6e3f29d9944e20bf5589f2a2380155c8.ppt
- Количество слайдов: 122

SIP Tutorial Introduction to SIP Original Slides by Alan Johnston and Henry Sinnreich, MCI (at VON’ 03(

Contents SIP Overview SIP in detail SIP Call Flow Scenarios SIP Security SIP Programming Some Related Works 2

SIP Overview What SIP is, Multimedia Protocol Stack, Short History and Related Protocols are included.
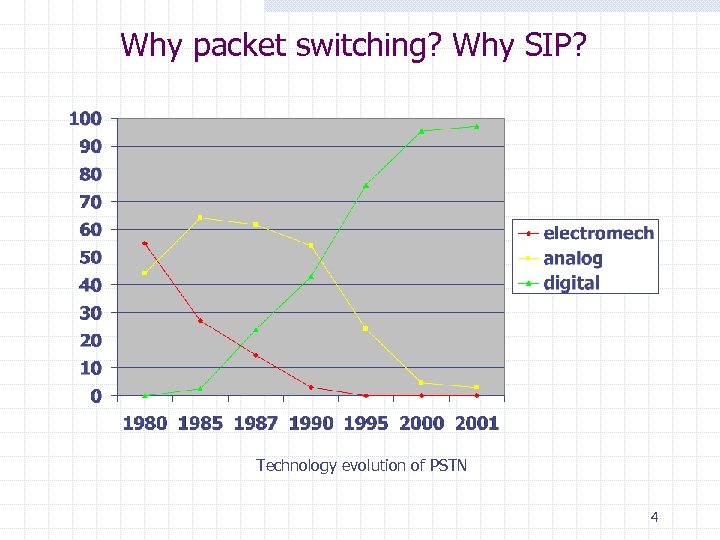
Why packet switching? Why SIP? Technology evolution of PSTN 4

Session Initiation Protocol Overview Application Layer Signaling Protocol Used to establish, modify, and terminate multimedia sessions Part of Internet Multimedia Architecture Can use UDP, TCP, TLS, SCTP, etc. Based on HTTP (Web) n n Similar text-based structure Uses URIs (Uniform Resource Indicators) Applications include (but not limited to): n Voice, video, gaming, instant messaging, presence, call control, etc. 5

Security & Privacy SIP Authentication n Challenge/Response based on shared secret - SIP Digest Mechanism also used by HTTP Used for client devices Encryption using private/public keys n Used between servers Privacy and security n SIP signaling can be encrypted w S/MIME (Secure/Multipurpose Internet Mail Extensions) n n Defined in RFC 2633 SIP can be transported over w IPSec n Defined in RFC 2401 w TLS (Transport Layer Security) n Defined in RFC 2246 6
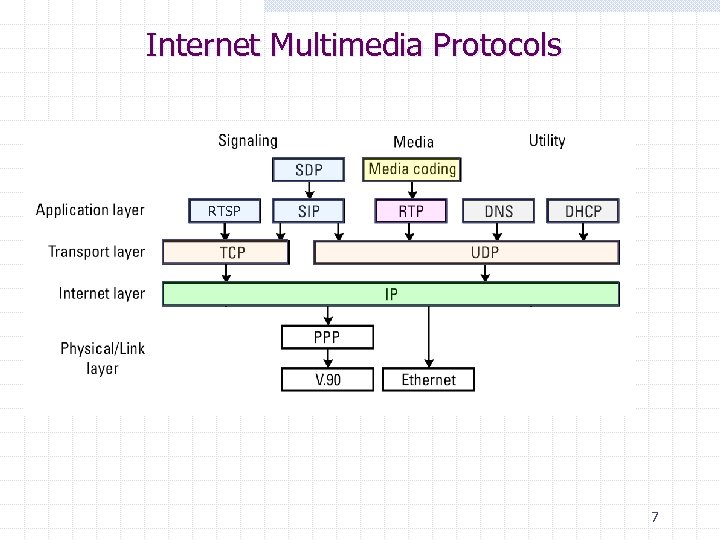
Internet Multimedia Protocols RTSP 7
A Short History of SIP Internet Engineering Task Force (IETF) protocol Inventors: M. Handley, H. Schulzrinne, E. Schooler, and J. Rosenberg Became “Proposed Standard” and RFC 2543 in March 1999 in MMUSIC WG. Separate SIP WG established in September 1999. Now new SIPPING (applications) and SIMPLE (presence and instant messaging) WGs using SIP. RFC 2543 bis-09 I-D became RFC 3261 in June 2002 n n n Added four new authors: G. Camarillo, A. Johnston, J. Peterson, and R. Sparks. Entire spec rewritten for clarity, but some new features Mostly backwards compatible with RFC 2543 8
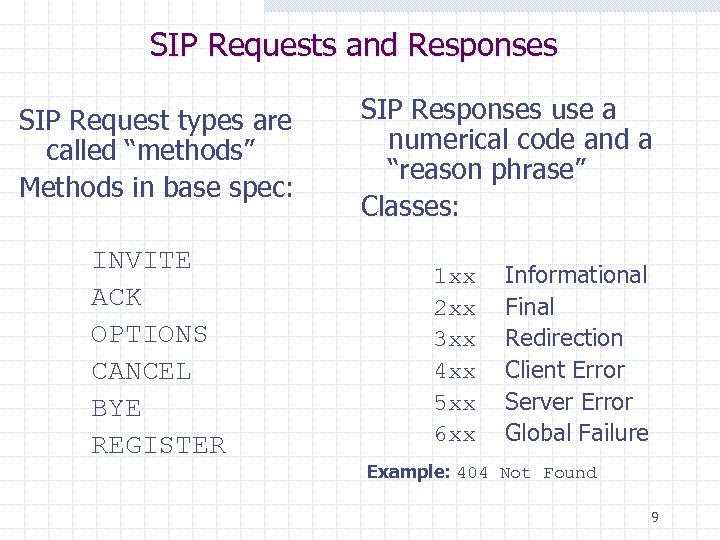
SIP Requests and Responses SIP Request types are called “methods” Methods in base spec: INVITE ACK OPTIONS CANCEL BYE REGISTER SIP Responses use a numerical code and a “reason phrase” Classes: 1 xx 2 xx 3 xx 4 xx 5 xx 6 xx Informational Final Redirection Client Error Server Error Global Failure Example: 404 Not Found 9

Related Protocols: SDP SIP carries (encapsulates) SDP messages SDP specifies codecs and media termination points Only one of many possible MIME attachments carried by SIP Ø SDP – Session Description Protocol Used to describe media session. Ø Carried as a message body in SIP messages. Ø Is a text-based protocol Ø Uses RTP/AVP Profiles for common media types Ø Defined by RFC 2327 Ø w E. g. RFC 3551 “RTP Profile for Audio and Video Conferences with Minimal Control” 10
Related Protocol: RTP Ø RTP – Real-time Transport Protocol Ø Used to transport media packets over IP Ø RTP adds a bit-oriented header containing: Ø name of media source Ø timestamp Ø codec type Ø sequence number Ø Defined by H. Schulzrinne et al, RFC 1889. Ø Profiles defined by RFC 1890. Ø RTCP for exchange of participant and quality reports. 11
SIP Uniform Resource Indicators (URIs) Same form as email addresses: user@domain Ø Two URI schemes: Ø Ø sip: henry@siptest. mci. com is a SIP URI Ø Most common form introduced in RFC 2543 Ø sips: henry@siptest. mci. com is a Secure SIP Ø New scheme introduced in RFC 3261 Ø Requires TLS over TCP as transport for security Ø URI Two types of SIP URIs: Ø Address of Record (AOR) (identifies a user) sip: henry@mci. com (Needs DNS SRV records to locate SIP Servers for mci. com domain) Ø Contact (identifies a device and is usually a Fully Qualified Domain Name, FQDN) Ø sip: henry@127. 24. 45. 4 or sip: henry@cube 43. lab. mci. com (Which needs no resolution for routing) Ø 12
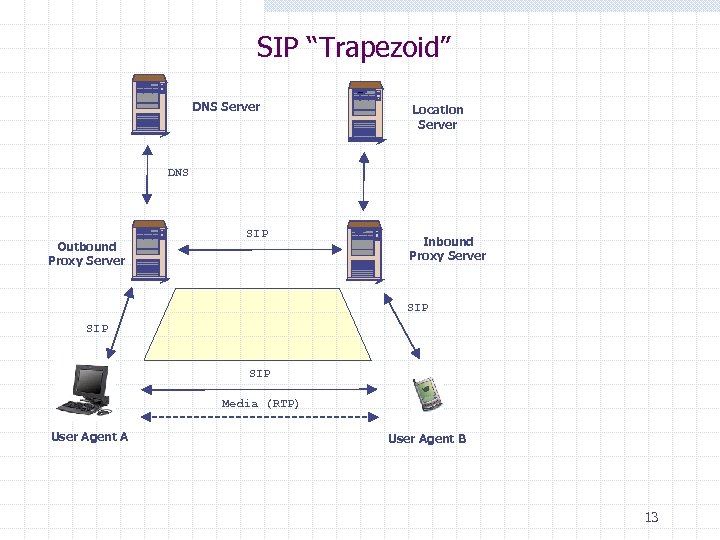
SIP “Trapezoid” DNS Server Location Server DNS Outbound Proxy Server SIP Inbound Proxy Server SIP SIP Media (RTP) User Agent A User Agent B 13
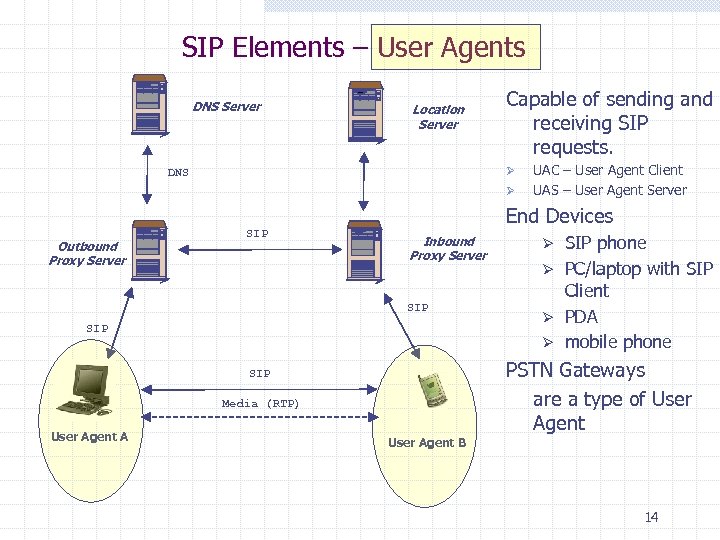
SIP Elements – User Agents DNS Server Location Server Capable of sending and receiving SIP requests. Ø DNS Ø Outbound Proxy Server SIP End Devices Inbound Proxy Server SIP SIP phone Ø PC/laptop with SIP Client Ø PDA Ø mobile phone Ø PSTN Gateways are a type of User Agent SIP Media (RTP) User Agent A UAC – User Agent Client UAS – User Agent Server User Agent B 14
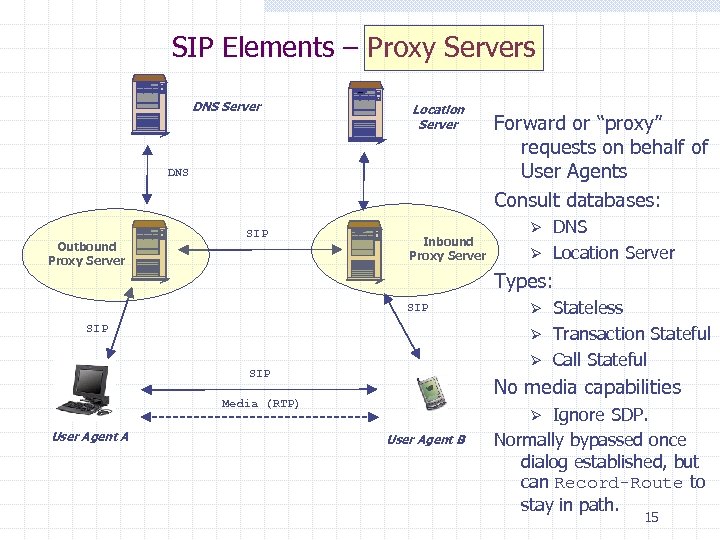
SIP Elements – Proxy Servers DNS Server Location Server DNS Outbound Proxy Server SIP Inbound Proxy Server DNS Ø Location Server Ø Types: SIP SIP Stateless Ø Transaction Stateful Ø Call Stateful Ø No media capabilities Media (RTP) User Agent A Forward or “proxy” requests on behalf of User Agents Consult databases: Ignore SDP. Normally bypassed once dialog established, but can Record-Route to stay in path. Ø User Agent B 15
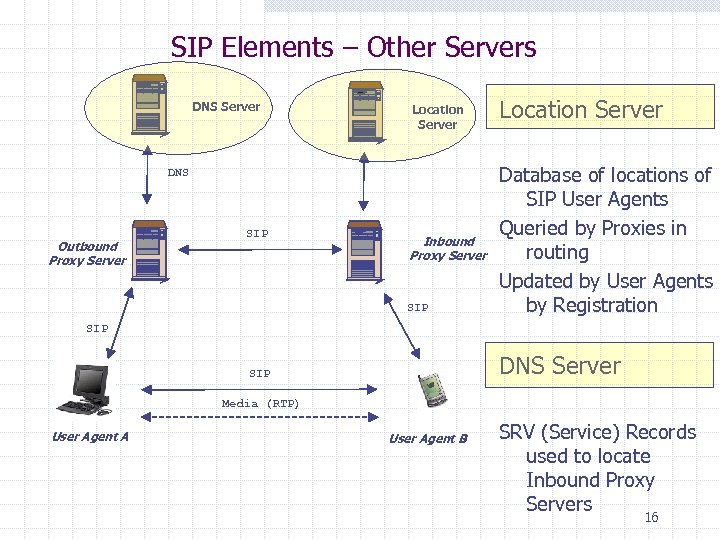
SIP Elements – Other Servers DNS Server Location Server DNS Outbound Proxy Server SIP Inbound Proxy Server SIP Location Server Database of locations of SIP User Agents Queried by Proxies in routing Updated by User Agents by Registration SIP DNS Server SIP Media (RTP) User Agent A User Agent B SRV (Service) Records used to locate Inbound Proxy Servers 16

SIP Client and Server SIP Elements are either n n User Agents (end devices that initiate and terminate media sessions) Servers (that assist in session setup) w Proxies w Registrars w Redirect servers A User Agent acts as a n n Client when it initiates a request (UAC) Server when it responds to a request (UAS) 17
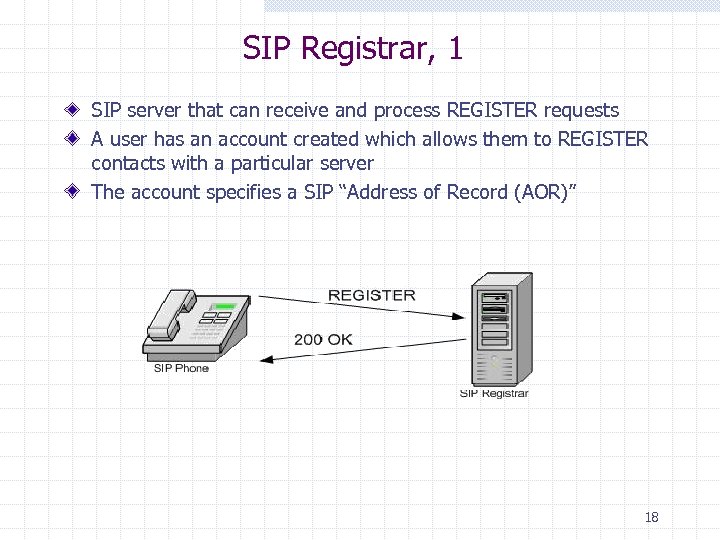
SIP Registrar, 1 SIP server that can receive and process REGISTER requests A user has an account created which allows them to REGISTER contacts with a particular server The account specifies a SIP “Address of Record (AOR)” 18

