7b491bbd0fdeda4a5eda47d7f77efc59.ppt
- Количество слайдов: 51
 Session 52 Security Architecture – What Does It Mean Katie Blot Nina Colon
Session 52 Security Architecture – What Does It Mean Katie Blot Nina Colon
 Security Architecture - What Does It Mean? “What is security architecture and what are the critical functionalities? Learn about Federal Student Aid's security architecture - the what and the why and how it affects you. Federal Student Aid's security architecture pilot with the e. Campus-Based (e. CB) system will be discussed as well as our plans for the future, including E-Authentication. ” 2
Security Architecture - What Does It Mean? “What is security architecture and what are the critical functionalities? Learn about Federal Student Aid's security architecture - the what and the why and how it affects you. Federal Student Aid's security architecture pilot with the e. Campus-Based (e. CB) system will be discussed as well as our plans for the future, including E-Authentication. ” 2
 Agenda • Security Architecture Overview (Katie Blot) • Security Architecture and e. CB (Nina Colon) • E-Authentication Overview (Katie Blot) 3
Agenda • Security Architecture Overview (Katie Blot) • Security Architecture and e. CB (Nina Colon) • E-Authentication Overview (Katie Blot) 3
 Security Architecture Overview
Security Architecture Overview
 What is Security Architecture? • Security Architecture uses Tivoli Access Manager (TAM) to enable consistent Authentication, Authorization, and Accountability – Authentication: Who are you? – Authorization: What are you allowed to do? – Accountability: What did you do? • Security Architecture will enable a single unique source of Identity Management throughout Federal Student Aid using Tivoli Identity Manager (TIM) – One user profile person for all Security Architecture protected applications • Federal Student Aid Security Infrastructure utilizing TIM and TAM provides the best in breed security software products to support the Federal Student Aid Security Architecture 5
What is Security Architecture? • Security Architecture uses Tivoli Access Manager (TAM) to enable consistent Authentication, Authorization, and Accountability – Authentication: Who are you? – Authorization: What are you allowed to do? – Accountability: What did you do? • Security Architecture will enable a single unique source of Identity Management throughout Federal Student Aid using Tivoli Identity Manager (TIM) – One user profile person for all Security Architecture protected applications • Federal Student Aid Security Infrastructure utilizing TIM and TAM provides the best in breed security software products to support the Federal Student Aid Security Architecture 5
 Security Architecture Functions: • Provides consistent security services & configurations across Federal Student Aid systems – Decrease security risks – Improves maintainability of systems – Offloads ad hoc application security from application teams • Gives better service to our customers/partners – Single sign-on for web applications – Simplified registration/approval processing – Delegated administration Promote enterprise security management – Consolidated security views and reporting – Flexibility to accommodate new or redeployed systems – Lowers security development and operational costs • 6
