26b702623b66701c1ef6fa1cfa1a991a.ppt
- Количество слайдов: 75

SEMANTIC WEB COMMUNICATION “Realizing What Semantic Web Can Be……. ” Anup Patel - 07305042 Sapan Shah - 07305061 Nilesh Padariya - 07305064 Vishal Vachhani - 07305 R 01
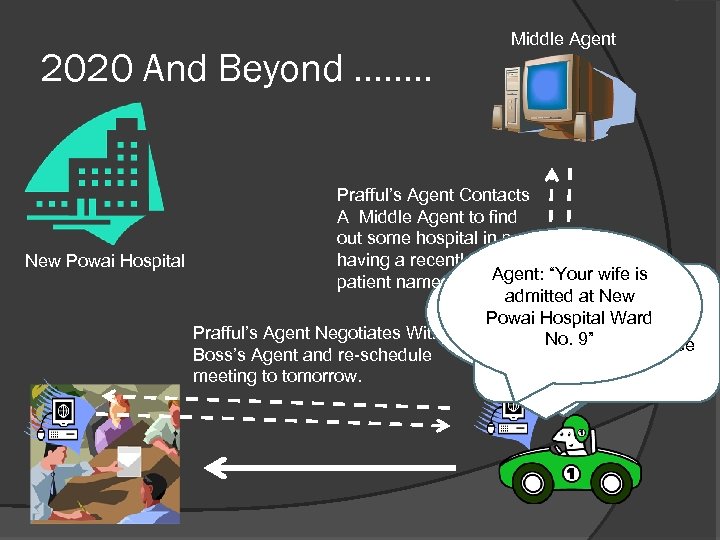
2020 And Beyond ……. . Middle Agent Prafful’s Agent Contacts A Middle Agent to find out some hospital in powai having a recently admitted New Powai Hospital Phone: “Your wife is had Agent: patient named Hansa. Agent: accident Newis is an “Yourat don’t admitted meeting Prafful: “I stillshe know re-scheduled have Prafful: should Prafful: to admitted at“Isome Powai Hospital“I admitted where is she. Ward Prafful’s Agent Negotiates With tomorrow 5: 00 agent informpowai …” a my hospitalmeeting with use No. …. PM” in powaiin 9” I should Boss’s Agent and re-schedule to reschedule. I my boss and my agent …. ” meeting to tomorrow. am late ……. ” meeting”

Motivation Original driver: Automation - Make information on the Web more “machine-friendly” - Origins of the Semantic Web are in web metadata Short term goal: Interoperability - Combining information from multiple sources - Web Services: discovery, composition Long term goal: “Departure from the Tool Paradigm” - instead of using computers like tools, make them work on our behalf - removing humans from the loop to the extent possible

Roadmap 1. 2. 3. 4. 5. 6. 7. 8. 9. Semantic Web Introduction Semantic Web Agents Multi-Agent System Communication Agent Communication Language SPARQL Semantic Web Trust Semantic Web Status Conclusion Bibliography

1. Semantic Web The Semantic Web is an evolving extension of the World Wide Web in which web content can be expressed not only in natural language, but also in a format that can be read and used by software agents, thus permitting them to find, share and integrate information more easily. -- Wikipedia
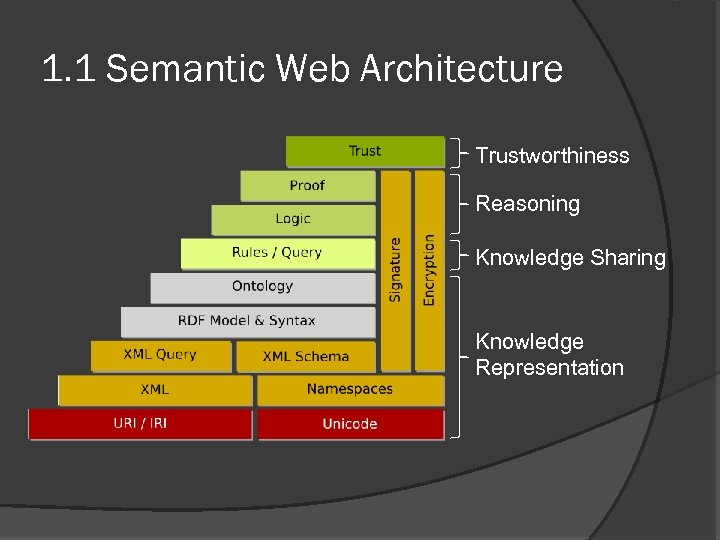
1. 1 Semantic Web Architecture Trustworthiness Reasoning Knowledge Sharing Knowledge Representation

1. 2 Tree of Knowledge Technologies Semantic Technology Languages AI Knowledge Representation Content Management Languages Process Knowledge Languages Software Modeling Languages

2. Semantic Web Agents Agent in AI is any thing that can be viewed as perceiving its environment through sensors and acting upon that environment through effectors, showing a rational behavior. E. g. A human agent has eyes, ears and other organs as as sensors, and hands, legs, mouth, and other body parts for effectors. Agent = Architecture + Program. Semantic Web Agents are agents in the web environment.

2. 1 Agent Definition The definition of agents has not been agreed upon universally but, we can have some good characteristic of such agents, which are : - Autonomy - Reasoning Ability - Learning Ability - Mobility - Sociability - Cooperation - Negotiation

2. 1 Agent Definition (Contd. . ) From semantic web point of view agents can be thought of as intelligent software program that host a collection of web services. Unlike standard Web Services, an agent can reason about: - How to handle external request ? - Order in which to carry out the request ?

2. 2 Multi-Agent System (MAS) MAS is distributed system which incorporates more than one independent agents. The collection of agents interact, and solve problems that are outside their individual capacities. Agents in MAS display a dual behavior: on the one hand they are goal directed programs that autonomously solve problems and on the other hand have a social dimension when they interoperate as part of MAS. Semantic web in future will be one large MAS containing millions of agents communicating with each other.