SIP Registrar, 2 SIP Registrars store the location of SIP endpoints n Each SIP endpoint Registers w with a Registrar using it’s Address of Record and Contact address w Address of Record for John Smith in From: header From: John Smith <sip: jsmith@zultys. com w Contact: header tells Registrar where to send messages Contact: John Smith <sip: jsmith@192. 168. 1. 100> SIP Proxies n n query SIP Registrars for routing information Incoming calls addressed to sip: jsmith@zultys. com w now routed by the Proxy to the Contact: header URL sip: jsmith@192. 168. 1. 100 19
Proxy Server SIP Proxy servers route SIP messages n Stateless Proxies use stateless protocols like UDP to talk to endpoints w Low Proxy overhead w Ephemeral connections, dropped as soon as message is forwarded n Stateful Proxies use TCP or other stateful protocols to set up a permanent connection w High Proxy overhead w Endpoint connection must be set up, maintained and torn down for the duration of the session 20
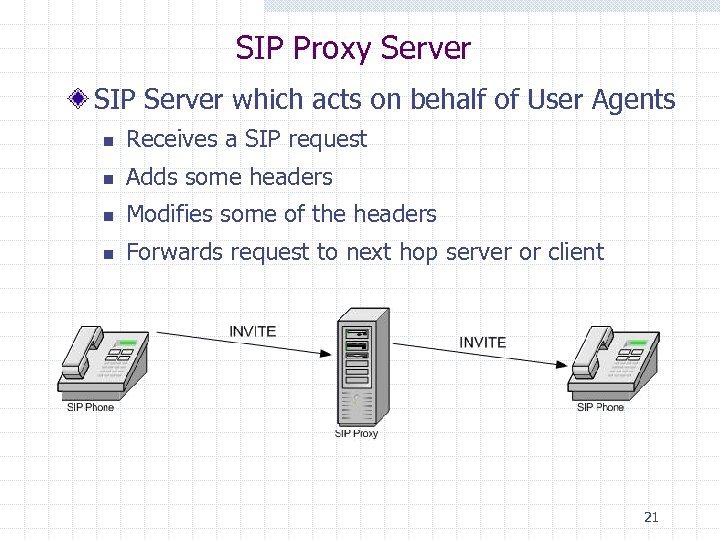
SIP Proxy Server SIP Server which acts on behalf of User Agents n Receives a SIP request n Adds some headers n Modifies some of the headers n Forwards request to next hop server or client 21
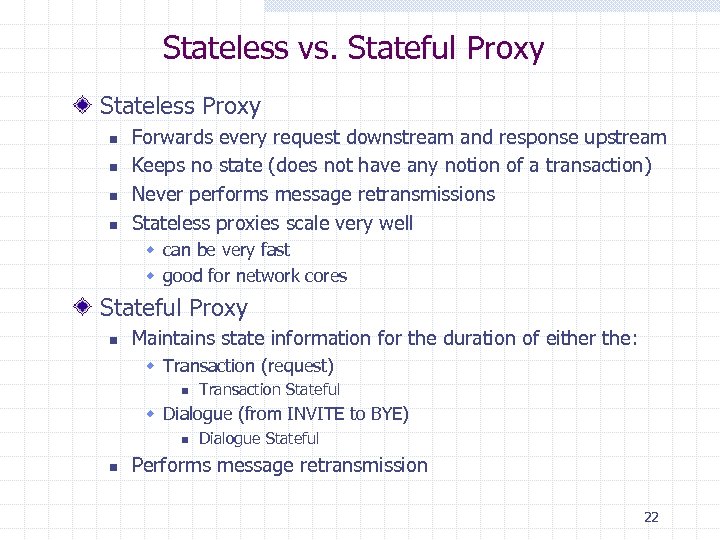
Stateless vs. Stateful Proxy Stateless Proxy n n Forwards every request downstream and response upstream Keeps no state (does not have any notion of a transaction) Never performs message retransmissions Stateless proxies scale very well w can be very fast w good for network cores Stateful Proxy n Maintains state information for the duration of either the: w Transaction (request) n Transaction Stateful w Dialogue (from INVITE to BYE) n n Dialogue Stateful Performs message retransmission 22
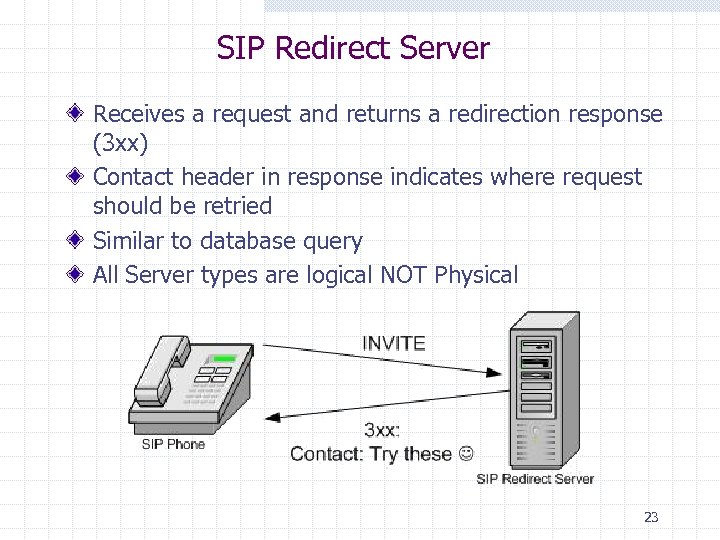
SIP Redirect Server Receives a request and returns a redirection response (3 xx) Contact header in response indicates where request should be retried Similar to database query All Server types are logical NOT Physical 23
Locating SIP Servers Manual provisioning DHCP SIP Option 120 n RFC 3361 Multicast (deprecated) DNS SRV method n n n Get local domain name automatically from DHCP server Perform SRV record query through DNS on that domain for _sip. _udp. <domain name> Send SIP REGISTER message to resolved server n phone is up and running without user intervention 24

SIP in detail Now, we are going to study SIP in detail including SIP Request, SIP Response and SIP Header

SIP Request Methods, 1 SIP used for Peer-to-Peer Communication though it uses a Client-Server model Requests are called “methods” Six methods are defined in base RFC 3261: w w w INVITE ACK OPTIONS BYE CANCEL REGISTER 26

SIP Request Methods, 2 REGISTER n Register contact with Registrar INVITE/ACK/BYE/CANCEL/UPDATE n Creates, negotiates and tears down a call (dialogue) MESSAGE n Creates an Instant Messaging session SUBSCRIBE n Subscribe to a service (like message waiting indication) NOTIFY n Notify a change in service state (new Voicemail) 27

SIP Methods - INVITE, 1 INVITE requests the establishment of a session Carried in Message Body (SDP) n n Type of session IP Address Port Codec 28

SIP Methods - INVITE, 2 An INVITE during an existing session (dialogue) is called a re-INVITEs can be used to n n Place calls on or remove calls from hold Change session parameters and codecs The SIP UPDATE method is the proposed replacement for this technique 29
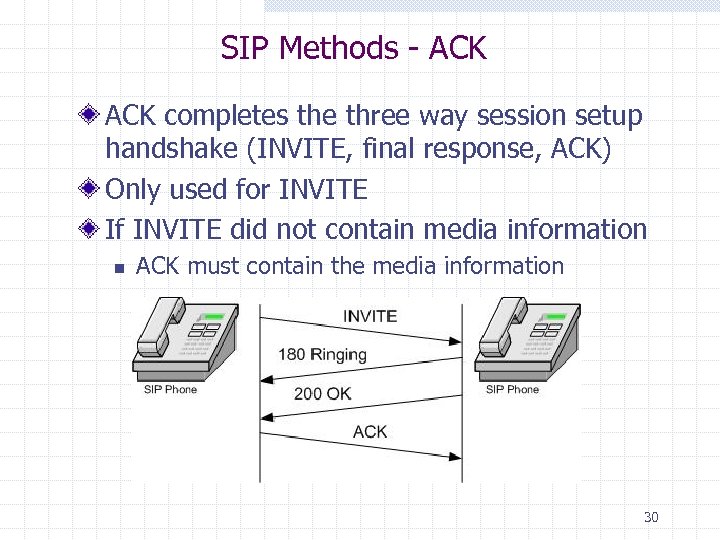
SIP Methods - ACK completes the three way session setup handshake (INVITE, final response, ACK) Only used for INVITE If INVITE did not contain media information n ACK must contain the media information 30

SIP Methods - OPTIONS requests the capabilities of another User Agent Response lists supported methods, extensions, codecs, etc. User Agent responds to OPTIONS the same as if an INVITE (e. g. if Busy, returns 486 Busy Here) Very basic presence information 31

SIP Methods – BYE and CANCEL BYE terminates an established session n User Agents stop sending media packets (RTP) CANCEL terminates a pending session. n n INVITE sent but no final response (non-1 xx) yet received. User Agents and Proxies stop processing INVITE Can be sent by a proxy or User Agent Useful for “forking proxy” w Parallel search using multiple registration Contacts. w First successful wins, rest are cancelled. 32

SIP Methods - REGISTER Registration allows a User Agent to upload current location and URLs to a Registrar can upload into Location Service Incoming requests can then be proxied or redirected to that location Built in SIP support of mobility UAs do not need static IP addresses n Obtain IP address via DHCP, REGISTER indicating new IP Address as contact 33
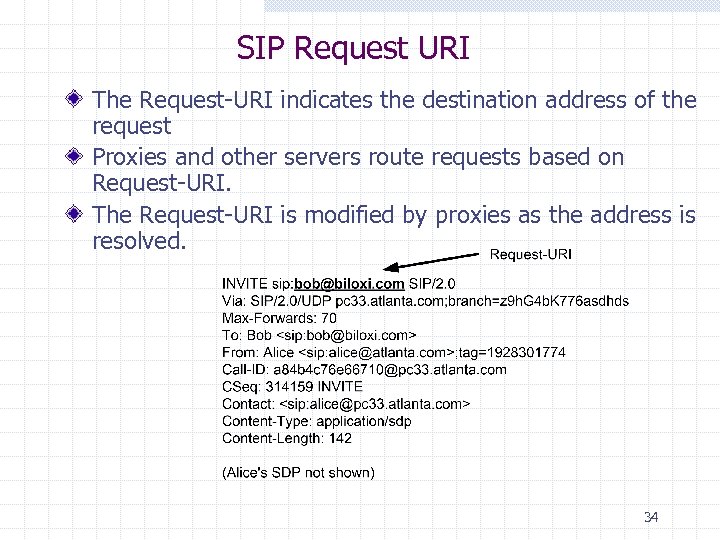
SIP Request URI The Request-URI indicates the destination address of the request Proxies and other servers route requests based on Request-URI. The Request-URI is modified by proxies as the address is resolved. 34

SIP From and To Tags are pseudo-random numbers inserted in To or From headers to uniquely identify a call leg INVITE request From header contains a tag Any User Agent or Server generating a response adds a tag to the To header in the response n To: sip: john@company. com; tag=123456 35

SIP Method - INFO Used to transport mid-call signaling information Only one pending INFO at a time Typical use - PSTN signaling message carried as MIME attachment n E. g. ISDN User-to-User information Defined in RFC 2976 36

SIP Method - REFER Indicates that recipient (identified by the Request-URI) should contact a third party using the contact information provided in the request Typical Use: Call Transfer features Allowed outside an established dialogue 37

SIP Method - PRACK Provisional Response ACKnowlegement Used to acknowledge receipt of provisional response n n n 183 Session Progress Does not apply to 100 Trying responses Only provisional responses 101 -199 may be sent reliably and acknowledged with PRACK If no PRACK sent, response retransmitted Defined in RFC 3262 38
SIP Methods – SUBSCRIBE and NOTIFY SUBSCRIBE requests notification of when a particular event occurs n Use Expires=0 to unsubscribe A NOTIFY message is sent to indicate the event status Sample Applications n n Presence Message waiting indication for voicemail Defined in RFC 3265 39

SIP Method - MESSAGE Extension to SIP for Instant Messaging (IM) MESSAGE requests n n carry the content in the form of MIME body parts use the standard MIME headers to identify the content 40
SIP Responses SIP Requests generate Responses with codes borrowed from HTTP Classes: n n n 1 xx 2 xx 3 xx 4 xx 5 xx 6 xx Informational Final Redirection Client Error Server Error Global Failure Response example “ 404 Not Found” 41
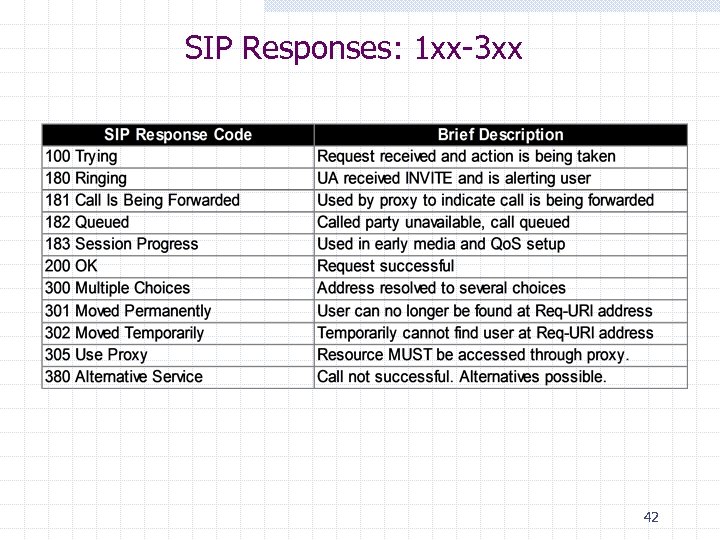
SIP Responses: 1 xx-3 xx 42
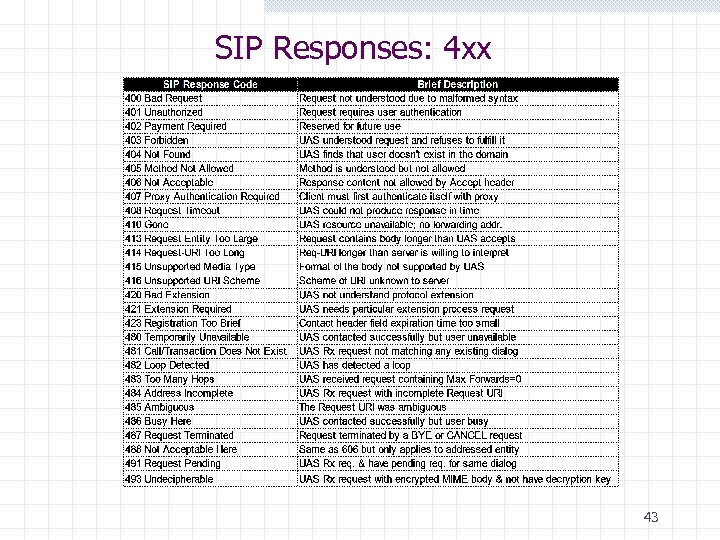
SIP Responses: 4 xx 43
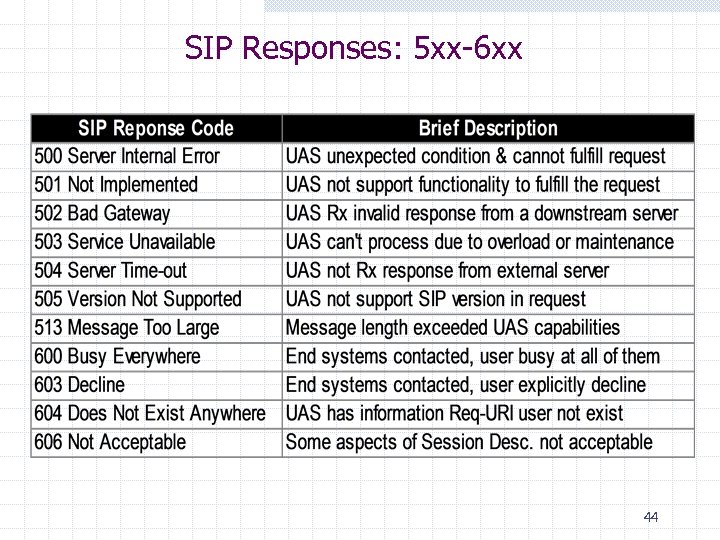
SIP Responses: 5 xx-6 xx 44
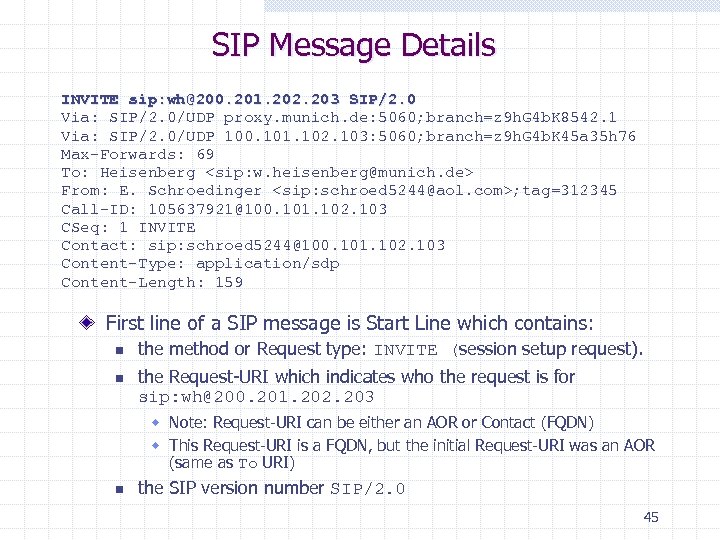
SIP Message Details INVITE sip: wh@200. 201. 202. 203 SIP/2. 0 Via: SIP/2. 0/UDP proxy. munich. de: 5060; branch=z 9 h. G 4 b. K 8542. 1 Via: SIP/2. 0/UDP 100. 101. 102. 103: 5060; branch=z 9 h. G 4 b. K 45 a 35 h 76 Max-Forwards: 69 To: Heisenberg <sip: w. heisenberg@munich. de> From: E. Schroedinger <sip: schroed 5244@aol. com>; tag=312345 Call-ID: 105637921@100. 101. 102. 103 CSeq: 1 INVITE Contact: sip: schroed 5244@100. 101. 102. 103 Content-Type: application/sdp Content-Length: 159 First line of a SIP message is Start Line which contains: n n the method or Request type: INVITE (session setup request). the Request-URI which indicates who the request is for sip: wh@200. 201. 202. 203 w Note: Request-URI can be either an AOR or Contact (FQDN) w This Request-URI is a FQDN, but the initial Request-URI was an AOR (same as To URI) n the SIP version number SIP/2. 0 45

