134df78fe586a5259d1d746f9a535bbf.ppt
- Количество слайдов: 32
 SHEEO/NCES Network Conference and IPEDS Workshop Kathleen Styles, Chief Privacy Officer, U. S. Department of Education Emily Anthony, National Center for Education Statistics Tod Massa, State Council of Higher Education for Virginia Baron Rodriguez, PTAC Mark Hall, PTAC Tom Szuba, PTAC May 3, 2011
SHEEO/NCES Network Conference and IPEDS Workshop Kathleen Styles, Chief Privacy Officer, U. S. Department of Education Emily Anthony, National Center for Education Statistics Tod Massa, State Council of Higher Education for Virginia Baron Rodriguez, PTAC Mark Hall, PTAC Tom Szuba, PTAC May 3, 2011
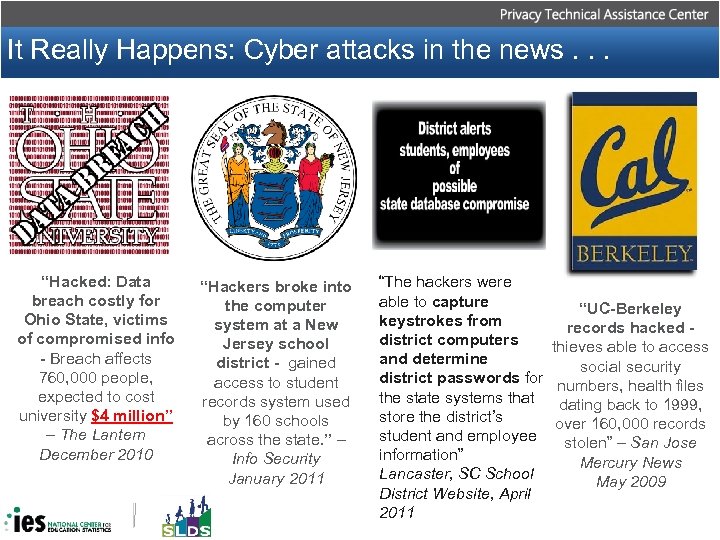 It Really Happens: Cyber attacks in the news. . . “Hacked: Data breach costly for Ohio State, victims of compromised info - Breach affects 760, 000 people, expected to cost university $4 million” – The Lantern December 2010 “Hackers broke into the computer system at a New Jersey school district - gained access to student records system used by 160 schools across the state. ” – Info Security January 2011 “The hackers were able to capture “UC-Berkeley keystrokes from records hacked - district computers thieves able to access and determine social security district passwords for numbers, health files the state systems that dating back to 1999, store the district’s over 160, 000 records student and employee stolen” – San Jose information” Mercury News Lancaster, SC School May 2009 District Website, April 2011
It Really Happens: Cyber attacks in the news. . . “Hacked: Data breach costly for Ohio State, victims of compromised info - Breach affects 760, 000 people, expected to cost university $4 million” – The Lantern December 2010 “Hackers broke into the computer system at a New Jersey school district - gained access to student records system used by 160 schools across the state. ” – Info Security January 2011 “The hackers were able to capture “UC-Berkeley keystrokes from records hacked - district computers thieves able to access and determine social security district passwords for numbers, health files the state systems that dating back to 1999, store the district’s over 160, 000 records student and employee stolen” – San Jose information” Mercury News Lancaster, SC School May 2009 District Website, April 2011
 Privacy, Security, and Confidentiality at USED • The Privacy Technical Assistance Center (PTAC) is one component of USED’s comprehensive privacy initiative, which also includes: - Chief Privacy Officer - Technical Briefs - FERPA Notice of Proposed Rulemaking (NPRM) • Run in conjunction with the NCES SLDS program as an extension of technical assistance efforts: - Webinars, best practice briefs - Site Visits, Technical Assistance Experts, Personnel Exchange Network 3
Privacy, Security, and Confidentiality at USED • The Privacy Technical Assistance Center (PTAC) is one component of USED’s comprehensive privacy initiative, which also includes: - Chief Privacy Officer - Technical Briefs - FERPA Notice of Proposed Rulemaking (NPRM) • Run in conjunction with the NCES SLDS program as an extension of technical assistance efforts: - Webinars, best practice briefs - Site Visits, Technical Assistance Experts, Personnel Exchange Network 3
 Background: NCES • The National Center for Education Statistics (NCES) is the primary federal entity for collecting and analyzing data related to education in the U. S. and other nations. • NCES is located within the U. S. Department of Education and the Institute of Education Sciences. • http: //nces. ed. gov 4
Background: NCES • The National Center for Education Statistics (NCES) is the primary federal entity for collecting and analyzing data related to education in the U. S. and other nations. • NCES is located within the U. S. Department of Education and the Institute of Education Sciences. • http: //nces. ed. gov 4
