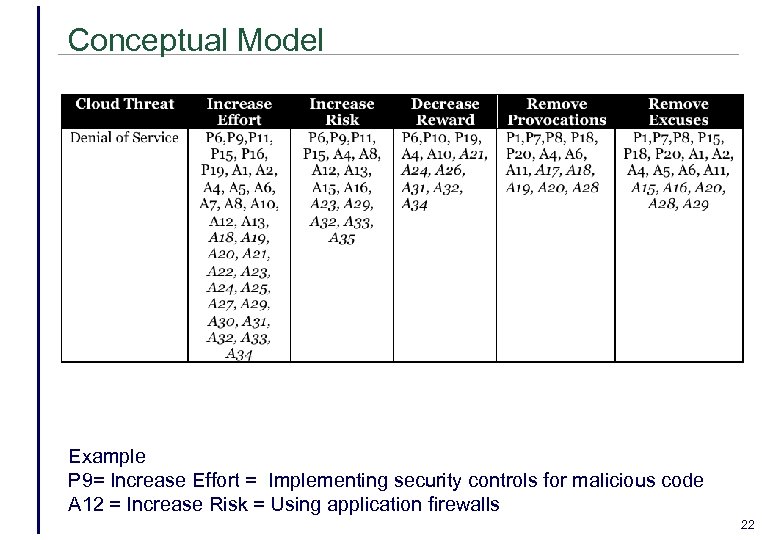 Conceptual Model Example P 9= Increase Effort = Implementing security controls for malicious code A 12 = Increase Risk = Using application firewalls 22
Conceptual Model Example P 9= Increase Effort = Implementing security controls for malicious code A 12 = Increase Risk = Using application firewalls 22
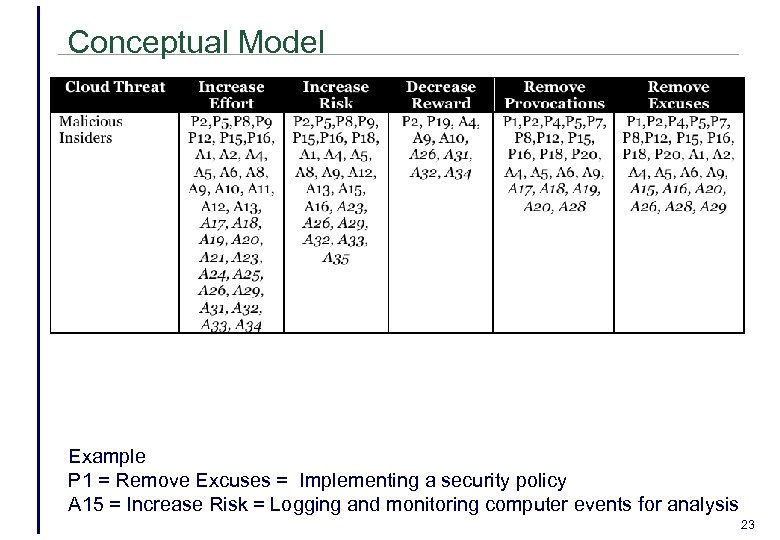 Conceptual Model Example P 1 = Remove Excuses = Implementing a security policy A 15 = Increase Risk = Logging and monitoring computer events for analysis 23
Conceptual Model Example P 1 = Remove Excuses = Implementing a security policy A 15 = Increase Risk = Logging and monitoring computer events for analysis 23
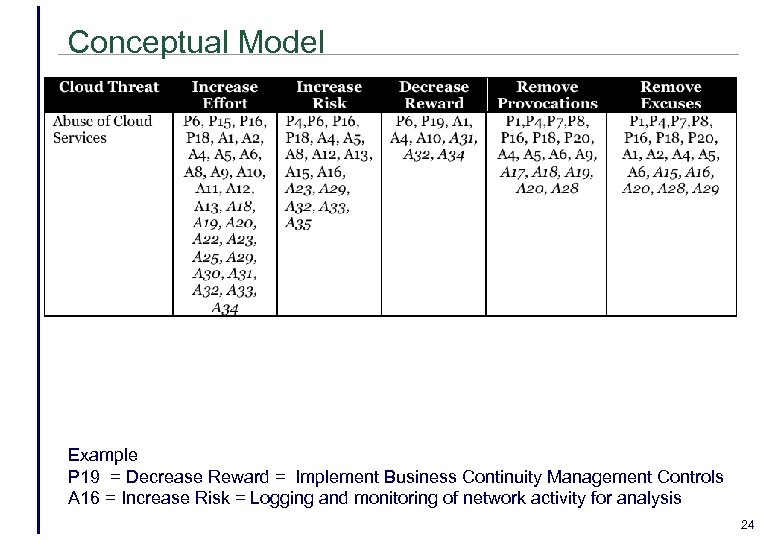 Conceptual Model Example P 19 = Decrease Reward = Implement Business Continuity Management Controls A 16 = Increase Risk = Logging and monitoring of network activity for analysis 24
Conceptual Model Example P 19 = Decrease Reward = Implement Business Continuity Management Controls A 16 = Increase Risk = Logging and monitoring of network activity for analysis 24
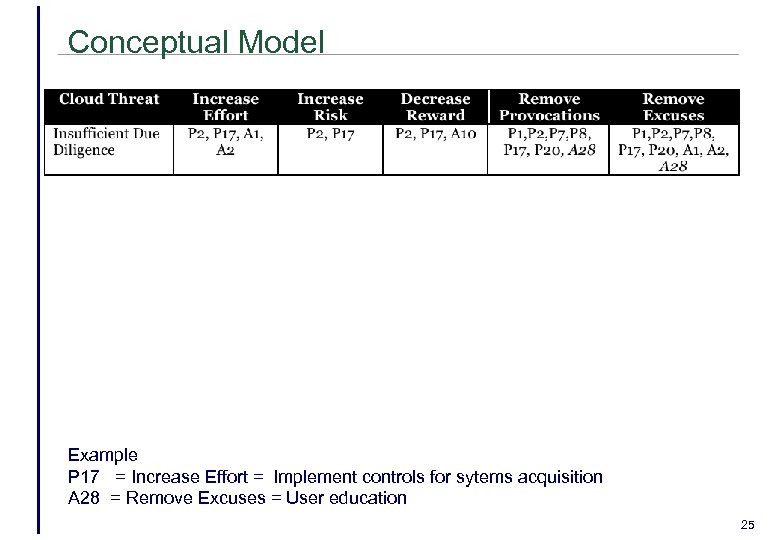 Conceptual Model Example P 17 = Increase Effort = Implement controls for sytems acquisition A 28 = Remove Excuses = User education 25
Conceptual Model Example P 17 = Increase Effort = Implement controls for sytems acquisition A 28 = Remove Excuses = User education 25
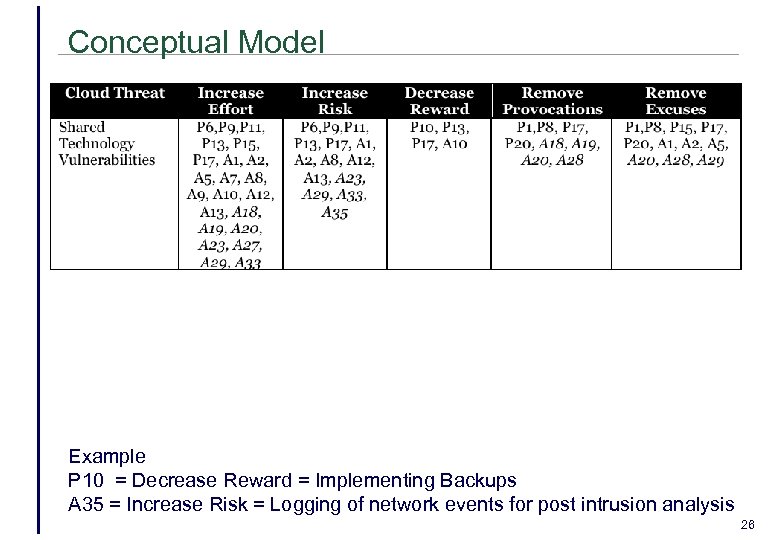 Conceptual Model Example P 10 = Decrease Reward = Implementing Backups A 35 = Increase Risk = Logging of network events for post intrusion analysis 26
Conceptual Model Example P 10 = Decrease Reward = Implementing Backups A 35 = Increase Risk = Logging of network events for post intrusion analysis 26
 Methodology • Approaching a Private Iaa. S Service Provider • Studied through work done and published in Vidal, Choo 2015. • Qualitative Research through semi-structured Interviews with a Private Cloud administrators, managers and consumers • Understand their awareness of Cloud Security threats • Understand awareness of security measures already available • Indicate receptiveness to additional or enhanced security measures • View of effectiveness of changing environment to deter criminal activity 27
