1302a937a9d5c944552522cbec7c5c12.ppt
- Количество слайдов: 29

Shibboleth Update a. k. a. “shibble-ware” Michael R Gettes, Duke University On behalf of the project team November 2004

What is Shibboleth? (Biblical) • A word which was made the criterion by which to distinguish the Ephraimites from the Gileadites. The Ephraimites, not being able to pronounce “sh”, called the word sibboleth. See --Judges xii. • Hence, the criterion, test, or watchword of a party; a party cry or pet phrase. Webster's Revised Unabridged Dictionary (1913)
What is Shibboleth? (modern era) • An initiative to develop an architecture and policy framework supporting the sharing – between domains -of secured web resources and services • A project delivering an open source implementation of the architecture and framework • Deliverables: –Software for Identity Provider (Origins/campuses) –Software for Service Providers (targets/vendors) –Operational Federations (scalable trust)

So… What is Shibboleth? • A Web Single-Signon System (SSO)? • An Access Control Mechanism for Attributes? • A Standard Interface and Vocabulary for Attributes? • A Standard for Adding Authn and Authz to Applications?
Attribute-based Authorization • Identity-based approach – The identity of a prospective user is passed to the controlled resource and is used to determine (perhaps with requests for additional attributes about the user) whether to permit access. – This approach requires the user to trust the target to protect privacy. • Attribute-based approach – Attributes are exchanged about a prospective user until the controlled resource has sufficient information to make a decision. – This approach does not degrade privacy.