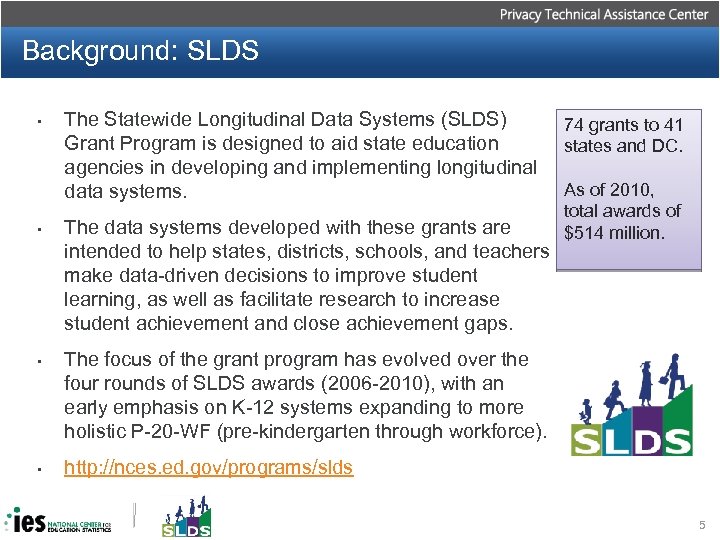 Background: SLDS • The Statewide Longitudinal Data Systems (SLDS) Grant Program is designed to aid state education agencies in developing and implementing longitudinal data systems. • The data systems developed with these grants are intended to help states, districts, schools, and teachers make data-driven decisions to improve student learning, as well as facilitate research to increase student achievement and close achievement gaps. • The focus of the grant program has evolved over the four rounds of SLDS awards (2006 -2010), with an early emphasis on K-12 systems expanding to more holistic P-20 -WF (pre-kindergarten through workforce). • http: //nces. ed. gov/programs/slds 74 grants to 41 states and DC. As of 2010, total awards of $514 million. 5
Background: SLDS • The Statewide Longitudinal Data Systems (SLDS) Grant Program is designed to aid state education agencies in developing and implementing longitudinal data systems. • The data systems developed with these grants are intended to help states, districts, schools, and teachers make data-driven decisions to improve student learning, as well as facilitate research to increase student achievement and close achievement gaps. • The focus of the grant program has evolved over the four rounds of SLDS awards (2006 -2010), with an early emphasis on K-12 systems expanding to more holistic P-20 -WF (pre-kindergarten through workforce). • http: //nces. ed. gov/programs/slds 74 grants to 41 states and DC. As of 2010, total awards of $514 million. 5
 What is PTAC? The Privacy Technical Assistance Center at USED… • A “one-stop” shop for technical assistance related to best practices on privacy and data security • Provides stakeholders with: ü A set of tools, resources, and other opportunities to receive assistance with privacy, security, and confidentiality of longitudinal data systems. ü A means for stakeholders to share their best practices, documents, and other relevant resources in the areas of privacy, security, and confidentiality. ü A focal point for queries and responses to the privacy-related needs of state education agencies (SEAs), local education agencies (LEAs), and institutions of higher education (IHEs) in a confidential, safe environment. ü A set of resources to promote compliance with FERPA and summarize best practices for ensuring the confidentiality and security of personally identifiable information. 6
What is PTAC? The Privacy Technical Assistance Center at USED… • A “one-stop” shop for technical assistance related to best practices on privacy and data security • Provides stakeholders with: ü A set of tools, resources, and other opportunities to receive assistance with privacy, security, and confidentiality of longitudinal data systems. ü A means for stakeholders to share their best practices, documents, and other relevant resources in the areas of privacy, security, and confidentiality. ü A focal point for queries and responses to the privacy-related needs of state education agencies (SEAs), local education agencies (LEAs), and institutions of higher education (IHEs) in a confidential, safe environment. ü A set of resources to promote compliance with FERPA and summarize best practices for ensuring the confidentiality and security of personally identifiable information. 6
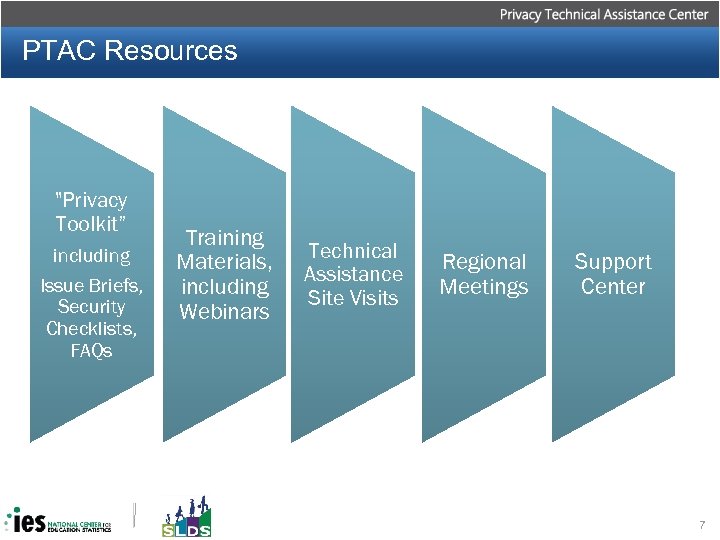 PTAC Resources "Privacy Toolkit” including Issue Briefs, Security Checklists, FAQs Training Materials, including Webinars Technical Assistance Site Visits Regional Meetings Support Center 7
PTAC Resources "Privacy Toolkit” including Issue Briefs, Security Checklists, FAQs Training Materials, including Webinars Technical Assistance Site Visits Regional Meetings Support Center 7
