ddd55b9ec5010919d97153d1c5392065.ppt
- Количество слайдов: 41
 Session (5) Secure Unix Administration
Session (5) Secure Unix Administration
 User Management The /etc/passwd file contains: Login name Encrypted password when shadow file is not used UID Default GID “GECOS” information: full name, office, extension, home phone. chfn (passwd –g on solaries) Home directory Login shell The contents of a passwd file maybe shared with other systems with shared access through NIS or NISPlus. The user name must be meaningful while being of a reasonable size. If there is a name that is too long, one can make a short version and add an alias in the /etc/mail/aliases directory to refer to the long name. For instance, Rahman Tashakkori is rt on cs. An alias could be added in the aliases file as: rtashakkori. Security tip: avoid duplicate ids on different systems on the same network. At some point you may decide to share resources and that can cause problems. This in particular may cause a serious problem with e-mail.
User Management The /etc/passwd file contains: Login name Encrypted password when shadow file is not used UID Default GID “GECOS” information: full name, office, extension, home phone. chfn (passwd –g on solaries) Home directory Login shell The contents of a passwd file maybe shared with other systems with shared access through NIS or NISPlus. The user name must be meaningful while being of a reasonable size. If there is a name that is too long, one can make a short version and add an alias in the /etc/mail/aliases directory to refer to the long name. For instance, Rahman Tashakkori is rt on cs. An alias could be added in the aliases file as: rtashakkori. Security tip: avoid duplicate ids on different systems on the same network. At some point you may decide to share resources and that can cause problems. This in particular may cause a serious problem with e-mail.
 The /etc/master. passwd file On Free. BSD, the real passwd file is /etc/master. passwd. The /etc/paaswd file exists for backward compatibility, but it is generated from the master. passwd file and is never edited directly. This file acts like the shadow file which is readable by root only. The master. passwd file contains three additional fields: • Login class – determines user resource limits and control other login settings. It is an entry in the /etc/login. conf file. • Password change time - known as “password aging”. It contains the time after which the user will be forced to change his/her password. • Expiration time – the time and date at which the account will expire. The user will not be able to log into the system after the expiration time unless the account is reset.
The /etc/master. passwd file On Free. BSD, the real passwd file is /etc/master. passwd. The /etc/paaswd file exists for backward compatibility, but it is generated from the master. passwd file and is never edited directly. This file acts like the shadow file which is readable by root only. The master. passwd file contains three additional fields: • Login class – determines user resource limits and control other login settings. It is an entry in the /etc/login. conf file. • Password change time - known as “password aging”. It contains the time after which the user will be forced to change his/her password. • Expiration time – the time and date at which the account will expire. The user will not be able to log into the system after the expiration time unless the account is reset.
 Echelon, the U. S. -based spy system whose existence has been long rumored but never substantiated, does indeed exist and poses a serious privacy threat, according to a newly released, 108 -page report from the European Parliament. The report is based upon interviews with experts in the fields of security and communications, who have provided testimony that the United Kingdom, Australia, Canada, and New Zealand are helping the United States manage the communicationsinterception system. The report claims that Echelon intercepts "a very small portion" of corporate and civilian communications across the globe, but could come up with no proof that the system is sharing these communications with U. S. companies. The report suggests that computer users protect their e-mail communications from Echelon by using encryption. (Associated Press, 29 May 2001) Thanks to Dr. Kenneth Jacker for providing the news.
Echelon, the U. S. -based spy system whose existence has been long rumored but never substantiated, does indeed exist and poses a serious privacy threat, according to a newly released, 108 -page report from the European Parliament. The report is based upon interviews with experts in the fields of security and communications, who have provided testimony that the United Kingdom, Australia, Canada, and New Zealand are helping the United States manage the communicationsinterception system. The report claims that Echelon intercepts "a very small portion" of corporate and civilian communications across the globe, but could come up with no proof that the system is sharing these communications with U. S. companies. The report suggests that computer users protect their e-mail communications from Echelon by using encryption. (Associated Press, 29 May 2001) Thanks to Dr. Kenneth Jacker for providing the news.
 Free. BSD /etc/login. conf file This file sets account-related parameters for users and groups of users. It follows the same format as termcap and printcap. Entries in this file are: Resource limits (max process size, number of open files, etc. . ) Session accounting limits (when login is allowed and for how long) Default environment variables Default paths (PATH, MANPATH, etc…) Location of the message of the day Host and TTY-based access control Default umask Account control (min password length, password aging) Example: sysadmin: : ignorenologin: : requirehome@: : maxproc=unlimited: : openfiles=unlimited: : tc=default: who? can login even if nologin No need for /home, NFS fail Unlimited number of processes Unlimited open files Use the default for other entries
Free. BSD /etc/login. conf file This file sets account-related parameters for users and groups of users. It follows the same format as termcap and printcap. Entries in this file are: Resource limits (max process size, number of open files, etc. . ) Session accounting limits (when login is allowed and for how long) Default environment variables Default paths (PATH, MANPATH, etc…) Location of the message of the day Host and TTY-based access control Default umask Account control (min password length, password aging) Example: sysadmin: : ignorenologin: : requirehome@: : maxproc=unlimited: : openfiles=unlimited: : tc=default: who? can login even if nologin No need for /home, NFS fail Unlimited number of processes Unlimited open files Use the default for other entries
 The shadow file This file is part of the added security precaution on Solaris, Iris and Red Hat Linux. This file is not a superset of passwd file. Both files must be maintained by manually. It contains 9 fields for each user: Login name Encrypted password Date of last password change Minimum number of days between password change Maximum number of days between password change Number of days to give advance notice regarding password expiration Account expiration date Flags – reserved for future use Example: rt: in. NO. VAsc 1 Wn. : 11031: : 180: 14: : 18627