2. 2 Multi-Agent System (Contd. ) Ontologies in MAS provide agents : - The basic representation that allows them to reason about interactions with other agents. - Shared knowledge that they can use to communicate and work together. In general we can distinguish between Private Ontologies that allow the agent to organize its own problem solving and reasoning, and Public Ontologies that the agent shares with the rest of the agents in the MAS. Private ontologies are used to represent Private Knowledge whereas, public ontologies are used to represent Public Knowledge of an semantic web agent.
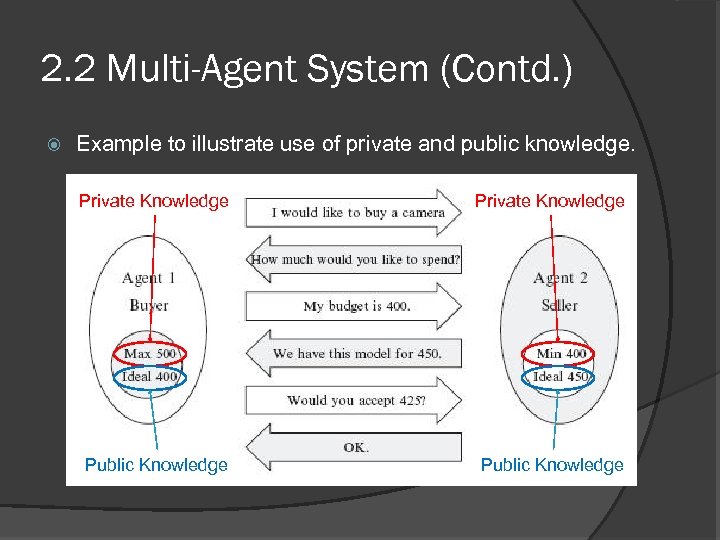
2. 2 Multi-Agent System (Contd. ) Example to illustrate use of private and public knowledge. Private Knowledge Public Knowledge
3. MAS Communication In MAS communication we are effectively seeking to mimic the process of (verbal) communication between humans, which by itself is very ambitious task. At the lowest level, there are two main techniques that facilitate communication: - Message Passing: The agents communicate by the direct exchange of messages that encapsulate knowledge. - Shared State: The Agents communicate by asserting and retracting facts in a shared knowledge base. The web uses a message passing approach (TCP + UDP) so, semantic web communication also have based on message passing approach (HTTP + XML).
3. MAS Communication (Contd. ) For communication on semantic web some issues must be promptly addressed, like: - Automatic discovery of agents. - Effectively manage the shared knowledge. - It must be coordinated, correct, and robust to failure. To solve the problem of automatic discovery of agents we have Middle-Agent architectures. To solve the problem of managing shared knowledge we have network architectures.
3. 1 Middle Agent Architecture Middle-agents assist in locating service providers, and connecting service providers with service requesters. A variety of middle agent types based on privacy considerations of service providers capabilities and requesters preferences are possible. Middle Agent Architectures are techniques to solve problem of automated discovery of agents in MAS.

3. 1 Middle Agent Architecture (Contd. ) Two important types of middle-agent have been identified. Service Matchmaker: The Matchmaker serves as a "yellow pages" of agent capabilities, matching service providers with service requestors based on agent capability descriptions. The Matchmaker system allows agents to find each other by providing a mechanism for registering each agent's capabilities. For each query it searches its dynamic database of "advertisements" for a registered agent that can fulfill the incoming request.

3. 1 Middle Agent Architecture (Contd. ) Service Matchmaker
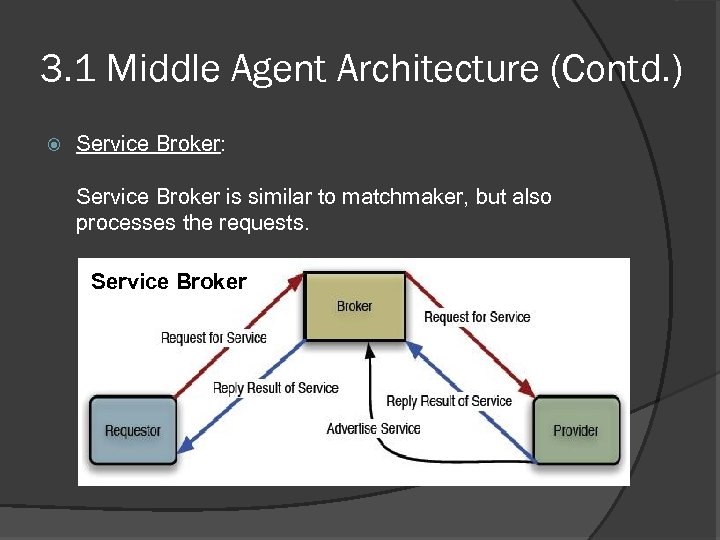
3. 1 Middle Agent Architecture (Contd. ) Service Broker: Service Broker is similar to matchmaker, but also processes the requests. Service Broker
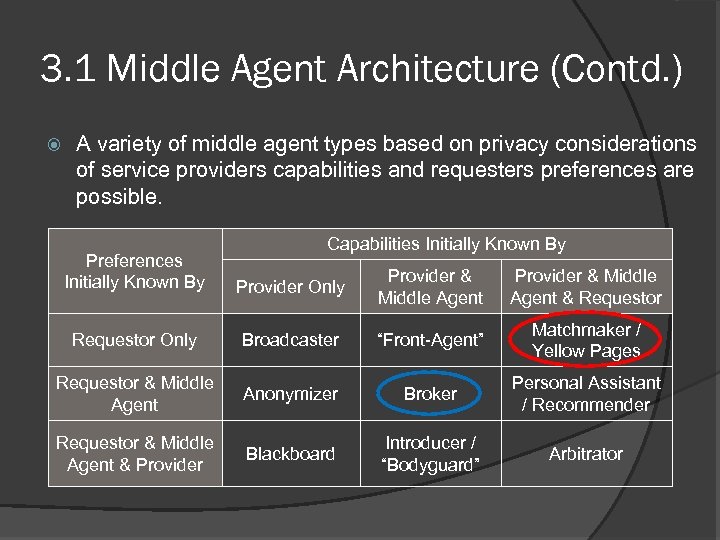
3. 1 Middle Agent Architecture (Contd. ) A variety of middle agent types based on privacy considerations of service providers capabilities and requesters preferences are possible. Capabilities Initially Known By Preferences Initially Known By Provider Only Provider & Middle Agent & Requestor Only Broadcaster “Front-Agent” Matchmaker / Yellow Pages Requestor & Middle Agent Anonymizer Broker Personal Assistant / Recommender Requestor & Middle Agent & Provider Blackboard Introducer / “Bodyguard” Arbitrator
3. 2 Network Architectures so far, mainly assumed some kind of centralized client/server architecture. But Service Oriented Architectures can equally well be decentralized. Network Architectures are techniques to effectively store and retrieve shared knowledge of all agents in MAS. We can three types of architectures possible here: - Centralized (Client-Server) - Decentralized (Peer-to-Peer) - Hybrid (Client-Server and Peer-to-Peer)

