6d7fd689473855449460786e547fff1e.ppt
- Количество слайдов: 34
 Sidevõrgud IRT 0020 loeng 8 06. nov. 2006 Avo Ots telekommunikatsiooni õppetool raadio- ja sidetehnika instituut avots@lr. ttu. ee 1
Sidevõrgud IRT 0020 loeng 8 06. nov. 2006 Avo Ots telekommunikatsiooni õppetool raadio- ja sidetehnika instituut avots@lr. ttu. ee 1
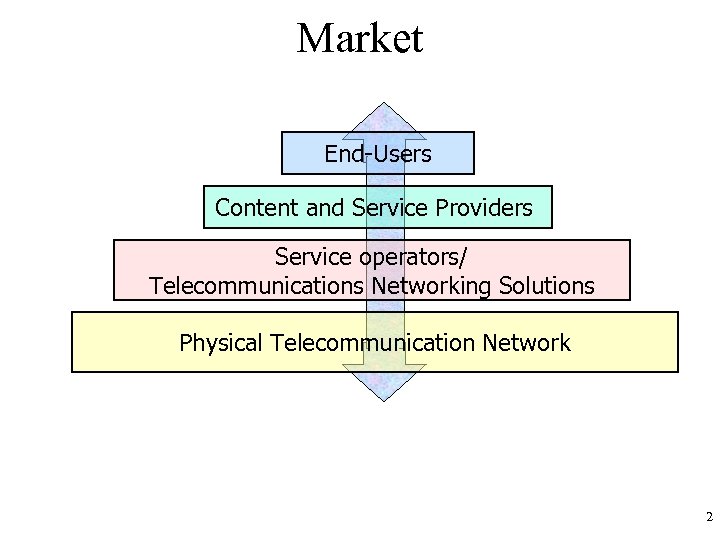 Market End-Users Content and Service Providers Service operators/ Telecommunications Networking Solutions Physical Telecommunication Network 2
Market End-Users Content and Service Providers Service operators/ Telecommunications Networking Solutions Physical Telecommunication Network 2
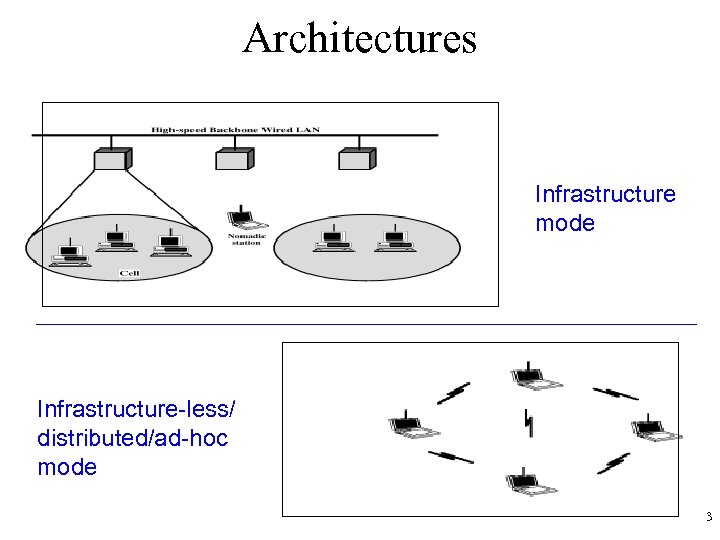 Architectures Infrastructure mode Infrastructure-less/ distributed/ad-hoc mode 3
Architectures Infrastructure mode Infrastructure-less/ distributed/ad-hoc mode 3
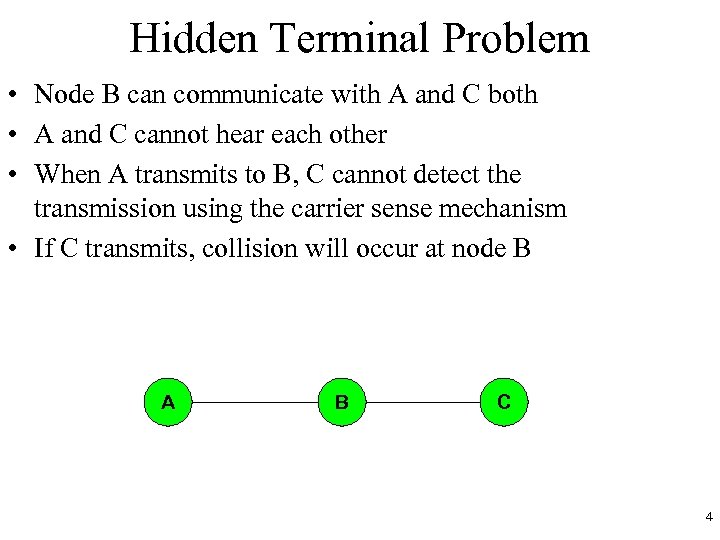 Hidden Terminal Problem • Node B can communicate with A and C both • A and C cannot hear each other • When A transmits to B, C cannot detect the transmission using the carrier sense mechanism • If C transmits, collision will occur at node B A B C 4
Hidden Terminal Problem • Node B can communicate with A and C both • A and C cannot hear each other • When A transmits to B, C cannot detect the transmission using the carrier sense mechanism • If C transmits, collision will occur at node B A B C 4
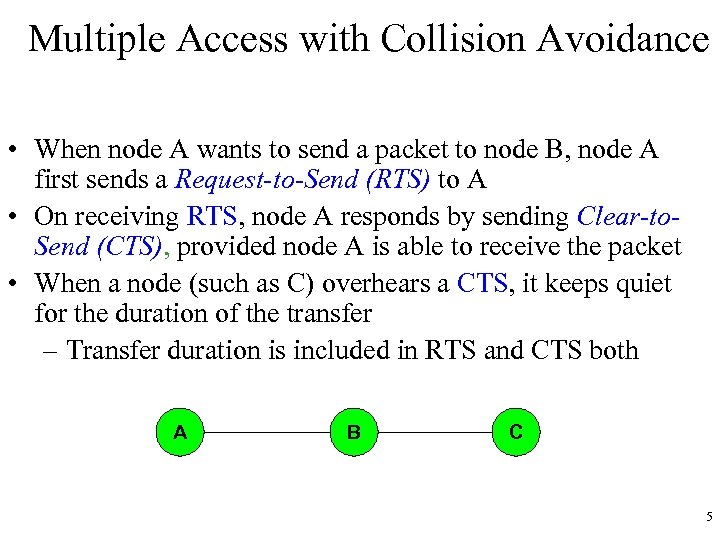 Multiple Access with Collision Avoidance • When node A wants to send a packet to node B, node A first sends a Request-to-Send (RTS) to A • On receiving RTS, node A responds by sending Clear-to. Send (CTS), provided node A is able to receive the packet • When a node (such as C) overhears a CTS, it keeps quiet for the duration of the transfer – Transfer duration is included in RTS and CTS both A B C 5
Multiple Access with Collision Avoidance • When node A wants to send a packet to node B, node A first sends a Request-to-Send (RTS) to A • On receiving RTS, node A responds by sending Clear-to. Send (CTS), provided node A is able to receive the packet • When a node (such as C) overhears a CTS, it keeps quiet for the duration of the transfer – Transfer duration is included in RTS and CTS both A B C 5
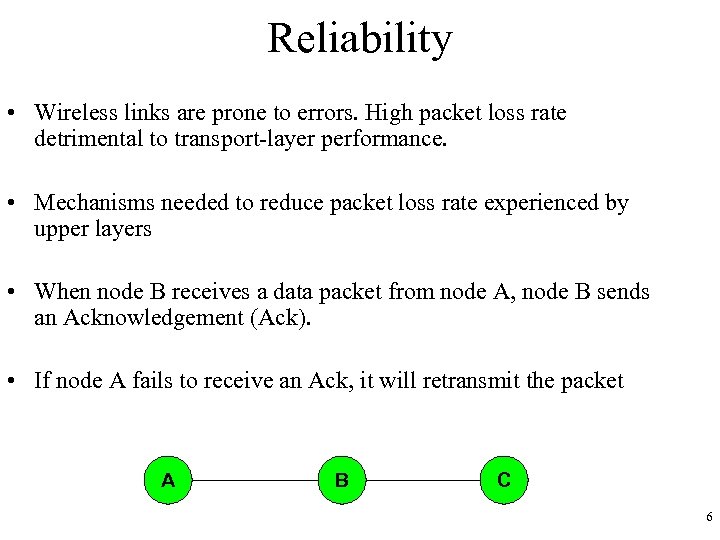 Reliability • Wireless links are prone to errors. High packet loss rate detrimental to transport-layer performance. • Mechanisms needed to reduce packet loss rate experienced by upper layers • When node B receives a data packet from node A, node B sends an Acknowledgement (Ack). • If node A fails to receive an Ack, it will retransmit the packet A B C 6