How Does it Work? Hmmmm…. It’s magic. : -)
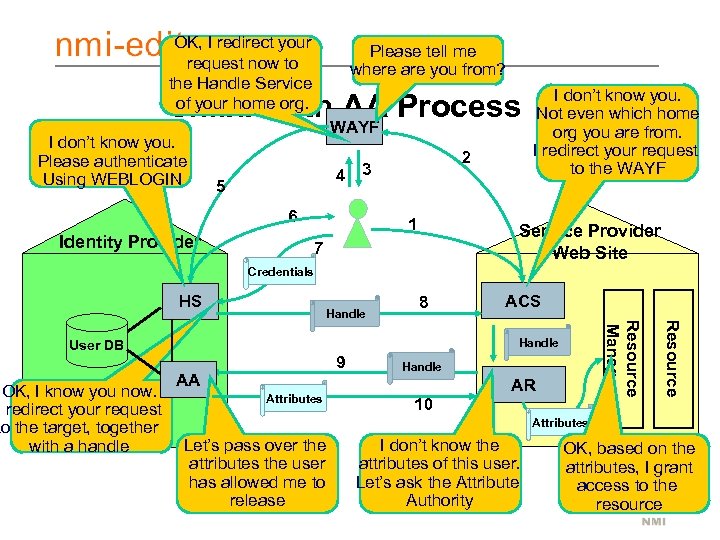
OK, I redirect your request now to the Handle Service of your home org. Please tell me where are you from? Shibboleth. WAYF Process AA I don’t know you. Please authenticate Using WEBLOGIN 2 4 3 5 6 Identity Provider 1 I don’t know you. Not even which home org you are from. I redirect your request to the WAYF Service Provider Web Site 7 Credentials HS ACS 9 AA Attributes Handle AR 10 Resource Handle User DB OK, I know you now. I redirect your request to the target, together with a handle 8 Resource Manager Handle Attributes Let’s pass over the attributes the user has allowed me to release I don’t know the attributes of this user. Let’s ask the Attribute Authority OK, based on the attributes, I grant access to the resource
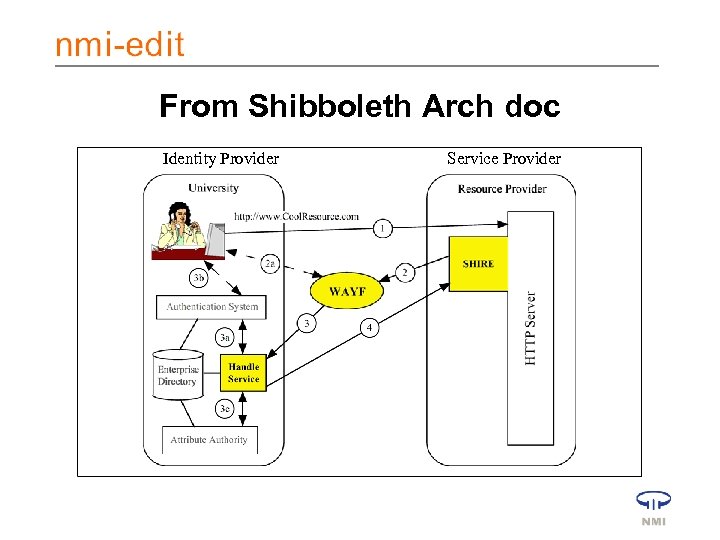
From Shibboleth Arch doc Identity Provider Service Provider
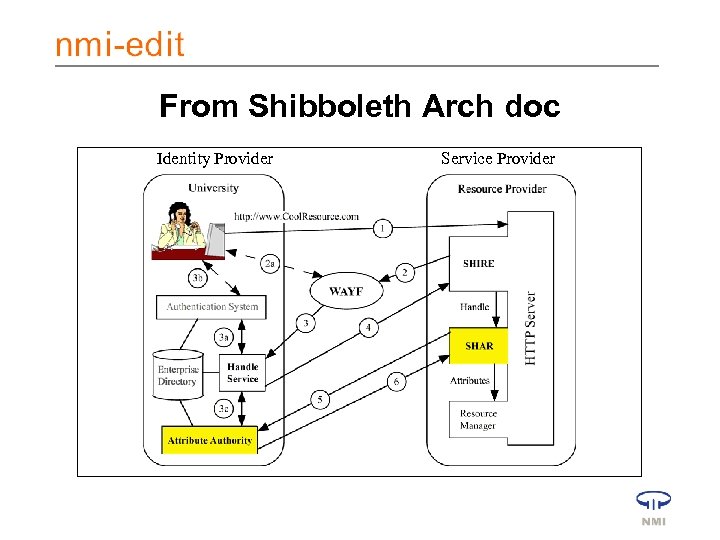
From Shibboleth Arch doc Identity Provider Service Provider