Security Architecture Functions: • Provides consistent security services & configurations across Federal Student Aid systems – Decrease security risks – Improves maintainability of systems – Offloads ad hoc application security from application teams • Gives better service to our customers/partners – Single sign-on for web applications – Simplified registration/approval processing – Delegated administration Promote enterprise security management – Consolidated security views and reporting – Flexibility to accommodate new or redeployed systems – Lowers security development and operational costs • 6
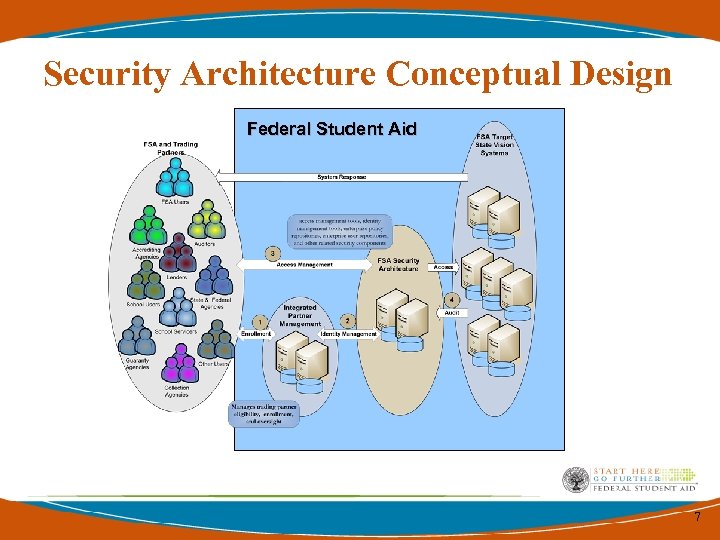 Security Architecture Conceptual Design Federal Student Aid 7
Security Architecture Conceptual Design Federal Student Aid 7
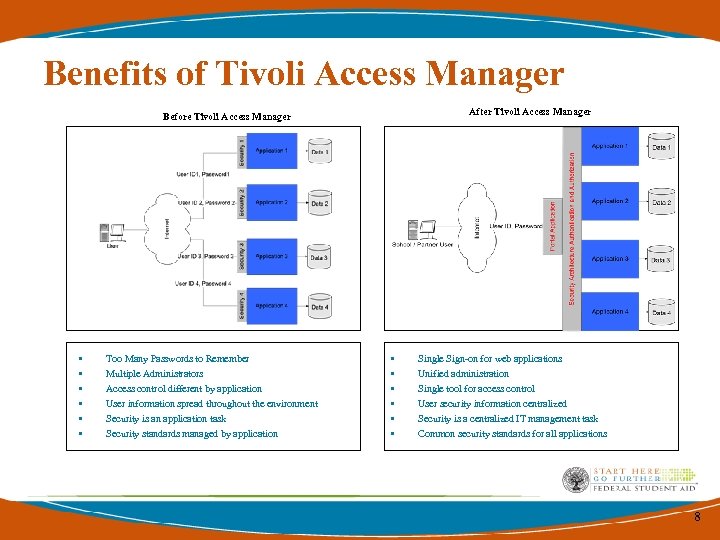 Benefits of Tivoli Access Manager After Tivoli Access Manager Before Tivoli Access Manager • • • Too Many Passwords to Remember Multiple Administrators Access control different by application User information spread throughout the environment Security is an application task Security standards managed by application • • • Single Sign-on for web applications Unified administration Single tool for access control User security information centralized Security is a centralized IT management task Common security standards for all applications 8
Benefits of Tivoli Access Manager After Tivoli Access Manager Before Tivoli Access Manager • • • Too Many Passwords to Remember Multiple Administrators Access control different by application User information spread throughout the environment Security is an application task Security standards managed by application • • • Single Sign-on for web applications Unified administration Single tool for access control User security information centralized Security is a centralized IT management task Common security standards for all applications 8
 Security Architecture Today • Eight applications secured behind Security Architecture – Including Financial Partners Data. Mart and Experimental Sites • e. CB Integration with Security Architecture in Dec 2006 – Registration for existing e. CB users available in PC Lab – New users will be able to self-register in December • Federal Student Aid Target State Vision applications are being built with Security Architecture. These applications include: – IPM – ADvance – Portals – Enterprise Service Bus (ESB) – e-Authentication to e. CB 9
Security Architecture Today • Eight applications secured behind Security Architecture – Including Financial Partners Data. Mart and Experimental Sites • e. CB Integration with Security Architecture in Dec 2006 – Registration for existing e. CB users available in PC Lab – New users will be able to self-register in December • Federal Student Aid Target State Vision applications are being built with Security Architecture. These applications include: – IPM – ADvance – Portals – Enterprise Service Bus (ESB) – e-Authentication to e. CB 9
