67480a11017831c004c5510a65e0efd9.ppt
- Количество слайдов: 17
 Service Layer Session Management Group Name: WG 2 -ARC Source: IDCC, LGE, ZTE Meeting Date: TP 16 Agenda Item:
Service Layer Session Management Group Name: WG 2 -ARC Source: IDCC, LGE, ZTE Meeting Date: TP 16 Agenda Item:
 Outline • Definition of M 2 M Service Layer Session • M 2 M Service Layer Session Requirements • M 2 M Service Layer Session Use Case Examples • M 2 M Service Layer Session Value-Add • Previous work at ARC on Service Layer Session
Outline • Definition of M 2 M Service Layer Session • M 2 M Service Layer Session Requirements • M 2 M Service Layer Session Use Case Examples • M 2 M Service Layer Session Value-Add • Previous work at ARC on Service Layer Session
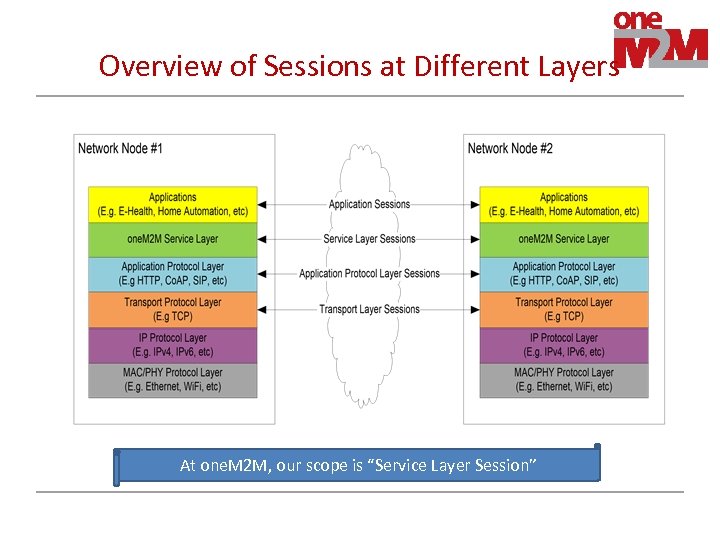 Overview of Sessions at Different Layers At one. M 2 M, our scope is “Service Layer Session”
Overview of Sessions at Different Layers At one. M 2 M, our scope is “Service Layer Session”
 Definition of M 2 M Session TS 0011 (TS 0011 Common Terminology V 1. 2. 1) • M 2 M session: service layer communication relationship between endpoints managed via M 2 M Common Services consisting of session authentication, connection establishment/termination, transmission of information and establishment/termination of Underlying Network services
Definition of M 2 M Session TS 0011 (TS 0011 Common Terminology V 1. 2. 1) • M 2 M session: service layer communication relationship between endpoints managed via M 2 M Common Services consisting of session authentication, connection establishment/termination, transmission of information and establishment/termination of Underlying Network services
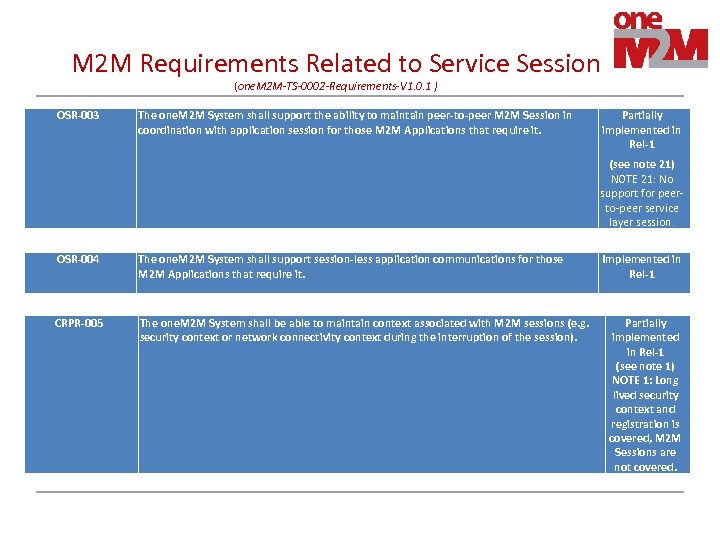 M 2 M Requirements Related to Service Session (one. M 2 M-TS-0002 -Requirements-V 1. 0. 1 ) OSR-003 The one. M 2 M System shall support the ability to maintain peer-to-peer M 2 M Session in coordination with application session for those M 2 M Applications that require it. Partially implemented in Rel-1 (see note 21) NOTE 21: No support for peerto-peer service layer session. OSR-004 The one. M 2 M System shall support session-less application communications for those M 2 M Applications that require it. CRPR-005 The one. M 2 M System shall be able to maintain context associated with M 2 M sessions (e. g. security context or network connectivity context during the interruption of the session). Implemented in Rel-1 Partially implemented in Rel-1 (see note 1) NOTE 1: Long lived security context and registration is covered, M 2 M Sessions are not covered.
