bd1e5b95e6b04305e72dc8075f179456.ppt
- Количество слайдов: 24
 SIMDAT Authentification and Autorisation Matteo Dell’Acqua ET-CTS meeting, Toulouse, 26 -30 May 2008
SIMDAT Authentification and Autorisation Matteo Dell’Acqua ET-CTS meeting, Toulouse, 26 -30 May 2008
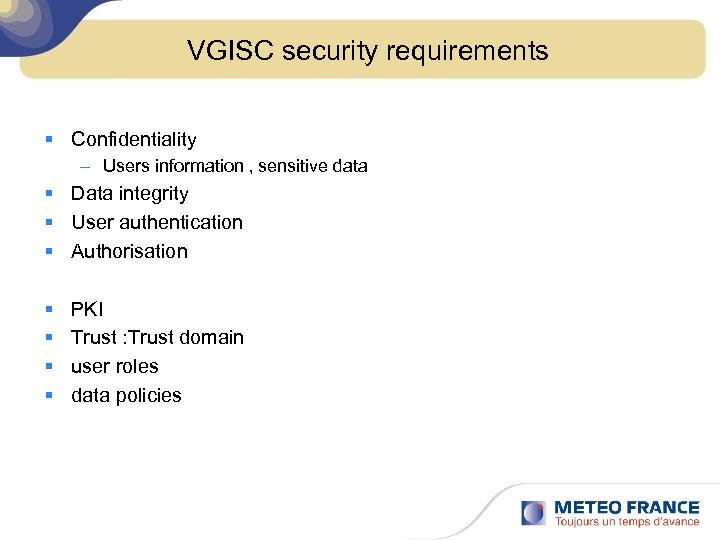 VGISC security requirements § Confidentiality – Users information , sensitive data § Data integrity § User authentication § Authorisation § § PKI Trust : Trust domain user roles data policies
VGISC security requirements § Confidentiality – Users information , sensitive data § Data integrity § User authentication § Authorisation § § PKI Trust : Trust domain user roles data policies
 Virtual Organisation Principles A D B C E F
Virtual Organisation Principles A D B C E F
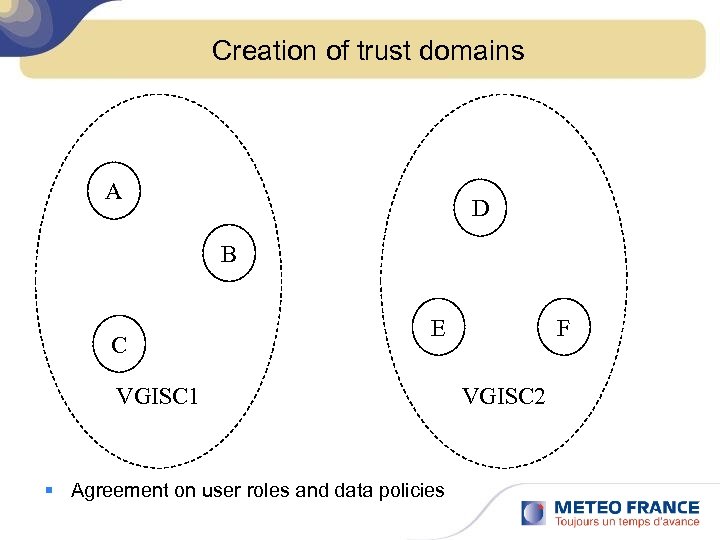 Creation of trust domains A D B C E VGISC 1 § Agreement on user roles and data policies F VGISC 2
Creation of trust domains A D B C E VGISC 1 § Agreement on user roles and data policies F VGISC 2
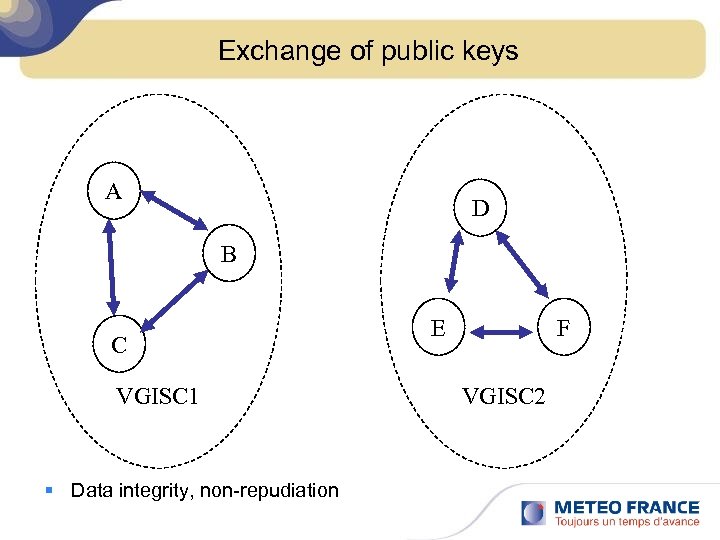 Exchange of public keys A D B C VGISC 1 § Data integrity, non-repudiation E F VGISC 2
Exchange of public keys A D B C VGISC 1 § Data integrity, non-repudiation E F VGISC 2
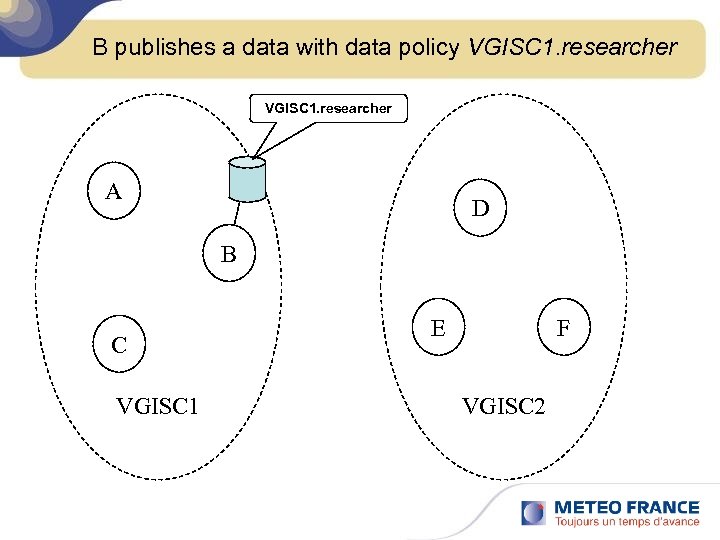 B publishes a data with data policy VGISC 1. researcher A D B C VGISC 1 E F VGISC 2