SIP Headers SIP Requests and Responses contain Headers (similar to Email headers) n Required Headers w w w n To From Via Call-ID CSeq Max-Forwards Optional Headers: w Subject, Date, Authentication (and many others) 46
SIP Message Details INVITE sip: w. h@200. 201. 202. 203 SIP/2. 0 Via: SIP/2. 0/UDP proxy. munich. de: 5060; branch=z 9 h. G 4 b. K 8542. 1 Via: SIP/2. 0/UDP 100. 101. 102. 103: 5060; branch=z 9 h. G 4 b. K 45 a 35 h 76 Max-Forwards: 69 To: Heisenberg <sip: w. heisenberg@munich. de> From: E. Schroedinger <sip: schroed 5244@aol. com>; tag=312345 Call-ID: 105637921@100. 101. 102. 103 CSeq: 1 INVITE Contact: sip: schroed 5244@100. 101. 102. 103 Content-Type: application/sdp Content-Length: 159 Via headers show the path the request has taken n n The bottom Via header is inserted by the User Agent which initiated the request Additional Via headers are inserted by each proxy in the path The Via headers are used to route responses back the same way Required branch parameter contains a “cookie” (z 9 h. G 4 b. K) then a transaction-ID. 47
SIP Message Details INVITE sip: w. h@200. 201. 202. 203 SIP/2. 0 Via: SIP/2. 0/UDP proxy. munich. de: 5060; branch=z 9 h. G 4 b. K 8542. 1 Via: SIP/2. 0/UDP 100. 101. 102. 103: 5060; branch=z 9 h. G 4 b. K 45 a 35 h 76 Max-Forwards: 69 To: Heisenberg <sip: w. heisenberg@munich. de> From: E. Schroedinger <sip: schroed 5244@aol. com>; tag=312345 Call-ID: 105637921@100. 101. 102. 103 CSeq: 1 INVITE Contact: sip: schroed 5244@100. 101. 102. 103 Content-Type: application/sdp Content-Length: 159 Max-Forwards is a count decremented by each proxy that forwards the request. When count goes to zero, request is discarded and 483 Too Many Hops response is sent. Used for stateless loop detection. 48
SIP Message Details INVITE sip: w. h@200. 201. 202. 203 SIP/2. 0 Via: SIP/2. 0/UDP proxy. munich. de: 5060; branch=z 9 h. G 4 b. K 8542. 1 Via: SIP/2. 0/UDP 100. 101. 102. 103: 5060; branch=z 9 h. G 4 b. K 45 a 35 h 76 Max-Forwards: 69 To: Heisenberg <sip: w. heisenberg@munich. de> From: E. Schroedinger <sip: schroed 5244@aol. com>; tag=312345 Call-ID: 105637921@100. 101. 102. 103 CSeq: 1 INVITE Contact: sip: schroed 5244@100. 101. 102. 103 Content-Type: application/sdp Content-Length: 159 Dialog (formerly called call leg) information is in headers: n To tag, From tag, and Call-ID (Note: Not URIs) To and From URIs usually contain AOR URIs. All requests and responses in this call will use this same Dialog information. Call-ID is unique identifier usually composed of n pseudo-random string “@” hostname or IP Address 49
SIP Message Details INVITE sip: w. h@200. 201. 202. 203 SIP/2. 0 Via: SIP/2. 0/UDP proxy. munich. de: 5060; branch=z 9 h. G 4 b. K 8542. 1 Via: SIP/2. 0/UDP 100. 101. 102. 103: 5060; branch=z 9 h. G 4 b. K 45 a 35 h 76 Max-Forwards: 69 To: Heisenberg <sip: w. heisenberg@munich. de> From: E. Schroedinger <sip: schroed 5244@aol. com>; tag=312345 Call-ID: 105637921@100. 101. 102. 103 CSeq: 1 INVITE Contact: sip: schroed 5244@100. 101. 102. 103 Content-Type: application/sdp Content-Length: 159 CSeq Command Sequence Number n n n Initialized at start of call (1 in this example) Incremented for each subsequent request Used to distinguish a retransmission from a new request Also contains the request type (method) - INVITE 50
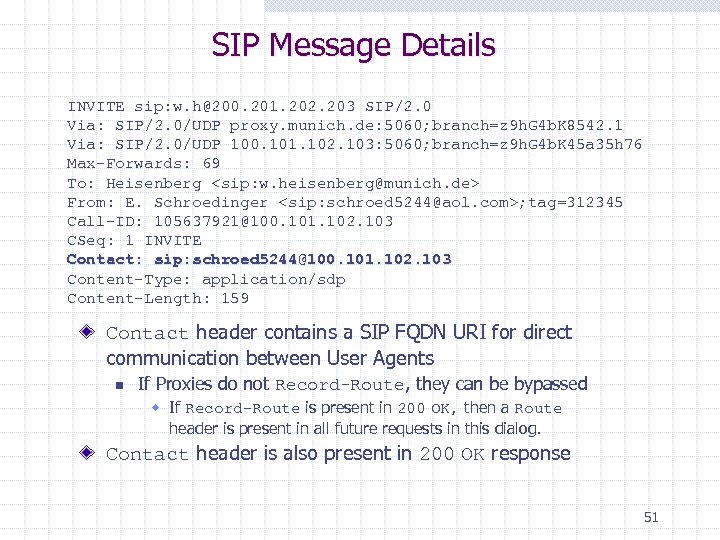
SIP Message Details INVITE sip: w. h@200. 201. 202. 203 SIP/2. 0 Via: SIP/2. 0/UDP proxy. munich. de: 5060; branch=z 9 h. G 4 b. K 8542. 1 Via: SIP/2. 0/UDP 100. 101. 102. 103: 5060; branch=z 9 h. G 4 b. K 45 a 35 h 76 Max-Forwards: 69 To: Heisenberg <sip: w. heisenberg@munich. de> From: E. Schroedinger <sip: schroed 5244@aol. com>; tag=312345 Call-ID: 105637921@100. 101. 102. 103 CSeq: 1 INVITE Contact: sip: schroed 5244@100. 101. 102. 103 Content-Type: application/sdp Content-Length: 159 Contact header contains a SIP FQDN URI for direct communication between User Agents n If Proxies do not Record-Route, they can be bypassed w If Record-Route is present in 200 OK, then a Route header is present in all future requests in this dialog. Contact header is also present in 200 OK response 51
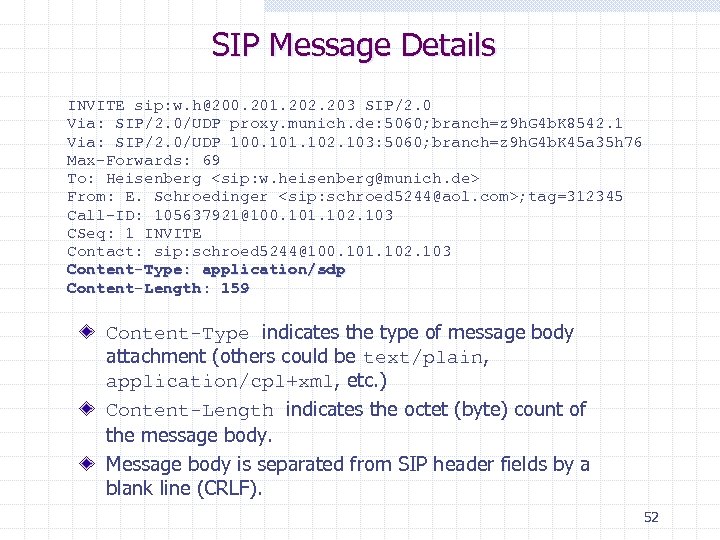
SIP Message Details INVITE sip: w. h@200. 201. 202. 203 SIP/2. 0 Via: SIP/2. 0/UDP proxy. munich. de: 5060; branch=z 9 h. G 4 b. K 8542. 1 Via: SIP/2. 0/UDP 100. 101. 102. 103: 5060; branch=z 9 h. G 4 b. K 45 a 35 h 76 Max-Forwards: 69 To: Heisenberg <sip: w. heisenberg@munich. de> From: E. Schroedinger <sip: schroed 5244@aol. com>; tag=312345 Call-ID: 105637921@100. 101. 102. 103 CSeq: 1 INVITE Contact: sip: schroed 5244@100. 101. 102. 103 Content-Type: application/sdp Content-Length: 159 Content-Type indicates the type of message body attachment (others could be text/plain, application/cpl+xml, etc. ) Content-Length indicates the octet (byte) count of the message body. Message body is separated from SIP header fields by a blank line (CRLF). 52
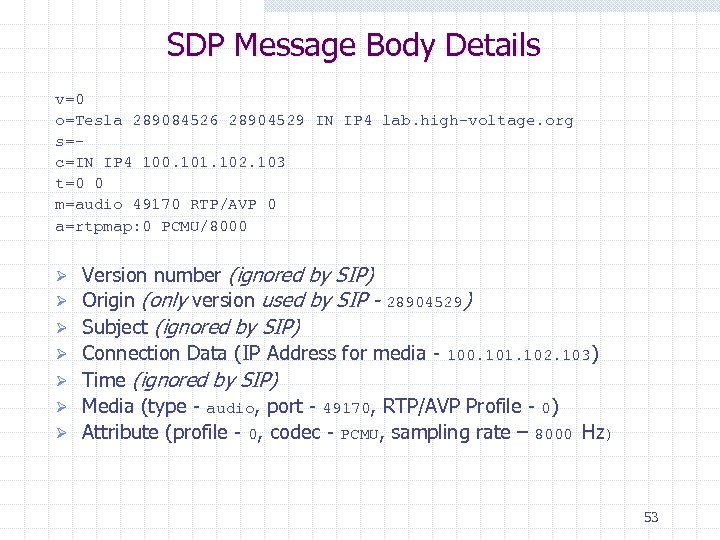
SDP Message Body Details v=0 o=Tesla 289084526 28904529 IN IP 4 lab. high-voltage. org s=c=IN IP 4 100. 101. 102. 103 t=0 0 m=audio 49170 RTP/AVP 0 a=rtpmap: 0 PCMU/8000 Ø Ø Ø Ø Version number (ignored by SIP) Origin (only version used by SIP - 28904529) Subject (ignored by SIP) Connection Data (IP Address for media - 100. 101. 102. 103) Time (ignored by SIP) Media (type - audio, port - 49170, RTP/AVP Profile - 0) Attribute (profile - 0, codec - PCMU, sampling rate – 8000 Hz) 53
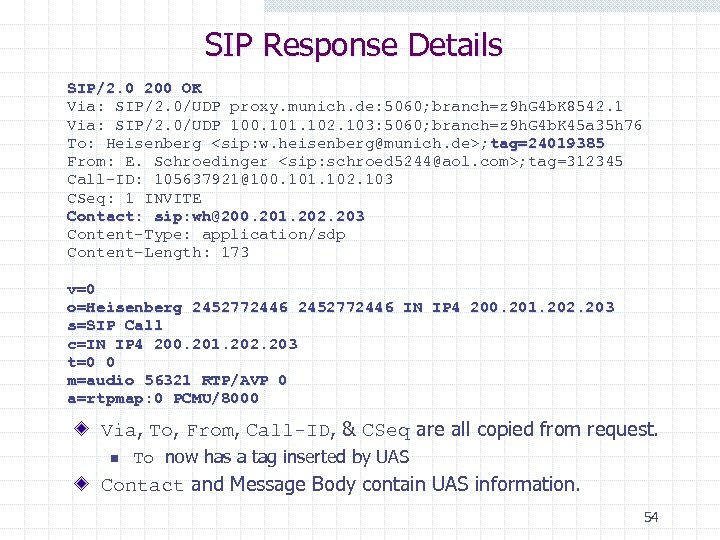
SIP Response Details SIP/2. 0 200 OK Via: SIP/2. 0/UDP proxy. munich. de: 5060; branch=z 9 h. G 4 b. K 8542. 1 Via: SIP/2. 0/UDP 100. 101. 102. 103: 5060; branch=z 9 h. G 4 b. K 45 a 35 h 76 To: Heisenberg <sip: w. heisenberg@munich. de>; tag=24019385 From: E. Schroedinger <sip: schroed 5244@aol. com>; tag=312345 Call-ID: 105637921@100. 101. 102. 103 CSeq: 1 INVITE Contact: sip: wh@200. 201. 202. 203 Content-Type: application/sdp Content-Length: 173 v=0 o=Heisenberg 2452772446 IN IP 4 200. 201. 202. 203 s=SIP Call c=IN IP 4 200. 201. 202. 203 t=0 0 m=audio 56321 RTP/AVP 0 a=rtpmap: 0 PCMU/8000 Via, To, From, Call-ID, & CSeq are all copied from request. n To now has a tag inserted by UAS Contact and Message Body contain UAS information. 54