The shadow file This file is part of the added security precaution on Solaris, Iris and Red Hat Linux. This file is not a superset of passwd file. Both files must be maintained by manually. It contains 9 fields for each user: Login name Encrypted password Date of last password change Minimum number of days between password change Maximum number of days between password change Number of days to give advance notice regarding password expiration Account expiration date Flags – reserved for future use Example: rt: in. NO. VAsc 1 Wn. : 11031: : 180: 14: : 18627
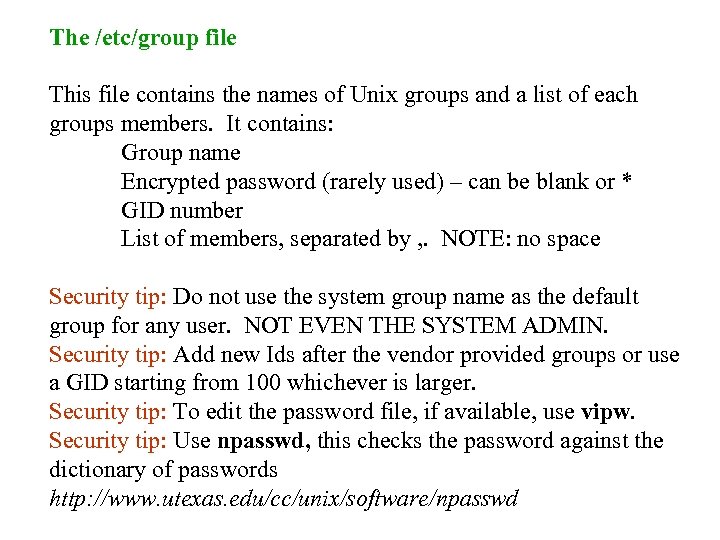 The /etc/group file This file contains the names of Unix groups and a list of each groups members. It contains: Group name Encrypted password (rarely used) – can be blank or * GID number List of members, separated by , . NOTE: no space Security tip: Do not use the system group name as the default group for any user. NOT EVEN THE SYSTEM ADMIN. Security tip: Add new Ids after the vendor provided groups or use a GID starting from 100 whichever is larger. Security tip: To edit the password file, if available, use vipw. Security tip: Use npasswd, this checks the password against the dictionary of passwords http: //www. utexas. edu/cc/unix/software/npasswd
The /etc/group file This file contains the names of Unix groups and a list of each groups members. It contains: Group name Encrypted password (rarely used) – can be blank or * GID number List of members, separated by , . NOTE: no space Security tip: Do not use the system group name as the default group for any user. NOT EVEN THE SYSTEM ADMIN. Security tip: Add new Ids after the vendor provided groups or use a GID starting from 100 whichever is larger. Security tip: To edit the password file, if available, use vipw. Security tip: Use npasswd, this checks the password against the dictionary of passwords http: //www. utexas. edu/cc/unix/software/npasswd
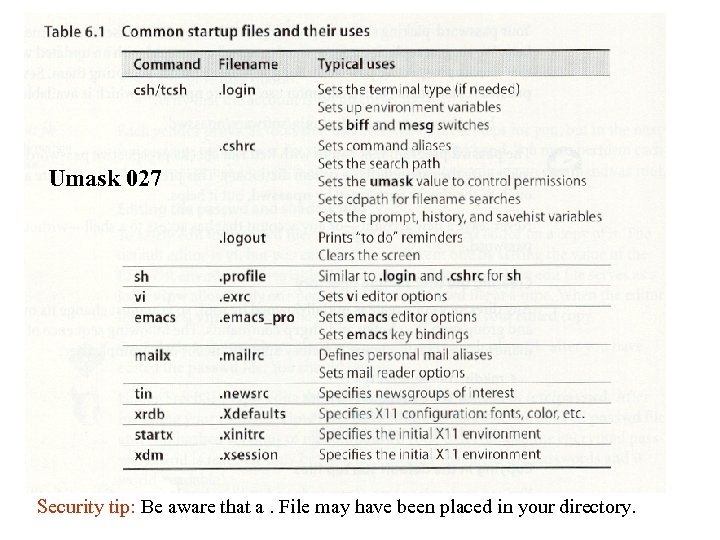 Umask 027 Security tip: Be aware that a. File may have been placed in your directory.
Umask 027 Security tip: Be aware that a. File may have been placed in your directory.
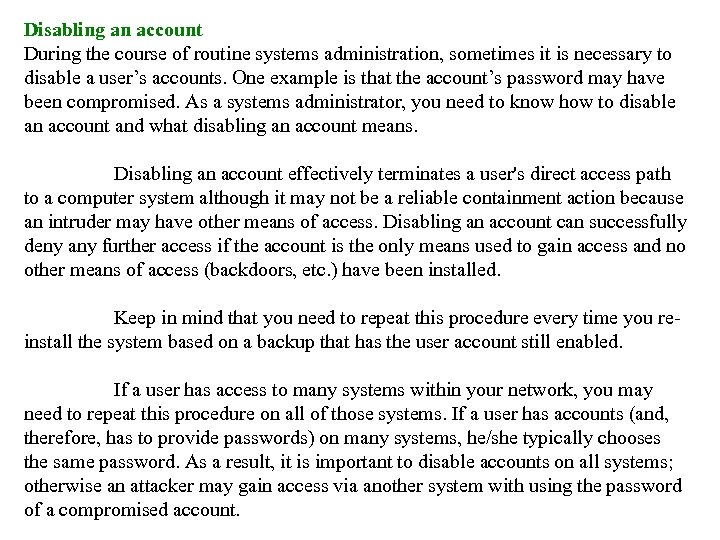 Disabling an account During the course of routine systems administration, sometimes it is necessary to disable a user’s accounts. One example is that the account’s password may have been compromised. As a systems administrator, you need to know how to disable an account and what disabling an account means. Disabling an account effectively terminates a user's direct access path to a computer system although it may not be a reliable containment action because an intruder may have other means of access. Disabling an account can successfully deny any further access if the account is the only means used to gain access and no other means of access (backdoors, etc. ) have been installed. Keep in mind that you need to repeat this procedure every time you reinstall the system based on a backup that has the user account still enabled. If a user has access to many systems within your network, you may need to repeat this procedure on all of those systems. If a user has accounts (and, therefore, has to provide passwords) on many systems, he/she typically chooses the same password. As a result, it is important to disable accounts on all systems; otherwise an attacker may gain access via another system with using the password of a compromised account.
Disabling an account During the course of routine systems administration, sometimes it is necessary to disable a user’s accounts. One example is that the account’s password may have been compromised. As a systems administrator, you need to know how to disable an account and what disabling an account means. Disabling an account effectively terminates a user's direct access path to a computer system although it may not be a reliable containment action because an intruder may have other means of access. Disabling an account can successfully deny any further access if the account is the only means used to gain access and no other means of access (backdoors, etc. ) have been installed. Keep in mind that you need to repeat this procedure every time you reinstall the system based on a backup that has the user account still enabled. If a user has access to many systems within your network, you may need to repeat this procedure on all of those systems. If a user has accounts (and, therefore, has to provide passwords) on many systems, he/she typically chooses the same password. As a result, it is important to disable accounts on all systems; otherwise an attacker may gain access via another system with using the password of a compromised account.
 We recommend that you begin this process by creating the following directory: # mkdir /root/disabled_users # chmod 0700 /root/disabled_users # mkdir /root/disabled_users/fred # chmod 0700 /root/disabled_users/fred At this early stage, save all timestamp information about the entire file system. # /usr/local/tct/bin/mactime -y -d / -R 1/1/1970 > /root/disabled_users/fred/timestamp # compress /root/disabled_users/fred/timestamps Switch to single user mode. # init 1 Remove cron and at jobs. To transfer any cron job, use the following command: # mv /var/spool/cronjobs/fred /root/disabled_users/fred. cron To transfer all at jobs for a user, all files belonging to that user need to be specified: # find /var/spool/cron/atjobs/* -user fred -print
We recommend that you begin this process by creating the following directory: # mkdir /root/disabled_users # chmod 0700 /root/disabled_users # mkdir /root/disabled_users/fred # chmod 0700 /root/disabled_users/fred At this early stage, save all timestamp information about the entire file system. # /usr/local/tct/bin/mactime -y -d / -R 1/1/1970 > /root/disabled_users/fred/timestamp # compress /root/disabled_users/fred/timestamps Switch to single user mode. # init 1 Remove cron and at jobs. To transfer any cron job, use the following command: # mv /var/spool/cronjobs/fred /root/disabled_users/fred. cron To transfer all at jobs for a user, all files belonging to that user need to be specified: # find /var/spool/cron/atjobs/* -user fred -print
 For example, if the above command reveals that Fred owns the at job a 0000300 f 66, perform the following steps : # mkdir /root/disabled_users/fred/at # mv /var/spool/cron/atjobs/a 0000300 f 66 /root/disabled_users/fred/at/ Finally, disable execution of at jobs by removing the user's name from the file /usr/lib/cron/atd. allow (if applicable) and inserting the user's name into the file /usr/lib/cron/atd. deny. Transfer all user files to a protected directory. # cd /users/fred # /usr/local/bin/tar -cvf /root/disabled_users/fred/users. fred. tar. # compress /root/disabled_users/fred/users. fred. tar Once you are sure that all of the user’s files have been copied and compressed, remove them from the user's home directory and also remove the home directory itself.