 Security Architecture and e. Campus-Based 10
Security Architecture and e. Campus-Based 10
 Security Architecture – How Is It Easier Than SAIG Enrollment? • All forms will be pre-populated with existing data from the SAIG Enrollment System and verified and updated by individual users. • New users will need to provide all data necessary to create userid and password. • Required data fields will be indicated by an *. • The user must know his or her institution/organization OPEID or correct Institution/organization name. • The Institution/Organization name and location will be displayed so that user can be sure of selecting the right school. 11
Security Architecture – How Is It Easier Than SAIG Enrollment? • All forms will be pre-populated with existing data from the SAIG Enrollment System and verified and updated by individual users. • New users will need to provide all data necessary to create userid and password. • Required data fields will be indicated by an *. • The user must know his or her institution/organization OPEID or correct Institution/organization name. • The Institution/Organization name and location will be displayed so that user can be sure of selecting the right school. 11
 Security Architecture – How Is It Easier Than SAIG Enrollment? • The access rights are pre-defined from pre-loaded data from the SAIG Enrollment System. • Access rights will be rolled over from the prior year. • Rolling the access rights from the prior years will alleviate the need for the Destination Point Administrator (DPA) go back into the Enrollment System to give user access rights to new year. 12
Security Architecture – How Is It Easier Than SAIG Enrollment? • The access rights are pre-defined from pre-loaded data from the SAIG Enrollment System. • Access rights will be rolled over from the prior year. • Rolling the access rights from the prior years will alleviate the need for the Destination Point Administrator (DPA) go back into the Enrollment System to give user access rights to new year. 12
 Change in Registration Process • Starting December 16, 2006 all current user of e. CB will need to register with Security Architecture • There will be no issuances of PINs for use with e. CB application for Authentication of user • Starting December 16, 2006 Authentication will be only through Security Architecture with a userid and password. 13
Change in Registration Process • Starting December 16, 2006 all current user of e. CB will need to register with Security Architecture • There will be no issuances of PINs for use with e. CB application for Authentication of user • Starting December 16, 2006 Authentication will be only through Security Architecture with a userid and password. 13