Reliability • Wireless links are prone to errors. High packet loss rate detrimental to transport-layer performance. • Mechanisms needed to reduce packet loss rate experienced by upper layers • When node B receives a data packet from node A, node B sends an Acknowledgement (Ack). • If node A fails to receive an Ack, it will retransmit the packet A B C 6
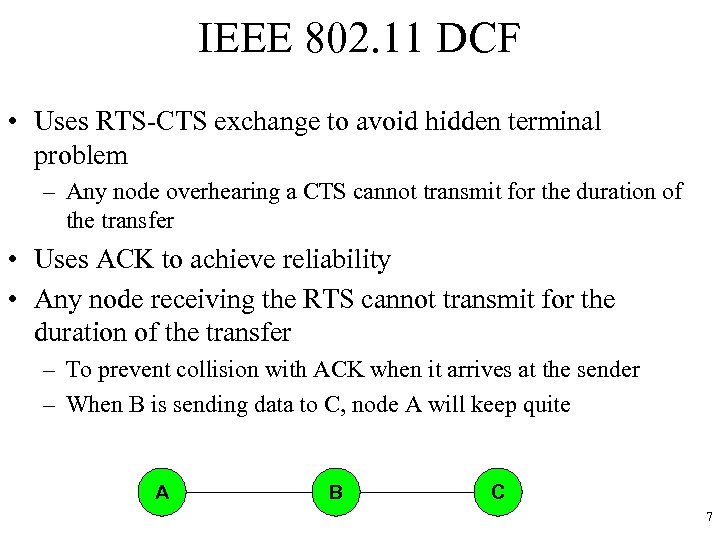 IEEE 802. 11 DCF • Uses RTS-CTS exchange to avoid hidden terminal problem – Any node overhearing a CTS cannot transmit for the duration of the transfer • Uses ACK to achieve reliability • Any node receiving the RTS cannot transmit for the duration of the transfer – To prevent collision with ACK when it arrives at the sender – When B is sending data to C, node A will keep quite A B C 7
IEEE 802. 11 DCF • Uses RTS-CTS exchange to avoid hidden terminal problem – Any node overhearing a CTS cannot transmit for the duration of the transfer • Uses ACK to achieve reliability • Any node receiving the RTS cannot transmit for the duration of the transfer – To prevent collision with ACK when it arrives at the sender – When B is sending data to C, node A will keep quite A B C 7
 Collision Avoidance • With half-duplex radios, collision detection is not possible • CSMA/CA: Wireless MAC protocols often use collision avoidance techniques, in conjunction with a (physical or virtual) carrier sense mechanism – Carrier sense: When a node wishes to transmit a packet, it first waits until the channel is idle – Collision avoidance: Once channel becomes idle, the node waits for a randomly chosen duration before attempting to transmit 8
Collision Avoidance • With half-duplex radios, collision detection is not possible • CSMA/CA: Wireless MAC protocols often use collision avoidance techniques, in conjunction with a (physical or virtual) carrier sense mechanism – Carrier sense: When a node wishes to transmit a packet, it first waits until the channel is idle – Collision avoidance: Once channel becomes idle, the node waits for a randomly chosen duration before attempting to transmit 8
 Congestion Avoidance • When transmitting a packet, choose a backoff interval in the range [0, cw] – cw is contention window • Count down the backoff interval when medium is idle – Count-down is suspended if medium becomes busy • When backoff interval reaches 0, transmit RTS 9
Congestion Avoidance • When transmitting a packet, choose a backoff interval in the range [0, cw] – cw is contention window • Count down the backoff interval when medium is idle – Count-down is suspended if medium becomes busy • When backoff interval reaches 0, transmit RTS 9