3. 2 Network Architecture (Contd. ) Centralized (Client-Server):
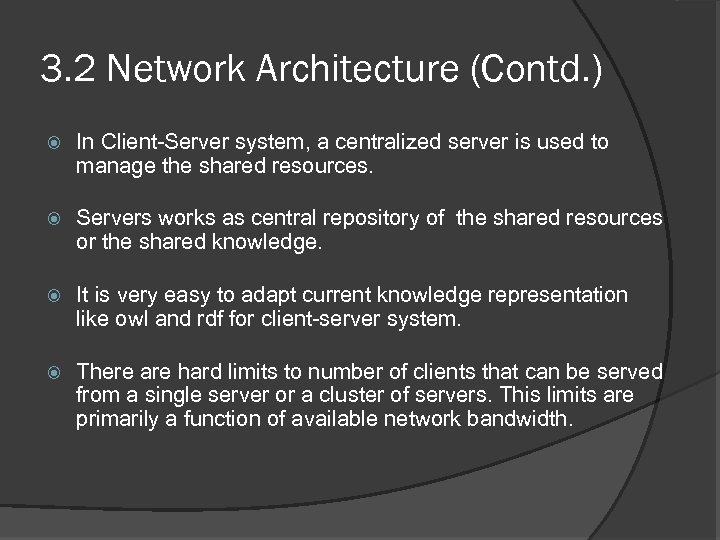
3. 2 Network Architecture (Contd. ) In Client-Server system, a centralized server is used to manage the shared resources. Servers works as central repository of the shared resources or the shared knowledge. It is very easy to adapt current knowledge representation like owl and rdf for client-server system. There are hard limits to number of clients that can be served from a single server or a cluster of servers. This limits are primarily a function of available network bandwidth.
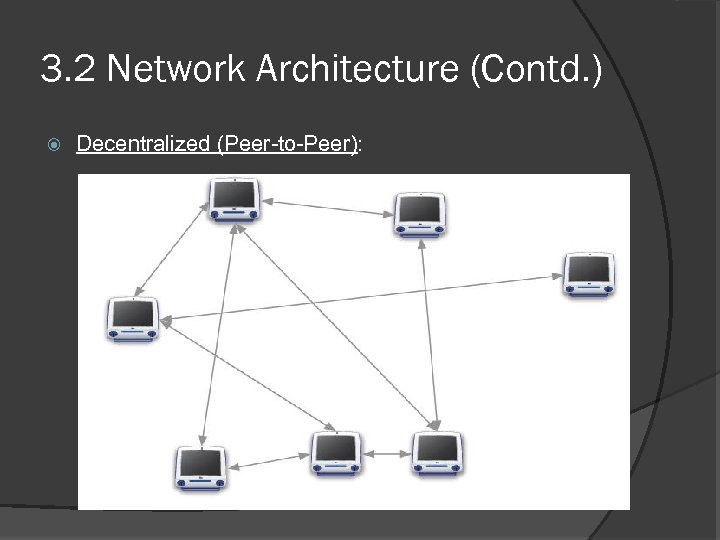
3. 2 Network Architecture (Contd. ) Decentralized (Peer-to-Peer):
3. 2 Network Architecture (Contd. ) P 2 P is a self-organizing system of equal, autonomous entities (peers) which aims for the shared usage of distributed resources in a networked environment avoiding central services. Peers interact directly with each other, usually without central coordination. Each peer has autonomy over its own resources. Peers can act as both clients and servers; i. e. , no intrinsic asymmetry of role. The network saturation problem does not occur to decentralized P 2 P network.
3. 2 Network Architecture (Contd. ) In this approach information is copied and distributed throughout network. Thus, when a client wish to obtain some information it can retrieve it from multiple sources and thereby avoid overloading at one node. For Example: Bit Torrent, DC++ Construction of P 2 P architecture for semantic web has important design implications : - The communicative process must be adapted to work with specific P 2 P technique. - The reasoning process must make decisions on what information to share and how to retrieve information required for reasoning.
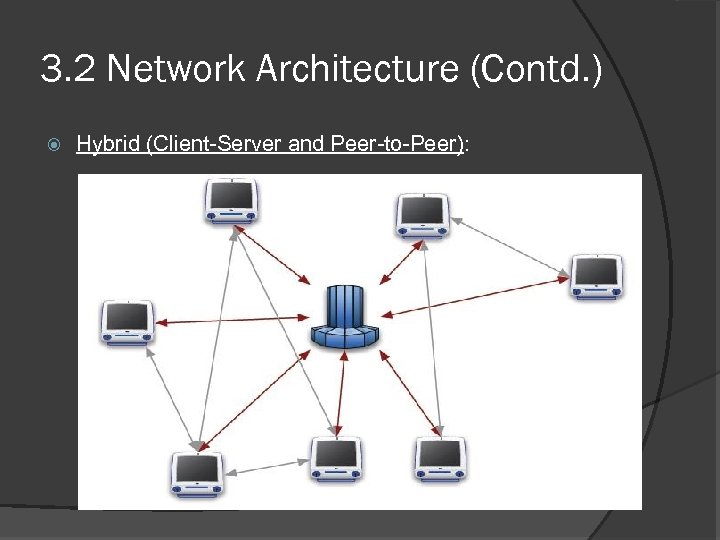
3. 2 Network Architecture (Contd. ) Hybrid (Client-Server and Peer-to-Peer):

4. Agent Communication Language Abbreviated as ‘ACL’ for short. In agent communication our source of inspiration in human communication. We try to mimic human communication in ACL. The foundation of ACL lies in the Speech Act Theory.

4. 1 Speech Act Proposed by John Austin extended by John Searle. How language is used by people everyday to achieve their goals and intentions. Certain natural language utterances have the characteristics of physical actions. Certain performative verbs in speech act changes the state of the world like physical actions.

4. 2 Types of Speech Acts Representative: which commits the speaker to the truth of what is being asserted. e. g. inform Directive: attempts to get the hearer to do something e. g. , ‘please make the tea’ Commisives: which commit the speaker for doing something, e. g. , ‘I promise to…’ Expressive: whereby a speaker expresses a mental state, e. g. , ‘thank you!’ Declarative: effect some change on the state of affairs. e. g. declaring war.

