dd6873dfa7c5fdf6e28530453eb1820f.ppt
- Количество слайдов: 33
 SHIELDS: metrics, tools and Internet services to improve security in application developments Dr. Domenico Rotondi TXT e-solutions Sp. A Italy OWASP-Day III Centro di Competenza ICT-Puglia - Dipartimento di Informatica Università degli Studi di Bari 23 rd February 2009 - Bari (Italy) Copyright © 2009 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License. The OWASP Foundation http: //www. owasp. org
SHIELDS: metrics, tools and Internet services to improve security in application developments Dr. Domenico Rotondi TXT e-solutions Sp. A Italy OWASP-Day III Centro di Competenza ICT-Puglia - Dipartimento di Informatica Università degli Studi di Bari 23 rd February 2009 - Bari (Italy) Copyright © 2009 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License. The OWASP Foundation http: //www. owasp. org
 Summary Software Development & Security Why SHIELDS Approach SHIELDS Expected Impacts & Outcomes SHIELDS Consortium TXT interest in SHIELDS and OWASP SHIELDS Summary Data OWASP Day III – 23 rd , February 2009 O WASP-Italy
Summary Software Development & Security Why SHIELDS Approach SHIELDS Expected Impacts & Outcomes SHIELDS Consortium TXT interest in SHIELDS and OWASP SHIELDS Summary Data OWASP Day III – 23 rd , February 2009 O WASP-Italy
 Software Development & Security Software vulnerabilities becoming critical due to: Law/regulation (Sarbanes-Oxley Act, Health Insurance Portability and Accountability Act, Online Privacy Protection Act, Privacy Protection, …) Direct economic losses (data breach recovery $140/record source : Ponemon Institute survey) Business reputation damage Customers productivity losses (downtime, recovery, …) Certification Programmes (e. g. Microsoft Dynamics Industry Solutions Initiative) … OWASP Day III – 23 rd , February 2009 O WASP-Italy
Software Development & Security Software vulnerabilities becoming critical due to: Law/regulation (Sarbanes-Oxley Act, Health Insurance Portability and Accountability Act, Online Privacy Protection Act, Privacy Protection, …) Direct economic losses (data breach recovery $140/record source : Ponemon Institute survey) Business reputation damage Customers productivity losses (downtime, recovery, …) Certification Programmes (e. g. Microsoft Dynamics Industry Solutions Initiative) … OWASP Day III – 23 rd , February 2009 O WASP-Italy
