875fef0a6142b00fe2cceb5a81576350.ppt
- Количество слайдов: 108
 Semester 1 Module 2 Networking Fundamentals Andres, Wen-Yuan Liao Department of Computer Science and Engineering De Lin Institute of Technology andres@dlit. edu. tw http: //www. cse. dlit. edu. tw/~andres
Semester 1 Module 2 Networking Fundamentals Andres, Wen-Yuan Liao Department of Computer Science and Engineering De Lin Institute of Technology andres@dlit. edu. tw http: //www. cse. dlit. edu. tw/~andres
 Overview l l l l l Explain the importance of bandwidth in networking. Use an analogy to explain bandwidth. Identify bps, kbps, Mbps, and Gbps as units of bandwidth. Explain the difference between bandwidth and throughput. Calculate data transfer rates. Explain why layered models are used to describe data communication. Explain the development of the OSI model. List the advantages of a layered approach. Identify each of the seven layers of the OSI model.
Overview l l l l l Explain the importance of bandwidth in networking. Use an analogy to explain bandwidth. Identify bps, kbps, Mbps, and Gbps as units of bandwidth. Explain the difference between bandwidth and throughput. Calculate data transfer rates. Explain why layered models are used to describe data communication. Explain the development of the OSI model. List the advantages of a layered approach. Identify each of the seven layers of the OSI model.
 l l l l Identify the four layers of the TCP/IP model. Describe the similarities and differences between the two models. Briefly outline the history of networking. Identify devices used in networking. Understand the role of protocols in networking. Define LAN, WAN, MAN, and SAN. Explain VPNs and their advantages. Describe the differences between intranets and extranets.
l l l l Identify the four layers of the TCP/IP model. Describe the similarities and differences between the two models. Briefly outline the history of networking. Identify devices used in networking. Understand the role of protocols in networking. Define LAN, WAN, MAN, and SAN. Explain VPNs and their advantages. Describe the differences between intranets and extranets.
 Outline l l l Networking Terminology Bandwidth Networking Models
Outline l l l Networking Terminology Bandwidth Networking Models
 Data networks l l l There was no efficient way of sharing data among multiple microcomputers Floppy disks. Sneakernet created multiple copies of the data. If two people modified the file and then tried to share it, what will happen? Businesses needed a solution to address the following problems: l l l How to avoid duplication of equipment and resources? How to communicate efficiently? How to set up and manage a network?
Data networks l l l There was no efficient way of sharing data among multiple microcomputers Floppy disks. Sneakernet created multiple copies of the data. If two people modified the file and then tried to share it, what will happen? Businesses needed a solution to address the following problems: l l l How to avoid duplication of equipment and resources? How to communicate efficiently? How to set up and manage a network?
 l l l Networking technology could increase productivity while saving money. In the mid-1980 s, each company that created network hardware and software used its own company standards. Network technologies were incompatible with each other. Difficult to communicate with each other. This often required the old network equipment to be removed to implement the new equipment.
l l l Networking technology could increase productivity while saving money. In the mid-1980 s, each company that created network hardware and software used its own company standards. Network technologies were incompatible with each other. Difficult to communicate with each other. This often required the old network equipment to be removed to implement the new equipment.
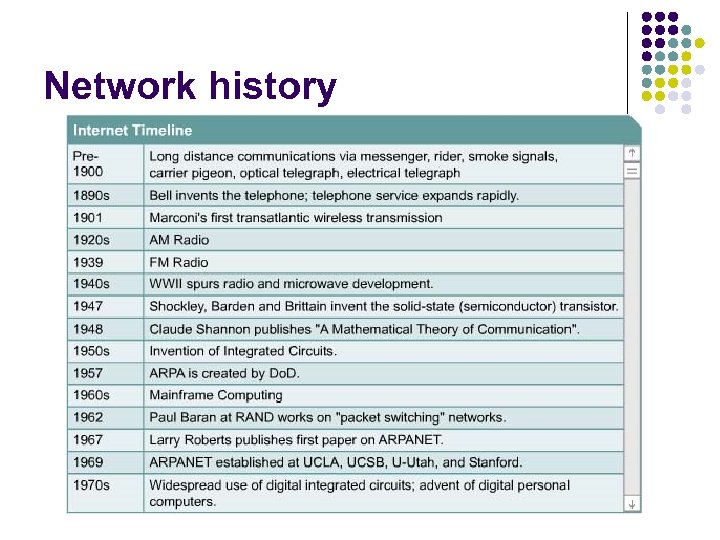
 l l l LAN standards provided an open set of guidelines for creating network hardware and software, the equipment from different companies could then become compatible. In a LAN system, each department of the company is a kind of electronic island. WANs could connect user networks over large geographic areas.
l l l LAN standards provided an open set of guidelines for creating network hardware and software, the equipment from different companies could then become compatible. In a LAN system, each department of the company is a kind of electronic island. WANs could connect user networks over large geographic areas.
 Network history
Network history


