7625adabd3b2f494a747698f6899ac8a.ppt
- Количество слайдов: 29
 Sicurezza II A. A. 2010 -2011 LDAP Speaker: André Panisson, Ph. D student Università degli Studi di Torino, Computer Science Department Corso Svizzera, 185 – 10149, Torino, Italy panisson@di. unito. it Sicurezza II, A. A. 2010/2011
Sicurezza II A. A. 2010 -2011 LDAP Speaker: André Panisson, Ph. D student Università degli Studi di Torino, Computer Science Department Corso Svizzera, 185 – 10149, Torino, Italy panisson@di. unito. it Sicurezza II, A. A. 2010/2011
 LDAP o LDAP Stands for Lightweight Directory Access Protocol o It is a client-server protocol for reading and editing directories over an IP network • A directory in this sense is a hierarchical set of records: • telephone directory, for example o Part of the X. 500 standards, a series of computer networking standards covering electronic directory services (X. 509 is part of the X. 500 series, and it is an ITU-T standard for a public key infrastructure) Open. ID, OAuth are protocols available for Web users and applications on the Internet. LDAP/SAML are protocols used in Intranets/Enterprises Sicurezza II, A. A. 2010/2011
LDAP o LDAP Stands for Lightweight Directory Access Protocol o It is a client-server protocol for reading and editing directories over an IP network • A directory in this sense is a hierarchical set of records: • telephone directory, for example o Part of the X. 500 standards, a series of computer networking standards covering electronic directory services (X. 509 is part of the X. 500 series, and it is an ITU-T standard for a public key infrastructure) Open. ID, OAuth are protocols available for Web users and applications on the Internet. LDAP/SAML are protocols used in Intranets/Enterprises Sicurezza II, A. A. 2010/2011
 LDAP – how it works? o A client starts an LDAP session by connecting to an LDAP server, called a Directory System Agent (DSA), by default on TCP port 389 o The client then sends an operation request to the server, and the server sends responses in return o Some of the available operations: • Search: search for and/or retrieve directory entries • Add a new entry • Delete an entry • Modify an entry • … Sicurezza II, A. A. 2010/2011
LDAP – how it works? o A client starts an LDAP session by connecting to an LDAP server, called a Directory System Agent (DSA), by default on TCP port 389 o The client then sends an operation request to the server, and the server sends responses in return o Some of the available operations: • Search: search for and/or retrieve directory entries • Add a new entry • Delete an entry • Modify an entry • … Sicurezza II, A. A. 2010/2011
 LDIF o LDIF Stands for LDAP Data Interchange Format o It is a standard plain text data interchange format for representing LDAP directory content • Example: dn: cn=Andre Panisson, ou=people, dc=di, dc=unito, dc=it objectclass: inet. Org. Person cn: Andre Panisson cn: Panisson Andre sn: Andre uid: panisson userpassword: prova carlicense: HISCAR 124 homephone: 555 -111 -2223 mail: panisson@di. unito. it mail: panisson@gmail. com ou: Docenti Sicurezza II, A. A. 2010/2011