SIP Call Flow Scenarios As followings …

SIP Call Flow Scenarios Ø Ø Ø Ø Call Attempt - Unsuccessful Presence Subscription Registration Presence Notification Instant Message Exchange Call Setup – Successful Call Hold Call Transfer Call Flows and full message details: “SIP Basic Call Flow Examples” I-D by A. Johnston et al. Ø “SIP Service Examples” I-D by A. Johnston et al. Ø 56
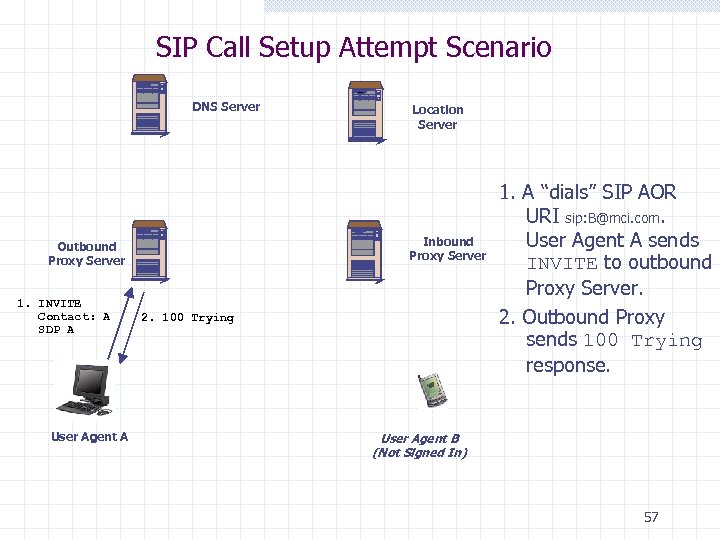
SIP Call Setup Attempt Scenario DNS Server Inbound Proxy Server Outbound Proxy Server 1. INVITE Contact: A SDP A User Agent A Location Server 2. 100 Trying 1. A “dials” SIP AOR URI sip: B@mci. com. User Agent A sends INVITE to outbound Proxy Server. 2. Outbound Proxy sends 100 Trying response. User Agent B (Not Signed In) 57
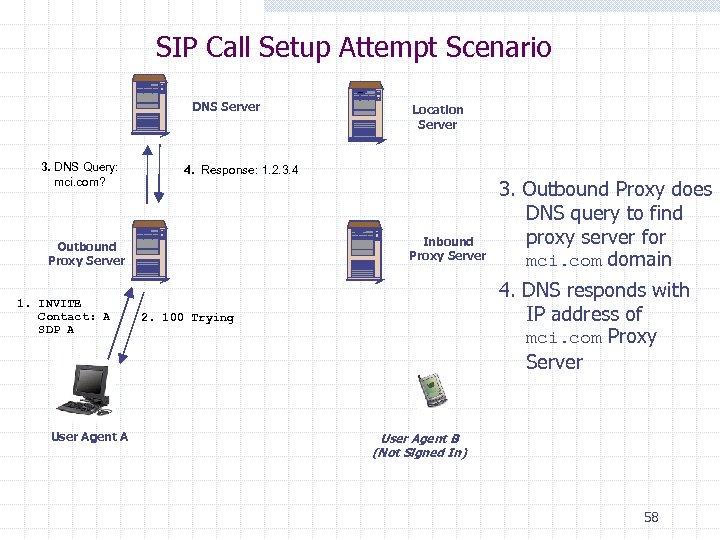
SIP Call Setup Attempt Scenario DNS Server 3. DNS Query: mci. com? 4. Response: 1. 2. 3. 4 Inbound Proxy Server Outbound Proxy Server 1. INVITE Contact: A SDP A User Agent A Location Server 3. Outbound Proxy does DNS query to find proxy server for mci. com domain 4. DNS responds with IP address of mci. com Proxy Server 2. 100 Trying User Agent B (Not Signed In) 58
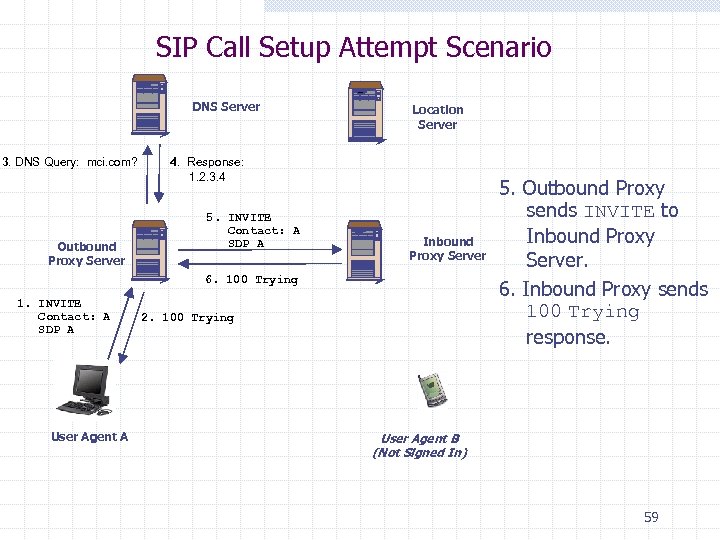
SIP Call Setup Attempt Scenario DNS Server 3. DNS Query: mci. com? Outbound Proxy Server Location Server 4. Response: 1. 2. 3. 4 5. INVITE Contact: A SDP A Inbound Proxy Server 6. 100 Trying 1. INVITE Contact: A SDP A User Agent A 2. 100 Trying 5. Outbound Proxy sends INVITE to Inbound Proxy Server. 6. Inbound Proxy sends 100 Trying response. User Agent B (Not Signed In) 59
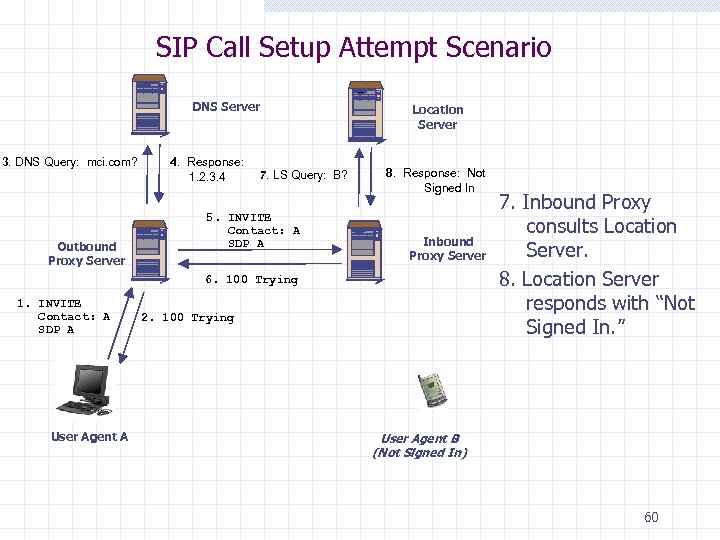
SIP Call Setup Attempt Scenario DNS Server 3. DNS Query: mci. com? Outbound Proxy Server 4. Response: 1. 2. 3. 4 7. LS Query: B? 5. INVITE Contact: A SDP A Location Server 8. Response: Not Signed In Inbound Proxy Server 6. 100 Trying 1. INVITE Contact: A SDP A User Agent A 2. 100 Trying 7. Inbound Proxy consults Location Server. 8. Location Server responds with “Not Signed In. ” User Agent B (Not Signed In) 60
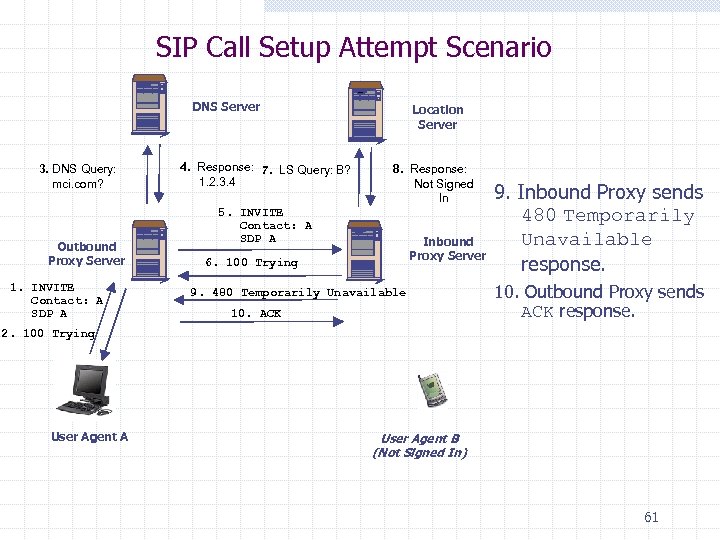
SIP Call Setup Attempt Scenario DNS Server 3. DNS Query: mci. com? Outbound Proxy Server 1. INVITE Contact: A SDP A 4. Response: 7. LS Query: B? 1. 2. 3. 4 Location Server 8. Response: Not Signed In 5. INVITE Contact: A SDP A Inbound Proxy Server 6. 100 Trying 9. 480 Temporarily Unavailable 10. ACK 9. Inbound Proxy sends 480 Temporarily Unavailable response. 10. Outbound Proxy sends ACK response. 2. 100 Trying User Agent A User Agent B (Not Signed In) 61
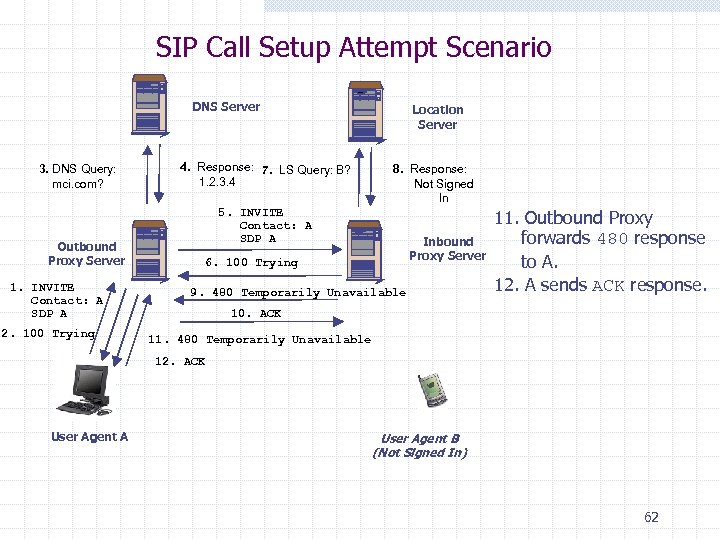
SIP Call Setup Attempt Scenario DNS Server 3. DNS Query: mci. com? Outbound Proxy Server 1. INVITE Contact: A SDP A 2. 100 Trying Location Server 4. Response: 7. LS Query: B? 1. 2. 3. 4 8. Response: Not Signed In 5. INVITE Contact: A SDP A Inbound Proxy Server 6. 100 Trying 9. 480 Temporarily Unavailable 11. Outbound Proxy forwards 480 response to A. 12. A sends ACK response. 10. ACK 11. 480 Temporarily Unavailable 12. ACK User Agent A User Agent B (Not Signed In) 62
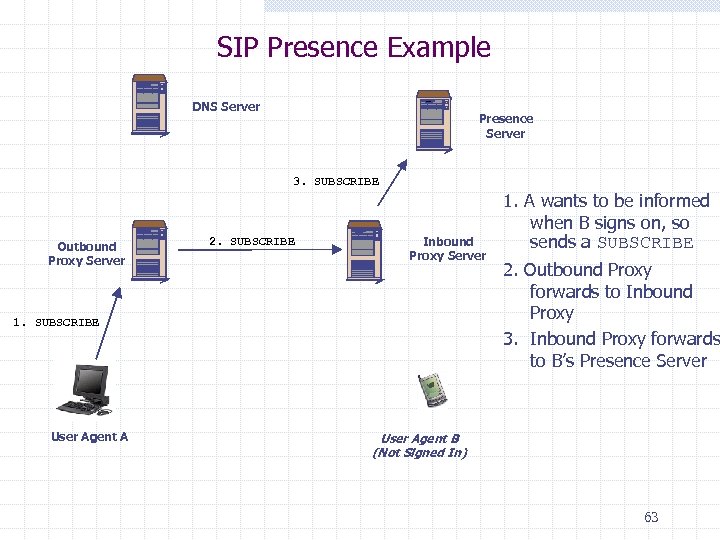
SIP Presence Example DNS Server Presence Server 3. SUBSCRIBE Outbound Proxy Server 2. SUBSCRIBE Inbound Proxy Server 1. SUBSCRIBE User Agent A 1. A wants to be informed when B signs on, so sends a SUBSCRIBE 2. Outbound Proxy forwards to Inbound Proxy 3. Inbound Proxy forwards to B’s Presence Server User Agent B (Not Signed In) 63
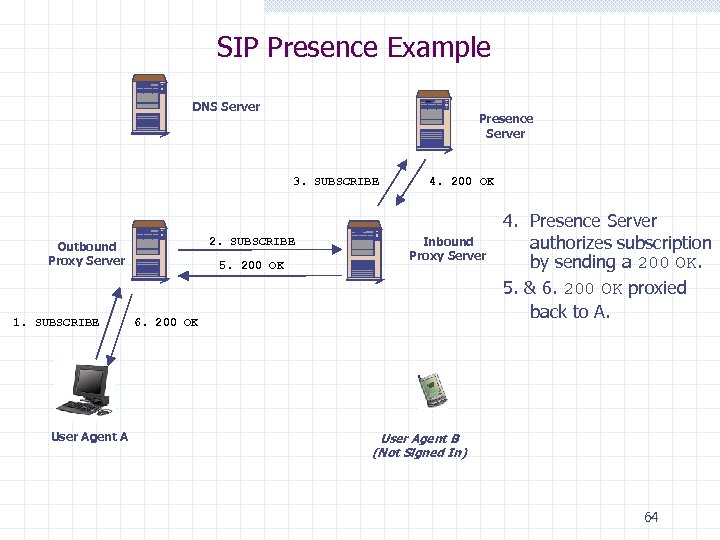
SIP Presence Example DNS Server Presence Server 3. SUBSCRIBE 2. SUBSCRIBE Outbound Proxy Server 1. SUBSCRIBE User Agent A 5. 200 OK 4. 200 OK Inbound Proxy Server 6. 200 OK 4. Presence Server authorizes subscription by sending a 200 OK. 5. & 6. 200 OK proxied back to A. User Agent B (Not Signed In) 64
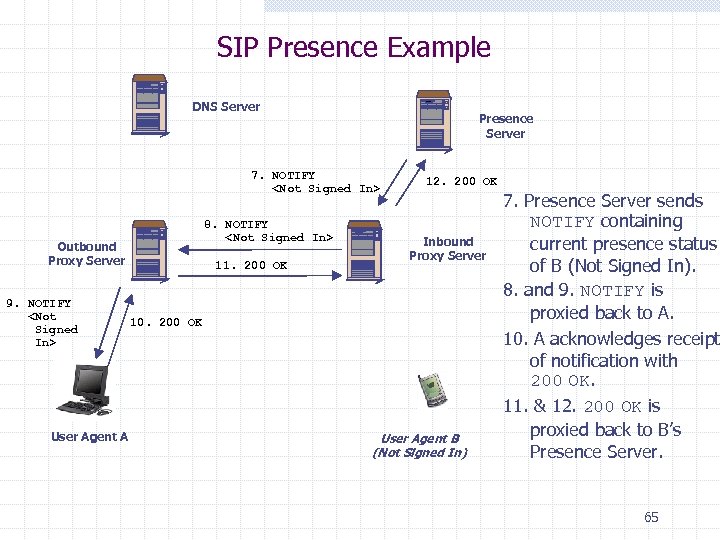
SIP Presence Example DNS Server Presence Server 7. NOTIFY <Not Signed In> Outbound Proxy Server 9. NOTIFY <Not Signed In> User Agent A 8. NOTIFY <Not Signed In> 11. 200 OK 12. 200 OK Inbound Proxy Server 10. 200 OK User Agent B (Not Signed In) 7. Presence Server sends NOTIFY containing current presence status of B (Not Signed In). 8. and 9. NOTIFY is proxied back to A. 10. A acknowledges receipt of notification with 200 OK. 11. & 12. 200 OK is proxied back to B’s Presence Server. 65
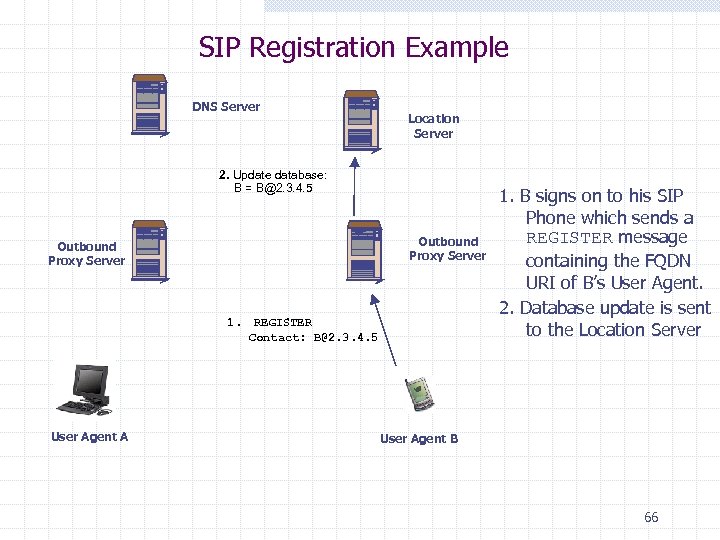
SIP Registration Example DNS Server Location Server 2. Update database: B = B@2. 3. 4. 5 Outbound Proxy Server 1. REGISTER Contact: B@2. 3. 4. 5 User Agent A 1. B signs on to his SIP Phone which sends a REGISTER message containing the FQDN URI of B’s User Agent. 2. Database update is sent to the Location Server User Agent B 66
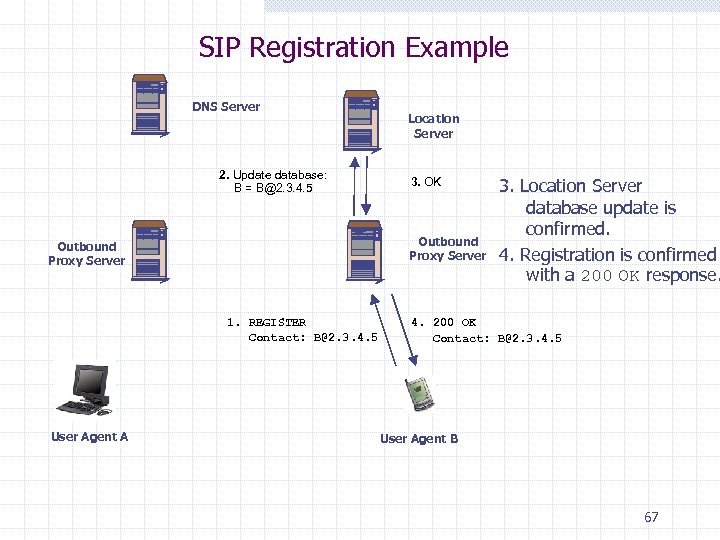
SIP Registration Example DNS Server 2. Update database: B = B@2. 3. 4. 5 3. OK Outbound Proxy Server 1. REGISTER Contact: B@2. 3. 4. 5 User Agent A Location Server 3. Location Server database update is confirmed. 4. Registration is confirmed with a 200 OK response. 4. 200 OK Contact: B@2. 3. 4. 5 User Agent B 67
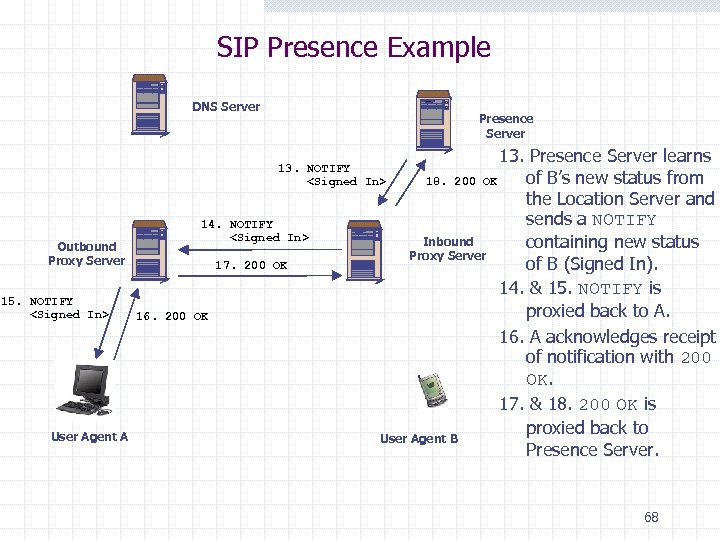
SIP Presence Example DNS Server Presence Server 13. Presence Server learns of B’s new status from 18. 200 OK the Location Server and sends a NOTIFY Inbound containing new status Proxy Server of B (Signed In). 14. & 15. NOTIFY is proxied back to A. 16. A acknowledges receipt of notification with 200 OK. 17. & 18. 200 OK is proxied back to User Agent B Presence Server. 13. NOTIFY <Signed In> Outbound Proxy Server 15. NOTIFY <Signed In> User Agent A 14. NOTIFY <Signed In> 17. 200 OK 16. 200 OK 68