 Networking devices l Equipment that connects directly to a network segment is referred to as a device. l l End-user devices : They include computers, printers, scanners, and other devices that provide services directly to the user. Network devices : They include all the devices that connect the end-user devices together to allow them to communicate.
Networking devices l Equipment that connects directly to a network segment is referred to as a device. l l End-user devices : They include computers, printers, scanners, and other devices that provide services directly to the user. Network devices : They include all the devices that connect the end-user devices together to allow them to communicate.
 l End-user devices l l l End-user devices that provide users with a connection to the network are also referred to as hosts. The host devices can exist without a network, but without the network the host capabilities are greatly reduced. A NIC is a printed circuit board that fits into the expansion slot of a bus on a computer motherboard, or it can be a peripheral device. Each NIC is identified by a unique code called a Media Access Control (MAC) address. This address is used to control data communication for the host on the network.
l End-user devices l l l End-user devices that provide users with a connection to the network are also referred to as hosts. The host devices can exist without a network, but without the network the host capabilities are greatly reduced. A NIC is a printed circuit board that fits into the expansion slot of a bus on a computer motherboard, or it can be a peripheral device. Each NIC is identified by a unique code called a Media Access Control (MAC) address. This address is used to control data communication for the host on the network.



 l Networking devices : l Repeater : l l Repeaters regenerate analog or digital signals distorted by transmission loss due to attenuation. The purpose of a network repeater is to regenerate and retime network signals at the bit level. This allows them to travel a longer distance on the media. A repeater does not perform intelligent routing like a bridge or router.
l Networking devices : l Repeater : l l Repeaters regenerate analog or digital signals distorted by transmission loss due to attenuation. The purpose of a network repeater is to regenerate and retime network signals at the bit level. This allows them to travel a longer distance on the media. A repeater does not perform intelligent routing like a bridge or router.
 l Hubs : l l l They concentrate connections. In other words, they take a group of hosts and allow the network to see them as a single unit. This is done passively, without any other effect on the data transmission. Active hubs not only concentrate hosts, but they also regenerate signals. Multi-ported Repeater.
l Hubs : l l l They concentrate connections. In other words, they take a group of hosts and allow the network to see them as a single unit. This is done passively, without any other effect on the data transmission. Active hubs not only concentrate hosts, but they also regenerate signals. Multi-ported Repeater.
 l Bridges : l l l They provide connections between LANs. Not only do bridges connect LANs, but they also perform a check on the data to determine whether it should cross the bridge or not. This makes each part of the network more efficient.
l Bridges : l l l They provide connections between LANs. Not only do bridges connect LANs, but they also perform a check on the data to determine whether it should cross the bridge or not. This makes each part of the network more efficient.
 l Workgroup switches : l l l They add more intelligence to data transfer management. Not only can they determine whether data should remain on a LAN or not, but they can transfer the data only to the connection that needs that data. Multi-ported Bridge.
l Workgroup switches : l l l They add more intelligence to data transfer management. Not only can they determine whether data should remain on a LAN or not, but they can transfer the data only to the connection that needs that data. Multi-ported Bridge.
 l Routers : l l They have all the capabilities listed above. Routers can regenerate signals, concentrate multiple connections, convert data transmission formats, and manage data transfers. They can also connect to a WAN, which allows them to connect LANs that are separated by great distances. None of the other devices can provide this type of connection.
l Routers : l l They have all the capabilities listed above. Routers can regenerate signals, concentrate multiple connections, convert data transmission formats, and manage data transfers. They can also connect to a WAN, which allows them to connect LANs that are separated by great distances. None of the other devices can provide this type of connection.

 Network topology l Network topology defines the structure of the network. l l Physical topology, which is the actual layout of the wire or media. Logical topology, which defines how the media is accessed by the hosts for sending data.
Network topology l Network topology defines the structure of the network. l l Physical topology, which is the actual layout of the wire or media. Logical topology, which defines how the media is accessed by the hosts for sending data.
 l Physical topologies : l Bus topology l l l It uses a single backbone cable that is terminated at both ends. All the hosts connect directly to this backbone. Ring topology l l It connects one host to the next and the last host to the first. This creates a physical ring of cable.
l Physical topologies : l Bus topology l l l It uses a single backbone cable that is terminated at both ends. All the hosts connect directly to this backbone. Ring topology l l It connects one host to the next and the last host to the first. This creates a physical ring of cable.
 l Star topology l l It connects all cables to a central point of concentration. Extended star topology l l It links individual stars together by connecting the hubs and/or switches. This topology can extend the scope and coverage of the network.
l Star topology l l It connects all cables to a central point of concentration. Extended star topology l l It links individual stars together by connecting the hubs and/or switches. This topology can extend the scope and coverage of the network.
 l Hierarchical topology l l l It is similar to an extended star. Instead of linking the hubs and/or switches together, the system is linked to a computer that controls the traffic on the topology. Tree topology.
l Hierarchical topology l l l It is similar to an extended star. Instead of linking the hubs and/or switches together, the system is linked to a computer that controls the traffic on the topology. Tree topology.
 l Mesh topology l l l Each host has its own connections to all other hosts. It provides much protection as possible from interruption of service. Although the Internet has multiple paths to any one location, it does not adopt the full mesh topology.
l Mesh topology l l l Each host has its own connections to all other hosts. It provides much protection as possible from interruption of service. Although the Internet has multiple paths to any one location, it does not adopt the full mesh topology.