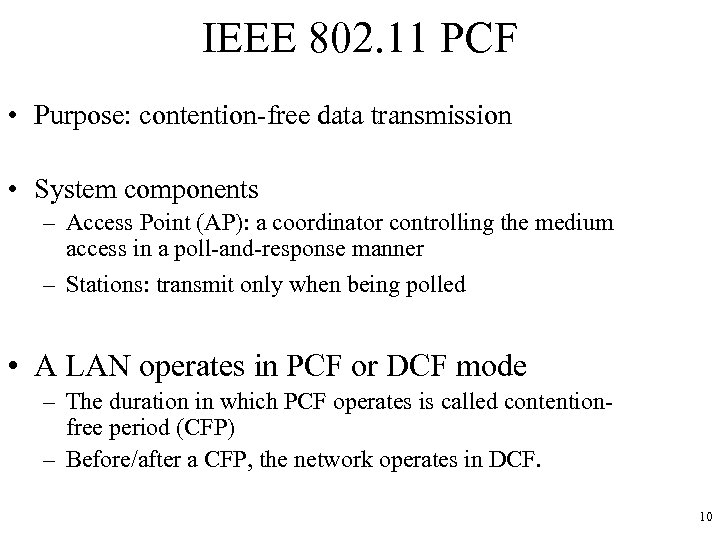 IEEE 802. 11 PCF • Purpose: contention-free data transmission • System components – Access Point (AP): a coordinator controlling the medium access in a poll-and-response manner – Stations: transmit only when being polled • A LAN operates in PCF or DCF mode – The duration in which PCF operates is called contentionfree period (CFP) – Before/after a CFP, the network operates in DCF. 10
IEEE 802. 11 PCF • Purpose: contention-free data transmission • System components – Access Point (AP): a coordinator controlling the medium access in a poll-and-response manner – Stations: transmit only when being polled • A LAN operates in PCF or DCF mode – The duration in which PCF operates is called contentionfree period (CFP) – Before/after a CFP, the network operates in DCF. 10
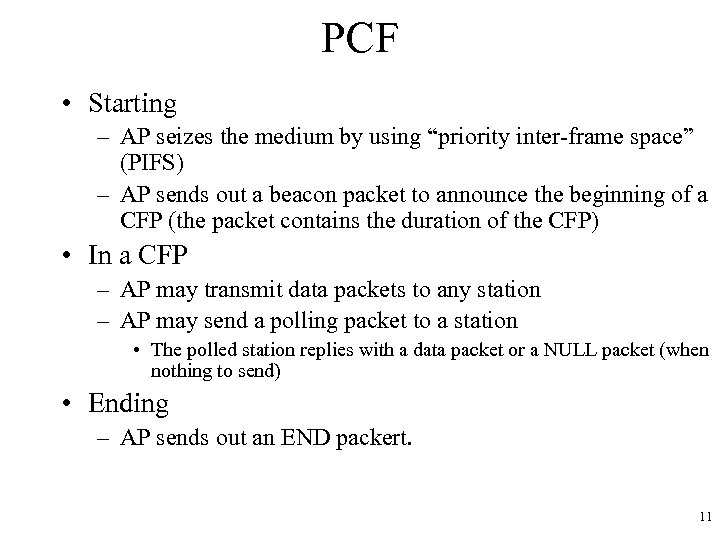 PCF • Starting – AP seizes the medium by using “priority inter-frame space” (PIFS) – AP sends out a beacon packet to announce the beginning of a CFP (the packet contains the duration of the CFP) • In a CFP – AP may transmit data packets to any station – AP may send a polling packet to a station • The polled station replies with a data packet or a NULL packet (when nothing to send) • Ending – AP sends out an END packert. 11
PCF • Starting – AP seizes the medium by using “priority inter-frame space” (PIFS) – AP sends out a beacon packet to announce the beginning of a CFP (the packet contains the duration of the CFP) • In a CFP – AP may transmit data packets to any station – AP may send a polling packet to a station • The polled station replies with a data packet or a NULL packet (when nothing to send) • Ending – AP sends out an END packert. 11
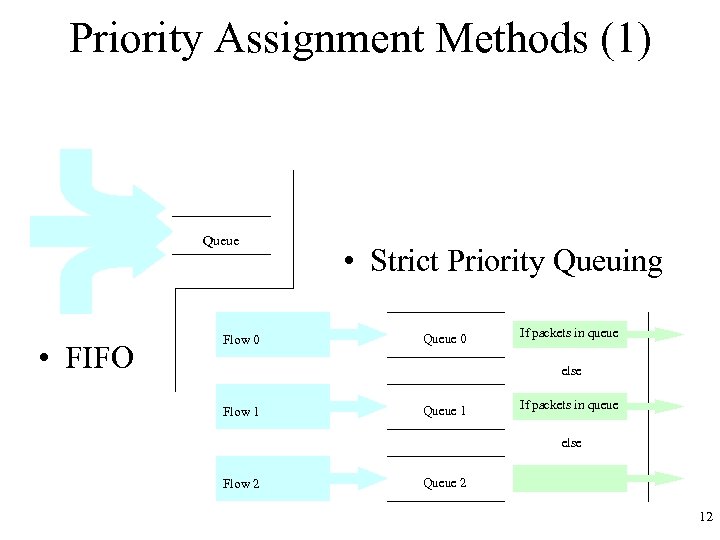 Priority Assignment Methods (1) Queue • FIFO Flow 0 • Strict Priority Queuing Queue 0 If packets in queue else Flow 1 Queue 1 If packets in queue else Flow 2 Queue 2 12
Priority Assignment Methods (1) Queue • FIFO Flow 0 • Strict Priority Queuing Queue 0 If packets in queue else Flow 1 Queue 1 If packets in queue else Flow 2 Queue 2 12
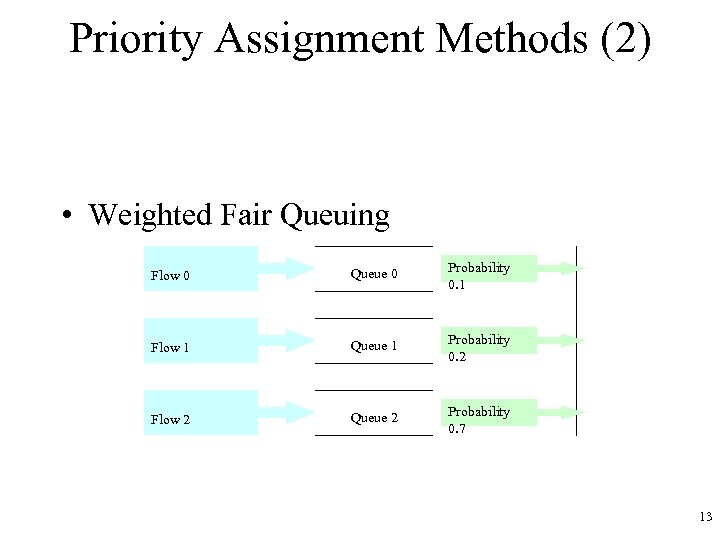 Priority Assignment Methods (2) • Weighted Fair Queuing Flow 0 Queue 0 Probability 0. 1 Flow 1 Queue 1 Probability 0. 2 Flow 2 Queue 2 Probability 0. 7 13
Priority Assignment Methods (2) • Weighted Fair Queuing Flow 0 Queue 0 Probability 0. 1 Flow 1 Queue 1 Probability 0. 2 Flow 2 Queue 2 Probability 0. 7 13
 MAC Management • Synchronization – finding and staying with a WLAN. – Synchronization functions • Power management – sleeping without missing any messages – power management functions, e. g. , periodic sleep, frame buffering, traffic indication map • Association and Re-association – joining a network, roaming, moving from one AP to another, scanning 14
