c5a53352b11bad39b660368d227b3e41.ppt
- Количество слайдов: 20
 Signed Class. Ads and Restricted Delegation Ian D. Alderman Computer Sciences Department University of Wisconsin-Madison alderman@cs. wisc. edu http: //www. cs. wisc. edu/condor Condor Week 2007
Signed Class. Ads and Restricted Delegation Ian D. Alderman Computer Sciences Department University of Wisconsin-Madison alderman@cs. wisc. edu http: //www. cs. wisc. edu/condor Condor Week 2007
 Condor Week 2007 www. cs. wisc. edu/condor 2
Condor Week 2007 www. cs. wisc. edu/condor 2
 Security Issues in Multiple Administrative Domains › Multiple administrative domains aren’t well › protected from each other, yet are increasingly common: Condor-C, Condor-G, flocking… As cooperation between administrative domains increases, so does utilization. Can we take advantage of this without also increasing risk? Protect: Condor Week 2007 Job input and output data Execute Machines Data unrelated to the job www. cs. wisc. edu/condor 3
Security Issues in Multiple Administrative Domains › Multiple administrative domains aren’t well › protected from each other, yet are increasingly common: Condor-C, Condor-G, flocking… As cooperation between administrative domains increases, so does utilization. Can we take advantage of this without also increasing risk? Protect: Condor Week 2007 Job input and output data Execute Machines Data unrelated to the job www. cs. wisc. edu/condor 3
 Shoulders of Giants Principle of least privilege: “Every program and every user of the system should operate using the least set of privileges necessary to complete the job. ” - Saltzer and Schroeder, 1975 Condor Week 2007 www. cs. wisc. edu/condor 4
Shoulders of Giants Principle of least privilege: “Every program and every user of the system should operate using the least set of privileges necessary to complete the job. ” - Saltzer and Schroeder, 1975 Condor Week 2007 www. cs. wisc. edu/condor 4
 Credential Scope › Jobs either carry no credentials or the full › › credentials of the submitting user. Jobs with credentials can impersonate the submitting user without any restriction. Intermediaries that handle credentials can lose or abuse them, or alter tasks, input, and results. Limit the scope of credentials to what the job needs and no more. Condor Week 2007 www. cs. wisc. edu/condor 5
