ad5f935bd944f584475e902bef42d3ae.ppt
- Количество слайдов: 40
 Single-hop and Multi-hop MANET Security S. Srinivasan Professor of CIS University of Louisville, Kentucky, USA 1
Single-hop and Multi-hop MANET Security S. Srinivasan Professor of CIS University of Louisville, Kentucky, USA 1
 Outline • • Mobile Ad hoc Network (MANET) Single-hop Networks Multi-hop Networks Current models: – Denial of Service (Do. S) – Selfish node – Routing • Our research • Open research areas involving MANET 2
Outline • • Mobile Ad hoc Network (MANET) Single-hop Networks Multi-hop Networks Current models: – Denial of Service (Do. S) – Selfish node – Routing • Our research • Open research areas involving MANET 2
 MANET • • • MANET is a temporary network No central server Infrastructure-free Comparison with wired network Trust establishment 3
MANET • • • MANET is a temporary network No central server Infrastructure-free Comparison with wired network Trust establishment 3
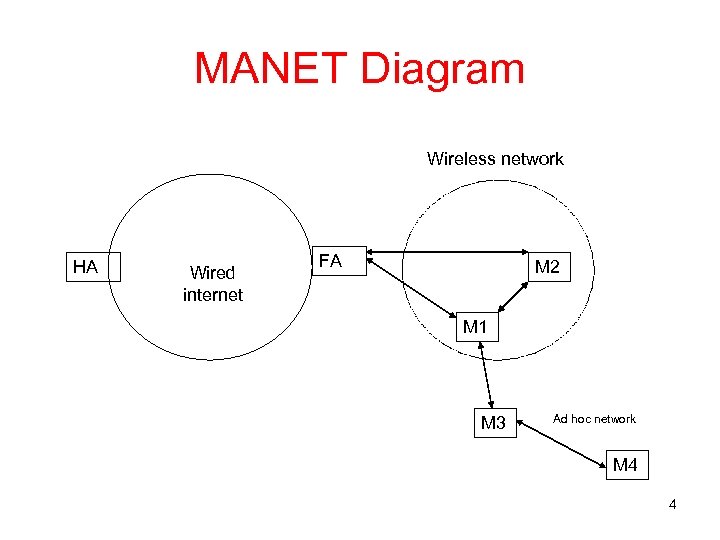 MANET Diagram Wireless network HA Wired internet FA M 2 M 1 M 3 Ad hoc network M 4 4
MANET Diagram Wireless network HA Wired internet FA M 2 M 1 M 3 Ad hoc network M 4 4
 MANET Security • Principal aspects are: – Confidentiality – Integrity • Vulnerabilities are: – Malicious nodes – Covert channels – Eavesdroppers 5
MANET Security • Principal aspects are: – Confidentiality – Integrity • Vulnerabilities are: – Malicious nodes – Covert channels – Eavesdroppers 5
 Single-hop Networks • Base Station (BS) plays a critical role • BS is involved in communication with every Mobile Node (MN) • BS takes care of channel assignment for RTS (Request To Send) and CTS (Clear To Send) packets • Usual MAC protocol is slotted ALOHA (GSM uses this for access requests) 6
Single-hop Networks • Base Station (BS) plays a critical role • BS is involved in communication with every Mobile Node (MN) • BS takes care of channel assignment for RTS (Request To Send) and CTS (Clear To Send) packets • Usual MAC protocol is slotted ALOHA (GSM uses this for access requests) 6
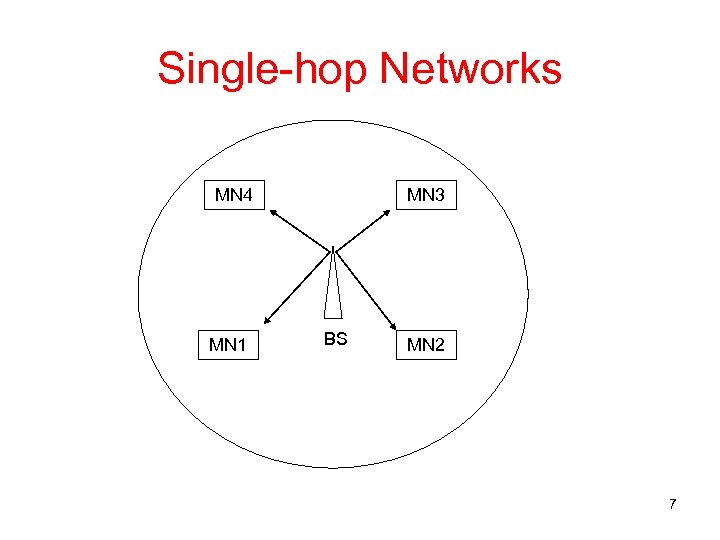 Single-hop Networks MN 4 MN 1 MN 3 BS MN 2 7
Single-hop Networks MN 4 MN 1 MN 3 BS MN 2 7
 Single-hop Networks • Usually 7 frequencies are reused • Neighboring cells use different frequencies • Within each cell dedicated single channels are used for each direction of traffic 8
Single-hop Networks • Usually 7 frequencies are reused • Neighboring cells use different frequencies • Within each cell dedicated single channels are used for each direction of traffic 8
 Multi-hop Networks • Extends coverage area of single-hop networks • Mobile node to mobile node connections allowed • More demands placed on MAC protocols than single-hop networks • Multi-hop networks can provide connection -oriented service by partitioning available bandwidth to multiple channels 9
Multi-hop Networks • Extends coverage area of single-hop networks • Mobile node to mobile node connections allowed • More demands placed on MAC protocols than single-hop networks • Multi-hop networks can provide connection -oriented service by partitioning available bandwidth to multiple channels 9