 l l The logical topology of a network is how the hosts communicate across the medium. The two most common types of logical topologies are : l l broadcast token passing
l l The logical topology of a network is how the hosts communicate across the medium. The two most common types of logical topologies are : l l broadcast token passing
 l Broadcast topology l l It simply means that each host sends its data to all other hosts on the network medium. There is no order that the stations must follow to use the network. It is first come, first serve. Ethernet works this way.
l Broadcast topology l l It simply means that each host sends its data to all other hosts on the network medium. There is no order that the stations must follow to use the network. It is first come, first serve. Ethernet works this way.
 l Token passing l l l Token passing controls network access by passing an electronic token sequentially to each host. When a host receives the token, that host can send data on the network. If the host has no data to send, it passes the token to the next host and the process repeats itself. Two examples of networks that use token passing are : l Token Ring l Fiber Distributed Data Interface (FDDI)
l Token passing l l l Token passing controls network access by passing an electronic token sequentially to each host. When a host receives the token, that host can send data on the network. If the host has no data to send, it passes the token to the next host and the process repeats itself. Two examples of networks that use token passing are : l Token Ring l Fiber Distributed Data Interface (FDDI)

 Network protocols l l Protocol suites are collections of protocols that enable network communication from one host through the network to another host. A protocol is a formal description of a set of rules and conventions that govern a particular aspect of how devices on a network communicate. Protocols determine the format, timing, sequencing, and error control in data communication. Without protocols, the computer cannot make or rebuild the stream of incoming bits from another computer into the original format.
Network protocols l l Protocol suites are collections of protocols that enable network communication from one host through the network to another host. A protocol is a formal description of a set of rules and conventions that govern a particular aspect of how devices on a network communicate. Protocols determine the format, timing, sequencing, and error control in data communication. Without protocols, the computer cannot make or rebuild the stream of incoming bits from another computer into the original format.
 l Protocols control all aspects of data communication, which include the following: l l l How the physical network is built. How computers connect to the network. How the data is formatted for transmission. How that data is sent. How to deal with errors. Standard: IEEE, ANSI, TIA, EIA, ITU, CCITT.
l Protocols control all aspects of data communication, which include the following: l l l How the physical network is built. How computers connect to the network. How the data is formatted for transmission. How that data is sent. How to deal with errors. Standard: IEEE, ANSI, TIA, EIA, ITU, CCITT.

 Local-area networks (LANs) l LANs consist of the following components: l l l Computers Network interface cards Peripheral devices Networking media Network devices Locally share files and printers efficiently.
Local-area networks (LANs) l LANs consist of the following components: l l l Computers Network interface cards Peripheral devices Networking media Network devices Locally share files and printers efficiently.
 l l l It makes internal communications possible. They tie data, local communications, and computing equipment together. Some common LAN technologies are: l l l Ethernet Token Ring FDDI
l l l It makes internal communications possible. They tie data, local communications, and computing equipment together. Some common LAN technologies are: l l l Ethernet Token Ring FDDI
 Wide-area networks (WANs) l l l WANs connect user networks over a large geographical area. It allows computers, printers, and other devices on a LAN to share and be shared with distant locations. Allow access over serial interfaces operating at lower speeds. Provide full-time or part-time connectivity to local services. Provide e-mail, World Wide Web, file transfer, and ecommerce services.
Wide-area networks (WANs) l l l WANs connect user networks over a large geographical area. It allows computers, printers, and other devices on a LAN to share and be shared with distant locations. Allow access over serial interfaces operating at lower speeds. Provide full-time or part-time connectivity to local services. Provide e-mail, World Wide Web, file transfer, and ecommerce services.
 l Some common WAN technologies are: l l l Modems Integrated Services Digital Network (ISDN) Digital Subscriber Line (DSL) Frame Relay US (T) and Europe (E) Carrier Series – T 1, E 1, T 3, E 3 Synchronous Optical Network (SONET)
l Some common WAN technologies are: l l l Modems Integrated Services Digital Network (ISDN) Digital Subscriber Line (DSL) Frame Relay US (T) and Europe (E) Carrier Series – T 1, E 1, T 3, E 3 Synchronous Optical Network (SONET)
 Metropolitan-area networks (MANs) l l l A MAN is a network that spans a metropolitan area such as a city or suburban area. A MAN usually consists of two or more LANs in a common geographic area. For example, a bank with multiple branches may utilize a MAN. Typically, a service provider is used to connect two or more LAN sites using private communication lines or optical services. A MAN can also be created using wireless bridge technology by beaming signals across public areas.
Metropolitan-area networks (MANs) l l l A MAN is a network that spans a metropolitan area such as a city or suburban area. A MAN usually consists of two or more LANs in a common geographic area. For example, a bank with multiple branches may utilize a MAN. Typically, a service provider is used to connect two or more LAN sites using private communication lines or optical services. A MAN can also be created using wireless bridge technology by beaming signals across public areas.