For example, if the above command reveals that Fred owns the at job a 0000300 f 66, perform the following steps : # mkdir /root/disabled_users/fred/at # mv /var/spool/cron/atjobs/a 0000300 f 66 /root/disabled_users/fred/at/ Finally, disable execution of at jobs by removing the user's name from the file /usr/lib/cron/atd. allow (if applicable) and inserting the user's name into the file /usr/lib/cron/atd. deny. Transfer all user files to a protected directory. # cd /users/fred # /usr/local/bin/tar -cvf /root/disabled_users/fred/users. fred. tar. # compress /root/disabled_users/fred/users. fred. tar Once you are sure that all of the user’s files have been copied and compressed, remove them from the user's home directory and also remove the home directory itself.
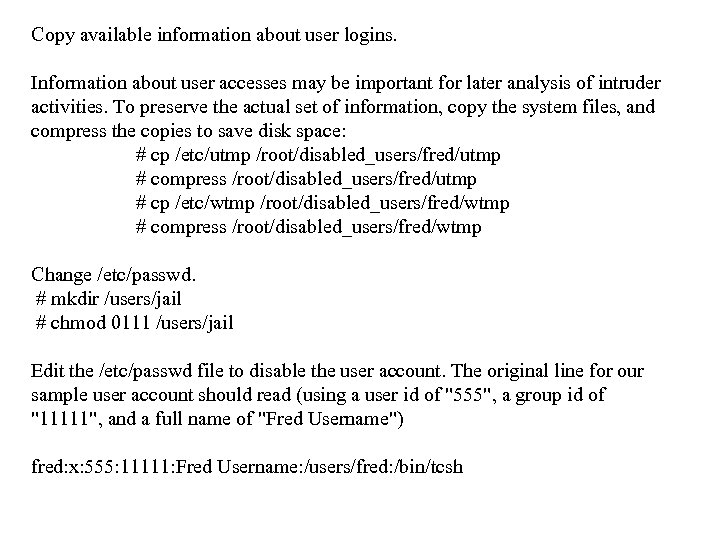 Copy available information about user logins. Information about user accesses may be important for later analysis of intruder activities. To preserve the actual set of information, copy the system files, and compress the copies to save disk space: # cp /etc/utmp /root/disabled_users/fred/utmp # compress /root/disabled_users/fred/utmp # cp /etc/wtmp /root/disabled_users/fred/wtmp # compress /root/disabled_users/fred/wtmp Change /etc/passwd. # mkdir /users/jail # chmod 0111 /users/jail Edit the /etc/passwd file to disable the user account. The original line for our sample user account should read (using a user id of "555", a group id of "11111", and a full name of "Fred Username") fred: x: 555: 11111: Fred Username: /users/fred: /bin/tcsh
Copy available information about user logins. Information about user accesses may be important for later analysis of intruder activities. To preserve the actual set of information, copy the system files, and compress the copies to save disk space: # cp /etc/utmp /root/disabled_users/fred/utmp # compress /root/disabled_users/fred/utmp # cp /etc/wtmp /root/disabled_users/fred/wtmp # compress /root/disabled_users/fred/wtmp Change /etc/passwd. # mkdir /users/jail # chmod 0111 /users/jail Edit the /etc/passwd file to disable the user account. The original line for our sample user account should read (using a user id of "555", a group id of "11111", and a full name of "Fred Username") fred: x: 555: 11111: Fred Username: /users/fred: /bin/tcsh
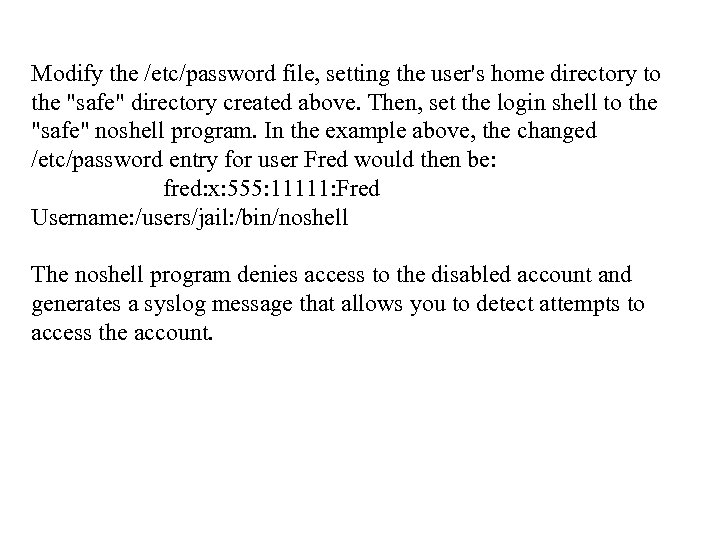 Modify the /etc/password file, setting the user's home directory to the "safe" directory created above. Then, set the login shell to the "safe" noshell program. In the example above, the changed /etc/password entry for user Fred would then be: fred: x: 555: 11111: Fred Username: /users/jail: /bin/noshell The noshell program denies access to the disabled account and generates a syslog message that allows you to detect attempts to access the account.
Modify the /etc/password file, setting the user's home directory to the "safe" directory created above. Then, set the login shell to the "safe" noshell program. In the example above, the changed /etc/password entry for user Fred would then be: fred: x: 555: 11111: Fred Username: /users/jail: /bin/noshell The noshell program denies access to the disabled account and generates a syslog message that allows you to detect attempts to access the account.