LDIF o LDIF Stands for LDAP Data Interchange Format o It is a standard plain text data interchange format for representing LDAP directory content • Example: dn: cn=Andre Panisson, ou=people, dc=di, dc=unito, dc=it objectclass: inet. Org. Person cn: Andre Panisson cn: Panisson Andre sn: Andre uid: panisson userpassword: prova carlicense: HISCAR 124 homephone: 555 -111 -2223 mail: panisson@di. unito. it mail: panisson@gmail. com ou: Docenti Sicurezza II, A. A. 2010/2011
 X 509 certificates o It opens the possibility to load certificates in the format X 509 in order to authenticate users using the user certificate Sicurezza II, A. A. 2010/2011
X 509 certificates o It opens the possibility to load certificates in the format X 509 in order to authenticate users using the user certificate Sicurezza II, A. A. 2010/2011
 LDIF Fields Main Fields: o dn: distinguished name o dc: domain component o ou: organizational unit o cn: common name dn: cn=The Postmaster, dc=example, dc=com object. Class: organizational. Role cn: The Postmaster Sicurezza II, A. A. 2010/2011
LDIF Fields Main Fields: o dn: distinguished name o dc: domain component o ou: organizational unit o cn: common name dn: cn=The Postmaster, dc=example, dc=com object. Class: organizational. Role cn: The Postmaster Sicurezza II, A. A. 2010/2011
 Lab objectives o Deploy a basic LDAP server • Load user info • Browse/search for user info o Configure Apache to authenticate users using LDAP Sicurezza II, A. A. 2010/2011
Lab objectives o Deploy a basic LDAP server • Load user info • Browse/search for user info o Configure Apache to authenticate users using LDAP Sicurezza II, A. A. 2010/2011
 Lab Goals o Deploy a basic LDAP server • Load user info • Browse/search for user info o Configure Apache to authenticate users using LDAP Sicurezza II, A. A. 2010/2011
Lab Goals o Deploy a basic LDAP server • Load user info • Browse/search for user info o Configure Apache to authenticate users using LDAP Sicurezza II, A. A. 2010/2011
 Lab Preparation • Server Apache 2. 2. 13 at $HOME/apache Sicurezza II, A. A. 2010/2011
Lab Preparation • Server Apache 2. 2. 13 at $HOME/apache Sicurezza II, A. A. 2010/2011
 Open. LDAP • www. openldap. org • An open source implementation of the Lightweight Directory Access Protocol Sicurezza II, A. A. 2010/2011
Open. LDAP • www. openldap. org • An open source implementation of the Lightweight Directory Access Protocol Sicurezza II, A. A. 2010/2011
 Open. LDAP • Download Open. LDAP version 2. 4. 25 • Extract it: tar -xvzf openldap-2. 4. 25. tgz • Check the files README, INSTALL • Create the target directory and build it: mkdir $HOME/openldap/ cd openldap-2. 4. 25. /configure --prefix=$HOME/openldap/ make depend make install Sicurezza II, A. A. 2010/2011