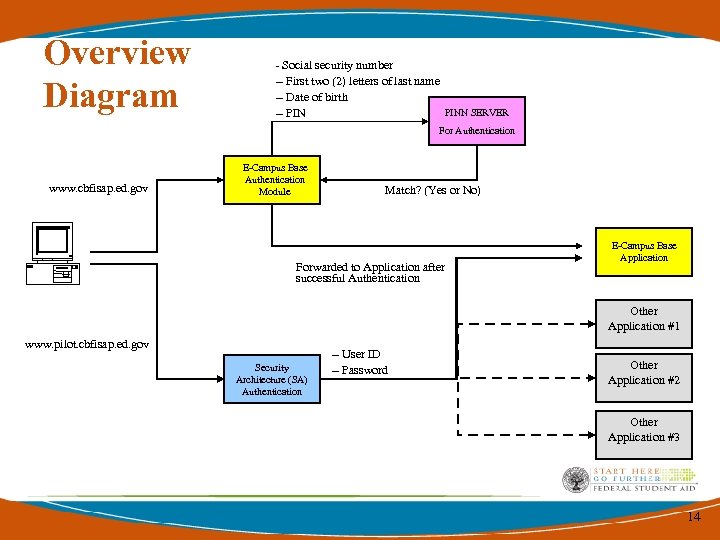 Overview Diagram - Social security number -- First two (2) letters of last name -- Date of birth -- PINN SERVER For Authentication www. cbfisap. ed. gov E-Campus Base Authentication Module Match? (Yes or No) Forwarded to Application after successful Authentication E-Campus Base Application Other Application #1 www. pilot. cbfisap. ed. gov Security Architecture (SA) Authentication -- User ID -- Password Other Application #2 Other Application #3 14
Overview Diagram - Social security number -- First two (2) letters of last name -- Date of birth -- PINN SERVER For Authentication www. cbfisap. ed. gov E-Campus Base Authentication Module Match? (Yes or No) Forwarded to Application after successful Authentication E-Campus Base Application Other Application #1 www. pilot. cbfisap. ed. gov Security Architecture (SA) Authentication -- User ID -- Password Other Application #2 Other Application #3 14
 What Is New? • Registration screens are the same for all parties – DPA – FAA – Third Party Service Providers • Email is sent to registrants’ Supervisors for additional confirmation of user account being created. 15
What Is New? • Registration screens are the same for all parties – DPA – FAA – Third Party Service Providers • Email is sent to registrants’ Supervisors for additional confirmation of user account being created. 15
 e. Campus Based Login • Go to e. CB home page at the following URL: – www. cbfisap. ed. gov • Click Login • Current e. CB users data is preloaded and limited additional information is needed to complete the registration. – You will be referred to the Security Architecture system from e. CB login. 16
e. Campus Based Login • Go to e. CB home page at the following URL: – www. cbfisap. ed. gov • Click Login • Current e. CB users data is preloaded and limited additional information is needed to complete the registration. – You will be referred to the Security Architecture system from e. CB login. 16
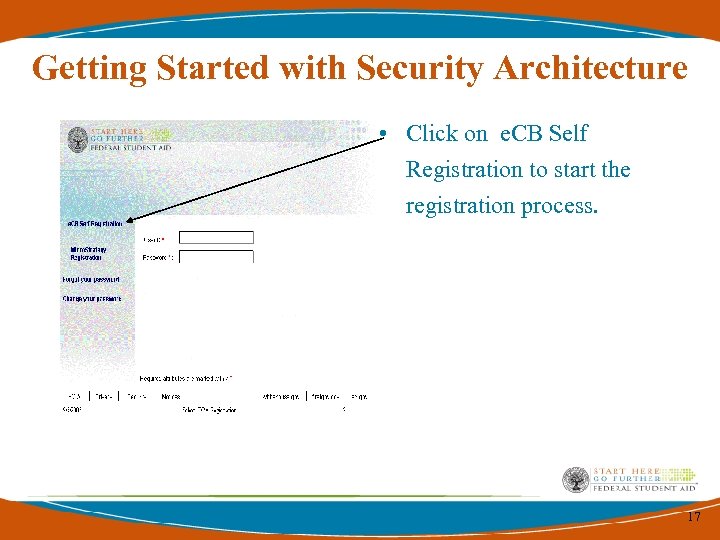 Getting Started with Security Architecture • Click on e. CB Self Registration to start the registration process. 17
Getting Started with Security Architecture • Click on e. CB Self Registration to start the registration process. 17
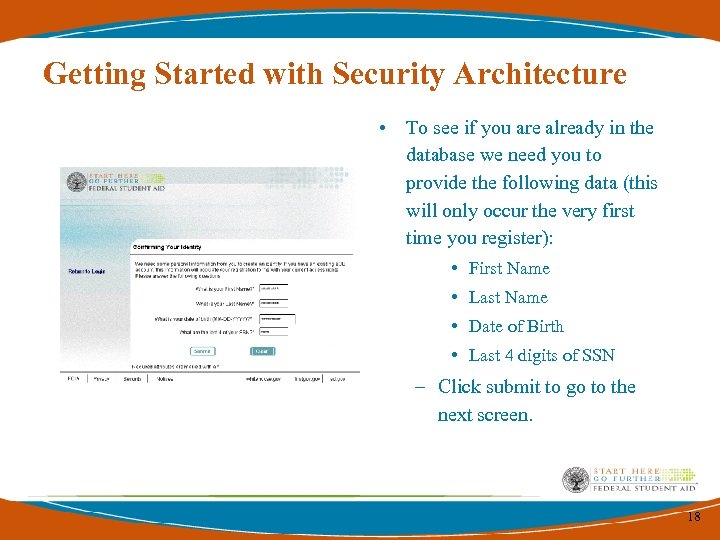 Getting Started with Security Architecture • To see if you are already in the database we need you to provide the following data (this will only occur the very first time you register): • First Name • Last Name • Date of Birth • Last 4 digits of SSN – Click submit to go to the next screen. 18
Getting Started with Security Architecture • To see if you are already in the database we need you to provide the following data (this will only occur the very first time you register): • First Name • Last Name • Date of Birth • Last 4 digits of SSN – Click submit to go to the next screen. 18
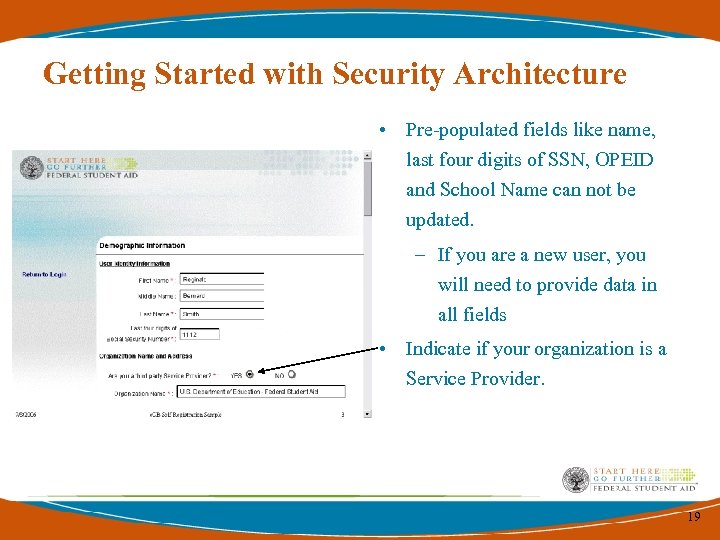 Getting Started with Security Architecture • Pre-populated fields like name, last four digits of SSN, OPEID and School Name can not be updated. – If you are a new user, you will need to provide data in all fields • Indicate if your organization is a Service Provider. 19