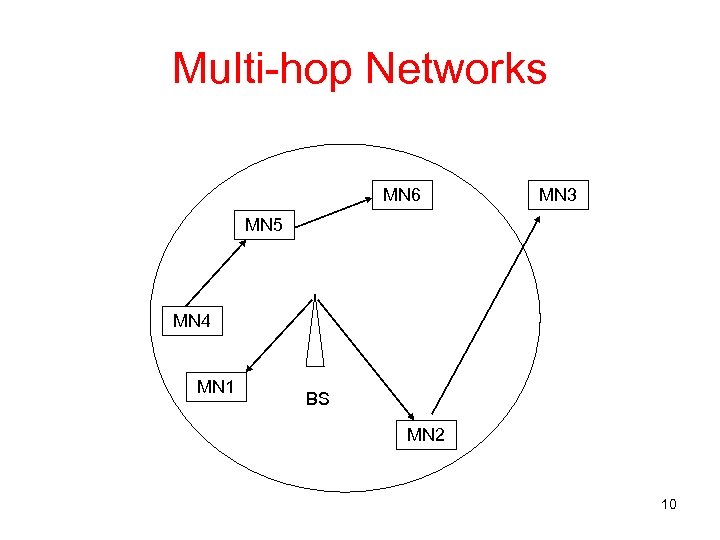 Multi-hop Networks MN 6 MN 3 MN 5 MN 4 MN 1 BS MN 2 10
Multi-hop Networks MN 6 MN 3 MN 5 MN 4 MN 1 BS MN 2 10
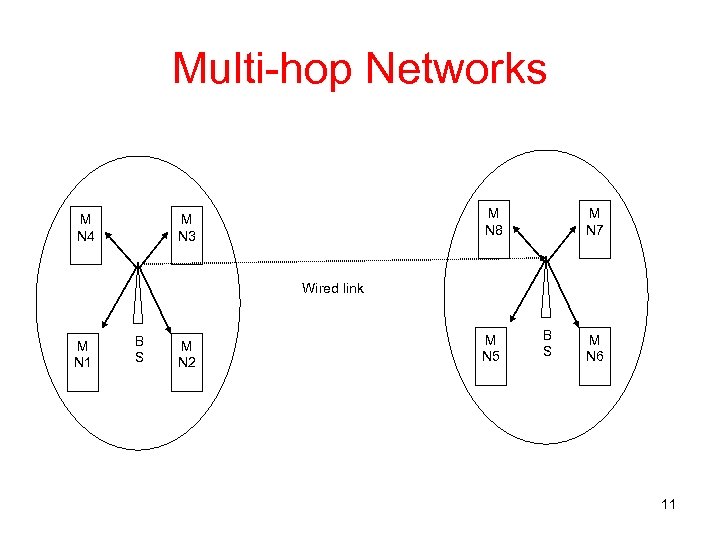 Multi-hop Networks M N 4 M N 8 M N 3 M N 7 Wired link M N 1 B S M N 2 M N 5 B S M N 6 11
Multi-hop Networks M N 4 M N 8 M N 3 M N 7 Wired link M N 1 B S M N 2 M N 5 B S M N 6 11
 Multi-hop Networks • Common protocols used are the Floor Acquisition Multiple Access (FAMA) class of protocols • 802. 11 DCF (Distributed Coordination Function) protocol is very cost effective and mature. This is actually a CSMA/CA. • Typically the transmission range of a mobile device is not a constraint but the traffic a cell can support is 12
Multi-hop Networks • Common protocols used are the Floor Acquisition Multiple Access (FAMA) class of protocols • 802. 11 DCF (Distributed Coordination Function) protocol is very cost effective and mature. This is actually a CSMA/CA. • Typically the transmission range of a mobile device is not a constraint but the traffic a cell can support is 12
 Multi-hop Networks • Policy of not reusing a channel in adjacent cells works in single-hop networks • In multi-hop networks, sharing of data and control channel in the entire service area is preferable • Benefits of multi-hop networks over single-hop networks are: – robustness – higher bandwidth availability – spatial reuse 13
Multi-hop Networks • Policy of not reusing a channel in adjacent cells works in single-hop networks • In multi-hop networks, sharing of data and control channel in the entire service area is preferable • Benefits of multi-hop networks over single-hop networks are: – robustness – higher bandwidth availability – spatial reuse 13
 Multi-hop Networks • Robustness comes from not having a single path such as via an Access Point (AP) • Example: email • Bandwidth is higher at shorter range • Less power is required to transmit over shorter distances • Since multiple paths exist to the network over multiple nodes, there is no bottleneck of an AP 14
Multi-hop Networks • Robustness comes from not having a single path such as via an Access Point (AP) • Example: email • Bandwidth is higher at shorter range • Less power is required to transmit over shorter distances • Since multiple paths exist to the network over multiple nodes, there is no bottleneck of an AP 14
 Current Models • Denial of Service (Do. S) – Malicious nodes and selfish nodes cause Do. S • Yi et al (2002) discuss Mobile Certification Authority (MOCA) protocol for MANETs using PKI • MOCA distributes Certificate Authority functionality to selected nodes based on trust 15
Current Models • Denial of Service (Do. S) – Malicious nodes and selfish nodes cause Do. S • Yi et al (2002) discuss Mobile Certification Authority (MOCA) protocol for MANETs using PKI • MOCA distributes Certificate Authority functionality to selected nodes based on trust 15
 Current Models • Avoine et al (2002) discuss their fair key exchange model called Guardian Angel • Uses probabilistic techniques without any trusted third party for key exchange 16