Open. LDAP • Download Open. LDAP version 2. 4. 25 • Extract it: tar -xvzf openldap-2. 4. 25. tgz • Check the files README, INSTALL • Create the target directory and build it: mkdir $HOME/openldap/ cd openldap-2. 4. 25. /configure --prefix=$HOME/openldap/ make depend make install Sicurezza II, A. A. 2010/2011
 Open. LDAP • Edit the file $HOME/openldap/etc/openldap/slapd. conf • Include the following schemas: include /home/panisson/openldap/etc/openldap/schema/core. schema /home/panisson/openldap/etc/openldap/schema/cosine. schema /home/panisson/openldap/etc/openldap/schema/inetorgperson. schema • Configure the database: database bdb suffix "dc=di, dc=unito, dc=it” rootdn "cn=Manager, dc=di, dc=unito, dc=it" Sicurezza II, A. A. 2010/2011
Open. LDAP • Edit the file $HOME/openldap/etc/openldap/slapd. conf • Include the following schemas: include /home/panisson/openldap/etc/openldap/schema/core. schema /home/panisson/openldap/etc/openldap/schema/cosine. schema /home/panisson/openldap/etc/openldap/schema/inetorgperson. schema • Configure the database: database bdb suffix "dc=di, dc=unito, dc=it” rootdn "cn=Manager, dc=di, dc=unito, dc=it" Sicurezza II, A. A. 2010/2011
 Open. LDAP • Start LDAP on port 8389: $HOME/openldap/libexec/slapd -h "ldap: //0. 0: 8389" • Connect to the server using ldapsearch: $HOME/openldap/bin/ldapsearch -h localhost -p 8389 -x -b '' -s base '(objectclass=*)' naming. Contexts Sicurezza II, A. A. 2010/2011
Open. LDAP • Start LDAP on port 8389: $HOME/openldap/libexec/slapd -h "ldap: //0. 0: 8389" • Connect to the server using ldapsearch: $HOME/openldap/bin/ldapsearch -h localhost -p 8389 -x -b '' -s base '(objectclass=*)' naming. Contexts Sicurezza II, A. A. 2010/2011
 Open. LDAP • Create a file user. ldif: dn: dc=di, dc=unito, dc=it dc: di object. Class: top object. Class: domain dn: ou=people, dc=di, dc=unito, dc=it ou: people object. Class: top object. Class: organizational. Unit dn: cn=Andre Panisson, ou=people, dc=di, dc=unito, dc=it objectclass: inet. Org. Person cn: Andre Panisson cn: Panisson Andre sn: Andre uid: panisson userpassword: prova carlicense: HISCAR 124 homephone: 555 -111 -2223 mail: panisson@di. unito. it mail: panisson@gmail. com ou: Docenti Sicurezza II, A. A. 2010/2011
Open. LDAP • Create a file user. ldif: dn: dc=di, dc=unito, dc=it dc: di object. Class: top object. Class: domain dn: ou=people, dc=di, dc=unito, dc=it ou: people object. Class: top object. Class: organizational. Unit dn: cn=Andre Panisson, ou=people, dc=di, dc=unito, dc=it objectclass: inet. Org. Person cn: Andre Panisson cn: Panisson Andre sn: Andre uid: panisson userpassword: prova carlicense: HISCAR 124 homephone: 555 -111 -2223 mail: panisson@di. unito. it mail: panisson@gmail. com ou: Docenti Sicurezza II, A. A. 2010/2011
 Open. LDAP • Load to LDAP server using ldapadd: $HOME/openldap/bin/ldapadd -h localhost -p 8389 -D "cn=Manager, dc=di, dc=unito, dc=it" -W -f user. ldif Sicurezza II, A. A. 2010/2011
Open. LDAP • Load to LDAP server using ldapadd: $HOME/openldap/bin/ldapadd -h localhost -p 8389 -D "cn=Manager, dc=di, dc=unito, dc=it" -W -f user. ldif Sicurezza II, A. A. 2010/2011