 Change /etc/ftpusers. The disabled account cannot be used by ftp once the password in the /etc/shadow file is disabled (as explained in the next step). Even so, adding the user name to /etc/ftpusers disables any ftp access independent of any other configuration. Change /etc/shadow. fred: dsaf. FDQp/c 2 a. Y: 6445: : : to the following line: fred: *NK*: 6445: : : Disable the user's account in any application-specific account database. Often users use the same password for every system and application they are accessing. All other system and application-specific accounts that the user had access to should be disabled. Refer to the application-specific documentation. Reboot to switch back to multi-user mode. Initiate multi-user mode by rebooting with the following command: # init 6 Reference: http: //www. cert. org/security-improvement/implementations/i 049. 04. html
Change /etc/ftpusers. The disabled account cannot be used by ftp once the password in the /etc/shadow file is disabled (as explained in the next step). Even so, adding the user name to /etc/ftpusers disables any ftp access independent of any other configuration. Change /etc/shadow. fred: dsaf. FDQp/c 2 a. Y: 6445: : : to the following line: fred: *NK*: 6445: : : Disable the user's account in any application-specific account database. Often users use the same password for every system and application they are accessing. All other system and application-specific accounts that the user had access to should be disabled. Refer to the application-specific documentation. Reboot to switch back to multi-user mode. Initiate multi-user mode by rebooting with the following command: # init 6 Reference: http: //www. cert. org/security-improvement/implementations/i 049. 04. html
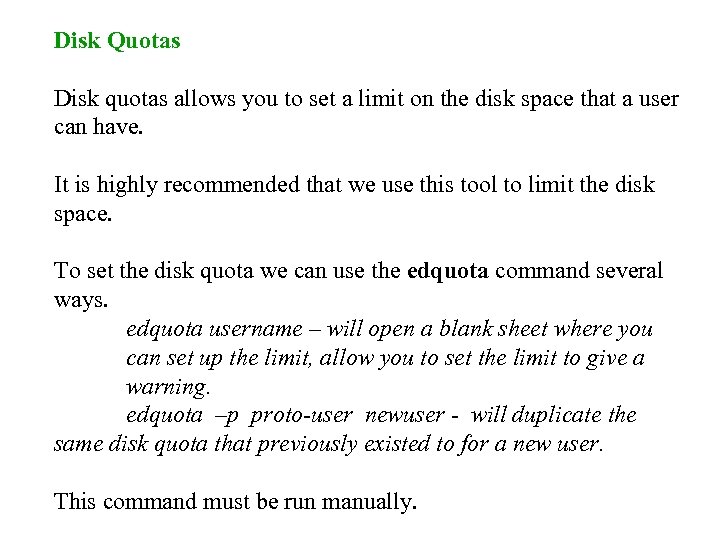 Disk Quotas Disk quotas allows you to set a limit on the disk space that a user can have. It is highly recommended that we use this tool to limit the disk space. To set the disk quota we can use the edquota command several ways. edquota username – will open a blank sheet where you can set up the limit, allow you to set the limit to give a warning. edquota –p proto-user newuser - will duplicate the same disk quota that previously existed to for a new user. This command must be run manually.
Disk Quotas Disk quotas allows you to set a limit on the disk space that a user can have. It is highly recommended that we use this tool to limit the disk space. To set the disk quota we can use the edquota command several ways. edquota username – will open a blank sheet where you can set up the limit, allow you to set the limit to give a warning. edquota –p proto-user newuser - will duplicate the same disk quota that previously existed to for a new user. This command must be run manually.
 Periodic Processes Automation of different tasks on the system provides more control of the system to the system administrator. Almost all tasks can be coded in shell, Perl, or expect script. On Unix machines, periodic execution is handled by the cron daemon. cron starts when the system boots and remains running as long as the system is up. cron reads one or more configuration files containing the lists of command lines and times at which they are to be invoked. The command lines are executed by sh. A cron configuration file is called a “crontab”, short for “cron table. ”
Periodic Processes Automation of different tasks on the system provides more control of the system to the system administrator. Almost all tasks can be coded in shell, Perl, or expect script. On Unix machines, periodic execution is handled by the cron daemon. cron starts when the system boots and remains running as long as the system is up. cron reads one or more configuration files containing the lists of command lines and times at which they are to be invoked. The command lines are executed by sh. A cron configuration file is called a “crontab”, short for “cron table. ”
 cron – cont. Typically, there is one crontab file per user. crontab files are named with the login names of the users. cron uses these filenames to find out which UID to use when running the commands that each file contains. Old version of cron – scans the crontab periodically and execute all commands that should have been run since the last scan. Modern version of cron – parses the crontabs, figures out which one of the listed commands needs to be run soonest, and go to sleep until the command’s execution time has arrived. A hangup signal is not necessary to force the cron to reread the crontab, crontab automatically tells cron to update itself whenever it changes a configuration file.
cron – cont. Typically, there is one crontab file per user. crontab files are named with the login names of the users. cron uses these filenames to find out which UID to use when running the commands that each file contains. Old version of cron – scans the crontab periodically and execute all commands that should have been run since the last scan. Modern version of cron – parses the crontabs, figures out which one of the listed commands needs to be run soonest, and go to sleep until the command’s execution time has arrived. A hangup signal is not necessary to force the cron to reread the crontab, crontab automatically tells cron to update itself whenever it changes a configuration file.
 cron – cont. cron usually does its work silently, but some versions can keep a log file /var/cron/log or /var/adm/crn/log that lists the commands that were executed and the times at which they ran. The logging flag must be off by default until a problem has been noticed. Two problems that must be watched closely: 1. Most crons do not compensate for commands that are missed while the system is down. 2. Some versions of cron do not understand daylight saving time. That results in some commands to skip or to run twice.
cron – cont. cron usually does its work silently, but some versions can keep a log file /var/cron/log or /var/adm/crn/log that lists the commands that were executed and the times at which they ran. The logging flag must be off by default until a problem has been noticed. Two problems that must be watched closely: 1. Most crons do not compensate for commands that are missed while the system is down. 2. Some versions of cron do not understand daylight saving time. That results in some commands to skip or to run twice.
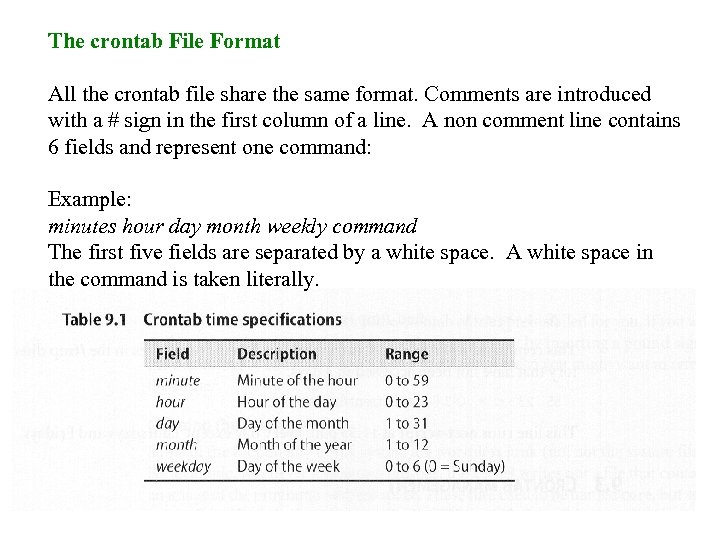 The crontab File Format All the crontab file share the same format. Comments are introduced with a # sign in the first column of a line. A non comment line contains 6 fields and represent one command: Example: minutes hour day month weekly command The first five fields are separated by a white space. A white space in the command is taken literally.
The crontab File Format All the crontab file share the same format. Comments are introduced with a # sign in the first column of a line. A non comment line contains 6 fields and represent one command: Example: minutes hour day month weekly command The first five fields are separated by a white space. A white space in the command is taken literally.