WAYF a second! • WAYF – Provides NO, ZERO, NADA, ZIP security – It does NOT represent the federation – Federation != WAYF – WAYF != Federation – Consideration for WAYF security is a future item • WAYF is just a simple navigation tool
Demo! • http: //shibboleth. blackboard. com/
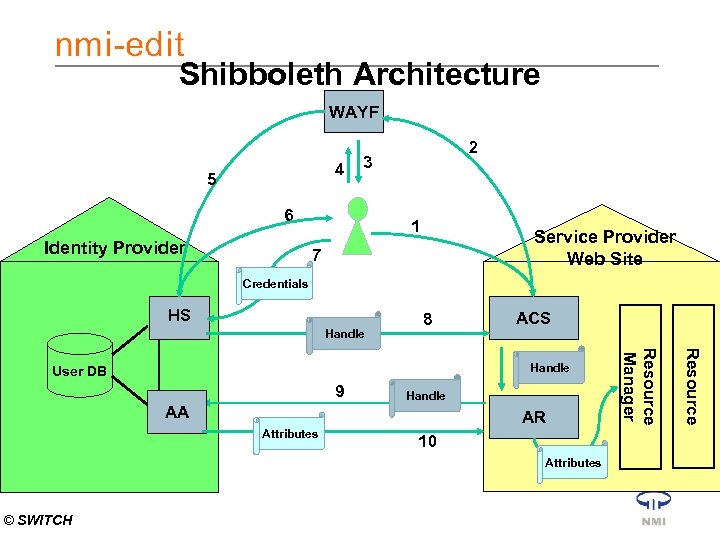
Shibboleth Architecture WAYF 4 5 6 Identity Provider 2 3 1 Service Provider Web Site 7 Credentials HS Handle 8 ACS Handle AA AR Attributes 10 Attributes © SWITCH Resource 9 Resource Manager Handle User DB
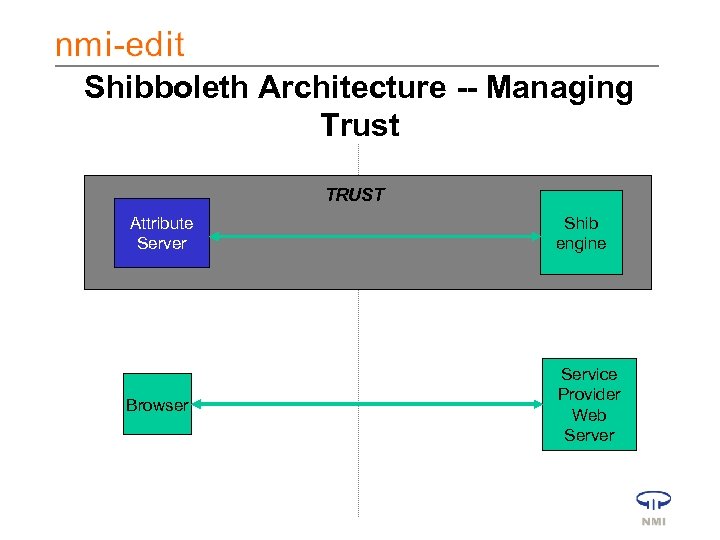
Shibboleth Architecture -- Managing Trust TRUST Attribute Server Shib engine Browser Service Provider Web Server
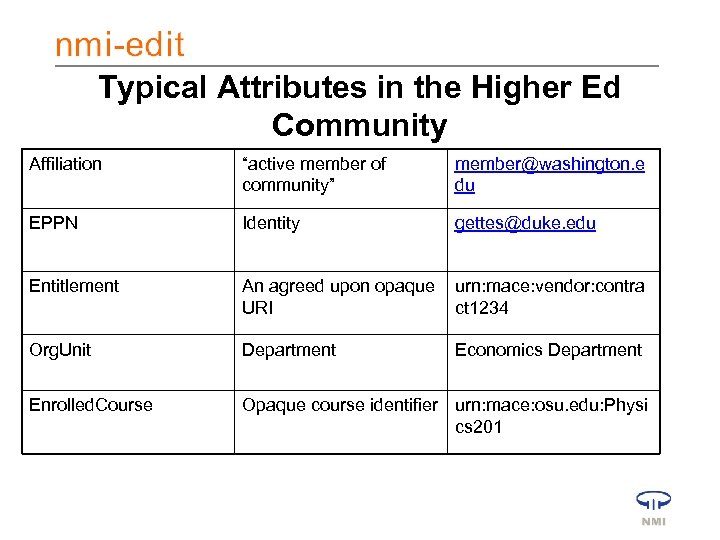
Typical Attributes in the Higher Ed Community Affiliation “active member of community” member@washington. e du EPPN Identity gettes@duke. edu Entitlement An agreed upon opaque URI urn: mace: vendor: contra ct 1234 Org. Unit Department Economics Department Enrolled. Course Opaque course identifier urn: mace: osu. edu: Physi cs 201