Credential Scope › Jobs either carry no credentials or the full › › credentials of the submitting user. Jobs with credentials can impersonate the submitting user without any restriction. Intermediaries that handle credentials can lose or abuse them, or alter tasks, input, and results. Limit the scope of credentials to what the job needs and no more. Condor Week 2007 www. cs. wisc. edu/condor 5
 Goals › Make security assumptions explicit. › Reduce the number and scope of › › assumptions that must be made about infrastructure w. r. t. security. Provide end-to-end security options in addition to point-to-point security. Provide end-to-end cryptographic audit. Alter attacker incentives. Reduce barriers to increased cooperation and utilization. Condor Week 2007 www. cs. wisc. edu/condor 6
Goals › Make security assumptions explicit. › Reduce the number and scope of › › assumptions that must be made about infrastructure w. r. t. security. Provide end-to-end security options in addition to point-to-point security. Provide end-to-end cryptographic audit. Alter attacker incentives. Reduce barriers to increased cooperation and utilization. Condor Week 2007 www. cs. wisc. edu/condor 6
 Condor Week 2007 www. cs. wisc. edu/condor 7
Condor Week 2007 www. cs. wisc. edu/condor 7
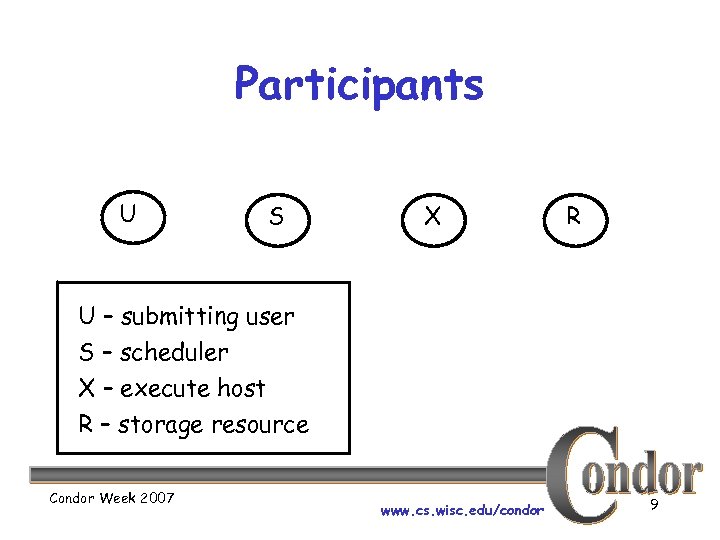 Participants U S X R U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 www. cs. wisc. edu/condor 9
Participants U S X R U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 www. cs. wisc. edu/condor 9
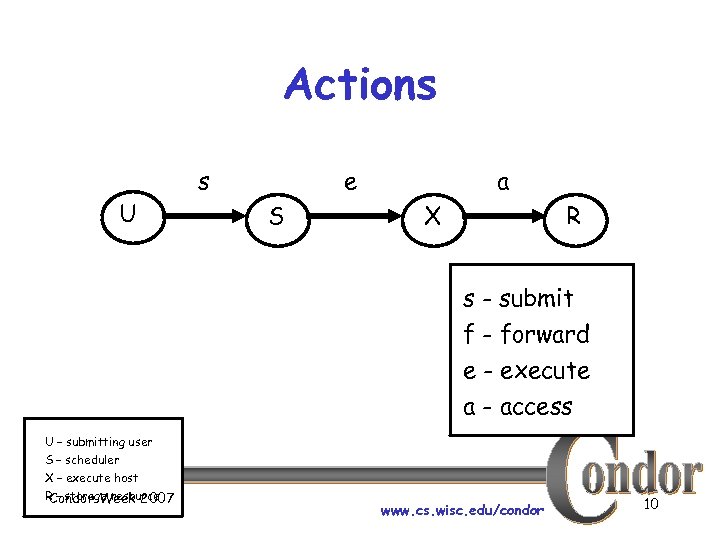 Actions s U e S a X R s - submit f - forward e - execute a - access U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 www. cs. wisc. edu/condor 10
Actions s U e S a X R s - submit f - forward e - execute a - access U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 www. cs. wisc. edu/condor 10
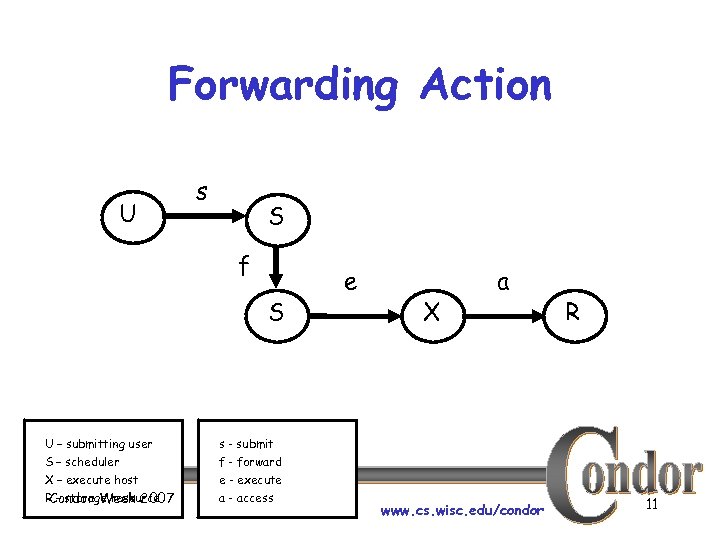 Forwarding Action U s S f S U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 s - submit f - forward e - execute a - access e X a www. cs. wisc. edu/condor R 11
