30ce71c60d9bae4b7fddd76f08e5f625.ppt
- Количество слайдов: 33

Server Hardening by Shad Rich ISQS 6342 Spring 2004

Prerequisites Implement and enforce internal security policy n Determine risk n Place server in an appropriate physical location n
Server OS This presentation will concentrate on Linux servers. n There are several documents available at www. microsoft. com describing hardening of Windows XP and 2003. n

OS Hardening Basics Install bare necessities n Keep all system software up-to-date n Delete/disable unnecessary user accounts n Do not grant shell access unless needed n Run public services in chrooted file systems n Remove SUID bits n

OS Hardening Basics cont… Configure logging and review the logs regularly n Every host should be its own firewall n Check systems with security scanners n Document configurations for later use n

Before Installation Set BIOS password n Plan partitioning scheme n n place /var, /opt, /usr/local on separate partitions
OS Installation If possible, do not connect to the internet to install. n Do a very basic install. n Do not install the X Window System or any desktop managers unless absolutely necessary. n Install the latest versions if possible…if not, upgrade. n

Post Install n Set a boot loader password n /etc/lilo. conf image=/boot/2. 2. 14 -vmlinuz # Kernel location label=Linux # Arbritrary kernel label read-only password=hackme restricted # Sets password n /boot/grub/menu. lst timeout 3 password hackme # Sets password
Post Install cont… n Remove root prompt on the kernel n /etc/mkinitrd. conf # DELAY The number of seconds the linuxrc script should wait # to allow the user to interrupt it before the system is brought # up DELAY=0 n Regenerate your ramdisk image cd /boot mkinitrd -o initrd. img-2. 4. 18 -k 7 /lib/modules/2. 4. 18 -k 7

Kernel Download the latest kernel source from www. kernel. org or another mirror n Many distributions make the kernel source available through their package managers, e. g. rpm, apt-get, emerge n

Extract Kernel Source Move the kernel source to an appropriate directory, e. g. /usr/src n Extract the kernel source: n n For tar. gz files: tar –zxvf kernel-source-file. tar. gz n For bz 2 files tar –jxvf kernel-source-file. bz 2

Configure Kernel Source cd /usr/src/kernel-source-dir/ n make config, make menuconfig n Select only the most basic options needed to run the server. n Do not enable sound, usb, serial, or parallel port drivers if not needed for server functionality n
Compile Kernel and Modules n Generic: n n n su make dep make clean make bz. Image modules_install make bzlilo (if using lilo boot loader) Debian: n n n su make-kpkg clean make-kpkg –append-to-version=. <date> kernel_image modules_image dpkg –i. . /kernel-image. date. deb Edit /etc/lilo. conf or /boot/grub/menu. lst to boot new kernel

Common Unneeded Services rpc services – nfsd, nfsclient n r-services – rsh, rlogin, rcp n inetd n linuxconfd n sendmail n telnet, FTP, POP n

Identify Unneeded Services n What’s running? n n What ports are open? n n nmap localhost What is started on boot? n n ps aux | less ls –la /etc/rc#. d/ (anything starting with “S”) What is inetd running? n n chkconfig –list (Red. Hat) netstat -pn -l -A inet /usr/sbin/lsof -i | grep LISTEN grep -v "^#" /etc/inetd. conf | sort -u

Remove Unneeded Services chkconfig –level 2 linuxconf off n rm /etc/rc#. d/S 20 ssh n comment out services in /etc/inetd. conf on Debian systems n
Automated Hardening n Bastille Linux n n n original was going to be a secure distribution instead became a set of scripts for hardening existing distributions packages for multiple platforms n n Red. Hat/Mandrake Debian Mac OS X HP-UX
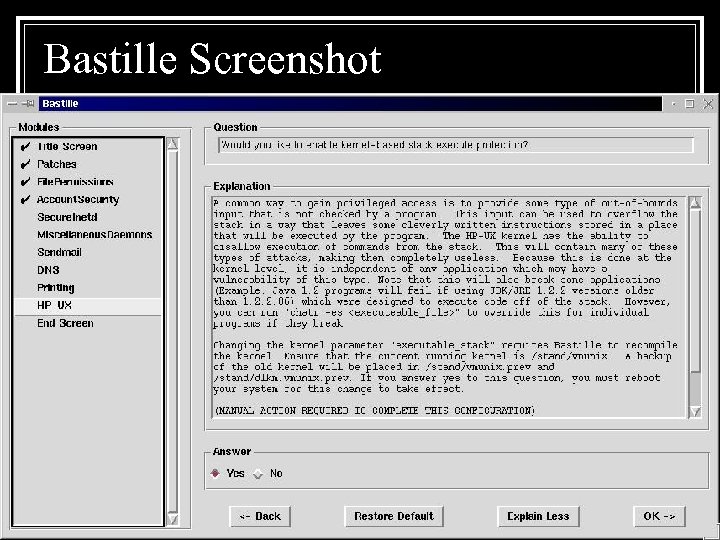
Bastille Screenshot