B publishes a data with data policy VGISC 1. researcher A D B C VGISC 1 E F VGISC 2
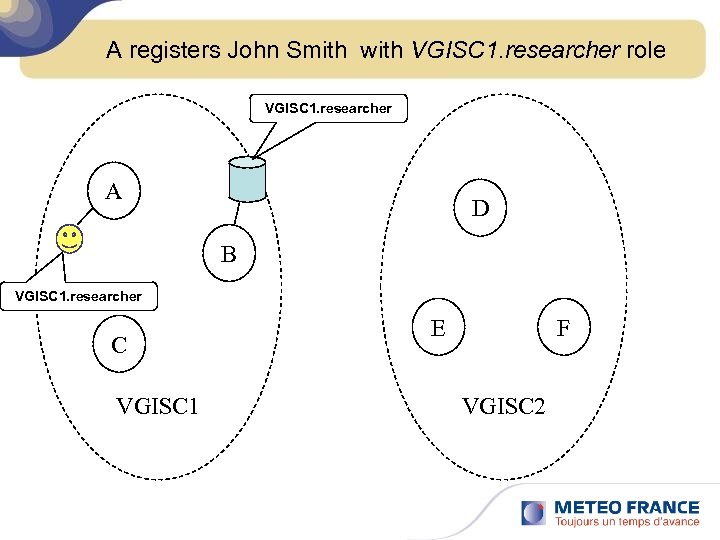 A registers John Smith with VGISC 1. researcher role VGISC 1. researcher A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
A registers John Smith with VGISC 1. researcher role VGISC 1. researcher A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
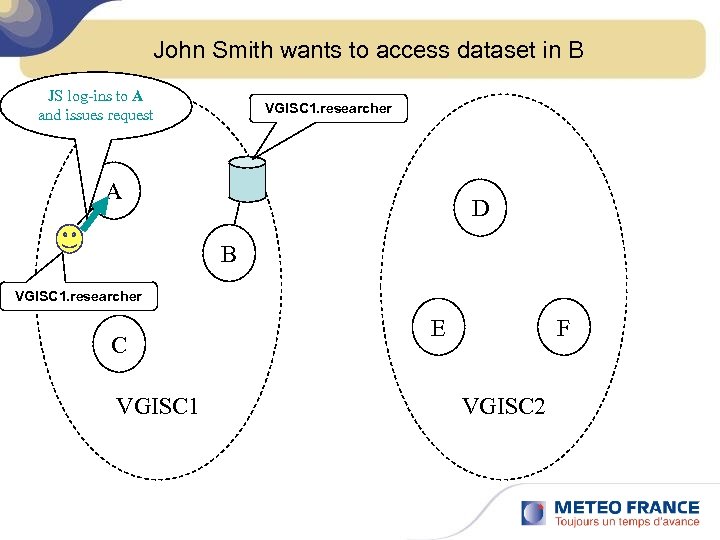 John Smith wants to access dataset in B JS log-ins to A and issues request VGISC 1. researcher A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
John Smith wants to access dataset in B JS log-ins to A and issues request VGISC 1. researcher A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
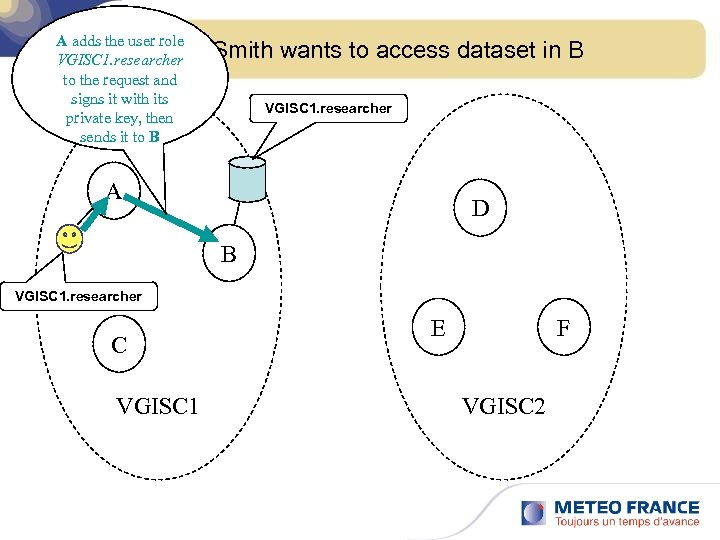 A adds the user role John VGISC 1. researcher to the request and signs it with its private key, then sends it to B Smith wants to access dataset in B VGISC 1. researcher A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
A adds the user role John VGISC 1. researcher to the request and signs it with its private key, then sends it to B Smith wants to access dataset in B VGISC 1. researcher A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
