3690f397caa59b5ba40f25cc652642d5.ppt
- Количество слайдов: 37

Sigurnost IT resursa nove generacije Dalibor Ratković dalibor. ratkovic@telegroup. ba Tele. Group 03. 11. 2010. god.

Agenda • Današnja situacija na polju IT sigurnosti • Mehanizmi zaštite • Praktična riješenja • Pitanja i odgovori • Demonstracija i pilot projekti kod korisnika Slide 2

Rizici kojima ste izloženi • Prekid poslovnih aktivnosti • Gubitak produktivnosti • Krađa informacija • Odgovornost za nastalu situaciju • Narušena reputacija i gubitak povjerenja kod korisnika Slide 3

Upravljanje procesom sigurnosti • 99% organizacija je prijavilo incident iako su imali antivirusnu zaštitu i firewall sisteme • Potrebno je izvršiti zaštitu od svih mogućih prijetnji Slide 4
Kreatori čuvenih virusa • Profil: – Muškarci – Između 14 i 34 godine – Bez djevojke – BEZ KOMERCIJALNOG INTERESA !!!! Slide 5
Današnja realnost • According to investigators, in 2003, a student of Balakov Institute of Engineering, Technology and Management, Ivan Maksakov, 22, developed a few knowbots and set up a network of hackers. The bots initiated Do. Sattacks on the web-sites of bookmakers, which were accepting stakes in the Internet. Slide 6

Organizovane kriminalne grupe Slide 7

Phishing • Andrew Schwarmkoff • Connection to the russian Mafia • Phishing of Creditcard-Numbers • „The Phisher-King“ Slide 8

Koliko je velika malware industrija? The FBI claims financial loss from spyware and other computer-related crimes have cost U. S. businesses $62 Billion in 2005 26, 150 unique phishing variations counted in August 2006 by the Anti. Phishing Working Group Costs of goods and services in cybercrime forums: $1000 – $5000: Trojan program, which could steal online account information $ 500: Credit Card Number with PIN $80 -$300: Change of billing data, including account number, billing adress, Social Security number, home adress and birth date $150: Driver‘s licence $150: Birth certificate $100: Social Security Card $7 - $25: Credit card number with security code and expiration date. $7: Paypal account log-on and password Slide 9
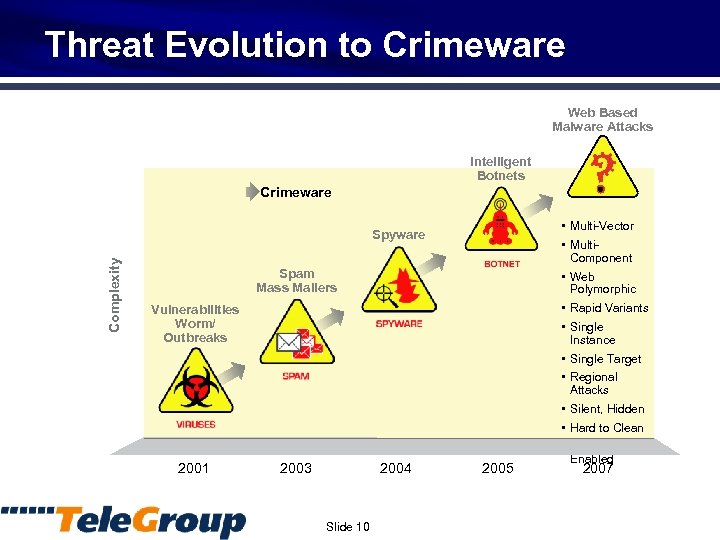
Threat Evolution to Crimeware Web Based Malware Attacks Intelligent Botnets Crimeware Complexity Spyware Spam Mass Mailers Vulnerabilities Worm/ Outbreaks 2001 2003 2004 Slide 10 2005 • Multi-Vector • Multi. Component • Web Polymorphic • Rapid Variants • Single Instance • Single Target • Regional Attacks • Silent, Hidden • Hard to Clean • Botnet Enabled 2007
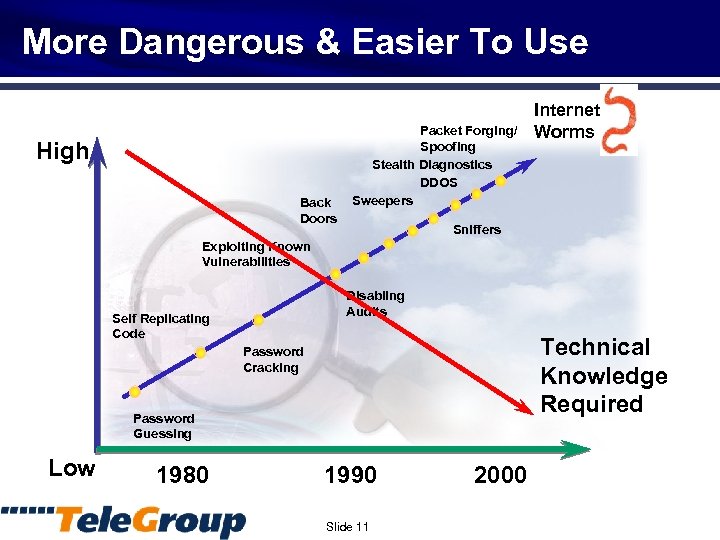
More Dangerous & Easier To Use High Back Doors Packet Forging/ Spoofing Stealth Diagnostics DDOS Sweepers Internet Worms Sniffers Exploiting Known Vulnerabilities Disabling Audits Self Replicating Code Technical Knowledge Required Password Cracking Password Guessing Low 1980 1990 Slide 11 2000