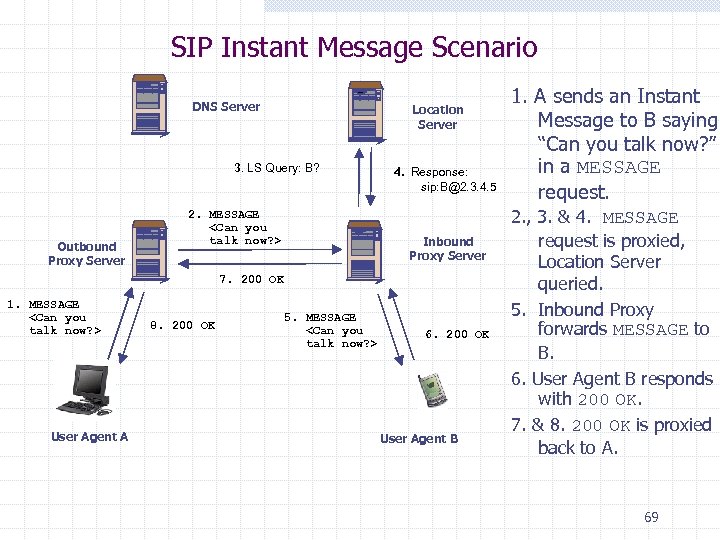
SIP Instant Message Scenario DNS Server Location Server 3. LS Query: B? Outbound Proxy Server 4. Response: sip: B@2. 3. 4. 5 2. MESSAGE <Can you talk now? > Inbound Proxy Server 7. 200 OK 1. MESSAGE <Can you talk now? > User Agent A 8. 200 OK 5. MESSAGE <Can you talk now? > 6. 200 OK User Agent B 1. A sends an Instant Message to B saying “Can you talk now? ” in a MESSAGE request. 2. , 3. & 4. MESSAGE request is proxied, Location Server queried. 5. Inbound Proxy forwards MESSAGE to B. 6. User Agent B responds with 200 OK. 7. & 8. 200 OK is proxied back to A. 69
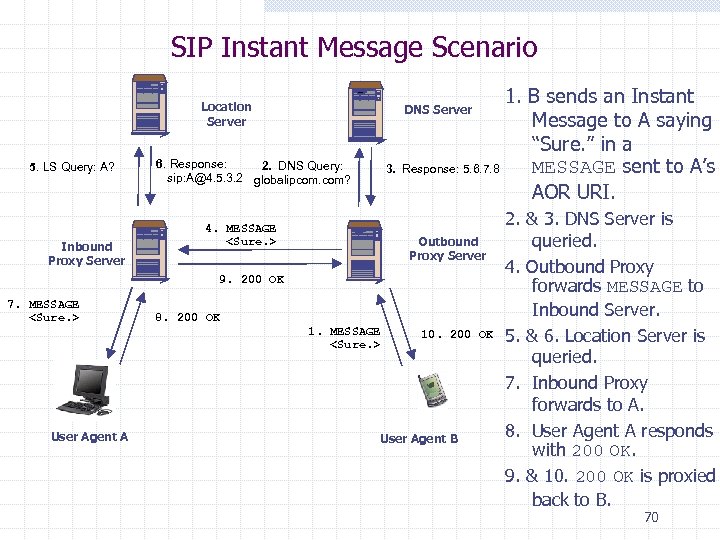
SIP Instant Message Scenario Location Server 5. LS Query: A? Inbound Proxy Server 1. B sends an Instant Message to A saying “Sure. ” in a MESSAGE sent to A’s Response: 5. 6. 7. 8 AOR URI. DNS Server 6. Response: 2. DNS Query: sip: A@4. 5. 3. 2 globalipcom. com? 3. 4. MESSAGE <Sure. > Outbound Proxy Server 9. 200 OK 7. MESSAGE <Sure. > User Agent A 8. 200 OK 1. MESSAGE <Sure. > 10. 200 OK User Agent B 2. & 3. DNS Server is queried. 4. Outbound Proxy forwards MESSAGE to Inbound Server. 5. & 6. Location Server is queried. 7. Inbound Proxy forwards to A. 8. User Agent A responds with 200 OK. 9. & 10. 200 OK is proxied back to B. 70
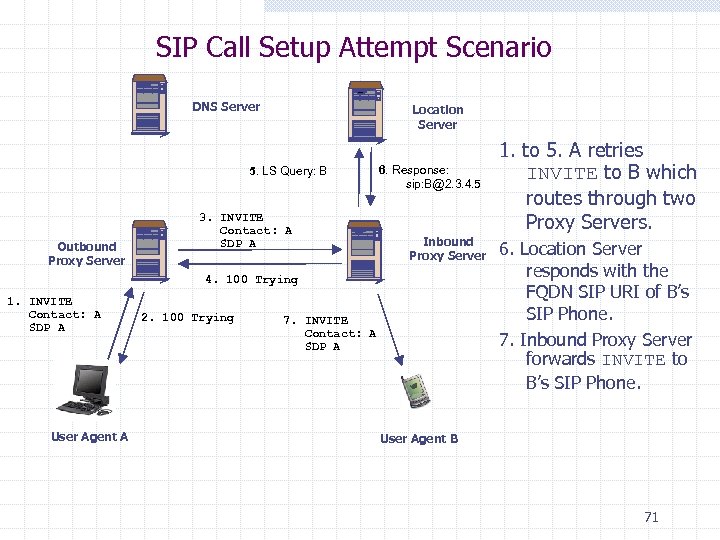
SIP Call Setup Attempt Scenario DNS Server Location Server 5. LS Query: B Outbound Proxy Server 3. INVITE Contact: A SDP A 6. Response: sip: B@2. 3. 4. 5 Inbound Proxy Server 4. 100 Trying 1. INVITE Contact: A SDP A User Agent A 2. 100 Trying 7. INVITE Contact: A SDP A 1. to 5. A retries INVITE to B which routes through two Proxy Servers. 6. Location Server responds with the FQDN SIP URI of B’s SIP Phone. 7. Inbound Proxy Server forwards INVITE to B’s SIP Phone. User Agent B 71
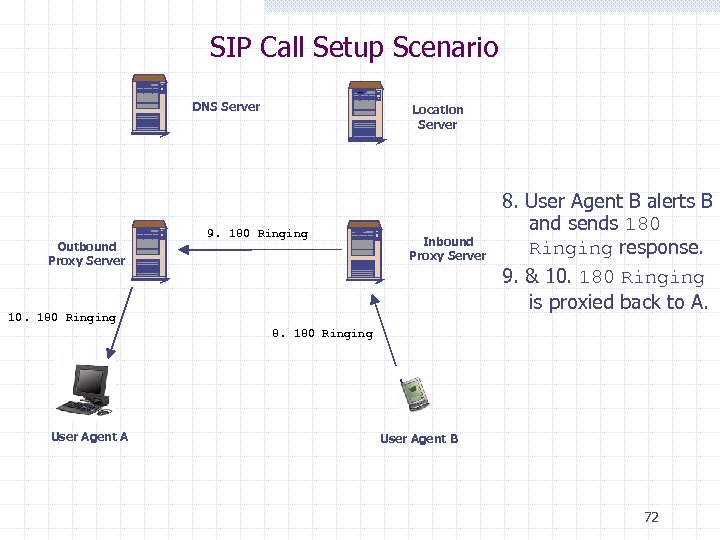
SIP Call Setup Scenario DNS Server Outbound Proxy Server Location Server 9. 180 Ringing Inbound Proxy Server 10. 180 Ringing 8. User Agent B alerts B and sends 180 Ringing response. 9. & 10. 180 Ringing is proxied back to A. 8. 180 Ringing User Agent A User Agent B 72
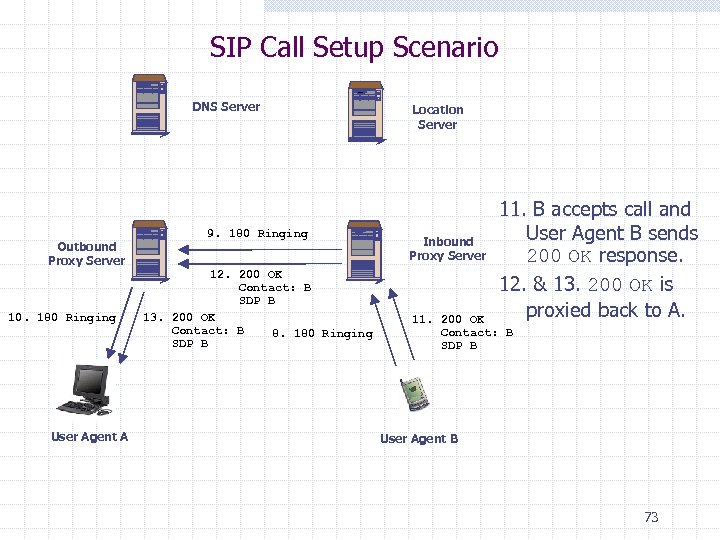
SIP Call Setup Scenario DNS Server Outbound Proxy Server 10. 180 Ringing User Agent A 9. 180 Ringing 12. 200 OK Contact: B SDP B 13. 200 OK Contact: B 8. 180 Ringing SDP B Location Server Inbound Proxy Server 11. B accepts call and User Agent B sends 200 OK response. 12. & 13. 200 OK is proxied back to A. 11. 200 OK Contact: B SDP B User Agent B 73
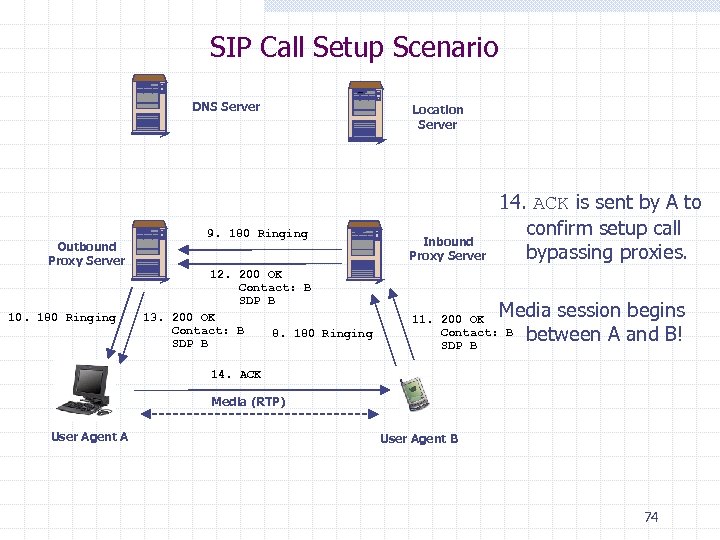
SIP Call Setup Scenario DNS Server Outbound Proxy Server 10. 180 Ringing 9. 180 Ringing 12. 200 OK Contact: B SDP B 13. 200 OK Contact: B 8. 180 Ringing SDP B Location Server Inbound Proxy Server 14. ACK is sent by A to confirm setup call bypassing proxies. Media session begins between A and B! 11. 200 OK Contact: B SDP B 14. ACK Media (RTP) User Agent A User Agent B 74
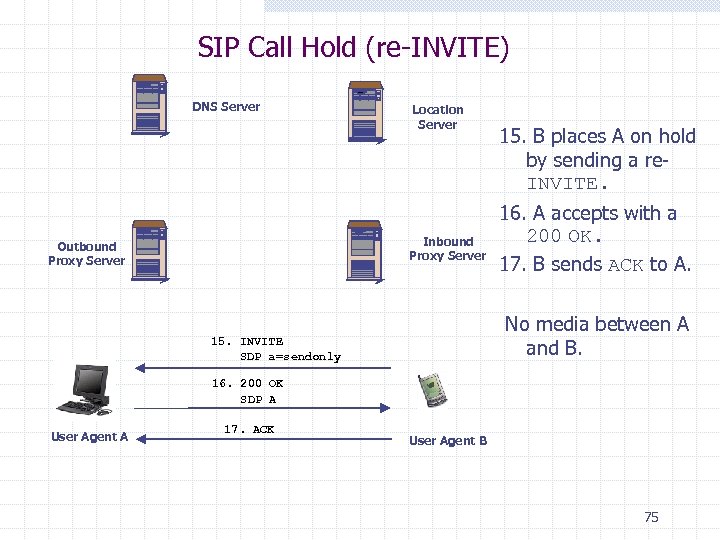
SIP Call Hold (re-INVITE) DNS Server Location Server Inbound Proxy Server Outbound Proxy Server 15. B places A on hold by sending a re. INVITE. 16. A accepts with a 200 OK. 17. B sends ACK to A. No media between A and B. 15. INVITE SDP a=sendonly 16. 200 OK SDP A User Agent A 17. ACK User Agent B 75
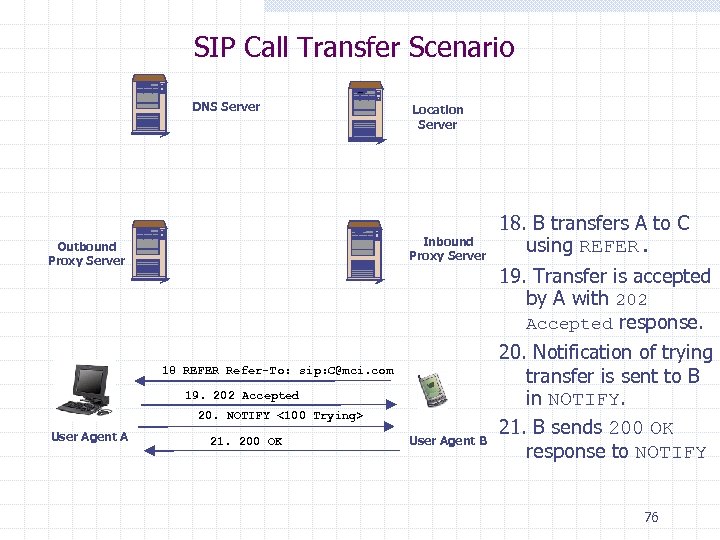
SIP Call Transfer Scenario DNS Server Location Server Inbound Proxy Server Outbound Proxy Server 19. Transfer is accepted by A with 202 Accepted response. 18 REFER Refer-To: sip: C@mci. com 19. 202 Accepted 20. NOTIFY <100 Trying> User Agent A 18. B transfers A to C using REFER. 21. 200 OK User Agent B 20. Notification of trying transfer is sent to B in NOTIFY. 21. B sends 200 OK response to NOTIFY 76
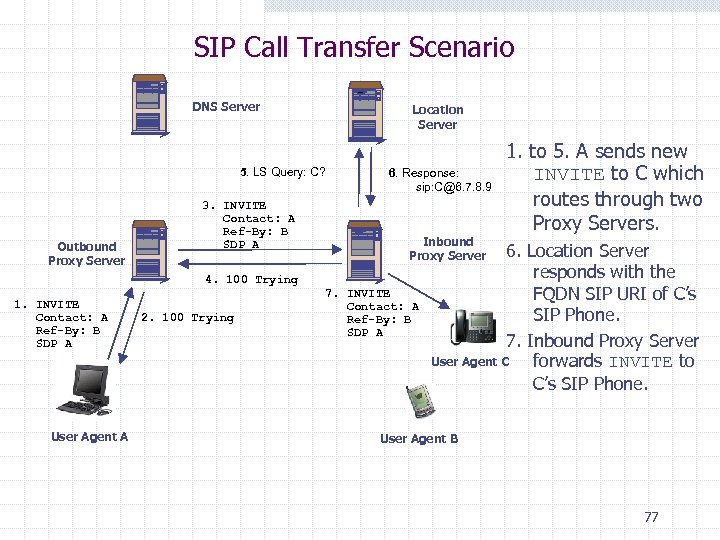
SIP Call Transfer Scenario DNS Server Location Server 5. LS Query: C? Outbound Proxy Server 3. INVITE Contact: A Ref-By: B SDP A 6. Response: sip: C@6. 7. 8. 9 Inbound Proxy Server 4. 100 Trying 1. INVITE Contact: A Ref-By: B SDP A User Agent A 2. 100 Trying 7. INVITE Contact: A Ref-By: B SDP A 1. to 5. A sends new INVITE to C which routes through two Proxy Servers. 6. Location Server responds with the FQDN SIP URI of C’s SIP Phone. 7. Inbound Proxy Server User Agent C forwards INVITE to C’s SIP Phone. User Agent B 77
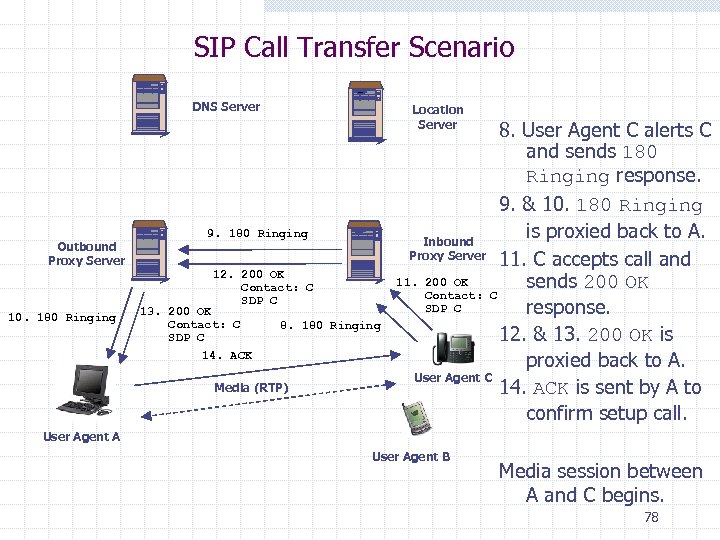
SIP Call Transfer Scenario DNS Server Outbound Proxy Server Location Server 9. 180 Ringing 12. 200 OK Contact: C SDP C 10. 180 Ringing 13. 200 OK Contact: C SDP C 14. ACK 8. 180 Ringing Media (RTP) 8. User Agent C alerts C and sends 180 Ringing response. 9. & 10. 180 Ringing is proxied back to A. Inbound Proxy Server 11. C accepts call and 11. 200 OK sends 200 OK Contact: C SDP C response. 12. & 13. 200 OK is proxied back to A. User Agent C 14. ACK is sent by A to confirm setup call. User Agent A User Agent B Media session between A and C begins. 78
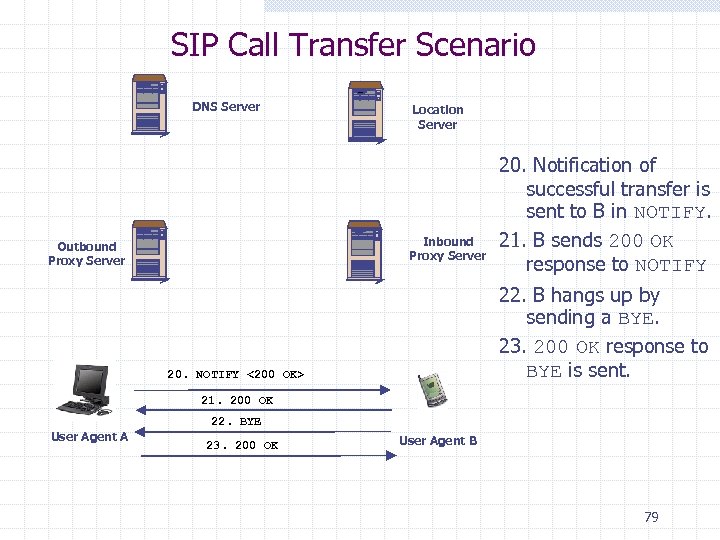
SIP Call Transfer Scenario DNS Server Location Server Inbound Proxy Server Outbound Proxy Server 20. Notification of successful transfer is sent to B in NOTIFY. 21. B sends 200 OK response to NOTIFY 22. B hangs up by sending a BYE. 23. 200 OK response to BYE is sent. 20. NOTIFY <200 OK> 21. 200 OK 22. BYE User Agent A 23. 200 OK User Agent B 79