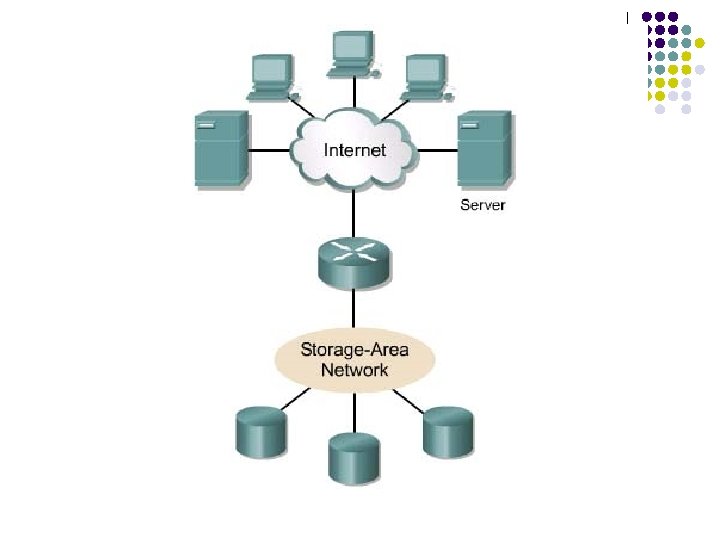
 Storage-area networks (SANs) l l l A SAN is a dedicated, high-performance network used to move data between servers and storage resources. SAN technology allows high-speed server-tostorage, storage-to-storage, or server-to-server connectivity. Separate network infrastructure.
Storage-area networks (SANs) l l l A SAN is a dedicated, high-performance network used to move data between servers and storage resources. SAN technology allows high-speed server-tostorage, storage-to-storage, or server-to-server connectivity. Separate network infrastructure.
 l SANs offer the following features: l l l Performance – SANs enable concurrent access of disk or tape arrays by two or more servers at high speeds, providing enhanced system performance. Availability – SANs have disaster tolerance built in, because data can be mirrored using a SAN up to 10 kilometers (km) or 6. 2 miles away. Scalability – Like a LAN/WAN, it can use a variety of technologies. This allows easy relocation of backup data, operations, file migration, and data replication between systems.
l SANs offer the following features: l l l Performance – SANs enable concurrent access of disk or tape arrays by two or more servers at high speeds, providing enhanced system performance. Availability – SANs have disaster tolerance built in, because data can be mirrored using a SAN up to 10 kilometers (km) or 6. 2 miles away. Scalability – Like a LAN/WAN, it can use a variety of technologies. This allows easy relocation of backup data, operations, file migration, and data replication between systems.
 Virtual private network (VPN) l l A VPN is a private network that is constructed within a public network infrastructure such as the global Internet. A secure tunnel between the telecommuter’s PC and a VPN router in the headquarters.
Virtual private network (VPN) l l A VPN is a private network that is constructed within a public network infrastructure such as the global Internet. A secure tunnel between the telecommuter’s PC and a VPN router in the headquarters.