 The crontab File Format Each of the time-related fields may contain • • A star, which matches everything A single integer, which matches exactly Two integers separated by a dash, matching a range of values A comma-separated series of integers or ranges, matching any listed value Example: 45 10 * * 1 -5 means “ 10: 45 a. m. Monday through Friday. ” Warning: never put a * in the first field, unless you want the command to run every minute. What does this mean? 0, 30 * 13 * 5 a) Every 30 minutes on Friday and every 30 minutes on the 13 th of the month b) Every 30 minutes on Friday the 13 th
The crontab File Format Each of the time-related fields may contain • • A star, which matches everything A single integer, which matches exactly Two integers separated by a dash, matching a range of values A comma-separated series of integers or ranges, matching any listed value Example: 45 10 * * 1 -5 means “ 10: 45 a. m. Monday through Friday. ” Warning: never put a * in the first field, unless you want the command to run every minute. What does this mean? 0, 30 * 13 * 5 a) Every 30 minutes on Friday and every 30 minutes on the 13 th of the month b) Every 30 minutes on Friday the 13 th
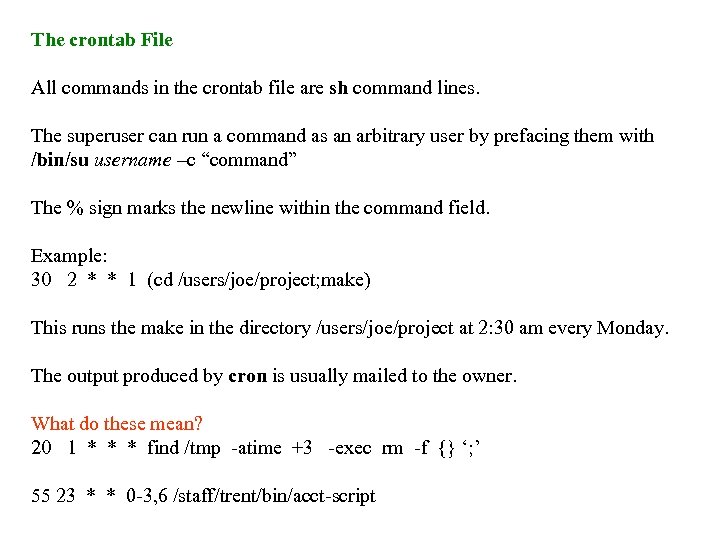 The crontab File All commands in the crontab file are sh command lines. The superuser can run a command as an arbitrary user by prefacing them with /bin/su username –c “command” The % sign marks the newline within the command field. Example: 30 2 * * 1 (cd /users/joe/project; make) This runs the make in the directory /users/joe/project at 2: 30 am every Monday. The output produced by cron is usually mailed to the owner. What do these mean? 20 1 * * * find /tmp -atime +3 -exec rm -f {} ‘; ’ 55 23 * * 0 -3, 6 /staff/trent/bin/acct-script
The crontab File All commands in the crontab file are sh command lines. The superuser can run a command as an arbitrary user by prefacing them with /bin/su username –c “command” The % sign marks the newline within the command field. Example: 30 2 * * 1 (cd /users/joe/project; make) This runs the make in the directory /users/joe/project at 2: 30 am every Monday. The output produced by cron is usually mailed to the owner. What do these mean? 20 1 * * * find /tmp -atime +3 -exec rm -f {} ‘; ’ 55 23 * * 0 -3, 6 /staff/trent/bin/acct-script
 crontab Management crontab filename installs filename as the desired crontab replacing the previous file. crontab –e – checks out a copy of your crontab, invokes your editor on it (it is defined by the editor environment variable), and then resubmits it to the crontab directory. crontab –l – lists the contents of your crontab to standard output. crontab –r – removes it, no crontab file will remain. crontab –r username – erases the crontab belonging to the username. Warning: If you execute crontab without an argument, it will try to read the crontab from the standard input. DO NOT Use Ctrl-D to exit, this will erase the entire crontab file. Use Ctrl-C instead.
crontab Management crontab filename installs filename as the desired crontab replacing the previous file. crontab –e – checks out a copy of your crontab, invokes your editor on it (it is defined by the editor environment variable), and then resubmits it to the crontab directory. crontab –l – lists the contents of your crontab to standard output. crontab –r – removes it, no crontab file will remain. crontab –r username – erases the crontab belonging to the username. Warning: If you execute crontab without an argument, it will try to read the crontab from the standard input. DO NOT Use Ctrl-D to exit, this will erase the entire crontab file. Use Ctrl-C instead.
 crontab Management All users can submit crontab files to cron. Two configuration files: cron. allow cron. deny allow you to override this policy. Depending on the system these files may be found under /etc/cron. d /usr/lib/cron /var/spool/cron /var/cron – Free. BSD and they are called allow and deny. The allow or cron. allow file contains all users who may submit crontabs, one user per line. In the case that the allow file does not exist, the cron. deny or deny is checked to find out who does not have access. Note: The access control is defined by crontab not cron.
crontab Management All users can submit crontab files to cron. Two configuration files: cron. allow cron. deny allow you to override this policy. Depending on the system these files may be found under /etc/cron. d /usr/lib/cron /var/spool/cron /var/cron – Free. BSD and they are called allow and deny. The allow or cron. allow file contains all users who may submit crontabs, one user per line. In the case that the allow file does not exist, the cron. deny or deny is checked to find out who does not have access. Note: The access control is defined by crontab not cron.
 Some Common Uses for CRON Cleaning the filesystem (core files, NSF temp files, …) • Core files are the files that kernels writes whenever a crash occurs. • Since NFS is stateless, it uses a special convention to preserve files that are in use by remote machines but have been deleted on the server. These files will be names as. nsfxxx where xxx is a number. • Many programs create temporary files in /tmp or /var/tmp directory. A system administrator may have an script that erases the files on nightly base.
Some Common Uses for CRON Cleaning the filesystem (core files, NSF temp files, …) • Core files are the files that kernels writes whenever a crash occurs. • Since NFS is stateless, it uses a special convention to preserve files that are in use by remote machines but have been deleted on the server. These files will be names as. nsfxxx where xxx is a number. • Many programs create temporary files in /tmp or /var/tmp directory. A system administrator may have an script that erases the files on nightly base.
 Some Common Uses for CRON Below is the list of some of these house keeping commands: %find / -xdev –name core –atime +7 –exec rm –f {} ‘; ’ You need to make sure not to remove files that are cross mounted. The –xdev will check that you erase the filesystems owned by the root. %find / -xdev –atime +3 ‘(‘ –name ‘#*’ –o –name ‘. #*’–o -name ‘*. CKP’ –o –name ‘*~’ –o –name ‘. nfs*’ ‘)’ –exec rm –f {} ‘; ’ Deletes files that begin with #, end with. CKP or ~ or. nfsxxx.
Some Common Uses for CRON Below is the list of some of these house keeping commands: %find / -xdev –name core –atime +7 –exec rm –f {} ‘; ’ You need to make sure not to remove files that are cross mounted. The –xdev will check that you erase the filesystems owned by the root. %find / -xdev –atime +3 ‘(‘ –name ‘#*’ –o –name ‘. #*’–o -name ‘*. CKP’ –o –name ‘*~’ –o –name ‘. nfs*’ ‘)’ –exec rm –f {} ‘; ’ Deletes files that begin with #, end with. CKP or ~ or. nfsxxx.