4. 3 Components of Speech Act In general Two Components: – Performative Verb (e. g. , request, inform, promise, … ) – Propositional Content (e. g. , “the door is closed”) More Examples: performative = request content = “the door is closed” speech act = “please close the door” performative = inquire content = “the door is closed” speech act = “is the door closed ? ”

4. 4 ACL Examples Communication is performed by exchanging messages where each message has an associated performativemessage types. Agent Communication Languages define common sets of performatives. Two Popular ACLs - KQML - FIPA-ACL.
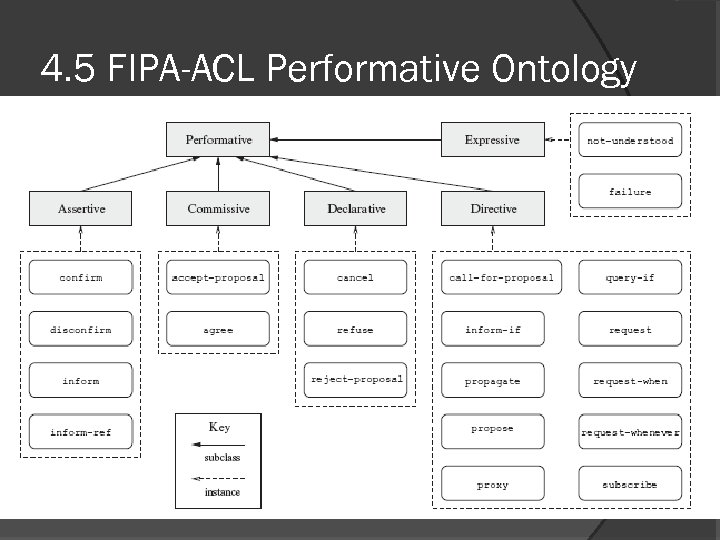
4. 5 FIPA-ACL Performative Ontology

4. 6 Basic Problem of FIPA-ACL Semantics Verification Problem Sincerity Assumption – agent always acts in accordance with their intentions. Too restrictive in open environment – web. Despite these FIPA-ACL remained popular - e. g. JADE multi agent platform – performatives are used to facilitate the exchange of message but compliance with formal model is not enforce.

4. 7 Dialogue Communication rarely consists of a single act of speech in isolation. It typically consists of sequence of messages exchanges between participants such as Conversation. This type of communication is termed as Dialogue.
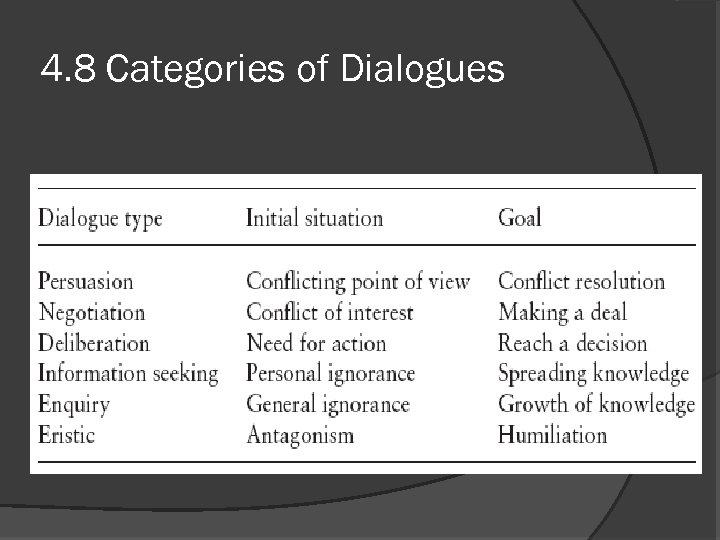
4. 8 Categories of Dialogues

4. 9 Dialogue frames Key construct – Dialogue Type identifies dialogue type & kind of values over which it operates. Different Dialogues can take different kind of values. e. g. Beliefs, Contract, Plans Frame F is a tuple with four elements ( T, V , t, U) T = Dialogue Type V = Value over which the dialogue operates t = Topic of the Dialogue U = list of utterances which define the actual dialogue steps between the participants x & y e. g. {U}

4. 10 Protocols in FIPA-ACL It refers to the stereotyped pattern of conversation between the agents. The protocols are generally pre-specified by the agent designer & agents needs to discover which protocols to follow during Dialogue. Choice of protocols to be followed can be negotiated by the agents. In FIPA-ACL the convention is to put the name of the protocol in the : protocol parameter of the message.
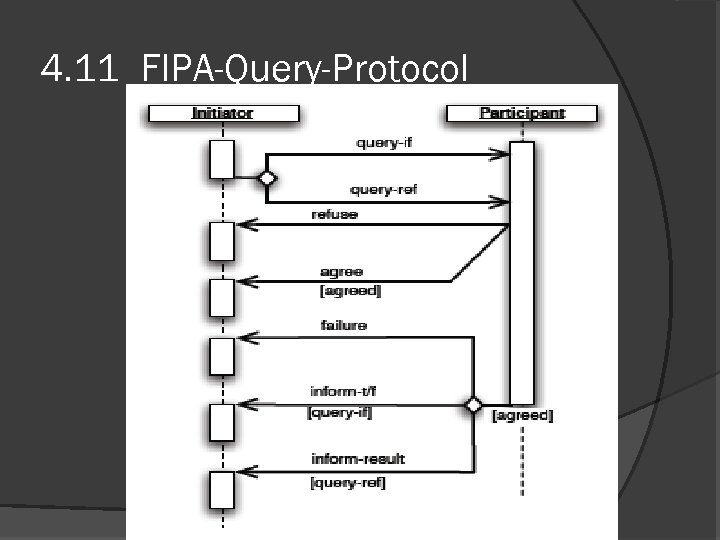
4. 11 FIPA-Query-Protocol
4. 12 ACL in MAS Reduce the complexity to pair wise interaction between agents. Has limitations in terms of multicast & broadcast communication. As the size of the MAS increases, the ability to communicate reliably deteriorates. MAS operating over web has to face some basic problems such as delay in message passing, messages may be lost. So Asynchronous agents are required. An open MAS is designed to enable interoperability between agents from many different sources. These may introduce problems like malicious, untrustworthy agents.