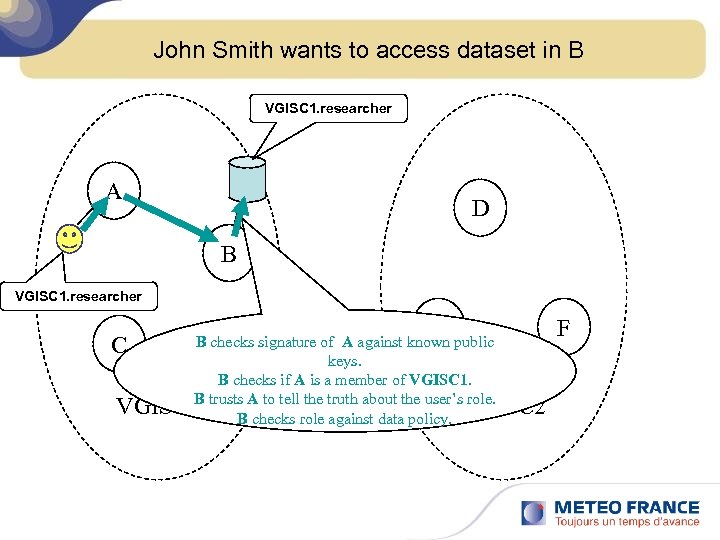 John Smith wants to access dataset in B VGISC 1. researcher A D B VGISC 1. researcher E B checks signature of A against known public C keys. B checks if A is a member of VGISC 1. B the role. VGISC 1 trusts A to tellrole truth about the user’s. VGISC 2 B checks against data policy. F
John Smith wants to access dataset in B VGISC 1. researcher A D B VGISC 1. researcher E B checks signature of A against known public C keys. B checks if A is a member of VGISC 1. B the role. VGISC 1 trusts A to tellrole truth about the user’s. VGISC 2 B checks against data policy. F
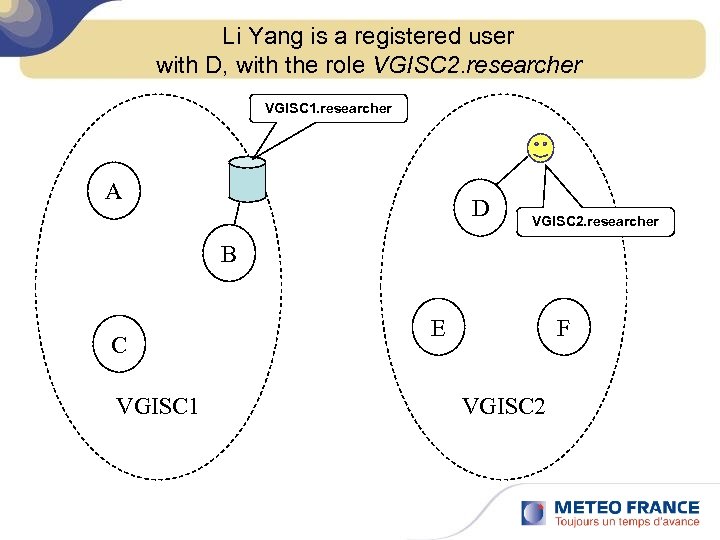 Li Yang is a registered user with D, with the role VGISC 2. researcher VGISC 1. researcher A D VGISC 2. researcher B C VGISC 1 E F VGISC 2
Li Yang is a registered user with D, with the role VGISC 2. researcher VGISC 1. researcher A D VGISC 2. researcher B C VGISC 1 E F VGISC 2
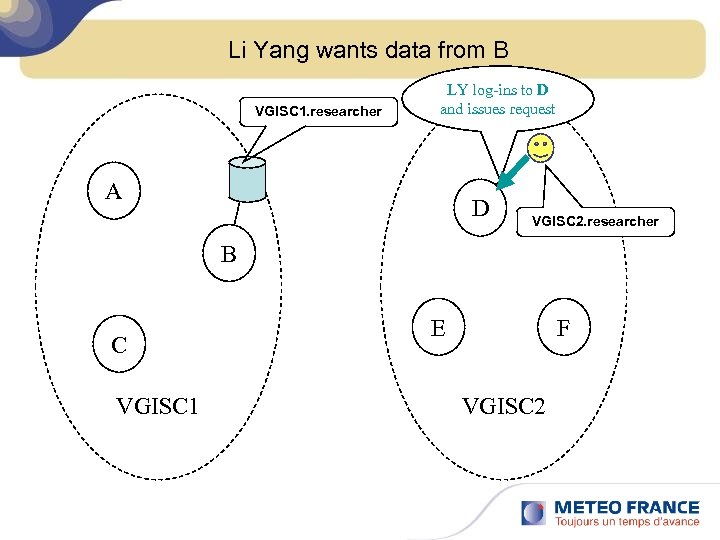 Li Yang wants data from B VGISC 1. researcher LY log-ins to D and issues request A D VGISC 2. researcher B C VGISC 1 E F VGISC 2
Li Yang wants data from B VGISC 1. researcher LY log-ins to D and issues request A D VGISC 2. researcher B C VGISC 1 E F VGISC 2
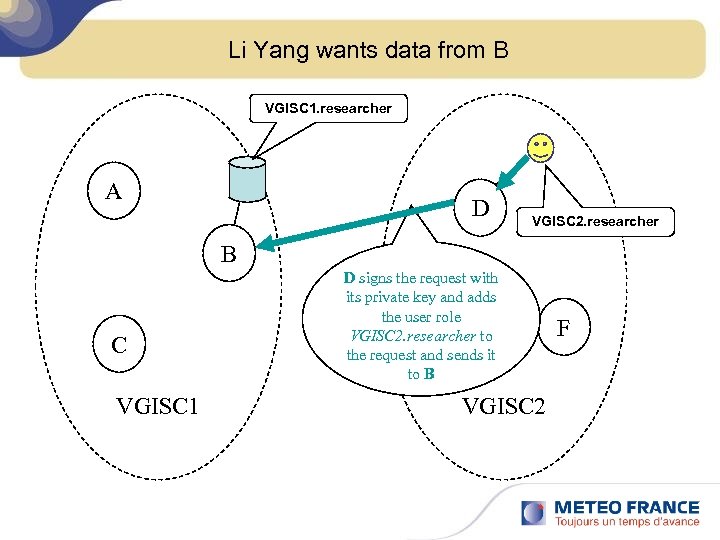 Li Yang wants data from B VGISC 1. researcher A D VGISC 2. researcher B C VGISC 1 D signs the request with its private key and adds the user role E VGISC 2. researcher to the request and sends it to B VGISC 2 F