 Benefits of VPNs l l A VPN is a service that offers secure, reliable connectivity over a shared public network infrastructure such as the Internet. The most cost-effective method of establishing a point-to-point connection between remote users and an enterprise customer's network.
Benefits of VPNs l l A VPN is a service that offers secure, reliable connectivity over a shared public network infrastructure such as the Internet. The most cost-effective method of establishing a point-to-point connection between remote users and an enterprise customer's network.
 l The following are three main types of VPNs: l Access VPNs – Access VPNs provide remote access for mobile worker and small office/home office (SOHO) to the headquarters of the Intranet or Extranet over a shared infrastructure. Access VPNs use analog, dialup, ISDN, digital subscriber line (DSL), mobile IP, and cable technologies to securely connect mobile users, telecommuters, and branch offices.
l The following are three main types of VPNs: l Access VPNs – Access VPNs provide remote access for mobile worker and small office/home office (SOHO) to the headquarters of the Intranet or Extranet over a shared infrastructure. Access VPNs use analog, dialup, ISDN, digital subscriber line (DSL), mobile IP, and cable technologies to securely connect mobile users, telecommuters, and branch offices.
 l l Intranet VPNs – Intranet VPNs link regional and remote offices to the headquarters of the internal network over a shared infrastructure using dedicated connections. Intranet VPNs differ from Extranet VPNs in that they allow access only to the employees of the enterprise. Extranet VPNs – Extranet VPNs link business partners to the headquarters of the network over a shared infrastructure using dedicated connections. Extranet VPNs differ from Intranet VPNs in that they allow access to users outside the enterprise.
l l Intranet VPNs – Intranet VPNs link regional and remote offices to the headquarters of the internal network over a shared infrastructure using dedicated connections. Intranet VPNs differ from Extranet VPNs in that they allow access only to the employees of the enterprise. Extranet VPNs – Extranet VPNs link business partners to the headquarters of the network over a shared infrastructure using dedicated connections. Extranet VPNs differ from Intranet VPNs in that they allow access to users outside the enterprise.

 Intranets and extranets l Intranet l One common configuration of a LAN is an intranet. l Intranets are designed to permit users who have access privileges to the internal LAN of the organization. l Browser technology is used as the common front end to access information on servers such as financial, graphical, or text-based data. l Extranet l l Extranets refer to applications and services that are Intranet based, and use extended, secure access to external users or enterprises. This access is usually accomplished through passwords, user IDs, and other application-level security.
Intranets and extranets l Intranet l One common configuration of a LAN is an intranet. l Intranets are designed to permit users who have access privileges to the internal LAN of the organization. l Browser technology is used as the common front end to access information on servers such as financial, graphical, or text-based data. l Extranet l l Extranets refer to applications and services that are Intranet based, and use extended, secure access to external users or enterprises. This access is usually accomplished through passwords, user IDs, and other application-level security.

 Outline l l l Networking Terminology Bandwidth Networking Models
Outline l l l Networking Terminology Bandwidth Networking Models
 Importance of bandwidth l Why bandwidth is important : l l Bandwidth is finite Bandwidth is not free Bandwidth requirements are growing at a rapid rate Bandwidth is critical to network performance
Importance of bandwidth l Why bandwidth is important : l l Bandwidth is finite Bandwidth is not free Bandwidth requirements are growing at a rapid rate Bandwidth is critical to network performance
 l Bandwidth is finite l l Bandwidth is limited by the laws of physics and by the technologies used to place information on the media. 56 kbps modems with twisted-pair phone wires. Newer technologies, DSL also use the same twisted-pair phone wires, it provides much greater bandwidth than conventional modems. Optical fiber has the physical potential to provide virtually limitless bandwidth.
l Bandwidth is finite l l Bandwidth is limited by the laws of physics and by the technologies used to place information on the media. 56 kbps modems with twisted-pair phone wires. Newer technologies, DSL also use the same twisted-pair phone wires, it provides much greater bandwidth than conventional modems. Optical fiber has the physical potential to provide virtually limitless bandwidth.
 l Bandwidth is not free l l l It is possible to buy equipment for a LAN that will provide nearly unlimited bandwidth over a long period of time. For WAN connections, it is almost always necessary to buy bandwidth from a service provider. A network manager needs to make the right decisions about the kinds of equipment and services to buy.
l Bandwidth is not free l l l It is possible to buy equipment for a LAN that will provide nearly unlimited bandwidth over a long period of time. For WAN connections, it is almost always necessary to buy bandwidth from a service provider. A network manager needs to make the right decisions about the kinds of equipment and services to buy.
 l Bandwidth requirements are growing at a rapid rate l l l New network technologies and infrastructures are built to provide greater bandwidth. New applications are created to take advantage of the greater capacity. Streaming video and audio. IP telephony systems. The successful networking professional must anticipate the need for increased bandwidth and act accordingly.
l Bandwidth requirements are growing at a rapid rate l l l New network technologies and infrastructures are built to provide greater bandwidth. New applications are created to take advantage of the greater capacity. Streaming video and audio. IP telephony systems. The successful networking professional must anticipate the need for increased bandwidth and act accordingly.
 l Bandwidth is critical to network performance l l l It is a key factor in analyzing network performance, designing new networks, and understanding the Internet. Information flows as a string of bits from computer to computer throughout the world. The Internet is bandwidth.
l Bandwidth is critical to network performance l l l It is a key factor in analyzing network performance, designing new networks, and understanding the Internet. Information flows as a string of bits from computer to computer throughout the world. The Internet is bandwidth.
 The desktop (Analogies) l l Bandwidth has been defined as the amount of information that can flow through a network in a given time. There are two analogies that may make it easier to visualize bandwidth in a network. l l Bandwidth is like the width of a pipe. Bandwidth is like the number of lanes on a highway.
The desktop (Analogies) l l Bandwidth has been defined as the amount of information that can flow through a network in a given time. There are two analogies that may make it easier to visualize bandwidth in a network. l l Bandwidth is like the width of a pipe. Bandwidth is like the number of lanes on a highway.