Sadašnja Situacija • 22, 000 new malware samples per day, a network worm breakout and the sandboxenabled antivirus • Nearly 30, 000 Malicious Web Sites Appear Each Day Slide 12

Međunarodni standardi • Financial Services Regulations Ø Basel II – Global Ø Gramm-Leach-Bliley Act (GLBA) – US Ø Payment Card Industry (PCI) Security Standard – Global • Industrijski standardi Ø BS ISO/IEC 27002 Compliance - Global Ø Cobi. T - Global Ø Data Protection Act (DPA) - UK Slide 13

Metodologija zaštite u IP mrežama Slide 14
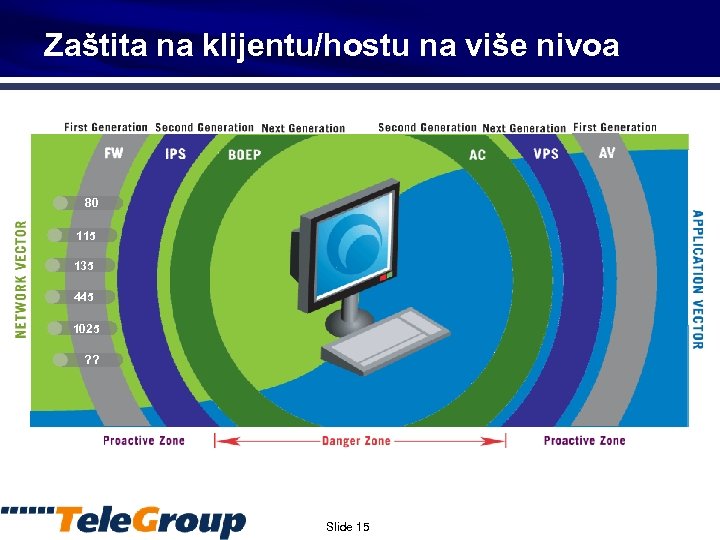
Zaštita na klijentu/hostu na više nivoa 80 115 135 445 1025 ? ? Slide 15
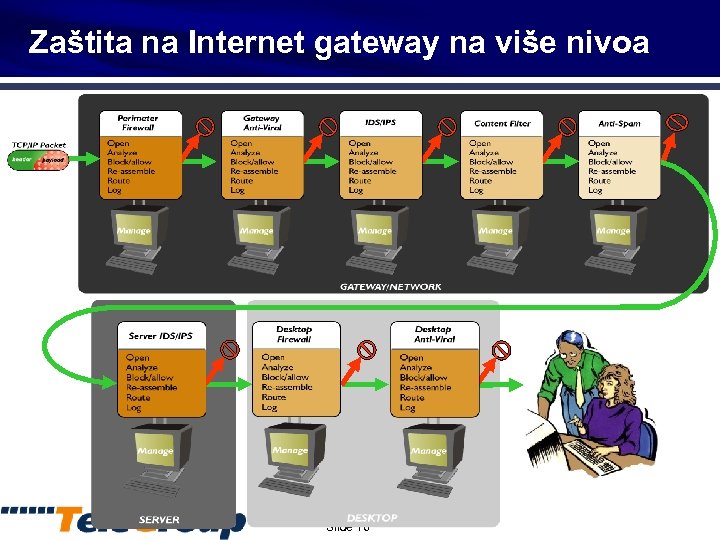
Zaštita na Internet gateway na više nivoa Slide 16
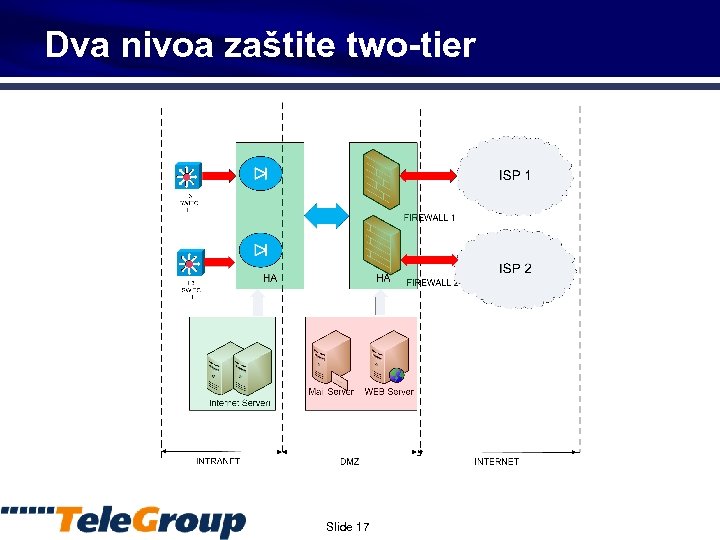
Dva nivoa zaštite two-tier Slide 17

RIješenja 1 • Firewall • IPS/IDS sitemi • Content Monitoring/Filtering • Antivirus na hostovima, mail box i na nivou GW • Antispam zaštita • Endpoint security • WAF • SSL VPN Slide 18

RIješenja 2 • Data Leakage Prevention • Encryption/PKI/Digital Certificates • Identity & Access Management (NAC) • Patch Management • Penetration Testing/Risk & Vulnerability Assessment • Log and Event Management Platform • Database Security • IT Forensics Slide 19