Target – Managing Attribute Acceptance • • Rules that define who can assert what…. . MIT can assert student@mit. edu Chicago can assert staff@argonne. gov Brown CANNOT assert student@mit. edu • Important for entitlement values

What are federations? • Associations of enterprises that come together to exchange information about their users and resources in order to enable collaborations and transactions • Built on the premise of –Initially “Authenticate locally, act globally” –Now, “Enroll and authenticate and attribute locally, act federally. ” • Federation provides only modest operational support and consistency in how members communicate with each other • Enterprises (and users) retain control over what attributes are released to a resource; the resources retain control (though they may delegate) over the authorization decision. • Over time, this will all change…

In. Common federation • First US Higher Ed Federation • Precursor federation, In. Queue, a proving ground or testbed and will feed into In. Common after organizations are deemed interoperable. • http: //www. incommonfederation. org
Service Providers http: //shibboleth. internet 2. edu/ And see the link on the left labeled “Shib-enabled Service Providers”

So… What is Shibboleth? • A Web Single-Signon System (SSO)? • An Access Control Mechanism for Attributes? • A Standard Interface and Vocabulary for Attributes? • A Standard for Adding Authn and Authz to Applications?
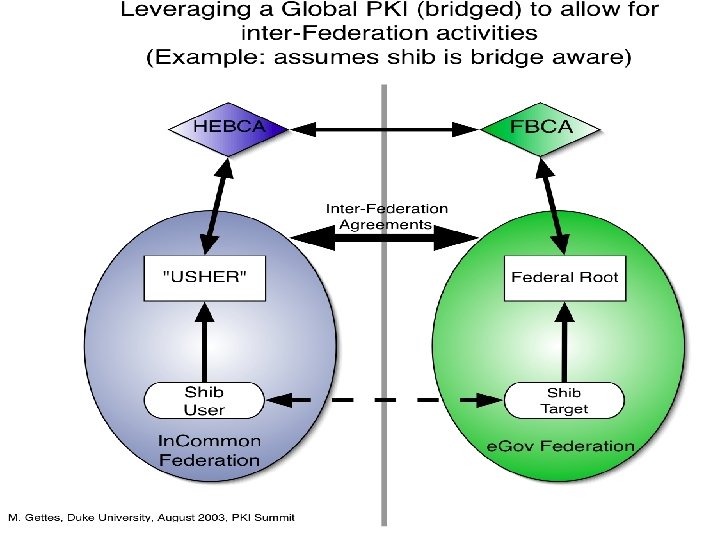
Sample Inter. Federation

Got SHIB?