Forwarding Action U s S f S U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 s - submit f - forward e - execute a - access e X a www. cs. wisc. edu/condor R 11
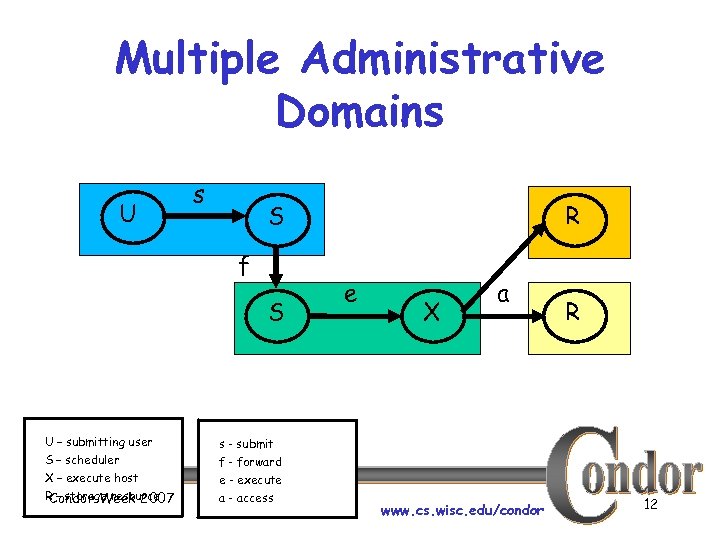 Multiple Administrative Domains U s f S U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 R S s - submit f - forward e - execute a - access e X a www. cs. wisc. edu/condor R 12
Multiple Administrative Domains U s f S U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 R S s - submit f - forward e - execute a - access e X a www. cs. wisc. edu/condor R 12
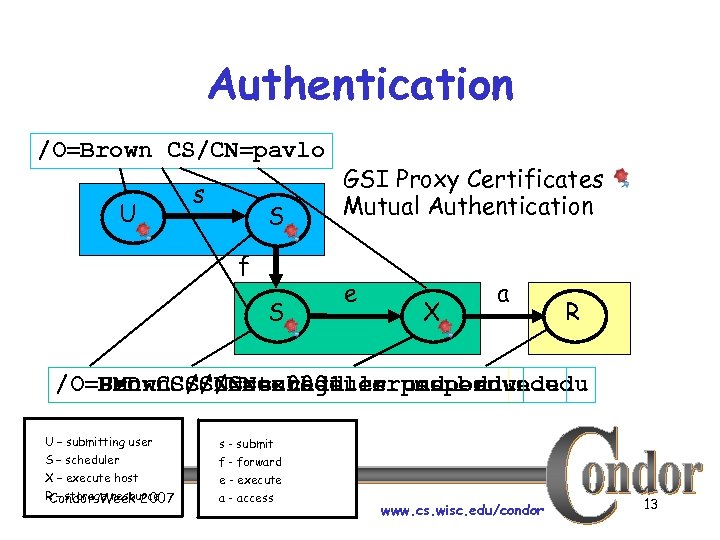 Authentication /O=Brown CS/CN=pavlo U s S f S GSI Proxy Certificates Mutual Authentication e X a R /O=UMD CS/CN=scheduler. cs. penn. edu /O=Penn. CS/CN=storage. cs. umd. edu /O=Brown. CS/CN=ex 0001. cs. penn. edu CS/CN=scheduler. cs. brown. edu U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 s - submit f - forward e - execute a - access www. cs. wisc. edu/condor 13
Authentication /O=Brown CS/CN=pavlo U s S f S GSI Proxy Certificates Mutual Authentication e X a R /O=UMD CS/CN=scheduler. cs. penn. edu /O=Penn. CS/CN=storage. cs. umd. edu /O=Brown. CS/CN=ex 0001. cs. penn. edu CS/CN=scheduler. cs. brown. edu U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 s - submit f - forward e - execute a - access www. cs. wisc. edu/condor 13
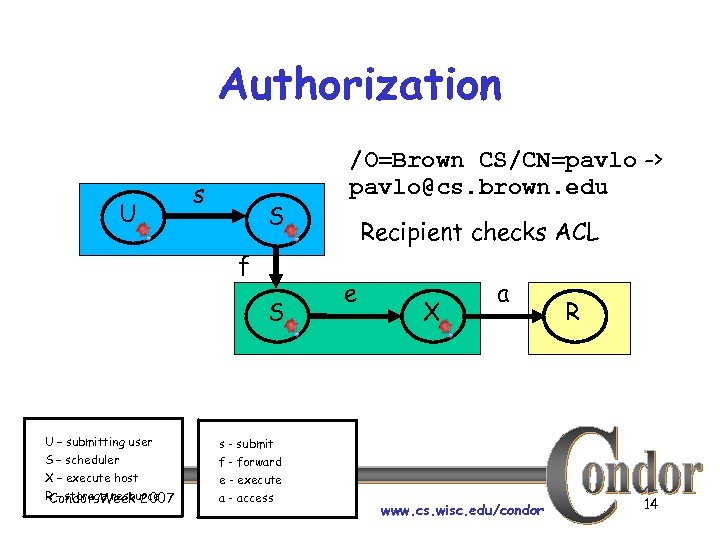 Authorization U s S f S U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 s - submit f - forward e - execute a - access /O=Brown CS/CN=pavlo -> pavlo@cs. brown. edu Recipient checks ACL e X a www. cs. wisc. edu/condor R 14
Authorization U s S f S U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 s - submit f - forward e - execute a - access /O=Brown CS/CN=pavlo -> pavlo@cs. brown. edu Recipient checks ACL e X a www. cs. wisc. edu/condor R 14
 Problems › Authorization entirely in the hands of the › › › recipients: no restrictions can be expressed by the submitter. Credential too permissive: can be used to access anything on resources, run any job on execute machine. Unnecessary reliance on schedulers to preserve confidentiality and integrity of credentials. No audit trail. Condor Week 2007 www. cs. wisc. edu/condor 15
