7302688c8ebd331aee1cba12c3e21f92.ppt
- Количество слайдов: 39

Session # T- 7 Web 2. 0 Technologies and Privacy/Security Considerations Sandy England & Joseph Salama

Agenda • Web 2. 0 technologies • Opportunities and Challenges • Policy/Legal/ Privacy/Security Issues – Privacy Act – E-Government Act & FISMA • Web 2. 0 Potential Issues and Concerns • Conclusion Source: http: //dccblawg. blogspot. com/2007/11/legal-implications-of-web-20. html 2

Introduction • Our targeted users are attracted to social networking communities that foster user-driven content • How can we leverage social networking to extend our reach and message? • Web 2. 0 brings a new set of challenges - privacy, data security, and legal issues Source: http: //www. cooltownstudios. com/images/web 2. 0. jpg 3

What is Web 2. 0? • From Wikipedia: – Web 2. 0 is a living term describing changing trends in the use of World Wide Web technology and web design that aims to enhance creativity, information sharing, collaboration, and functionality of the web – Web 2. 0 concepts have led to the development and evolution of web-based communities and hosted services, such as social-networking sites, video sharing sites, wikis, blogs, and folksonomies http: //en. wikipedia. org/wiki/Web_2. 0 4

What is Web 2. 0? • Community – Users organize themselves and work in partnership with common goals • Active participation – Users move from passive role (reading) to active role (authoring) • The Wisdom of Crowds: – Individual users add value – Aggregate data into a collective thought – Applications get better/smarter the more people use them 5

Web 2. 0 By Example Web 1. 0 Double. Click Ofoto Akamai Britannica Online Personal websites Page views Screen scraping Publishing Systems Directories (taxonomy) Stickiness Domain name speculation Web 2. 0 Google Ad. Sense Flickr Bit. Torrent Wikipedia Blogging Cost per click Web services Participation Wikis Tagging ("folksonomy") Syndication Search engine optimization http: //www. oreillynet. com/pub/a/oreilly/tim/news/2005/09/30/what-is-web-20. html 6
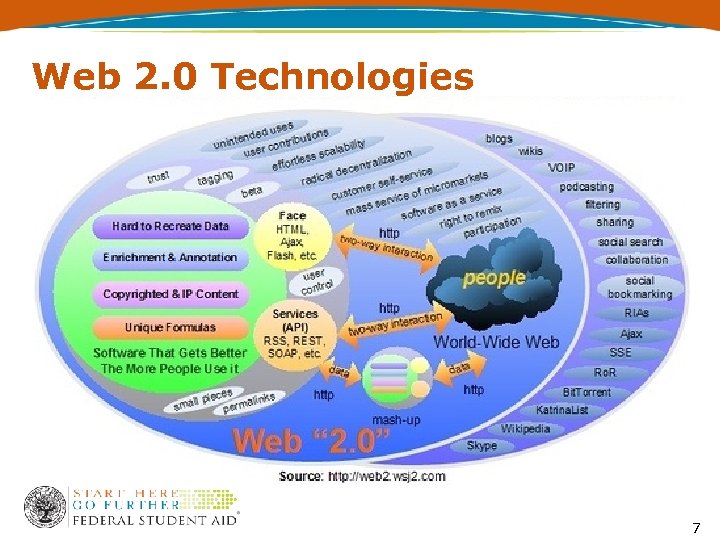
Web 2. 0 Technologies 7
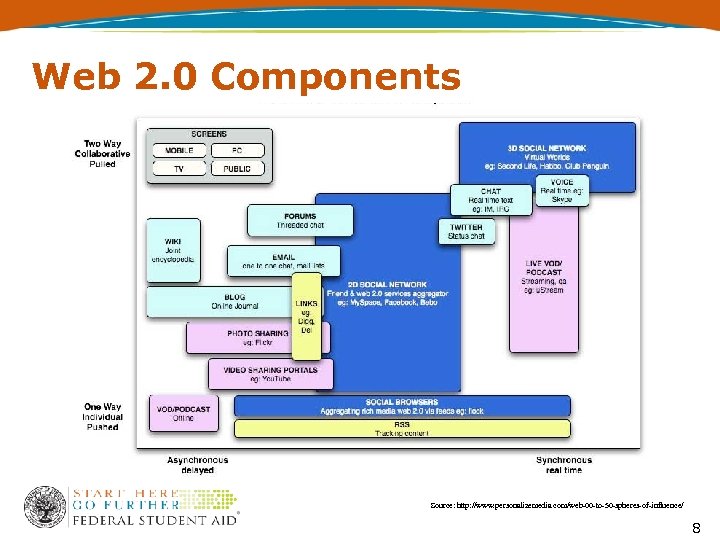
Web 2. 0 Components Source: http: //www. personalizemedia. com/web-00 -to-50 -spheres-of-influence/ 8
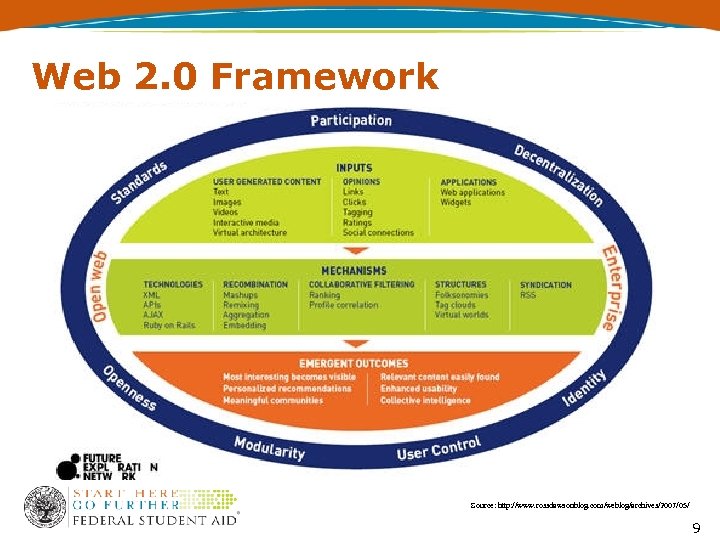
Web 2. 0 Framework Source: http: //www. rossdawsonblog. com/weblog/archives/2007/05/ 9