Li Yang wants data from B VGISC 1. researcher A D VGISC 2. researcher B C VGISC 1 D signs the request with its private key and adds the user role E VGISC 2. researcher to the request and sends it to B VGISC 2 F
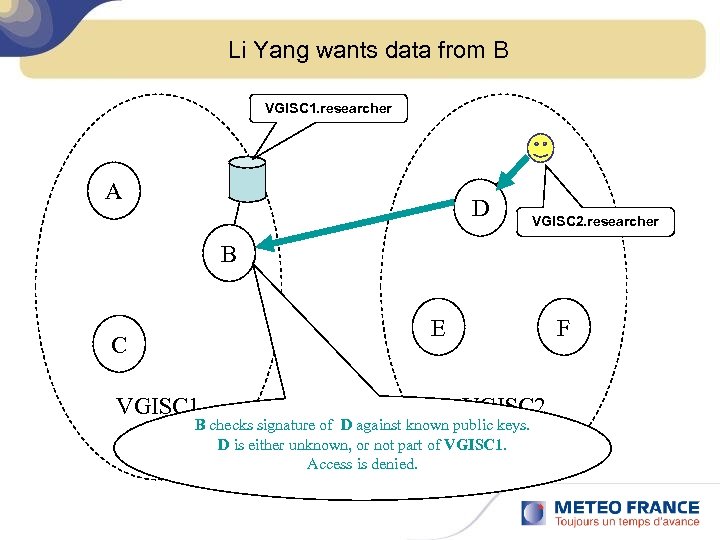 Li Yang wants data from B VGISC 1. researcher A D VGISC 2. researcher B E C VGISC 1 F VGISC 2 B checks signature of D against known public keys. D is either unknown, or not part of VGISC 1. Access is denied.
Li Yang wants data from B VGISC 1. researcher A D VGISC 2. researcher B E C VGISC 1 F VGISC 2 B checks signature of D against known public keys. D is either unknown, or not part of VGISC 1. Access is denied.
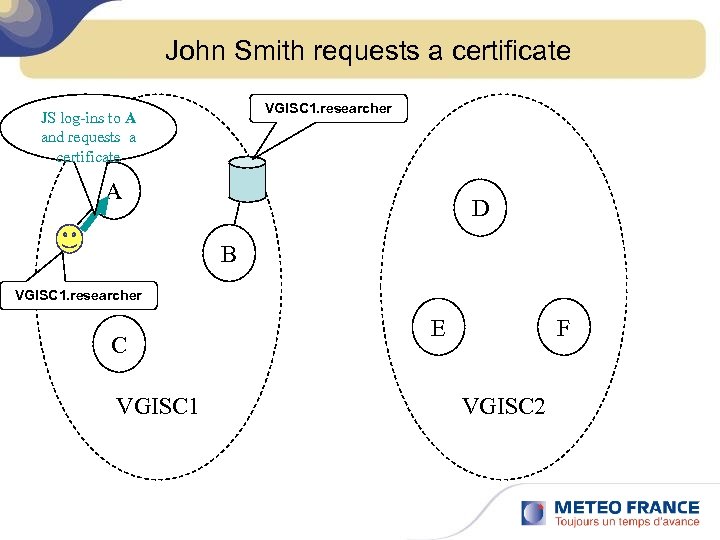 John Smith requests a certificate VGISC 1. researcher JS log-ins to A and requests a certificate A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
John Smith requests a certificate VGISC 1. researcher JS log-ins to A and requests a certificate A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
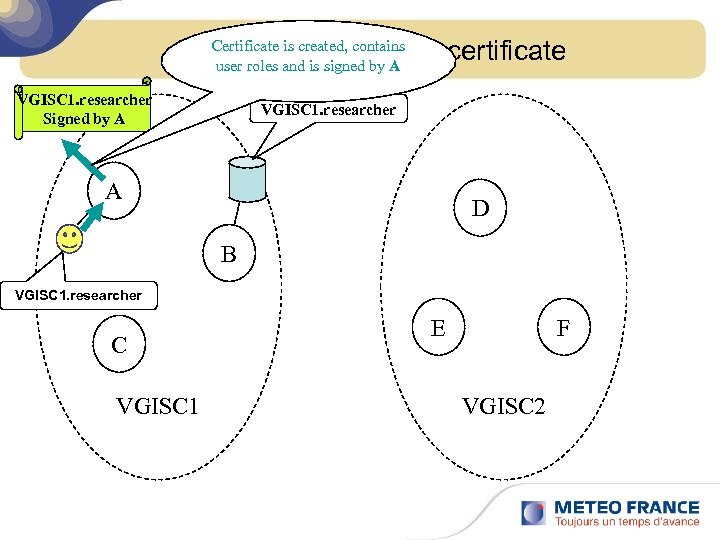 Certificate is created, contains John Smithisexport his certificate user roles and signed by A VGISC 1. researcher Signed by A VGISC 1. researcher A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