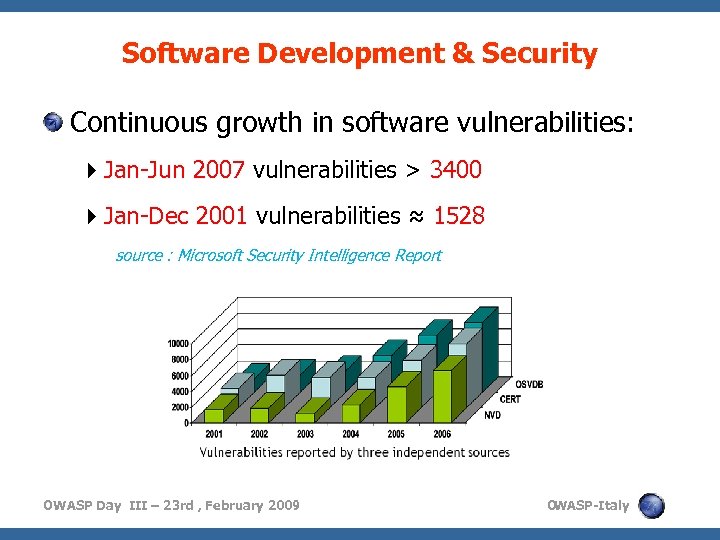 Software Development & Security Continuous growth in software vulnerabilities: Jan-Jun 2007 vulnerabilities > 3400 Jan-Dec 2001 vulnerabilities ≈ 1528 source : Microsoft Security Intelligence Report OWASP Day III – 23 rd , February 2009 O WASP-Italy
Software Development & Security Continuous growth in software vulnerabilities: Jan-Jun 2007 vulnerabilities > 3400 Jan-Dec 2001 vulnerabilities ≈ 1528 source : Microsoft Security Intelligence Report OWASP Day III – 23 rd , February 2009 O WASP-Italy
 Software Development & Security industry is becoming more efficient: Security-enhanced SW Development Life Cycle (Microsoft SDL-SD 3 Framework, OWASP CLASP, …) Improved code scanning tools Fuzz testing techniques & tools … OWASP Day III – 23 rd , February 2009 O WASP-Italy
Software Development & Security industry is becoming more efficient: Security-enhanced SW Development Life Cycle (Microsoft SDL-SD 3 Framework, OWASP CLASP, …) Improved code scanning tools Fuzz testing techniques & tools … OWASP Day III – 23 rd , February 2009 O WASP-Italy
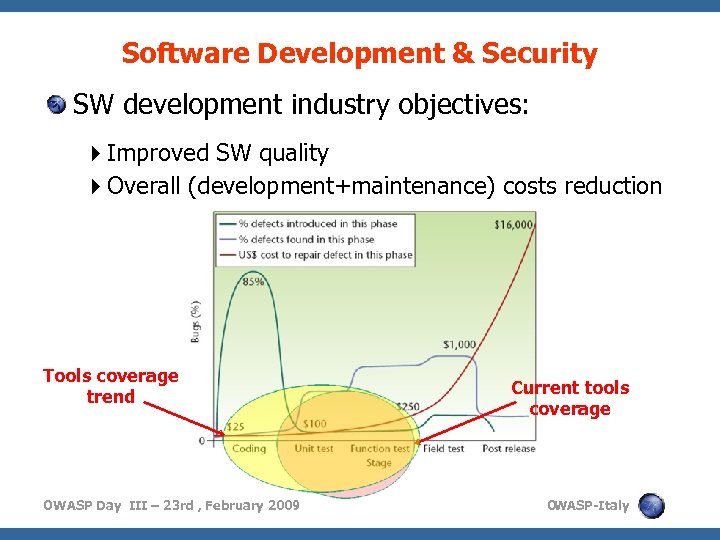 Software Development & Security SW development industry objectives: Improved SW quality Overall (development+maintenance) costs reduction Tools coverage trend OWASP Day III – 23 rd , February 2009 Current tools coverage O WASP-Italy
Software Development & Security SW development industry objectives: Improved SW quality Overall (development+maintenance) costs reduction Tools coverage trend OWASP Day III – 23 rd , February 2009 Current tools coverage O WASP-Italy
 Software Development & Security First results: Security-enhanced SW Development Life Cycle Guidelines (OWASP: Guide to Building Secure Web Applications, Testing Guide, Code Review Guide, …) Checklists (e. g. : Microsoft ASP. NET 2. 0 Security Checklist, OWASP Top Ten Project, …) Security training/awareness Specific/improved tools More secure code libraries (e. g. : OWASP Enterprise Security API, Microsoft security-enhanced versions of CRT functions, …) OWASP Day III – 23 rd , February 2009 O WASP-Italy