Getting Started with Security Architecture • Pre-populated fields like name, last four digits of SSN, OPEID and School Name can not be updated. – If you are a new user, you will need to provide data in all fields • Indicate if your organization is a Service Provider. 19
 Getting Started with Security Architecture • Your demographic information has been pre-populated. We have carried over your information from the SAIG Participation Management System. – Please verify that the information provided is still correct. – If the information is incorrect in our system, please make necessary updates during the registration process. • Fields such as address and email can be updated. 20
Getting Started with Security Architecture • Your demographic information has been pre-populated. We have carried over your information from the SAIG Participation Management System. – Please verify that the information provided is still correct. – If the information is incorrect in our system, please make necessary updates during the registration process. • Fields such as address and email can be updated. 20
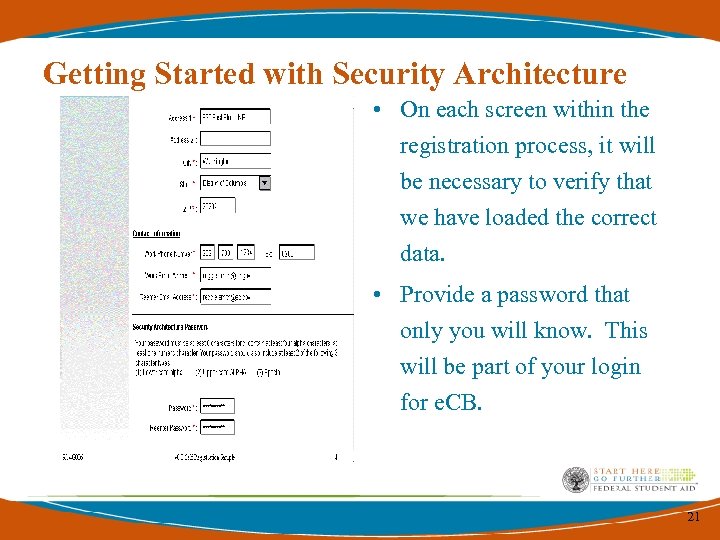 Getting Started with Security Architecture • On each screen within the registration process, it will be necessary to verify that we have loaded the correct data. • Provide a password that only you will know. This will be part of your login for e. CB. 21
Getting Started with Security Architecture • On each screen within the registration process, it will be necessary to verify that we have loaded the correct data. • Provide a password that only you will know. This will be part of your login for e. CB. 21
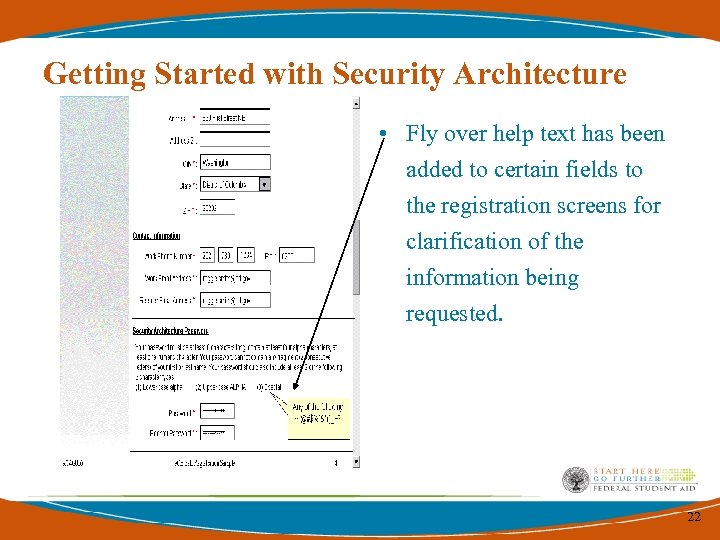 Getting Started with Security Architecture • Fly over help text has been added to certain fields to the registration screens for clarification of the information being requested. 22
Getting Started with Security Architecture • Fly over help text has been added to certain fields to the registration screens for clarification of the information being requested. 22
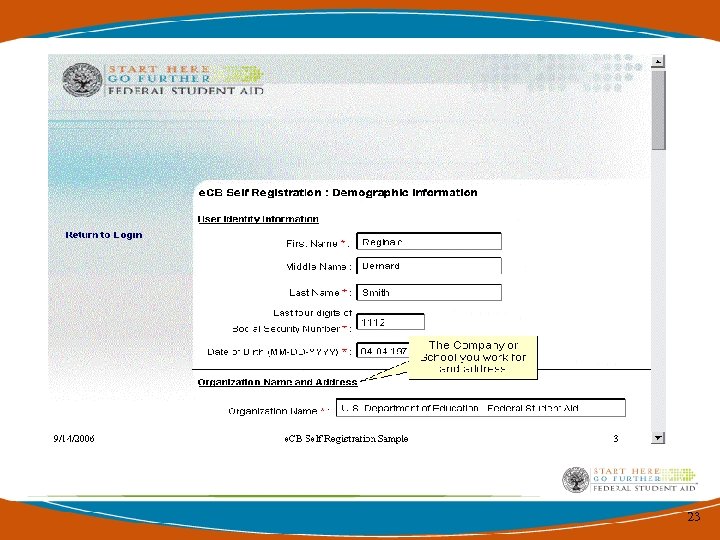 23
23
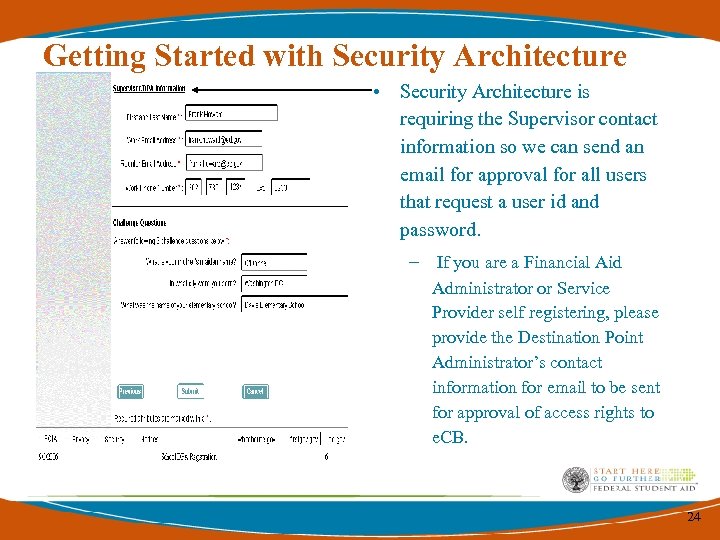 Getting Started with Security Architecture • Security Architecture is requiring the Supervisor contact information so we can send an email for approval for all users that request a user id and password. – If you are a Financial Aid Administrator or Service Provider self registering, please provide the Destination Point Administrator’s contact information for email to be sent for approval of access rights to e. CB. 24
Getting Started with Security Architecture • Security Architecture is requiring the Supervisor contact information so we can send an email for approval for all users that request a user id and password. – If you are a Financial Aid Administrator or Service Provider self registering, please provide the Destination Point Administrator’s contact information for email to be sent for approval of access rights to e. CB. 24