Partneri Telegroupa Slide 20

Partneri Slide 21

Content Monitoring/Filtering • Kontrola Internet pristupa kao značajnog elementa u poslovanju • Privatno korištenje Interneta narušava poslovne aplikacije – 30 -40% saobraćaja ne koristi se u poslovne svrhe – P 2 P programi, Instat Messanger, Skype, Kaaza. . . • 30% od ukupnog broja zaposlenih šalju povjerljive informacije slučajno ili namjerno Slide 22
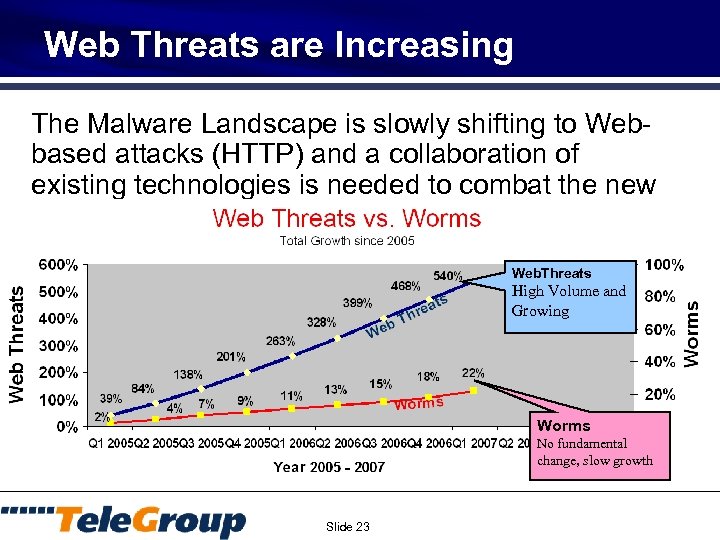
Web Threats are Increasing The Malware Landscape is slowly shifting to Webbased attacks (HTTP) and a collaboration of existing technologies is