Software Development & Security First results: Security-enhanced SW Development Life Cycle Guidelines (OWASP: Guide to Building Secure Web Applications, Testing Guide, Code Review Guide, …) Checklists (e. g. : Microsoft ASP. NET 2. 0 Security Checklist, OWASP Top Ten Project, …) Security training/awareness Specific/improved tools More secure code libraries (e. g. : OWASP Enterprise Security API, Microsoft security-enhanced versions of CRT functions, …) OWASP Day III – 23 rd , February 2009 O WASP-Italy
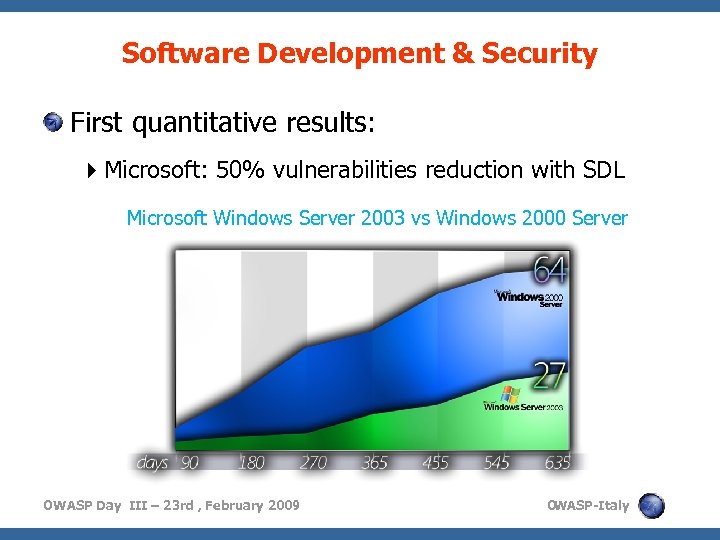 Software Development & Security First quantitative results: Microsoft: 50% vulnerabilities reduction with SDL Microsoft Windows Server 2003 vs Windows 2000 Server OWASP Day III – 23 rd , February 2009 O WASP-Italy
Software Development & Security First quantitative results: Microsoft: 50% vulnerabilities reduction with SDL Microsoft Windows Server 2003 vs Windows 2000 Server OWASP Day III – 23 rd , February 2009 O WASP-Italy
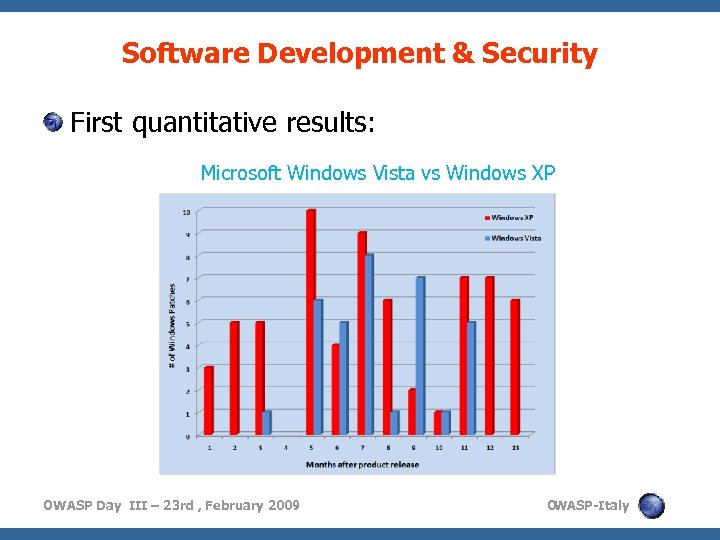 Software Development & Security First quantitative results: Microsoft Windows Vista vs Windows XP OWASP Day III – 23 rd , February 2009 O WASP-Italy
Software Development & Security First quantitative results: Microsoft Windows Vista vs Windows XP OWASP Day III – 23 rd , February 2009 O WASP-Italy
 Why SHIELDS? OWASP Day III – 23 rd , February 2009 O WASP-Italy
Why SHIELDS? OWASP Day III – 23 rd , February 2009 O WASP-Italy
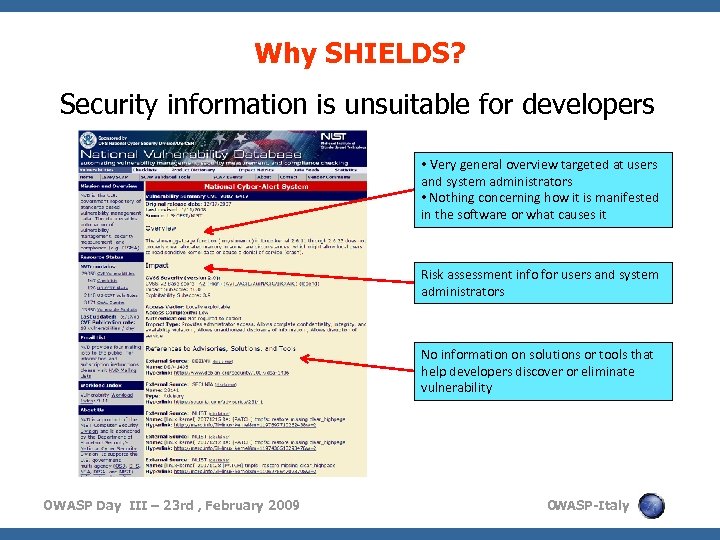 Why SHIELDS? Security information is unsuitable for developers • Very general overview targeted at users and system administrators • Nothing concerning how it is manifested in the software or what causes it Risk assessment info for users and system administrators No information on solutions or tools that help developers discover or eliminate vulnerability OWASP Day III – 23 rd , February 2009 O WASP-Italy
Why SHIELDS? Security information is unsuitable for developers • Very general overview targeted at users and system administrators • Nothing concerning how it is manifested in the software or what causes it Risk assessment info for users and system administrators No information on solutions or tools that help developers discover or eliminate vulnerability OWASP Day III – 23 rd , February 2009 O WASP-Italy
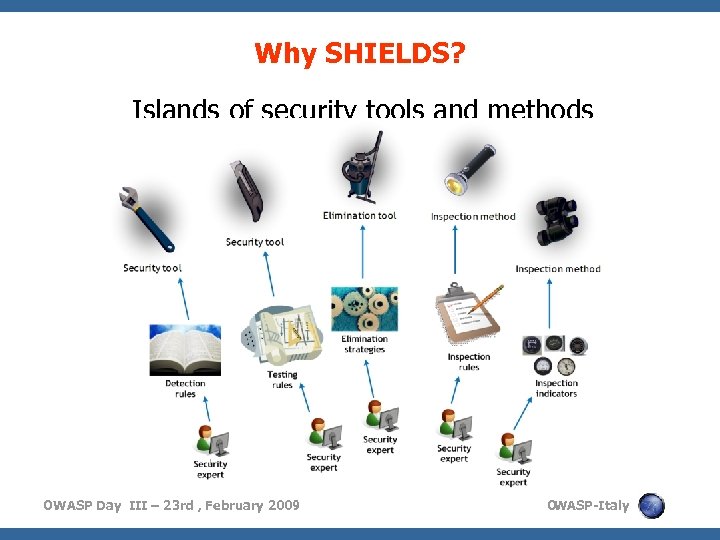 Why SHIELDS? Islands of security tools and methods OWASP Day III – 23 rd , February 2009 O WASP-Italy