5. SPARQL Simple Protocol And Rdf Query Language SPARQL = Query Language + Protocol + XML Results Format It’s a Query language for RDF Data, and it involves: - Basic graph pattern matching. - No inference in the query language itself. As a Protocol it uses: - HTTP binding - SOAP binding XML Results Format are: - Easy to transform (XSLT, XQuery)

5. 1 It’s Turtles all the way down Turtle (Terse RDF Triple Language ): − An RDF serialization <http: //example/person/A> <http: //xmlns. com/foaf. 0. 1/name> “Nilesh” − The RDF part of N 3 − Human-friendly alternative to RDF/XML Blank Node @prefix person: <http: //example/person/>. @prefix foaf: <http: //xmlns. com/foaf/0. 1/>. person: A foaf: name “Nilesh". person: A foaf: mbox <mailto: nileshsp@example. net>. ------person: B foaf: name “Sapan". | name | _: b foaf: name “Vishal". _: b foaf: mbox <mailto: vishalv@example. org> ====. | “Nilesh” | | ”Sapan”| A "hello world" of queries | ”Vishal” | SELECT ? name ------WHERE { ? x foaf: name ? name }
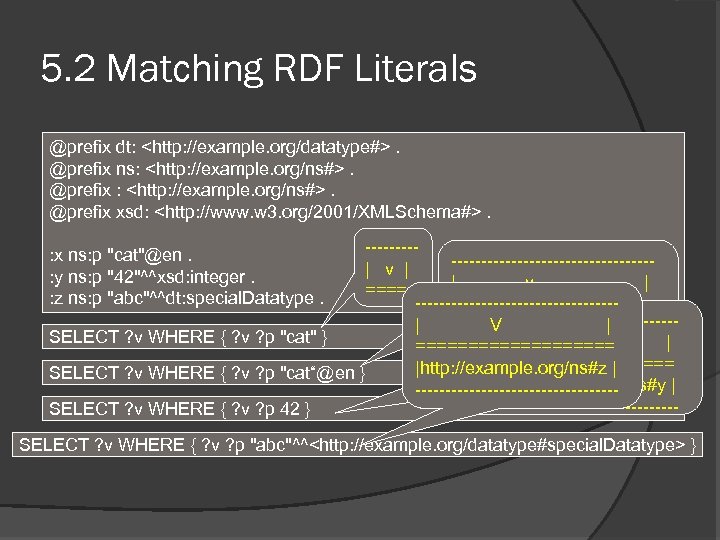
5. 2 Matching RDF Literals @prefix dt: <http: //example. org/datatype#>. @prefix ns: <http: //example. org/ns#>. @prefix xsd: <http: //www. w 3. org/2001/XMLSchema#>. ---------------------| v | ===== -----------------========== -----------------| V | |http: //example. org/ns#x | SELECT ? v WHERE { ? v ? p "cat" } | V ========== ----------------- | ========== |http: //example. org/ns#z | SELECT ? v WHERE { ? v ? p "cat“@en } |http: //example. org/ns#y | ---------------------------------SELECT ? v WHERE { ? v ? p 42 } : x ns: p "cat"@en. : y ns: p "42"^^xsd: integer. : z ns: p "abc"^^dt: special. Datatype. SELECT ? v WHERE { ? v ? p "abc"^^<http: //example. org/datatype#special. Datatype> }
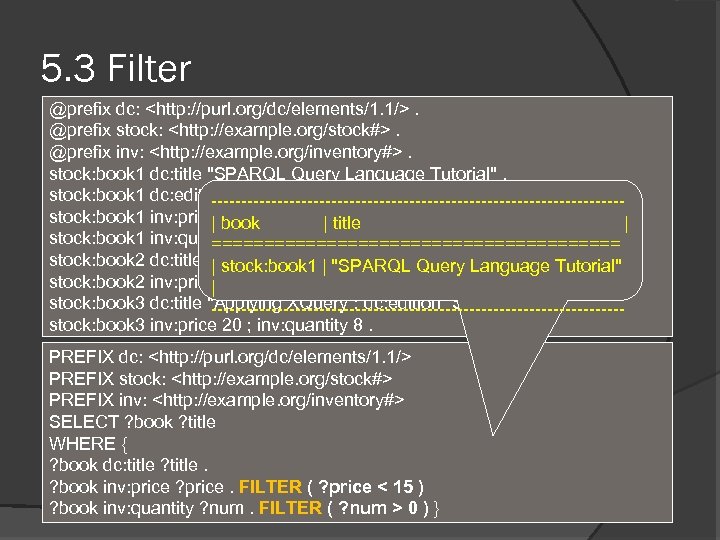
5. 3 Filter @prefix dc: <http: //purl. org/dc/elements/1. 1/>. @prefix stock: <http: //example. org/stock#>. @prefix inv: <http: //example. org/inventory#>. stock: book 1 dc: title "SPARQL Query Language Tutorial". stock: book 1 dc: edition “First” ----------------------------------stock: book 1 inv: price book | 10. | title | stock: book 1 inv: quantity 3. ==================== stock: book 2 dc: title "SPARQL Query Language (2 nd Language Tutorial" | stock: book 1 | "SPARQL Query ed)". stock: book 2 inv: price 20 ; inv: quantity 5. | stock: book 3 dc: title "Applying XQuery“; dc: edition “Second”. ----------------------------------stock: book 3 inv: price 20 ; inv: quantity 8. PREFIX dc: <http: //purl. org/dc/elements/1. 1/> PREFIX stock: <http: //example. org/stock#> PREFIX inv: <http: //example. org/inventory#> SELECT ? book ? title WHERE { ? book dc: title ? title. ? book inv: price ? price. FILTER ( ? price < 15 ) ? book inv: quantity ? num. FILTER ( ? num > 0 ) }

5. 4 Other Solution Modifiers PREFIX dc: <http: //purl. org/dc/elements/1. 1/> SELECT ? title ? edition { ? x dc: title ? title. OPTIONAL {? x dc: edition ? edition } } PREFIX foaf: <http: //xmlns. com/foaf/0. 1/> SELECT ? name WHERE { ? x foaf: name ? name } ORDER BY ? name PREFIX foaf: <http: //xmlns. com/foaf/0. 1/> SELECT DISTINCT ? name WHERE { ? x foaf: name ? name } ORDER BY ? name LIMIT 5 OFFSET 10
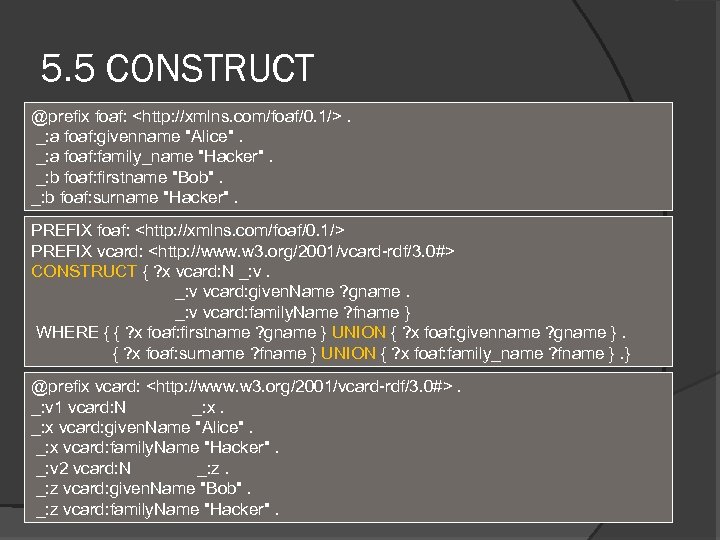
5. 5 CONSTRUCT @prefix foaf: <http: //xmlns. com/foaf/0. 1/>. _: a foaf: givenname "Alice". _: a foaf: family_name "Hacker". _: b foaf: firstname "Bob". _: b foaf: surname "Hacker". PREFIX foaf: <http: //xmlns. com/foaf/0. 1/> PREFIX vcard: <http: //www. w 3. org/2001/vcard-rdf/3. 0#> CONSTRUCT { ? x vcard: N _: v vcard: given. Name ? gname. _: v vcard: family. Name ? fname } WHERE { { ? x foaf: firstname ? gname } UNION { ? x foaf: givenname ? gname }. { ? x foaf: surname ? fname } UNION { ? x foaf: family_name ? fname }. } @prefix vcard: <http: //www. w 3. org/2001/vcard-rdf/3. 0#>. _: v 1 vcard: N _: x vcard: given. Name "Alice". _: x vcard: family. Name "Hacker". _: v 2 vcard: N _: z vcard: given. Name "Bob". _: z vcard: family. Name "Hacker".