MAC Management • Synchronization – finding and staying with a WLAN. – Synchronization functions • Power management – sleeping without missing any messages – power management functions, e. g. , periodic sleep, frame buffering, traffic indication map • Association and Re-association – joining a network, roaming, moving from one AP to another, scanning 14
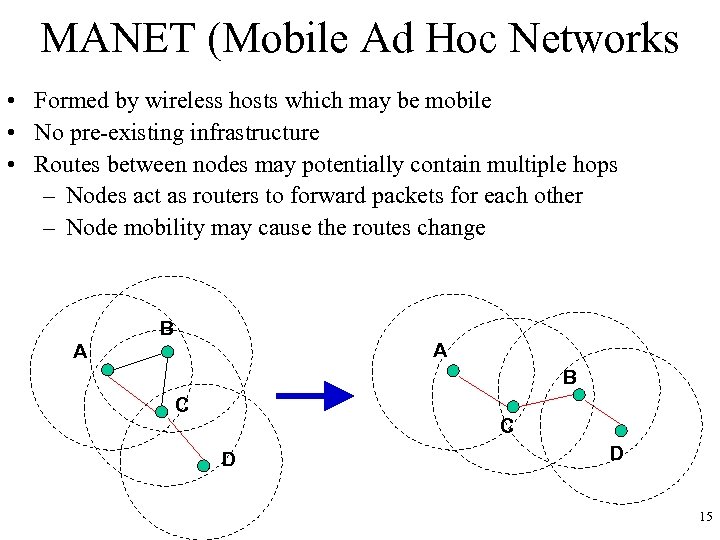 MANET (Mobile Ad Hoc Networks • Formed by wireless hosts which may be mobile • No pre-existing infrastructure • Routes between nodes may potentially contain multiple hops – Nodes act as routers to forward packets for each other – Node mobility may cause the routes change B A A B C C D D 15
MANET (Mobile Ad Hoc Networks • Formed by wireless hosts which may be mobile • No pre-existing infrastructure • Routes between nodes may potentially contain multiple hops – Nodes act as routers to forward packets for each other – Node mobility may cause the routes change B A A B C C D D 15
 Why MANET? • Advantages: low-cost, flexibility – Ease & Speed of deployment – Decreased dependence on infrastructure • Applications – Military environments • soldiers, tanks, planes – Civilian environments • vehicle networks • conferences / stadiums • outside activities – Emergency operations • search-and-rescue / policing and fire fighting 16
Why MANET? • Advantages: low-cost, flexibility – Ease & Speed of deployment – Decreased dependence on infrastructure • Applications – Military environments • soldiers, tanks, planes – Civilian environments • vehicle networks • conferences / stadiums • outside activities – Emergency operations • search-and-rescue / policing and fire fighting 16
 Challenges • Collaboration – Collaborations are necessary to maintain a MANET and its functionality. – How to collaborate effectively and efficiently? – How to motivate/enforce nodes to collaborate? • Dynamic topology – Nodes mobility – Interference in wireless communications 17
Challenges • Collaboration – Collaborations are necessary to maintain a MANET and its functionality. – How to collaborate effectively and efficiently? – How to motivate/enforce nodes to collaborate? • Dynamic topology – Nodes mobility – Interference in wireless communications 17
 Routing Protocols: Overview • Proactive protocols – Determine routes independent of traffic pattern – Traditional link-state and distance-vector routing protocols are proactive – Examples: • DSDV (Dynamic sequenced distance-vector) • OLSR (Optimized Link State Routing) • Reactive protocols – Maintain routes only if needed – Examples: • DSR (Dynamic source routing) • AODV (on-demand distance vector) 18