Certificate is created, contains John Smithisexport his certificate user roles and signed by A VGISC 1. researcher Signed by A VGISC 1. researcher A D B VGISC 1. researcher C VGISC 1 E F VGISC 2
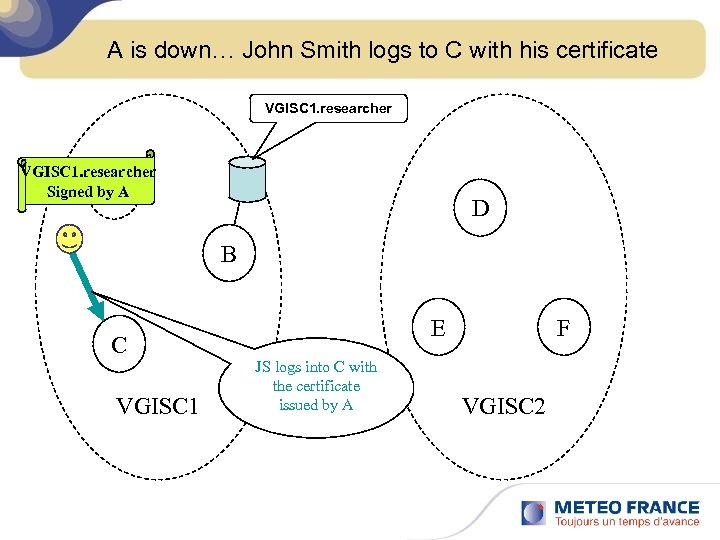 A is down… John Smith logs to C with his certificate VGISC 1. researcher Signed by A A D B C VGISC 1 E JS logs into C with the certificate issued by A F VGISC 2
A is down… John Smith logs to C with his certificate VGISC 1. researcher Signed by A A D B C VGISC 1 E JS logs into C with the certificate issued by A F VGISC 2
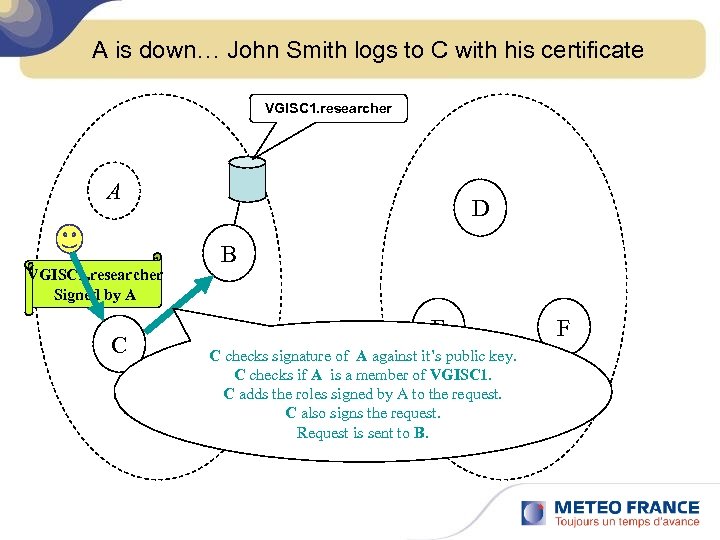 A is down… John Smith logs to C with his certificate VGISC 1. researcher A VGISC 1. researcher Signed by A C VGISC 1 D B E C checks signature of A against it’s public key. C checks if A is a member of VGISC 1. C adds the roles signed by A to the request. C also signs the request. VGISC 2 Request is sent to B. F
A is down… John Smith logs to C with his certificate VGISC 1. researcher A VGISC 1. researcher Signed by A C VGISC 1 D B E C checks signature of A against it’s public key. C checks if A is a member of VGISC 1. C adds the roles signed by A to the request. C also signs the request. VGISC 2 Request is sent to B. F