Methodology • Approaching a Private Iaa. S Service Provider • Studied through work done and published in Vidal, Choo 2015. • Qualitative Research through semi-structured Interviews with a Private Cloud administrators, managers and consumers • Understand their awareness of Cloud Security threats • Understand awareness of security measures already available • Indicate receptiveness to additional or enhanced security measures • View of effectiveness of changing environment to deter criminal activity 27
 Findings and Conclusions • Results of interviews 28
Findings and Conclusions • Results of interviews 28
 Future Work • Possibility of implementation parts of the conceptual model to existing Cloud Computing or Iaa. S environments. • Measuring effectiveness of the model through reduction of security incidents 29
Future Work • Possibility of implementation parts of the conceptual model to existing Cloud Computing or Iaa. S environments. • Measuring effectiveness of the model through reduction of security incidents 29
 References Mell, P & Grance, T 2011, 'The NIST definition of cloud computing'. Zhang, Y, Juels, A, Reiter, MK & Ristenpart, T 2012, 'Cross-VM side channels and their use to extract private keys', Proceedings of the 2012 ACM conference on Computer and communications security, ACM, pp. 305 -316. Dawoud, W, Takouna, I & Meinel, C 2010, 'Infrastructure as a service security: Challenges and solutions', Informatics and Systems (INFOS), 2010 The 7 th International Conference on, IEEE, pp. 1 -8. Choo, K-KR 2010, Cloud computing challenges and future directions, Australian Institute of Criminology, Canberra. Attorney-General's Department 2013, National Plan to Combat Cybercrime, Canberra, ACT, Australia. Paganini, P 2013, 2013 - The Impact of Cybercrime, Infosec Institute. Hutchings, A, Smith, RG & James, L 2013, 'Cloud computing for small business: Criminal and security threats and prevention measures'. 30