Routing Protocols: Overview • Proactive protocols – Determine routes independent of traffic pattern – Traditional link-state and distance-vector routing protocols are proactive – Examples: • DSDV (Dynamic sequenced distance-vector) • OLSR (Optimized Link State Routing) • Reactive protocols – Maintain routes only if needed – Examples: • DSR (Dynamic source routing) • AODV (on-demand distance vector) 18
 Routing Protocols: Tradeoff • Latency of route discovery – Proactive protocols may have lower latency since routes are maintained at all times – Reactive protocols may have higher latency because a route from X to Y may be found only when X attempts to send to Y • Overhead of route discovery/maintenance – Reactive protocols may have lower overhead since routes are determined only if needed – Proactive protocols can (but not necessarily) result in higher overhead due to continuous route updating 19
Routing Protocols: Tradeoff • Latency of route discovery – Proactive protocols may have lower latency since routes are maintained at all times – Reactive protocols may have higher latency because a route from X to Y may be found only when X attempts to send to Y • Overhead of route discovery/maintenance – Reactive protocols may have lower overhead since routes are determined only if needed – Proactive protocols can (but not necessarily) result in higher overhead due to continuous route updating 19
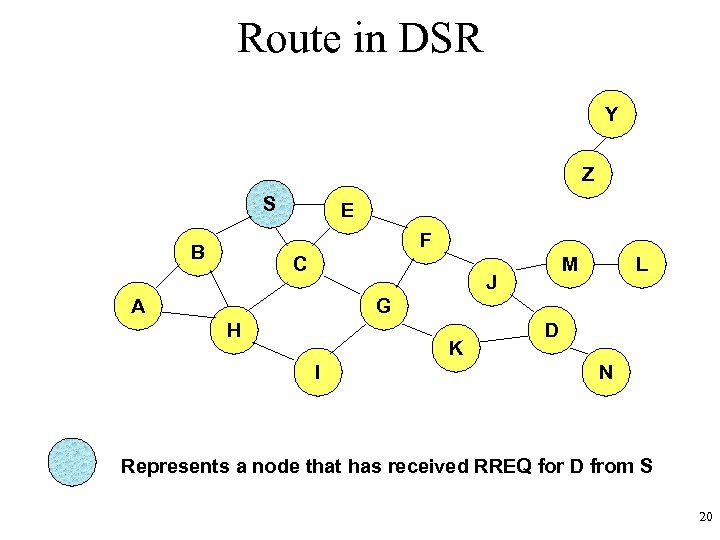 Route in DSR Y Z S E F B C M J A L G H K I D N Represents a node that has received RREQ for D from S 20
Route in DSR Y Z S E F B C M J A L G H K I D N Represents a node that has received RREQ for D from S 20
 Dynamic Source Routing • When node S wants to send a packet to node D, but does not know a route to D, node S initiates a routing process • Runs in three phases – Route Discovery Route Reply Path Establishment • Route Discovery – Source node S floods Route Request (RREQ) – Each node appends own identifier when forwarding RREQ 21
Dynamic Source Routing • When node S wants to send a packet to node D, but does not know a route to D, node S initiates a routing process • Runs in three phases – Route Discovery Route Reply Path Establishment • Route Discovery – Source node S floods Route Request (RREQ) – Each node appends own identifier when forwarding RREQ 21
 Dynamic Source Routing (DSR) • Each packet header contains a route, which is represented as a complete sequence of nodes between a source-destination pair • Protocol consists of two phases – route discovery – route maintenance • Optimizations for efficiency – Route cache – Piggybacking – Error handling 22