5. 6 DESCRIBE PREFIX books: <http: //example. org/book/> PREFIX dc: <http: //purl. org/dc/elements/1. 1/> DESCRIBE ? book WHERE { ? book dc: title "Harry Potter and the Prisoner Of Azkaban" } <rdf: RDF> <rdf: Description rdf: about="http: //example. org/book 3"> <dc: creator rdf: parse. Type="Resource"> <vcard: N rdf: parse. Type="Resource"> <vcard: Given>Joanna</vcard: Given> <vcard: Family>Rowling</vcard: Family> </vcard: N> <vcard: FN>J. K. Rowling</vcard: FN> </dc: creator> <dc: title>Harry Potter and the Prisoner Of Azkaban</dc: title> </rdf: Description> </rdf: RDF>
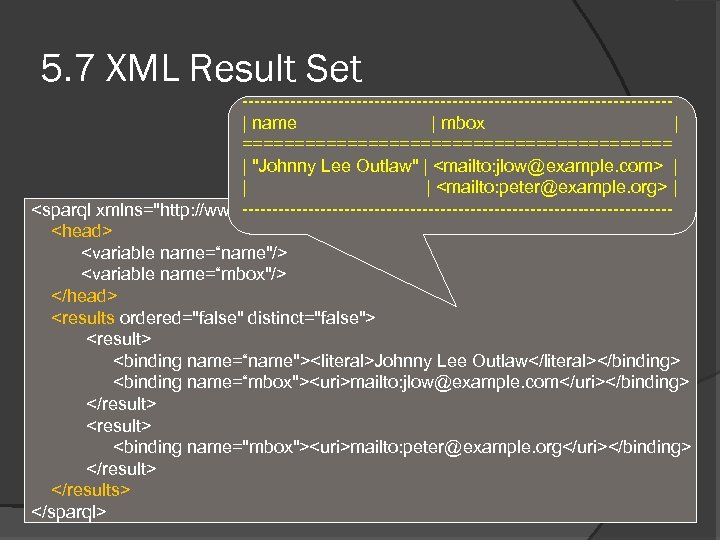
5. 7 XML Result Set ------------------------------------| name | mbox | ===================== | "Johnny Lee Outlaw" | <mailto: jlow@example. com> | | | <mailto: peter@example. org> | ------------------------------------<sparql xmlns="http: //www. w 3. org/2005/sparql-results#"> <head> <variable name=“name"/> <variable name=“mbox"/> </head> <results ordered="false" distinct="false"> <result> <binding name=“name"><literal>Johnny Lee Outlaw</literal></binding> <binding name=“mbox"><uri>mailto: jlow@example. com</uri></binding> </result> <binding name="mbox"><uri>mailto: peter@example. org</uri></binding> </results> </sparql>
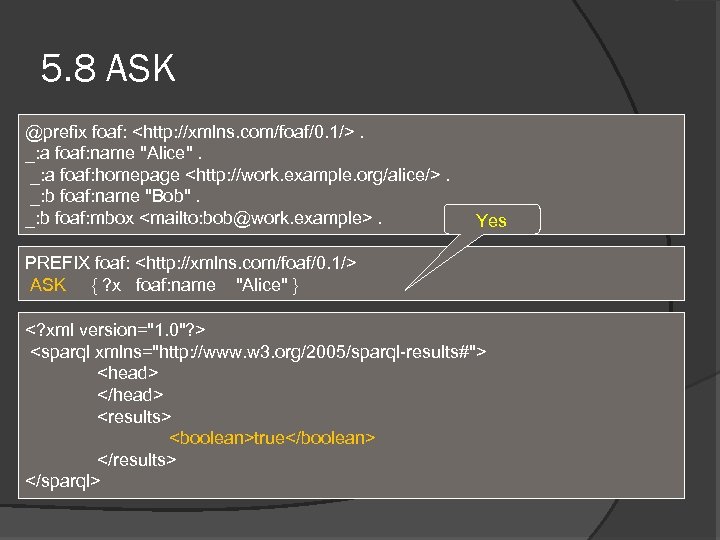
5. 8 ASK @prefix foaf: <http: //xmlns. com/foaf/0. 1/>. _: a foaf: name "Alice". _: a foaf: homepage <http: //work. example. org/alice/>. _: b foaf: name "Bob". _: b foaf: mbox <mailto: bob@work. example>. Yes PREFIX foaf: <http: //xmlns. com/foaf/0. 1/> ASK { ? x foaf: name "Alice" } <? xml version="1. 0"? > <sparql xmlns="http: //www. w 3. org/2005/sparql-results#"> <head> </head> <results> <boolean>true</boolean> </results> </sparql>

5. 9 More Features RDF Dataset - Collection of RDF Graphs - use FROM <http: //planetrdf. com/bloggers. rdf> & FROM NAMED <http: //site 1. example. com/foo. rdf> Inbuilt functions for testing values - Is. Literal - Is. Blank - str - regex
5. 10 Limitation of SPARQL No nested queries No Insert, Update, Delete queries No aggregation functions

6. Semantic Web Trust Some of the important questions for the Semantic Web Communication are : - How trust worthy is the information found on semantic web ? - How do I decide that an agent is trust worth ? To answer this questions we have semantic web trust in action.