Current Models • Avoine et al (2002) discuss their fair key exchange model called Guardian Angel • Uses probabilistic techniques without any trusted third party for key exchange 16
 Current Models • Selfish nodes • Buttyan et al (2003) show using simulation how selfish nodes fail to participate in packet forwarding • Buttyan study shows that every node spends 80% of energy for packet forwarding • A nuglet counter is used here to keep track of selfish node behavior. It is a tamper resistant hardware security module attached to a node. Detects selfishness in packet forwarding. 17
Current Models • Selfish nodes • Buttyan et al (2003) show using simulation how selfish nodes fail to participate in packet forwarding • Buttyan study shows that every node spends 80% of energy for packet forwarding • A nuglet counter is used here to keep track of selfish node behavior. It is a tamper resistant hardware security module attached to a node. Detects selfishness in packet forwarding. 17
 Current Models • Nuglet counter is decreased when it originates a packet and increased when it forwards a packet • Nodes that participate in the ad hoc network must maintain a positive nuglet counter • If n is the number of intermediate nodes to the destination, then the originator can send the packet if its nuglet counter is >= n. In that case the nuglet counter is decreased by n. Otherwise, the node cannot send its packet • When the node forwards one packet for others then its nuglet counter is increased by one 18
Current Models • Nuglet counter is decreased when it originates a packet and increased when it forwards a packet • Nodes that participate in the ad hoc network must maintain a positive nuglet counter • If n is the number of intermediate nodes to the destination, then the originator can send the packet if its nuglet counter is >= n. In that case the nuglet counter is decreased by n. Otherwise, the node cannot send its packet • When the node forwards one packet for others then its nuglet counter is increased by one 18
 Current Models • Michiardi et al (2002) have developed the CORE (Collaborative Reputation) model for monitoring behavior of neighboring nodes for selfish behavior • Each node monitors the behavior of neighboring nodes for a specific function. If performance matches expected behavior then observation is positive. • One node sends a probing message to a node one hop away. If the message is acknowledged within the timeout period then the neighbor did the forwarding. • Lack of positive values would result in node getting isolated 19
Current Models • Michiardi et al (2002) have developed the CORE (Collaborative Reputation) model for monitoring behavior of neighboring nodes for selfish behavior • Each node monitors the behavior of neighboring nodes for a specific function. If performance matches expected behavior then observation is positive. • One node sends a probing message to a node one hop away. If the message is acknowledged within the timeout period then the neighbor did the forwarding. • Lack of positive values would result in node getting isolated 19