Why SHIELDS? Islands of security tools and methods OWASP Day III – 23 rd , February 2009 O WASP-Italy
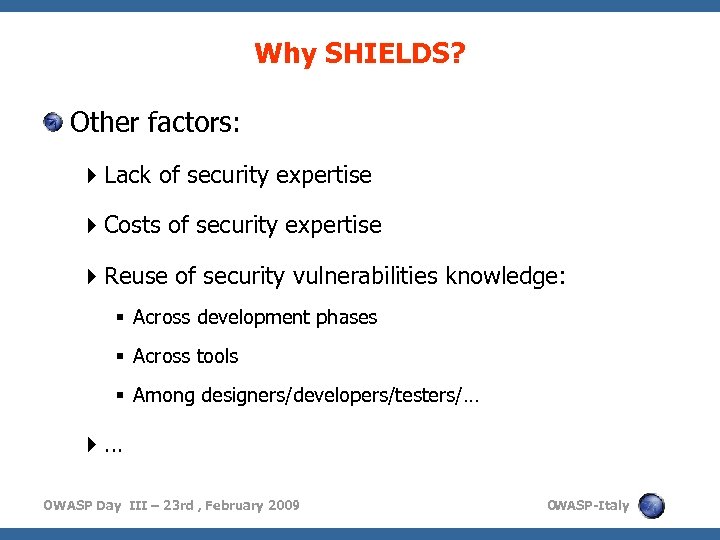 Why SHIELDS? Other factors: Lack of security expertise Costs of security expertise Reuse of security vulnerabilities knowledge: Across development phases Across tools Among designers/developers/testers/… … OWASP Day III – 23 rd , February 2009 O WASP-Italy
Why SHIELDS? Other factors: Lack of security expertise Costs of security expertise Reuse of security vulnerabilities knowledge: Across development phases Across tools Among designers/developers/testers/… … OWASP Day III – 23 rd , February 2009 O WASP-Italy
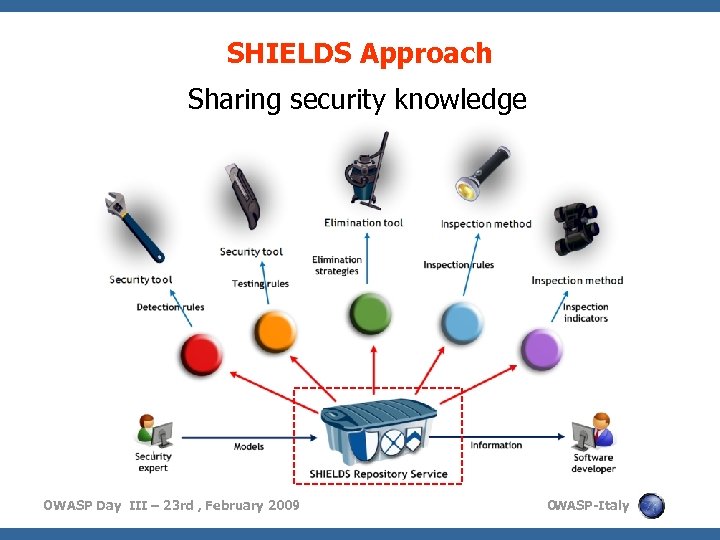 SHIELDS Approach Sharing security knowledge OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Approach Sharing security knowledge OWASP Day III – 23 rd , February 2009 O WASP-Italy
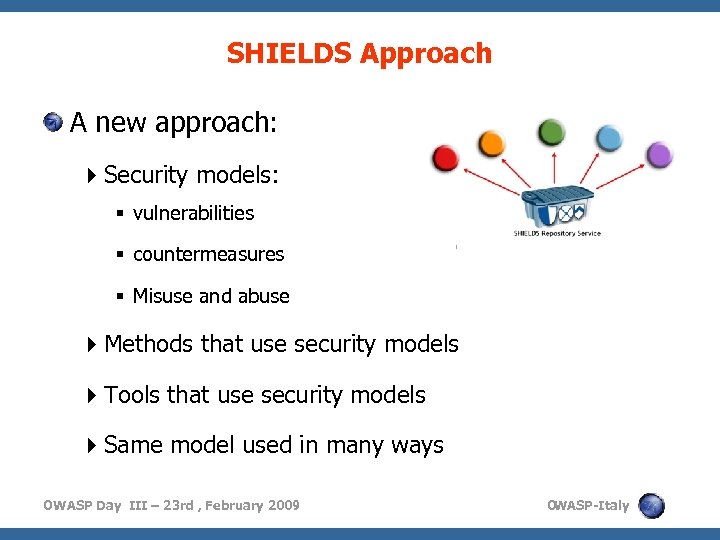 SHIELDS Approach A new approach: Security models: vulnerabilities countermeasures Misuse and abuse Methods that use security models Tools that use security models Same model used in many ways OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Approach A new approach: Security models: vulnerabilities countermeasures Misuse and abuse Methods that use security models Tools that use security models Same model used in many ways OWASP Day III – 23 rd , February 2009 O WASP-Italy
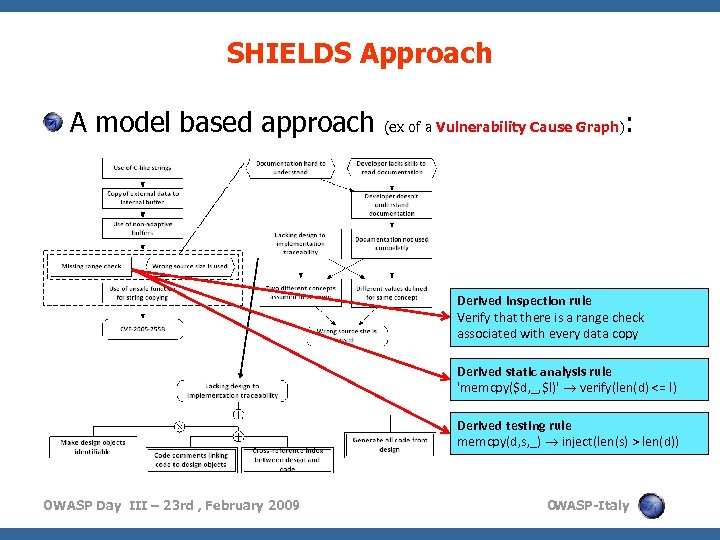 SHIELDS Approach A model based approach (ex of a Vulnerability Cause Graph) : Derived inspection rule Verify that there is a range check associated with every data copy Derived static analysis rule 'memcpy($d, _, $l)' verify(len(d) <= l) Derived testing rule memcpy(d, s, _) inject(len(s) > len(d)) OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Approach A model based approach (ex of a Vulnerability Cause Graph) : Derived inspection rule Verify that there is a range check associated with every data copy Derived static analysis rule 'memcpy($d, _, $l)' verify(len(d) <= l) Derived testing rule memcpy(d, s, _) inject(len(s) > len(d)) OWASP Day III – 23 rd , February 2009 O WASP-Italy
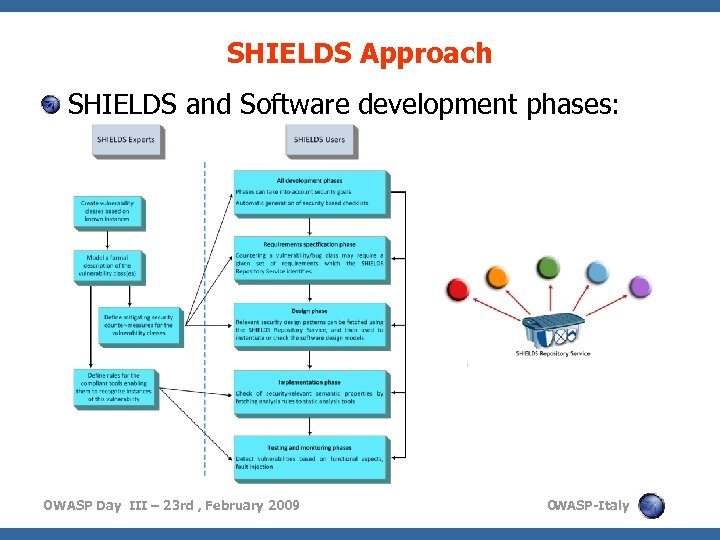 SHIELDS Approach SHIELDS and Software development phases: OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Approach SHIELDS and Software development phases: OWASP Day III – 23 rd , February 2009 O WASP-Italy