 Measurement l l Bandwidth is the measure of how much information, or bits, can flow from one place to another in a given amount of time, or seconds. In digital systems, the basic unit of bandwidth is: l l l bits per second (bps) thousands of bits per second (kbps) millions of bits per second (Mbps) billions of bits per second (Gbps) trillions of bits per second (Tbps)
Measurement l l Bandwidth is the measure of how much information, or bits, can flow from one place to another in a given amount of time, or seconds. In digital systems, the basic unit of bandwidth is: l l l bits per second (bps) thousands of bits per second (kbps) millions of bits per second (Mbps) billions of bits per second (Gbps) trillions of bits per second (Tbps)

 l Bandwidth vs. Speed l l l They are not exactly the same thing. One may say, for example, that a T 3 connection at 45 Mbps operates at a higher speed than a T 1 connection at 1. 544 Mbps ? If only a small amount of their data-carrying capacity is being used, each of these connection types will carry data at roughly the same speed. It is usually more accurate to say that a T 3 connection has greater bandwidth than a T 1 connection. This is because the T 3 connection is able to carry more information in the same period of time, not because it has a higher speed.
l Bandwidth vs. Speed l l l They are not exactly the same thing. One may say, for example, that a T 3 connection at 45 Mbps operates at a higher speed than a T 1 connection at 1. 544 Mbps ? If only a small amount of their data-carrying capacity is being used, each of these connection types will carry data at roughly the same speed. It is usually more accurate to say that a T 3 connection has greater bandwidth than a T 1 connection. This is because the T 3 connection is able to carry more information in the same period of time, not because it has a higher speed.
 Limitations l Bandwidth varies depending upon the l l l Type of media : twisted-pair copper wire, coaxial cable, optical fiber, and air. LAN and WAN technologies used. The actual bandwidth is determined by the signaling methods, network interface cards (NICs), and other items of network equipment that are chosen.
Limitations l Bandwidth varies depending upon the l l l Type of media : twisted-pair copper wire, coaxial cable, optical fiber, and air. LAN and WAN technologies used. The actual bandwidth is determined by the signaling methods, network interface cards (NICs), and other items of network equipment that are chosen.


 Throughput l l l Bandwidth is the measure of the amount of information that can move through the network in a given period of time. Throughput refers to actual measured bandwidth, at a specific time of day, using specific Internet routes, and while a specific set of data is transmitted on the network. Throughput is often far less than the maximum possible digital bandwidth of the medium that is being used.
Throughput l l l Bandwidth is the measure of the amount of information that can move through the network in a given period of time. Throughput refers to actual measured bandwidth, at a specific time of day, using specific Internet routes, and while a specific set of data is transmitted on the network. Throughput is often far less than the maximum possible digital bandwidth of the medium that is being used.
 l The factors that determine throughput l l l l l Internetworking devices Type of data being transferred Network topology Number of users on the network Routing within the “Cloud” Time of day User computer Server computer Power conditions
l The factors that determine throughput l l l l l Internetworking devices Type of data being transferred Network topology Number of users on the network Routing within the “Cloud” Time of day User computer Server computer Power conditions
 Data transfer calculation l l transfer time = size of file / bandwidth (T=S/BW) Two important points should be considered when doing this calculation: l l The result is an estimate only, because the file size does not include any overhead added by encapsulation. A more accurate estimate can be attained if throughput is substituted for bandwidth in the equation.
Data transfer calculation l l transfer time = size of file / bandwidth (T=S/BW) Two important points should be considered when doing this calculation: l l The result is an estimate only, because the file size does not include any overhead added by encapsulation. A more accurate estimate can be attained if throughput is substituted for bandwidth in the equation.