 The SLDS Technical Briefs • This series of Technical Briefs focuses on privacy, confidentiality, and security considerations related to data in student record systems, especially longitudinal data systems. • The briefs are intended to inform practitioners responsible for the development, maintenance, protection, or use of student record data. • Author: Marilyn Seastrom, Chief Statistician and Acting Deputy Commissioner, NCES. • NCES is seeking input and comments on these briefs. If you have any comments or suggestions, please send them to SLDStechbrief@ed. gov. 8
The SLDS Technical Briefs • This series of Technical Briefs focuses on privacy, confidentiality, and security considerations related to data in student record systems, especially longitudinal data systems. • The briefs are intended to inform practitioners responsible for the development, maintenance, protection, or use of student record data. • Author: Marilyn Seastrom, Chief Statistician and Acting Deputy Commissioner, NCES. • NCES is seeking input and comments on these briefs. If you have any comments or suggestions, please send them to SLDStechbrief@ed. gov. 8
 The SLDS Technical Briefs SLDS Technical Brief #1: Basic Concepts and Definitions for Privacy and Confidentiality in Student Education Records ü Discusses basic concepts and definitions that establish a common set of terms related to the protection of personally identifiable information, especially in education records in the Statewide Longitudinal Data Systems (SLDS). ü This Brief also outlines a privacy framework that is tied to Fair Information Practice Principles that have been promulgated in both the United States and international privacy work. 9
The SLDS Technical Briefs SLDS Technical Brief #1: Basic Concepts and Definitions for Privacy and Confidentiality in Student Education Records ü Discusses basic concepts and definitions that establish a common set of terms related to the protection of personally identifiable information, especially in education records in the Statewide Longitudinal Data Systems (SLDS). ü This Brief also outlines a privacy framework that is tied to Fair Information Practice Principles that have been promulgated in both the United States and international privacy work. 9
 The SLDS Technical Briefs 1. Basic Concepts and Definitions for Privacy and Confidentiality in Student Education Records. 2. Data Stewardship: Managing Personally Identifiable Information in Electronic Student Education Records. 3. Statistical Methods for Protecting Personally Identifiable Information in Aggregate Reporting. Now AVAILABLE at http: //nces. ed. gov/programs/ptac/Technical. Briefs. aspx 10
The SLDS Technical Briefs 1. Basic Concepts and Definitions for Privacy and Confidentiality in Student Education Records. 2. Data Stewardship: Managing Personally Identifiable Information in Electronic Student Education Records. 3. Statistical Methods for Protecting Personally Identifiable Information in Aggregate Reporting. Now AVAILABLE at http: //nces. ed. gov/programs/ptac/Technical. Briefs. aspx 10
 The SLDS Technical Briefs 4. Data Access for External Researchers. 5. Electronic Data Security, Protecting PII, and Electronic Student Education Records. 6. Privacy Training: Increasing Awareness of Protections for PII in Student Education Records. 7. Sharing Data Across Sectors. To be released later in 2011/12 (topics subject to change) 11
The SLDS Technical Briefs 4. Data Access for External Researchers. 5. Electronic Data Security, Protecting PII, and Electronic Student Education Records. 6. Privacy Training: Increasing Awareness of Protections for PII in Student Education Records. 7. Sharing Data Across Sectors. To be released later in 2011/12 (topics subject to change) 11
 Frequently Asked Questions • ED recognizes that SEAs, LEAs, and IHEs engaged in building SLDSs are asking similar questions about privacy, confidentiality, and security issues. • What is needed? Technical assistance that includes responses to frequently asked questions (FAQs) that are: • • • Accurate Consistent Timely User-friendly (clear, concise, and actionable) Trusted 12