References Mell, P & Grance, T 2011, 'The NIST definition of cloud computing'. Zhang, Y, Juels, A, Reiter, MK & Ristenpart, T 2012, 'Cross-VM side channels and their use to extract private keys', Proceedings of the 2012 ACM conference on Computer and communications security, ACM, pp. 305 -316. Dawoud, W, Takouna, I & Meinel, C 2010, 'Infrastructure as a service security: Challenges and solutions', Informatics and Systems (INFOS), 2010 The 7 th International Conference on, IEEE, pp. 1 -8. Choo, K-KR 2010, Cloud computing challenges and future directions, Australian Institute of Criminology, Canberra. Attorney-General's Department 2013, National Plan to Combat Cybercrime, Canberra, ACT, Australia. Paganini, P 2013, 2013 - The Impact of Cybercrime, Infosec Institute. Hutchings, A, Smith, RG & James, L 2013, 'Cloud computing for small business: Criminal and security threats and prevention measures'. 30
 References PWC 2014, US Cybercrime: Rising risks, reduced readiness. Key findings from the 2014 US State of Cybercrime Survey, Price Waterhouse Coopers Hartel, P, Junger, M & Wieringa, R 2010, 'Cyber-crime science= crime science+ information security'. Felson, M & Clarke, RVG 1998, Opportunity makes the thief: Practical theory for crime prevention, Home Office, Policing and Reducing Crime Unit, Research, Development and Statistics Directorate London. Clarke, R 1997, Situational crime prevention, Criminal Justice Press Monsey, NY. Vidal, C & Choo, R 2015, 'The current state of an Iaa. S provider', in R Ko & KKR Choo (eds), The Cloud Security Ecosystem: Technical, Legal, Business and Management Issues, Syngress, Massachusetts, USA, pp. 401 -426. Pratt, TC, Holtfreter, K & Reisig, MD 2010, 'Routine Online Activity and Internet Fraud Targeting: Extending the Generality of Routine Activity Theory', Journal of Research in Crime and Delinquency, vol. 47, no. 3, pp. 267 -296. 31
References PWC 2014, US Cybercrime: Rising risks, reduced readiness. Key findings from the 2014 US State of Cybercrime Survey, Price Waterhouse Coopers Hartel, P, Junger, M & Wieringa, R 2010, 'Cyber-crime science= crime science+ information security'. Felson, M & Clarke, RVG 1998, Opportunity makes the thief: Practical theory for crime prevention, Home Office, Policing and Reducing Crime Unit, Research, Development and Statistics Directorate London. Clarke, R 1997, Situational crime prevention, Criminal Justice Press Monsey, NY. Vidal, C & Choo, R 2015, 'The current state of an Iaa. S provider', in R Ko & KKR Choo (eds), The Cloud Security Ecosystem: Technical, Legal, Business and Management Issues, Syngress, Massachusetts, USA, pp. 401 -426. Pratt, TC, Holtfreter, K & Reisig, MD 2010, 'Routine Online Activity and Internet Fraud Targeting: Extending the Generality of Routine Activity Theory', Journal of Research in Crime and Delinquency, vol. 47, no. 3, pp. 267 -296. 