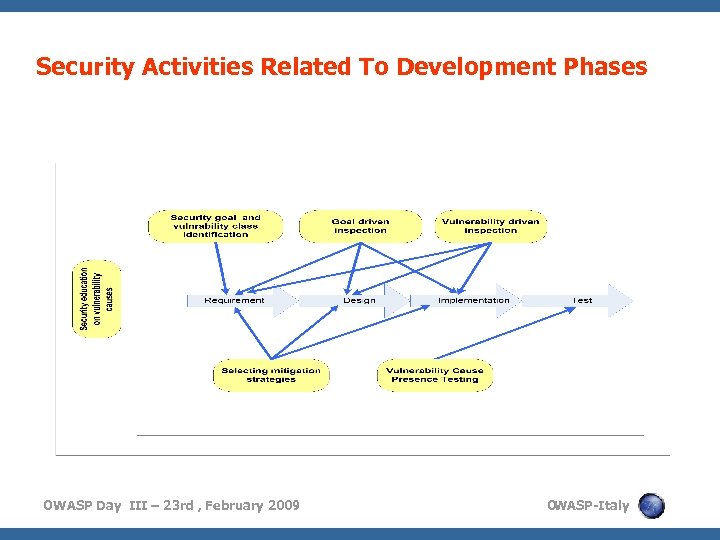 Security Activities Related To Development Phases OWASP Day III – 23 rd , February 2009 O WASP-Italy
Security Activities Related To Development Phases OWASP Day III – 23 rd , February 2009 O WASP-Italy
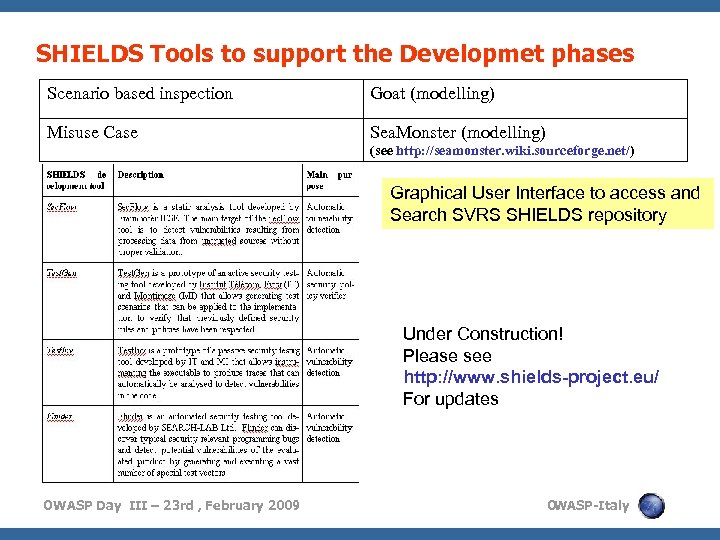 SHIELDS Tools to support the Developmet phases Scenario based inspection Goat (modelling) Misuse Case Sea. Monster (modelling) (see http: //seamonster. wiki. sourceforge. net/) Graphical User Interface to access and Search SVRS SHIELDS repository Under Construction! Please see http: //www. shields-project. eu/ For updates OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Tools to support the Developmet phases Scenario based inspection Goat (modelling) Misuse Case Sea. Monster (modelling) (see http: //seamonster. wiki. sourceforge. net/) Graphical User Interface to access and Search SVRS SHIELDS repository Under Construction! Please see http: //www. shields-project. eu/ For updates OWASP Day III – 23 rd , February 2009 O WASP-Italy
 SHIELDS Approach SHIELDS advantages: Reduced/no duplication of effort: Every update can potentially affect all tools SHIELDS reported vulnerabilities can impact all phases Higher assurance: Tools can quickly acquire knowledge to face new vulnerabilities Improved software quality: Developers get more and better security information Developers improve their security expertise … OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Approach SHIELDS advantages: Reduced/no duplication of effort: Every update can potentially affect all tools SHIELDS reported vulnerabilities can impact all phases Higher assurance: Tools can quickly acquire knowledge to face new vulnerabilities Improved software quality: Developers get more and better security information Developers improve their security expertise … OWASP Day III – 23 rd , February 2009 O WASP-Italy
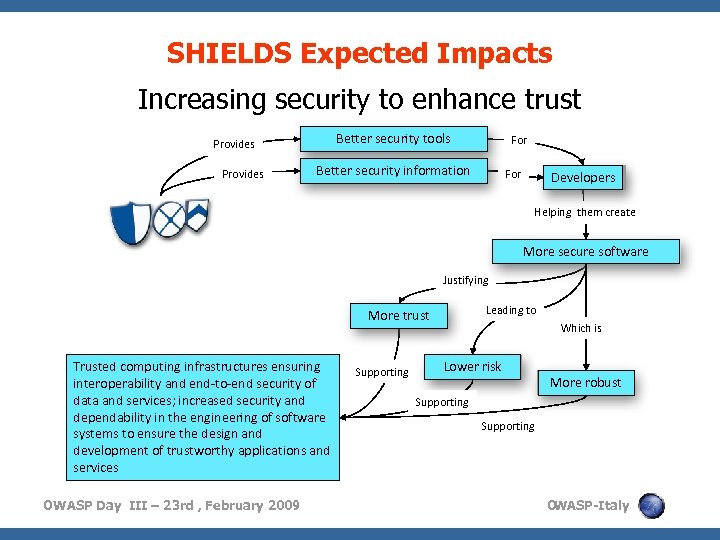 SHIELDS Expected Impacts Increasing security to enhance trust Better security tools Provides For Better security information For Developers Helping them create More secure software Justifying Leading to More trust Trusted computing infrastructures ensuring interoperability and end-to-end security of data and services; increased security and dependability in the engineering of software systems to ensure the design and development of trustworthy applications and services OWASP Day III – 23 rd , February 2009 Supporting Which is Lower risk More robust Supporting O WASP-Italy