Frequently Asked Questions • ED recognizes that SEAs, LEAs, and IHEs engaged in building SLDSs are asking similar questions about privacy, confidentiality, and security issues. • What is needed? Technical assistance that includes responses to frequently asked questions (FAQs) that are: • • • Accurate Consistent Timely User-friendly (clear, concise, and actionable) Trusted 12
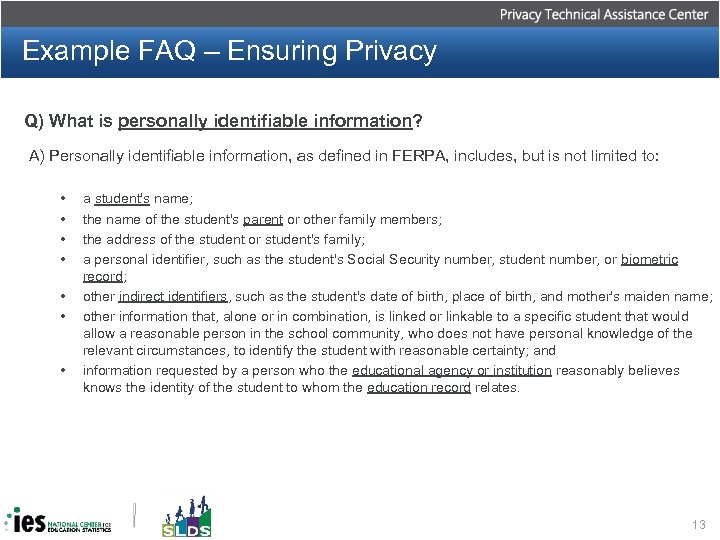 Example FAQ – Ensuring Privacy Q) What is personally identifiable information? A) Personally identifiable information, as defined in FERPA, includes, but is not limited to: • • a student's name; the name of the student's parent or other family members; the address of the student or student's family; a personal identifier, such as the student's Social Security number, student number, or biometric record; other indirect identifiers, such as the student's date of birth, place of birth, and mother's maiden name; other information that, alone or in combination, is linked or linkable to a specific student that would allow a reasonable person in the school community, who does not have personal knowledge of the relevant circumstances, to identify the student with reasonable certainty; and information requested by a person who the educational agency or institution reasonably believes knows the identity of the student to whom the education record relates. 13
Example FAQ – Ensuring Privacy Q) What is personally identifiable information? A) Personally identifiable information, as defined in FERPA, includes, but is not limited to: • • a student's name; the name of the student's parent or other family members; the address of the student or student's family; a personal identifier, such as the student's Social Security number, student number, or biometric record; other indirect identifiers, such as the student's date of birth, place of birth, and mother's maiden name; other information that, alone or in combination, is linked or linkable to a specific student that would allow a reasonable person in the school community, who does not have personal knowledge of the relevant circumstances, to identify the student with reasonable certainty; and information requested by a person who the educational agency or institution reasonably believes knows the identity of the student to whom the education record relates. 13
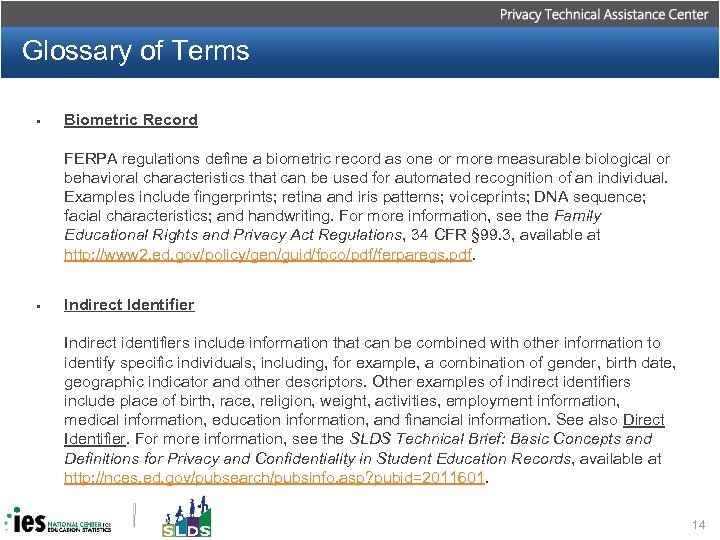 Glossary of Terms • Biometric Record FERPA regulations define a biometric record as one or more measurable biological or behavioral characteristics that can be used for automated recognition of an individual. Examples include fingerprints; retina and iris patterns; voiceprints; DNA sequence; facial characteristics; and handwriting. For more information, see the Family Educational Rights and Privacy Act Regulations, 34 CFR § 99. 3, available at http: //www 2. ed. gov/policy/gen/guid/fpco/pdf/ferparegs. pdf. • Indirect Identifier Indirect identifiers include information that can be combined with other information to identify specific individuals, including, for example, a combination of gender, birth date, geographic indicator and other descriptors. Other examples of indirect identifiers include place of birth, race, religion, weight, activities, employment information, medical information, education information, and financial information. See also Direct Identifier. For more information, see the SLDS Technical Brief: Basic Concepts and Definitions for Privacy and Confidentiality in Student Education Records, available at http: //nces. ed. gov/pubsearch/pubsinfo. asp? pubid=2011601. 14