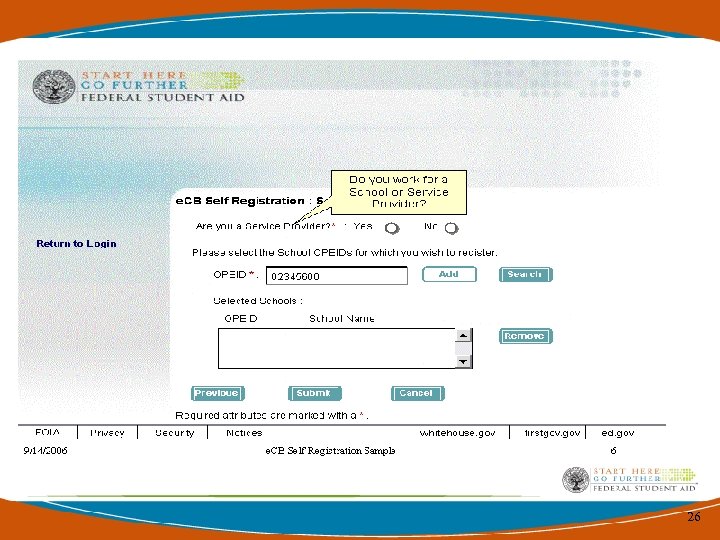
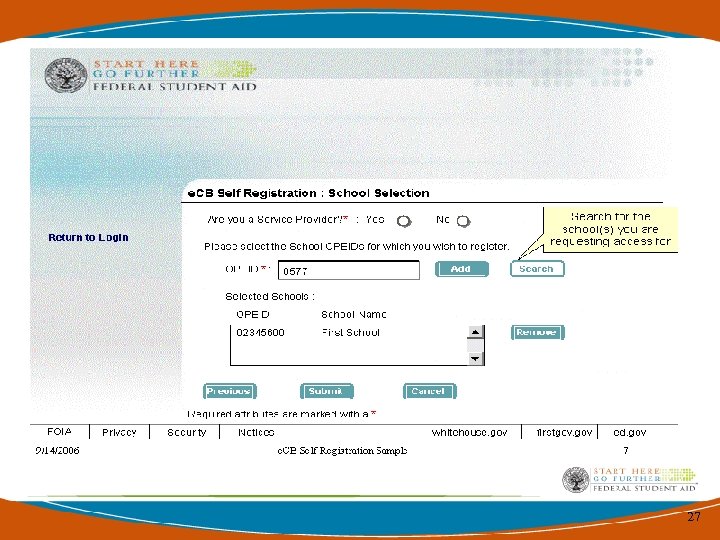
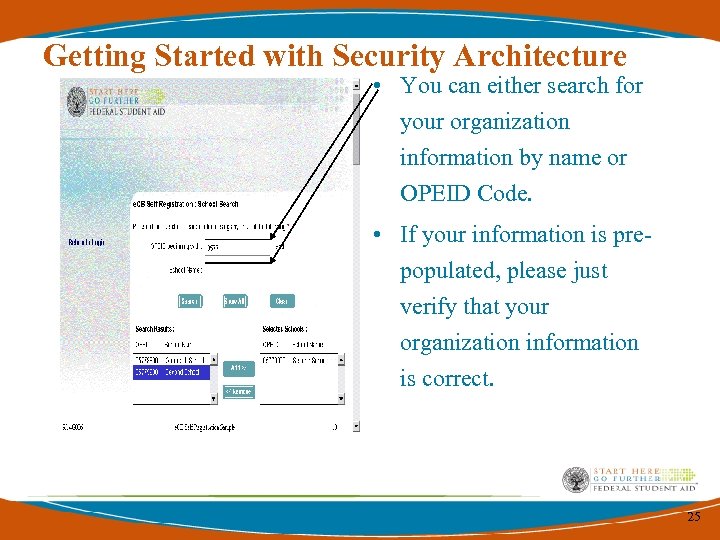 Getting Started with Security Architecture • You can either search for your organization information by name or OPEID Code. • If your information is prepopulated, please just verify that your organization information is correct. 25
Getting Started with Security Architecture • You can either search for your organization information by name or OPEID Code. • If your information is prepopulated, please just verify that your organization information is correct. 25
 26
26
 27
27
 28
28
 29
29
 30
30
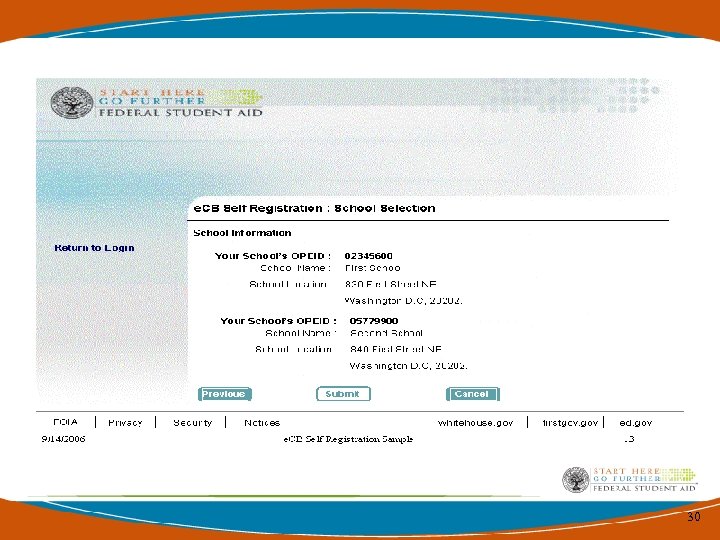
 Getting Started with Security Architecture • You will be asked to confirm the registration information that either has been pre-populated in the system or that you have entered on each screen. 31
Getting Started with Security Architecture • You will be asked to confirm the registration information that either has been pre-populated in the system or that you have entered on each screen. 31
 32
32
 33
33
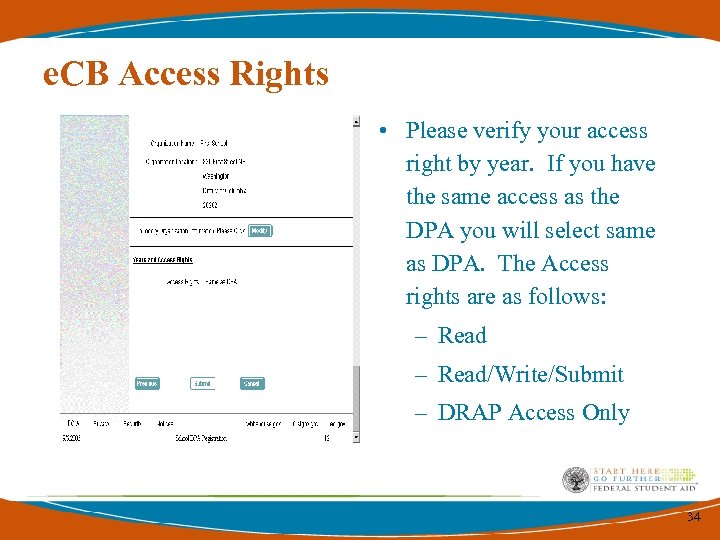 e. CB Access Rights • Please verify your access right by year. If you have the same access as the DPA you will select same as DPA. The Access rights are as follows: – Read/Write/Submit – DRAP Access Only 34
e. CB Access Rights • Please verify your access right by year. If you have the same access as the DPA you will select same as DPA. The Access rights are as follows: – Read/Write/Submit – DRAP Access Only 34
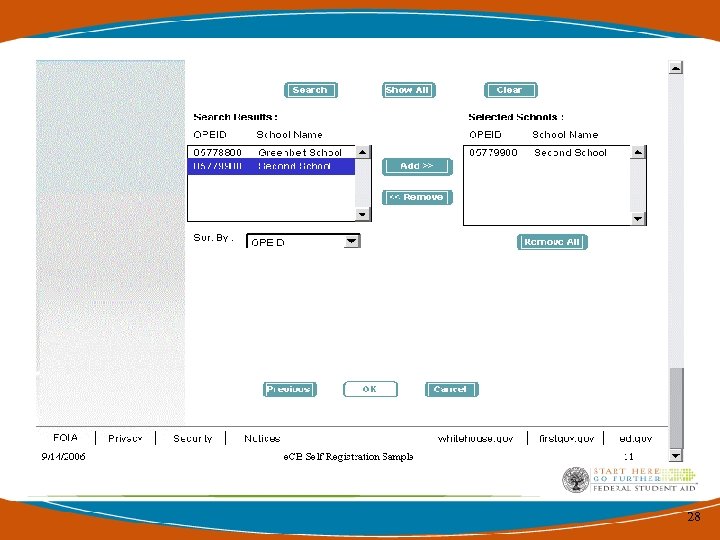
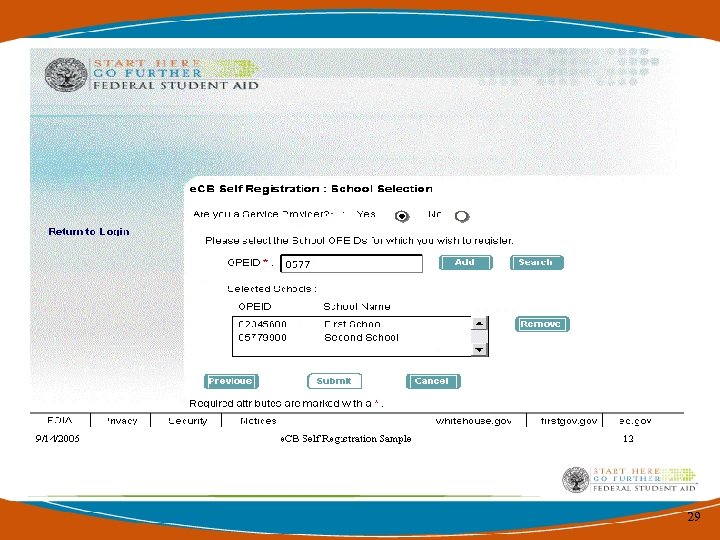
 Access Rights for Multiple Schools • If you are a Service Provider with more than 1 campus or Institution please register complete access rights for each OPEID and access for each cycle year. 35
Access Rights for Multiple Schools • If you are a Service Provider with more than 1 campus or Institution please register complete access rights for each OPEID and access for each cycle year. 35
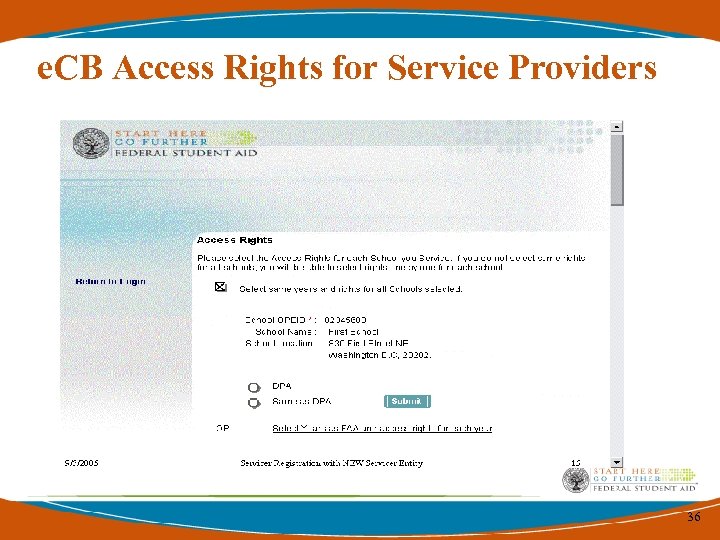 e. CB Access Rights for Service Providers 36
e. CB Access Rights for Service Providers 36
 Access Rights • If you are a DPA or Service Provider with more than 1 campus or Institution, please register complete access rights for each OPEID. 37
Access Rights • If you are a DPA or Service Provider with more than 1 campus or Institution, please register complete access rights for each OPEID. 37
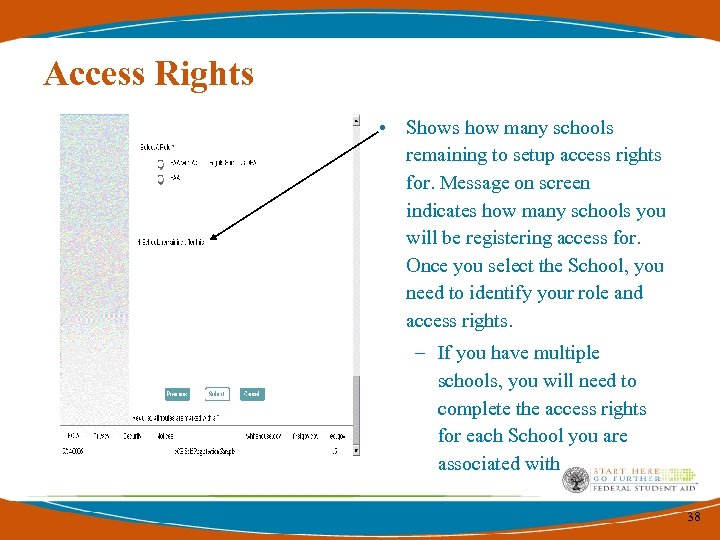 Access Rights • Shows how many schools remaining to setup access rights for. Message on screen indicates how many schools you will be registering access for. Once you select the School, you need to identify your role and access rights. – If you have multiple schools, you will need to complete the access rights for each School you are associated with 38
Access Rights • Shows how many schools remaining to setup access rights for. Message on screen indicates how many schools you will be registering access for. Once you select the School, you need to identify your role and access rights. – If you have multiple schools, you will need to complete the access rights for each School you are associated with 38