Dynamic Source Routing (DSR) • Each packet header contains a route, which is represented as a complete sequence of nodes between a source-destination pair • Protocol consists of two phases – route discovery – route maintenance • Optimizations for efficiency – Route cache – Piggybacking – Error handling 22
 DSR Route Discovery • Source broadcasts route request (id, target) • Intermediate node action – Discard if id is in
DSR Route Discovery • Source broadcasts route request (id, target) • Intermediate node action – Discard if id is in
 DSR Route Maintenance • Use acknowledgements or a layer-2 scheme to detect broken links; inform sender via route error packet • If no route to the source exists – Use piggybacking – Send out a route request and buffer route error • Sender truncates all routes which use nodes mentioned in route error • Initiate route discovery 24
DSR Route Maintenance • Use acknowledgements or a layer-2 scheme to detect broken links; inform sender via route error packet • If no route to the source exists – Use piggybacking – Send out a route request and buffer route error • Sender truncates all routes which use nodes mentioned in route error • Initiate route discovery 24
 Optimizations for efficiency • Route Cache – Use cached entries for during route discovery – Promiscuous mode to add more routes – Use hop based delays for local congestion – Must be careful to avoid loop formation – Non propagating RREQs 25
Optimizations for efficiency • Route Cache – Use cached entries for during route discovery – Promiscuous mode to add more routes – Use hop based delays for local congestion – Must be careful to avoid loop formation – Non propagating RREQs 25
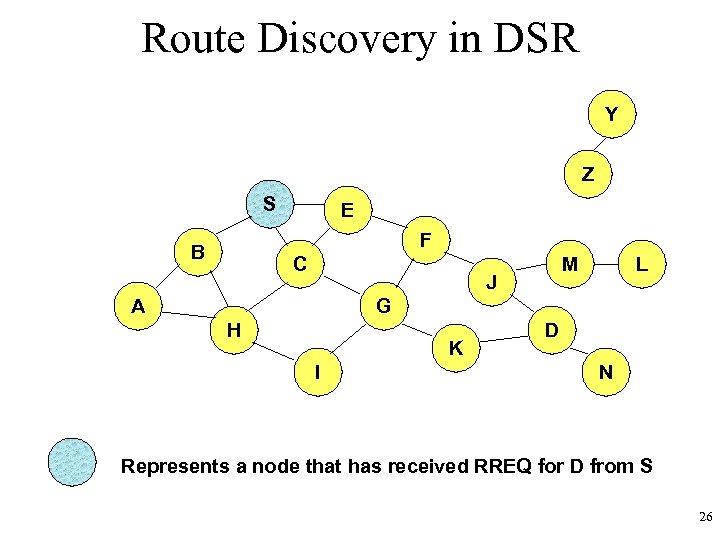 Route Discovery in DSR Y Z S E F B C M J A L G H K I D N Represents a node that has received RREQ for D from S 26
Route Discovery in DSR Y Z S E F B C M J A L G H K I D N Represents a node that has received RREQ for D from S 26
![Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C](https://present5.com/presentation/6d7fd689473855449460786e547fff1e/image-27.jpg) Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C M J A L G H K I D N Represents transmission of RREQ [X, Y] Represents list of identifiers appended to RREQ 27
Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C M J A L G H K I D N Represents transmission of RREQ [X, Y] Represents list of identifiers appended to RREQ 27
![Route Discovery in DSR Y S E Z [S, E] F B C A Route Discovery in DSR Y S E Z [S, E] F B C A](https://present5.com/presentation/6d7fd689473855449460786e547fff1e/image-28.jpg) Route Discovery in DSR Y S E Z [S, E] F B C A M J [S, C] H G K I L D N 28
Route Discovery in DSR Y S E Z [S, E] F B C A M J [S, C] H G K I L D N 28