SHIELDS Expected Impacts Increasing security to enhance trust Better security tools Provides For Better security information For Developers Helping them create More secure software Justifying Leading to More trust Trusted computing infrastructures ensuring interoperability and end-to-end security of data and services; increased security and dependability in the engineering of software systems to ensure the design and development of trustworthy applications and services OWASP Day III – 23 rd , February 2009 Supporting Which is Lower risk More robust Supporting O WASP-Italy
 SHIELDS Expected Outcomes SHIELDS Repository Service: A network accessible service providing: guidelines Models (vulnerabilities, countermeasures, Misuse and abuse) Tools Security tools: Partners provided (Search-Lab, Montimage, Fraunhofer) … OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Expected Outcomes SHIELDS Repository Service: A network accessible service providing: guidelines Models (vulnerabilities, countermeasures, Misuse and abuse) Tools Security tools: Partners provided (Search-Lab, Montimage, Fraunhofer) … OWASP Day III – 23 rd , February 2009 O WASP-Italy
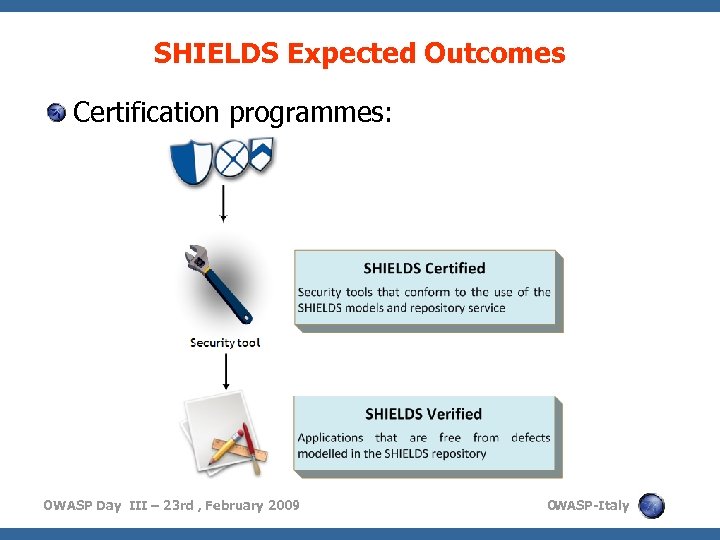 SHIELDS Expected Outcomes Certification programmes: OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Expected Outcomes Certification programmes: OWASP Day III – 23 rd , February 2009 O WASP-Italy
 SHIELDS Consortium OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Consortium OWASP Day III – 23 rd , February 2009 O WASP-Italy
 TXT interest in SHIELDS TXT e-solutions Spa: TXT (www. txtgroup. com) is specialized in modular software products and solutions for: Demand & Supply Chain Management Content Management TXT presence: OWASP Day III – 23 rd , February 2009 O WASP-Italy
TXT interest in SHIELDS TXT e-solutions Spa: TXT (www. txtgroup. com) is specialized in modular software products and solutions for: Demand & Supply Chain Management Content Management TXT presence: OWASP Day III – 23 rd , February 2009 O WASP-Italy
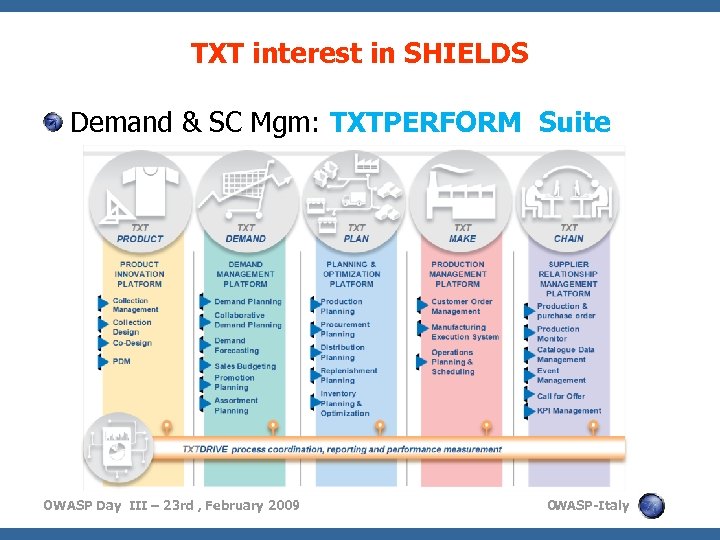 TXT interest in SHIELDS Demand & SC Mgm: TXTPERFORM Suite OWASP Day III – 23 rd , February 2009 O WASP-Italy