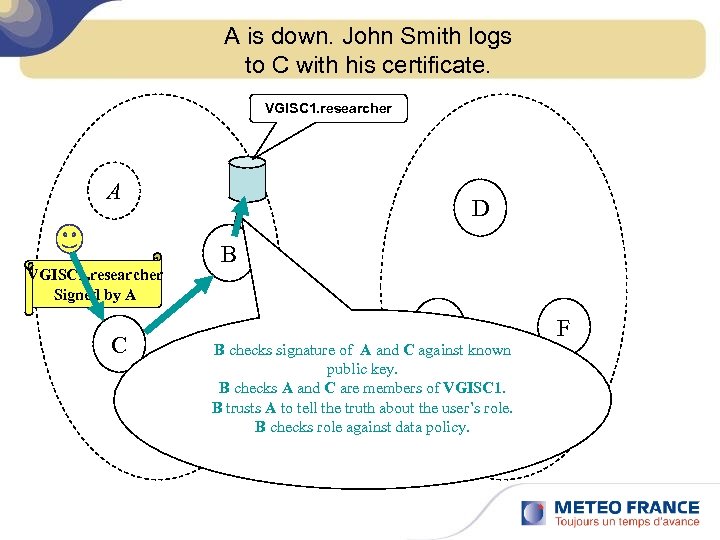 A is down. John Smith logs to C with his certificate. VGISC 1. researcher A VGISC 1. researcher Signed by A C VGISC 1 D B E B checks signature of A and C against known public key. B checks A and C are members of VGISC 1. B trusts A to tell the truth about the user’s role. VGISC 2 B checks role against data policy. F
A is down. John Smith logs to C with his certificate. VGISC 1. researcher A VGISC 1. researcher Signed by A C VGISC 1 D B E B checks signature of A and C against known public key. B checks A and C are members of VGISC 1. B trusts A to tell the truth about the user’s role. VGISC 2 B checks role against data policy. F
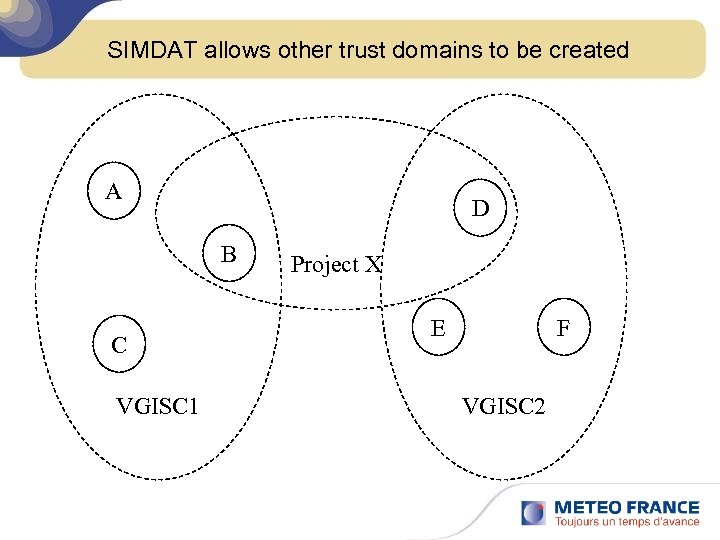 SIMDAT allows other trust domains to be created A D B C VGISC 1 Project X E F VGISC 2
SIMDAT allows other trust domains to be created A D B C VGISC 1 Project X E F VGISC 2
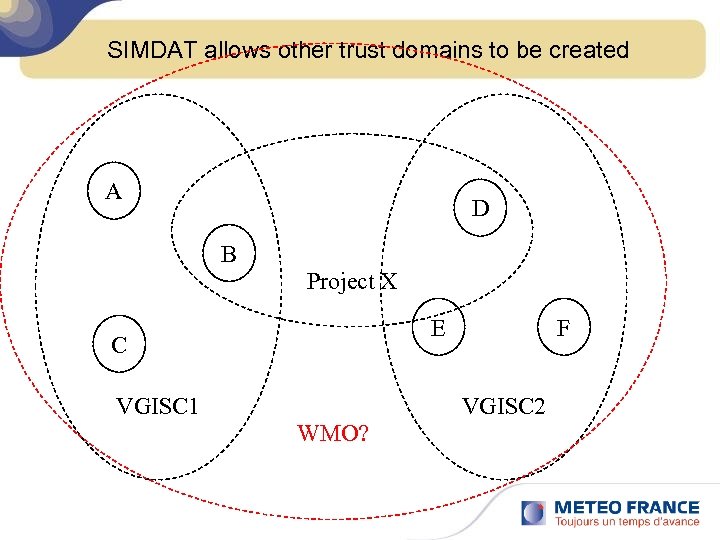 SIMDAT allows other trust domains to be created A D B Project X E C VGISC 1 WMO? F VGISC 2
SIMDAT allows other trust domains to be created A D B Project X E C VGISC 1 WMO? F VGISC 2
 Development status Development of the Domain Authority: Authorization Engine – Support for Domains • X 509 Certificates used to check exchanged messages and security tokens [use of a PKI with several CAs] – Support for Attribute Certificates containing the user’s roles • SAML Tokens • Support for data policies qualifying the datasets. They have two components domain. policy – Development of a user database on each nodes to locally manage the users and roles • User’s only known at DWD will access some datasets at Meteo-France