Web 2. 0 Technologies • User-Generated Content (e. g. Flick. R and You. Tube) • Web Content Sharing (e. g. Digg) • Social Bookmarking (e. g. Del. icio. us) • Blogs • Wikis • AJAX • Etc. Source: http: //edtechtrek. blogspot. com/2008_03_01_archive. html 10

User-Generated Content • Users upload and share personal videos (e. g. You. Tube) and pictures (e. g. Flick. R) • Organize media through tagging of themes, channels, collections, sets, etc. and allow commenting • How could we do it? – Enable peer-to-peer mentoring and support – Share tips, stories, how they overcame obstacles – Their lessons become sources of inspiration and motivation for others 11
Blogs • Publish articles and info about any subject • Share information and discuss topics • An effective communication tool • Can be updated at virtually zero cost • Organize content with meta -data, categorizations, and labels 12
Wikis • Speed and flexibility: Wiki means "fast" in Hawaiian • Effective tool for collaborative authoring • Allows users to create and edit pages • Breaks away from structured hierarchies to share information • The collective intelligence becomes a creative genius 13

Web 2. 0 Opportunities • Collaborate more easily: – Internally (employees) – Externally (partners and customers) • Allow citizens to have greater input • Enable citizens to help each other – peer to peer collaboration • Create communities, which in turn create creative solutions to problems – Aggregate constituent wisdom: “The whole is smarter than the one” 14