Glossary of Terms • Biometric Record FERPA regulations define a biometric record as one or more measurable biological or behavioral characteristics that can be used for automated recognition of an individual. Examples include fingerprints; retina and iris patterns; voiceprints; DNA sequence; facial characteristics; and handwriting. For more information, see the Family Educational Rights and Privacy Act Regulations, 34 CFR § 99. 3, available at http: //www 2. ed. gov/policy/gen/guid/fpco/pdf/ferparegs. pdf. • Indirect Identifier Indirect identifiers include information that can be combined with other information to identify specific individuals, including, for example, a combination of gender, birth date, geographic indicator and other descriptors. Other examples of indirect identifiers include place of birth, race, religion, weight, activities, employment information, medical information, education information, and financial information. See also Direct Identifier. For more information, see the SLDS Technical Brief: Basic Concepts and Definitions for Privacy and Confidentiality in Student Education Records, available at http: //nces. ed. gov/pubsearch/pubsinfo. asp? pubid=2011601. 14
 Example of Templates/Tools (coming soon to web site) • Security Checklists • Sample Memorandums of Understanding • Sample Acceptable Use Policies • Glossary of Terms • Webinar Series (2011) o o Summer: NCES Brief – Data Stewardship Summer: Threats to your data, what you should know Fall: NPRM – Finalized – Latest News Winter: FERPA & Interagency data exchange 15
Example of Templates/Tools (coming soon to web site) • Security Checklists • Sample Memorandums of Understanding • Sample Acceptable Use Policies • Glossary of Terms • Webinar Series (2011) o o Summer: NCES Brief – Data Stewardship Summer: Threats to your data, what you should know Fall: NPRM – Finalized – Latest News Winter: FERPA & Interagency data exchange 15
 Regional Meetings (2011) • South: AERA, New Orleans – April 9 • • • Northeast: EIMAC, Washington, DC – April 18 • • • FERPA/NPRM News Guest speaker: Kathleen Styles, ED Chief Privacy Officer Cyber Security Session Security Audit Panel NCES Events Ø Summer Data Conference Ø Annual MIS Conference Ø SLDS Grantee Conferences Ø National Forum on Education Statistics West: SHEEO/NCES Network Conference & IPEDS Workshop – May 3 • • • Technical Brief 1: Concepts and Definitions Technical Brief 2: Data Stewardship Technical Brief 3: Statistical Methods for Protecting PII Technical Brief 4: Data Access for External Researchers Intro to PTAC Workshop on Security Data Exchanges: Federated Models USED Privacy Update Discussion: Postsecondary perspectives on data sharing, security, and partnership Midwest: Education Information Council – August 16
Regional Meetings (2011) • South: AERA, New Orleans – April 9 • • • Northeast: EIMAC, Washington, DC – April 18 • • • FERPA/NPRM News Guest speaker: Kathleen Styles, ED Chief Privacy Officer Cyber Security Session Security Audit Panel NCES Events Ø Summer Data Conference Ø Annual MIS Conference Ø SLDS Grantee Conferences Ø National Forum on Education Statistics West: SHEEO/NCES Network Conference & IPEDS Workshop – May 3 • • • Technical Brief 1: Concepts and Definitions Technical Brief 2: Data Stewardship Technical Brief 3: Statistical Methods for Protecting PII Technical Brief 4: Data Access for External Researchers Intro to PTAC Workshop on Security Data Exchanges: Federated Models USED Privacy Update Discussion: Postsecondary perspectives on data sharing, security, and partnership Midwest: Education Information Council – August 16
 Site Visits • Voluntary! • No cost!! • Designed to assist states with their privacy and security needs. • Not an audit of security or compliance. • Can provide independent, objective, third party assistance in the areas of SLDS and Cyber Security. 17
Site Visits • Voluntary! • No cost!! • Designed to assist states with their privacy and security needs. • Not an audit of security or compliance. • Can provide independent, objective, third party assistance in the areas of SLDS and Cyber Security. 17
 Site Visit Expert Help • Audit response assistance. • Independent validation of implementation recommendations as a result of security review. • Security policy reviews. • Governance assistance (multi-agency). • Facilitation of multi-agency privacy/security discussions. • If interested, send request to Privacy. TA@ed. gov 18