SIP Security
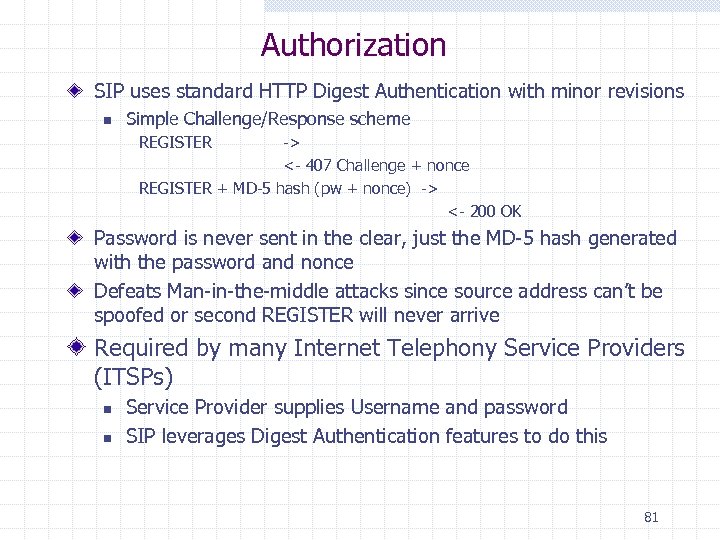
Authorization SIP uses standard HTTP Digest Authentication with minor revisions n Simple Challenge/Response scheme REGISTER -> <- 407 Challenge + nonce REGISTER + MD-5 hash (pw + nonce) -> <- 200 OK Password is never sent in the clear, just the MD-5 hash generated with the password and nonce Defeats Man-in-the-middle attacks since source address can’t be spoofed or second REGISTER will never arrive Required by many Internet Telephony Service Providers (ITSPs) n n Service Provider supplies Username and password SIP leverages Digest Authentication features to do this 81
TLS and sips: Implementation of TLS is mandatory for proxies, redirect servers and registrars The ; transport=tls URI parameter value is deprecated A sips: URI scheme (otherwise identical to the sip: scheme) indicates that all hops between the requestor and the resource identified by the URI must be encrypted with TLS. If the request is retargeted once the resource is reached, it must use secured transports. 82
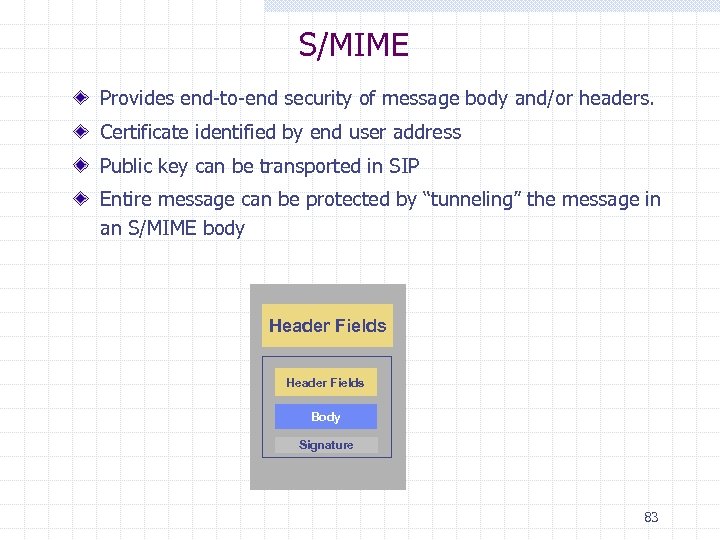
S/MIME Provides end-to-end security of message body and/or headers. Certificate identified by end user address Public key can be transported in SIP Entire message can be protected by “tunneling” the message in an S/MIME body Header Fields Body Signature 83

Attacks IPhreakers n n n IP knowledge Known weaknesses Evolution 2600 Hz -> voicemail/int’l GWs -> IP telephony Internal or external threat ? Targets: home user, enterprise, government, etc ? Protocol implementations n PROTOS The human element 84

Attacks : denial of service Denial of service n n Network Protocol (SIP INVITE) Systems / Applications Phone Availability (BC/DR) n n n Requires: power Alternatives (Business Continuity/Disaster Recovery) ? E 911 (laws and technical aspect) GSM PSTN-to-GSM 85
Attacks : fraud Call-ID spoofing User rights takeover n Fake authentication server Effects n n Access to voicemail Value added numbers Social engineering Replay 86

Attacks: interception Interception n “Who talks with who” (Network sniffing, Servers (SIP, CDR, etc) LAN n n Physical access to the LAN ARP attacks Unauthenticated devices (phones and servers) Different layers (MAC address, user, physical port, etc) Where to intercept ? n n Where is the user located ? Networks crossed ? Lawful Intercept n n n CALEA ETSI standard Architecture and risks 87

Attacks : systems Systems n n Mostly none is hardened by default Worms, exploits, Trojan horses Attacks : phone (S)IP phone n Startup w DHCP, TFTP, etc. n Physical access w Hidden configuration tabs n n n TCP/IP stacks Firmware/configuration Trojan horse/rootkit 88

Defense Signaling: SIP n Secure SIP vs SS 7 (physical security) Transport: Secure RTP (with Mi. KEY) Network: Qo. S [LLQ] (and rate-limit) Firewall: application level filtering Phone: signed firmware Identification: TLS n Clients by the server n Servers by the client 3 P: project, security processes and policies 89

SIP Programming
SIP based Application Interfaces These include : n JAIN SIP w Low level and very complex API w CNRSIP API is one of available reference implementations. n SIP Servlets w proposed within JAIN n SIP API for J 2 ME w intermediate level API (minimal SIP knowledge required) n n SIP CGI CPL ( Call Processing Language) w XML based 91
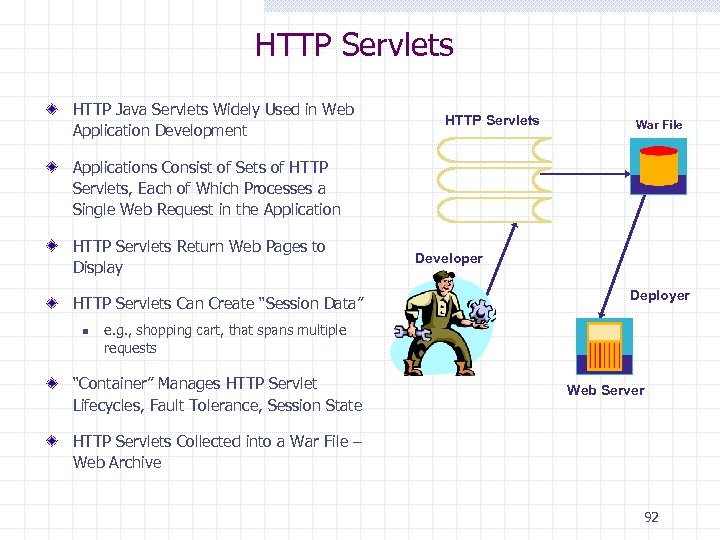
HTTP Servlets HTTP Java Servlets Widely Used in Web Application Development HTTP Servlets War File Applications Consist of Sets of HTTP Servlets, Each of Which Processes a Single Web Request in the Application HTTP Servlets Return Web Pages to Display HTTP Servlets Can Create “Session Data” n Developer Deployer e. g. , shopping cart, that spans multiple requests “Container” Manages HTTP Servlet Lifecycles, Fault Tolerance, Session State Web Server HTTP Servlets Collected into a War File – Web Archive 92