Web 2. 0 Challenges • Web 2. 0 can enhance the delivery of public services and citizens’ engagements with government • However, a number of challenges prevent us from diving head first into Web 2. 0 – – – Privacy issues Control of Content Anonymous postings (yes or no? ) User Trust - can change content of others Vandalism Plagiarism and Copyright infringement • Balancing our role as responsible officials: – To protect citizens in this online world – To respect the First Amendment’s protection of free speech 15

Web 2. 0 Challenges (cont. ) • “Protect government information commensurate with the risk and magnitude of harm that could result from the loss, misuse, or unauthorized access to or modification of such information… (consistent with)…the risk-based policy for costeffective security established by the Computer Security Act of 1987. ” OMB Circular A-130 16

Privacy/Security Considerations • Laws, mandates, policies, and processes that require agencies to protect the use of data collected from citizens – Privacy Act – System of Records – Information Clearance – E-Gov Act and FISMA • Confidentiality, Integrity, and Availability of Information – OMB Circular A-130, Appendix III … and many more … 17

Privacy Concerns • A full 93% of children ages 12 -17 are online! • 55% of online teens use social networks • 55% of teens have created an online profile • 48% of teens visit social networking sites daily • 22% visit several times a day • 66% of teens with profiles say that their information is not visible to all Internet users Pew Internet & American Life Project, “Parent and Teenager Internet Use” (Oct. 24, 2007) Pew Internet & American Life Project, “Teens, Privacy & Online Social Networks” (Apr. 18, 2007) Pew Internet & American Life Project, “Teens and Online Stranger Contact” (Oct. 14, 2007) 18

Privacy Concerns (cont. ) • 63% of teens with profiles believe a motivated person could eventually identify them from the information they publicly provide on their profiles • 7% of online teens say they have been contacted by a stranger – either through “friend” requests, spam email, or comments posted on a blogging or photo sharing site – who made them feel scared or uncomfortable Pew Internet & American Life Project, “Parent and Teenager Internet Use” (Oct. 24, 2007) Pew Internet & American Life Project, “Teens, Privacy & Online Social Networks” (Apr. 18, 2007) Pew Internet & American Life Project, “Teens and Online Stranger Contact” (Oct. 14, 2007) 19

Privacy Goals • Guiding Policies and Processes – System of Record Notification (SORN) Process – Information Clearance (IC) Process • Guiding Principles: – Don’t collect PII data unless truly necessary – Randomly generate IDs which can’t be mapped back to user names – Ensure user account information is invisible – Disallow lookups so strangers cannot iterate through IDs to see public information 20

Liability • Liability laws addressing complex new divisions of responsibility in online relationships between government, businesses and citizens • Is there liability for providing an application that enables stalking and other violations? – Need comprehensive Terms & Conditions of Use – Hide profile data by default – Easy to use privacy settings 21

Intellectual Property • You. Tube/Google facing legal action from Viacom for allowing copyrighted material to be uploaded to the video sharing site • Universal initially attacked My. Space for illegal sharing of music before developing a branded virtual jukebox that users can post to their profile • Signing off a blog post with image of your favorite cartoon character may infringe copyright laws • Yet … copyright law has faced these challenges since the beginning of the Internet 22

Legislative and Policy Drivers Ø E-Government Act, Public Law 107 -347 (Title III) Federal Information Security Management Act of 2002 (FISMA) Ø OMB Circular A-130 (Appendix III) Management of Federal Automated Information Resources Ø OMB Memorandum M-06 -16 Protection of Sensitive Information 23

FISMA Requirements • FISMA directed that federal standards be created to address the specification of minimum security requirements for federal information and information systems by: – Conducting security categorization of the information and information systems based on risk levels – Authorization of system processing prior to operations and periodically thereafter 24

FISMA Requirements (cont. ) • All Federal agencies are responsible for ensuring appropriate security controls • FISMA applies to information and information systems used by the agency, contractors, and other organizations and sources • Require agencies to certify their systems to operate • Security certification is the assessment of those security controls 25