 Digital versus analog l l Analog bandwidth is measured by how much of the electromagnetic spectrum is occupied by each signal. The basic unit of analog bandwidth is hertz (Hz), or cycles per second. The analog video signal that requires a wide frequency range for transmission cannot be squeezed into a smaller band. Therefore, if the necessary analog bandwidth is not available, the signal cannot be sent.
Digital versus analog l l Analog bandwidth is measured by how much of the electromagnetic spectrum is occupied by each signal. The basic unit of analog bandwidth is hertz (Hz), or cycles per second. The analog video signal that requires a wide frequency range for transmission cannot be squeezed into a smaller band. Therefore, if the necessary analog bandwidth is not available, the signal cannot be sent.
 l l l In digital signaling all information is sent as bits, regardless of the kind of information it is. Voice, video, and data all become streams of bits when they are prepared for transmission over digital media. Unlimited amounts of information can be sent over the smallest or lowest bandwidth digital channel.
l l l In digital signaling all information is sent as bits, regardless of the kind of information it is. Voice, video, and data all become streams of bits when they are prepared for transmission over digital media. Unlimited amounts of information can be sent over the smallest or lowest bandwidth digital channel.
 Outline l l l Networking Terminology Bandwidth Networking Models
Outline l l l Networking Terminology Bandwidth Networking Models
 Using layers to analyze problems in a flow of materials
Using layers to analyze problems in a flow of materials

 Using layers to describe data communication l l A data communications protocol is a set of rules or an agreement that determines the format and transmission of data. It is important that all the devices on the network must speak the same language or protocol on each layer.
Using layers to describe data communication l l A data communications protocol is a set of rules or an agreement that determines the format and transmission of data. It is important that all the devices on the network must speak the same language or protocol on each layer.

 OSI model l The early development of networks was disorganized in many ways. International Organization for Standardization (ISO) created the Open System Interconnection (OSI) reference model in 1984. It is considered the best tool available for teaching people about sending and receiving data on a network.
OSI model l The early development of networks was disorganized in many ways. International Organization for Standardization (ISO) created the Open System Interconnection (OSI) reference model in 1984. It is considered the best tool available for teaching people about sending and receiving data on a network.

 OSI layers l l The OSI reference model is a framework that is used to understand how information travels throughout a network. Advantages l l l It breaks network communication into smaller, more manageable parts. It standardizes network components to allow multiple vendor development and support. It allows different types of network hardware and software to communicate with each other. It prevents changes in one layer from affecting other layers. It divides network communication into smaller parts to make learning it easier to understand.
OSI layers l l The OSI reference model is a framework that is used to understand how information travels throughout a network. Advantages l l l It breaks network communication into smaller, more manageable parts. It standardizes network components to allow multiple vendor development and support. It allows different types of network hardware and software to communicate with each other. It prevents changes in one layer from affecting other layers. It divides network communication into smaller parts to make learning it easier to understand.







 Peer-to-peer communications l l Peer-to-peer : In order for data to travel from the source to the destination, each layer of the OSI model at the source must communicate with its peer layer at the destination. Each layer of communication on the source computer communicates with a layer-specific PDU (Protocol Data Unit), and with its peer layer on the destination computer. The lower layer uses encapsulation to put the PDU from the upper layer into its data field; then it adds whatever headers and trailers the layer needs to perform its function. Next, as the data moves down through the layers of the OSI model, additional headers and trailers are added.
Peer-to-peer communications l l Peer-to-peer : In order for data to travel from the source to the destination, each layer of the OSI model at the source must communicate with its peer layer at the destination. Each layer of communication on the source computer communicates with a layer-specific PDU (Protocol Data Unit), and with its peer layer on the destination computer. The lower layer uses encapsulation to put the PDU from the upper layer into its data field; then it adds whatever headers and trailers the layer needs to perform its function. Next, as the data moves down through the layers of the OSI model, additional headers and trailers are added.
 l The network layer l l Provides a service to the transport layer. Move the data through the internetwork. Encapsulate the data and attaching a header creating a packet (the Layer 3 PDU). The header contains information required to complete the transfer, such as source and destination logical addresses.
l The network layer l l Provides a service to the transport layer. Move the data through the internetwork. Encapsulate the data and attaching a header creating a packet (the Layer 3 PDU). The header contains information required to complete the transfer, such as source and destination logical addresses.
 l The data link layer l l Provides a service to the network layer. Encapsulates the network layer information in a frame (the Layer 2 PDU). The frame header contains information (for example, physical addresses) required to complete the data link functions. The data link layer provides a service to the network layer.
l The data link layer l l Provides a service to the network layer. Encapsulates the network layer information in a frame (the Layer 2 PDU). The frame header contains information (for example, physical addresses) required to complete the data link functions. The data link layer provides a service to the network layer.
 l l Segments Packets Frames Bits : layer 4 PDU : layer 3 PDU : layer 2 PDU : layer 1 PDU
l l Segments Packets Frames Bits : layer 4 PDU : layer 3 PDU : layer 2 PDU : layer 1 PDU

 TCP/IP model l l The U. S. Department of Defense (Do. D) created the TCP/IP reference model. For military purposes.
TCP/IP model l l The U. S. Department of Defense (Do. D) created the TCP/IP reference model. For military purposes.
 l TCP l The transport layer deals with the quality of service issues of reliability, flow control, and error correction. l l TCP is a connection-oriented protocol. IP l l Best path determination and packet switching occur at IP layer. IP can be thought to point the way for the packets, while TCP provides a reliable transport.
l TCP l The transport layer deals with the quality of service issues of reliability, flow control, and error correction. l l TCP is a connection-oriented protocol. IP l l Best path determination and packet switching occur at IP layer. IP can be thought to point the way for the packets, while TCP provides a reliable transport.