SIP Servlet API Java extension API for SIP servers Similar in spirit to HTTP servlet API Server matches incoming messages against local rules in order to decide which servlet to pass message to The API gives full control to servlets to handle SIP messages, e. g. n has full access to headers and body n proxy or redirect requests n respond to or reject requests n forward responses upstream n initiate requests Servers may choose to provide constrained environment to selected servlets (e. g. using sandbox security model) 93
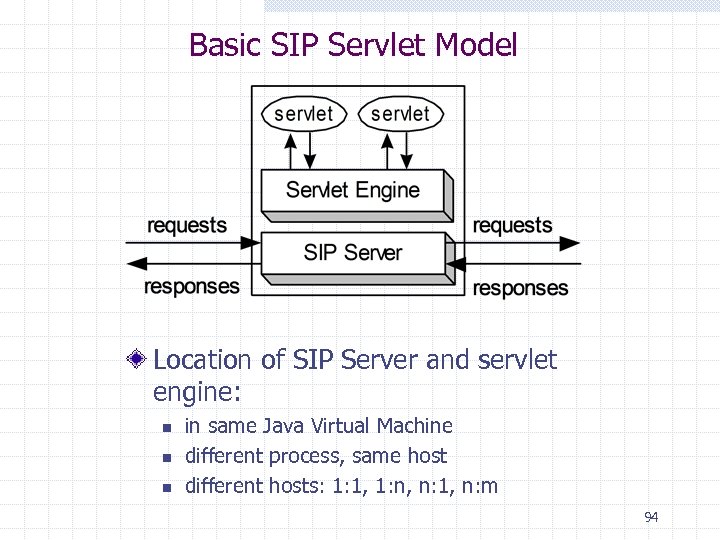
Basic SIP Servlet Model Location of SIP Server and servlet engine: n n n in same Java Virtual Machine different process, same host different hosts: 1: 1, 1: n, n: 1, n: m 94
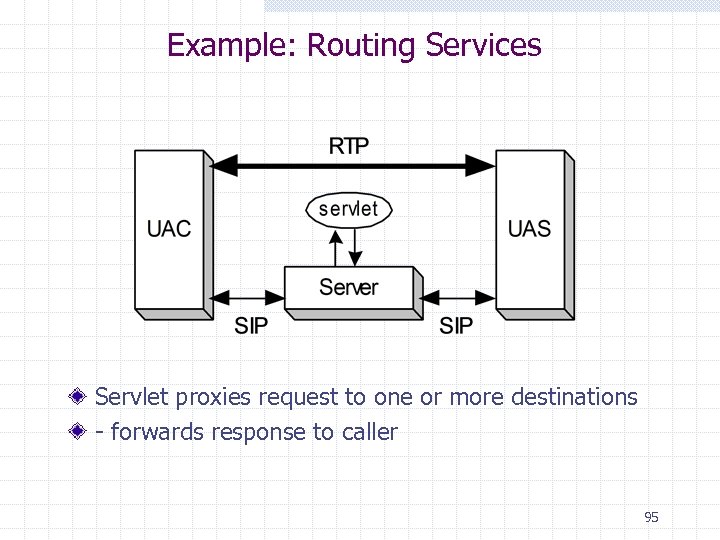
Example: Routing Services Servlet proxies request to one or more destinations - forwards response to caller 95
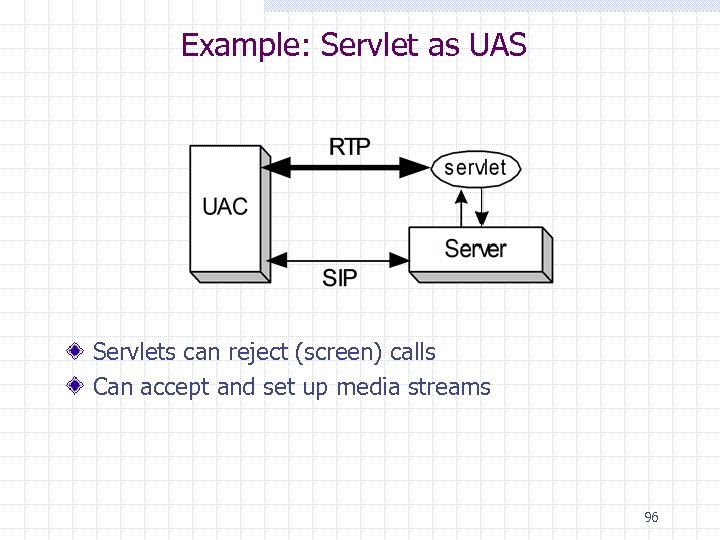
Example: Servlet as UAS Servlets can reject (screen) calls Can accept and set up media streams 96
Benefits of Servlet Model Powerful: n Full access to SIP signaling Performance: n No need to fork new process for each request n The same servlet can handle many requests simultaneously Safety: type checked; no pointers; exception handling Convenience: n high level abstractions. n Tight integration with server: logging, security, location database Lifecycle model allows servlets to n maintain state, e. g. database connections n manage timers Access to wide range of APIs 97
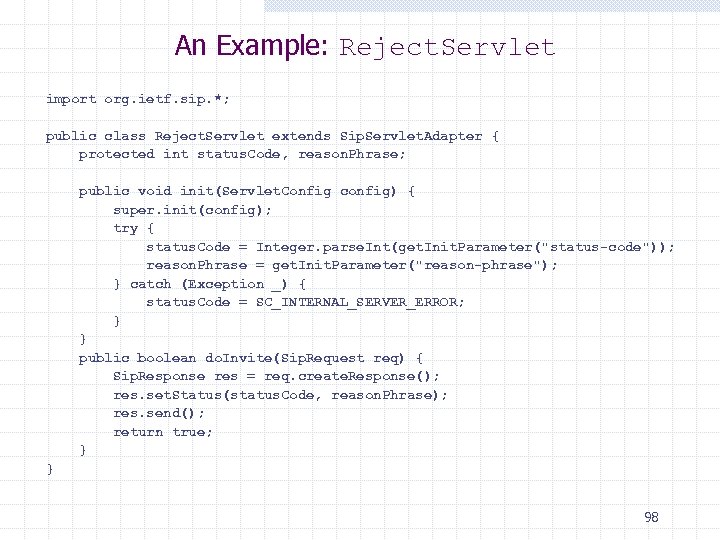
An Example: Reject. Servlet import org. ietf. sip. *; public class Reject. Servlet extends Sip. Servlet. Adapter { protected int status. Code, reason. Phrase; public void init(Servlet. Config config) { super. init(config); try { status. Code = Integer. parse. Int(get. Init. Parameter("status-code")); reason. Phrase = get. Init. Parameter("reason-phrase"); } catch (Exception _) { status. Code = SC_INTERNAL_SERVER_ERROR; } } public boolean do. Invite(Sip. Request req) { Sip. Response res = req. create. Response(); res. set. Status(status. Code, reason. Phrase); res. send(); return true; } } 98
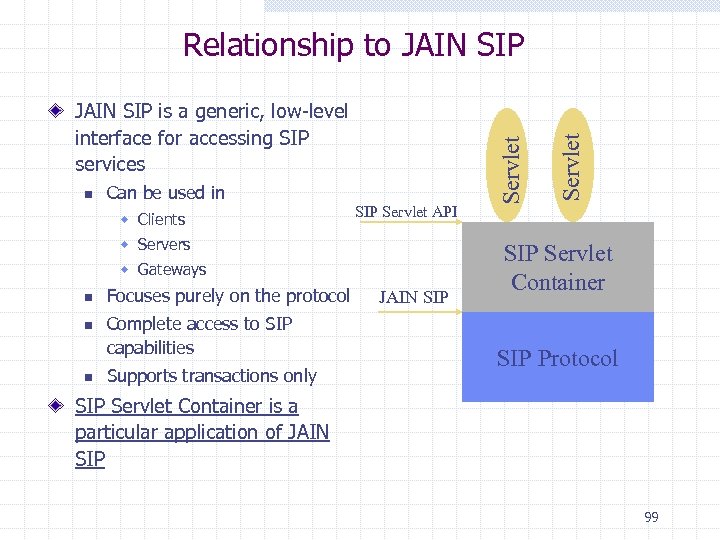
n Can be used in w Clients SIP Servlet API w Servers w Gateways n n n Focuses purely on the protocol Complete access to SIP capabilities Supports transactions only JAIN SIP Servlet JAIN SIP is a generic, low-level interface for accessing SIP services Servlet Relationship to JAIN SIP Servlet Container SIP Protocol SIP Servlet Container is a particular application of JAIN SIP 99
Relationship to JAIN SIP Servlets focus on high volume carrier grade servers Add significant, non-SIP protocol functions n n n n Lifecycle management Domain objects Context and configuration Deployment descriptors Archive files Synchronization primitives Security Add significant SIP protocol functions n Construction of requests and responses from domain objects Hide many parts of JAIN SIP n n Direct access to many headers is not provided Write access to most everything is often restricted Servlets should be defined to allow a SIP container to be built using JAIN SIP n n SIP Objects in Servlet API defined with interfaces that match JAIN SIP signatures Cannot directly expose JAIN SIP objects, though 100

SIP CGI Almost identical to HTTP CGI Language independent ( Perl, Tcl, C, C++, . . . ) Any binary may be executed as a separate program Suitable for services that contains substantial web content Passes message parameters through environmental variables to a separate program. More flexible but more risky Feb. 1, 2001: RFC 3050 (Common Gateway Interface for SIP) published 101

Call Processing Language )CPL( Designed by the IETF to support sophisticated telephony services May be used by both SIP or H. 323. XML based scripting language for describing controlling call services Simple Syntax Extendible Easily edited by GUI tools Scripts runs on network SIP signaling server to create end user services Lightweight CPL interpreter is need to parser & validate scripts 102
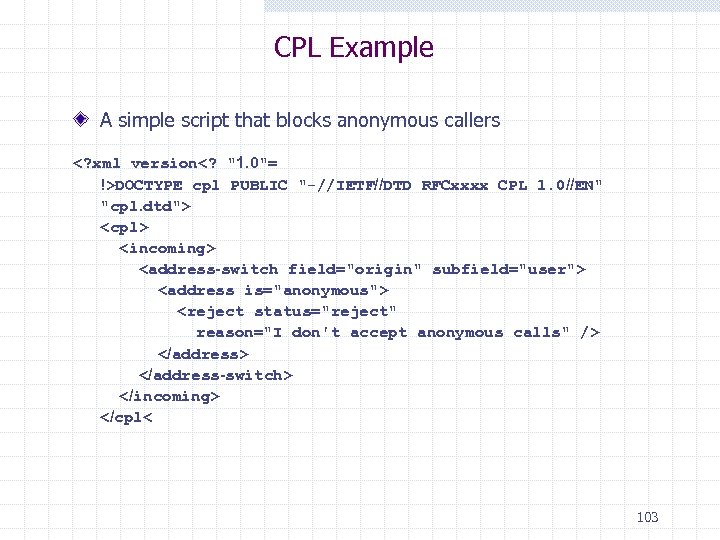
CPL Example A simple script that blocks anonymous callers <? xml version<? "1. 0"= !>DOCTYPE cpl PUBLIC "-//IETF//DTD RFCxxxx CPL 1. 0//EN" "cpl. dtd"> <cpl> <incoming> <address-switch field="origin" subfield="user"> <address is="anonymous"> <reject status="reject" reason="I don't accept anonymous calls" /> </address> </address-switch> </incoming> </cpl< 103

Some Related Works Parlay IMS IPv 6

Why Parlay is Important to Galaxy Open standard Range of services Many levels of sophistication and complexity Secure framework for discovery of and access to services by third party applications Registration of non-Parlay service APIs Independent of specific network and software environment 105
Why Unified Communications? Messages Calls Private Job • Fixed Private • Fax • E-mail • Mobile • SMS • Vo. IP • V-mail • MPEG • IM 106
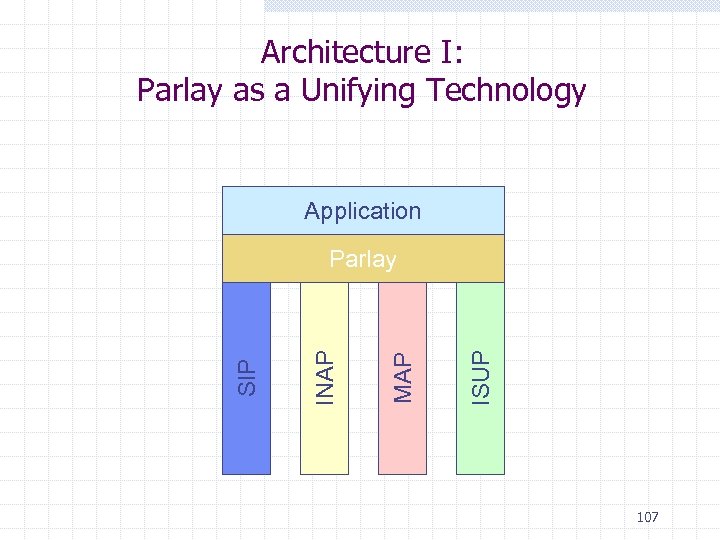
Architecture I: Parlay as a Unifying Technology Application ISUP MAP INAP SIP Parlay 107
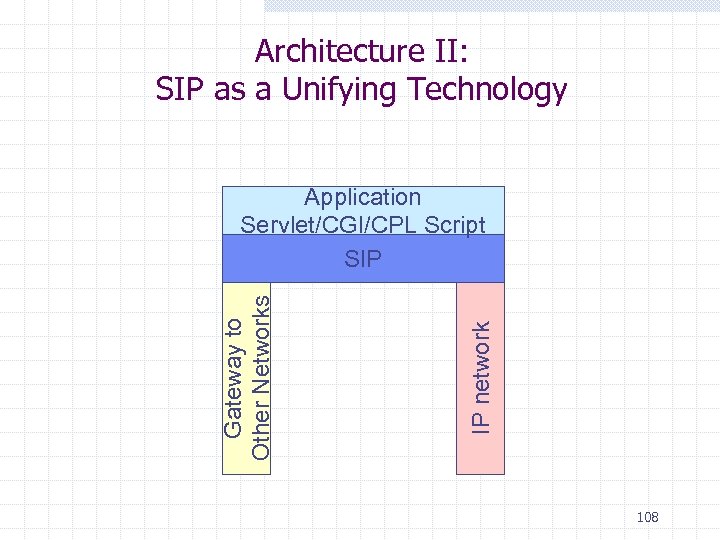
Architecture II: SIP as a Unifying Technology IP network Gateway to Other Networks Application Servlet/CGI/CPL Script SIP 108
Key Questions Which of these two models is correct, or are there opportunities for both approaches to co-exist? How well can a generic network API sit on top of SIP? For example, would it severely limit a developer, and what advantages would it offer? Which aspects of network functionality will actually be useful in practice to developers? 109
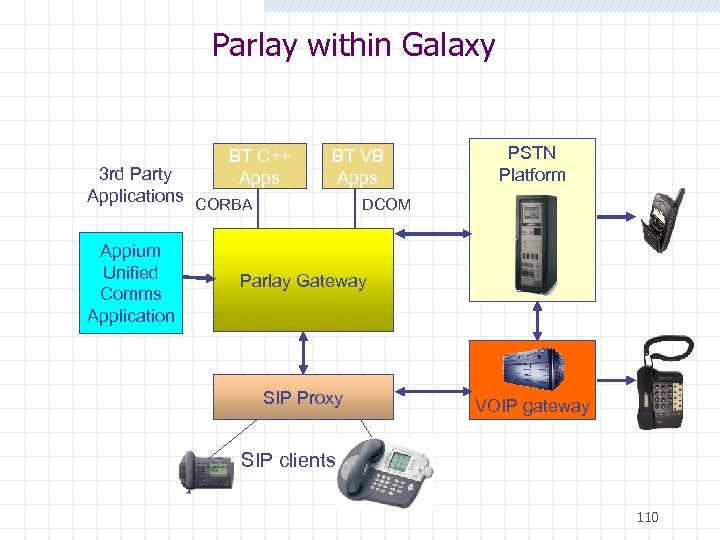
Parlay within Galaxy BT C++ Apps 3 rd Party Applications CORBA Appium Unified Comms Application BT VB Apps PSTN Platform DCOM Parlay Gateway SIP Proxy VOIP gateway SIP clients 110
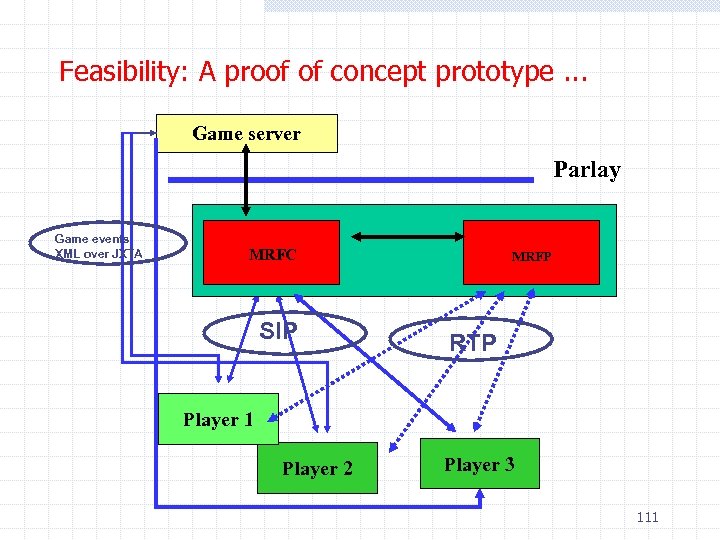
Feasibility: A proof of concept prototype. . . Game server Parlay Game events XML over JXTA MRFC SIP MRFP RTP Player 1 Player 2 Player 3 111