Security Accreditation • Required by OMB Circular A-130, Appendix III, security accreditation provides a form of quality control • Challenges Federal managers to implement the most effective security controls possible • Is the official management decision given by a senior agency official to authorize operation • The senior agency official is usually the highest level executive in each organization within the agency 26

Security Accreditation (cont. ) • By accrediting an information system, an agency official explicitly accepts the risk and responsibility for the security of the system • The agency official is fully accountable for any adverse impacts to the agency if a breach of security occurs • Thus, responsibility and accountability are core principles that characterize security accreditation 27

Official Information Dissemination • All efforts to provide official government information to external stakeholders • Includes various types of media, such as video, paper, web, etc. (NIST SP 800 -60 rev 2, section C. 2. 6. 2) • FISMA in a nutshell: – Categorization – Certification – Accreditation – Authorization 28

Security Categorizations • Security Objectives: – Confidentiality – Integrity – Availability • Impact levels: – Low – Moderate – High

Confidentiality • Information Dissemination Type for Confidentiality: – The loss of confidentiality results in the unauthorized disclosure of information • Recommended Confidentiality Impact Level for Web 2. 0 Applications – Low 30

Integrity • Information Dissemination Type for Integrity: – The loss of integrity results in the unauthorized modification or destruction of information (e. g. , modified web pages, electronic mail, etc. ) • Recommended Integrity Impact Level for Web 2. 0 Applications – Low 31

Availability • Information Dissemination Type for Availability: – The loss of availability results in the disruption of access to or use of information or information system • Recommended Availability Impact Level for Web 2. 0 Applications – Low 32

Web 2. 0 is NOT the Issue • Adverse Events can affect operations and/or public confidence in a Federal agency • Security controls can be put into place to mitigate these risks • Examples: ― Web filtering software for blocking malicious behaviors (e. g. , scanning inbound content and inbound binary files) ― Strip / rewrite HTML and Java. Script code ― Lock down of browsers to disable scripting ― Implement virtualization ― Promote user awareness of Web-related risks ― Create and enforce acceptable use policies 33

Concerns/Recommendations • Content Control ― Requires trusting third parties with content ― Many uses of Web 2. 0 may not make sense for agencies that interact directly with the public and wish to maintain tight control over content • Personally Identifiable Information ― Discuss security, legal, and privacy concerns and determine strategy and approach ― Develop privacy & acceptable use policies/processes for the dissemination of official information type via Web 2. 0 ― Plan ahead for clearance process ― Develop policies for management of data 34
Concerns/Recommendations • Interlinked Platforms ― Difficult to remotely administer ― Less control of security ― May be affected by attacks aimed at other web sites or that are hosted by external provider ― Securing public web servers in accordance with NIST Special Publication 800 -44 Version 2 cannot be imposed on interlinked computing platforms not owned by the Federal government ― Nearly impossible and/or cost prohibitive to “certify and accredit” interlinked computing platforms in accordance with FISMA 35

Getting Started • Educate the organization on Web 2. 0 • How it can help the organization meet fastevolving objectives? • Align clear priorities for online collaboration with organizational objectives • Initiate a pilot project • Evaluate technology strategy and compatibility Source: William D. Eggers - Global Public Sector Research Director, Deloitte 36

Getting Started (cont. ) • Create policies that maximize benefits of adopting Web 2. 0 in organization • Measure results by establishing key performance indicators that measure the strategy’s effectiveness • Embrace a culture of collaboration and continually evolve how interaction happens with stakeholders inside and outside of government Source: William D. Eggers - Global Public Sector Research Director, Deloitte 37

Questions?

Contact Information We appreciate your feedback and comments. We can be reached at: Joseph Salama, ED Chief Information Security Officer Phone: 202 -245 -6069 Email: Joseph. Salama@ed. gov Sandy England, FSA Enterprise Portal Manager Phone: 202 -377 -3537 Email: Sandy. England@ed. gov 39
7302688c8ebd331aee1cba12c3e21f92.ppt