 Some Common Uses for CRON %find /var/preserve –mtime +14 –exec rm –f {} ‘; ’ Removes files in /var/preserve two weeks after they were last modified. Examples of these type of files are those created by vi when for some reason the editing session is interrupted. These files can be recovered using vi –r filename. If they are not recovered, they are saved in the /var/preserve directory. %cd /tmp; find. ! –name lost+found –type d –mtime +3 –exec /bin/rm -rf {} ‘; ’ Recursively removes all subdirectories of /tmp not modified in 72 hours. Anything in /tmp may be deleted at the boot time, but files in lost+found will not be deleted.
Some Common Uses for CRON %find /var/preserve –mtime +14 –exec rm –f {} ‘; ’ Removes files in /var/preserve two weeks after they were last modified. Examples of these type of files are those created by vi when for some reason the editing session is interrupted. These files can be recovered using vi –r filename. If they are not recovered, they are saved in the /var/preserve directory. %cd /tmp; find. ! –name lost+found –type d –mtime +3 –exec /bin/rm -rf {} ‘; ’ Recursively removes all subdirectories of /tmp not modified in 72 hours. Anything in /tmp may be deleted at the boot time, but files in lost+found will not be deleted.
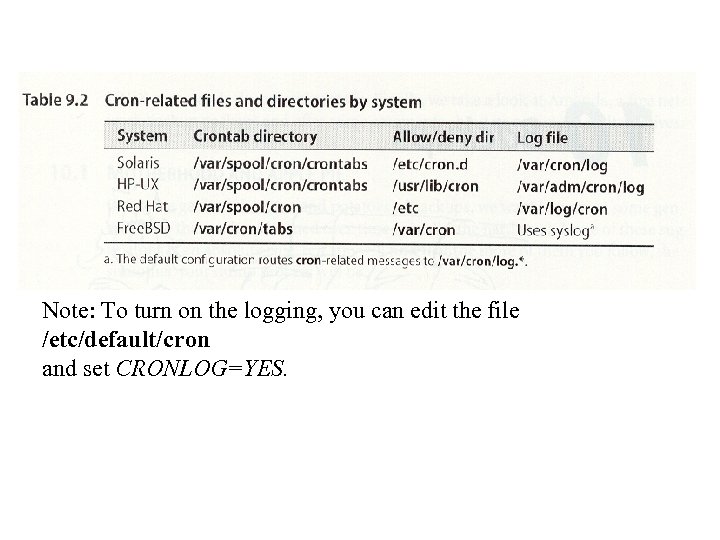 Note: To turn on the logging, you can edit the file /etc/default/cron and set CRONLOG=YES.
Note: To turn on the logging, you can edit the file /etc/default/cron and set CRONLOG=YES.
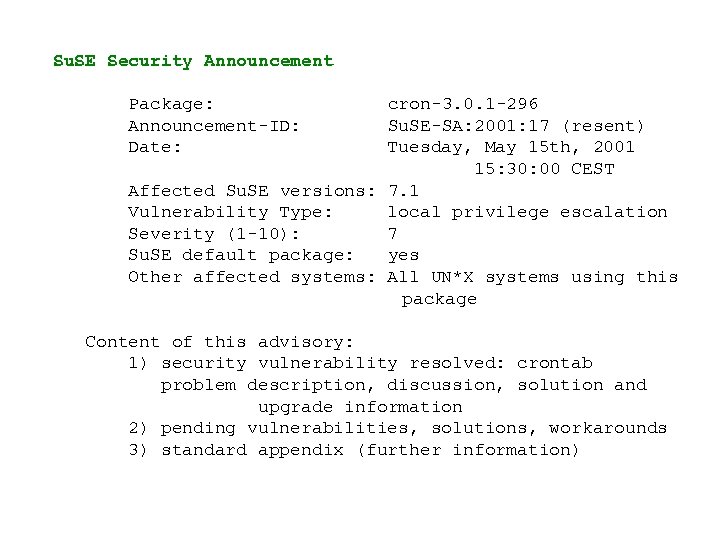 Su. SE Security Announcement Package: Announcement-ID: Date: cron-3. 0. 1 -296 Su. SE-SA: 2001: 17 (resent) Tuesday, May 15 th, 2001 15: 30: 00 CEST Affected Su. SE versions: 7. 1 Vulnerability Type: local privilege escalation Severity (1 -10): 7 Su. SE default package: yes Other affected systems: All UN*X systems using this package Content of this advisory: 1) security vulnerability resolved: crontab problem description, discussion, solution and upgrade information 2) pending vulnerabilities, solutions, workarounds 3) standard appendix (further information)
Su. SE Security Announcement Package: Announcement-ID: Date: cron-3. 0. 1 -296 Su. SE-SA: 2001: 17 (resent) Tuesday, May 15 th, 2001 15: 30: 00 CEST Affected Su. SE versions: 7. 1 Vulnerability Type: local privilege escalation Severity (1 -10): 7 Su. SE default package: yes Other affected systems: All UN*X systems using this package Content of this advisory: 1) security vulnerability resolved: crontab problem description, discussion, solution and upgrade information 2) pending vulnerabilities, solutions, workarounds 3) standard appendix (further information)
 1) problem description, brief discussion, solution, upgrade information The crontab program is running setuser-id root and invokes the editor specified in the EDITOR environment variable, usually vi. If crontab discovers that the format of the edited file is incorrect, it executes the editor again but fails to drop its root privileges before. Therefore it is possible to execute arbitrary commands as root. It has been fixed by properly dropping the privileges before executing the editor. This bug was found by Sebastian Krahmer. A possible temporary workaround is to remove the suid bit of the /usr/bin/crontab program: chmod -s /usr/bin/crontab. If you change the mode, you should also do so in the file /etc/permissions* A permanent solution for the problem is to update the cron package from our ftp server.
1) problem description, brief discussion, solution, upgrade information The crontab program is running setuser-id root and invokes the editor specified in the EDITOR environment variable, usually vi. If crontab discovers that the format of the edited file is incorrect, it executes the editor again but fails to drop its root privileges before. Therefore it is possible to execute arbitrary commands as root. It has been fixed by properly dropping the privileges before executing the editor. This bug was found by Sebastian Krahmer. A possible temporary workaround is to remove the suid bit of the /usr/bin/crontab program: chmod -s /usr/bin/crontab. If you change the mode, you should also do so in the file /etc/permissions* A permanent solution for the problem is to update the cron package from our ftp server.