 Access Rights for Multiple Schools • If you are a DPA or Service Provider with more than 1 campus or Institution, please register complete access rights for each OPEID and access for each cycle year. 39
Access Rights for Multiple Schools • If you are a DPA or Service Provider with more than 1 campus or Institution, please register complete access rights for each OPEID and access for each cycle year. 39
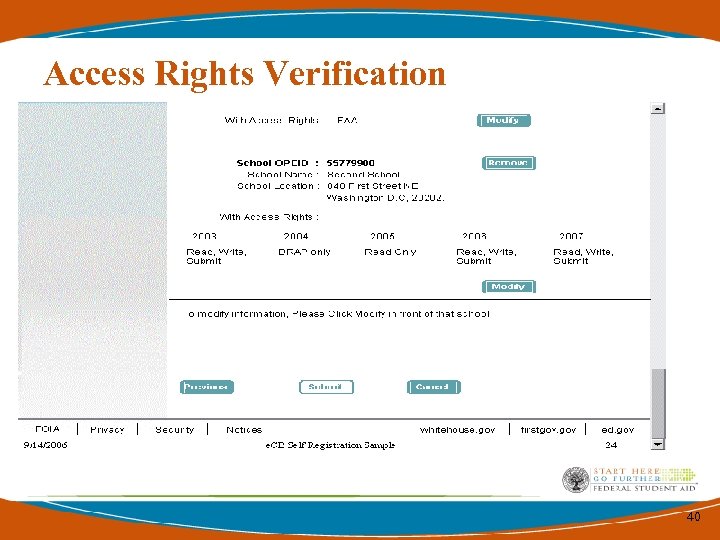 Access Rights Verification 40
Access Rights Verification 40
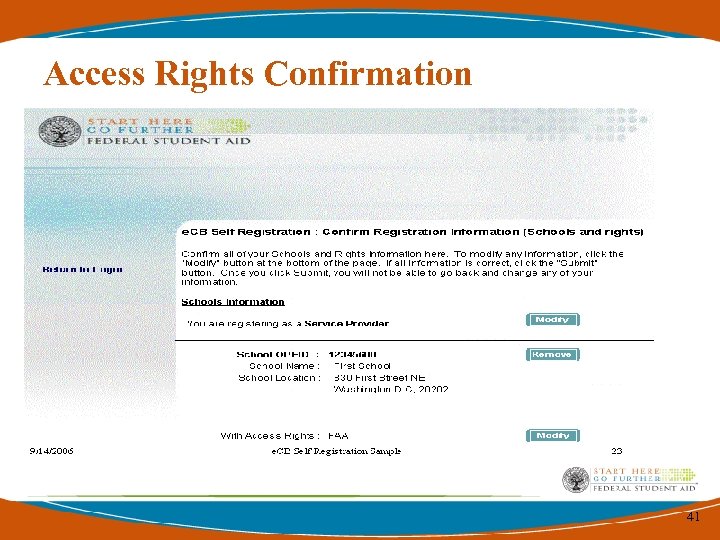 Access Rights Confirmation 41
Access Rights Confirmation 41
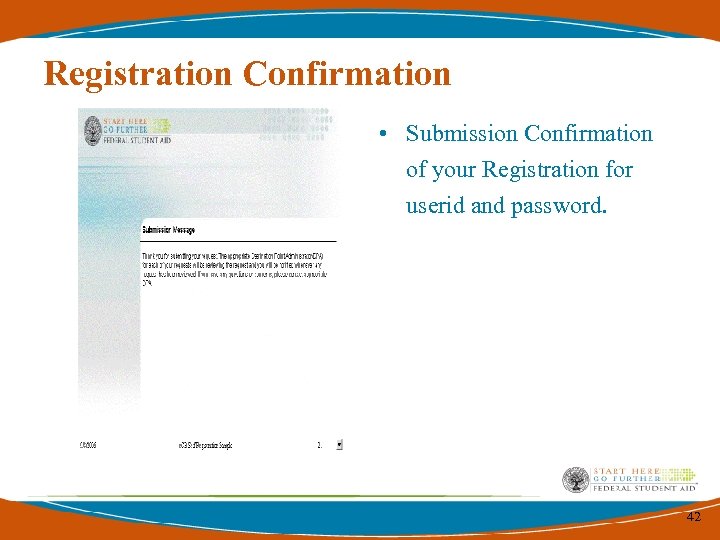 Registration Confirmation • Submission Confirmation of your Registration for userid and password. 42
Registration Confirmation • Submission Confirmation of your Registration for userid and password. 42
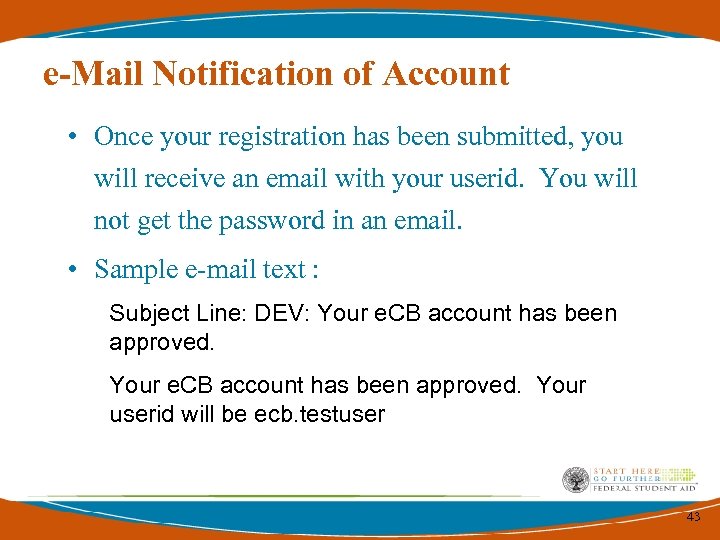 e-Mail Notification of Account • Once your registration has been submitted, you will receive an email with your userid. You will not get the password in an email. • Sample e-mail text : Subject Line: DEV: Your e. CB account has been approved. Your userid will be ecb. testuser 43
e-Mail Notification of Account • Once your registration has been submitted, you will receive an email with your userid. You will not get the password in an email. • Sample e-mail text : Subject Line: DEV: Your e. CB account has been approved. Your userid will be ecb. testuser 43
 What Next? • After your initial registration, you will go to www. cbfisap. ed. gov and click “login” • You will be directed to the Security Architecture Screen to provide your userid and password. • You will no longer need to provide your SSN, DOB, First 2 letter of last name or PIN. • We will verify you are in the database and then pass your access rights back to e. CB and you will continue to work in the application. 44
What Next? • After your initial registration, you will go to www. cbfisap. ed. gov and click “login” • You will be directed to the Security Architecture Screen to provide your userid and password. • You will no longer need to provide your SSN, DOB, First 2 letter of last name or PIN. • We will verify you are in the database and then pass your access rights back to e. CB and you will continue to work in the application. 44
 E-Authentication Overview
E-Authentication Overview
 What is E-Authentication? • It is about authenticating identity credentials…but the set of identity credentials is expanded…to include other external electronic credentials. • For Federal Student Aid business systems… you could use your school credential to access our systems instead of the ones we provide. • For other Federal Agency business systems…you could do the same thing. 46