![Route Discovery in DSR Y Z S E [S, E, F, J] F B Route Discovery in DSR Y Z S E [S, E, F, J] F B](https://present5.com/presentation/6d7fd689473855449460786e547fff1e/image-29.jpg) Route Discovery in DSR Y Z S E [S, E, F, J] F B C M J A L G H K I D [S, C, G, K] N 29
Route Discovery in DSR Y Z S E [S, E, F, J] F B C M J A L G H K I D [S, C, G, K] N 29
 Route Reply in DSR • Destination D on receiving the first RREQ, sends a Route Reply (RREP) • RREP is sent on a route obtained by reversing the route appended to received RREQ • RREP includes the route from S to D on which RREQ was received by node D 30
Route Reply in DSR • Destination D on receiving the first RREQ, sends a Route Reply (RREP) • RREP is sent on a route obtained by reversing the route appended to received RREQ • RREP includes the route from S to D on which RREQ was received by node D 30
![Route Reply in DSR Y S E Z RREP [S, E, F, J, D] Route Reply in DSR Y S E Z RREP [S, E, F, J, D]](https://present5.com/presentation/6d7fd689473855449460786e547fff1e/image-31.jpg) Route Reply in DSR Y S E Z RREP [S, E, F, J, D] F B C M J A L G H K I D N Represents RREP control message 31
Route Reply in DSR Y S E Z RREP [S, E, F, J, D] F B C M J A L G H K I D N Represents RREP control message 31
 Route Reply in DSR • Node S on receiving RREP, caches the route included in the RREP • When node S sends a data packet to D, the entire route is included in the packet header – Hence the name source routing • Intermediate nodes use the source route included in a packet to determine to whom a packet should be forwarded 32
Route Reply in DSR • Node S on receiving RREP, caches the route included in the RREP • When node S sends a data packet to D, the entire route is included in the packet header – Hence the name source routing • Intermediate nodes use the source route included in a packet to determine to whom a packet should be forwarded 32
![Data Delivery in DSR Y DATA [S, E, F, J, D] S Z E Data Delivery in DSR Y DATA [S, E, F, J, D] S Z E](https://present5.com/presentation/6d7fd689473855449460786e547fff1e/image-33.jpg) Data Delivery in DSR Y DATA [S, E, F, J, D] S Z E F B C M J A L G H K I D N Packet header size grows with route length 33
Data Delivery in DSR Y DATA [S, E, F, J, D] S Z E F B C M J A L G H K I D N Packet header size grows with route length 33