 Open. LDAP Clients • Connect to LDAP using a client: http: //jxplorer. org/ • http: //phpldapadmin. sourceforge. net/ Sicurezza II, A. A. 2010/2011
Open. LDAP Clients • Connect to LDAP using a client: http: //jxplorer. org/ • http: //phpldapadmin. sourceforge. net/ Sicurezza II, A. A. 2010/2011
 LDAP and Certificates • Create a new key and X. 509 certificate: • Create user key: openssl genrsa -out userkey. pem 2048 openssl req -key userkey. pem -new -out userreq. pem • Create certificate and sign using CA openssl x 509 -days 365 -CA ca-bundle. crt -CAkey CA. key -CAcreateserial -CAserial ca. srl -req -in userreq. pem -out usercert. pem • Convert to pkcs 12 and import it to your browser: openssl pkcs 12 -in usercert. pem -inkey userkey. pem -export -out usercert. pk 12 • Convert certificate to DER format openssl x 509 -outform DER -in usercert. pem -out usercert. der • Encode it in base 64 openssl base 64 -A < usercert. der > usercert. der. b 64 Sicurezza II, A. A. 2010/2011
LDAP and Certificates • Create a new key and X. 509 certificate: • Create user key: openssl genrsa -out userkey. pem 2048 openssl req -key userkey. pem -new -out userreq. pem • Create certificate and sign using CA openssl x 509 -days 365 -CA ca-bundle. crt -CAkey CA. key -CAcreateserial -CAserial ca. srl -req -in userreq. pem -out usercert. pem • Convert to pkcs 12 and import it to your browser: openssl pkcs 12 -in usercert. pem -inkey userkey. pem -export -out usercert. pk 12 • Convert certificate to DER format openssl x 509 -outform DER -in usercert. pem -out usercert. der • Encode it in base 64 openssl base 64 -A < usercert. der > usercert. der. b 64 Sicurezza II, A. A. 2010/2011
 LDAP and Certificates • Create a LDIF with the certificate contents: dn: cn=Andre Panisson, ou=people, dc=di, dc=unito, dc=it changetype: modify replace: user. Certificate; binary: : < contents of usercert. der. b 64 > • Import it to LDAP: $HOME/openldap/bin/ldapadd -h localhost -p 8389 -D "cn=Manager, dc=di, dc=unito, dc=it" -W -f cert. ldif Sicurezza II, A. A. 2010/2011
LDAP and Certificates • Create a LDIF with the certificate contents: dn: cn=Andre Panisson, ou=people, dc=di, dc=unito, dc=it changetype: modify replace: user. Certificate; binary: : < contents of usercert. der. b 64 > • Import it to LDAP: $HOME/openldap/bin/ldapadd -h localhost -p 8389 -D "cn=Manager, dc=di, dc=unito, dc=it" -W -f cert. ldif Sicurezza II, A. A. 2010/2011
 Apache and LDAP • LDAP module for Apache: http: //httpd. apache. org/docs/2. 2/mod_authnz_ldap. html • Install LDAP modules mod_ldap and mod_authnz_ldap: cp /usr/home/docenti/panisson/mod_ldap. so $HOME/apache/modules cp /usr/home/docenti/panisson/mod_authnz_ldap. so $HOME/apache/modules • To build Apache with LDAP modules: . /configure --enable-module=SO --enable-ssl --prefix=$HOME/apache --enable-ldap=shared --enable-auth-ldap=shared --with-ldap --with-ldap-include=$HOME/openldap/include --with-ldap-lib=$HOME/openldap/lib --enable-authnz-ldap=shared Sicurezza II, A. A. 2010/2011