 Current Models • How selfish behavior is detected: – Each node selects a backoff value in the range [0, CW] where CW is contention window duration – When channel is idle, the backoff counter is decremented by one after every time slot – Counter is frozen when channel is busy – Misbehaving nodes attempt to choose a backoff value in the range [0, CW/4] thereby they get quicker access to the bus – This is controlled by the receiver monitoring the sender behavior by assigning a backoff value to sender 20
Current Models • How selfish behavior is detected: – Each node selects a backoff value in the range [0, CW] where CW is contention window duration – When channel is idle, the backoff counter is decremented by one after every time slot – Counter is frozen when channel is busy – Misbehaving nodes attempt to choose a backoff value in the range [0, CW/4] thereby they get quicker access to the bus – This is controlled by the receiver monitoring the sender behavior by assigning a backoff value to sender 20
 Current Models • Routing • Main methods are: – AODV (Ad hoc On-demand Distance Vector) – DSDV (Destination Sequenced Distance Vector) – AODV is a reactive protocol – DSDV is a proactive protocol – DSDV maintains a dynamic routing table at all times 21
Current Models • Routing • Main methods are: – AODV (Ad hoc On-demand Distance Vector) – DSDV (Destination Sequenced Distance Vector) – AODV is a reactive protocol – DSDV is a proactive protocol – DSDV maintains a dynamic routing table at all times 21
 Current Models • Yang et al, ACM conf. , 2002, have developed a unified method called Self Organized Security (SOS) scheme using AODV method • SOS does not assume any prior trust arrangement among nodes • Each node in the network needs a token to participate • Tokens have expiration time stamp • Well-behaving nodes gain longer time duration before renewal 22
Current Models • Yang et al, ACM conf. , 2002, have developed a unified method called Self Organized Security (SOS) scheme using AODV method • SOS does not assume any prior trust arrangement among nodes • Each node in the network needs a token to participate • Tokens have expiration time stamp • Well-behaving nodes gain longer time duration before renewal 22
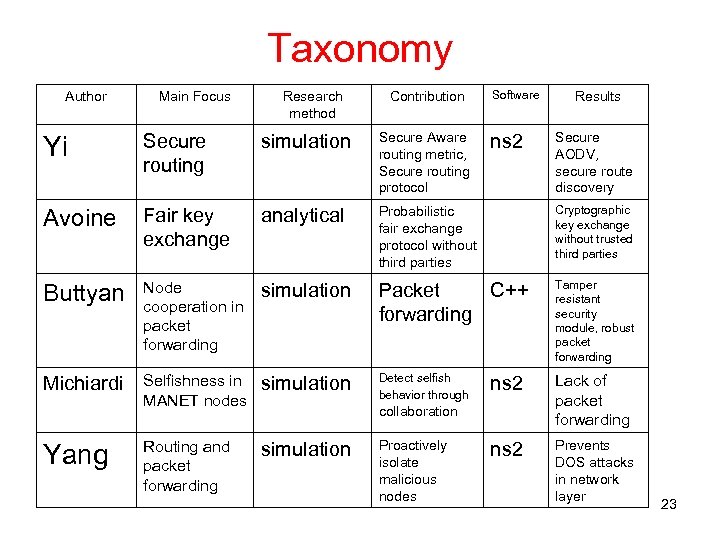 Taxonomy Author Main Focus Research method Contribution Software Results Yi Secure routing simulation Secure Aware routing metric, Secure routing protocol Avoine Fair key exchange analytical Probabilistic fair exchange protocol without third parties Cryptographic key exchange without trusted third parties Buttyan Node cooperation in packet forwarding simulation Packet C++ forwarding Tamper resistant security module, robust packet forwarding Michiardi Selfishness in MANET nodes simulation Detect selfish behavior through ns 2 Lack of packet forwarding Routing and packet forwarding simulation ns 2 Prevents DOS attacks in network layer Yang ns 2 collaboration Proactively isolate malicious nodes Secure AODV, secure route discovery 23