TXT interest in SHIELDS Demand & SC Mgm: TXTPERFORM Suite OWASP Day III – 23 rd , February 2009 O WASP-Italy
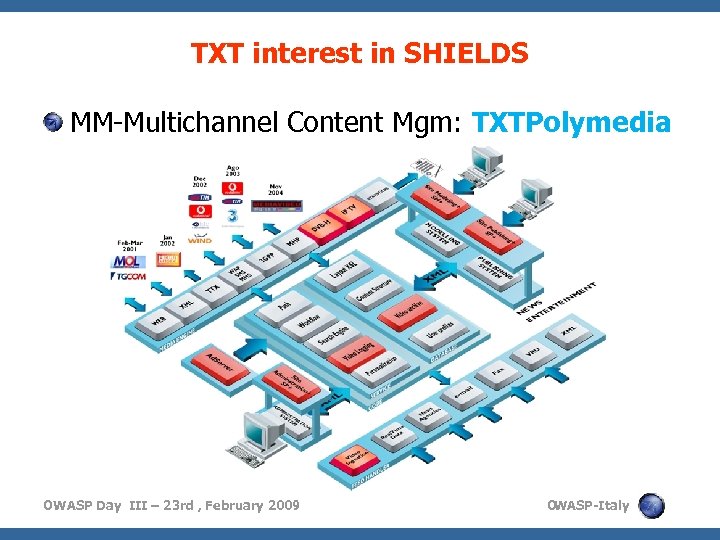 TXT interest in SHIELDS MM-Multichannel Content Mgm: TXTPolymedia OWASP Day III – 23 rd , February 2009 O WASP-Italy
TXT interest in SHIELDS MM-Multichannel Content Mgm: TXTPolymedia OWASP Day III – 23 rd , February 2009 O WASP-Italy
 TXT interest in SHIELDS TXT Software Development activities: Internal: TXTPerform: whole Software Development Lifecycle TXTPolymedia: whole Software Development Lifecycle External: SW Quality Assurance (not security related): mainly for M&T customers Ad-hoc development ISO 9001/2000 certified processes! OWASP Day III – 23 rd , February 2009 O WASP-Italy
TXT interest in SHIELDS TXT Software Development activities: Internal: TXTPerform: whole Software Development Lifecycle TXTPolymedia: whole Software Development Lifecycle External: SW Quality Assurance (not security related): mainly for M&T customers Ad-hoc development ISO 9001/2000 certified processes! OWASP Day III – 23 rd , February 2009 O WASP-Italy
 TXT interest in SHIELDS Languages & platforms: TXTPerform: C++, C# and Microsoft. Net Framework 3. 0 Microsoft SQL Server, Oracle TXTPolymedia: Java Open Source platforms (Apache, JBOSS, …) Microsoft SQL Server, Oracle, … TXT Typical SW company with all dvp problems OWASP Day III – 23 rd , February 2009 O WASP-Italy
TXT interest in SHIELDS Languages & platforms: TXTPerform: C++, C# and Microsoft. Net Framework 3. 0 Microsoft SQL Server, Oracle TXTPolymedia: Java Open Source platforms (Apache, JBOSS, …) Microsoft SQL Server, Oracle, … TXT Typical SW company with all dvp problems OWASP Day III – 23 rd , February 2009 O WASP-Italy
 TXT interest in SHIELDS Development lifecycles revised since 2005: to address security issues: Based on Microsoft Trustworthy Computing Security Development Lifecycle Adopted for all products’ major releases to certify TXT products: Microsoft Industry Builder Initiative (IBI): TXTDemand certified since 2006 Microsoft Dynamics Industry Solutions program (MDIS): TXTPerform 2008 certified in January 2009 … OWASP Day III – 23 rd , February 2009 O WASP-Italy