Apache and LDAP • LDAP module for Apache: http: //httpd. apache. org/docs/2. 2/mod_authnz_ldap. html • Install LDAP modules mod_ldap and mod_authnz_ldap: cp /usr/home/docenti/panisson/mod_ldap. so $HOME/apache/modules cp /usr/home/docenti/panisson/mod_authnz_ldap. so $HOME/apache/modules • To build Apache with LDAP modules: . /configure --enable-module=SO --enable-ssl --prefix=$HOME/apache --enable-ldap=shared --enable-auth-ldap=shared --with-ldap --with-ldap-include=$HOME/openldap/include --with-ldap-lib=$HOME/openldap/lib --enable-authnz-ldap=shared Sicurezza II, A. A. 2010/2011
 Apache and LDAP • Edit httpd. conf, add Load. Module ldap_modules/mod_ldap. so Load. Module authnz_ldap_modules/mod_authnz_ldap. so LDAPTrusted. Global. Cert CA_BASE 64 conf/ssl. crt/ca-bundle. crt
Apache and LDAP • Edit httpd. conf, add Load. Module ldap_modules/mod_ldap. so Load. Module authnz_ldap_modules/mod_authnz_ldap. so LDAPTrusted. Global. Cert CA_BASE 64 conf/ssl. crt/ca-bundle. crt
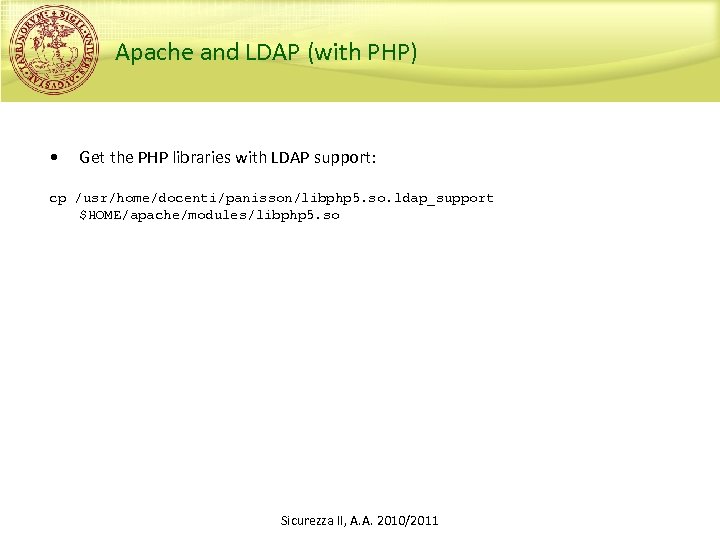 Apache and LDAP (with PHP) • Get the PHP libraries with LDAP support: cp /usr/home/docenti/panisson/libphp 5. so. ldap_support $HOME/apache/modules/libphp 5. so Sicurezza II, A. A. 2010/2011
Apache and LDAP (with PHP) • Get the PHP libraries with LDAP support: cp /usr/home/docenti/panisson/libphp 5. so. ldap_support $HOME/apache/modules/libphp 5. so Sicurezza II, A. A. 2010/2011
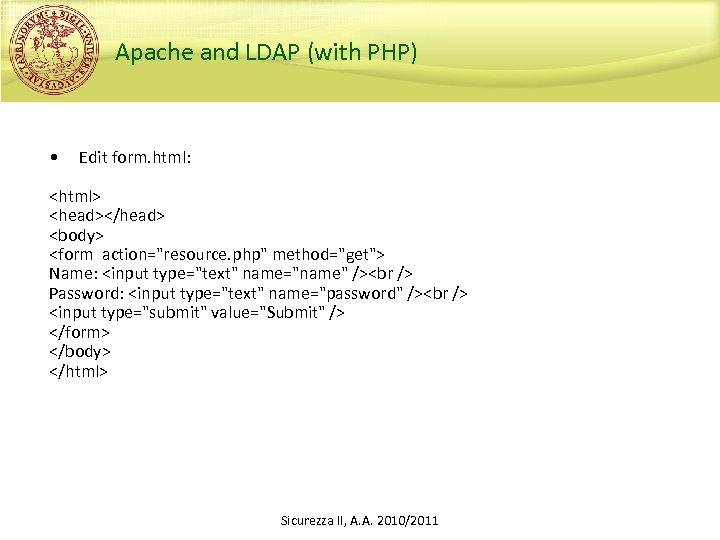 Apache and LDAP (with PHP) • Edit form. html:
Apache and LDAP (with PHP) • Edit form. html:
![Apache and LDAP (with PHP) • Edit resource. php: <? php $name = $_GET['name']; Apache and LDAP (with PHP) • Edit resource. php: <? php $name = $_GET['name'];](https://present5.com/presentation/7625adabd3b2f494a747698f6899ac8a/image-23.jpg) Apache and LDAP (with PHP) • Edit resource. php:
Apache and LDAP (with PHP) • Edit resource. php:
 Apache and LDAP (with PHP) • Edit resource. php (continuation):
Apache and LDAP (with PHP) • Edit resource. php (continuation):
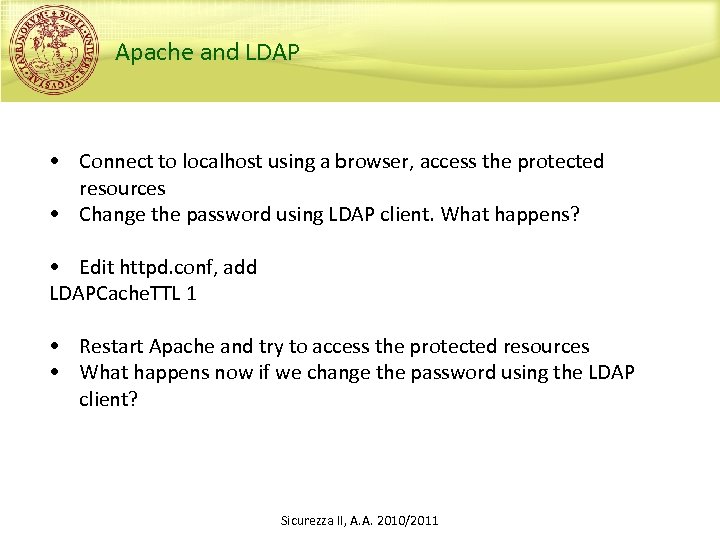 Apache and LDAP • Connect to localhost using a browser, access the protected resources • Change the password using LDAP client. What happens? • Edit httpd. conf, add LDAPCache. TTL 1 • Restart Apache and try to access the protected resources • What happens now if we change the password using the LDAP client? Sicurezza II, A. A. 2010/2011
Apache and LDAP • Connect to localhost using a browser, access the protected resources • Change the password using LDAP client. What happens? • Edit httpd. conf, add LDAPCache. TTL 1 • Restart Apache and try to access the protected resources • What happens now if we change the password using the LDAP client? Sicurezza II, A. A. 2010/2011
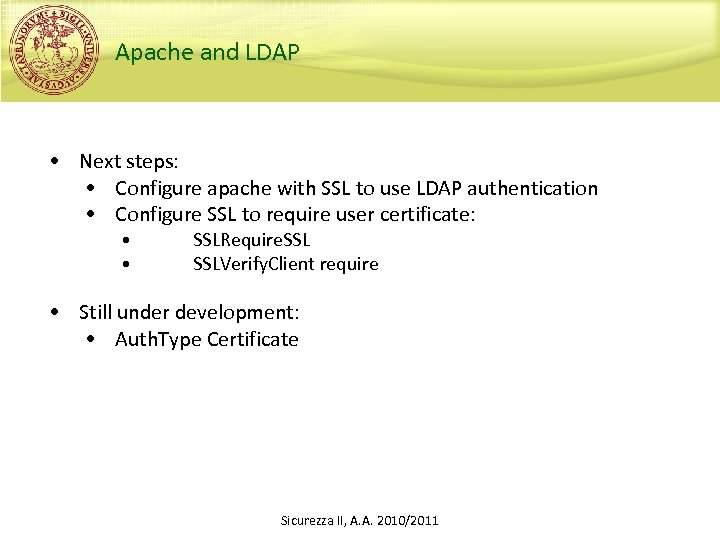 Apache and LDAP • Next steps: • Configure apache with SSL to use LDAP authentication • Configure SSL to require user certificate: • • SSLRequire. SSLVerify. Client require • Still under development: • Auth. Type Certificate Sicurezza II, A. A. 2010/2011