6. 1 Basic Terms Security : A goal, bad things don't happen Privacy: A goal, personal information is not disclosed or abused Policy: Rules for behavior Provenance: Information (metadata) about the source of some piece of data Trust: Belief in (expectation of) the behavior of a party for some given purpose
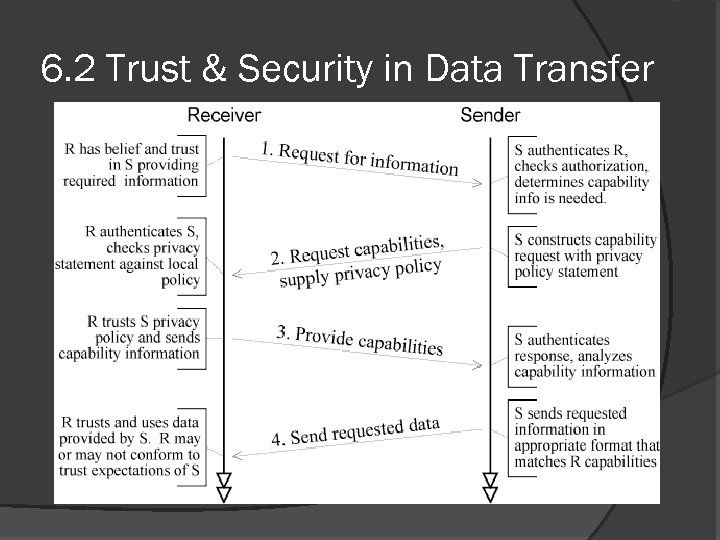
6. 2 Trust & Security in Data Transfer
6. 3 Basic Roles Information Providers - Want that their information is used / believed. - Might want to state their publishing intend (assertion, quote). Information Consumers - Want to use the information for different tasks. - Have different views of the world. - Have different subjective trust requirements. - Have different subjective preferences for certain trust mechanisms.

6. 4 Trust Policies We use a wide range of trust policies in everyday life: - We might trust Andy on restaurants but not on computers. - Buy only from sellers on e. Bay who have more than 100 positive ratings. - Regard literature as irrelevant, when it is older than 5 years, - Trust professors on their research field, believe foreign news only when they are reported by several independent sources. Goal : Allow a similar wide range of trust policies on the Semantic Web.
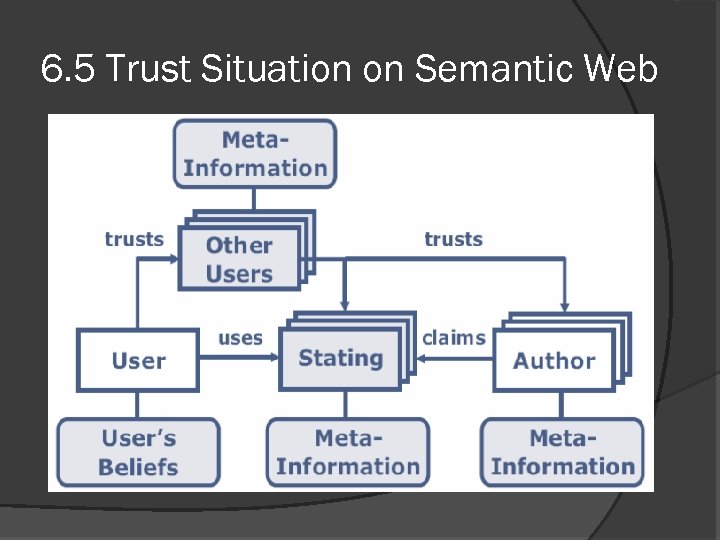
6. 5 Trust Situation on Semantic Web
6. 6 Requirements Of SW Trust Layer Use of all trust relevant information available: - WWWWW: who, what, where, when and why Support different, subjective, task-specific trust policies - Reputation-based - Context-based - Content-based Note: many applications don’t require total trustworthiness.
6. 7 Trust Mechanisms We can classify trust mechanisms into three categories based on support to different, subjective, and task-specifice trust policies: 1. Reputation-based trust mechanism 2. Context-based trust mechanism 3. Content-based trust mechanism
6. 7 Trust Mechanisms (Contd. ) Reputation-Based Trust Mechanism: - Include rating systems and web-of-trust mechanisms are a well researched area - Have a general problem: They require explicit and topic-specific trust ratings high effort for information consumers

6. 7 Trust Mechanisms (Contd. ) Context-Based Trust Mechanism: - Use background information about the information provider. - agents role in the application domain or his membership in a specific group e. g. policy: "Distrust everything a vendor says about his competitor“ or “Trust all members of organization A. ” - Information created in the information gathering process. - publishing and retrieval date and the retrieval URL - Information whether a signature is verifiable or not. e. g. policy: “Trust all information which has been signed and is not older than a month. ”

6. 7 Trust Mechanisms (Contd. ) Content-Based Trust Mechanism: - Use information content itself, together related information content published by other information providers. - Example policies: “Believe information which has been stated by at least independent sources. ” “Distrust product prices that are more than 50% below the average price. ”
6. 8 Named Graphs -Introduction Extension of RDF Graph For a named graph ng = ( n, g ) name(ng) = n rdfgraph(ng) = g A set of Named Graphs is collation of RDF graphs, each one of which is named with a URI Usefulness: - Foundation for the Trust layer - Restring information access - Keep tract of provenance Information - Signing RDF graphs - Information consumer can calculate Trust
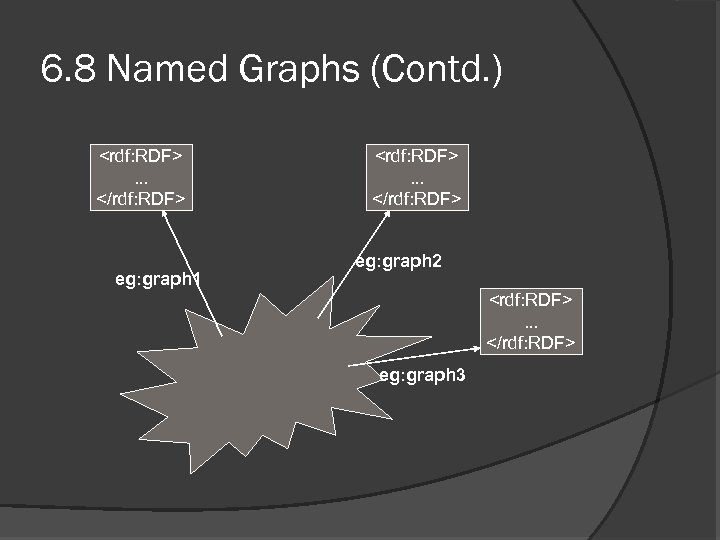
6. 8 Named Graphs (Contd. ) <rdf: RDF>. . . </rdf: RDF> eg: graph 1 <rdf: RDF>. . . </rdf: RDF> eg: graph 2 <rdf: RDF>. . . </rdf: RDF> eg: graph 3