Taxonomy Author Main Focus Research method Contribution Software Results Yi Secure routing simulation Secure Aware routing metric, Secure routing protocol Avoine Fair key exchange analytical Probabilistic fair exchange protocol without third parties Cryptographic key exchange without trusted third parties Buttyan Node cooperation in packet forwarding simulation Packet C++ forwarding Tamper resistant security module, robust packet forwarding Michiardi Selfishness in MANET nodes simulation Detect selfish behavior through ns 2 Lack of packet forwarding Routing and packet forwarding simulation ns 2 Prevents DOS attacks in network layer Yang ns 2 collaboration Proactively isolate malicious nodes Secure AODV, secure route discovery 23
 Our Research • We are pursuing four different research threads • Development of Threshold Index (TI) using fuzzy logic • X = { xi } is a sample space of significant parameters (e. g. , packets lost, number of collisions) • A = { (xi, µj(xi)), xi ε X } where µj is the grade of membership of xi 24
Our Research • We are pursuing four different research threads • Development of Threshold Index (TI) using fuzzy logic • X = { xi } is a sample space of significant parameters (e. g. , packets lost, number of collisions) • A = { (xi, µj(xi)), xi ε X } where µj is the grade of membership of xi 24
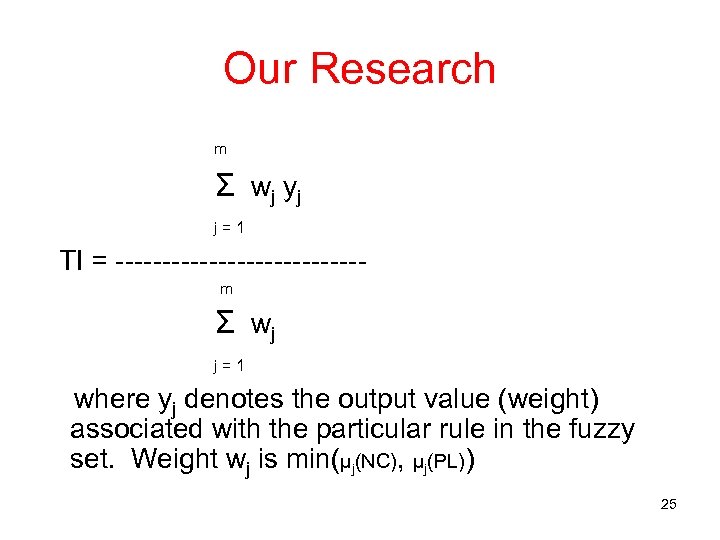 Our Research m Σ wj yj j = 1 TI = ------------- m Σ wj j = 1 where yj denotes the output value (weight) associated with the particular rule in the fuzzy set. Weight wj is min(µj(NC), µj(PL)) 25
Our Research m Σ wj yj j = 1 TI = ------------- m Σ wj j = 1 where yj denotes the output value (weight) associated with the particular rule in the fuzzy set. Weight wj is min(µj(NC), µj(PL)) 25
 Our Research • Rule strength wj = min(µj (xi)) where i ε {1, 2, …, n} and n is the number of input metrics for each rule • Given k membership values, m = kn • A sample fuzzy relation is shown next • In the example, we use the weights to be 1, 5 or 9 based on the firing rule corresponding to small, medium or large 26
Our Research • Rule strength wj = min(µj (xi)) where i ε {1, 2, …, n} and n is the number of input metrics for each rule • Given k membership values, m = kn • A sample fuzzy relation is shown next • In the example, we use the weights to be 1, 5 or 9 based on the firing rule corresponding to small, medium or large 26
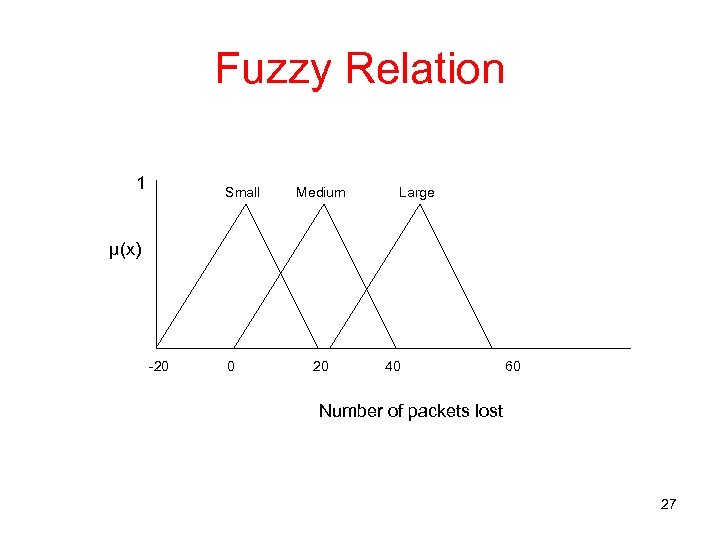 Fuzzy Relation 1 Small Medium Large µ(x) -20 0 20 40 60 Number of packets lost 27
Fuzzy Relation 1 Small Medium Large µ(x) -20 0 20 40 60 Number of packets lost 27
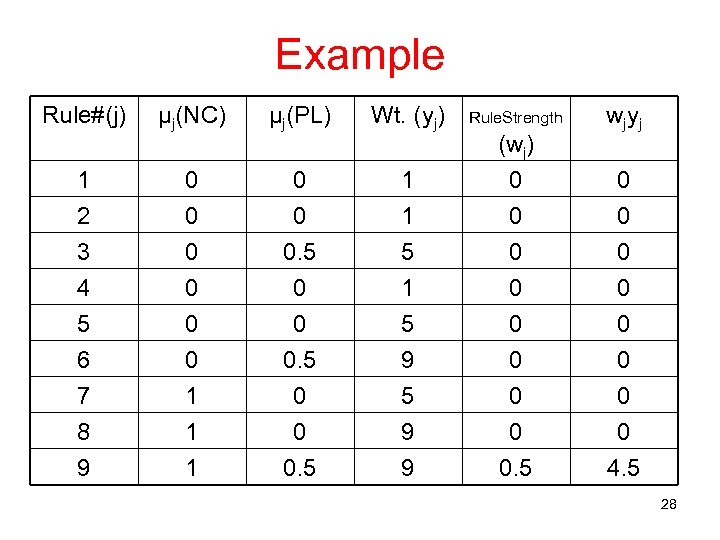 Example Rule#(j) µj(NC) µj(PL) Wt. (yj) 1 2 0 0 1 1 (wj) 0 0 3 4 5 6 7 8 9 0 0 1 1 1 0. 5 0 0 0. 5 5 1 5 9 9 0 0 0 0. 5 Rule. Strength wjyj 0 0 0 0 4. 5 28
Example Rule#(j) µj(NC) µj(PL) Wt. (yj) 1 2 0 0 1 1 (wj) 0 0 3 4 5 6 7 8 9 0 0 1 1 1 0. 5 0 0 0. 5 5 1 5 9 9 0 0 0 0. 5 Rule. Strength wjyj 0 0 0 0 4. 5 28
 Our Research • TI is used to classify the threat faced by mobile nodes. • Classifications used are normal, uncertain and vulnerable • Extensive simulation using ns 2 software has been done • Currently we are in the process of testing the scenarios using specialized hardware 29
Our Research • TI is used to classify the threat faced by mobile nodes. • Classifications used are normal, uncertain and vulnerable • Extensive simulation using ns 2 software has been done • Currently we are in the process of testing the scenarios using specialized hardware 29