TXT interest in SHIELDS Development lifecycles revised since 2005: to address security issues: Based on Microsoft Trustworthy Computing Security Development Lifecycle Adopted for all products’ major releases to certify TXT products: Microsoft Industry Builder Initiative (IBI): TXTDemand certified since 2006 Microsoft Dynamics Industry Solutions program (MDIS): TXTPerform 2008 certified in January 2009 … OWASP Day III – 23 rd , February 2009 O WASP-Italy
 SHIELDS - OWASP SHIELDS contributions: SHIELDS is in line with OWASP goals SHIELDS can contribute to the OWASP projects OWASP contributions to SHIELDS: SHIELDS needs input from the OWASP specialized community SHIELDS needs feedbacks from the OWASP community SHIELDS needs support to improve its work SHIELDS needs support to validate its work OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS - OWASP SHIELDS contributions: SHIELDS is in line with OWASP goals SHIELDS can contribute to the OWASP projects OWASP contributions to SHIELDS: SHIELDS needs input from the OWASP specialized community SHIELDS needs feedbacks from the OWASP community SHIELDS needs support to improve its work SHIELDS needs support to validate its work OWASP Day III – 23 rd , February 2009 O WASP-Italy
 SHIELDS Project Relevant Data Project data: EU FP 7 Theme: ICT-2007. 1. 4: Secure dependable and trusted infrastructures Type: Collaborative Project (STREP) Duration: 30 months Start: January 1, 2008 SHIELDS contacts: Coordinator: Professor Nahid Shahmehri (Linköpings universitet, nahsh@ida. liu. se) Dissemination Manager: Alessandra Bagnato (TXT e-solutions Spa, alessandra. bagnato@txt. it) Project Web site: http: //www. shields-project. eu OWASP Day III – 23 rd , February 2009 O WASP-Italy
SHIELDS Project Relevant Data Project data: EU FP 7 Theme: ICT-2007. 1. 4: Secure dependable and trusted infrastructures Type: Collaborative Project (STREP) Duration: 30 months Start: January 1, 2008 SHIELDS contacts: Coordinator: Professor Nahid Shahmehri (Linköpings universitet, nahsh@ida. liu. se) Dissemination Manager: Alessandra Bagnato (TXT e-solutions Spa, alessandra. bagnato@txt. it) Project Web site: http: //www. shields-project. eu OWASP Day III – 23 rd , February 2009 O WASP-Italy
 Thanks for your attention! OWASP Day III – 23 rd , February 2009 O WASP-Italy
Thanks for your attention! OWASP Day III – 23 rd , February 2009 O WASP-Italy