6. 9 Accepting Graphs A set of named graphs N will not give us a single meaning. Semantics can be determined by a subset A of N. There are total 2|N| subsets of N, hence we have 2|N| different meanings of N. Thus, trust is problem of determining A.
6. 10 Introduction To Tri. QL. P is a query language, that allows the formulation of trust policies within queries - uses graph patterns - supports set operations and different ranking mechanisms - returns justification trees together with the query results Justification trees - provide explanations why data should be trusted
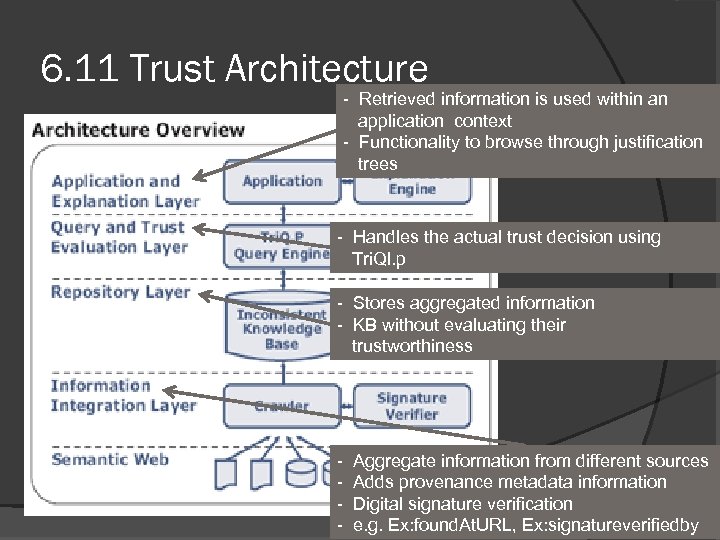
6. 11 Trust Architecture - Retrieved information is used within an application context - Functionality to browse through justification trees - Handles the actual trust decision using Tri. Ql. p - Stores aggregated information - KB without evaluating their trustworthiness - Aggregate information from different sources Adds provenance metadata information Digital signature verification e. g. Ex: found. At. URL, Ex: signatureverifiedby

6. 11 Algorithm For Trust Evaluation K is initial RDF KB (possibly empty or not), Input : a set of Named Graph N Algorithm: 1. Set A : = {} 2. choose n ∈ domain(N) − A, or terminate. 3. Set K’ : = K Ů n 4. If K’ is inconsistent then backtrack to 2. 5. if K’ is consistent then apply Trust policies 6. If it satisfies policies then set K : = K’ and A : = A Ů {n}, otherwise backtrack to 2. 7. Repeat from 2. Output: a set A – a set of Graph on which we can trust.
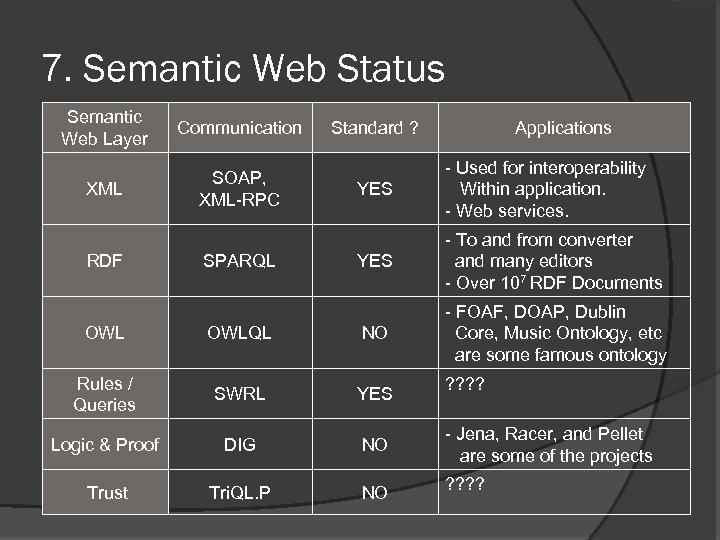
7. Semantic Web Status Semantic Web Layer Communication XML SOAP, XML-RPC RDF SPARQL Standard ? Applications YES - Used for interoperability Within application. - Web services. YES - To and from converter and many editors - Over 107 RDF Documents - FOAF, DOAP, Dublin Core, Music Ontology, etc are some famous ontology OWLQL NO Rules / Queries SWRL YES Logic & Proof DIG NO - Jena, Racer, and Pellet are some of the projects Trust Tri. QL. P NO ? ? ? ?

8. Conclusion Knowledge representation is very well developed in semantic web. Agent communication is still an active area of research, though we have standardized language like SPARQL, still lot of research is required in applying languages like FIPA-ACL to semantic web. Semantic web trust still remains the least explored of all the layers of semantic web. Named graphs laid an important foundation in this area. All in all semantic web is still a research field in academia
9. Bibliography Introduction - http: //www. wikipedia. org/Semantic_Web - http: //www. cs. cmu. edu/%7 Esoftagents/middle. html - Agency and Semantic Web, By Christopher Walton, Oxford Press. - Explorers Guide To Semantic Web, By Thomas B. P. , Manning Publication.

9. Bibliography (Contd. ) Agent Communication - Agency and Semantic Web, By Christopher Walton, Oxford Press. - Explorers Guide To Semantic Web, By Thomas B. P. , Manning Publication. - Lecture Notes of Multi-agent Semantic Web Systems, University of Edinburgh. SPARQL - http: //www. w 3. org/TR/2007/CR-rdf-sparql-query-20070614/ - http: //www. dajobe. org/2004/01/turtle/
9. Bibliography (Contd. ) Semantic Web Trust - http: //www. w 3. org/2004/03/trix/ (Named Graph Website, Link to Tri. QL) - http: //www. hpl. hp. com/techreports/2004/HPL-2004 -57. html (Named Graphs, Provenance and Trust) - http: //www. wiwiss. fu-berlin. de/suhl/bizer/Tri. QLP (Named Graphs paper by Carroll & Stickler) (Tri. QL. P) - http: //citeseer. ist. psu. edu/article/bizer 04 using. html (C. Bizer and R. Oldakowski. Using Context- and Content. Based Trust Policies on the Semantic Web. In 13 th World Wide Web Conference, WWWW 2004 (Poster), 2004. )

Questions ……. . ? ?

Thank You ……. .
26b702623b66701c1ef6fa1cfa1a991a.ppt