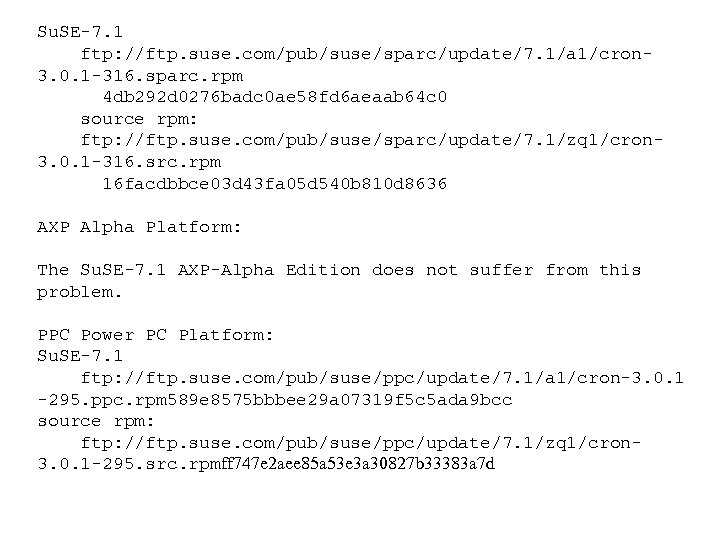 Su. SE-7. 1 ftp: //ftp. suse. com/pub/suse/sparc/update/7. 1/a 1/cron 3. 0. 1 -316. sparc. rpm 4 db 292 d 0276 badc 0 ae 58 fd 6 aeaab 64 c 0 source rpm: ftp: //ftp. suse. com/pub/suse/sparc/update/7. 1/zq 1/cron 3. 0. 1 -316. src. rpm 16 facdbbce 03 d 43 fa 05 d 540 b 810 d 8636 AXP Alpha Platform: The Su. SE-7. 1 AXP-Alpha Edition does not suffer from this problem. PPC Power PC Platform: Su. SE-7. 1 ftp: //ftp. suse. com/pub/suse/ppc/update/7. 1/a 1/cron-3. 0. 1 -295. ppc. rpm 589 e 8575 bbbee 29 a 07319 f 5 c 5 ada 9 bcc source rpm: ftp: //ftp. suse. com/pub/suse/ppc/update/7. 1/zq 1/cron 3. 0. 1 -295. src. rpmff 747 e 2 aee 85 a 53 e 3 a 30827 b 33383 a 7 d
Su. SE-7. 1 ftp: //ftp. suse. com/pub/suse/sparc/update/7. 1/a 1/cron 3. 0. 1 -316. sparc. rpm 4 db 292 d 0276 badc 0 ae 58 fd 6 aeaab 64 c 0 source rpm: ftp: //ftp. suse. com/pub/suse/sparc/update/7. 1/zq 1/cron 3. 0. 1 -316. src. rpm 16 facdbbce 03 d 43 fa 05 d 540 b 810 d 8636 AXP Alpha Platform: The Su. SE-7. 1 AXP-Alpha Edition does not suffer from this problem. PPC Power PC Platform: Su. SE-7. 1 ftp: //ftp. suse. com/pub/suse/ppc/update/7. 1/a 1/cron-3. 0. 1 -295. ppc. rpm 589 e 8575 bbbee 29 a 07319 f 5 c 5 ada 9 bcc source rpm: ftp: //ftp. suse. com/pub/suse/ppc/update/7. 1/zq 1/cron 3. 0. 1 -295. src. rpmff 747 e 2 aee 85 a 53 e 3 a 30827 b 33383 a 7 d
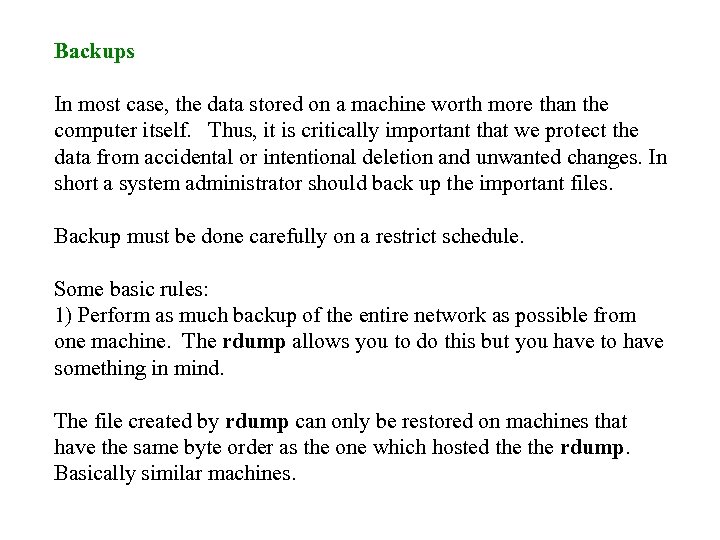 Backups In most case, the data stored on a machine worth more than the computer itself. Thus, it is critically important that we protect the data from accidental or intentional deletion and unwanted changes. In short a system administrator should back up the important files. Backup must be done carefully on a restrict schedule. Some basic rules: 1) Perform as much backup of the entire network as possible from one machine. The rdump allows you to do this but you have to have something in mind. The file created by rdump can only be restored on machines that have the same byte order as the one which hosted the rdump. Basically similar machines.
Backups In most case, the data stored on a machine worth more than the computer itself. Thus, it is critically important that we protect the data from accidental or intentional deletion and unwanted changes. In short a system administrator should back up the important files. Backup must be done carefully on a restrict schedule. Some basic rules: 1) Perform as much backup of the entire network as possible from one machine. The rdump allows you to do this but you have to have something in mind. The file created by rdump can only be restored on machines that have the same byte order as the one which hosted the rdump. Basically similar machines.
 Backup Rules 2) Label your tapes clearly The tape should include the name of the machine, file names, and dump date is almost critical. Remember, a tape without a label is a scratch tape. It is very important to label the tape with the exact dump command that has created the files. Thus, the restore can be done without trying to figure out the command. Labeling software and tools are very handy.
Backup Rules 2) Label your tapes clearly The tape should include the name of the machine, file names, and dump date is almost critical. Remember, a tape without a label is a scratch tape. It is very important to label the tape with the exact dump command that has created the files. Thus, the restore can be done without trying to figure out the command. Labeling software and tools are very handy.
 Backup Rules 3) Pick a good backup interval It is true that the more often we do the backup the less chance there is for a loss of major data. On the other hand we cannot do backup every minute. So the backup interval plays a major rule. On busy systems, back up of filesystems with home directories are done every workday. This back up is usually incremental during the week and is a complete backup at the end of the week. 4) Choose file system carefully File systems that are rarely modified do not need to be backed up as frequent as the files in the home directory. Some system files (/etc/passwd) that may be modified more often can be copied to a directory that is backed up everyday. DO NOT backup the /tmp directory at all.
Backup Rules 3) Pick a good backup interval It is true that the more often we do the backup the less chance there is for a loss of major data. On the other hand we cannot do backup every minute. So the backup interval plays a major rule. On busy systems, back up of filesystems with home directories are done every workday. This back up is usually incremental during the week and is a complete backup at the end of the week. 4) Choose file system carefully File systems that are rarely modified do not need to be backed up as frequent as the files in the home directory. Some system files (/etc/passwd) that may be modified more often can be copied to a directory that is backed up everyday. DO NOT backup the /tmp directory at all.