M 2 M Requirements Related to Service Session (one. M 2 M-TS-0002 -Requirements-V 1. 0. 1 ) OSR-003 The one. M 2 M System shall support the ability to maintain peer-to-peer M 2 M Session in coordination with application session for those M 2 M Applications that require it. Partially implemented in Rel-1 (see note 21) NOTE 21: No support for peerto-peer service layer session. OSR-004 The one. M 2 M System shall support session-less application communications for those M 2 M Applications that require it. CRPR-005 The one. M 2 M System shall be able to maintain context associated with M 2 M sessions (e. g. security context or network connectivity context during the interruption of the session). Implemented in Rel-1 Partially implemented in Rel-1 (see note 1) NOTE 1: Long lived security context and registration is covered, M 2 M Sessions are not covered.
 Current Status • What are supported today – Single hop “session” associated with registration • What are not supported today – End-to-end service layer session
Current Status • What are supported today – Single hop “session” associated with registration • What are not supported today – End-to-end service layer session
 Use Cases Requiring Sessions • Not all M 2 M use cases require end-to-end sessions, many use cases do, for example: – use cases requiring end-to-end security and privacy such as e. Health, banking and military – use cases requiring end-to-end quality of service such as video surveillance, patient monitoring, and emergency services
Use Cases Requiring Sessions • Not all M 2 M use cases require end-to-end sessions, many use cases do, for example: – use cases requiring end-to-end security and privacy such as e. Health, banking and military – use cases requiring end-to-end quality of service such as video surveillance, patient monitoring, and emergency services
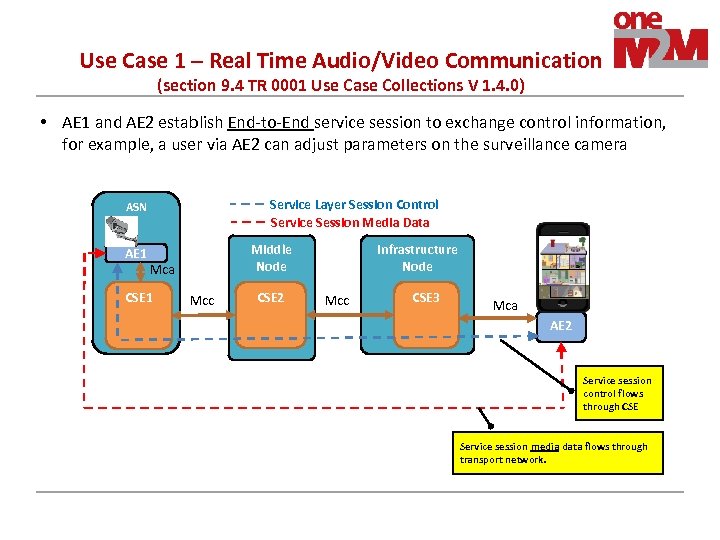 Use Case 1 – Real Time Audio/Video Communication (section 9. 4 TR 0001 Use Case Collections V 1. 4. 0) • AE 1 and AE 2 establish End-to-End service session to exchange control information, for example, a user via AE 2 can adjust parameters on the surveillance camera Service Layer Session Control Service Session Media Data ASN AE 1 Middle Node Mca CSE 1 Mcc CSE 2 Infrastructure Node Mcc CSE 3 Mca AE 2 Service session control flows through CSE Service session media data flows through transport network.