Site Visit Expert Help • Audit response assistance. • Independent validation of implementation recommendations as a result of security review. • Security policy reviews. • Governance assistance (multi-agency). • Facilitation of multi-agency privacy/security discussions. • If interested, send request to Privacy. TA@ed. gov 18
 PTAC Help Desk ü Contact • Phone, email, or use the form on the PTAC website (see contact info at the end of the presentation). • Submit a question, suggest a topic for regional meeting, request a site visit or document review. ü Issues are logged, clarified, and reviewed by subject matter experts (SMEs) • Expect to have any contact with PTAC acknowledged within one business day. ü If appropriate, the SMEs’ draft responses are forwarded to ED for review. • If the PTAC SMEs cannot answer the question, the issue is immediately forwarded to ED for internal review. ü Issues are reviewed at ED by the Privacy Advisory Committee (PAC). 19
PTAC Help Desk ü Contact • Phone, email, or use the form on the PTAC website (see contact info at the end of the presentation). • Submit a question, suggest a topic for regional meeting, request a site visit or document review. ü Issues are logged, clarified, and reviewed by subject matter experts (SMEs) • Expect to have any contact with PTAC acknowledged within one business day. ü If appropriate, the SMEs’ draft responses are forwarded to ED for review. • If the PTAC SMEs cannot answer the question, the issue is immediately forwarded to ED for internal review. ü Issues are reviewed at ED by the Privacy Advisory Committee (PAC). 19
 Privacy TA Team ED/NCES Program Manager: Emily Anthony Project Director: Baron Rodriguez Subject Matter Experts: Mark Hall, Anthony Bargar, Tom Szuba, Alexandra Henning, Allison Camara Help Desk Support: Dan Boland 20
Privacy TA Team ED/NCES Program Manager: Emily Anthony Project Director: Baron Rodriguez Subject Matter Experts: Mark Hall, Anthony Bargar, Tom Szuba, Alexandra Henning, Allison Camara Help Desk Support: Dan Boland 20
 Types of Resources Available from Privacy TA Center • ED Expertise • • Chief Privacy Officer Family Policy Compliance Office of General Council Office of Planning, Evaluation and Policy Development • NCES Chief Statistician 21
Types of Resources Available from Privacy TA Center • ED Expertise • • Chief Privacy Officer Family Policy Compliance Office of General Council Office of Planning, Evaluation and Policy Development • NCES Chief Statistician 21
 PTAC Role • PTAC and FPCO PTAC: Technical Assistance FPCO: Administers FERPA, authority over FERPA violations & regulations 22
PTAC Role • PTAC and FPCO PTAC: Technical Assistance FPCO: Administers FERPA, authority over FERPA violations & regulations 22
 Shrinking Budgets? Limited resources for security? Use the Privacy TA Center!! 23
Shrinking Budgets? Limited resources for security? Use the Privacy TA Center!! 23
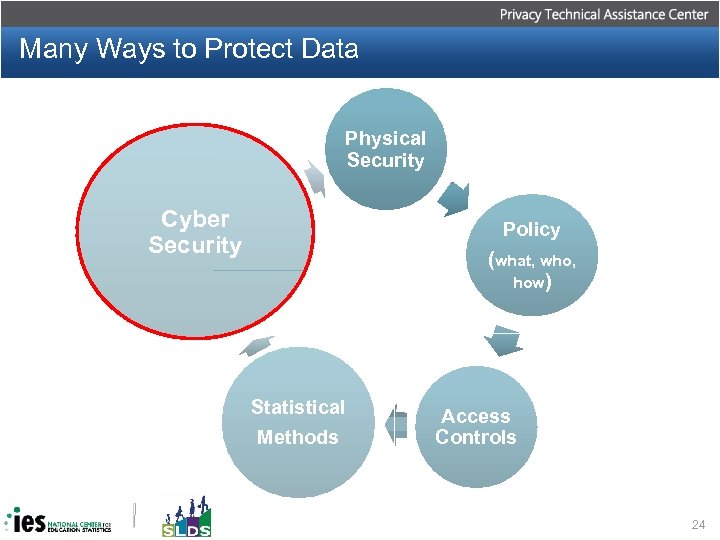 Many Ways to Protect Data Physical Security Cyber Security Policy (what, who, how) Statistical Methods Access Controls 24
Many Ways to Protect Data Physical Security Cyber Security Policy (what, who, how) Statistical Methods Access Controls 24
 Cyberspace - 2008 US National Security Presidential Directive 54/Homeland Security Presidential Directive 23 (NSPD-54/HSPD 23) CYBERSPACE is defined as the interdependent network of information technology infrastructures, including the Internet, telecommunications networks, computer systems, and embedded processors and controllers in critical industries. Common usage of the term also refers to the virtual environment of information and interactions between people. “It's now clear this cyber threat is one of the most serious economic and national security challenges we face as a nation. ” President Barak Obama, May 2009 25 25