Problems › Authorization entirely in the hands of the › › › recipients: no restrictions can be expressed by the submitter. Credential too permissive: can be used to access anything on resources, run any job on execute machine. Unnecessary reliance on schedulers to preserve confidentiality and integrity of credentials. No audit trail. Condor Week 2007 www. cs. wisc. edu/condor 15
 Attackers › Incentive to attack schedulers; compromise results in full control: ∘ Alter tasks (to attack execute hosts or cause them to attack external hosts). ∘ Access resources using credentials. ∘ Forge results returned to submitter. Condor Week 2007 www. cs. wisc. edu/condor 16
Attackers › Incentive to attack schedulers; compromise results in full control: ∘ Alter tasks (to attack execute hosts or cause them to attack external hosts). ∘ Access resources using credentials. ∘ Forge results returned to submitter. Condor Week 2007 www. cs. wisc. edu/condor 16
 Signed Class. Ads › Class. Ads with digital signatures. › Signature made and checked using X. 509 keys and certificates. › Altered Class. Ads are easily detected. › External files can be referenced using checksums. › Explicit association between a task and information about its origin and provenance. › Results can be signed as well: receipts. Condor Week 2007 www. cs. wisc. edu/condor 18
Signed Class. Ads › Class. Ads with digital signatures. › Signature made and checked using X. 509 keys and certificates. › Altered Class. Ads are easily detected. › External files can be referenced using checksums. › Explicit association between a task and information about its origin and provenance. › Results can be signed as well: receipts. Condor Week 2007 www. cs. wisc. edu/condor 18
 Task-specific Proxy TS Certificates › Proxy certificates with embedded signed Class. Ads. › Policy field in proxy certificate contains signed Class. Ad for the associated job. › Proxy delegation chain inalterably linked with particular job. Condor Week 2007 www. cs. wisc. edu/condor 19
Task-specific Proxy TS Certificates › Proxy certificates with embedded signed Class. Ads. › Policy field in proxy certificate contains signed Class. Ad for the associated job. › Proxy delegation chain inalterably linked with particular job. Condor Week 2007 www. cs. wisc. edu/condor 19