Use Case 1 – Real Time Audio/Video Communication (section 9. 4 TR 0001 Use Case Collections V 1. 4. 0) • AE 1 and AE 2 establish End-to-End service session to exchange control information, for example, a user via AE 2 can adjust parameters on the surveillance camera Service Layer Session Control Service Session Media Data ASN AE 1 Middle Node Mca CSE 1 Mcc CSE 2 Infrastructure Node Mcc CSE 3 Mca AE 2 Service session control flows through CSE Service session media data flows through transport network.
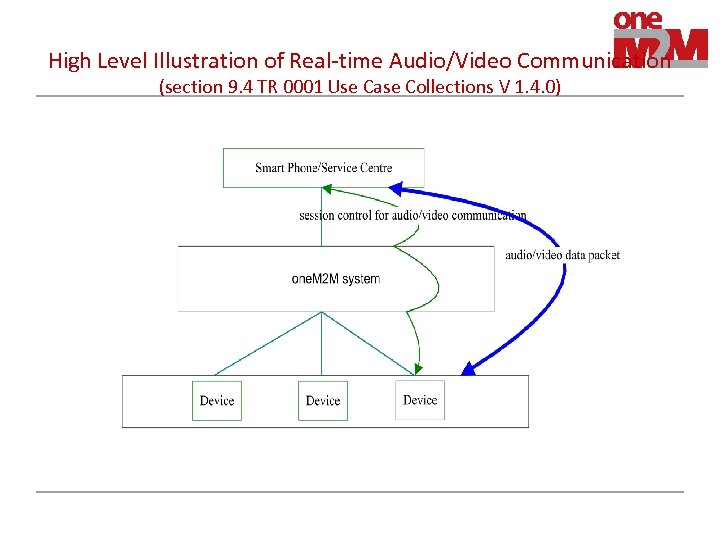 High Level Illustration of Real-time Audio/Video Communication (section 9. 4 TR 0001 Use Case Collections V 1. 4. 0)
High Level Illustration of Real-time Audio/Video Communication (section 9. 4 TR 0001 Use Case Collections V 1. 4. 0)
 Potential Requirements (section 9. 4 TR 0001 Use Case Collections V 1. 4. 0) • The one. M 2 M system shall provide a capability to allocate unique identifiers to devices for identification and session routing in one. M 2 M system. • The one. M 2 M system shall support to establish and terminate real-time audio/video session between M 2 M applications. • The one. M 2 M system shall provide a capability for a device to be registered in the system. • The one. M 2 M system shall support authorization if a request to and from the device for real-time audio/video call establishment is allowed. • The one. M 2 M system shall provide a capability for routing a request for real-time audio/video call establishment from or to the device. • The one. M 2 M system shall provide a capability for media control (e. g. negotiation of transcoding, Qo. S) between the M 2 M applications for real-time audio/video data packet transmission.
Potential Requirements (section 9. 4 TR 0001 Use Case Collections V 1. 4. 0) • The one. M 2 M system shall provide a capability to allocate unique identifiers to devices for identification and session routing in one. M 2 M system. • The one. M 2 M system shall support to establish and terminate real-time audio/video session between M 2 M applications. • The one. M 2 M system shall provide a capability for a device to be registered in the system. • The one. M 2 M system shall support authorization if a request to and from the device for real-time audio/video call establishment is allowed. • The one. M 2 M system shall provide a capability for routing a request for real-time audio/video call establishment from or to the device. • The one. M 2 M system shall provide a capability for media control (e. g. negotiation of transcoding, Qo. S) between the M 2 M applications for real-time audio/video data packet transmission.