 Our Research • A second thread of research involving MANETs deals with multi-hop networks as opposed to single-hop networks • Multi-hop networks involve not only laptops but also PDAs and cell phones • Trust aspects play a key role identifying nodes for inclusion in the network 30
Our Research • A second thread of research involving MANETs deals with multi-hop networks as opposed to single-hop networks • Multi-hop networks involve not only laptops but also PDAs and cell phones • Trust aspects play a key role identifying nodes for inclusion in the network 30
 Our Research • One work is based on a general security control for a multi-hop network • This is aimed at preventing attacks on paging and registration, also forging Foreign Agent (FA) • Uses mobile IP security (provides continuous connectivity for mobile hosts) • One protection method is to require all MNs to register • Authenticate MN, FA, HA as a unit • Allow only authenticated nodes to be in the multihop route 31
Our Research • One work is based on a general security control for a multi-hop network • This is aimed at preventing attacks on paging and registration, also forging Foreign Agent (FA) • Uses mobile IP security (provides continuous connectivity for mobile hosts) • One protection method is to require all MNs to register • Authenticate MN, FA, HA as a unit • Allow only authenticated nodes to be in the multihop route 31
 Our Research • Another work is based on secured macro/micromobility protocol for multi-hop cellular IP • Macro-mobility refers to support between local domains for mobility of MNs • Micro-mobility refers to support within a local domain for mobility of MNs • Multi-hop paging cache is used to maintain location of MNs • Multi-hop routing cache is used to maintain multihop routes 32
Our Research • Another work is based on secured macro/micromobility protocol for multi-hop cellular IP • Macro-mobility refers to support between local domains for mobility of MNs • Micro-mobility refers to support within a local domain for mobility of MNs • Multi-hop paging cache is used to maintain location of MNs • Multi-hop routing cache is used to maintain multihop routes 32
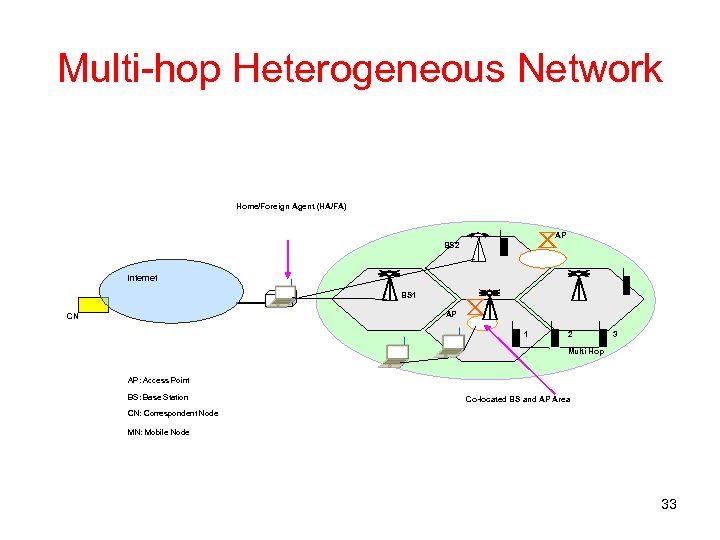 Multi-hop Heterogeneous Network Home/Foreign Agent (HA/FA) AP BS 2 Internet BS 1 AP CN 1 2 3 Multi Hop AP: Access Point BS: Base Station Co-located BS and AP Area CN: Correspondent Node MN: Mobile Node 33
Multi-hop Heterogeneous Network Home/Foreign Agent (HA/FA) AP BS 2 Internet BS 1 AP CN 1 2 3 Multi Hop AP: Access Point BS: Base Station Co-located BS and AP Area CN: Correspondent Node MN: Mobile Node 33
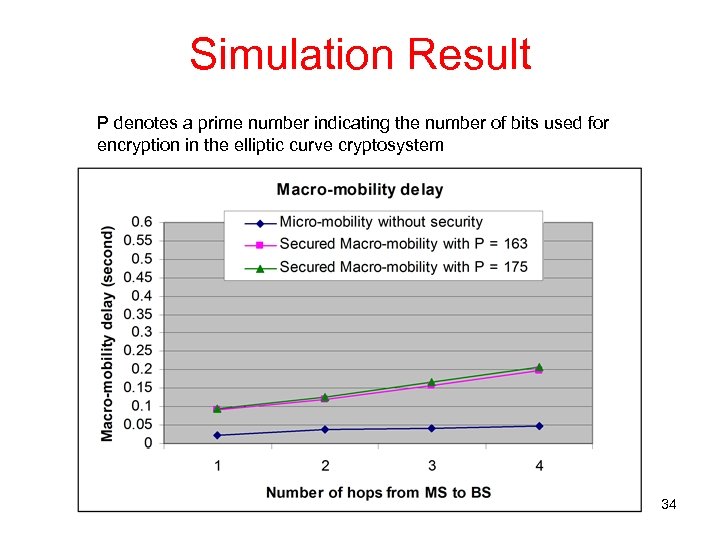 Simulation Result P denotes a prime number indicating the number of bits used for encryption in the elliptic curve cryptosystem 34
Simulation Result P denotes a prime number indicating the number of bits used for encryption in the elliptic curve cryptosystem 34
 Our Research • A third line of research involves mobility management • Mobility management involves knowing what nodes are allowable in a network at a given time • A fourth thread of research involves traceback of nodes. This will help in identifying malicious nodes. 35