 Backup Rules 5) Make the daily backups fit on one tape In perfect situation, you will dump the entire network on a single tape. That is not always possible. But you want to do daily backups on a single tape. You can mount a tape in the morning and set the cron to backup after midnight. Of course, with the growth of disk space and the cost of the large hard disks, this is becoming harder and harder. Some quick fixes: a) Buy a large capacity tape drive (DLT, …) that can fit the daily backups. If you can afford the tape drive ! b) Buy a stacker or library and feed multiple pieces of media to one device c) Change your dump sequence. d) Write a smarter script. How smart can it get? e) Use multiple backup devices.
Backup Rules 5) Make the daily backups fit on one tape In perfect situation, you will dump the entire network on a single tape. That is not always possible. But you want to do daily backups on a single tape. You can mount a tape in the morning and set the cron to backup after midnight. Of course, with the growth of disk space and the cost of the large hard disks, this is becoming harder and harder. Some quick fixes: a) Buy a large capacity tape drive (DLT, …) that can fit the daily backups. If you can afford the tape drive ! b) Buy a stacker or library and feed multiple pieces of media to one device c) Change your dump sequence. d) Write a smarter script. How smart can it get? e) Use multiple backup devices.
 Backup Rules 6) Make filesystems smaller than the dump device Avoid using multiple tapes, although your system may be able to handle it. This needs the change of the tapes during the backup and creates problems in labeling. 7) Keep tapes off-site and keep them secure You may not want to keep the backup tapes and the system CDs in the same location as the machine. If you decide to do so, keep them in a safe place that is not accessible easily. Depending on your site, you may want to keep your backups in a security deposit box in a bank. Note that the backup tapes contain all the critical information about your system as well as the users. You have to make sure these tapes are secure. Actually backup tapes can easily result in violation of system security!
Backup Rules 6) Make filesystems smaller than the dump device Avoid using multiple tapes, although your system may be able to handle it. This needs the change of the tapes during the backup and creates problems in labeling. 7) Keep tapes off-site and keep them secure You may not want to keep the backup tapes and the system CDs in the same location as the machine. If you decide to do so, keep them in a safe place that is not accessible easily. Depending on your site, you may want to keep your backups in a security deposit box in a bank. Note that the backup tapes contain all the critical information about your system as well as the users. You have to make sure these tapes are secure. Actually backup tapes can easily result in violation of system security!
 Backup Rules 8) Limit the activities during the backup Changes in the files scheduled for backup during the backup process may result in mistakes by the dump process. You have two ways to fix this; Do the backup when filesystems are not in use Limit the access to file system to dump only for the duration of the backup. 9) Check your backup after you finished Test the backup tape by reading parts of it. If the tape is bad you will find the problem before a serious problem happens. That is when you need the backup and you will find out that there is something wrong. Run restore t to generate a table of contents for each filesystem and to store the result on disk.
Backup Rules 8) Limit the activities during the backup Changes in the files scheduled for backup during the backup process may result in mistakes by the dump process. You have two ways to fix this; Do the backup when filesystems are not in use Limit the access to file system to dump only for the duration of the backup. 9) Check your backup after you finished Test the backup tape by reading parts of it. If the tape is bad you will find the problem before a serious problem happens. That is when you need the backup and you will find out that there is something wrong. Run restore t to generate a table of contents for each filesystem and to store the result on disk.
 Backup Rules 10) Develop a tape life cycle You may want to recycle (reuse) the old tapes after a period of time. There are two things to remember when you recycle; The tape is no longer contains critical filesystems. Thus, you have the newer version of the filesystems on newer tapes. The tape itself is still useable. Note that all manufacturers will give the effective life span of the tape. 11) Design the data for backups Disk storages are becoming bigger and more reliable. That may result is taking the backup less serious. You may want to determine: various type of data your site is using expected validity of each type of data the backup frequency that best suit your site the political boundaries that the data will travel You may want to separate the research data from others by putting them on a separate system. 12) Be ready for the worst
Backup Rules 10) Develop a tape life cycle You may want to recycle (reuse) the old tapes after a period of time. There are two things to remember when you recycle; The tape is no longer contains critical filesystems. Thus, you have the newer version of the filesystems on newer tapes. The tape itself is still useable. Note that all manufacturers will give the effective life span of the tape. 11) Design the data for backups Disk storages are becoming bigger and more reliable. That may result is taking the backup less serious. You may want to determine: various type of data your site is using expected validity of each type of data the backup frequency that best suit your site the political boundaries that the data will travel You may want to separate the research data from others by putting them on a separate system. 12) Be ready for the worst
 The Hazard to Backup Media and Devices Most backup media use magnetic properties to store the data, thus these media are subject to damage by electrical and magnetic fields: • Speakers create large electromagnetic fields. • Transformers and power supplies • Hard disks and tape drives (the motors) • Monitors (transformers and the high voltage coils) • Prolonged exposure to the Earth’s background radiation
The Hazard to Backup Media and Devices Most backup media use magnetic properties to store the data, thus these media are subject to damage by electrical and magnetic fields: • Speakers create large electromagnetic fields. • Transformers and power supplies • Hard disks and tape drives (the motors) • Monitors (transformers and the high voltage coils) • Prolonged exposure to the Earth’s background radiation
 Backup Devices and media Floppy Disk – 720 kb, 1. 4 MB, 2. 8 MB, … Super Floppies – Iomega zips CD-R and CD-RW Removable Hard disks 8 mm cartridge tapes (most common) DAT (4 mm) cartridge tapes Travan Tapes On. Stream ADR DLT AIT Mammoth Jukeboxes, stackers, and tape libraries Hard disks
Backup Devices and media Floppy Disk – 720 kb, 1. 4 MB, 2. 8 MB, … Super Floppies – Iomega zips CD-R and CD-RW Removable Hard disks 8 mm cartridge tapes (most common) DAT (4 mm) cartridge tapes Travan Tapes On. Stream ADR DLT AIT Mammoth Jukeboxes, stackers, and tape libraries Hard disks

 Just in case you decide to use samba to do your backup on a PC !! 1. Problem Description a) A setuid root installed smbmnt could lead to a security breach due to a race condition. b) The Net. BIOS name server nmbd is vulnerable to a denial-of-service attack. c) The message service of the SMB-/CIFS-server has got a buffer overflow. 2. Impact a) Users could mount arbitrary points in the filesystem, if smbmnt is setuid root. (smbmnt isn't installed setuid by default) b) If the Do. S attack was triggered, the nmbd daemon uses up CPU resources. c) The buffer overflow is only exploitable, if the "message command" option is set in the smb. conf file. (these option isn't set by default) 3. Solution Install the updated package, which is available from our ftp server sine some weeks.
Just in case you decide to use samba to do your backup on a PC !! 1. Problem Description a) A setuid root installed smbmnt could lead to a security breach due to a race condition. b) The Net. BIOS name server nmbd is vulnerable to a denial-of-service attack. c) The message service of the SMB-/CIFS-server has got a buffer overflow. 2. Impact a) Users could mount arbitrary points in the filesystem, if smbmnt is setuid root. (smbmnt isn't installed setuid by default) b) If the Do. S attack was triggered, the nmbd daemon uses up CPU resources. c) The buffer overflow is only exploitable, if the "message command" option is set in the smb. conf file. (these option isn't set by default) 3. Solution Install the updated package, which is available from our ftp server sine some weeks.