Cyberspace - 2008 US National Security Presidential Directive 54/Homeland Security Presidential Directive 23 (NSPD-54/HSPD 23) CYBERSPACE is defined as the interdependent network of information technology infrastructures, including the Internet, telecommunications networks, computer systems, and embedded processors and controllers in critical industries. Common usage of the term also refers to the virtual environment of information and interactions between people. “It's now clear this cyber threat is one of the most serious economic and national security challenges we face as a nation. ” President Barak Obama, May 2009 25 25
 Advanced & Persistent Cyber Threats & Consequences Threats to your data: • • Social Security Numbers/Identity Education Records Employee Data Financial Records • • It’s focused • • • It’s happening It’s sophisticated Disciplinary Actions Internal Memo’s and E-mail Medical Information Personal Documents 26
Advanced & Persistent Cyber Threats & Consequences Threats to your data: • • Social Security Numbers/Identity Education Records Employee Data Financial Records • • It’s focused • • • It’s happening It’s sophisticated Disciplinary Actions Internal Memo’s and E-mail Medical Information Personal Documents 26
 Top Data Protection Issues in Education’s Cyberspace • Protecting Personally Identifiable Information (PII) • As we strive towards a “digital nation, ” exposure to risk increases • More records online & accessible • Identity Theft (10% Children) • Keeping pace with Network & Systems Security • Protective measures are outpaced by the “bad-guy” • Traditional “wack-a-mole” patching doesn’t work anymore • Maintaining the foundation of Strategy, Policy, Governance & People • Training, Education & Awareness is key • Cloud computing complicates traditional security architecture approaches 27
Top Data Protection Issues in Education’s Cyberspace • Protecting Personally Identifiable Information (PII) • As we strive towards a “digital nation, ” exposure to risk increases • More records online & accessible • Identity Theft (10% Children) • Keeping pace with Network & Systems Security • Protective measures are outpaced by the “bad-guy” • Traditional “wack-a-mole” patching doesn’t work anymore • Maintaining the foundation of Strategy, Policy, Governance & People • Training, Education & Awareness is key • Cloud computing complicates traditional security architecture approaches 27
 Principles for Data Protection & Cyber Security Data Protection Act 1998 • • “Eight enforceable principles of good practice” Cyber Security Principles • • • Data must be: • • Fairly and lawfully processed Processed for limited purposes Adequate, relevant and not excessive Accurate Not kept longer than necessary Processed in accordance with the data subject's rights Secure Not transferred to other countries without adequate protection Data should: • Be confidential Maintain Integrity Be available Be authenticated Systems that process data should be: • • • Designed from the start with security in-mind Resilient and recoverable from attacks Maintained regularly 28 28
Principles for Data Protection & Cyber Security Data Protection Act 1998 • • “Eight enforceable principles of good practice” Cyber Security Principles • • • Data must be: • • Fairly and lawfully processed Processed for limited purposes Adequate, relevant and not excessive Accurate Not kept longer than necessary Processed in accordance with the data subject's rights Secure Not transferred to other countries without adequate protection Data should: • Be confidential Maintain Integrity Be available Be authenticated Systems that process data should be: • • • Designed from the start with security in-mind Resilient and recoverable from attacks Maintained regularly 28 28