Our Research • A third line of research involves mobility management • Mobility management involves knowing what nodes are allowable in a network at a given time • A fourth thread of research involves traceback of nodes. This will help in identifying malicious nodes. 35
 Open Research areas in MANET • MOCA method could be extended to browsing neighboring nodes’ routing tables. Goal is to find multiple routes. This will help in avoiding flooding attacks. • CORE method does not address attacks from active intruders. Nuglet counter could be better utilized for mutual provision of information services • Guardian Angel method could be extended to include Do. S or routing attacks 36
Open Research areas in MANET • MOCA method could be extended to browsing neighboring nodes’ routing tables. Goal is to find multiple routes. This will help in avoiding flooding attacks. • CORE method does not address attacks from active intruders. Nuglet counter could be better utilized for mutual provision of information services • Guardian Angel method could be extended to include Do. S or routing attacks 36
 Open Research areas in Multi-hop Networks • Studies are available based on routing or selfish-node behavior that involve AODV (Ad hoc On demand Distance Vector) or DSDV (Destination Sequenced Distance Vector). A hybrid approach is a viable alternative for performance considerations. • In Multi-hop cellular networks, we could find ways to improve the MAC protocols for faster throughput 37
Open Research areas in Multi-hop Networks • Studies are available based on routing or selfish-node behavior that involve AODV (Ad hoc On demand Distance Vector) or DSDV (Destination Sequenced Distance Vector). A hybrid approach is a viable alternative for performance considerations. • In Multi-hop cellular networks, we could find ways to improve the MAC protocols for faster throughput 37
 References • Michiardi, P. , and Molva, R. , “CORE: A COllaborative REputation mechanism to enforce node cooperation in Mobile Ad Hoc Networks, ” Communication and Multimedia Security Conference, 2002. • Buttyán, L. , and Hubaux, J. , “Stimulating Cooperation in Self-Organizing Mobile Ad Hoc Networks, ” Mobile Networks (MONET), 2003. • Avoine, G. and Vaudenay, S. , “Cryptography with Guardian Angels: Bringing Civilization to Pirates” Report on a Working Session on Security in Wireless Ad Hoc Networks, Levente Buttyan and Jean-Pierre Hubaux (eds. ), ACM Mobile Computing and Communications Review (MC 2 R), Vol. 6. , No. 4. , 2002. • Michiardi, P. , Molva, R. “Prevention of Denial of Service Attacks and selfishness in Mobile Ad Hoc Networks, ” Research Report RR-02 -063 - January 2002. 38