Keeping Software Updated Subscribe to distribution-specific security lists n Automated updates n n n Red Hat – up 2 date Debian – apt-get update; apt-get upgrade
Delete Unnecessary User Accounts Directly read /etc/passwd to identify unnecessary accounts n Use find to locate user files n find / -username –print

Minimize Use of SUID=root n Use find to locate violating files find / -perm +4000 –user root –type f –print find / -perm +2000 –group root –type f –print n Change permissions on the violating files chmod u-s /full/path/to/filename chmod g-s /full/path/to/filename

Run Services In chrooted File System chrooted file systems prevent hijacked daemons from accessing the entire file system. n Move service’s file structure to an isolated directory. n Change ownership from root to an arbitrary owner and group (Ex. named) n Change file permissions. n

Normal File Structure n Example of a normal BIND install: / /etc /usr/bin /var/run /var/named
chrooted File Structure n n n n /chroot/named/dev /chroot/named/etc/namedb/slave /chroot/named/var/run

Individual Host Firewalls Use ipchains on 2. 2 and earlier kernels n Use iptables on 2. 4 and later kernels n n Kernel options to be selected: n n n Connection Tracking FTP Protocol Support IP Tables Support IRC Protocol Support Any other desired modules
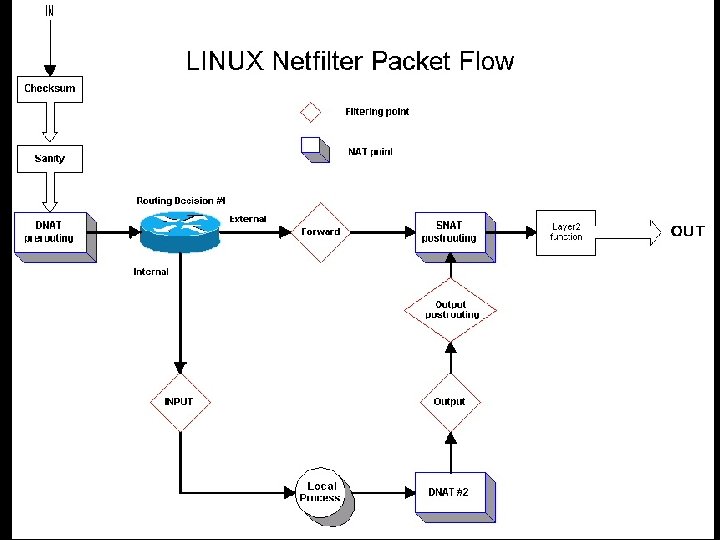
Using iptables n n n Create a new chain (-N). Delete an empty chain (-X). Change the policy for a built-in chain (-P). List the rules in a chain (-L). Flush the rules out of a chain (-F). Zero the packet and byte counters on all rules in a chain (-Z).
Manipulate Rules Inside Chains n n Append a new rule to a chain (-A). Insert a new rule at some position in a chain (-I). Replace a rule at some position in a chain (-R). Delete a rule at some position in a chain, or the first that matches (-D).
Example Firewall Script n http: //www. faqs. org/docs/iptables/examplec ode. html

System Loggers klogd – does kernel logging n syslogd – does system logging n n /etc/syslog. conf n n facility. selector /var/logfile syslog-ng – “syslog new generation” n n more advanced than syslogd /etc/syslog-ng. conf

Log Maintenance/Monitoring logrotate – automatically rotates specified log files n swatch – configured to alert system admin through e-mail or echo with system bell n

Security Scanning n To be done later in the semester…

References Bauer, Michael D. (2003). Building Secure Servers with Linux. Sebastobol: O’Reilly & Associates, Inc. n Fenzi, Kevin (2001). Linux Security HOWTO. Linux Documentation Project. n Burgess, Hal (2002). Security Quick-Start HOWTO for Linux Documentation Project. n
30ce71c60d9bae4b7fddd76f08e5f625.ppt