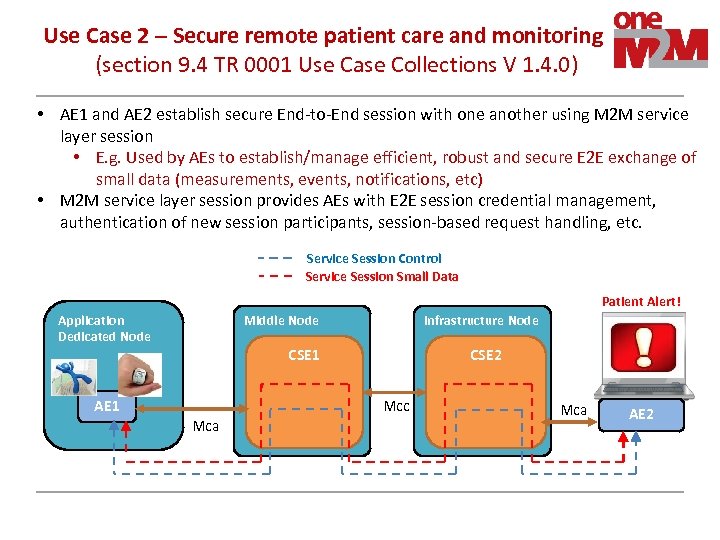 Use Case 2 – Secure remote patient care and monitoring (section 9. 4 TR 0001 Use Case Collections V 1. 4. 0) • AE 1 and AE 2 establish secure End-to-End session with one another using M 2 M service layer session • E. g. Used by AEs to establish/manage efficient, robust and secure E 2 E exchange of small data (measurements, events, notifications, etc) • M 2 M service layer session provides AEs with E 2 E session credential management, authentication of new session participants, session-based request handling, etc. Service Session Control Service Session Small Data Patient Alert! Application Dedicated Node Middle Node Infrastructure Node CSE 1 AE 1 Mca CSE 2 Mcc Mca AE 2
Use Case 2 – Secure remote patient care and monitoring (section 9. 4 TR 0001 Use Case Collections V 1. 4. 0) • AE 1 and AE 2 establish secure End-to-End session with one another using M 2 M service layer session • E. g. Used by AEs to establish/manage efficient, robust and secure E 2 E exchange of small data (measurements, events, notifications, etc) • M 2 M service layer session provides AEs with E 2 E session credential management, authentication of new session participants, session-based request handling, etc. Service Session Control Service Session Small Data Patient Alert! Application Dedicated Node Middle Node Infrastructure Node CSE 1 AE 1 Mca CSE 2 Mcc Mca AE 2
 Potential Requirements (section 7. 3 TR 0001 Use Case Collections V 1. 4. 0) • The M 2 M system shall support M 2 M applications with establishing a security context for protecting the privacy of application data from the underlying M 2 M service. • The M 2 M system must support mechanisms for binding identities used at service layer and/or application layer to the tamper proof identities that are available within the device secured Environment. • The M 2 M service layer must be able to accommodate delay requirements for the application based on the tagging applied to the application data. For instance, data that is marked critical must create notifications for first-level responders. • … … (didn’t include specific security requirements)
Potential Requirements (section 7. 3 TR 0001 Use Case Collections V 1. 4. 0) • The M 2 M system shall support M 2 M applications with establishing a security context for protecting the privacy of application data from the underlying M 2 M service. • The M 2 M system must support mechanisms for binding identities used at service layer and/or application layer to the tamper proof identities that are available within the device secured Environment. • The M 2 M service layer must be able to accommodate delay requirements for the application based on the tagging applied to the application data. For instance, data that is marked critical must create notifications for first-level responders. • … … (didn’t include specific security requirements)
 M 2 M Service Session Benefits • M 2 M service layer session enables end-to-end security • M 2 M service layer session enables CSE with method of organizing M 2 M AE traffic into flows • M 2 M service layer is well positioned to provide underlying networks with value-add information about AE flows • E. g. Required Qo. S, traffic pattern/schedule, device state, priority • Underlying networks can use this information to better optimize AE traffic flows through their network • E. g. Info from CSE can be used by underlying network to more efficiently configure network policies