 Lingid • • • J. Jun and M. L. Sichitiu, “The nominal capacity of wireless mesh networks, ” IEEE Wireless Communications, Oct. , pp. 8 -14, 2003. C. Zhu, M. J. Lee, and T. Saadawi, “On the route discovery latency of wireless mesh networks, ” in Proc. IEEE CCNC ’ 05, 2005, pp. 19 -23. J-H Huang, L-C Wang, and C-J Chang, “Coverage and capacity of a wireless mesh network, ” in 2005 International Conference on Wireless Networks, Communications, and Mobile Computing, 2005, vol. 1 pp. 458 -463. I. Akyildiz and X. Wang, “A survey on wireless mesh networks, ” IEEE Radio Communications, Sep. , pp. S 23 -S 30, 2005. The Internet Engineering Task Force, Ad hoc On-Demand Distance Vector (AODV) Routing. [Online] Jul. 2003, [2006 Apr. 21], Available at HTTP: http: //www. ietf. org/rfc 3561. txt The Internet Engineering Task Force, The Dynamic Source Routing Protocol for Mobile Ad Hoc Networks (DSR). [Online] Jul. 2004, [2006 Apr. 21], Available at HTTP: http: //www. ietf. org/internet-drafts/draft-ietf-manet-dsr 10. txt. The Internet Engineering Task Force, Optimized Link State Routing Protocol (OLSR). [Online] Oct. 2003, [2006 Apr. 21], Available at HTTP: http: //www. ietf. org/rfc 3626. txt. S. Naghian and J. Tervonen, “Semi-infrastructured mobile ad-hoc mesh networking, ” in Proc. IEEE PIMRC ‘ 03, 2003, vol. 2 pp. 1069 -1073. T-J Tsai and J-W Chen, “IEEE 802. 11 protocol over wireless mesh networks: problems and perspectives, ” in Proc. IEEE AINA ’ 05, 2005, vol. 2, pp. 60 -63. 34
Lingid • • • J. Jun and M. L. Sichitiu, “The nominal capacity of wireless mesh networks, ” IEEE Wireless Communications, Oct. , pp. 8 -14, 2003. C. Zhu, M. J. Lee, and T. Saadawi, “On the route discovery latency of wireless mesh networks, ” in Proc. IEEE CCNC ’ 05, 2005, pp. 19 -23. J-H Huang, L-C Wang, and C-J Chang, “Coverage and capacity of a wireless mesh network, ” in 2005 International Conference on Wireless Networks, Communications, and Mobile Computing, 2005, vol. 1 pp. 458 -463. I. Akyildiz and X. Wang, “A survey on wireless mesh networks, ” IEEE Radio Communications, Sep. , pp. S 23 -S 30, 2005. The Internet Engineering Task Force, Ad hoc On-Demand Distance Vector (AODV) Routing. [Online] Jul. 2003, [2006 Apr. 21], Available at HTTP: http: //www. ietf. org/rfc 3561. txt The Internet Engineering Task Force, The Dynamic Source Routing Protocol for Mobile Ad Hoc Networks (DSR). [Online] Jul. 2004, [2006 Apr. 21], Available at HTTP: http: //www. ietf. org/internet-drafts/draft-ietf-manet-dsr 10. txt. The Internet Engineering Task Force, Optimized Link State Routing Protocol (OLSR). [Online] Oct. 2003, [2006 Apr. 21], Available at HTTP: http: //www. ietf. org/rfc 3626. txt. S. Naghian and J. Tervonen, “Semi-infrastructured mobile ad-hoc mesh networking, ” in Proc. IEEE PIMRC ‘ 03, 2003, vol. 2 pp. 1069 -1073. T-J Tsai and J-W Chen, “IEEE 802. 11 protocol over wireless mesh networks: problems and perspectives, ” in Proc. IEEE AINA ’ 05, 2005, vol. 2, pp. 60 -63. 34