needed to combat the new wave of malware threats Web. Threats High Volume and Growing Worms No fundamental change, slow growth Slide 23
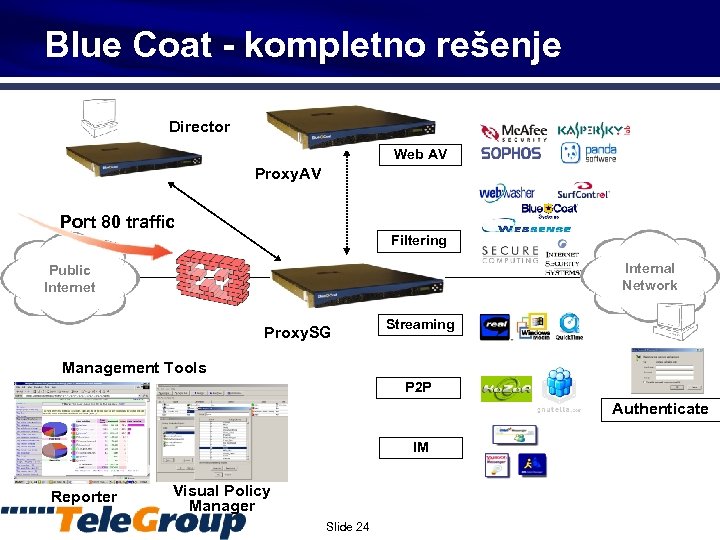
Blue Coat - kompletno rešenje Director Web AV Proxy. AV Port 80 traffic Filtering Internal Network Public Internet Proxy. SG Streaming Management Tools P 2 P Authenticate IM Reporter Visual Policy Manager Slide 24
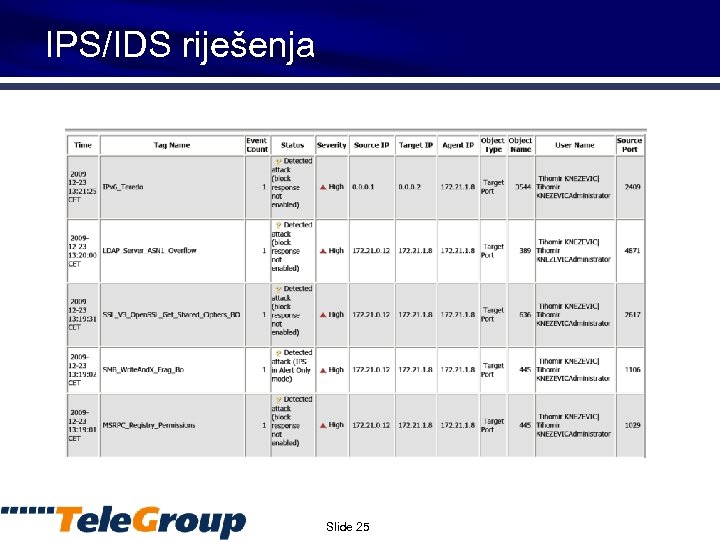
IPS/IDS riješenja Slide 25
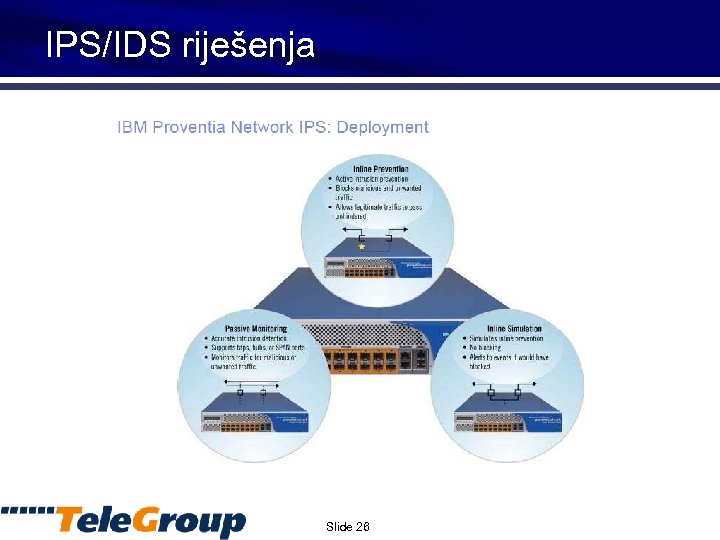
IPS/IDS riješenja Slide 26
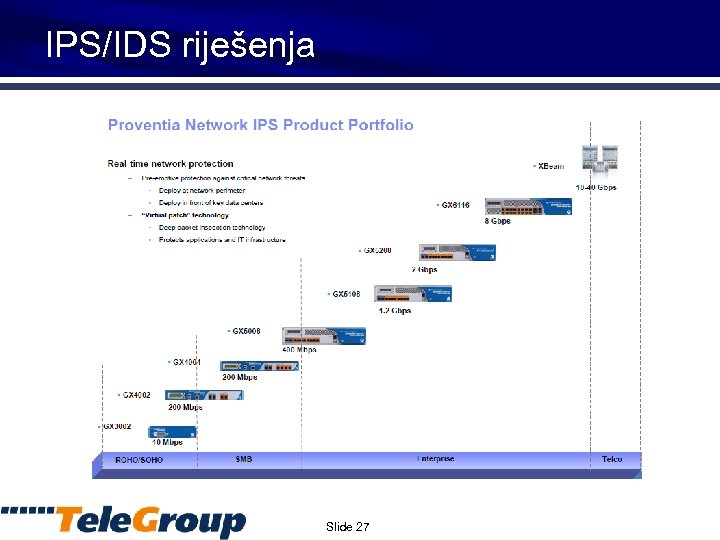
IPS/IDS riješenja Slide 27