Apache and LDAP • Next steps: • Configure apache with SSL to use LDAP authentication • Configure SSL to require user certificate: • • SSLRequire. SSLVerify. Client require • Still under development: • Auth. Type Certificate Sicurezza II, A. A. 2010/2011
 Apache and LDAP • Create a PHP script to verify the user certificate: function der 2 pem($certificate) { $beginpem = "-----BEGIN CERTIFICATE-----n"; $endpem = "-----END CERTIFICATE-----"; $result = ""; $certificate = base 64_encode($certificate); for ($i=0; $i<20; $i++) {$result. = substr($certificate, $i*64, 64). "n"; } return $beginpem. $result. $endpem; } // Build the PEM string. $pemdata = der 2 pem($certificate); // Get a certificate resource from the PEM string. $cert = openssl_x 509_read( $pemdata ); // Parse the resource and print out the contents. $cert_data = openssl_x 509_parse( $cert ); echo '
Apache and LDAP • Create a PHP script to verify the user certificate: function der 2 pem($certificate) { $beginpem = "-----BEGIN CERTIFICATE-----n"; $endpem = "-----END CERTIFICATE-----"; $result = ""; $certificate = base 64_encode($certificate); for ($i=0; $i<20; $i++) {$result. = substr($certificate, $i*64, 64). "n"; } return $beginpem. $result. $endpem; } // Build the PEM string. $pemdata = der 2 pem($certificate); // Get a certificate resource from the PEM string. $cert = openssl_x 509_read( $pemdata ); // Parse the resource and print out the contents. $cert_data = openssl_x 509_parse( $cert ); echo '
LDAP Certificate Credentials: '. $cert_data['name']; echo '
Client Certificate Credentials: '. $_SERVER["SSL_CLIENT_S_DN"]; // all done? clean up openssl_x 509_free( $cert ); Sicurezza II, A. A. 2010/2011
 Sicurezza II A. A. 2010 -2011 LDAP Grazie per l’attenzione! Speaker: André Panisson, Ph. D student Università degli Studi di Torino, Computer Science Department Corso Svizzera, 185 – 10149, Torino, Italy panisson@di. unito. it Sicurezza II, A. A. 2010/2011
Sicurezza II A. A. 2010 -2011 LDAP Grazie per l’attenzione! Speaker: André Panisson, Ph. D student Università degli Studi di Torino, Computer Science Department Corso Svizzera, 185 – 10149, Torino, Italy panisson@di. unito. it Sicurezza II, A. A. 2010/2011
 © 2009 by André Panisson. Permission to make digital or hard copies of part or all of this material is currently granted without fee provided that copies are made only for personal or classroom use, are not distributed for profit or commercial advantage, and that new copies bear this notice and the full citation. Sicurezza II, A. A. 2010/2011
© 2009 by André Panisson. Permission to make digital or hard copies of part or all of this material is currently granted without fee provided that copies are made only for personal or classroom use, are not distributed for profit or commercial advantage, and that new copies bear this notice and the full citation. Sicurezza II, A. A. 2010/2011