 l Application layer protocols l l l Transport Control Protocol (TCP) User Datagram Protocol (UDP) Internet layer l l File Transfer Protocol (FTP) Hypertext Transfer Protocol (HTTP) Simple Mail Transfer Protocol (SMTP) Domain Name System (DNS) Trivial File Transfer Protocol (TFTP) Internet Protocol (IP) Network access layer l Refers to any particular technology used on a specific network.
l Application layer protocols l l l Transport Control Protocol (TCP) User Datagram Protocol (UDP) Internet layer l l File Transfer Protocol (FTP) Hypertext Transfer Protocol (HTTP) Simple Mail Transfer Protocol (SMTP) Domain Name System (DNS) Trivial File Transfer Protocol (TFTP) Internet Protocol (IP) Network access layer l Refers to any particular technology used on a specific network.


 l Similarities include: l l l Both have layers. Both have application layers, though they include very different services. Both have comparable transport and network layers. Both models need to be known by networking professionals. Both assume packets are switched. This means that individual packets may take different paths to reach the same destination. This is contrasted with circuit-switched networks where all the packets take the same path.
l Similarities include: l l l Both have layers. Both have application layers, though they include very different services. Both have comparable transport and network layers. Both models need to be known by networking professionals. Both assume packets are switched. This means that individual packets may take different paths to reach the same destination. This is contrasted with circuit-switched networks where all the packets take the same path.
 l Differences include: l l l TCP/IP combines the presentation and session layer issues into its application layer. TCP/IP combines the OSI data link and physical layers into the network access layer. TCP/IP appears simpler because it has fewer layers. TCP/IP protocols are the standards around which the Internet developed, so the TCP/IP model gains credibility just because of its protocols. In contrast, networks are not usually built on the OSI protocol, even though the OSI model is used as a guide.
l Differences include: l l l TCP/IP combines the presentation and session layer issues into its application layer. TCP/IP combines the OSI data link and physical layers into the network access layer. TCP/IP appears simpler because it has fewer layers. TCP/IP protocols are the standards around which the Internet developed, so the TCP/IP model gains credibility just because of its protocols. In contrast, networks are not usually built on the OSI protocol, even though the OSI model is used as a guide.

 Detailed encapsulation process l Five conversion steps in order to encapsulate data: l l l Build the data. Package the data for end-to-end transport. Add the network IP address to the header. Add the data link layer header and trailer. Convert to bits for transmission.
Detailed encapsulation process l Five conversion steps in order to encapsulate data: l l l Build the data. Package the data for end-to-end transport. Add the network IP address to the header. Add the data link layer header and trailer. Convert to bits for transmission.
 l Build the data l l As a user sends an e-mail message, its alphanumeric characters are converted to data that can travel across the internetwork. Package the data for end-to-end transport l l The data is packaged for internetwork transport. By using segments, the transport function ensures that the message hosts at both ends of the e-mail system can reliably communicate.
l Build the data l l As a user sends an e-mail message, its alphanumeric characters are converted to data that can travel across the internetwork. Package the data for end-to-end transport l l The data is packaged for internetwork transport. By using segments, the transport function ensures that the message hosts at both ends of the e-mail system can reliably communicate.
 l Add the network IP address to the header l l l The data is put into a packet or datagram that contains a packet header with source and destination logical addresses. These addresses help network devices send the packets across the network along a chosen path. Add the data link layer header and trailer l l Each network device must put the packet into a frame. The frame allows connection to the next directlyconnected network device on the link.
l Add the network IP address to the header l l l The data is put into a packet or datagram that contains a packet header with source and destination logical addresses. These addresses help network devices send the packets across the network along a chosen path. Add the data link layer header and trailer l l Each network device must put the packet into a frame. The frame allows connection to the next directlyconnected network device on the link.
 l Convert to bits for transmission l l l The frame must be converted into a pattern of 1 s and 0 s (bits) for transmission on the medium. The medium on the physical internetwork can vary along the path used. For example, the e-mail message can originate on a LAN, cross a campus backbone, and go out a WAN link until it reaches its destination on another remote LAN.
l Convert to bits for transmission l l l The frame must be converted into a pattern of 1 s and 0 s (bits) for transmission on the medium. The medium on the physical internetwork can vary along the path used. For example, the e-mail message can originate on a LAN, cross a campus backbone, and go out a WAN link until it reaches its destination on another remote LAN.


 Good luck in your exams !
Good luck in your exams !