What is E-Authentication? • It is about authenticating identity credentials…but the set of identity credentials is expanded…to include other external electronic credentials. • For Federal Student Aid business systems… you could use your school credential to access our systems instead of the ones we provide. • For other Federal Agency business systems…you could do the same thing. 46
 How Could This Happen? • Approach this as an enterprise initiative. In this case, the enterprise is the federal government. • Get executive sponsorship. Federal agencies are participating as part of the Presidential Management Agenda (PMA) e. Gov initiative. • Establish the standards, governance agreements and technology that build a “circle of trust”. 47
How Could This Happen? • Approach this as an enterprise initiative. In this case, the enterprise is the federal government. • Get executive sponsorship. Federal agencies are participating as part of the Presidential Management Agenda (PMA) e. Gov initiative. • Establish the standards, governance agreements and technology that build a “circle of trust”. 47
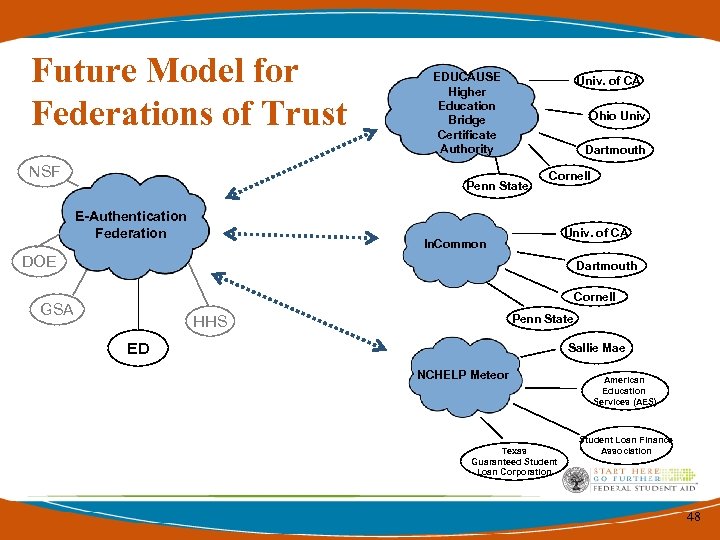 Future Model for Federations of Trust NSF EDUCAUSE Higher Education Bridge Certificate Authority Univ. of CA Ohio Univ. Dartmouth Penn State E-Authentication Federation Cornell Univ. of CA In. Common DOE Dartmouth Cornell GSA Penn State HHS ED Sallie Mae NCHELP Meteor Texas Guaranteed Student Loan Corporation American Education Services (AES) Student Loan Finance Association 48
Future Model for Federations of Trust NSF EDUCAUSE Higher Education Bridge Certificate Authority Univ. of CA Ohio Univ. Dartmouth Penn State E-Authentication Federation Cornell Univ. of CA In. Common DOE Dartmouth Cornell GSA Penn State HHS ED Sallie Mae NCHELP Meteor Texas Guaranteed Student Loan Corporation American Education Services (AES) Student Loan Finance Association 48
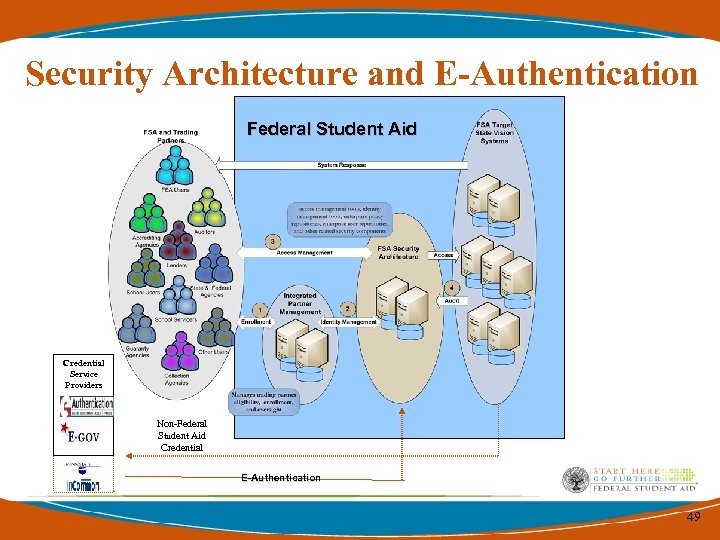 Security Architecture and E-Authentication Federal Student Aid Credential Service Providers Non-Federal Student Aid Credential E-Authentication 49
Security Architecture and E-Authentication Federal Student Aid Credential Service Providers Non-Federal Student Aid Credential E-Authentication 49
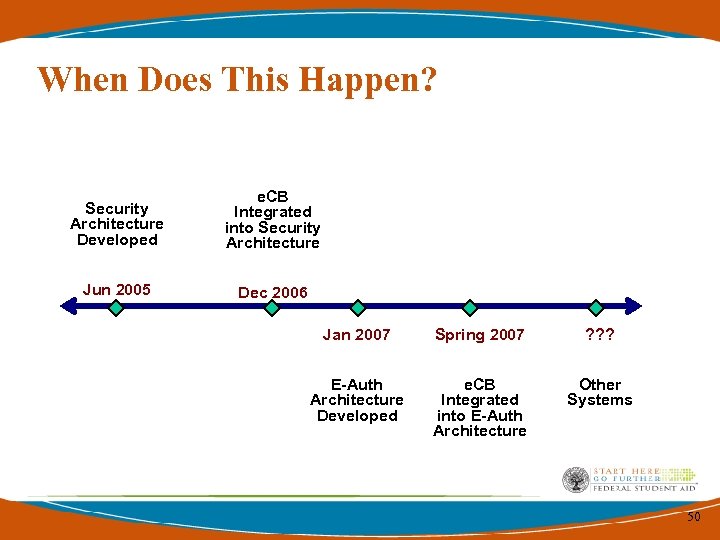 When Does This Happen? Security Architecture Developed e. CB Integrated into Security Architecture Jun 2005 Dec 2006 Jan 2007 Spring 2007 ? ? ? E-Auth Architecture Developed e. CB Integrated into E-Auth Architecture Other Systems 50
When Does This Happen? Security Architecture Developed e. CB Integrated into Security Architecture Jun 2005 Dec 2006 Jan 2007 Spring 2007 ? ? ? E-Auth Architecture Developed e. CB Integrated into E-Auth Architecture Other Systems 50
 Contact Information We appreciate your feedback and comments. We can be reached at: Name: Phone: Email: Katie Blot 202 -377 -3528 Katie. Blot@ed. gov Name: Phone: Email: Nina Colon 202 -377 -3384 Nina. Colon@ed. gov 51
Contact Information We appreciate your feedback and comments. We can be reached at: Name: Phone: Email: Katie Blot 202 -377 -3528 Katie. Blot@ed. gov Name: Phone: Email: Nina Colon 202 -377 -3384 Nina. Colon@ed. gov 51