Some Challenges for Parlay Which technologies should Parlay support? How can interoperability testing be encouraged? How can Parlay get feedback from developers? Sizeable specifications with complex interfaces and data types give long learning curve for developers? Although specifications are maturing, still few Parlay products commercially available. Why? How does Parlay keep pace with new protocols? 112

Parlay on a SIP Network ? Parlay adds security to SIP Parlay provides many features not available in SIP APIs Parlay provides a network independent model BUT. . . SIP APIs can make some simpler solutions for some applications envisaged by Parlay group Parlay could support SIP better SO. . . SIP will have a significant impact on the future of Parlay SIP and Parlay can already work well together and are a powerful combination 113
Global SIP/IMS deployment needs IPv 6 Introduction of SIP-based peer-to-peer services is an important step after current client-server based services. IP Multimedia Subsystem (IMS) is a service infrastructure based on the use of Session Initiation Protocol (SIP). n n 3 GPP Release 5 and 6 specifications 3 GPP 2 specifications In order to make peer-to-peer services work between different operators' networks, IPv 6 is needed - peer-to-peer services work well only with public IP addresses. n n Small scale IMS deployment / piloting can be started with IPv 4. IPv 6 is vital for wider scale, global IMS deployment. 114
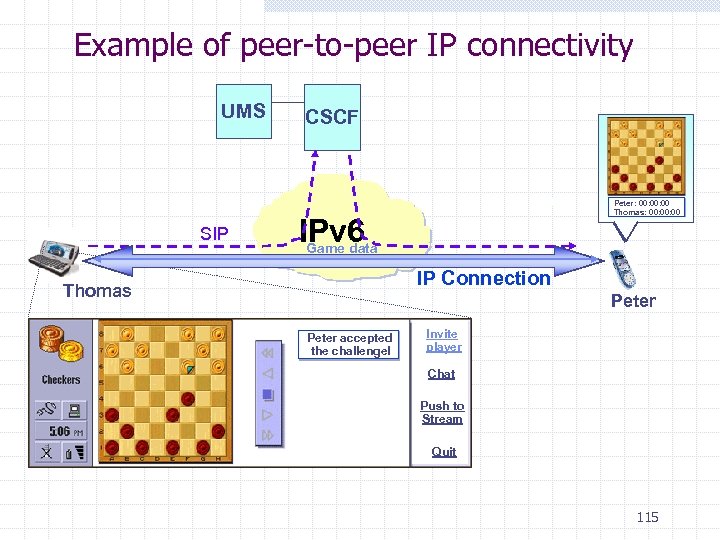
Example of peer-to-peer IP connectivity UMS CSCF Thomas challenges you to a game of checkers! Peter: 00: 00 SIP Accept Decline Thomas: 00: 00 IPv 6 Game data IP Connection Thomas Peter accepted the challenge! Invite player Chat Push to Stream Quit 115
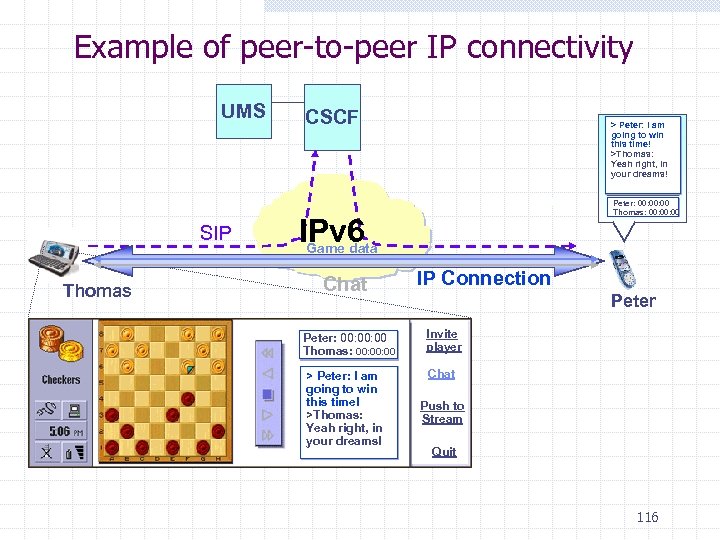
Example of peer-to-peer IP connectivity UMS SIP Thomas CSCF > Peter: I am going to win this time! >Thomas: Yeah right, in your dreams! Peter: 00: 00 Thomas: 00: 00 IPv 6 Game data Chat IP Connection Peter: 00: 00 Thomas: 00: 00 Invite player > Peter: I am going to win this time! >Thomas: Yeah right, in your dreams! Chat Push to Stream Quit 116
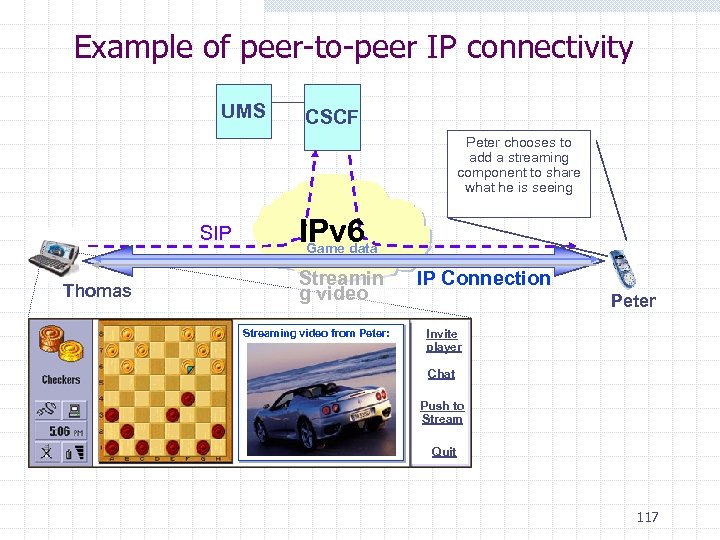
Example of peer-to-peer IP connectivity UMS CSCF Peter chooses to add a streaming component to share what he is seeing SIP Thomas IPv 6 Game data Streamin g video Streaming video from Peter: 00: 00 Thomas: 00: 00 > Peter: hey, look what just passed by! IP Connection Peter Invite player Chat Push to Stream Quit 117
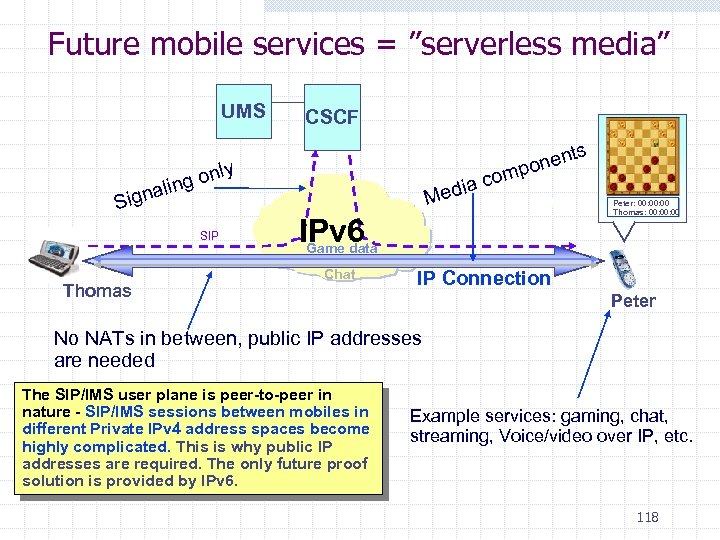
Future mobile services = ”serverless media” UMS CSCF ly on ling a Sign SIP Thomas s nent po m o dia c Me IPv 6 Game data Chat Peter: 00: 00 Thomas: 00: 00 IP Connection Peter No NATs in between, public IP addresses are needed The SIP/IMS user plane is peer-to-peer in nature - SIP/IMS sessions between mobiles in different Private IPv 4 address spaces become highly complicated. This is why public IP addresses are required. The only future proof solution is provided by IPv 6. Example services: gaming, chat, streaming, Voice/video over IP, etc. 118
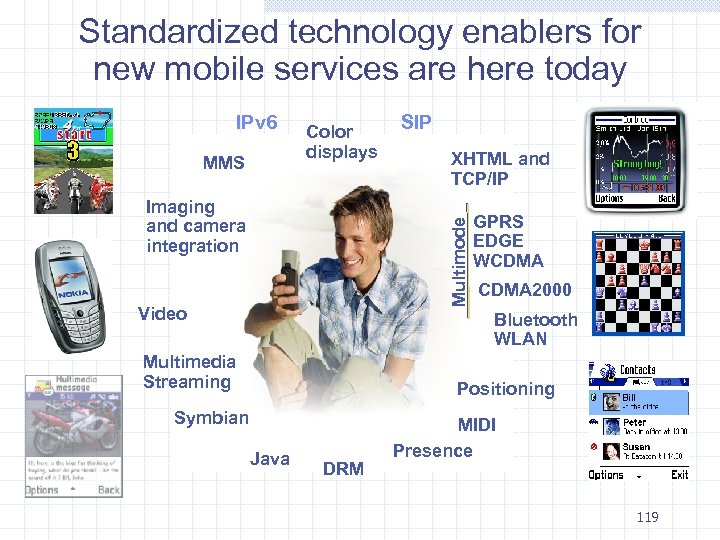
Standardized technology enablers for new mobile services are here today IPv 6 MMS Color displays XHTML and TCP/IP Multimode Imaging and camera integration SIP Video GPRS EDGE WCDMA 2000 Bluetooth WLAN Multimedia Streaming Positioning Symbian Java DRM MIDI Presence 119
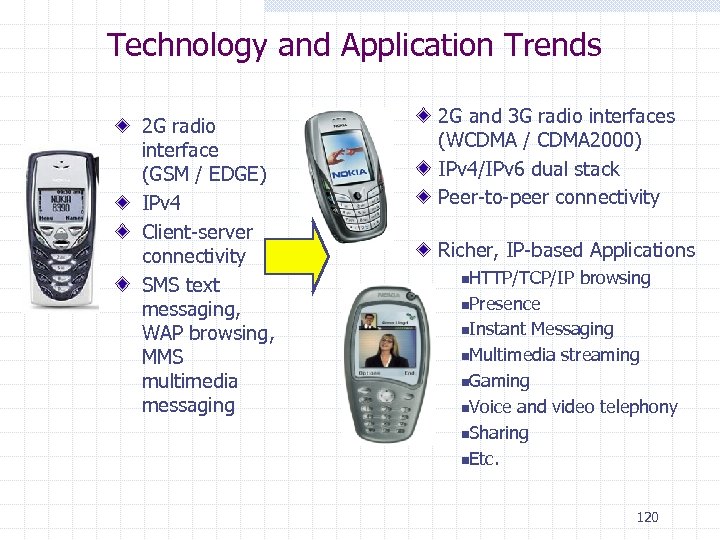
Technology and Application Trends 2 G radio interface (GSM / EDGE) IPv 4 Client-server connectivity SMS text messaging, WAP browsing, MMS multimedia messaging 2 G and 3 G radio interfaces (WCDMA / CDMA 2000) IPv 4/IPv 6 dual stack Peer-to-peer connectivity Richer, IP-based Applications n. HTTP/TCP/IP browsing n. Presence n. Instant Messaging n. Multimedia streaming n. Gaming n. Voice and video telephony n. Sharing n. Etc. 120
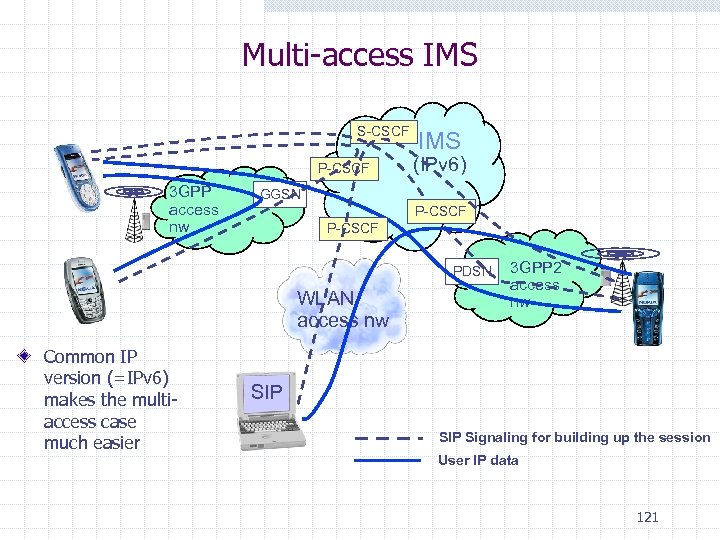
Multi-access IMS S-CSCF P-CSCF 3 GPP access nw IMS (IPv 6) GGSN P-CSCF PDSN WLAN access nw Common IP version (=IPv 6) makes the multiaccess case much easier 3 GPP 2 access nw SIP Signaling for building up the session User IP data 121

References Anders Kristensen, Hewlett-Packard Laboratories, Bristol, U. K Nicolas FISCHBACH, Senior Manager, IP Engineering/Security - COLT Telecom Jonathan Rosenberg, Dynamicsoft Ed Luff, Newport Networks Patrick Ferriter, ZULTYS 122
6e3f29d9944e20bf5589f2a2380155c8.ppt