Inter-Enterprise Authentication • Is Shibboleth authentication? – If so, to what degree? • How does Shibboleth compare to PKI? – PKI basics, no crypto -- just process • Greater understanding of what Shibboleth really brings to the landscape – Knowing what we are doing and why
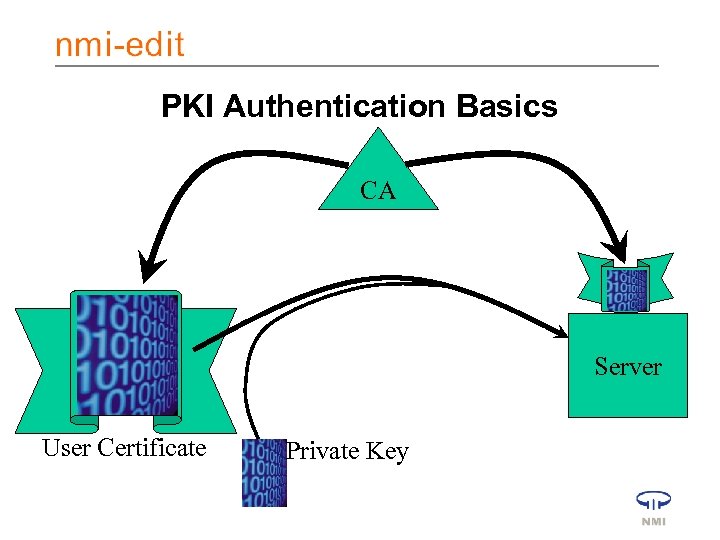
PKI Authentication Basics CA Server User Certificate Private Key
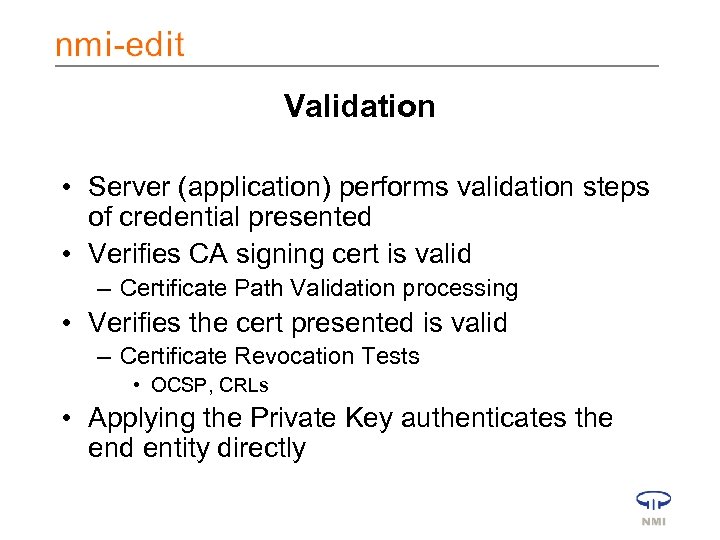
Validation • Server (application) performs validation steps of credential presented • Verifies CA signing cert is valid – Certificate Path Validation processing • Verifies the cert presented is valid – Certificate Revocation Tests • OCSP, CRLs • Applying the Private Key authenticates the end entity directly
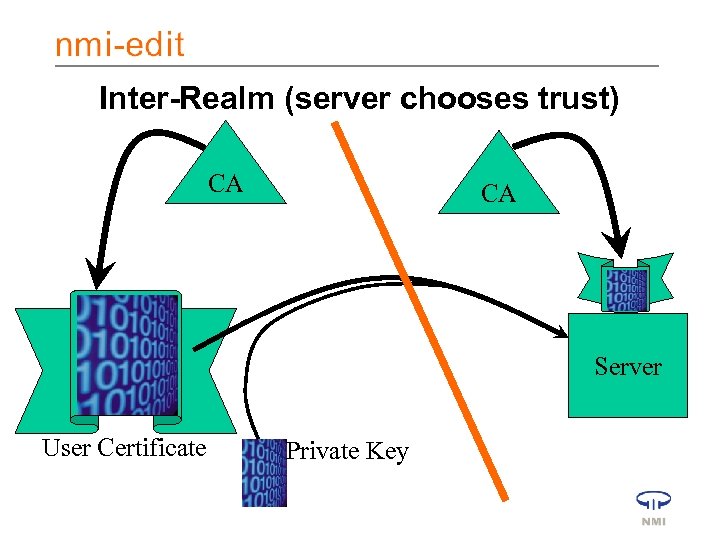
Inter-Realm (server chooses trust) CA CA Server User Certificate Private Key
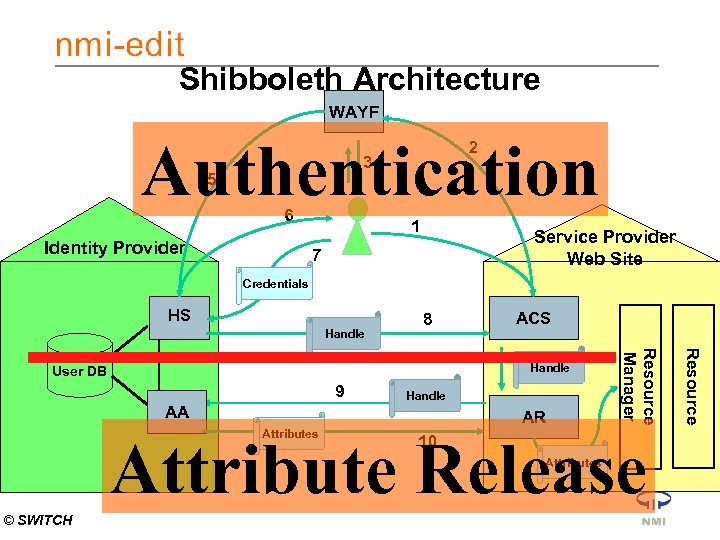
Shibboleth Architecture WAYF Authentication 4 5 6 Identity Provider 2 3 1 Service Provider Web Site 7 Credentials HS Handle 8 ACS Handle AA AR Attributes Attribute Release 10 Attributes © SWITCH Resource 9 Resource Manager Handle User DB
What shib does… • SAML assertion from HS to ACS – The Identity Provider is testifying about the Handle being passed • The ACS performs validation of Id Provider – Like PKI Path Validation (albeit simple) • The Service Provider trusts that the End Entity has been authenticated per the rules of the trust fabric

What shib does… (2) • Are Attributes the result of authentication? • Where does Level of Assurance fit in? – Is Lo. A an attribute or part of auth. N? – Are shib Lo. A and PKI Lo. A different?

• Q & A -- How can we help you?
1302a937a9d5c944552522cbec7c5c12.ppt