End. Point Security Know your environment § Vulnerability assessment and network discovery Manage Known Risk § Through effective patch management Manage Unknown Threats § Through white list based application control Prevent data leakage § White list based peripheral device management § Secure data in transit Secure mobile devices § Disk encryption with boot protection § Protection for mobile devices Slide 28
Lumension Device Control § Enables only authorized removable (peripheral) devices to connect to network, laptop, thin client, laptop and desktop § Reduces risk of data theft, data leakage and malware introduction via unauthorized removable media § Assures and proves compliance with the landslide of regulations governing privacy and accountability Slide 29
Blue Coat Visibility • Packet. Shaper – Install onto network (inline or out) – Auto. Discover & measure • Classify – Find all applications on network – See hard to find - P 2 P, Skype, You. Tube, i. Tunes, Flash TV – Break down Enterprise applications SAP, Citrix, Microsoft • Measure – Utilization – Response times – 120+ stats Slide 30
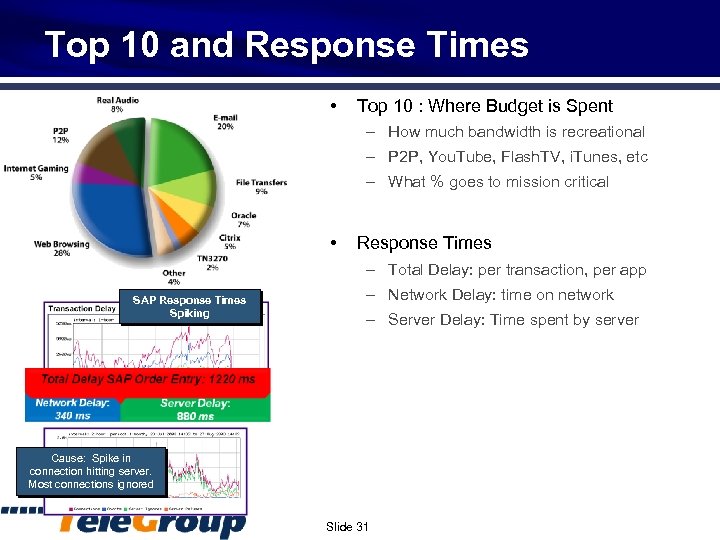
Top 10 and Response Times • Top 10 : Where Budget is Spent – How much bandwidth is recreational – P 2 P, You. Tube, Flash. TV, i. Tunes, etc – What % goes to mission critical • Response Times – Total Delay: per transaction, per app SAP Response Times Spiking – Network Delay: time on network – Server Delay: Time spent by server Cause: Spike in connection hitting server. Most connections ignored Slide 31
Packet. Shaper • Visibility – All Applications – Real Time Voice MOS • Granular QOS – Per App, User, Call – Intelligent MPLS – Real Time Optimization • Compression – Diskless – 2 x-4 x Capacity Gain 32 Slide 32