 Best Practices – NIST Selected PII Security Controls • Access Enforcement (ACLs, RBACs, encryption) • Separation of Duties • Least Privilege (read, write, edit) • Remote Access (limit or deny) • Access Control for Mobile Devices (deny or limit) • Auditable events and Audit Reviews (policy that monitors certain events) • Identification and Authentication • Media Access, Marking, Storage, Transport, and Sanitization • Transmission Confidentiality (encryption) • Protection of Information at Rest • Information System Monitoring (automated tools to detect suspicious transfers) NIST Special Pub 800 -122 Guide to Protecting the Confidentiality of Personally Identifiable Information, 29
Best Practices – NIST Selected PII Security Controls • Access Enforcement (ACLs, RBACs, encryption) • Separation of Duties • Least Privilege (read, write, edit) • Remote Access (limit or deny) • Access Control for Mobile Devices (deny or limit) • Auditable events and Audit Reviews (policy that monitors certain events) • Identification and Authentication • Media Access, Marking, Storage, Transport, and Sanitization • Transmission Confidentiality (encryption) • Protection of Information at Rest • Information System Monitoring (automated tools to detect suspicious transfers) NIST Special Pub 800 -122 Guide to Protecting the Confidentiality of Personally Identifiable Information, 29
 Best Practices – Multi-Factor Authentication 1. Be reliable, scalable, and available 2. Be compatible and interoperable with your Technology and Policy 3. Seamlessly integrate with existing architectures and infrastructure 4. Support web applications and should not require clientside software 5. Be compliant with NIST, FIPS and other federal standards 6. Be based on mature technology and should be commercially available with a broad installed market base If you have remote access users (especially those with super user access), MFA should be a high priority capability 30
Best Practices – Multi-Factor Authentication 1. Be reliable, scalable, and available 2. Be compatible and interoperable with your Technology and Policy 3. Seamlessly integrate with existing architectures and infrastructure 4. Support web applications and should not require clientside software 5. Be compliant with NIST, FIPS and other federal standards 6. Be based on mature technology and should be commercially available with a broad installed market base If you have remote access users (especially those with super user access), MFA should be a high priority capability 30
 Current Examples of Cyber Security Support from PTAC • Review and comment on network security portion of RFPs. • Review audit results and recommendations. • Site visits to review security architecture, capabilities and plans. • Best practice and security guidance documents. • Future: more technically-focused documents and training. 31
Current Examples of Cyber Security Support from PTAC • Review and comment on network security portion of RFPs. • Review audit results and recommendations. • Site visits to review security architecture, capabilities and plans. • Best practice and security guidance documents. • Future: more technically-focused documents and training. 31
 For more information… • Website • • Help Desk • • http: //nces. ed. gov/programs/PTAC/ Privacy. TA@ed. gov Toll Free Phone: 855 -249 -3072 Toll Free FAX: 855 -249 -3073 NCES • Emily. Anthony@ed. gov • • • Request assistance Upcoming events Subscribe to email list Recently released relevant ED publications Privacy TA Center publications Best practice guidelines Frequently Asked Questions Latest FERPA news Other on-line recommended resources 32
For more information… • Website • • Help Desk • • http: //nces. ed. gov/programs/PTAC/ Privacy. TA@ed. gov Toll Free Phone: 855 -249 -3072 Toll Free FAX: 855 -249 -3073 NCES • Emily. Anthony@ed. gov • • • Request assistance Upcoming events Subscribe to email list Recently released relevant ED publications Privacy TA Center publications Best practice guidelines Frequently Asked Questions Latest FERPA news Other on-line recommended resources 32