Development status Development of the Domain Authority: Authorization Engine – Support for Domains • X 509 Certificates used to check exchanged messages and security tokens [use of a PKI with several CAs] – Support for Attribute Certificates containing the user’s roles • SAML Tokens • Support for data policies qualifying the datasets. They have two components domain. policy – Development of a user database on each nodes to locally manage the users and roles • User’s only known at DWD will access some datasets at Meteo-France
 Development status § Development of tools to manage the VO – Web Admin Interface for the Node • • Create/delete domain, Add/remove domain member Import domain member’s certificates in Add/Create User, Add/Remove User’s Roles – Development of command-line tools offering the same services as the web interface § Use of NTP to synchronize all the Catalogue Nodes – To always deliver valid SAML tokens
Development status § Development of tools to manage the VO – Web Admin Interface for the Node • • Create/delete domain, Add/remove domain member Import domain member’s certificates in Add/Create User, Add/Remove User’s Roles – Development of command-line tools offering the same services as the web interface § Use of NTP to synchronize all the Catalogue Nodes – To always deliver valid SAML tokens
 Conclusion § There is a need to have different Authorization schemes – Some datasets will be accessible once the terms and conditions have been accepted • Fairly weak security: user will self-register, • The portal automatically associates some roles to the user once the user has agreed to the terms and conditions – Some datasets have to be very well protected and only accessible to a number of registered users • High level of security: An admin will register the users and associate roles to these users § There might be a need to support several Authz Token formats
Conclusion § There is a need to have different Authorization schemes – Some datasets will be accessible once the terms and conditions have been accepted • Fairly weak security: user will self-register, • The portal automatically associates some roles to the user once the user has agreed to the terms and conditions – Some datasets have to be very well protected and only accessible to a number of registered users • High level of security: An admin will register the users and associate roles to these users § There might be a need to support several Authz Token formats