M 2 M Service Session Benefits • M 2 M service layer session enables end-to-end security • M 2 M service layer session enables CSE with method of organizing M 2 M AE traffic into flows • M 2 M service layer is well positioned to provide underlying networks with value-add information about AE flows • E. g. Required Qo. S, traffic pattern/schedule, device state, priority • Underlying networks can use this information to better optimize AE traffic flows through their network • E. g. Info from CSE can be used by underlying network to more efficiently configure network policies
 M 2 M Service Session Benefits • M 2 M service layer is well-positioned to offload M 2 M AEs of some of the burden of E 2 E ‘over-the-top’ application-based sessions. • Today, many AEs are establishing end-to-end (E 2 E) sessions in an ‘overthe-top’ manner using application-based sessions. • E. g. To support secure and reliable exchange of small data (e. g. events, notifications, commands) • Much of the burden of establishing and managing these ‘over-the-top’ application sessions rests completely on AEs and humans • E. g. AEs must handle session management messaging themselves • E. g. Humans must enter end-to-end session login and password • For M 2 M, many devices will be un-manned and resource constrained. E 2 E application-based session establishment will need to be lighter weight and more automated
M 2 M Service Session Benefits • M 2 M service layer is well-positioned to offload M 2 M AEs of some of the burden of E 2 E ‘over-the-top’ application-based sessions. • Today, many AEs are establishing end-to-end (E 2 E) sessions in an ‘overthe-top’ manner using application-based sessions. • E. g. To support secure and reliable exchange of small data (e. g. events, notifications, commands) • Much of the burden of establishing and managing these ‘over-the-top’ application sessions rests completely on AEs and humans • E. g. AEs must handle session management messaging themselves • E. g. Humans must enter end-to-end session login and password • For M 2 M, many devices will be un-manned and resource constrained. E 2 E application-based session establishment will need to be lighter weight and more automated
 Previous Discussions and Texts on Service Layer Session (Annex I TS 0001 V 1. 2. 0) • An M 2 M service session is an end-to-end Service Layer connection managed by the Service Session Management (SSM) CSF. The SSM CSF manages M 2 M service sessions between AEs, between an AE and a CSE, or between CSEs. • The management of a M 2 M service session includes capabilities such as the management of session state, session authentication and establishment, management of Underlying Network connections and services related to the session, coordination of sessions spanning multiple hops of CSEs, exchange of information between session endpoints, and session termination.
Previous Discussions and Texts on Service Layer Session (Annex I TS 0001 V 1. 2. 0) • An M 2 M service session is an end-to-end Service Layer connection managed by the Service Session Management (SSM) CSF. The SSM CSF manages M 2 M service sessions between AEs, between an AE and a CSE, or between CSEs. • The management of a M 2 M service session includes capabilities such as the management of session state, session authentication and establishment, management of Underlying Network connections and services related to the session, coordination of sessions spanning multiple hops of CSEs, exchange of information between session endpoints, and session termination.
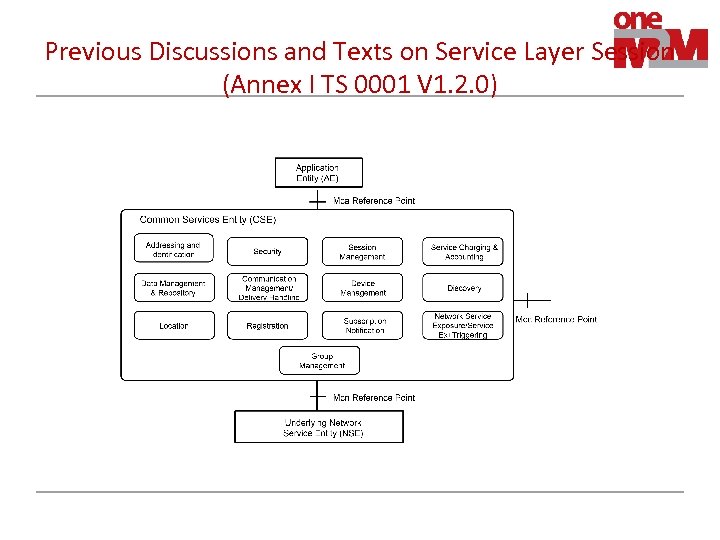 Previous Discussions and Texts on Service Layer Session (Annex I TS 0001 V 1. 2. 0)
Previous Discussions and Texts on Service Layer Session (Annex I TS 0001 V 1. 2. 0)
 Asking Input from ARC • Agree on the need to support service layer session and related parameters and management procedures • Work out solutions
Asking Input from ARC • Agree on the need to support service layer session and related parameters and management procedures • Work out solutions