31
 References Leukfeldt, ER 2014, 'Phishing for suitable targets in the Netherlands: Routine activity theory and phishing victimization', Cyberpsychology, Behavior, and Social Networking, vol. 17, no. 8, pp. 551 -555. Beebe, NL & Rao, VS 2005, 'Using situational crime prevention theory to explain the effectiveness of information systems security', Proceedings of the 2005 software conference, Las Vegas. Willison, R & Backhouse, J 2006, 'Opportunities for computer crime: considering systems risk from a criminological perspective', European journal of information systems, vol. 15, no. 4, pp. 403 -414. Cloud Security Alliance 2013, 'The Notorious nine: cloud computing top threats in 2013', Cloud Security Alliance. AS/NZS 2006, ISO/IEC 27002: 2006 - Information Technology - Security Techniques - Code of Practice for Information Security Management, Australian Signals Directorate 2014, Strategies to Mitigate Targeted Cyber Intrusions, Canberra. 32
References Leukfeldt, ER 2014, 'Phishing for suitable targets in the Netherlands: Routine activity theory and phishing victimization', Cyberpsychology, Behavior, and Social Networking, vol. 17, no. 8, pp. 551 -555. Beebe, NL & Rao, VS 2005, 'Using situational crime prevention theory to explain the effectiveness of information systems security', Proceedings of the 2005 software conference, Las Vegas. Willison, R & Backhouse, J 2006, 'Opportunities for computer crime: considering systems risk from a criminological perspective', European journal of information systems, vol. 15, no. 4, pp. 403 -414. Cloud Security Alliance 2013, 'The Notorious nine: cloud computing top threats in 2013', Cloud Security Alliance. AS/NZS 2006, ISO/IEC 27002: 2006 - Information Technology - Security Techniques - Code of Practice for Information Security Management, Australian Signals Directorate 2014, Strategies to Mitigate Targeted Cyber Intrusions, Canberra. 32