References • Michiardi, P. , and Molva, R. , “CORE: A COllaborative REputation mechanism to enforce node cooperation in Mobile Ad Hoc Networks, ” Communication and Multimedia Security Conference, 2002. • Buttyán, L. , and Hubaux, J. , “Stimulating Cooperation in Self-Organizing Mobile Ad Hoc Networks, ” Mobile Networks (MONET), 2003. • Avoine, G. and Vaudenay, S. , “Cryptography with Guardian Angels: Bringing Civilization to Pirates” Report on a Working Session on Security in Wireless Ad Hoc Networks, Levente Buttyan and Jean-Pierre Hubaux (eds. ), ACM Mobile Computing and Communications Review (MC 2 R), Vol. 6. , No. 4. , 2002. • Michiardi, P. , Molva, R. “Prevention of Denial of Service Attacks and selfishness in Mobile Ad Hoc Networks, ” Research Report RR-02 -063 - January 2002. 38
 References • Ermanno Pietrosemoli, Mesh Networks http: //wireless. ictp. trieste. it/school_2004/lectures/ermann o/mesh. pdf • Yi, S. , Naldurg, P. , Kravets, R. , “A Security-Aware Ad Hoc Routing Protocol for Wireless Networks, ” 6 th World Multi-Conference on Systemics, Cybernetics and Informatics (SCI 2002), 2002. • S. Alampalayam, A. Kumar, S. Srinivasan, “Mobile Ad hoc Network Security: A Taxonomy, ” 7 th IEEE Int’l Conf. on Computer Communications Security, Phoenix Park, South Korea, Feb. 23 -25, 2005. • Yang, H. , Meng, X. , and Lu, S. , “Self-Organized Network Layer Security in Mobile Ad Hoc Networks, ” ACM MOBICOM Wireless Security Workshop (Wi. Se'02), Atlanta, 2002. 39
References • Ermanno Pietrosemoli, Mesh Networks http: //wireless. ictp. trieste. it/school_2004/lectures/ermann o/mesh. pdf • Yi, S. , Naldurg, P. , Kravets, R. , “A Security-Aware Ad Hoc Routing Protocol for Wireless Networks, ” 6 th World Multi-Conference on Systemics, Cybernetics and Informatics (SCI 2002), 2002. • S. Alampalayam, A. Kumar, S. Srinivasan, “Mobile Ad hoc Network Security: A Taxonomy, ” 7 th IEEE Int’l Conf. on Computer Communications Security, Phoenix Park, South Korea, Feb. 23 -25, 2005. • Yang, H. , Meng, X. , and Lu, S. , “Self-Organized Network Layer Security in Mobile Ad Hoc Networks, ” ACM MOBICOM Wireless Security Workshop (Wi. Se'02), Atlanta, 2002. 39
 References • Y. D. Lin and Y. C. Hsu, “Multihop Cellular: A new architecture for wireless communications, ” IEEE Info. Com 2000, 1273 -1282. • R. Ananthapadmanabha, B. S. Manoj, and C. Siva Ram Murthy, “Multi-hop Cellular Networks: The architecture and routing protocols, ” 12 th Int’l Conf. on PIMRC, vol. 2, Sept. 2001, G-78 -G 82. • B. Xie, A. Kumar, S. Srinivasan, “GSCP: A General Security Control Protocol for Heterogeneous Multi-hop Network” • B. Xie, A. Kumar, S. Srinivasan, “Secured Macro/Micro-Mobility Protocol for Multi-hop Cellular IP” • C. J. Fullmer and J. J. Garcia-Luna-Aceves, “Floor Acquisition Multiple Access (FAMA) for Packet Radio Networks, ” ACM SIGCOMM 1995. 40
References • Y. D. Lin and Y. C. Hsu, “Multihop Cellular: A new architecture for wireless communications, ” IEEE Info. Com 2000, 1273 -1282. • R. Ananthapadmanabha, B. S. Manoj, and C. Siva Ram Murthy, “Multi-hop Cellular Networks: The architecture and routing protocols, ” 12 th Int’l Conf. on PIMRC, vol. 2, Sept. 2001, G-78 -G 82. • B. Xie, A. Kumar, S. Srinivasan, “GSCP: A General Security Control Protocol for Heterogeneous Multi-hop Network” • B. Xie, A. Kumar, S. Srinivasan, “Secured Macro/Micro-Mobility Protocol for Multi-hop Cellular IP” • C. J. Fullmer and J. J. Garcia-Luna-Aceves, “Floor Acquisition Multiple Access (FAMA) for Packet Radio Networks, ” ACM SIGCOMM 1995. 40