Reference • Telekom Srpske • Uprava za Indirektno oprezivanje, MUP RS • Klinički Centar • Univerzitet Apeiron, Slobomir Univerzitet, Statistički zavod RS, HET • Vlada Brčko distrikta • Volks. Banka, Komercijalna Banka • Nova Banka • Balkan Investment Banka • Pavlović Banka • Bobar Banka Slide 33
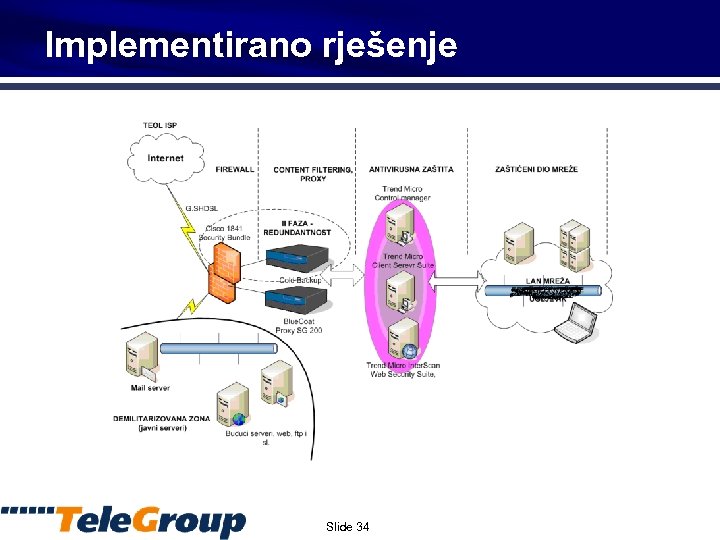
Implementirano rješenje Slide 34
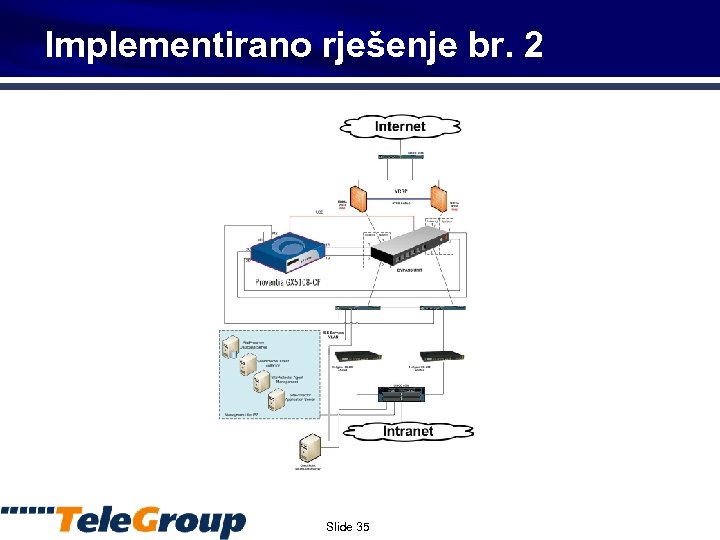
Implementirano rješenje br. 2 Slide 35

Implementirano rješenje br. 2 Slide 36

Pitanja i odgovori! Tele. Group Marije Bursać 8 78000 Banja Luka, Republika Srpska, Bi. H +387 51 321 000 http: //www. telegroup-bih. com
3690f397caa59b5ba40f25cc652642d5.ppt