 Action Authorization Expressions • Class. Ad language expressions included in the signed Class. Ad. • Can specify conditions on actions that the proxy certificate might be used for: submit, forwarding, execute, and access. • Permits the submitting user to limit how their credentials are used. Condor Week 2007 www. cs. wisc. edu/condor 20
Action Authorization Expressions • Class. Ad language expressions included in the signed Class. Ad. • Can specify conditions on actions that the proxy certificate might be used for: submit, forwarding, execute, and access. • Permits the submitting user to limit how their credentials are used. Condor Week 2007 www. cs. wisc. edu/condor 20
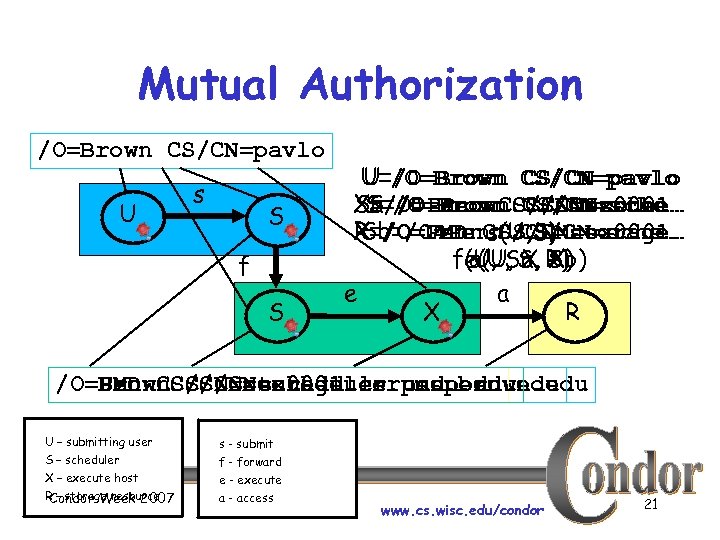 Mutual Authorization /O=Brown CS/CN=pavlo U s S f S U=/O=Brown CS/CN=pavlo S=/O=Brown CS/CN=sche… X=/O=Penn CS/CN=ex 0001… Sa=/O=Brown CS/CN=sche… S=/O=Penn CS/CN=sche… X=/O=Penn. CS/CN=storage… R=/O=UMD s(U, S) Sb=/O=Penn CS/CN=sche… CS/CN=ex 0001… f(U, Sa, R) e(U, S, Sb) a(U, X X) e a X R /O=UMD CS/CN=scheduler. cs. penn. edu /O=Penn. CS/CN=storage. cs. umd. edu /O=Brown. CS/CN=ex 0001. cs. penn. edu CS/CN=scheduler. cs. brown. edu U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 s - submit f - forward e - execute a - access www. cs. wisc. edu/condor 21
Mutual Authorization /O=Brown CS/CN=pavlo U s S f S U=/O=Brown CS/CN=pavlo S=/O=Brown CS/CN=sche… X=/O=Penn CS/CN=ex 0001… Sa=/O=Brown CS/CN=sche… S=/O=Penn CS/CN=sche… X=/O=Penn. CS/CN=storage… R=/O=UMD s(U, S) Sb=/O=Penn CS/CN=sche… CS/CN=ex 0001… f(U, Sa, R) e(U, S, Sb) a(U, X X) e a X R /O=UMD CS/CN=scheduler. cs. penn. edu /O=Penn. CS/CN=storage. cs. umd. edu /O=Brown. CS/CN=ex 0001. cs. penn. edu CS/CN=scheduler. cs. brown. edu U – submitting user S – scheduler X – execute host R – storage resource Condor Week 2007 s - submit f - forward e - execute a - access www. cs. wisc. edu/condor 21
 Questions? For more information, contact: Ian Alderman alderman@cs. wisc. edu Condor Week 2007 www. cs. wisc. edu/condor 22
Questions? For more information, contact: Ian Alderman alderman@cs. wisc. edu Condor Week 2007 www. cs. wisc. edu/condor 22


